Network Access Controlled Are You Exposed Threat Protection











- Slides: 19

Network Access. Controlled. ™ Are You Exposed? Threat Protection with Counter. ACT Len Rosenberg Security Engineer

Identify, Prove and Stop Who’s Connecting to Your Network Right Now ? Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

Identify, Prove and Stop Threats Before they Impact Network § Focus On The Source Of The Threat Stop Source Stop Attack Stop potential Damage • Hackers • Worm Propagating Sources § Control to Ensure Appropriate Access In real-time Identifies Ownership of Device Measures Compliance Enforces Policies Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

Counter. ACT – Hacker/Worm The Revolutionary Key Hackers and Worms have no knowledge of LAN/Network resources. They have to aggressively perform reconnaissance to look for LAN/Network vulnerabilities to exploit. Proof Point 400+ Customers Trust to put into Auto-Block Mode Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

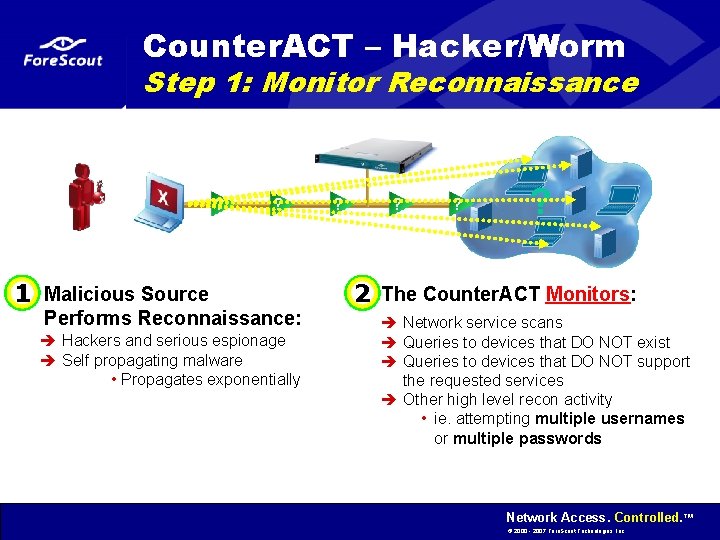
Counter. ACT – Hacker/Worm Step 1: Monitor Reconnaissance ? 1 Malicious Source Performs Reconnaissance: è Hackers and serious espionage è Self propagating malware • Propagates exponentially 2 The Counter. ACT Monitors: è Network service scans è Queries to devices that DO NOT exist è Queries to devices that DO NOT support the requested services è Other high level recon activity • ie. attempting multiple usernames or multiple passwords Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

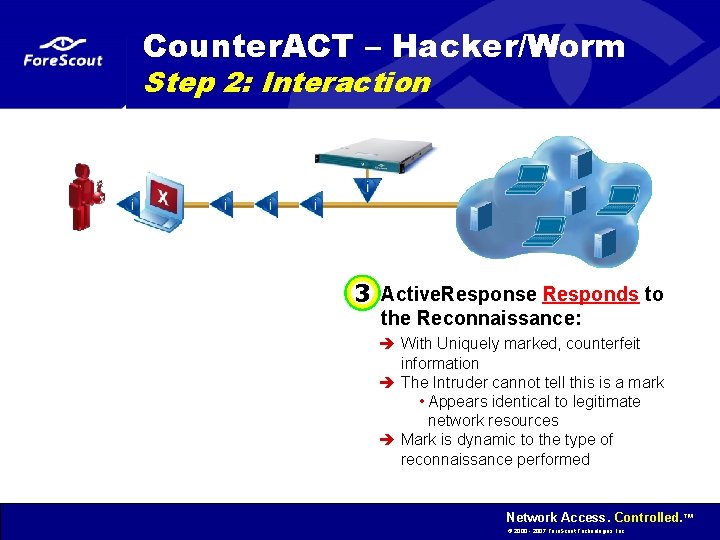
Counter. ACT – Hacker/Worm Step 2: Interaction 3 Active. Response Responds to the Reconnaissance: è With Uniquely marked, counterfeit information è The Intruder cannot tell this is a mark • Appears identical to legitimate network resources è Mark is dynamic to the type of reconnaissance performed Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

