Network Addressing Lesson 4 Objectives Exam Objective Matrix

Network Addressing Lesson 4
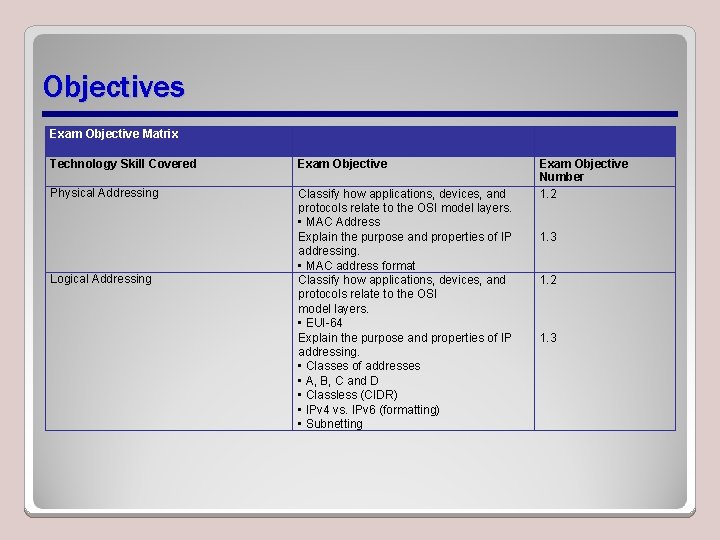
Objectives Exam Objective Matrix Technology Skill Covered Exam Objective Physical Addressing Classify how applications, devices, and protocols relate to the OSI model layers. • MAC Address Explain the purpose and properties of IP addressing. • MAC address format Classify how applications, devices, and protocols relate to the OSI model layers. • EUI-64 Explain the purpose and properties of IP addressing. • Classes of addresses • A, B, C and D • Classless (CIDR) • IPv 4 vs. IPv 6 (formatting) • Subnetting Logical Addressing Exam Objective Number 1. 2 1. 3
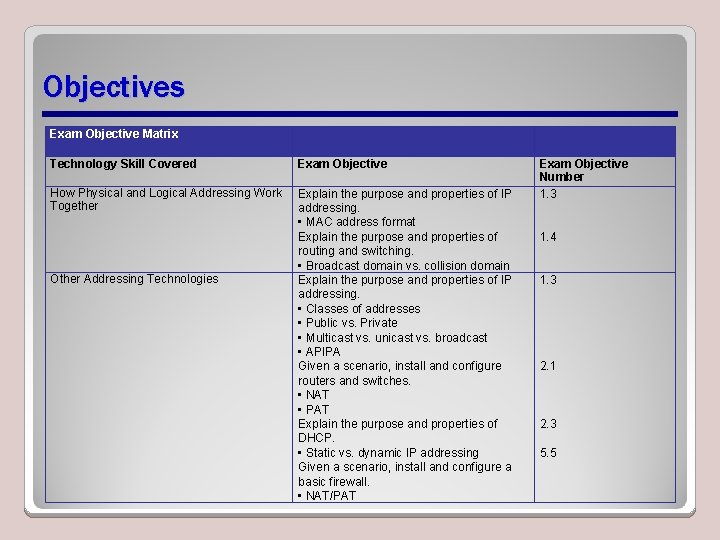
Objectives Exam Objective Matrix Technology Skill Covered Exam Objective How Physical and Logical Addressing Work Together Explain the purpose and properties of IP addressing. • MAC address format Explain the purpose and properties of routing and switching. • Broadcast domain vs. collision domain Explain the purpose and properties of IP addressing. • Classes of addresses • Public vs. Private • Multicast vs. unicast vs. broadcast • APIPA Given a scenario, install and configure routers and switches. • NAT • PAT Explain the purpose and properties of DHCP. • Static vs. dynamic IP addressing Given a scenario, install and configure a basic firewall. • NAT/PAT Other Addressing Technologies Exam Objective Number 1. 3 1. 4 1. 3 2. 1 2. 3 5. 5
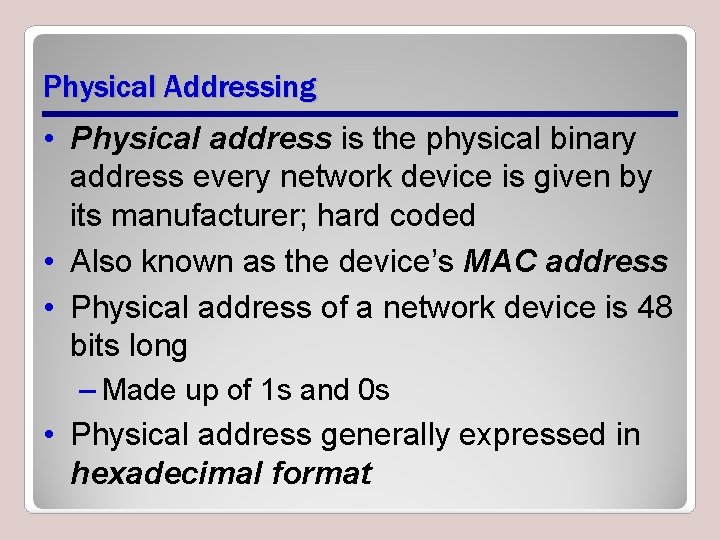
Physical Addressing • Physical address is the physical binary address every network device is given by its manufacturer; hard coded • Also known as the device’s MAC address • Physical address of a network device is 48 bits long – Made up of 1 s and 0 s • Physical address generally expressed in hexadecimal format
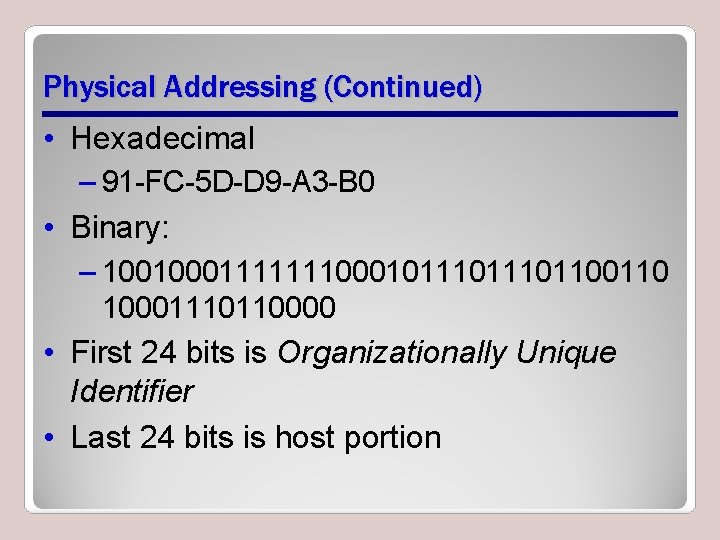
Physical Addressing (Continued) • Hexadecimal – 91 -FC-5 D-D 9 -A 3 -B 0 • Binary: – 10010001111111000101110110 10001110110000 • First 24 bits is Organizationally Unique Identifier • Last 24 bits is host portion
