Net Centric Warfare Technology Driven Agility Dawn Meyerriecks






















- Slides: 40

Net. Centric Warfare: Technology Driven Agility Dawn Meyerriecks Principal Director, Global Information Grid Enterprise Services (703)882 -1000 meyerrid@ncr. disa. mil

“Freedom is not synonymous with an easy life. . There are many difficult things about freedom: It does not give you safety, it creates moral dilemmas for you; it requires self-discipline; it imposes great responsibilities; but such is the nature of Man and in such consists his glory and salvation. ” Margaret Thatcher Current Operations Support : A Sample Operational Thread

Sample Mission Thread: Battle Damage Assessment to Target USAF Remote OPNS GWY DISN Langley Norfolk Mac. Dill European Spt Site Legend Army Navy Air Force Joint Commercial Sigonella Ali Al Salem Camp Doha PSAB Qatar

Networks @ Multiple Security Levels Comm Svr KG KG KG Intel Network Data Svr App Svr Client Intel Reachback App Client Svr Sensors Client Comm Svr Client JTF Deployed Data Svr CJTF Deployed App Svr Client C 2 Reachback KG KG Do. D Secret Network Data Svr App Svr KG Data Svr FW App Svr Personnel Reachback Logistics Reachback App Svr Do. D Intranet Shooter INTERNET

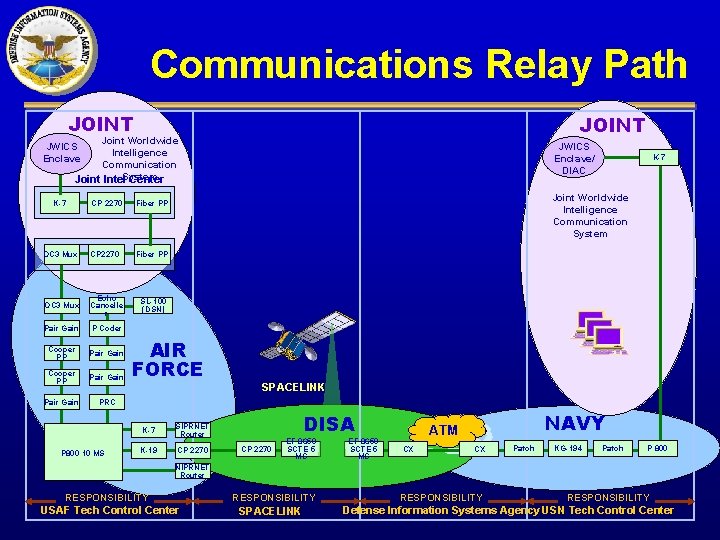
Communications Relay Path JOINT Joint Worldwide JWICS Intelligence Enclave Communication Joint Intel. System Center K-7 CP 2270 Fiber PP OC 3 Mux Echo Cancelle r SL-100 (DSN) Pair Gain P Coder Cooper PP Pair Gain PRC P 800 10 10 MS MS P 800 K-19 K-7 Joint Worldwide Intelligence Communication System AIR FORCE K-7 JWICS Enclave/ DIAC SPACELINK DISA SIPRNET Router CP 2270 EF 8650 SCTE 5 MS NAVY ATM CX CX Patch KG-194 Patch P 800 NIPRNET Router RESPONSIBILITY USAF Tech Control Center RESPONSIBILITY SPACELINK RESPONSIBILITY Defense Information Systems Agency USN Tech Control Center

Single Supporting Data Source JCS DIA National GCCS INSCOM NSA GCCS/ GCCS SOUTHCOM GCCS NIMA GCCS/ GCCS JTT EUCOM GCCS CENTCOM NIMA (St. Louis) JSOC JTT GCCS/ GCCS PACOM (JICPAC) MLDBR GCCS/ GCCS MLDBR GCCS CENTRIX (Coalition) GCCS/ TBMCS JTF-SWA (CFACC) JTT GCCS/ TBMCS JWICS SIPR GCCS/ GCCS ARCENT (CFLCC) JTT GCCS/ GCCS (ASAS) NAVCENT (CFMCC) JTT GCCS-M/ GCCS-M GCCS BATTLEGROUP GCCS-M/ GCCS-M IOS/ IOS SOCOM GCCS Service/JTF SOCCENT (CFSOCC) MARCENT JTT Co. Com STRATCOM West Coast BGs/ARGs/MEUs GCCS CENTAF NRO (Field Site) JTT GCCS clients

Common Operational Picture – Real-Time Video, Integrated Imagery

Common Operational Picture – Theater Ballistic Missile, Integrated Intelligence UNCLASSIFIED

Operation Iraqi Freedom Successes ØFirst- All-Service and SOF, Red, Blue, & Intel fused picture. ØFirst- Large-scale use of secure satellite phones in a combat environment. First- Extensive coalition automated information sharing exchange. Ø ØFirst- Desktop collaboration tools used for joint C 2. ØFirst- Widespread use of VTC as a C 2 system. ØFirst- Ubiquitous use of commercial SATCOM to supplement military SATCOM. ØFirst- Extensive coordinated use of UAVs. ØFirst- Real time in-transit/asset visibility.