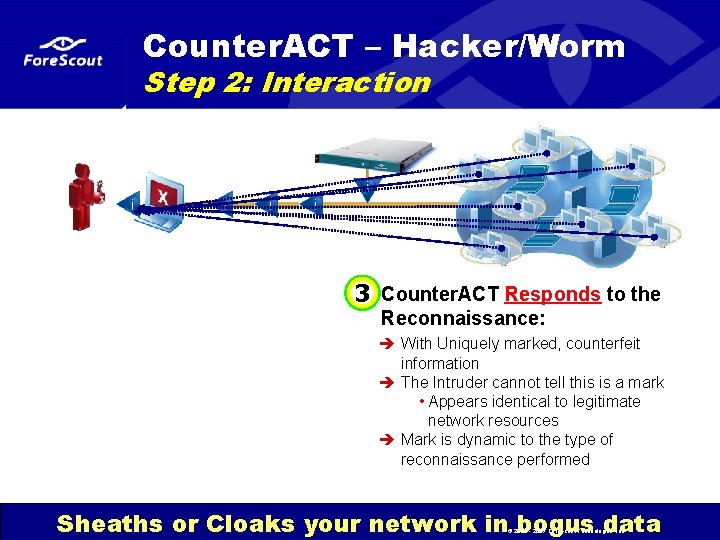
Counter. ACT – Hacker/Worm Step 2: Interaction 3 Counter. ACT Responds to the Reconnaissance: è With Uniquely marked, counterfeit information è The Intruder cannot tell this is a mark • Appears identical to legitimate network resources è Mark is dynamic to the type of reconnaissance performed Access. Controlled. ™ Sheaths or Cloaks your network in. Network bogus data © 2000 - 2007 Fore. Scout Technologies, Inc.

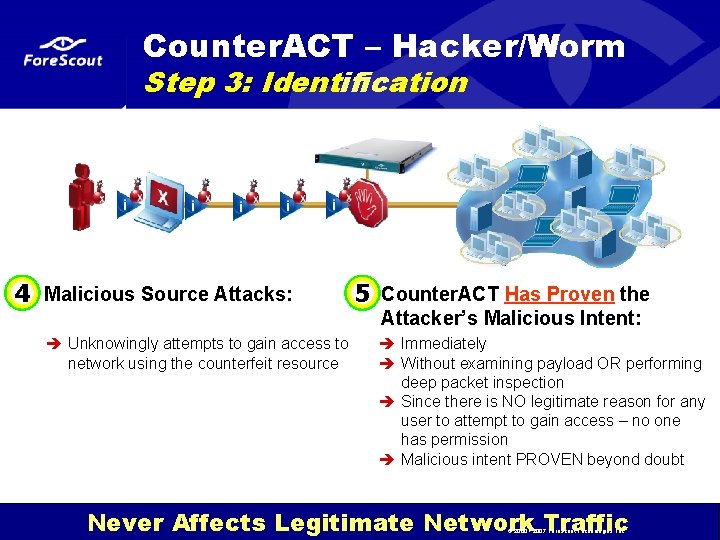
Counter. ACT – Hacker/Worm Step 3: Identification 4 Malicious Source Attacks: è Unknowingly attempts to gain access to network using the counterfeit resource 5 Counter. ACT Has Proven the Attacker’s Malicious Intent: è Immediately è Without examining payload OR performing deep packet inspection è Since there is NO legitimate reason for any user to attempt to gain access – no one has permission è Malicious intent PROVEN beyond doubt Network Access. Controlled. ™ Never Affects Legitimate Network Traffic © 2000 - 2007 Fore. Scout Technologies, Inc.

Counter. ACT – Hacker/Worm Protection NOT Disruption IF: Zero-day Attack unfolding - Accuracy of IPS allows for automatic action - Disruptive to attacker Non disruptive to network staff IF: Unknown Device/Person is infected - Completely block users access - Disruptive to user Non disruptive to your network IF: Known Device/Person in infected - Only surgically block infected ports Non disruptive to other activities Controlled. ™ In Production Networks For Over Network Four. Access. Years © 2000 - 2007 Fore. Scout Technologies, Inc.

Counter. ACT Network Access Control Universal Discovery Detects Every Device Determining if device is company owned or guest or contractor Without need for prior knowledge of device Interrogates All Devices End Point X-Ray For degree of security policy compliance Enforces real-time protection from self-propagating threats No quarantine by default requirement Enforcement Tailored To Violation Tailored Enforcement Level of restriction matched to the exact degree of policy violation Avoiding needless interruption of user productivity Deploy & Enforce Without Disruptions Non Disruptive No disruption to the network, IT staff and compliant users Automatically guiding non-compliant users into compliance Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

Universal Discovery Enforce Policy on ALL Devices Clientless Since No Software/Code Required on Endpoints • All Devices Detected Upon Network Connection • Guests, Contractors, Printers, Vo. IP Devices, etc • Applies to Local and Global Domain Users Universal Discovery Counter. ACT Works with Existing Domain • Treats Domain or Non-Domain Users Differently in Accordance with Defined Policies “Clientless solutions are typically the easiest to deploy, achieve broad protection and enforcement, and are the most scalable. ” Jeff Wilson, Principle Security Analyst Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

Universal Discovery Manages Guest/Student Access Counter. ACT Instantly Determines Whether the Device is Managed or a Guest/Student Depending on Policy in Place… Universal Discovery ¶ Automatically Assign to a Guest/Visitor VLAN with Internet Access ¶ Prompt Visitor for Login to the Device to Conduct an In-Depth Interrogation ¶ Limit or Block Access Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

