NET Application Design Considerations Mark Sapossnek CS 594



















- Slides: 89

. NET Application Design Considerations Mark Sapossnek CS 594 Computer Science Department Metropolitan College Boston University

Prerequisites w This module assumes that you understand the fundamentals of: n n n Object-oriented programming C# ADO. NET ASP. NET Web Services. NET Framework Class Library

Learning Objectives w Understand how to design a. NET application w Understand key design considerations on the following topics: n n Scalability Performance Availability Security

Agenda w w w Design Model and Process. NET System Architecture. NET Design Patterns Security Scalability Availability

Design Model and Process w Microsoft Enterprise Services Framework Services-Based Application Design Model w Design Process w Design Principles

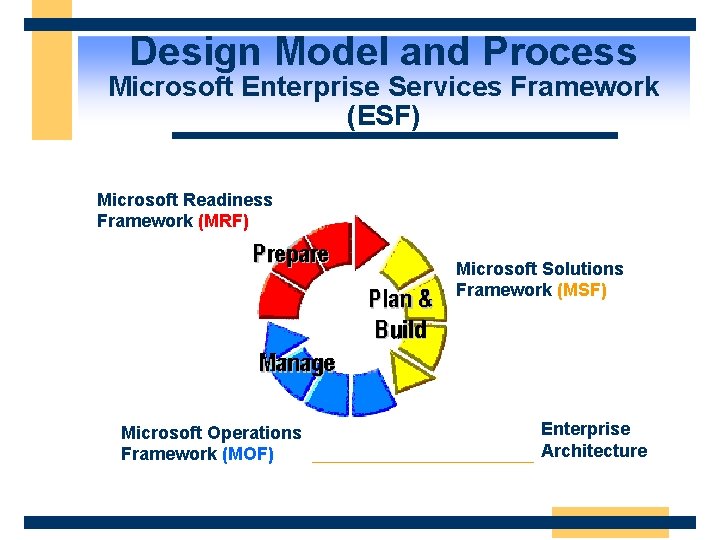
Design Model and Process Microsoft Enterprise Services Framework (ESF) Microsoft Readiness Framework (MRF) Microsoft Solutions Framework (MSF) Microsoft Operations Framework (MOF) Enterprise Architecture

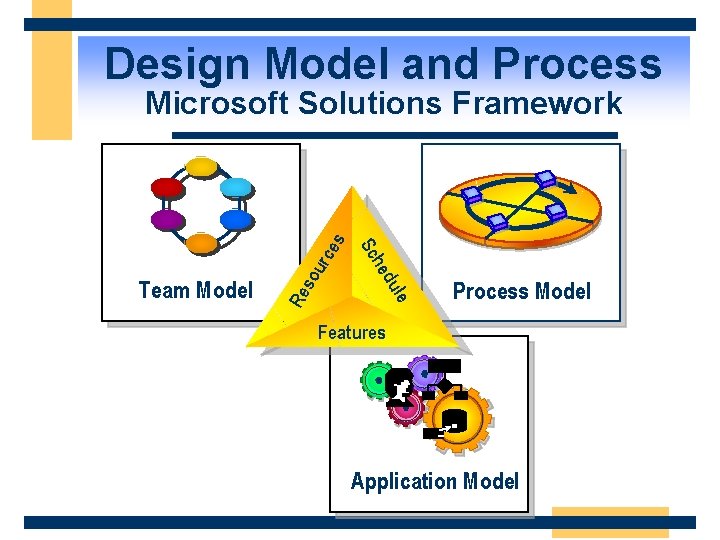
Design Model and Process urc so le du Re he Team Model Sc es Microsoft Solutions Framework Process Model Features Application Model

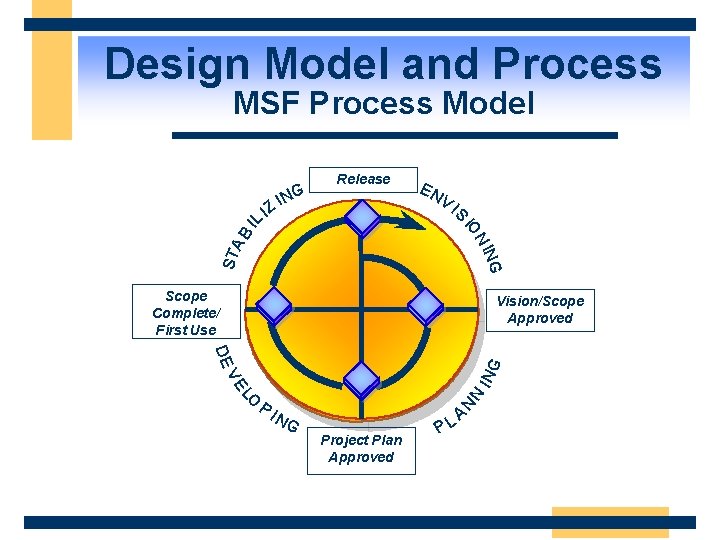
Design Model and Process MSF Process Model Release EN V I S ING STA BI N IO LI NG I Z Scope Complete/ First Use Vision/Scope Approved NG N LO N VE IN G DE PI Project Plan Approved PL A

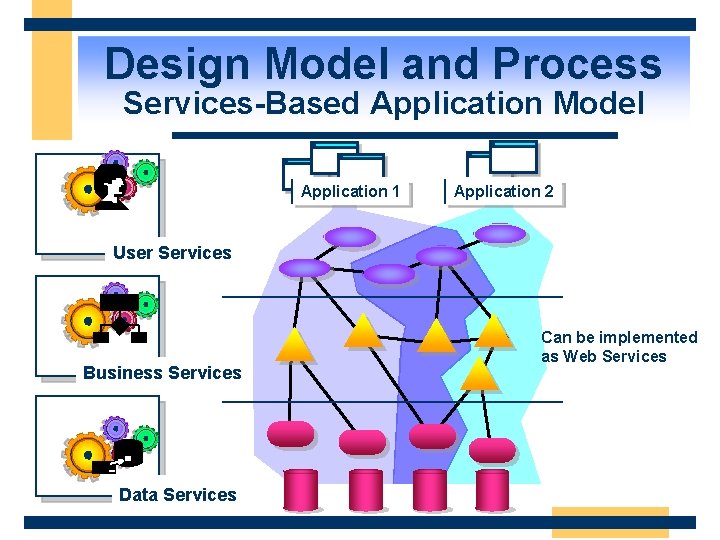
Design Model and Process Services-Based Application Model Application 1 Application 2 User Services Business Services Data Services Can be implemented as Web Services

