Network Access Control MSIT 458 The Chinchillas Agenda














- Slides: 25

Network Access Control MSIT 458 – The Chinchillas

Agenda • • • Introduction of Problem Pros and Cons of Existing Security Systems Possible Solutions Recommended Solution Implementation Final Recommendation 2

Introduction of Problem 3

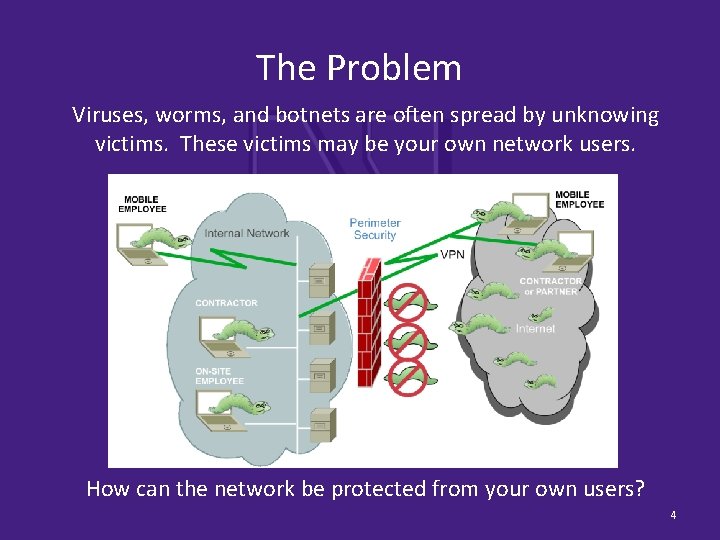
The Problem Viruses, worms, and botnets are often spread by unknowing victims. These victims may be your own network users. How can the network be protected from your own users? 4

The Problem 5

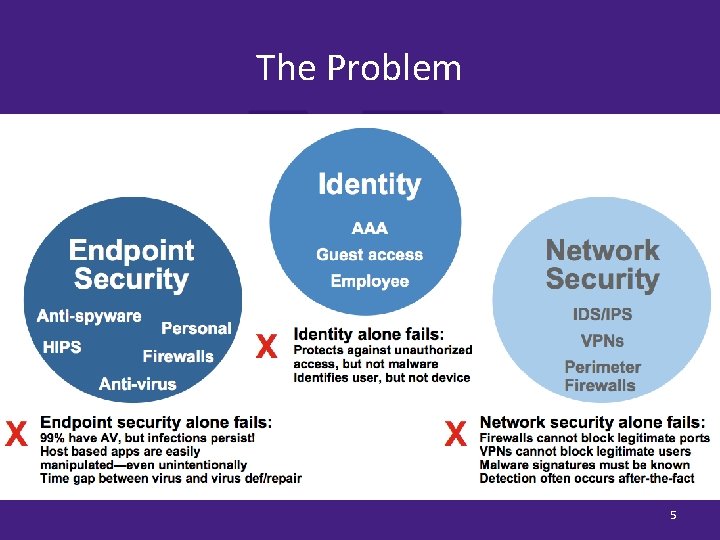
Pros and Cons of Existing Security Systems 6

Endpoint Security Symantec anti-virus deployed to individual workstations and servers in the data center Cisco personal firewall software installed on laptops with remote access enabled Pros Centrally managed anti-virus can identify workstations without updated virus definitions. Local firewall policy enforcement cannot be disabled by end users. Cons Anti-virus software slows machine performance to the point where users disable automatic updates and stop scans. There is no way to prevent users from altering the anti-virus software. Only users with VPN access have the protection provided by local firewall policy enforcement. There is no anti-spyware or host intrusion prevention solution 7 deployed.