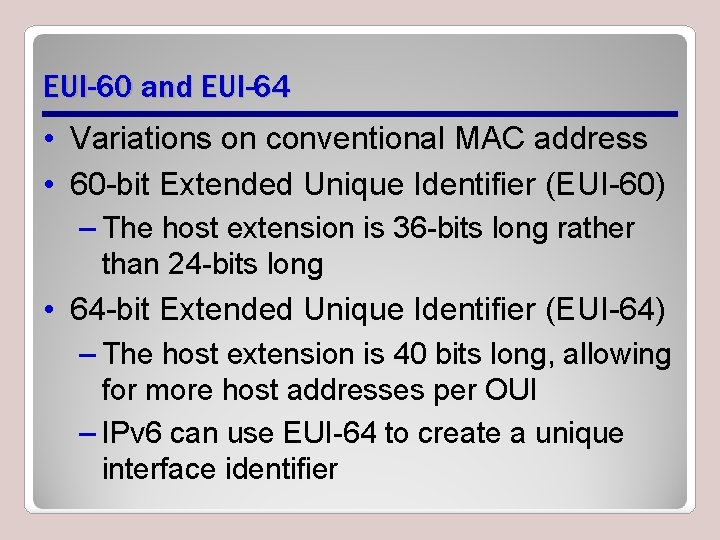
EUI-60 and EUI-64 • Variations on conventional MAC address • 60 -bit Extended Unique Identifier (EUI-60) – The host extension is 36 -bits long rather than 24 -bits long • 64 -bit Extended Unique Identifier (EUI-64) – The host extension is 40 bits long, allowing for more host addresses per OUI – IPv 6 can use EUI-64 to create a unique interface identifier

MAC Addressing • Refers to the function of the physical address, while the term “physical address” more often refers to the actual thing • A computer or network device uses the MAC address to move data frames from one computer or network device to an adjacent computer or network device • Hop: Each time a computer or network device hands off data frame to the next computer or network device down the line
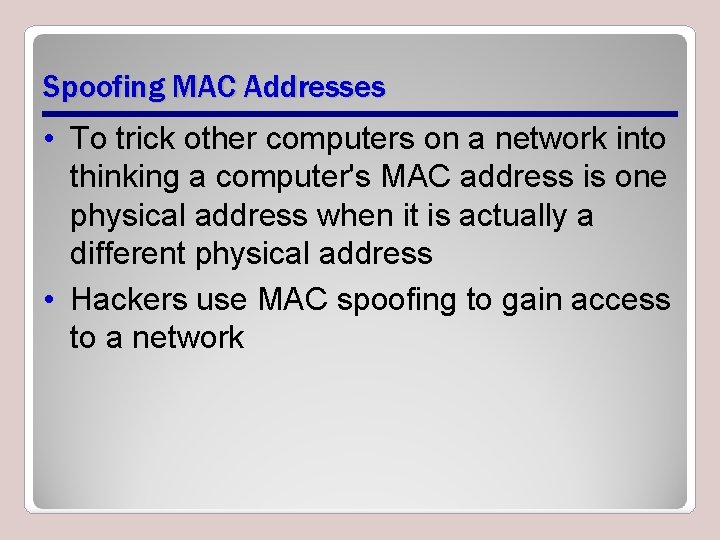
Spoofing MAC Addresses • To trick other computers on a network into thinking a computer's MAC address is one physical address when it is actually a different physical address • Hackers use MAC spoofing to gain access to a network

Logical Addressing • Every computer on a network needs a unique logical address • Used to ensure data packet follows best path to destination computer
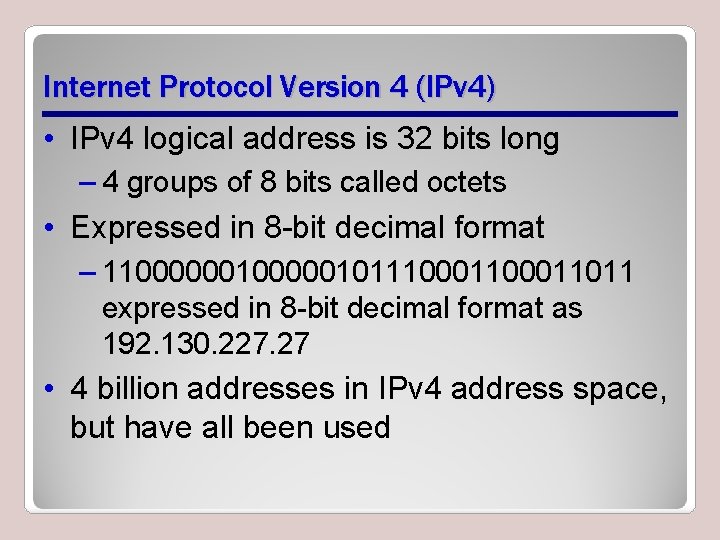
Internet Protocol Version 4 (IPv 4) • IPv 4 logical address is 32 bits long – 4 groups of 8 bits called octets • Expressed in 8 -bit decimal format – 110000001011100011011 expressed in 8 -bit decimal format as 192. 130. 227. 27 • 4 billion addresses in IPv 4 address space, but have all been used
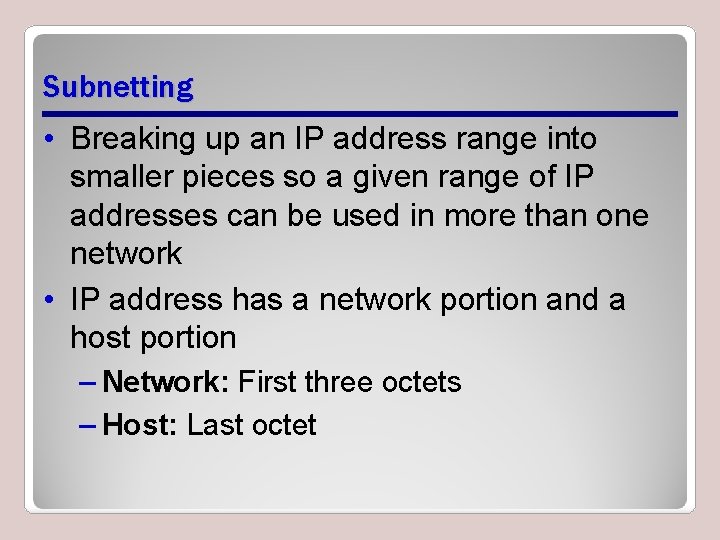
Subnetting • Breaking up an IP address range into smaller pieces so a given range of IP addresses can be used in more than one network • IP address has a network portion and a host portion – Network: First three octets – Host: Last octet
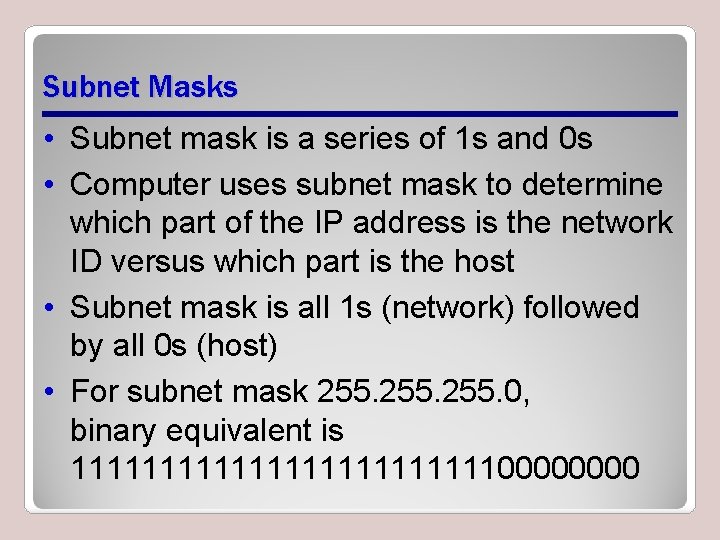