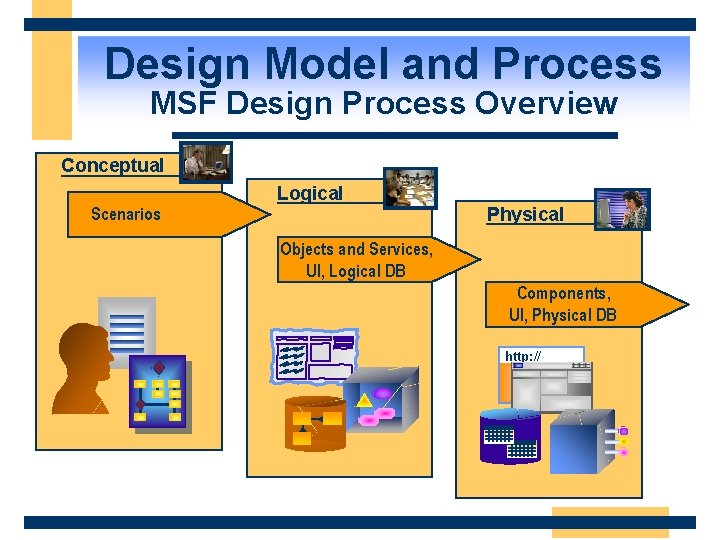
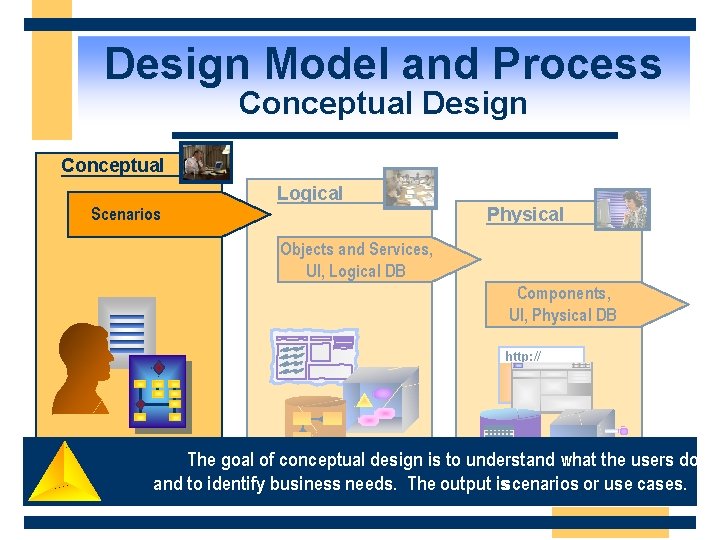
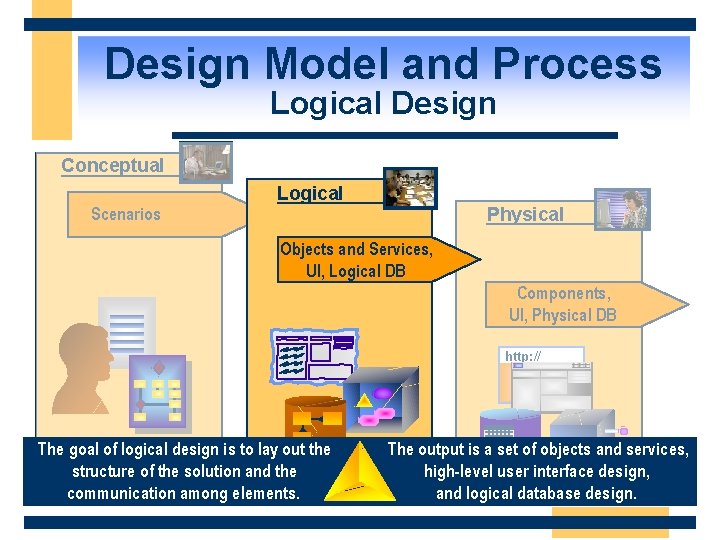
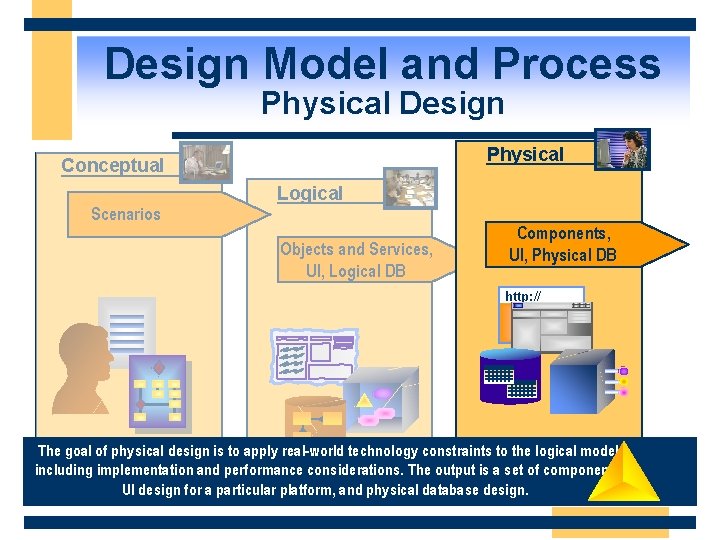
Design Model and Process MSF Design Process Overview Conceptual Logical Physical Scenarios Objects and Services, UI, Logical DB Components, UI, Physical DB http: //

Design Model and Process Conceptual Design Conceptual Logical Physical Scenarios Objects and Services, UI, Logical DB Components, UI, Physical DB http: // The goal of conceptual design is to understand what the users do and to identify business needs. The output isscenarios or use cases.

Design Model and Process Logical Design Conceptual Logical Physical Scenarios Objects and Services, UI, Logical DB Components, UI, Physical DB http: // The goal of logical design is to lay out the structure of the solution and the communication among elements. The output is a set of objects and services, high-level user interface design, and logical database design.

Design Model and Process Conceptual Physical Design Physical Conceptual Logical Scenarios Objects and Services, UI, Logical DB Components, UI, Physical DB http: // The goal of physical design is to apply real-world technology constraints to the logical model, including implementation and performance considerations. The output is a set of components, UI design for a particular platform, and physical database design.

Design Model and Process Design Principles w Understand solve the business problem w Communicate effectively with users and project teams w Design based on a modular approach n n n Consistent Distributable (Web-centric) Implementation language-independent Flexible Reusable Reliable w Balance innovation and discipline through each iteration w Pay attention to the Enterprise Architecture and Infrastructure

Design Model and Process Design Principles w Object Stereotypes Entity Service (Control) Boundary (Interface) w Design Patterns n E. g. Factory, Singleton, Proxy, Flyweight, Iterator, Façade, Memento, Adaptor

Agenda w w w Design Model and Process. NET System Architecture. NET Design Patterns Security Scalability Availability

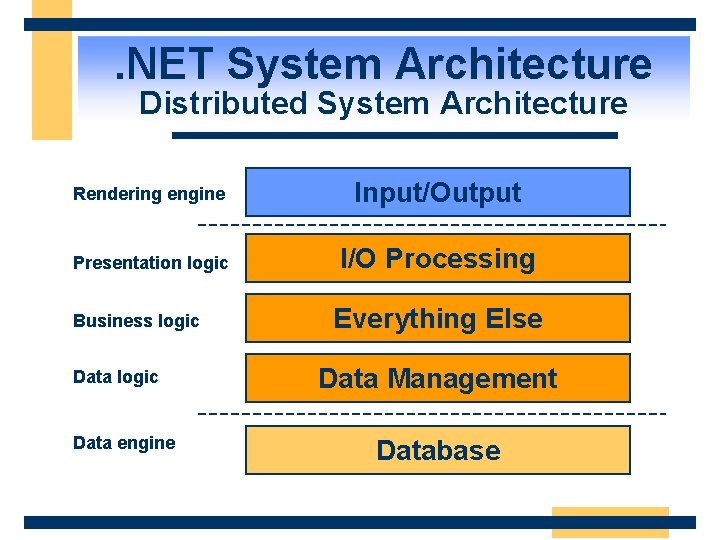
. NET System Architecture Distributed System Architecture Rendering engine Input/Output Presentation logic I/O Processing Business logic Data engine Everything Else Data Management Database

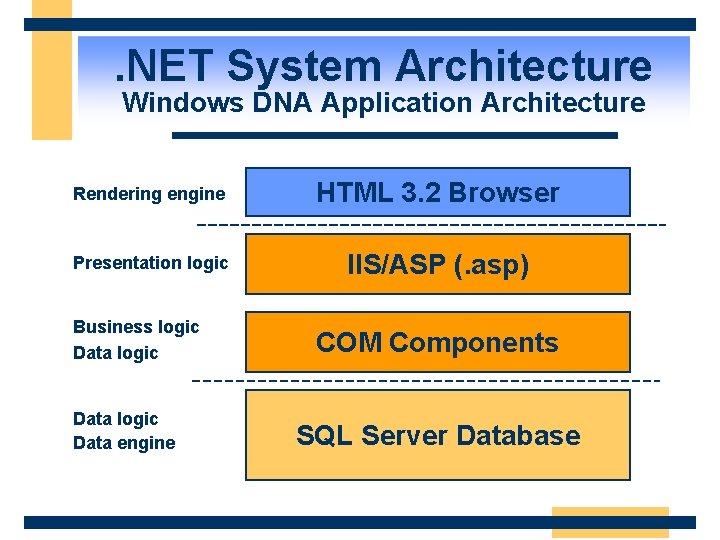
. NET System Architecture Windows DNA Application Architecture Rendering engine HTML 3. 2 Browser Presentation logic IIS/ASP (. asp) Business logic Data engine COM Components SQL Server Database