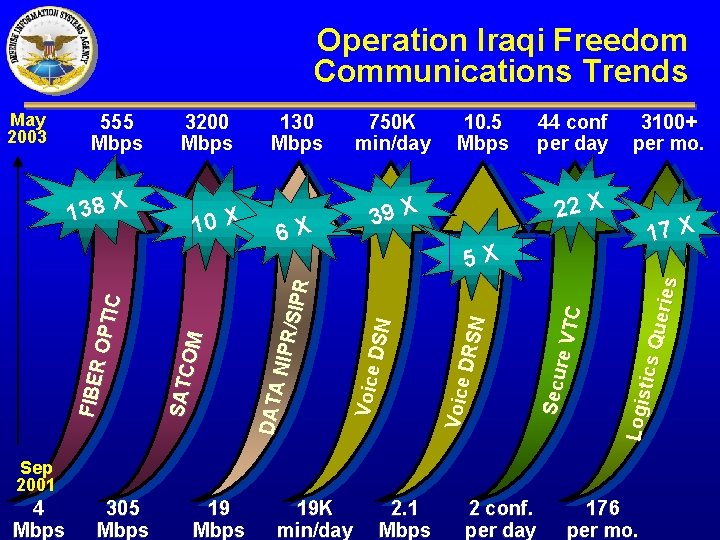
Operation Iraqi Freedom Communications Trends 750 K min/day 10. 5 Mbps 6 X 44 conf per day 3100+ per mo. 22 X 39 X 17 X Log i s tics S ecu r e V TC Quer ies 5 X Voice D RSN 10 X 130 Mbps V oi ce DSN F IBE R OPT IC 138 X 3200 Mbps DA TA NI PR /SIPR 555 Mbps SAT C OM May 2003 Sep 2001 4 Mbps 305 Mbps 19 K min/day 2. 1 Mbps 2 conf. per day 176 per mo.

Prec Le (Air thality 2 Gn d OP S) ision d Spee Kno wled ge ODS/OIF Comparisons ODS 3200 ISR Sortie Hours 7 Mos Buildup 10 % PGMs ~ 30 SOF Teams 10 % Integ Ops 4 Acft/Tgt OIF 1700 ISR Sortie Hours <3 Mos Buildup 70 % PGMs ~ 100 SOF Teams 90 % Integ Ops 1 Acft/4 Tgt RESULTS 3 X Info ½ of the Hours Footprint # Ships Msn Achieve t Speed of Mnvr Precision Decisions Collat Dam RQD Ord Economy Of Force Heavy Ord Rqmts

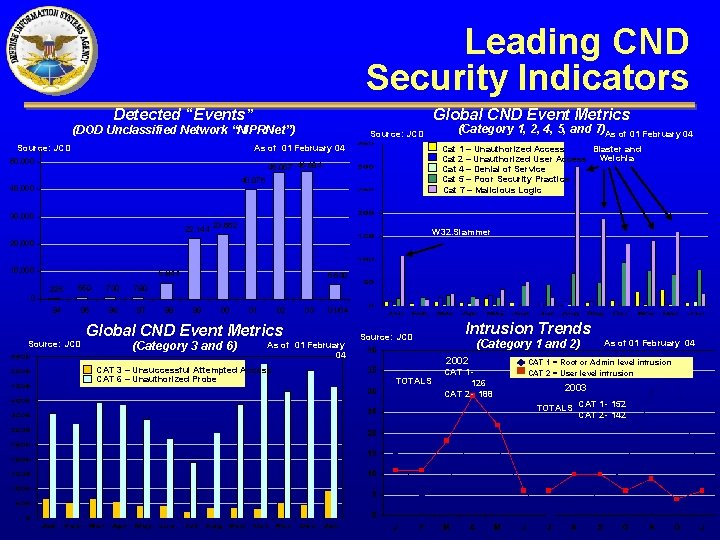
Leading CND Security Indicators Global CND Event Metrics Detected “Events” (DOD Unclassified Network “NIPRNet”) Source: JCD As of 01 February 04 50, 000 Blaster and Cat 1 – Unauthorized Access Cat 2 – Unauthorized User Access Welchia Cat 4 – Denial of Service Cat 5 – Poor Security Practice Cat 7 – Malicious Logic 46, 057 46, 684 40, 076 40, 000 (Category 1, 2, 4, 5, and 7)As of 01 February 04 30, 000 22, 144 23, 662 W 32. Slammer 20, 000 10, 000 0 5, 844 225 559 730 780 94 95 96 97 Source: JCD 98 5, 540 99 00 01 02 03 01/04 Global CND Event Metrics (Category 3 and 6) As of 01 February 04 CAT 3 – Unsuccessful Attempted Access CAT 6 – Unauthorized Probe Source: JCD Intrusion Trends (Category 1 and 2) 2002 TOTALS CAT 1 126 CAT 2 - 188 As of 01 February 04 CAT 1 = Root or Admin level intrusion CAT 2 = User level intrusion 2003 TOTALS CAT 1 - 152 CAT 2 - 142