Subnet Masks • Subnet mask is a series of 1 s and 0 s • Computer uses subnet mask to determine which part of the IP address is the network ID versus which part is the host • Subnet mask is all 1 s (network) followed by all 0 s (host) • For subnet mask 255. 0, binary equivalent is 1111111111110000
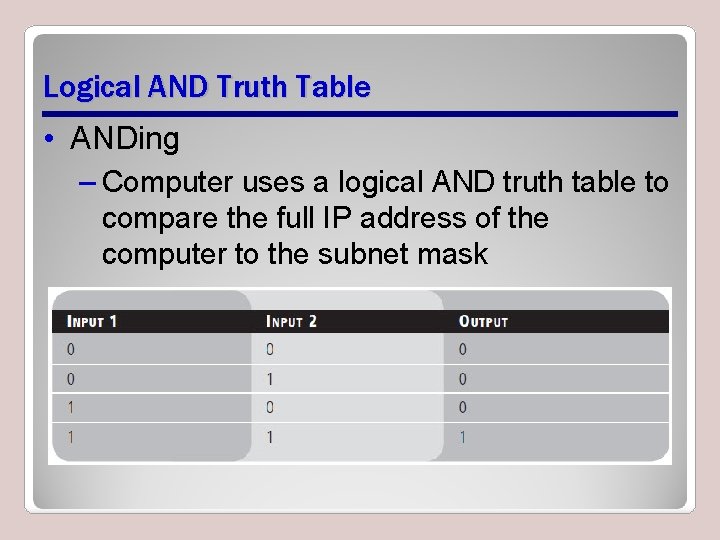
Logical AND Truth Table • ANDing – Computer uses a logical AND truth table to compare the full IP address of the computer to the subnet mask
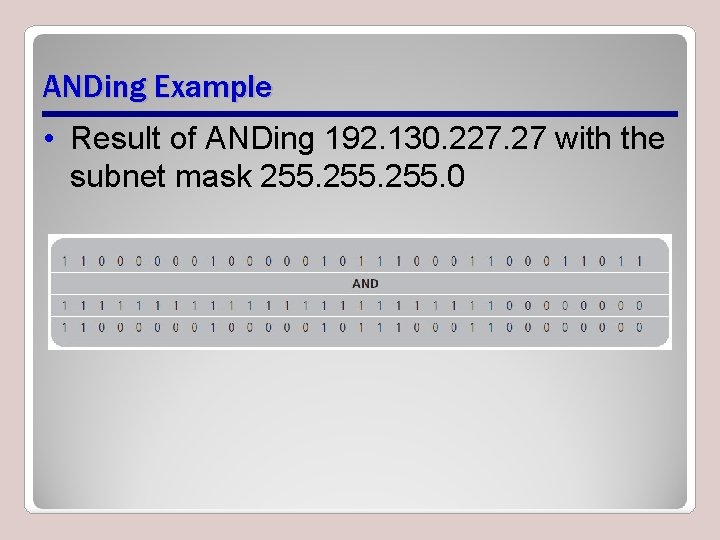
ANDing Example • Result of ANDing 192. 130. 227. 27 with the subnet mask 255. 0

Classful IP Addressing • Class A, B, C, D, and E • A, B, and C used by general population • Classful IP addressing – The classful method of determining what portion of an IP address is network ID and what portion of an IP address denotes hosts
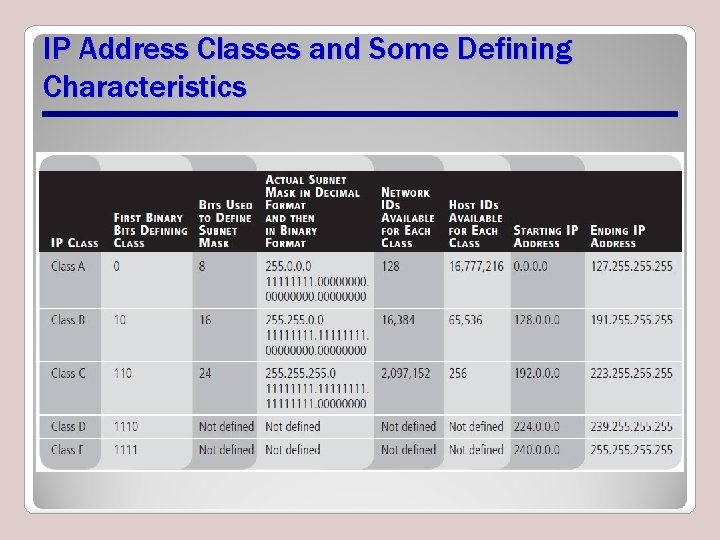
IP Address Classes and Some Defining Characteristics
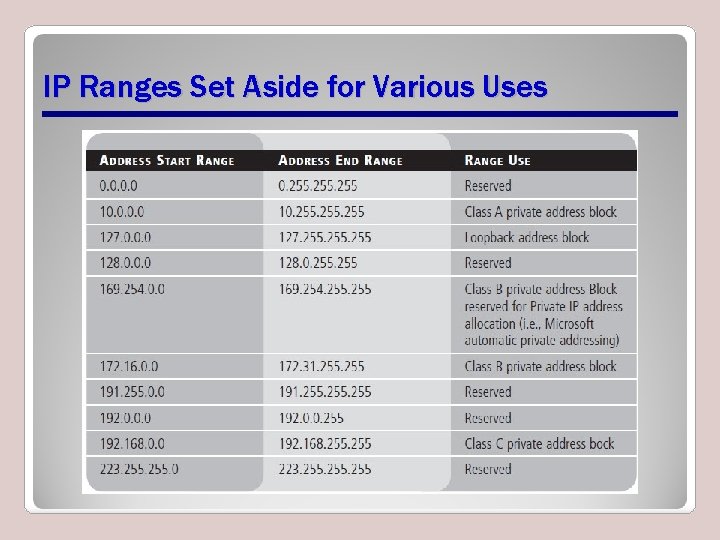
IP Ranges Set Aside for Various Uses
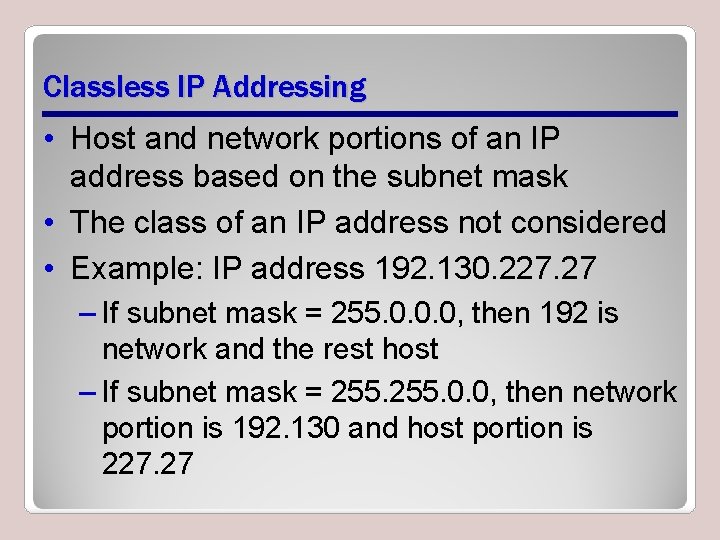
Classless IP Addressing • Host and network portions of an IP address based on the subnet mask • The class of an IP address not considered • Example: IP address 192. 130. 227. 27 – If subnet mask = 255. 0. 0. 0, then 192 is network and the rest host – If subnet mask = 255. 0. 0, then network portion is 192. 130 and host portion is 227. 27

Classless Inter-Domain Routing (CIDR) • Standard notation that indicates network ID and host ID of an IP address • Format is similar to 192. 130. 227. 27/n • /n indicates how many of the total 32 bits of the IP address’ binary form are to be used for the network IP portion – I. e. , tells what the subnet mask is • /n can be any number between 1 and 32, but 2 through 30 are used in practice
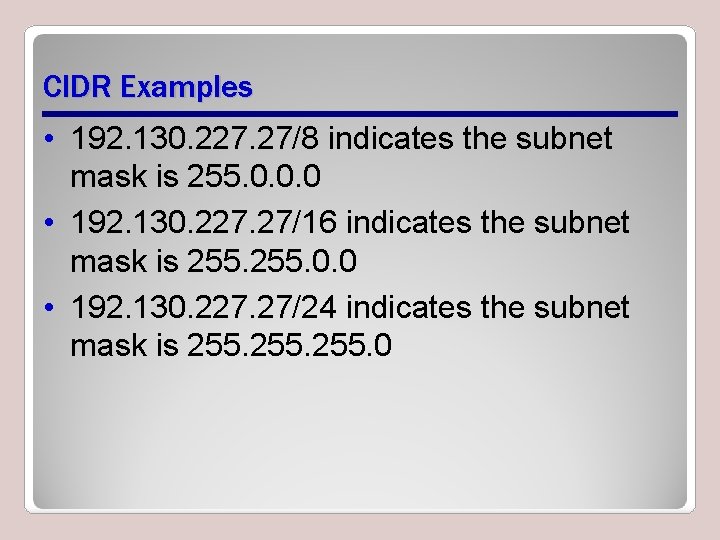
CIDR Examples • 192. 130. 227. 27/8 indicates the subnet mask is 255. 0. 0. 0 • 192. 130. 227. 27/16 indicates the subnet mask is 255. 0. 0 • 192. 130. 227. 27/24 indicates the subnet mask is 255. 0
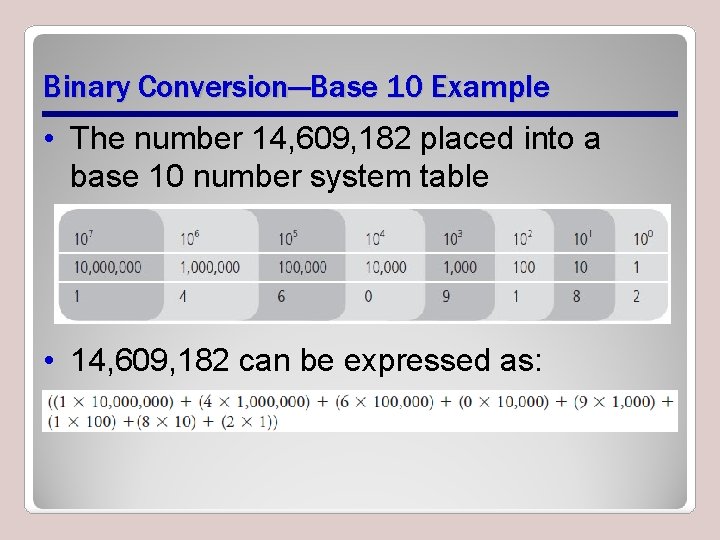