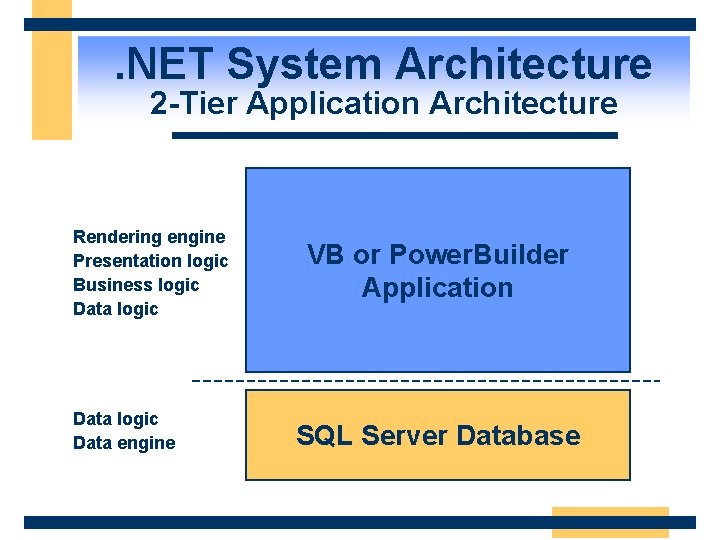
. NET System Architecture 2 -Tier Application Architecture Rendering engine Presentation logic Business logic Data engine VB or Power. Builder Application SQL Server Database

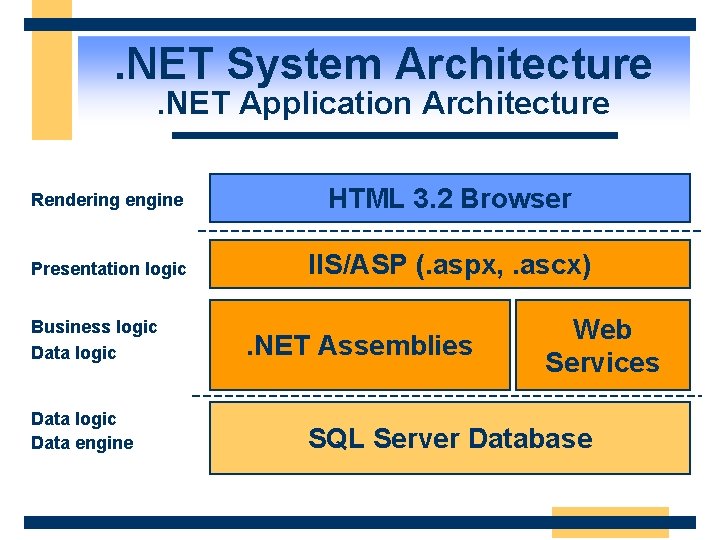
. NET System Architecture. NET Application Architecture Rendering engine HTML 3. 2 Browser Presentation logic IIS/ASP (. aspx, . ascx) Business logic Data engine . NET Assemblies Web Services SQL Server Database

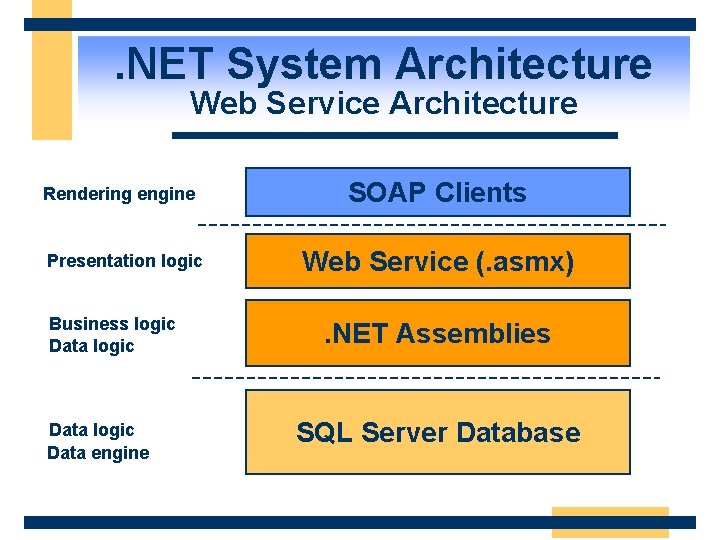
. NET System Architecture Web Service Architecture Rendering engine Presentation logic Business logic Data engine SOAP Clients Web Service (. asmx). NET Assemblies SQL Server Database

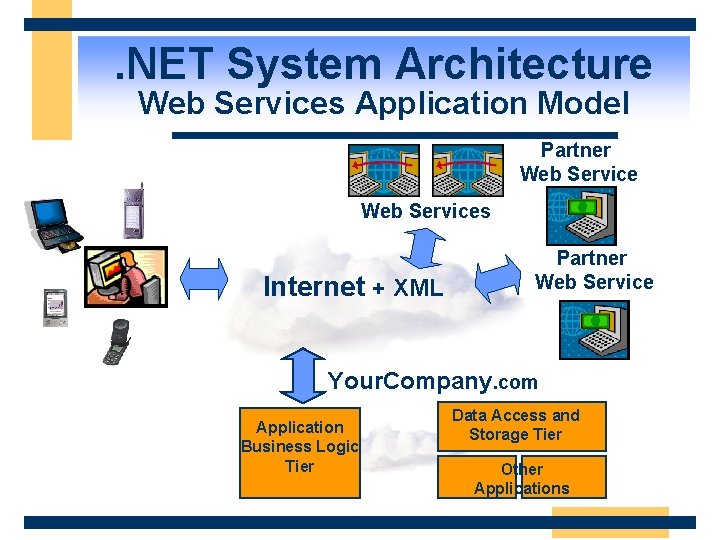
. NET System Architecture Web Services Application Model Partner Web Services Internet + XML Partner Web Service Your. Company. com Application Business Logic Tier Data Access and Storage Tier Other Applications

Agenda w w w Design Model and Process. NET System Architecture. NET Design Patterns Security Scalability Availability

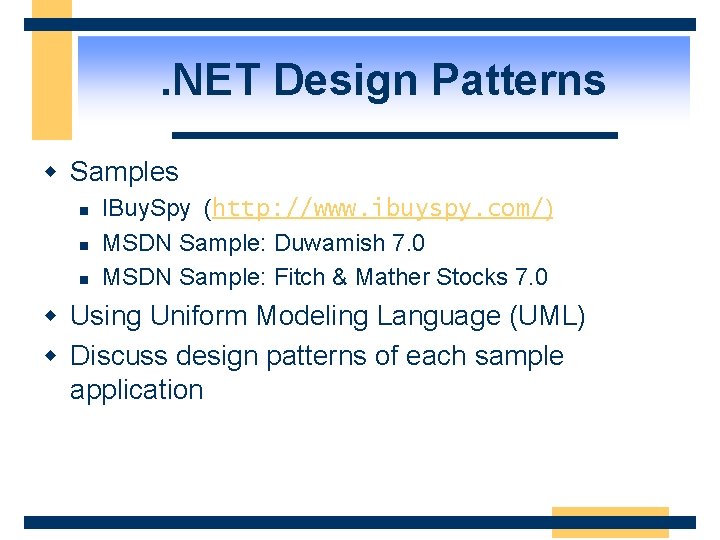
. NET Design Patterns w Samples n n n IBuy. Spy (http: //www. ibuyspy. com/) MSDN Sample: Duwamish 7. 0 MSDN Sample: Fitch & Mather Stocks 7. 0 w Using Uniform Modeling Language (UML) w Discuss design patterns of each sample application