Why We’re Here Today: The Challenge • Current Enterprise-Wide Infrastructure Approaches Are Aging • Good News: 27 Releases of Global Command Control Since 9/11 • Bad News: Insufficiently Scalable, Flexible, Technologically Dated • Current Web Services, Enterprise Application Integration, Service-Oriented Architectures Hold Promise • Good News: Early Enterprise Efforts Indicate Certain Aspects of Technology are Sufficiently Mature for Broad Application • Bad News: Lots of Maturation Still Required – Both for the Federal Enterprise to Use and for the Commercial Technology Itself

“…possibly the single-most transforming thing in our forces will not be a weapons system, but a set of interconnections and a substantially enhanced capability because of that awareness. ” awareness -- Defense Secretary Rumsfeld The Future

To Counter the Asymmetric Threat: Agile Net. Centric Warfare - Transform Federal Intranets into Service Oriented Architectures - Publish all information as early and as widely as possible - Empower Users to pull whatever they want whenever they want - Distribute Product Management to specialized Communities but - Clearly identify Information Producers to the Enterprise - Exploit Market Mechanisms Visibility Agility Supply & Demand ROI Metrics “Boundaryless Information Flow” Scale: Several Million Users; Tens of Thousands of Information Services

Keys to Agility 1 st - Comprehensive, accurate, shared Situation Awareness to enable self-synchronization 2 nd - Mobility and “Composability” to rapidly reconfigure forces and supporting information capabilities 3 rd - Service Oriented Architecture (SOA) • Modular, loosely coupled • Ubiquitous user access Rapidly reconfigurable Collaboration Result: Dramatically accelerated organizational learning* cycle! *Responders (Users) exhibit rapid behavior change in combat (continuous experimentation)

The New Assumptions • Industrial Age (System-centric) • • • Clear lines of authority Limited Scope (Finite system boundaries and user population) Known, relatively static requirements Predictable future (stable Business environment and standard processes) Deduce designs from high level abstractions and test effectiveness with small-scale experimentation Information Age (Net-centric) • • • Boundless information space with no single controlling authority Highly dynamic requirements w/ many unknowns Marginally predictable near term future Many users engaging in unpredictable ways at unpredictable intervals Highly, Dynamically Interconnected Designs must: 1. 2. Derive from massive simulations and ongoing real world observations Be agile before and after fielding in response to new conditions

The New Imperatives How to Improve Design of large, complex Netcentric capabilities? How to Lower Risks inherent in designing and deploying large, complex Net-centric capabilities? Shape evolution of Enterprise IT Vice Build systems

Net-centric Characteristics • Heterogeneous • Variety is essential and inevitable – basis for healthy evolutionary growth and survival within dynamic threat environment • Parallel • Multiple implementation and concurrent use of components and processes – increases speed and provides fail-over capability • Market-driven • Emphasizes Market principles vice top down direction to optimize – “Survival of the fit“ (v. selection of the fittest from a single perspective) • Developers “experiment early and often” to find the right niche • Agile and adaptable • Capable of rapid reconfiguration to meet new and unanticipated requirements or circumvent disruption • Expedient task-oriented collaborations vice static bureaucracy