Binary Conversion—Base 10 Example • The number 14, 609, 182 placed into a base 10 number system table • 14, 609, 182 can be expressed as:
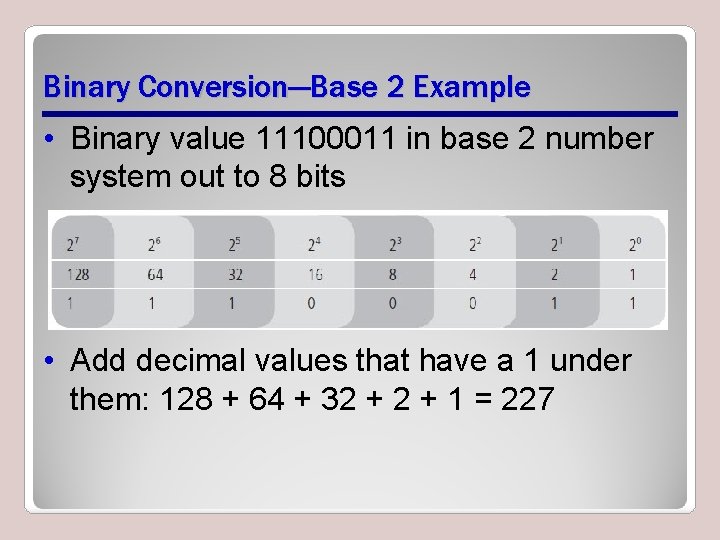
Binary Conversion—Base 2 Example • Binary value 11100011 in base 2 number system out to 8 bits • Add decimal values that have a 1 under them: 128 + 64 + 32 + 1 = 227
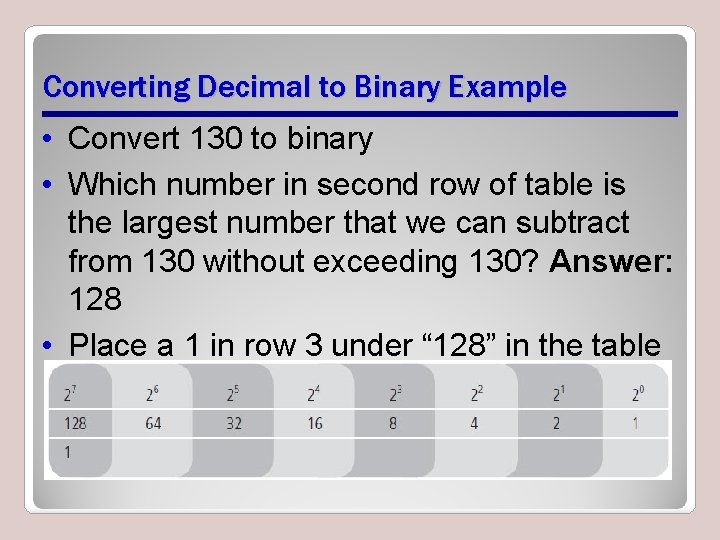
Converting Decimal to Binary Example • Convert 130 to binary • Which number in second row of table is the largest number that we can subtract from 130 without exceeding 130? Answer: 128 • Place a 1 in row 3 under “ 128” in the table
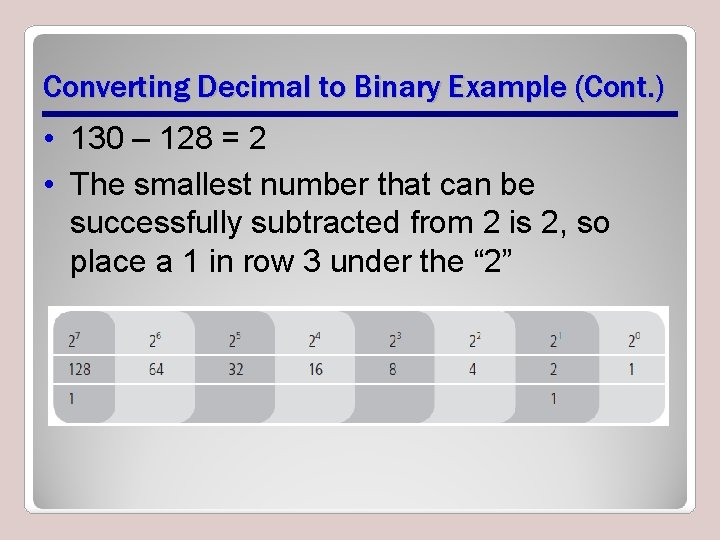
Converting Decimal to Binary Example (Cont. ) • 130 – 128 = 2 • The smallest number that can be successfully subtracted from 2 is 2, so place a 1 in row 3 under the “ 2”
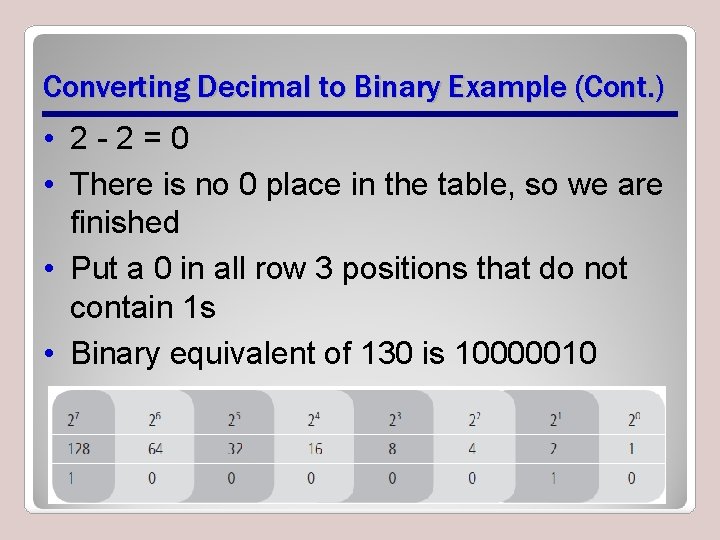
Converting Decimal to Binary Example (Cont. ) • 2 -2=0 • There is no 0 place in the table, so we are finished • Put a 0 in all row 3 positions that do not contain 1 s • Binary equivalent of 130 is 10000010

Determine Subnet Mask Using CIDR • Example: CIDR notation is 192. 130. 227. 27/12 • Use the value 8 to determine the subnet mask in each octet • 12 – 8 = 4 • First octet has eight 1 s, second octet uses the remaining four 1 s • An octet with eight 1 s is 255, so first octet of the subnet mask is 255
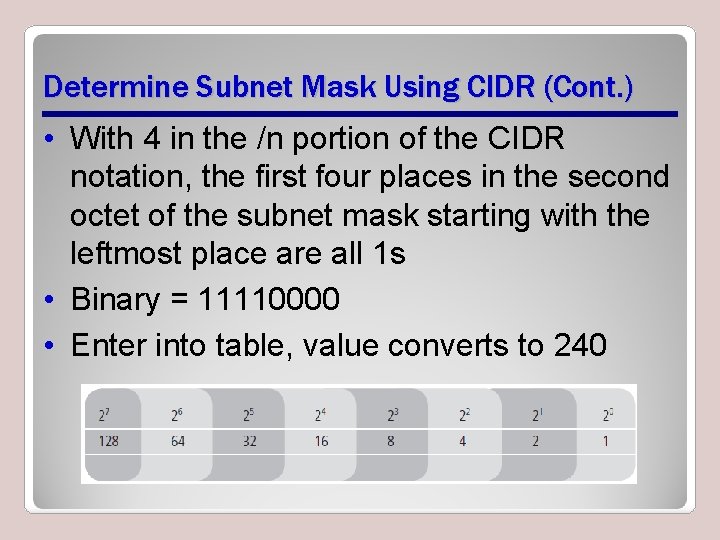
Determine Subnet Mask Using CIDR (Cont. ) • With 4 in the /n portion of the CIDR notation, the first four places in the second octet of the subnet mask starting with the leftmost place are all 1 s • Binary = 11110000 • Enter into table, value converts to 240

Determine Subnet Mask Using CIDR (Cont. ) • The value 240 should be in the second octet of the subnet mask • Since 4 is smaller than 8, there are no 1 s in the last two octets and so they will equal 0 • The subnet mask that results from the CIDR notation 192. 130. 227. 27/12 is therefore 255. 240. 0. 0