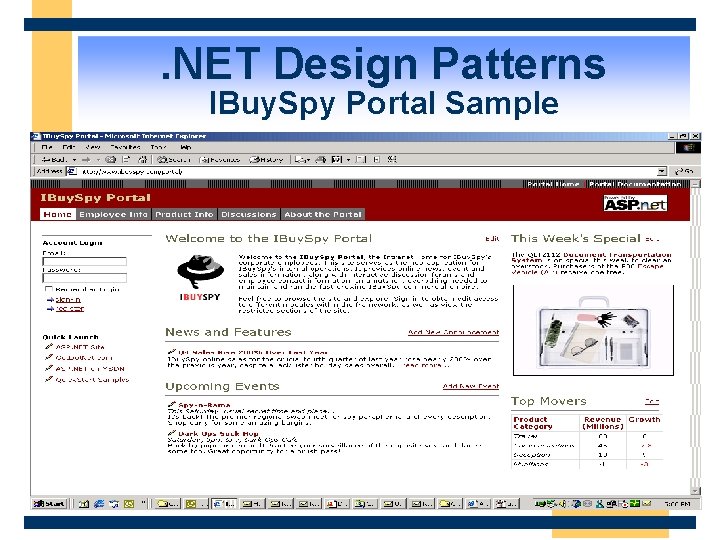
. NET Design Patterns IBuy. Spy Portal Sample

. NET Design Patterns IBuy. Spy Design Patterns w Clean code/HTML content separation using server controls w Pages that are constructed from dynamically-loaded User Controls w Configurable output caching of portal page regions w Modular site layout defined by XML configuration file

. NET Design Patterns IBuy. Spy Design Patterns w XML serialization that maps XML config file to custom config classes w Cached config settings automatically reloaded when file changes w Role-based security to control user access to portal content

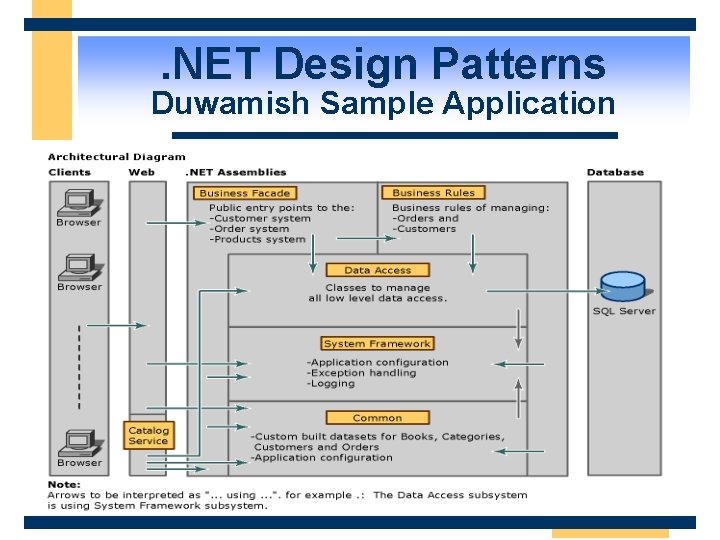
. NET Design Patterns Duwamish Sample Application

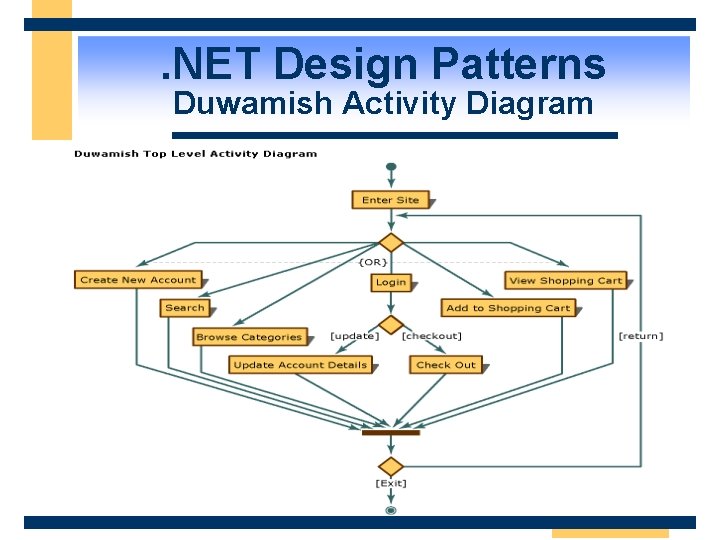
. NET Design Patterns Duwamish Activity Diagram

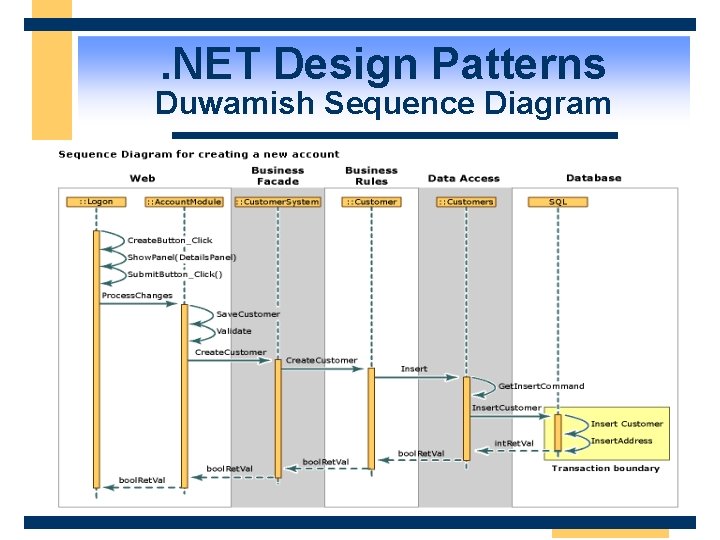
. NET Design Patterns Duwamish Sequence Diagram

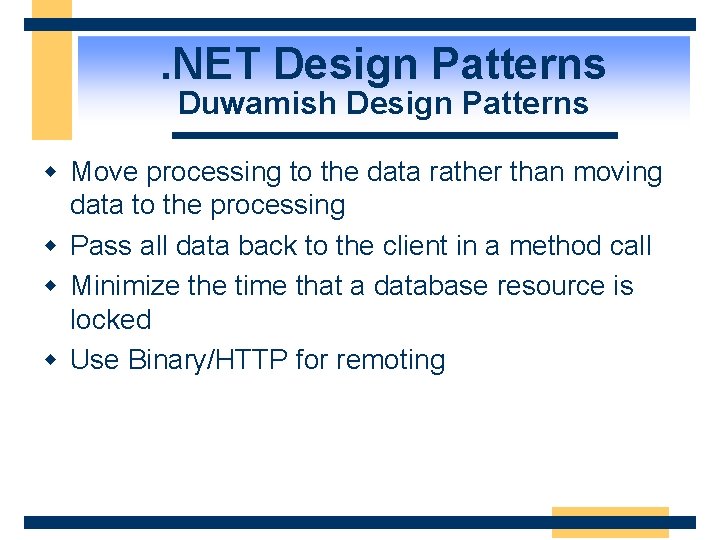
. NET Design Patterns Duwamish Design Patterns w Move processing to the data rather than moving data to the processing w Pass all data back to the client in a method call w Minimize the time that a database resource is locked w Use Binary/HTTP for remoting

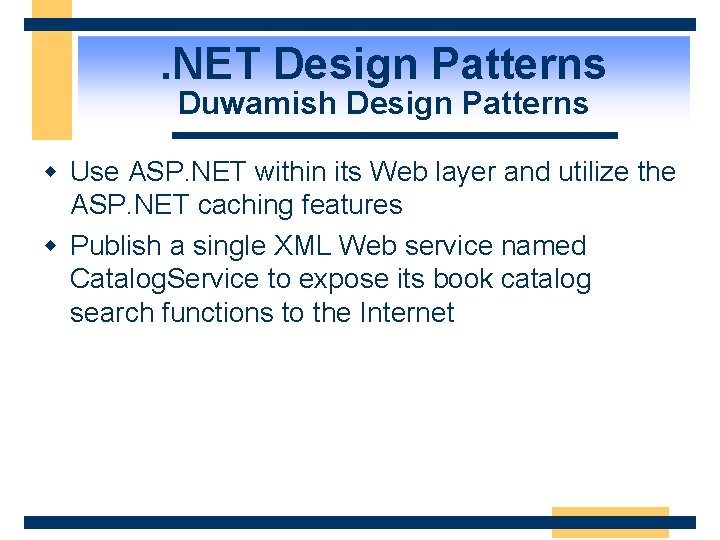
. NET Design Patterns Duwamish Design Patterns w Use ASP. NET within its Web layer and utilize the ASP. NET caching features w Publish a single XML Web service named Catalog. Service to expose its book catalog search functions to the Internet