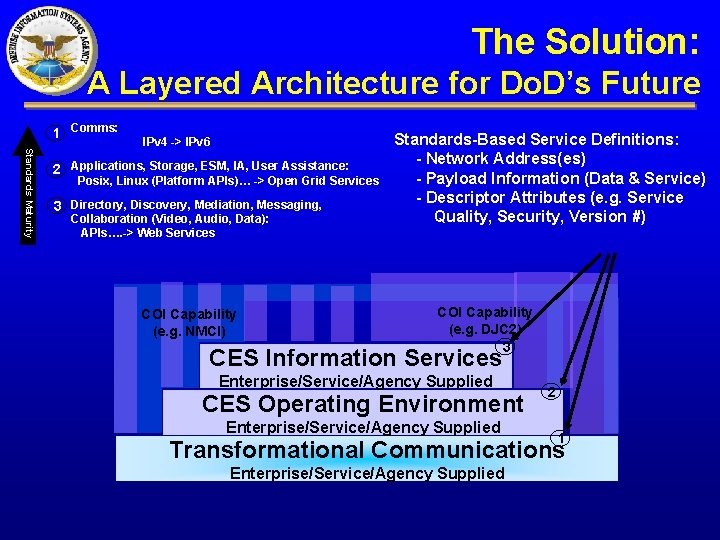
The Solution: A Layered Architecture for Do. D’s Future 1 Comms: Standards Maturity IPv 4 -> IPv 6 2 Applications, Storage, ESM, IA, User Assistance: Posix, Linux (Platform APIs)… -> Open Grid Services 3 Directory, Discovery, Mediation, Messaging, Collaboration (Video, Audio, Data): APIs…. -> Web Services COI Capability (e. g. NMCI) Standards-Based Service Definitions: - Network Address(es) - Payload Information (Data & Service) - Descriptor Attributes (e. g. Service Quality, Security, Version #) COI Capability (e. g. DJC 2) 3 CES Information Services Enterprise/Service/Agency Supplied CES Operating Environment Enterprise/Service/Agency Supplied 2 1 Transformational Communications Enterprise/Service/Agency Supplied

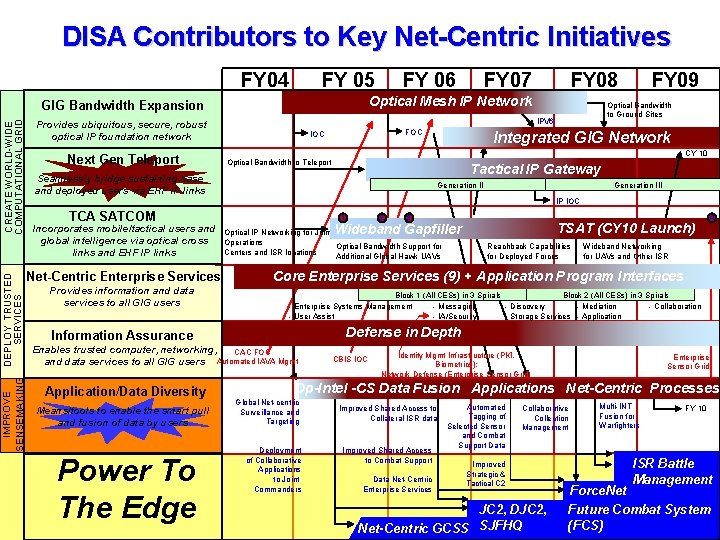
DISA Contributors to Key Net-Centric Initiatives FY 04 FY 05 CREATE WORLD-WIDE COMPUTATIONAL GRID DEPLOY TRUSTED SERVICES IMPROVE SENSEMAKING FY 07 FY 08 Optical Mesh IP Network GIG Bandwidth Expansion FOC IOC FY 09 Optical Bandwidth to Ground Sites IPV 6 Provides ubiquitous, secure, robust optical IP foundation network Next Gen Teleport FY 06 Integrated GIG Network CY 10 Optical Bandwidth to Teleport Tactical IP Gateway Seamlessly bridge sustaining base and deployed users via EHF IP links Generation III IP IOC TCA SATCOM Incorporates mobile/tactical users and global intelligence via optical cross links and EHF IP links Net-Centric Enterprise Services Provides information and data services to all GIG users 1 Power To The Edge TSAT (CY 10 Launch) Reachback Capabilities for Deployed Forces 4 Wideband Networking for UAVs and Other ISR Block 1 (All CESs) in 3 Spirals Block 2 (All CESs) in 3 Spirals - Enterprise Systems Management - Messaging - Discovery - Mediation - Collaboration - User Assist - IA/Security - Storage Services - Application Defense in Depth Enables trusted computer, networking, CAC FOC and data services to all GIG users Automated IAVA Mgmt Means/tools to enable the smart pull and fusion of data by users 3 Core Enterprise Services (9) + Application Program Interfaces Information Assurance Application/Data Diversity 2 Wideband Gapfiller Optical IP Networking for Joint Operations Optical Bandwidth Support for Centers and ISR locations Additional Global Hawk UAVs CBIS IOC Identity Mgmt Infrastructure (PKI, Biometrics); Network Defense (Enterprise Sensor Grid) Enterprise Sensor Grid Op-Intel -CS Data Fusion Applications Net-Centric Processes Global Net-centric Surveillance and Targeting Deployment of Collaborative Applications to Joint Commanders Improved Shared Access to Collateral ISR data Improved Shared Access to Combat Support Data Net-Centric Enterprise Services Automated Tagging of Selected Sensor and Combat Support Data Collaborative Collection Management Improved Strategic & Tactical C 2 JC 2, DJC 2, Net-Centric GCSS SJFHQ Multi-INT Fusion for Warfighters FY 10 ISR Battle Management Force. Net Future Combat System (FCS) (examples)