Determine Sub-network Ranges Using CIDR • CIDR notation can determine sub-network ranges • Sub-network is where a specific network IP address is divided into smaller networks to make more efficient use of the available IP addresses
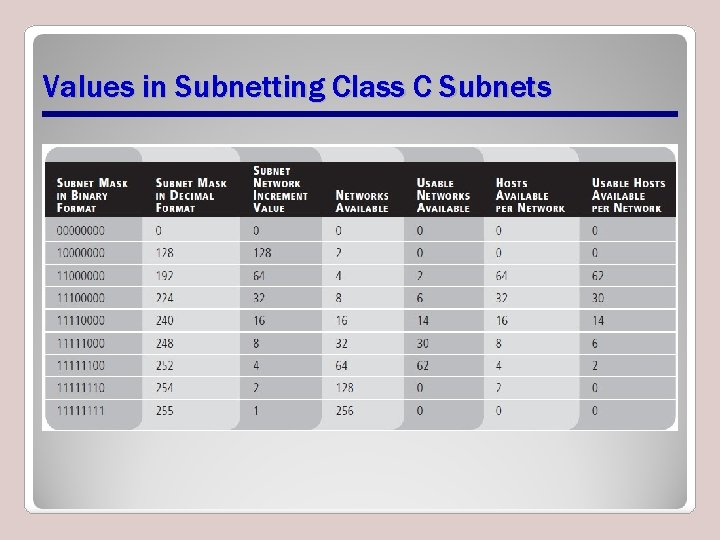
Values in Subnetting Class C Subnets
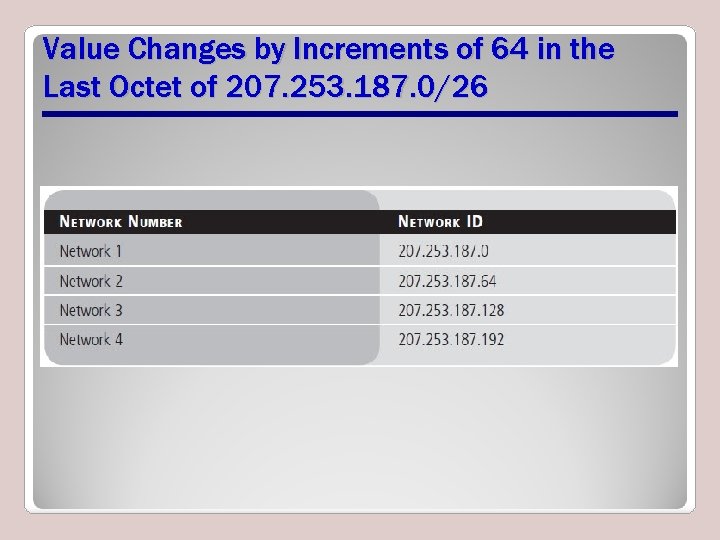
Value Changes by Increments of 64 in the Last Octet of 207. 253. 187. 0/26
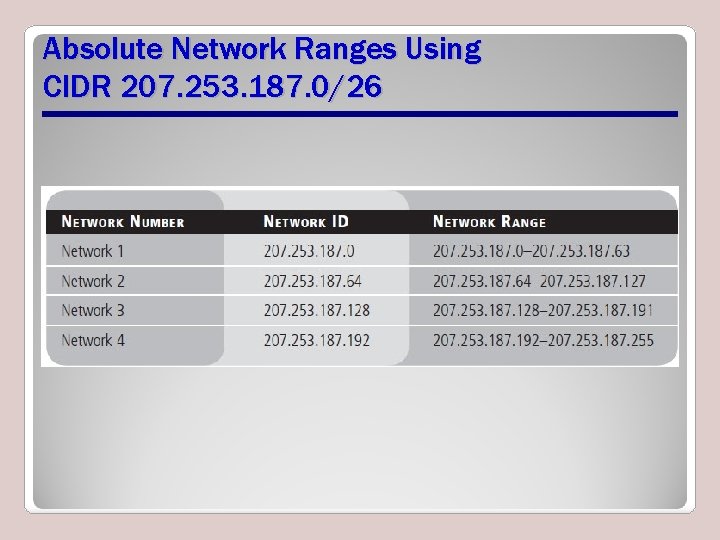
Absolute Network Ranges Using CIDR 207. 253. 187. 0/26
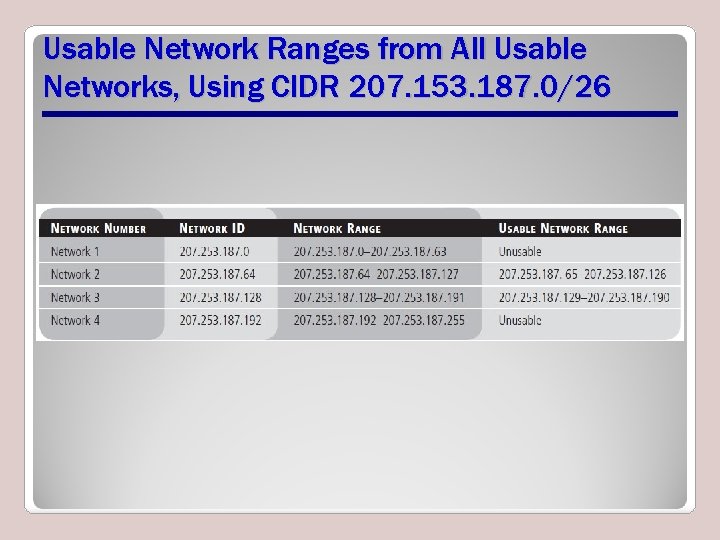
Usable Network Ranges from All Usable Networks, Using CIDR 207. 153. 187. 0/26
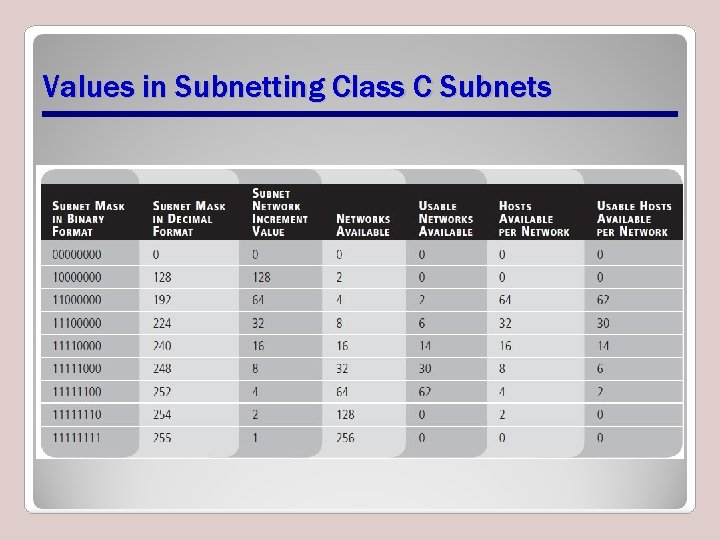
Values in Subnetting Class C Subnets
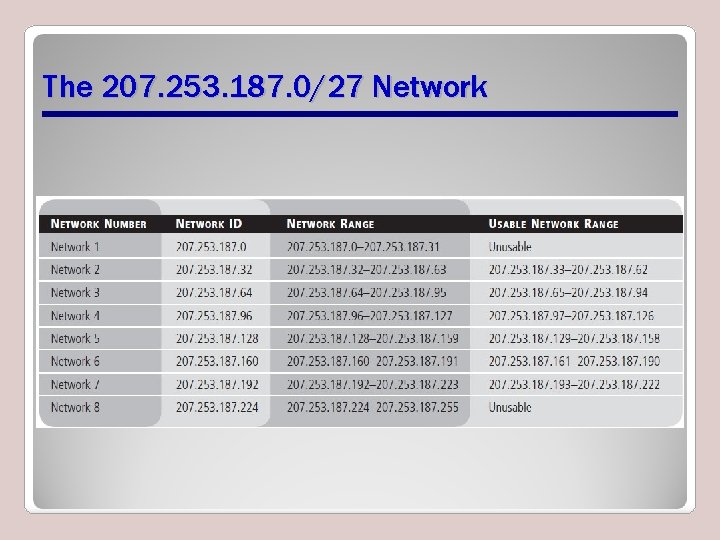
The 207. 253. 187. 0/27 Network

Internet Protocol Version 6 (IPv 6) • Uses 128 -bit IP addresses – Addresses expressed in hexadecimal numbers – 32 numbers and letters, 0– 9 and A–F – First 16 hexadecimal digits are network ID, last 16 hexadecimal digits are host ID – Example: 13 D 4: FA 97: 0000: 1258: AD 8 B: 1009: 34 D 6: 1 800 – No subnetting needed
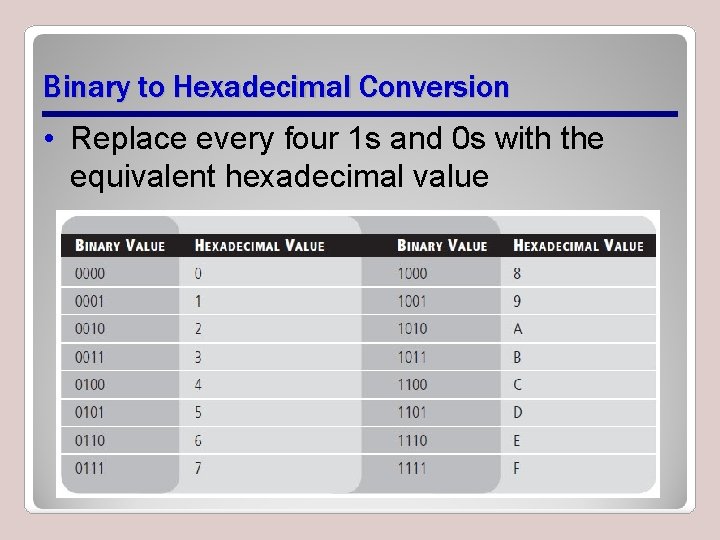
Binary to Hexadecimal Conversion • Replace every four 1 s and 0 s with the equivalent hexadecimal value

IPv 6 Address Double Colon Technique • Not all 16 -bit groups in IPv 6 address need to be shown • If IPv 6 address has a group of 16 bits equal to all 0 s, that 16 -bit section can be skipped 13 D 4: 0000: 1009: 34 D 6: 1800 can be written as 13 D 4: : 1009: 34 D 6: 1800
EUI-64 • Host can automatically assign itself a unique 64 -bit interface identifier • Two steps: 1. Divide MAC address between the Organizationally Unique Identifier (OUI) and the host portion of the MAC address – Add hexadecimal value FFFE between two portions of the MAC address
EUI-64 (Continued) 2. Invert 7 th bit of MAC address so it is opposite of what it was previously – This bit is called the universal/local flag – Normally set to 0; to invert, change to 1 • Result is a Modified EUI-64 address • Can be used by IPv 6 as a unique interface identifier on a device connected to a network