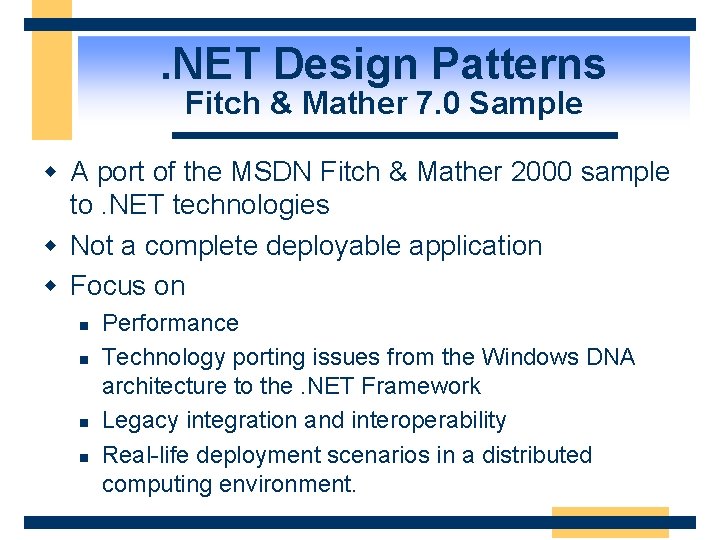
. NET Design Patterns Fitch & Mather 7. 0 Sample w A port of the MSDN Fitch & Mather 2000 sample to. NET technologies w Not a complete deployable application w Focus on n n Performance Technology porting issues from the Windows DNA architecture to the. NET Framework Legacy integration and interoperability Real-life deployment scenarios in a distributed computing environment.

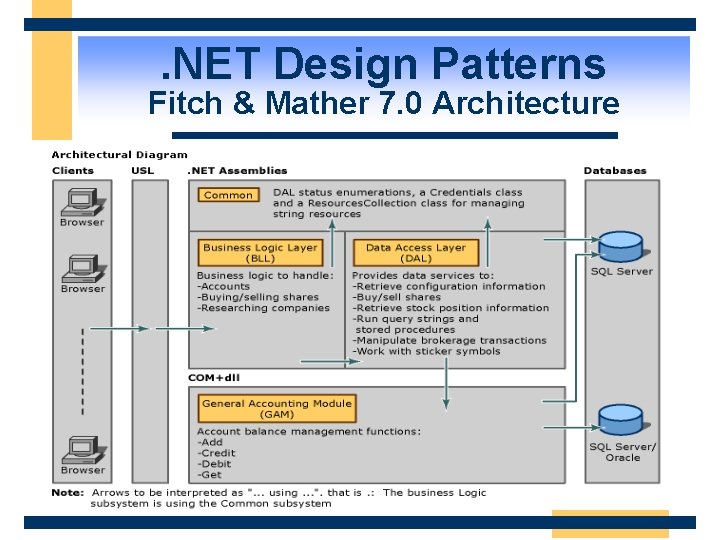
. NET Design Patterns Fitch & Mather 7. 0 Architecture

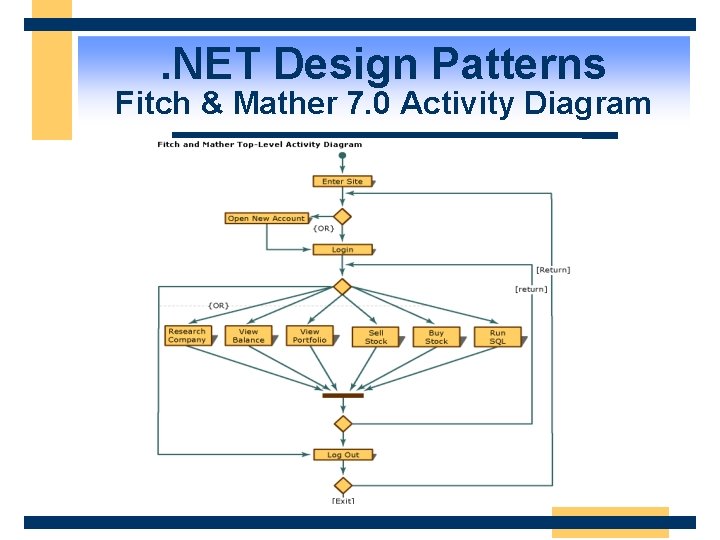
. NET Design Patterns Fitch & Mather 7. 0 Activity Diagram

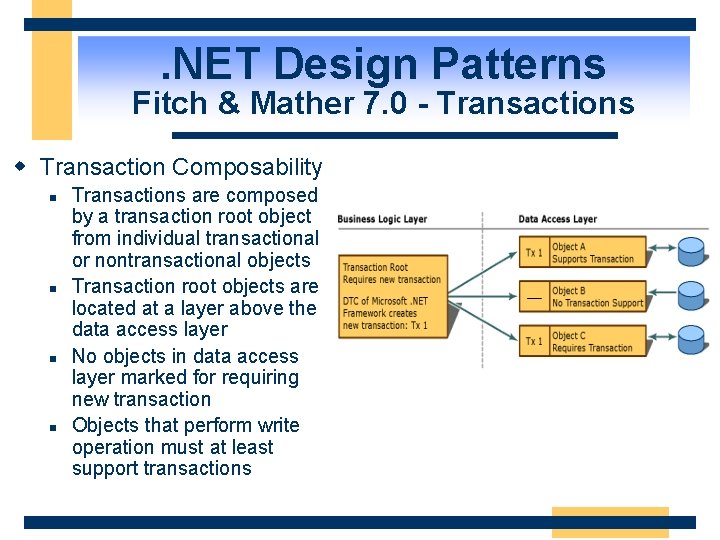
. NET Design Patterns Fitch & Mather 7. 0 - Transactions w Transaction Composability n n Transactions are composed by a transaction root object from individual transactional or nontransactional objects Transaction root objects are located at a layer above the data access layer No objects in data access layer marked for requiring new transaction Objects that perform write operation must at least support transactions

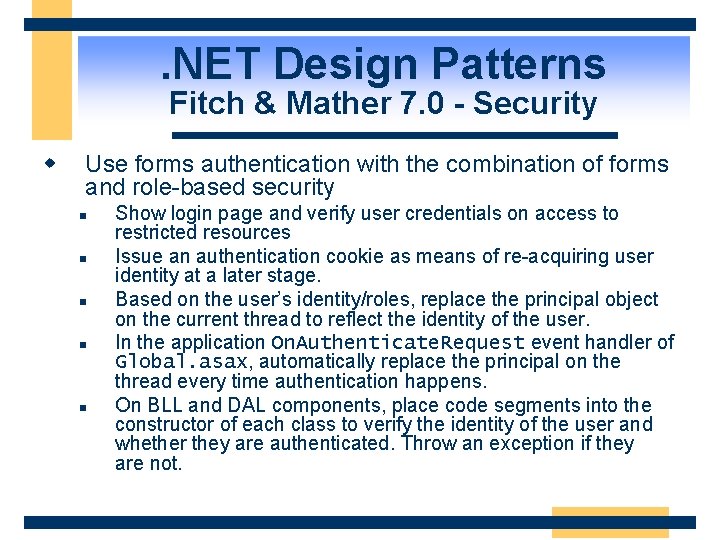
. NET Design Patterns Fitch & Mather 7. 0 - Security w Use forms authentication with the combination of forms and role-based security n n n Show login page and verify user credentials on access to restricted resources Issue an authentication cookie as means of re-acquiring user identity at a later stage. Based on the user’s identity/roles, replace the principal object on the current thread to reflect the identity of the user. In the application On. Authenticate. Request event handler of Global. asax, automatically replace the principal on the thread every time authentication happens. On BLL and DAL components, place code segments into the constructor of each class to verify the identity of the user and whether they are authenticated. Throw an exception if they are not.