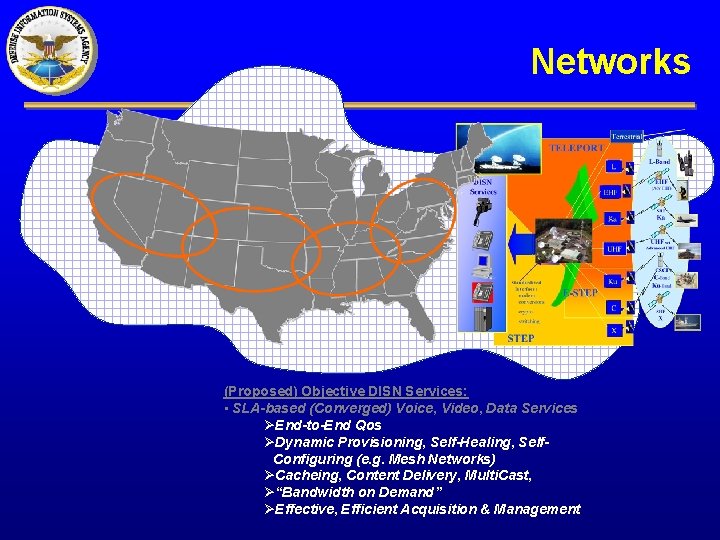
Networks (Proposed) Objective DISN Services: • SLA-based (Converged) Voice, Video, Data Services ØEnd-to-End Qos ØDynamic Provisioning, Self-Healing, Self. Configuring (e. g. Mesh Networks) ØCacheing, Content Delivery, Multi. Cast, Ø“Bandwidth on Demand” ØEffective, Efficient Acquisition & Management

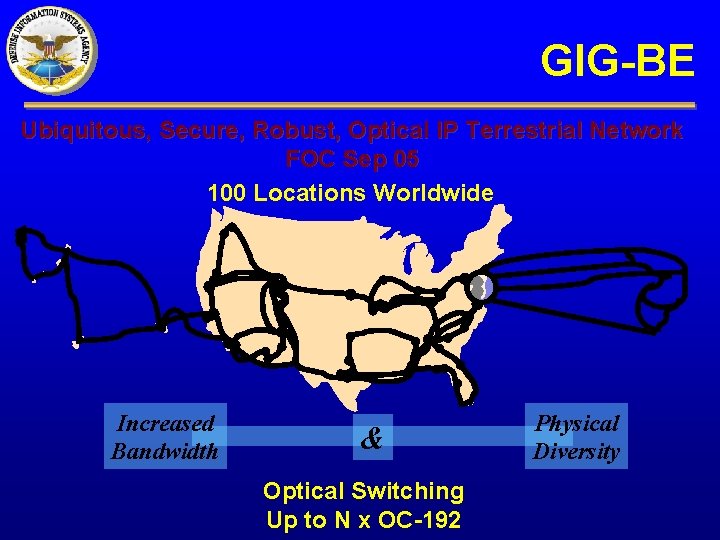
GIG-BE Ubiquitous, Secure, Robust, Optical IP Terrestrial Network FOC Sep 05 100 Locations Worldwide Increased Bandwidth & Optical Switching Up to N x OC-192 Physical Diversity

Teleport Pathfinder ADVANCED EHF MILSTAR (MDR - 02+) Protected (Protected/Survivable) Gapfiller WB (Mil Ka) DSCS (Capacity & Broadcast) SHF/ Ka DSCS-SLEP Wideband COMMERCIAL (C and Ku and L) GBS (Hosted on UFO) Tactical Terminals Advanced UHF UFO Narrowband SMART-T (EHF) SCAMP (EHF) Future High Cap & Broadcast System (Mobile User Services) NESP Follow-On (EHF) GMT LMST Army Wideband Tactical Teleport 99 01 STEP X 03 GEN I C/Ku UHF 05 GEN II Ka EHF L HF IP 07 09 GEN III Adv EHF Future Wideband 11 13