How Physical and Logical Addressing Work Together • This portion of lesson shows how logical addresses and physical addresses work together to ensure that data finds destination across a large network • For illustration purposes, assume represented network uses Ethernet for both its LAN and WAN portions
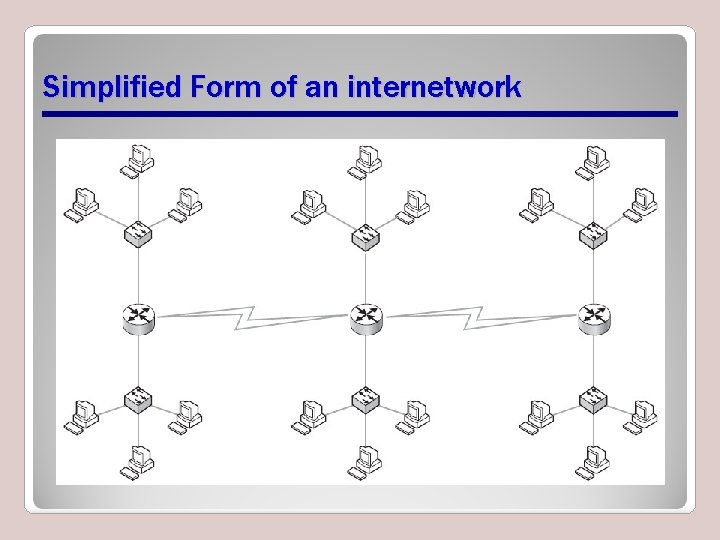
Simplified Form of an internetwork
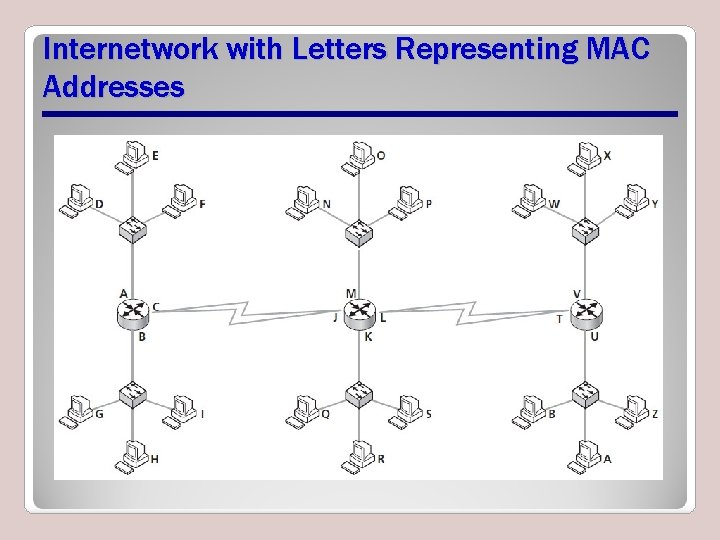
Internetwork with Letters Representing MAC Addresses
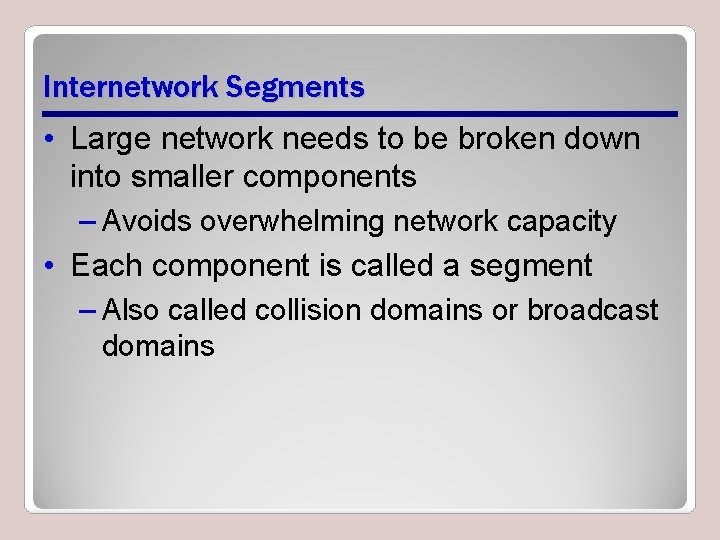
Internetwork Segments • Large network needs to be broken down into smaller components – Avoids overwhelming network capacity • Each component is called a segment – Also called collision domains or broadcast domains
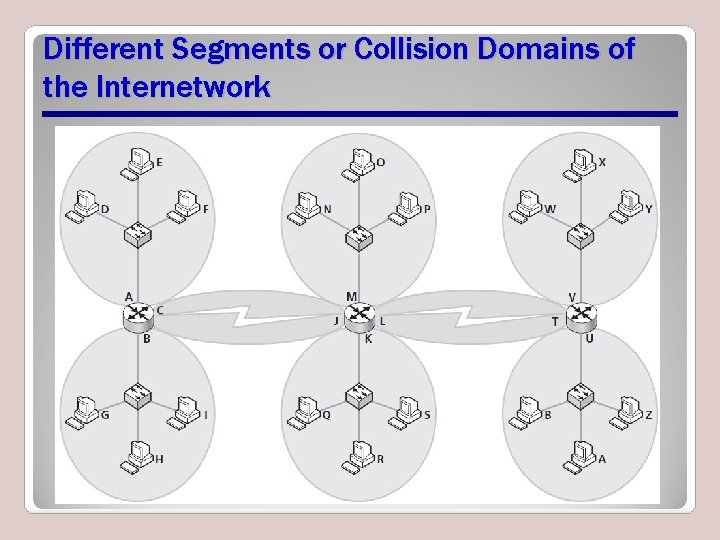
Different Segments or Collision Domains of the Internetwork
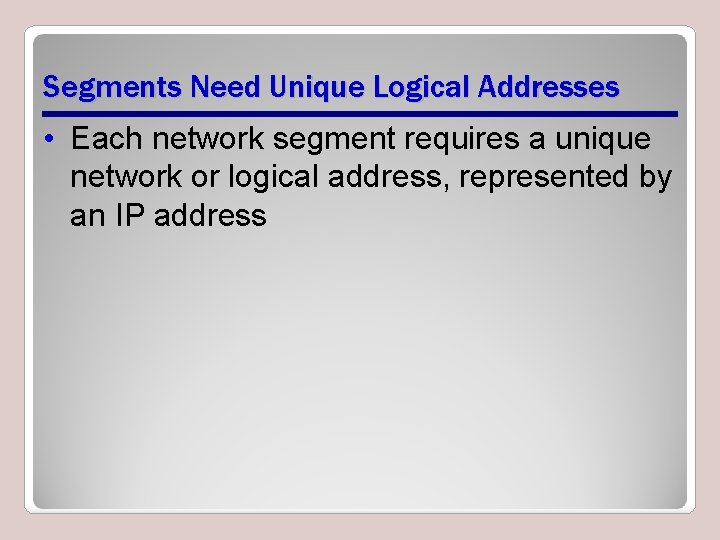
Segments Need Unique Logical Addresses • Each network segment requires a unique network or logical address, represented by an IP address
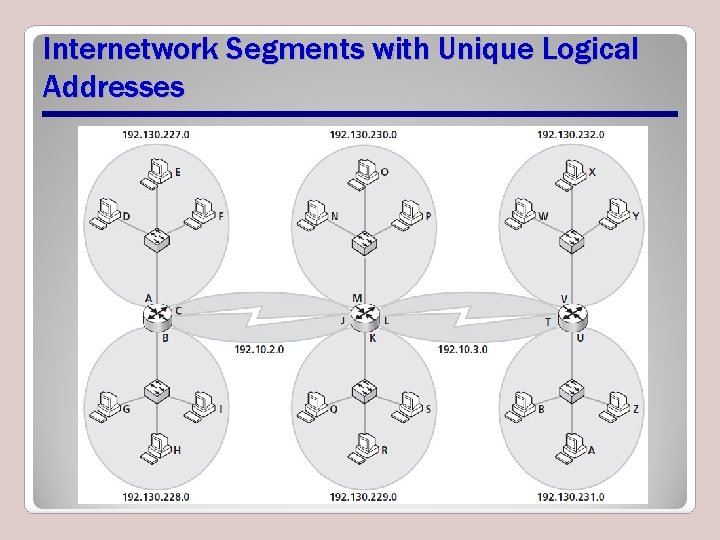
Internetwork Segments with Unique Logical Addresses

Devices Need Unique Logical Addresses • Each network interface within each segment also requires a unique network or logical address • Network address for each device within a segment must contain the network address of the entire segment as well as a unique identifier for each interface
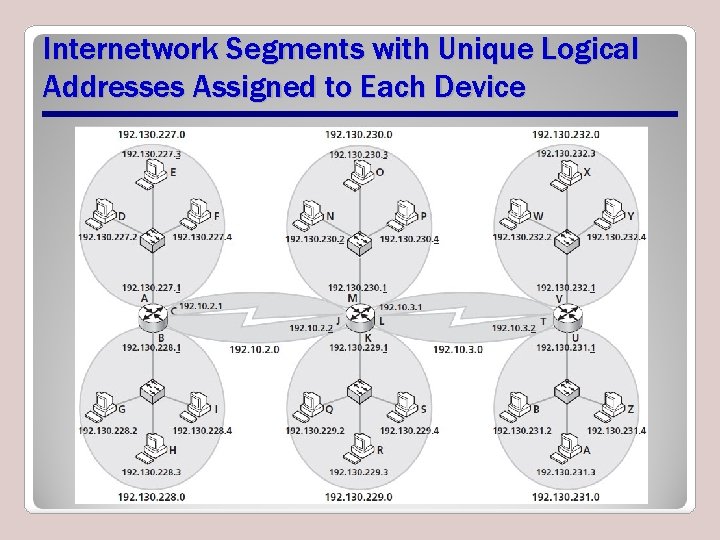
Internetwork Segments with Unique Logical Addresses Assigned to Each Device
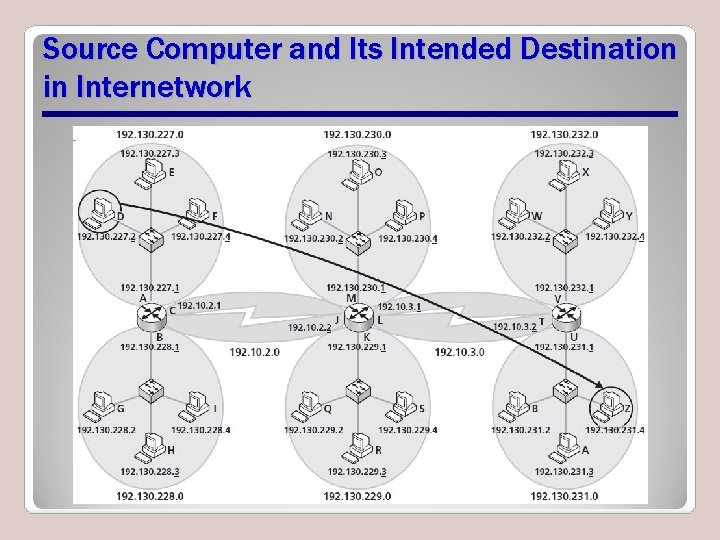
Source Computer and Its Intended Destination in Internetwork
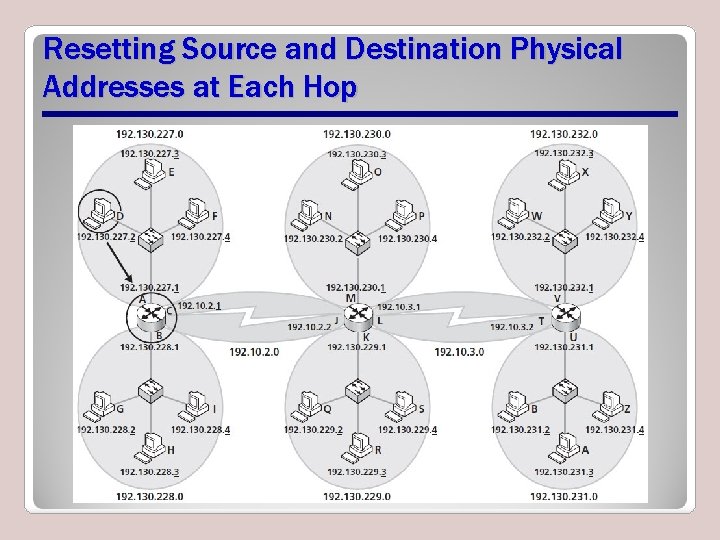
Resetting Source and Destination Physical Addresses at Each Hop
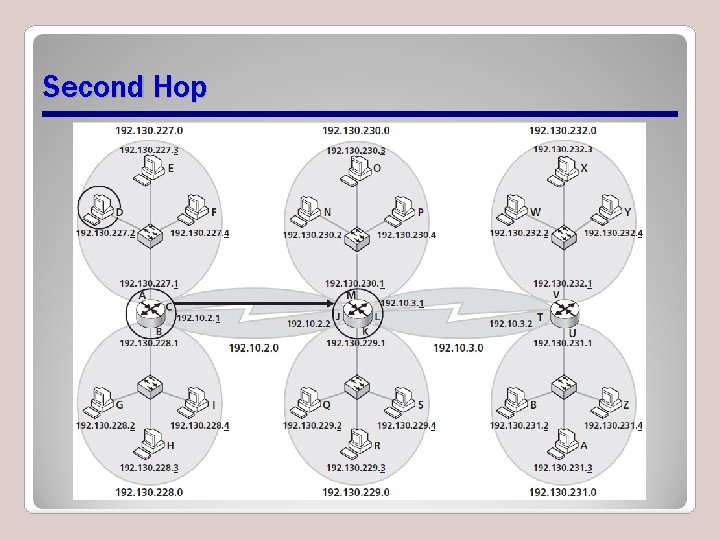
Second Hop
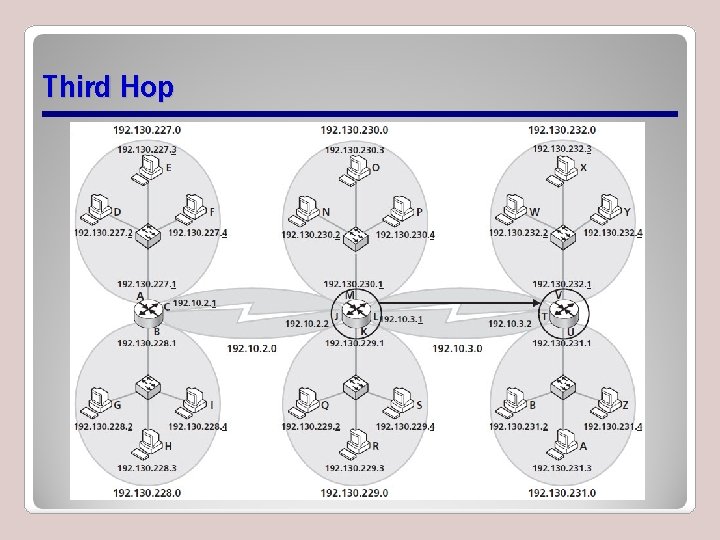
Third Hop
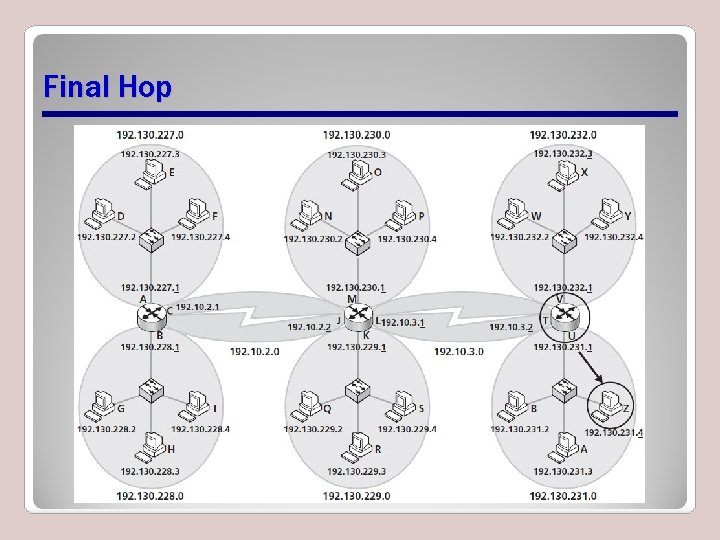
Final Hop
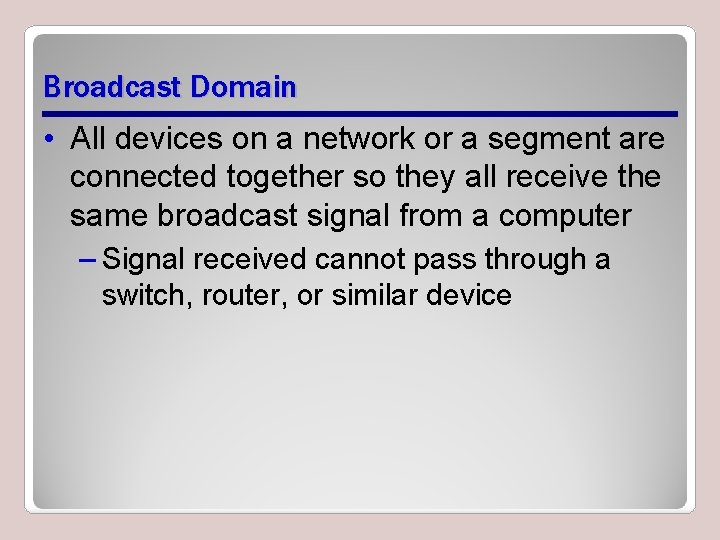