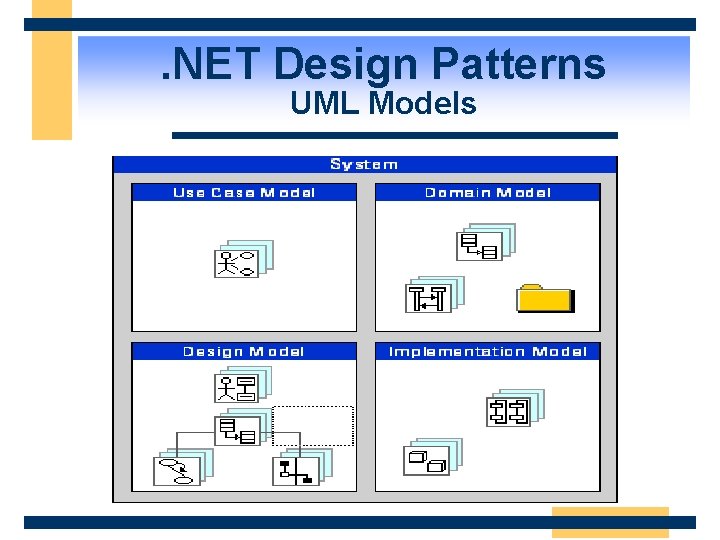
. NET Design Patterns UML Models

Agenda w w w Design Model and Process. NET System Architecture. NET Design Patterns Security Scalability Availability

Security Overview w Security is APAIN: n n n Authentication Who‘s there? Privacy No eavesdroppers Authorization What are you allowed to do? Integrity. Did the data get changed? Nonrepudiation Keep your promises w As always: understand the requirements n n E. g. Search vs. bank account vs. news Do you just need personalization?

Security Questions to Ask w Authentication n n How does the user provide their credentials? Where are credentials stored? l Temporary or persistent

Security Authentication Approaches w IIS/Windows n Basic, Digest, NTLM, Kerberos, Certificates w ASP. NET n n Windows Forms-based (cookie) authentication Microsoft Passport authentication Custom authentication

Security Forms-Based Authentication w Easy to implement n w w ASP. NET provides redirection Custom Login UI (no popup dialogs) Custom credential verification Custom application roles Support for advanced usage n n Application defined data Control over cookie lifetime, paths

Security Authorization Strategies w ASP. NET n n n Windows Security & ACLs URL Authorization Custom Authorization w All applications n n Declarative Method Authorization Explicit Authorization

Agenda w w w Design Model and Process. NET System Architecture. NET Design Patterns Security Scalability Availability

Scalability How Do You Handle Success? …

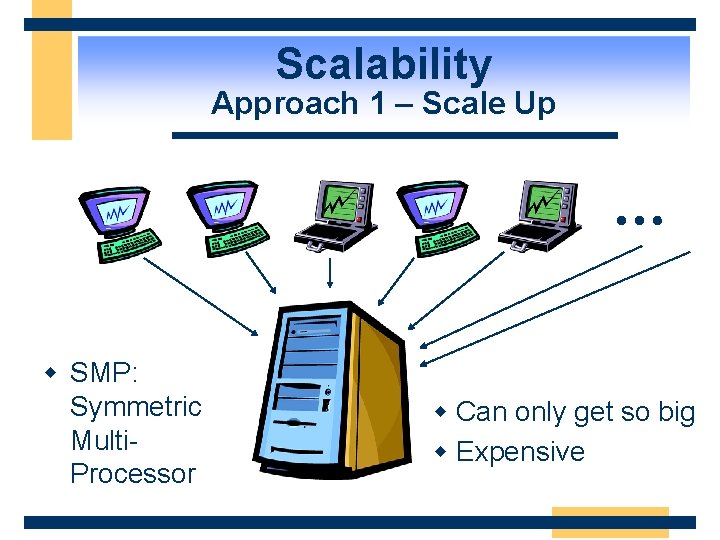
Scalability Approach 1 – Scale Up … w SMP: Symmetric Multi. Processor w Can only get so big w Expensive

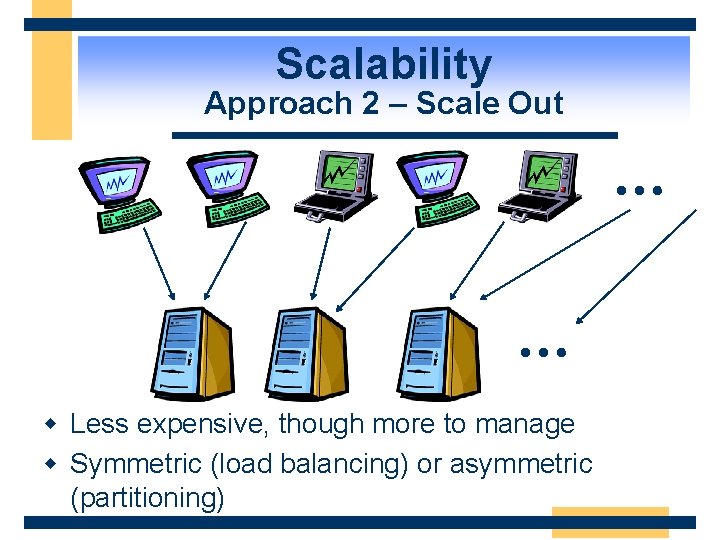
Scalability Approach 2 – Scale Out … … w Less expensive, though more to manage w Symmetric (load balancing) or asymmetric (partitioning)

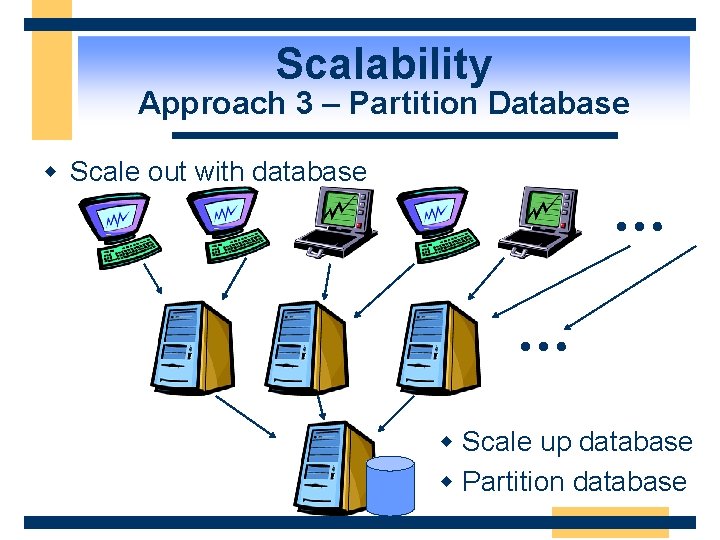
Scalability Approach 3 – Partition Database w Scale out with database … … w Scale up database w Partition database

Scalability Design for Scalability w Design a stateless application if possible n n w w w Use a database for state management Run on a cluster of Web servers Use caching or offline content generation Partition the database tier or the Web tier Use stored procedures Use transactions intelligently Use asynchronous programming techniques Benchmark your application – performance measurement and tuning

Scalability Use a Database for State Management w Design your Web application to run on a cluster of Web servers n Shared nothing, stateless w This means you must manage user session state somewhere other than the Web server w Use a database

Scalability Single Stateless Application Server w A single stateless server running your application code Application Code

Scalability Multiple Identical Stateless Application Servers w The application code is cloned across a set of identical servers Application Code

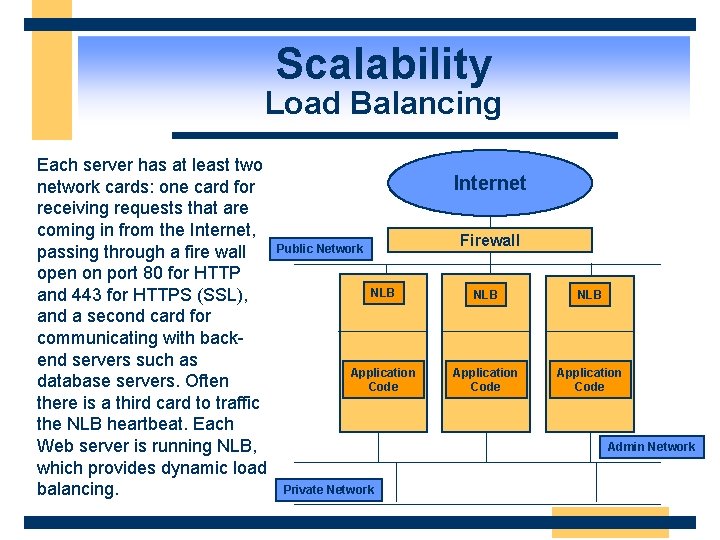
Scalability Load Balancing Each server has at least two network cards: one card for receiving requests that are coming in from the Internet, passing through a fire wall open on port 80 for HTTP and 443 for HTTPS (SSL), and a second card for communicating with backend servers such as database servers. Often there is a third card to traffic the NLB heartbeat. Each Web server is running NLB, which provides dynamic load balancing. Internet Firewall Public Network NLB NLB Application Code Admin Network Private Network