Transformational Communications System

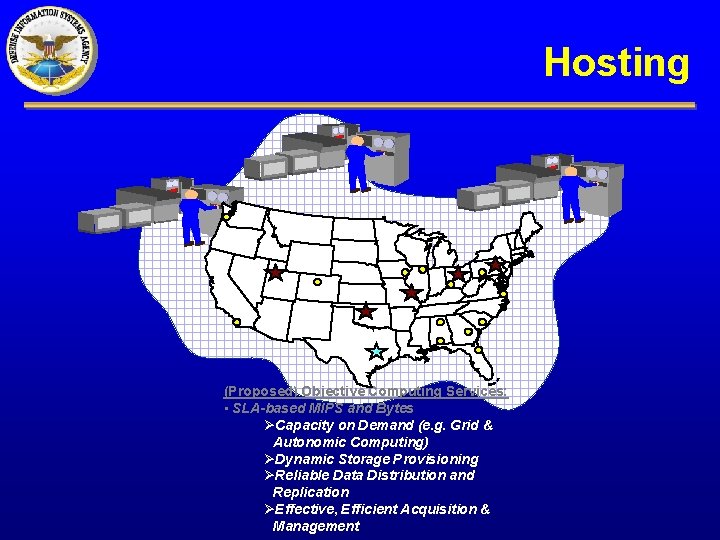
Hosting (Proposed) Objective Computing Services: • SLA-based MIPS and Bytes ØCapacity on Demand (e. g. Grid & Autonomic Computing) ØDynamic Storage Provisioning ØReliable Data Distribution and Replication ØEffective, Efficient Acquisition & Management

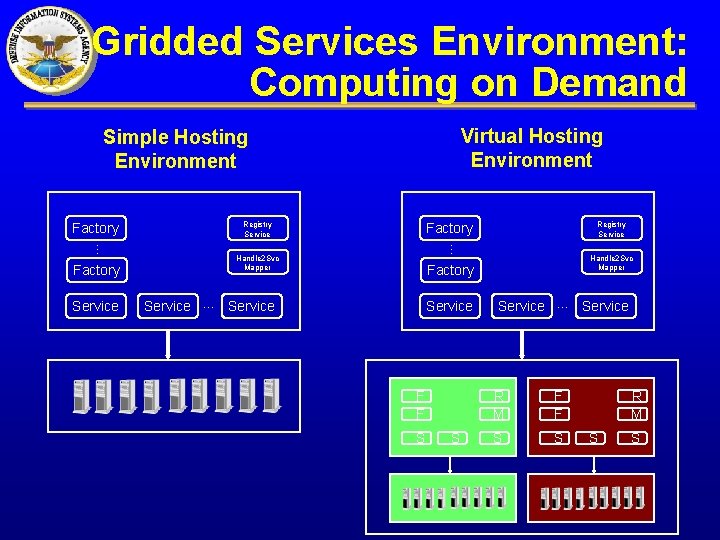
Gridded Services Environment: Computing on Demand Virtual Hosting Environment Simple Hosting Environment Registry Service … … Handle 2 Svc Mapper Factory Registry Service Factory Handle 2 Svc Mapper Factory Service F F S S Service … Factory R M F F S S Service R M S S

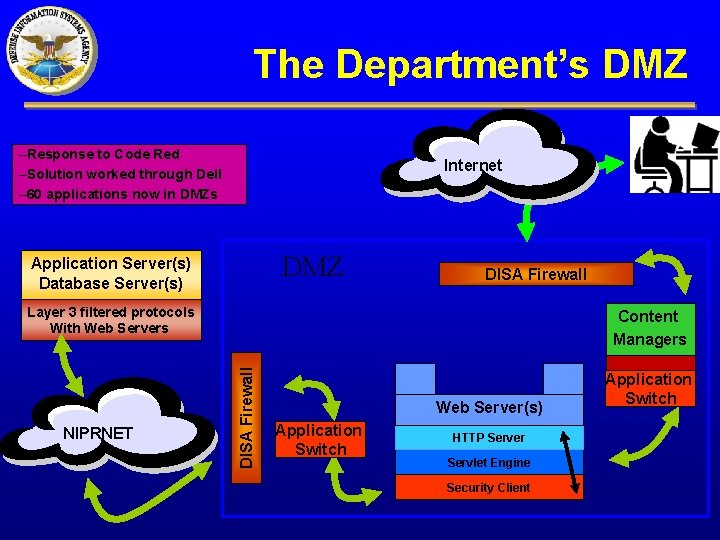
The Department’s DMZ –Response to Code Red –Solution worked through Dell – 60 applications now in DMZs Internet DMZ Application Server(s) Database Server(s) DISA Firewall Layer 3 filtered protocols With Web Servers DISA Firewall NIPRNET Content Managers Web Server(s) Application Switch HTTP Server Servlet Engine Security Client Application Switch

Infrastructure Cert Svr Dir Svr Portal Svr (Proposed) Objective Enterprise Services: • Building Blocks for Secure Integration of Applications and Data Sources ØIdentification & Authentication ØDirectory ØMessaging & Transactions ØInformation Management (Discovery, Access, Dissemination) ØCollaboration ØEnterprise Management

