NETFLOW analysis infrastructure at Indiana University Gregory Travis













- Slides: 20

NETFLOW analysis infrastructure at Indiana University Gregory Travis Advanced Network Management Lab (ANML) Indiana University greg@iu. edu

What do we do? • Research – Build new DDo. S/IDS systems – Learn what’s going on • Operational – Support REN-ISAC – Report upstream

ANML - Network Security • Abilene NOC presented with an opportunity to partner with Asta Network and Arbor Networks via Internet 2 • Distributed Denial of Service (DDo. S) detection equipment first installed at Indianapolis core node in 2000 • DDo. S detection equipment showed *many* DDo. S incidents traversing Abilene each day • Determined that this was a potential opportunity to provide more focus on security for the research and education network space

ANML - Network Security • Indiana University leveraged the security services provided to Abilene, along with the existing Policy and Security arms of the Office of the Vice President for Information Technology, into a proposal to perform the function of the Research and Education Information Sharing and Analysis Center (REN-ISAC) • February 21 st 2003, Indiana University signed an agreement with the National Infrastructure Protection Center to provide the REN-ISAC function • Doug Pearson is the director of the REN-ISAC (www. renisac. edu)

What’s an ISAC/REN-ISAC? • ISACs (Information Sharing and Analysis centers) are cooperations of private and public entities within Department of Homeland Security • The REN-ISAC Supports U. S. higher education and research communities by providing advanced network security services • Also supports efforts to protect the national cyber infrastructure

ANML I 2 DDo. S Monitoring • Multiple Systems monitoring NETFLOW data looking for indications of attack. – Arbor Networks – Internal exploratory tools – Snort • Systems feed output into central event database

What we do with the data • Input into tools for effective exploratory data analysis for NETFLOW data: – Ad-hoc (I. e. flowtools) – Relational (Postgres) – Third Party/Commercial (Arbor) – Hybrids

Hybrid Project • Provide an SQL like query language with a data storage system that is optimized for the storage and analysis of NETFLOW. • SQL databases have great expressing capability but are slow in this type of task. • Flowtools is faster but the expression language is a bit obtuse.

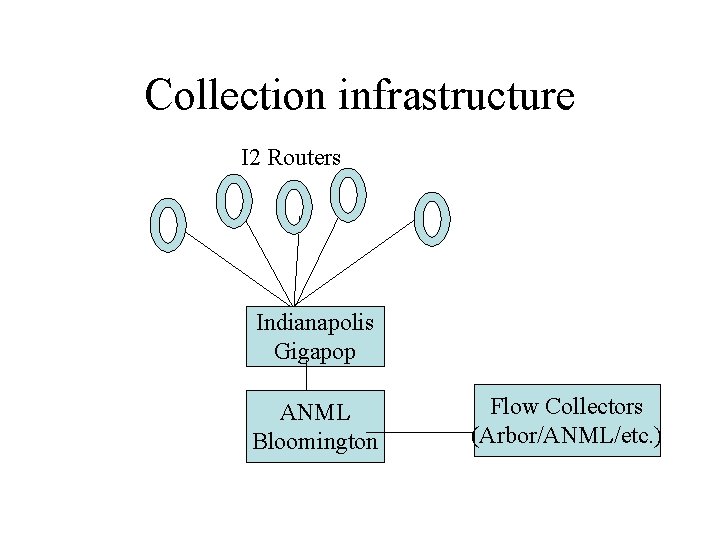
Collection infrastructure I 2 Routers Indianapolis Gigapop ANML Bloomington Flow Collectors (Arbor/ANML/etc. )

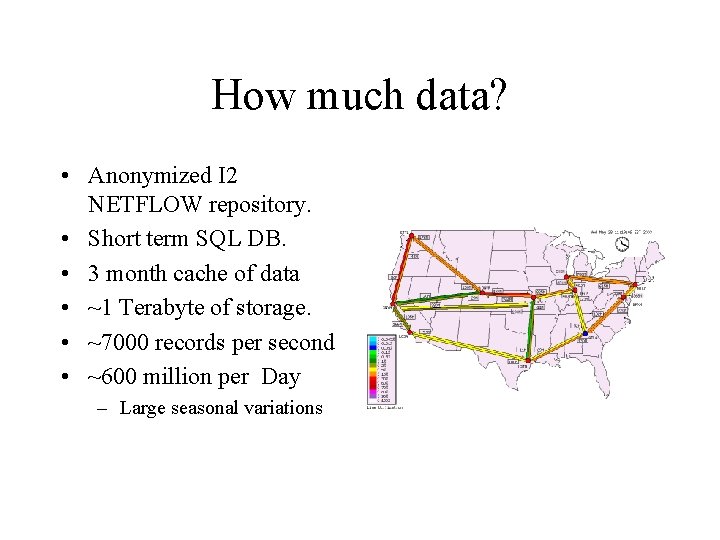
How much data? • Anonymized I 2 NETFLOW repository. • Short term SQL DB. • 3 month cache of data • ~1 Terabyte of storage. • ~7000 records per second • ~600 million per Day – Large seasonal variations