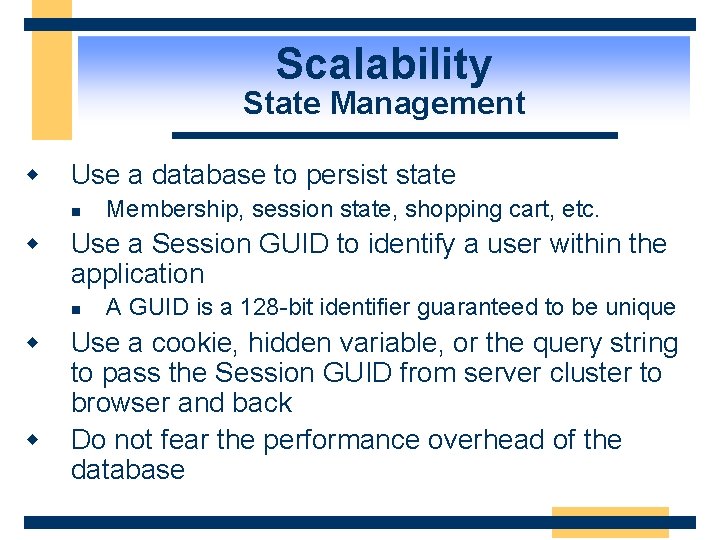
Scalability State Management w Use a database to persist state n w Use a Session GUID to identify a user within the application n w w Membership, session state, shopping cart, etc. A GUID is a 128 -bit identifier guaranteed to be unique Use a cookie, hidden variable, or the query string to pass the Session GUID from server cluster to browser and back Do not fear the performance overhead of the database

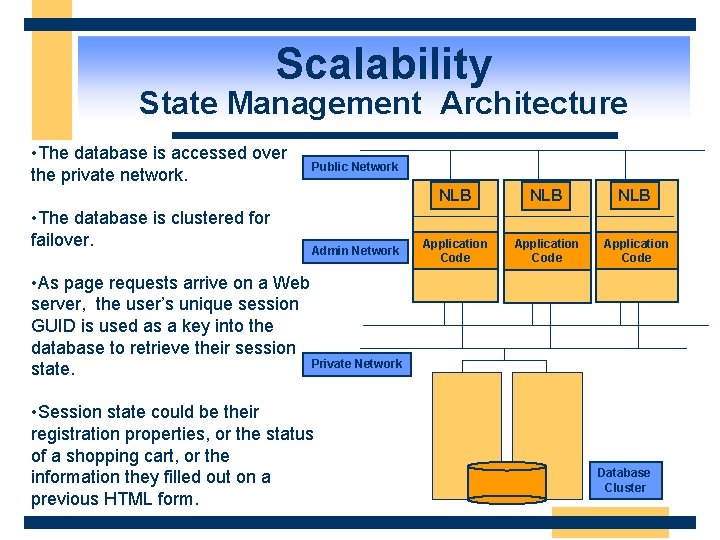
Scalability State Management Architecture • The database is accessed over the private network. • The database is clustered for failover. Public Network Admin Network NLB NLB Application Code • As page requests arrive on a Web server, the user’s unique session GUID is used as a key into the database to retrieve their session Private Network state. • Session state could be their registration properties, or the status of a shopping cart, or the information they filled out on a previous HTML form. Database Cluster

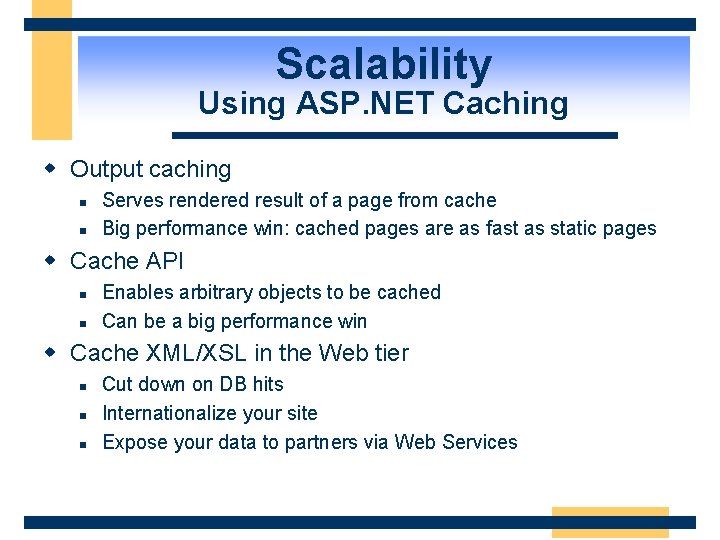
Scalability Using ASP. NET Caching w Output caching n n Serves rendered result of a page from cache Big performance win: cached pages are as fast as static pages w Cache API n n Enables arbitrary objects to be cached Can be a big performance win w Cache XML/XSL in the Web tier n n n Cut down on DB hits Internationalize your site Expose your data to partners via Web Services

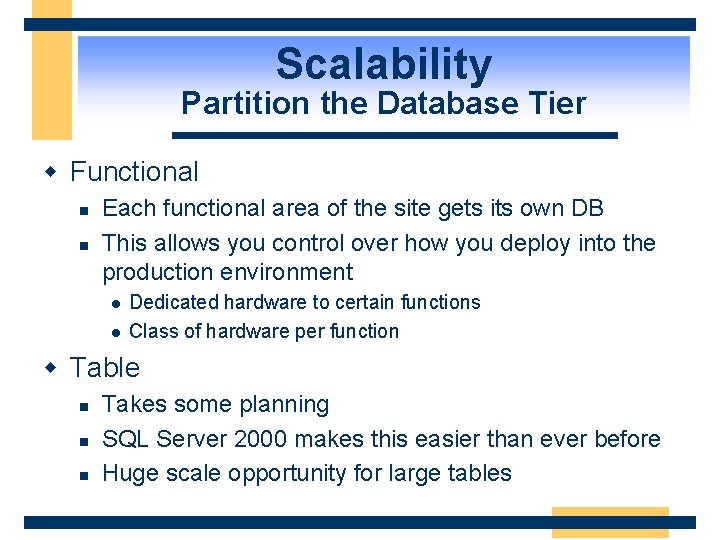
Scalability Partition the Database Tier w Functional n n Each functional area of the site gets its own DB This allows you control over how you deploy into the production environment l l Dedicated hardware to certain functions Class of hardware per function w Table n n n Takes some planning SQL Server 2000 makes this easier than ever before Huge scale opportunity for large tables

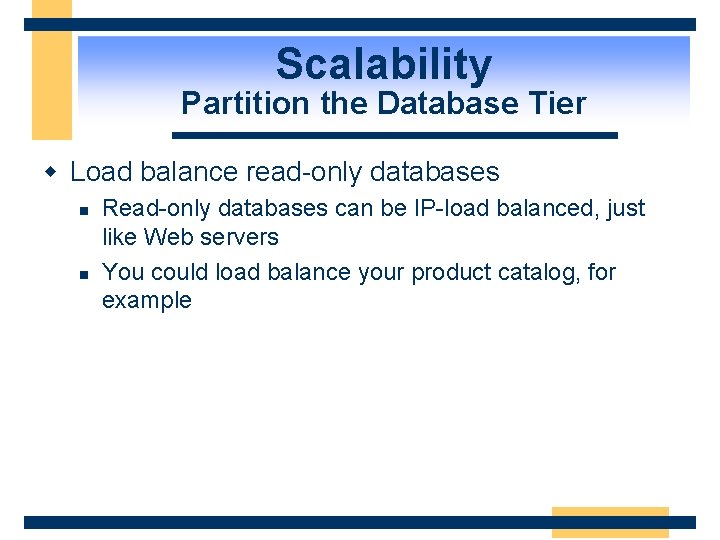
Scalability Partition the Database Tier w Load balance read-only databases n n Read-only databases can be IP-load balanced, just like Web servers You could load balance your product catalog, for example