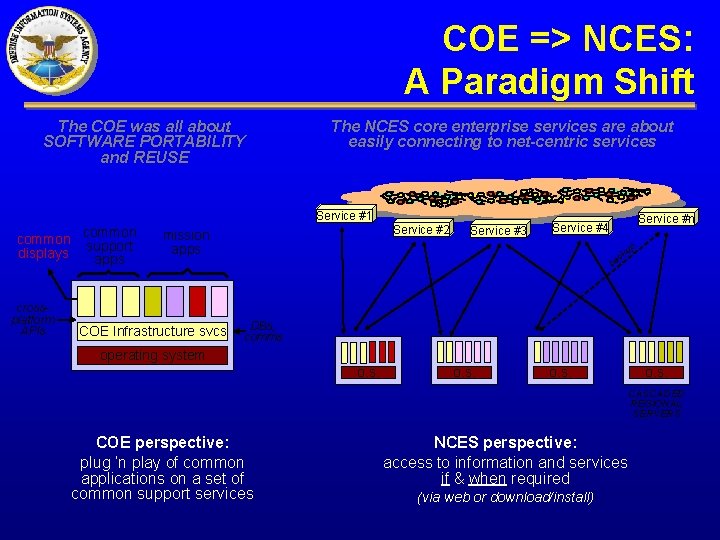
COE => NCES: A Paradigm Shift The COE was all about SOFTWARE PORTABILITY and REUSE The NCES core enterprise services are about easily connecting to net-centric services Service #1 common displays support apps crossplatform APIs mission apps COE Infrastructure svcs Service #2 Service #3 Service #n Service #4 p ku c ba DBs, comms operating system o. s. CASCADED REGIONAL SERVERS COE perspective: plug ‘n play of common applications on a set of common support services NCES perspective: access to information and services if & when required (via web or download/install)

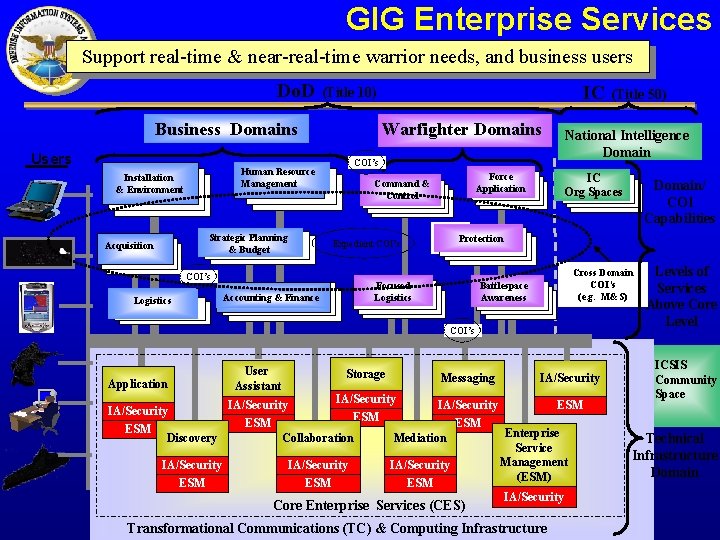
GIG Enterprise Services Support real-time & near-real-time warrior needs, and business users Do. D Warfighter Domains Business Domains Users Human Resource Management Installation & Environment Acquisition Strategic Planning & Budget COI’s Logistics Accounting & Finance IC (Title 10) COI’s Force Application Command & Control Expedient COI’s National Intelligence Domain IC Org Spaces Focused Logistics Application Storage Domain/ COI Capabilities COI’ Protection s Cross Domain COI’s (e. g. M&S) Battlespace Awareness COI’s User Assistant (Title 50) Messaging IA/Security ESM IA/Security ESM ESM Enterprise Discovery Collaboration Mediation Service Management IA/Security (ESM) ESM ESM IA/Security Core Enterprise Services (CES) Transformational Communications (TC) & Computing Infrastructure Levels of Services Above Core Level ICSIS Community Space Technical Infrastructure Domain

Applications… C 2 and Back. Office Cert Svr Dir Svr Portal Svr (Proposed) Objective Applications & Data Sources • Community of Interest Functionality • Secure, Interoperable Plug-n-Play Data Sources and Applications