Identity Four distinct user directories: Authentication • Access request forms required for creation of user accounts in each directory • Written password policy requires strong passwords and password expiration maintained/enforced separately in each directory Authorization • Authorization policies maintained in each directory by local administrators • Manual process for account termination, user access must be removed from each directory Accounting • Weekly directory access reviews compared against termination reports Pros My Reduced risk when an account in one directory is compromised ords w s s Pa Cons Policies cannot be maintained or enforced centrally Lots of passwords to keep track of → “loose” password management 8 Maintenance and SOX compliance nightmare

Network Security Port-based 802. 1 Q virtual local area networks (VLANs) for network and user segregation Pros Separate broadcast domains for trusted internal users and untrusted guest users – groups unable to communicate directly Trusted internal PCs cannot contract viruses from untrusted guest PCs Untrusted guest users are unable to access private internal servers Use of VLAN Trunking Protocol eases VLAN management Cons No measure to prevent untrusted guests from connecting to private ports Misconfiguration of a port will provide trusted network access Use of separate subnets leads to inefficient use IP address space Switches may be vulnerable to attacks related to MAC flooding, 9 tagging, multicast brute force, etc.

Gap Analysis in Current Solution • Policies for endpoint security are not enforceable • Users are not authenticated before access to the network. Identification is instead performed by the application • Several entry points: wireless, wired and VPN • Different types of users: full-time employees, vendors, partners and guests • VLAN assignment is not dictated by identity or security posture 10

Possible Solutions 11

Improve Endpoint Security • Deploy a comprehensive endpoint solution that includes anti-virus, anti-spyware, and host intrusion prevention capabilities • Define and enforce policies that do not allow end users to disable these protections • Deploy personal firewall software to all computers, not only VPN enabled systems • Design an employee education campaign stressing the importance of maintaining up to date security software definitions 12

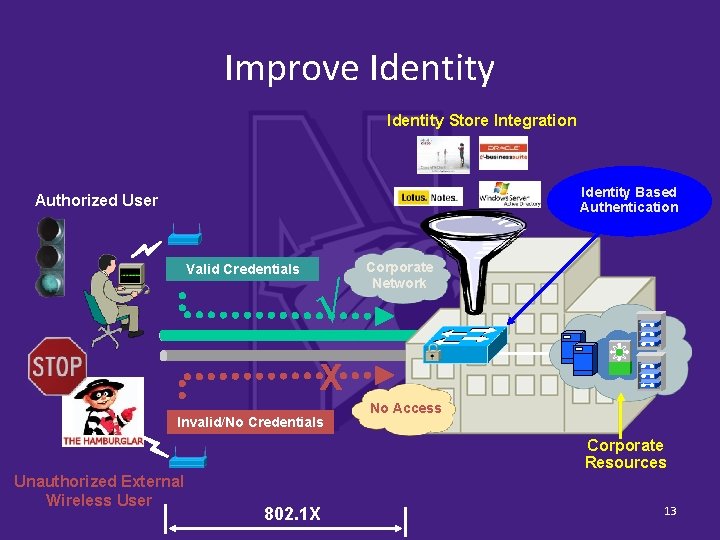
Improve Identity Store Integration Identity Based Authentication Authorized User Valid Credentials √ Corporate Network X Invalid/No Credentials No Access Corporate Resources Unauthorized External Wireless User 802. 1 X 13

Improve Network Security Virtual Private Networks • Provided by vendors such as Cisco and F 5 • Ensures confidentiality and integrity, but only for point to point connections R A M ! E T H G I N • Provided by vendors such as Sourcefire, 3 Com, and IBM T • Able to use both predefined (and regularly updated) signatures and N E statistics to detect and prevent attacks M E • May cost tens of thousands of dollars per Gbps of inspection with no G guaranteed return A N Firewalls A M • Provided by vendors such as Check Point, Juniper Networks, etc. Intrusion Detection and Prevention Systems • Control what hosts can access on other networks by port, protocol, or IP address • Unless installed on every PC, not useful between hosts on internal LANs 14