DDo. S Summary Reporting

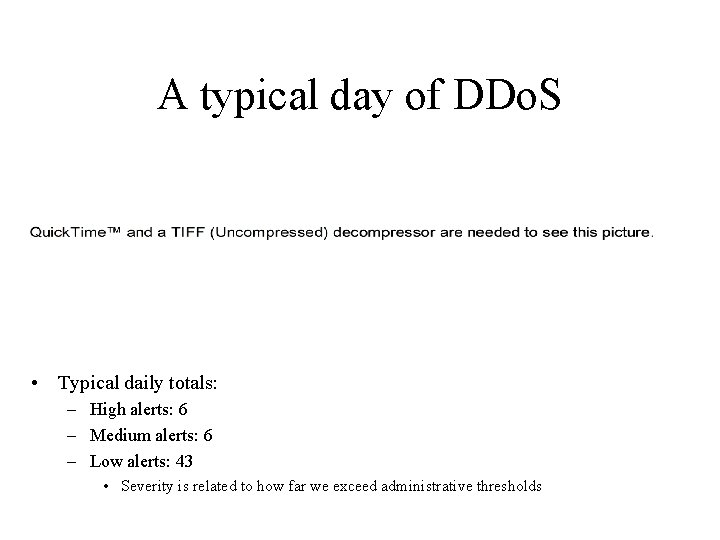
A typical day of DDo. S • Typical daily totals: – High alerts: 6 – Medium alerts: 6 – Low alerts: 43 • Severity is related to how far we exceed administrative thresholds

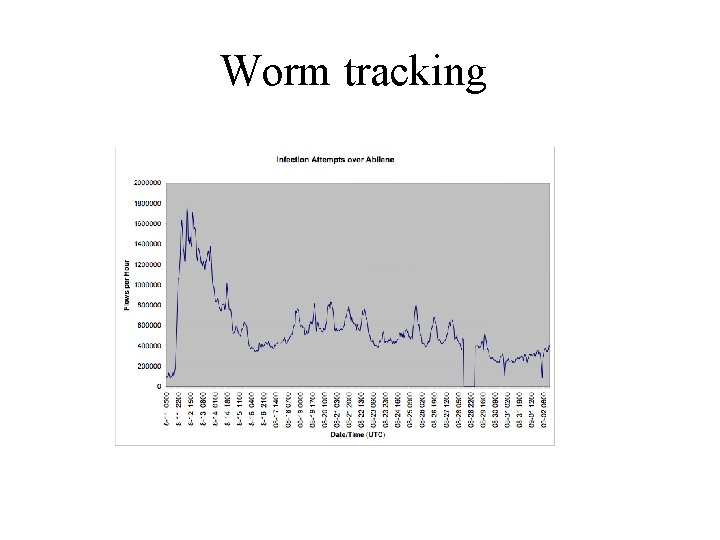
Worm tracking

Two types of data • We’ve been talking about anomaly tracking via NETFLOW but should also make mention of signature-based systems • Both methods have their strengths and weaknesses • Typically you will need to do both

NETFLOW • Very useful for monitoring high-volume networks • Doesn’t have wiretapping implications that signature-matching does – Data is already aggregated/depersonalized • But you can’t “see the data” which is good and bad – Sometimes difficult to know if an attack a real or just a data anomaly • Blaster example

Signature matching • Actually looking at the data on the wire to look for specific DDo. S/worm/etc. “signatures” • VERY compute intensive – Not practical “at wire speed” – Typically deployed on a per-LAN basis

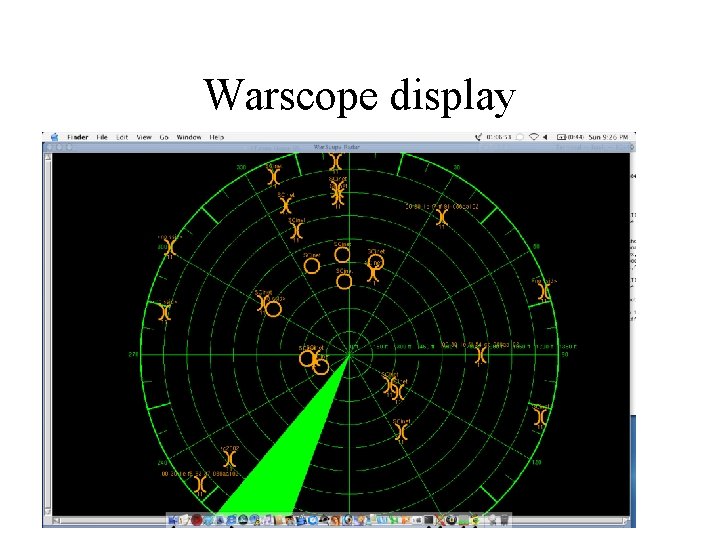
“Warscoping” • ANML developing location services for wireless devices • Number of instances where it’s important to be able to physically locate wireless devices – “ 911” services – Troubleshooting – Locating nefarious actors

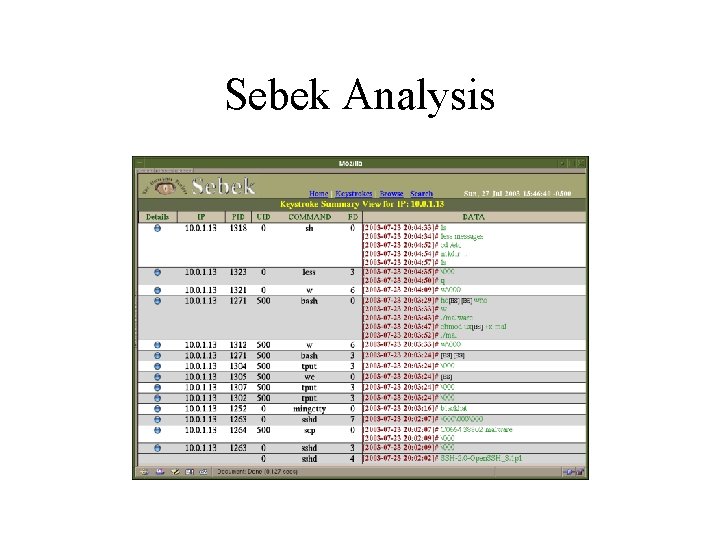
Other techniques we use • Honeypots – Tripwire – SEBEK • Warscoping – Geolocation

Warscope display

Sebek Analysis