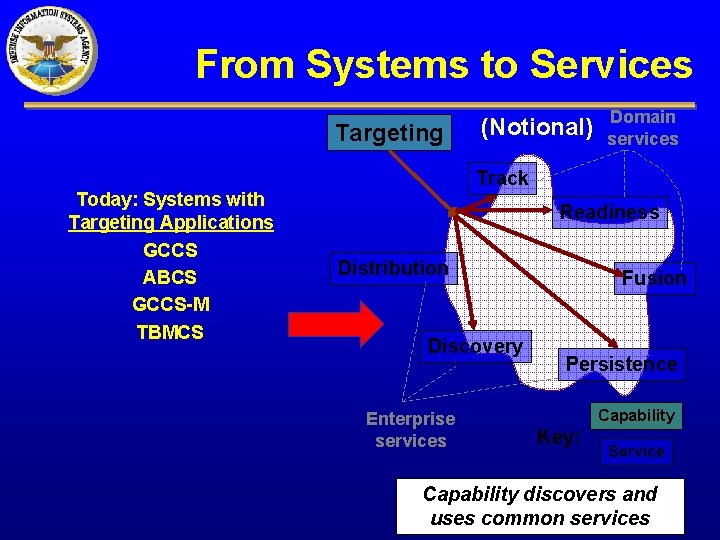
From Systems to Services Targeting Today: Systems with Targeting Applications GCCS ABCS GCCS-M TBMCS (Notional) Domain services Track Readiness Distribution Discovery Enterprise services Fusion Persistence Capability Key: Service Capability discovers and uses common services

“We can’t solve problems by using the same thinking we used when we created them” Albert Einstein The Results

Apps & Infrastructure with Redundancy (Target Bundle) ASSESS ENGAGE FIND FIX PLAN TARGET TRACK

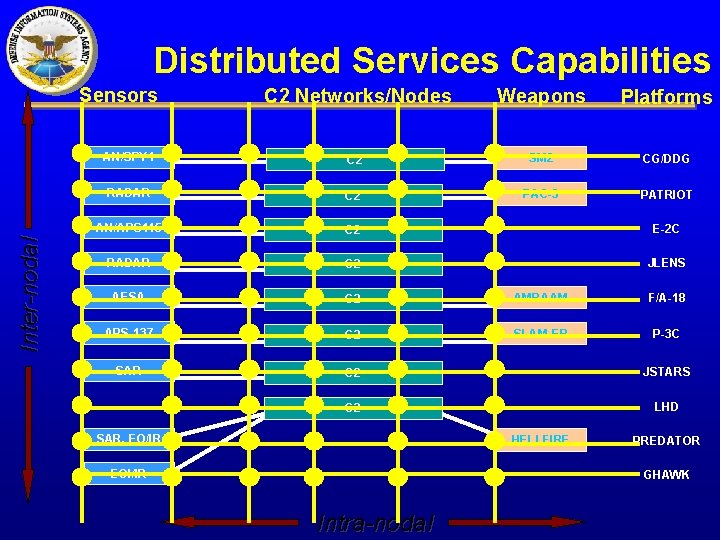
Distributed Services Capabilities Inter-nodal Sensors C 2 Networks/Nodes Weapons Platforms AN/SPY 1 C 2 SM 2 CG/DDG RADAR C 2 PAC-3 PATRIOT AN/APS 145 C 2 E-2 C RADAR C 2 JLENS AESA C 2 AMRAAM F/A-18 APS-137 C 2 SLAM-ER P-3 C SAR C 2 JSTARS C 2 LHD SAR, EO/IR HELLFIRE EOI/IR PREDATOR GHAWK Intra-nodal

Integration Pattern Emergence As-is: Stovepipe Patterns To-Be: Improved Integration

Illustrative Results Increased combat reach in selected scenarios: • • 40% more TAMD kills 50% reduction in number of leakers 100% increase in engagement envelope Up to ten-fold increase in overland percent area protected Most significant benefits realized when ALL combat reach capabilities implemented

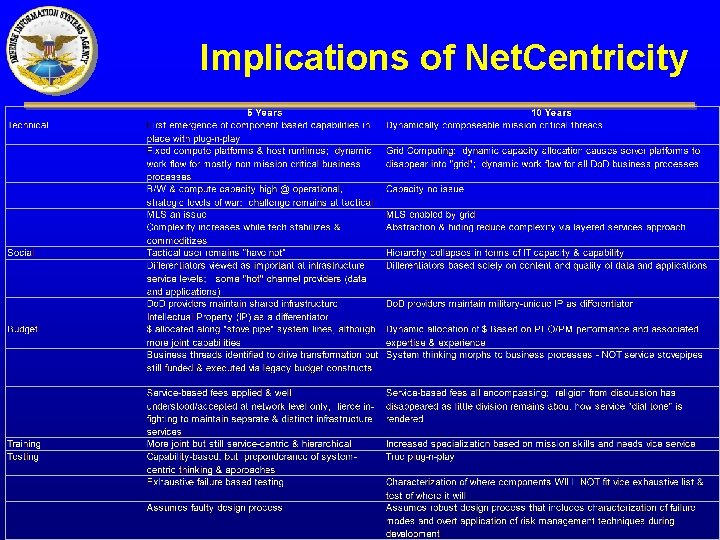
Implications of Net. Centricity