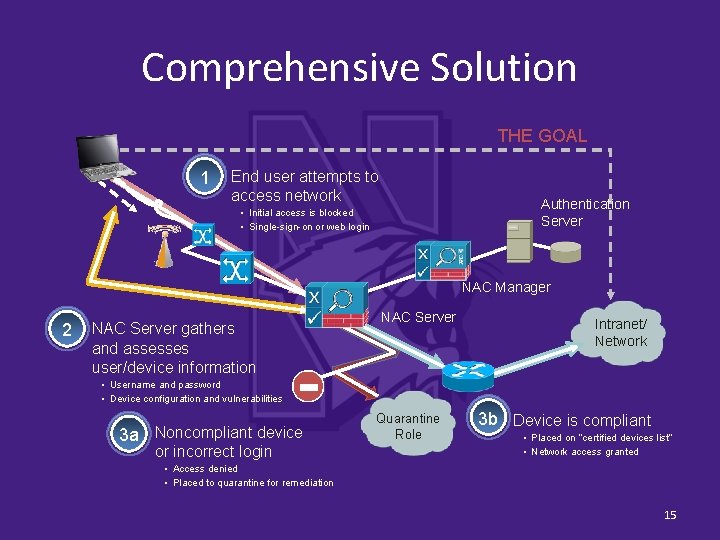
Comprehensive Solution THE GOAL 1 End user attempts to access network Authentication Server § Initial access is blocked § Single-sign-on or web login NAC Manager 2 NAC Server gathers and assesses user/device information NAC Server Intranet/ Network § Username and password § Device configuration and vulnerabilities 3 a Noncompliant device or incorrect login Quarantine Role 3 b Device is compliant § Placed on “certified devices list” § Network access granted § Access denied § Placed to quarantine for remediation 15

Recommended Solution 16

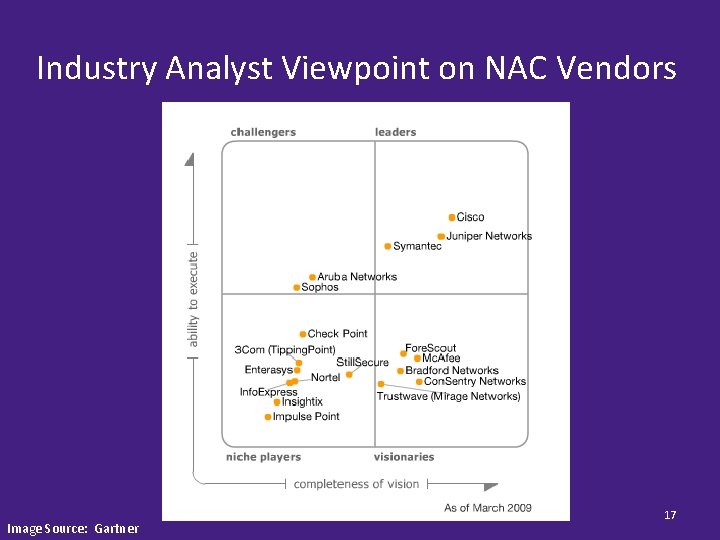
Industry Analyst Viewpoint on NAC Vendors Image Source: Gartner 17

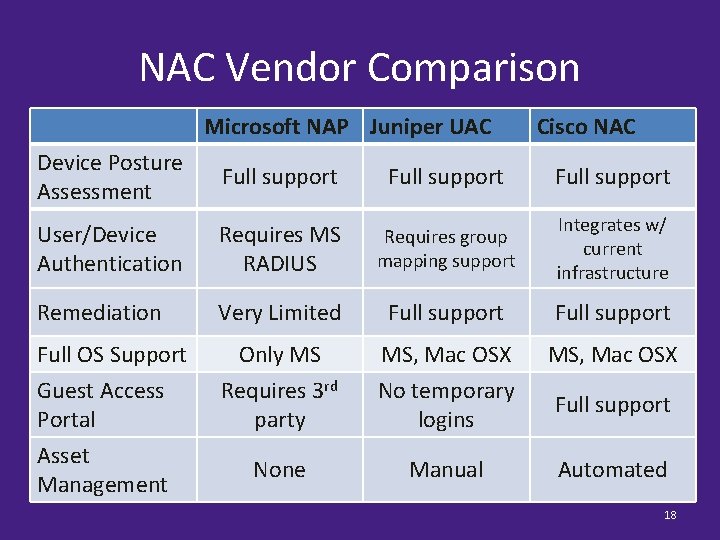
NAC Vendor Comparison Microsoft NAP Juniper UAC Cisco NAC Device Posture Cisco NAC UAC Microsoft NAP Full support Juniper Full support Assessment User/Device ✔ ✔ ✔ w/ Integrates Authentication Requires MS User/Device Requires group current mapping support Authentication RADIUS Device Posture ✔ ✔ ✔ infrastructure Remediation Full support Limited Very Remediation Very Limited Full support Full Limited support Full OS Support MS, Only MS, Mac Mac. MS OSX Only MSOSX Support Guest Access Requires 3 rd No temporary Full support Guest Access No temporary Portal party logins Full support No support Portal IDs Asset None Manual Automated Management 18