Tailored Enforcement Custom Fit To Your Business Needs Full Spectrum of Policy Enforcement Options • Degree of Disruption Directly Related to Degree of Violation • Maximum User Disruption is Reserved Only for Critical Violations Customized Policy Enforcement with Counter. ACT • Business Dictates Level of Enforcement of Policy Violations • Different Enforcement for Domain Users, Contractors and Guests Tailored Enforcement Not Binary • Provides Multiple Limited Disruption Enforcement Options • End User Can Remain Productive While Minor Policy Violations are Addressed Open Trouble Ticket Send Email Deploy a Virtual Firewall around an infected or non-compliant device Turn off physical switch port Terminate unauthorized applications HTTP Browser Hijack Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

Non Disruptive Deploy NAC without Disruption Non-Disruptive Deployment • Not-Inline Deployment • Ability to Deploy in/through Multiple Modes – Audit, Inform, Educate, Enforce Non-Disruptive Management Non Disruptive • NAC System Does Not Require Continual Monitoring • Simple Format for Updating/Changing Policies • HTTP Interrupt Automatically Informs User of Out-of-Policy Situations and Process to Self-Remediate and Return to Compliance without IT Intervention • High Availability ensures NAC policies are always enforced Non-Disruptive Access • Allows Contractors/Guests Access According to Policy Without Physical Adjustment to Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

Counter. ACT Non Disruptive Deployment Steps To Achieving NAC Deployment Without Network Disruption Know Your Network - Level of Current Policy Compliance - Quality of Created Policy Inform All Connecting Devices of New Policy - Hijack Browser Session Upon Every New Connection - Force verification login from notification dialogue box Engage Non Compliant End User Personally - With Net. Send or Browser Hijack Notify End User of Specific Policy Violation, Using Their Name Flexible Automatic Enforcement - Notify/Remediate/Limit Network Access/Quarantine/Deny Access Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

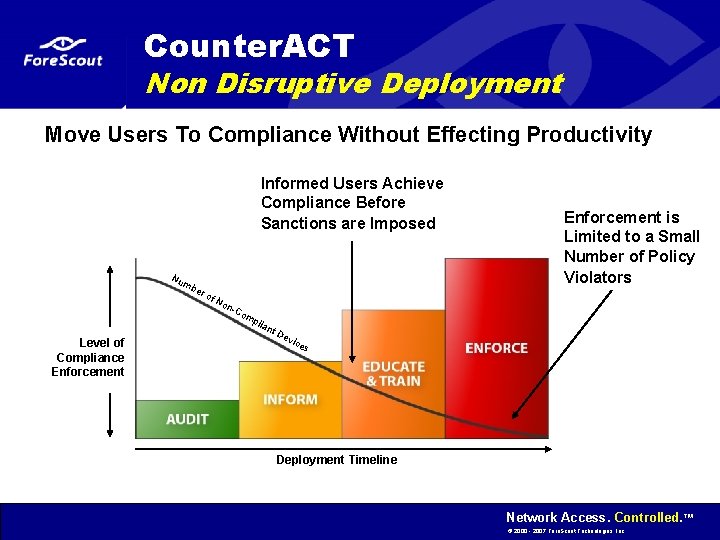
Counter. ACT Non Disruptive Deployment Move Users To Compliance Without Effecting Productivity Informed Users Achieve Compliance Before Sanctions are Imposed Nu mb er of No n -Co Level of Compliance Enforcement mp lian t. D Enforcement is Limited to a Small Number of Policy Violators evi ces Deployment Timeline Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

Network Access Control Analyst Recommendations “… All NAC projects should include the ability to establish baseline endpoints for malware and to quarantine infected devices before they gain network access. ” Lawrence Orans, Research Director “For mass-market broad deployment there is more than enough functionality in clientless solutions to create granular access policies that meet or exceed security and Jeff Wilson, Principle Security Analyst compliance requirements. ” "NAC is too important a process to wait another two years , and many enterprises have heterogeneous environments anyway. If you are unable to implement infrastructure-based NAC by year-end 2007, begin now with either endpoint software-based or appliance-based NAC solutions, but develop a strategy for integrating these solutions with infrastructure-based NAC. " John Pescatore VP Distinguished Analyst Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

Fore. Scout’s Counter. ACT Controlling Access Instantly Identifies Self-Propagating Threats • Without disrupting legitimate network traffic • Without requiring signatures • Unmatched Accuracy – Trusted by over 400 customers in auto-block mode Provides Network Access Policy Enforcement • Ensures all connecting devices are compliant with network security policies • End users do not have to be affected by NAC deployment (unless non-compliant) • Can easily determine access rights based upon domain membership Deploy Immediately w/o Fear of Network Disruption • Non-inline architecture for straight forward integration with existing infrastructure • Monitor and education modes provide simple way to bring users into compliance to reach degree of compliance desired before enforcement is turned on Counter. ACT is NAC at Work • NAC that is customer driven, global deployment proven • Cuts through confusion to provide a real “working” NAC solution Network Access. Controlled. ™ © 2000 - 2007 Fore. Scout Technologies, Inc.

Network Access. Controlled. ™