Broadcast Domain • All devices on a network or a segment are connected together so they all receive the same broadcast signal from a computer – Signal received cannot pass through a switch, router, or similar device
Collision Domain • Two or more devices on the same segment or network are able to cause their signal to interfere with the signal from another device on the same segment or network
Other Addressing Technologies • • Supernetting Network Address Translation (NAT) Assigning IP addresses Addressing schemes
Supernetting • The process of combining several IP ranges, usually Class C ranges, into one larger network • Example – Two IP address ranges: 204. 214. 56. 0 and 204. 214. 57. 0 – Combine (supernet) them into one aggregate range of IP addresses • Use the CIDR notation of 204. 214. 56. 0/23
Network Address Translation (NAT) • Take an IP address from an ISP or other location and use that one IP address to allow all Internet-enable devices to which it is connected to access the Internet
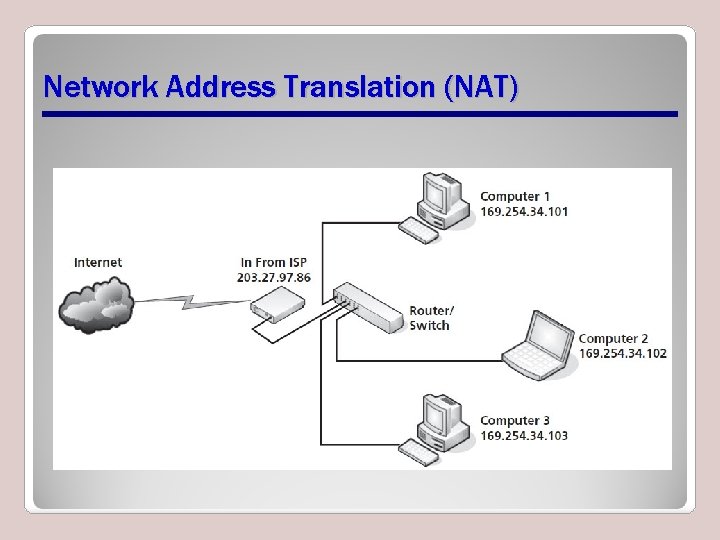
Network Address Translation (NAT)
Types of NAT • Source Network Address Translation (SNAT) • Port Address Translation (PAT)
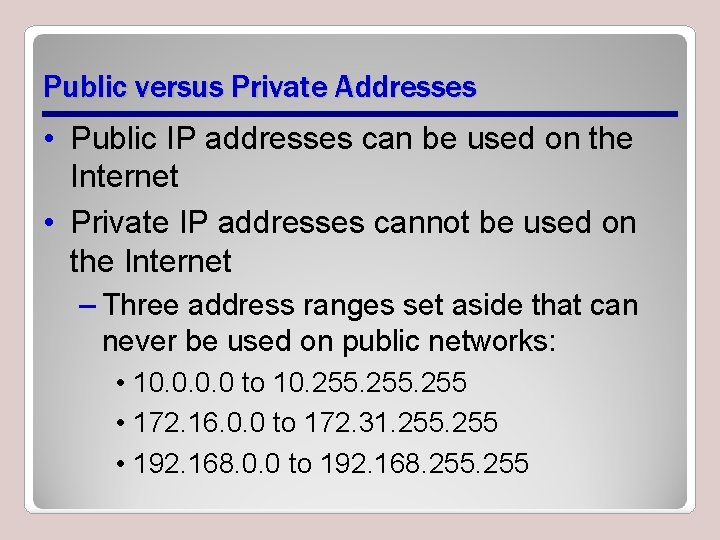
Public versus Private Addresses • Public IP addresses can be used on the Internet • Private IP addresses cannot be used on the Internet – Three address ranges set aside that can never be used on public networks: • 10. 0 to 10. 255 • 172. 16. 0. 0 to 172. 31. 255 • 192. 168. 0. 0 to 192. 168. 255
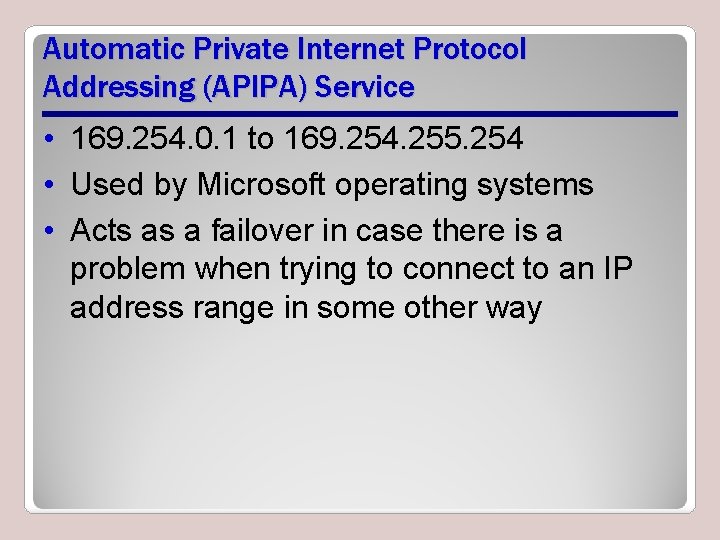
Automatic Private Internet Protocol Addressing (APIPA) Service • 169. 254. 0. 1 to 169. 254. 255. 254 • Used by Microsoft operating systems • Acts as a failover in case there is a problem when trying to connect to an IP address range in some other way
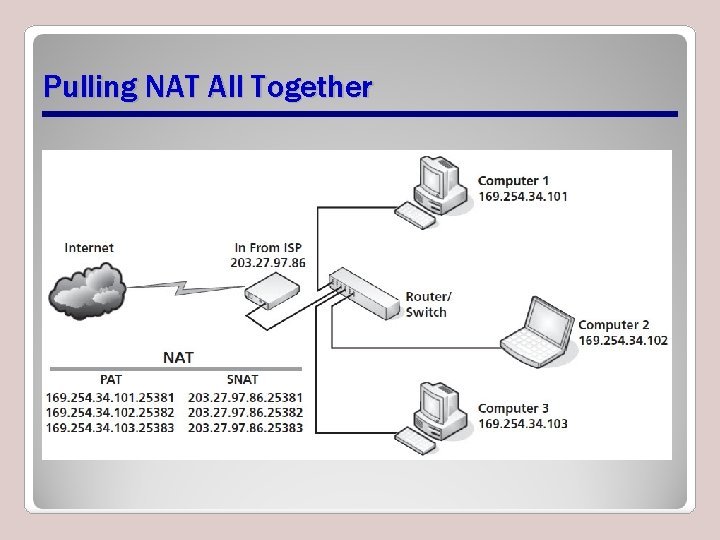
Pulling NAT All Together
Assigning IP Addresses • Static – IP addresses assigned to computers manually by the network administrator • Dynamic – Dynamic Host Configuration Protocol (DHCP) – Assigns IP addresses dynamically without requiring constant input from network administrator