Solution Implementation 19

Total Cost of Ownership Number of users supported: Up to 10, 000, including guests Initial Hardware/Software Cost = $125, 000 Implementation Cost = $25, 000 Maintenance Cost = $72, 000 per year Power & Cooling Cost = $3, 000 per year TCO = $150, 000 + $75, 000 per year = $225, 000 initial year cost TCO ≈ $500, 000 after 5 years 20

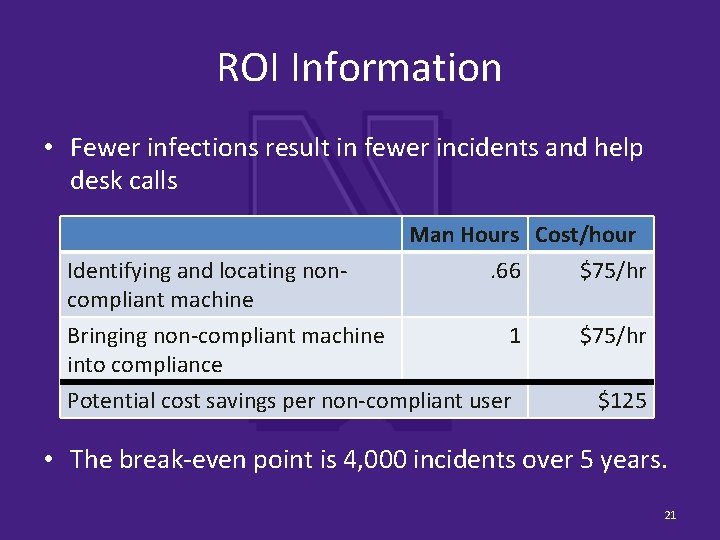
ROI Information • Fewer infections result in fewer incidents and help desk calls Identifying and locating noncompliant machine Bringing non-compliant machine into compliance Man Hours Cost/hour. 66 $75/hr 1 Potential cost savings per non-compliant user $75/hr $125 • The break-even point is 4, 000 incidents over 5 years. 21

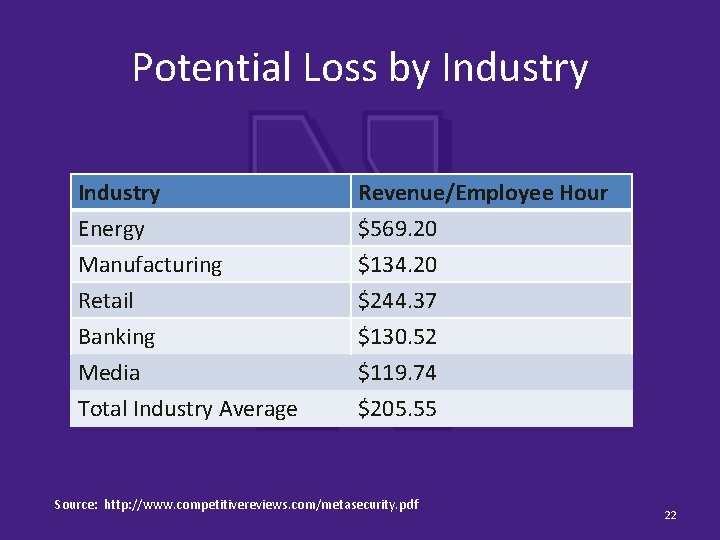
Potential Loss by Industry Energy Manufacturing Retail Revenue/Employee Hour $569. 20 $134. 20 $244. 37 Banking Media Total Industry Average $130. 52 $119. 74 $205. 55 Source: http: //www. competitivereviews. com/metasecurity. pdf 22

Feasibility Analysis • Already a Cisco network, so NAC would simply be an add-on to current network • Entry points can easily be identified • Anti-virus and other end-point protections already deployed to users • Non-compliance problems currently occur at a rate of 6 per day, indicating a positive ROI on a potential NAC investment 23

Final Recommendation We conclude that a comprehensive NAC system such as Cisco’s Network Admission Control would be a better investment than piecemeal improvements to the company’s current network security systems. 24

Questions? 25