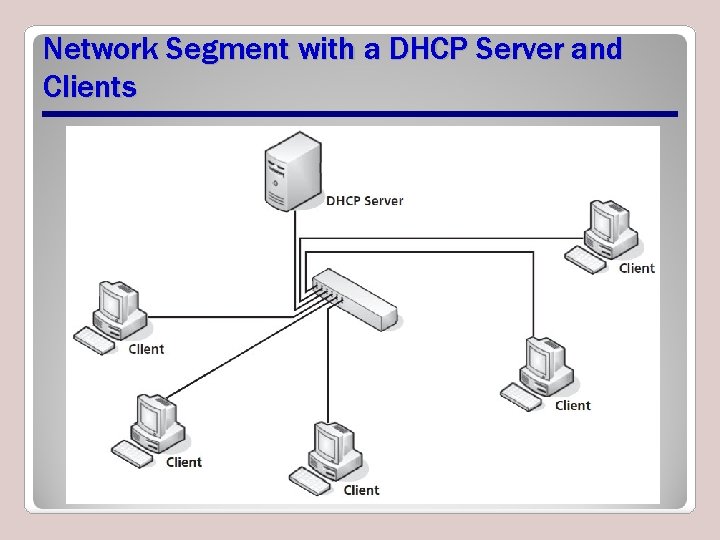
Network Segment with a DHCP Server and Clients
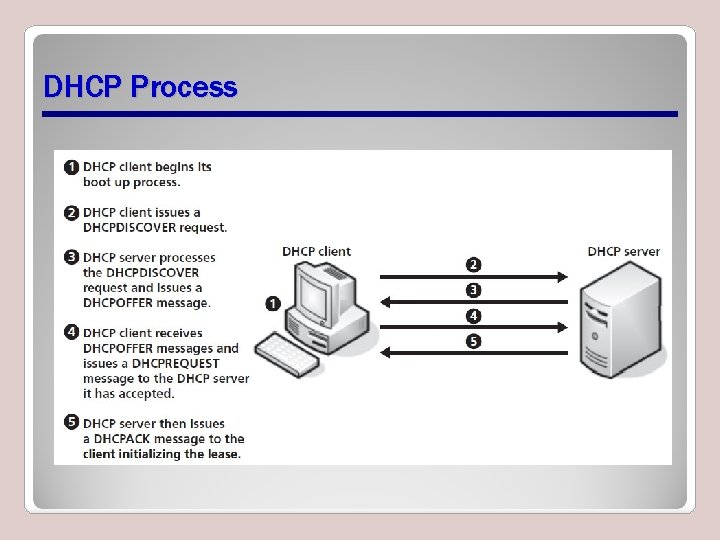
DHCP Process
Addressing Schemes Unicast Broadcast Multicast

Summary • A physical address is the physical binary address every network device is given by its manufacturer; it is hard coded. • The physical address of a network device is 48 bits long and is made up of 1 s and 0 s. • Every computer on a network needs a unique logical address. • Subnetting breaks up an IP address range into smaller pieces so a given range of IP addresses can be used in more than one network.
Summary (Continued) • Classful IP addressing is the classful method of determining what portion of an IP address is the network ID and what portion denotes hosts. • Classless Inter-Domain Routing (CIDR) is standard notation that indicates the network ID and host ID of an IP address. • IPv 6 uses 128 -bit IP addresses. Addresses are expressed in hexadecimal numbers, 32 numbers and letters, 0– 9 and A–F. • The first 16 hexadecimal digits of an IPv 6 address are the network ID, the last 16 digits the host ID.
Summary (Continued) • In a broadcast domain, all devices on a network or a segment are connected together so they all receive the same broadcast signal from a computer. • In a collision domain, two or more devices on the same segment or network are able to cause their signal to interfere with the signal from another device on the same segment or network. • Supernetting is the process of combining several IP ranges, usually Class C ranges, into one larger network.
Summary (Continued) • Network Address Translation (NAT) takes an IP address from an ISP or other location and uses that one IP address to allow all Internet-enable devices to which it is connected to access the Internet. • Static IP addresses are assigned manually. • Dynamic IP addresses are assigned automatically using Dynamic Host Configuration Protocol (DHCP).
- Slides: 72