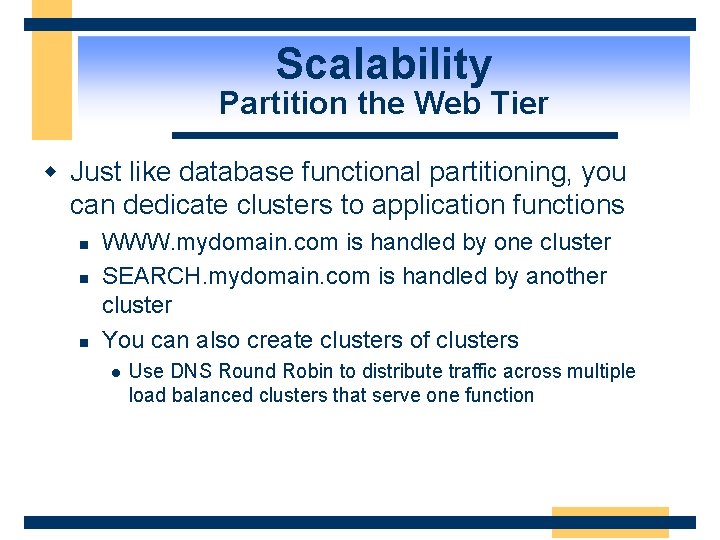
Scalability Partition the Web Tier w Just like database functional partitioning, you can dedicate clusters to application functions n n n WWW. mydomain. com is handled by one cluster SEARCH. mydomain. com is handled by another cluster You can also create clusters of clusters l Use DNS Round Robin to distribute traffic across multiple load balanced clusters that serve one function

Scalability Partition the Web Tier w Use DNS Host names or hardware solutions to distribute traffic to dedicated clusters w Once you have a stateless application, this is how you achieve huge scale n Scalability throttling with inexpensive hardware

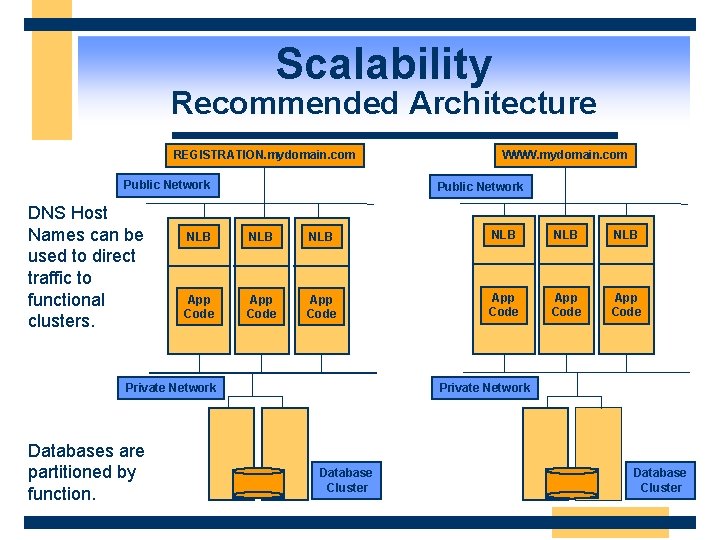
Scalability Recommended Architecture REGISTRATION. mydomain. com Public Network DNS Host Names can be used to direct traffic to functional clusters. Public Network NLB NLB NLB App Code App Code Private Network Databases are partitioned by function. WWW. mydomain. com Private Network Database Cluster

Scalability Benefits of Partitioning w More control over traffic flow through the application n Users who are searching or registering are moved off of the WWW cluster to keep the response time of the WWW cluster snappy w Application and server tuning can be different for each function n Search servers may have more memory, more CPUs than the servers handling WWW

Scalability Benefits of Partitioning w Different content management techniques can be used on different functions n n WWW may be primarily static content or dynamically generated offline. WWW may use XML and XSL for high performance UI formatting and internationalization Registration requires real-time database access and custom code w Administration of the clusters can be handled separately w Database partitioning gives you scale-out capabilities at the database tier

Scalability Using Stored Procedures w There is a real performance benefit to stored procedures n Compiled code in the database w DBA can tune stored procedures n Can’t tune embedded SQL w Good separation (API) between table structure and application code w Tradeoff is database portability

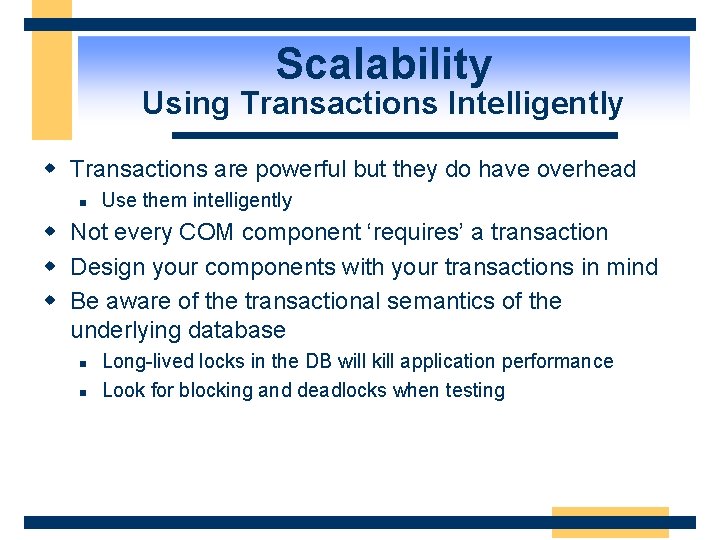
Scalability Using Transactions Intelligently w Transactions are powerful but they do have overhead n Use them intelligently w Not every COM component ‘requires’ a transaction w Design your components with your transactions in mind w Be aware of the transactional semantics of the underlying database n n Long-lived locks in the DB will kill application performance Look for blocking and deadlocks when testing

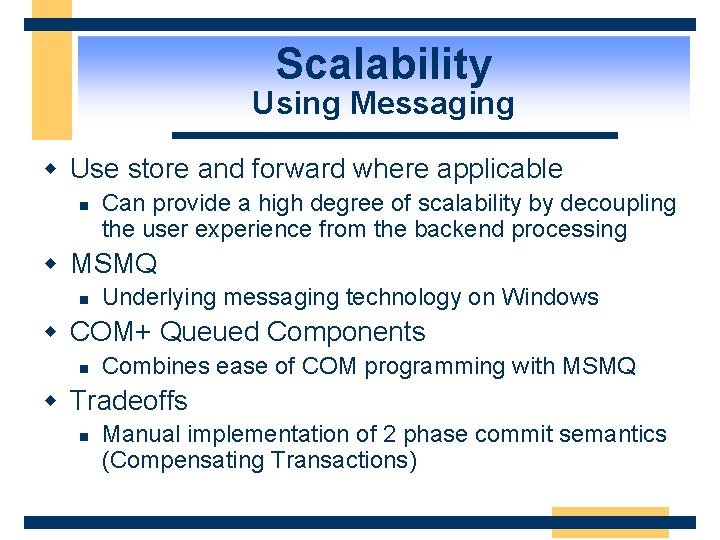
Scalability Using Messaging w Use store and forward where applicable n Can provide a high degree of scalability by decoupling the user experience from the backend processing w MSMQ n Underlying messaging technology on Windows w COM+ Queued Components n Combines ease of COM programming with MSMQ w Tradeoffs n Manual implementation of 2 phase commit semantics (Compensating Transactions)

Scalability Performance Tuning w Performance Tuning is the process by which you measure individual operations on your site n n n Still a bit of a black art Need to measure for detail but analyze with a holistic view of the system Database performance is key; focus there first w Know your tools n n n Perf. Mon WAST SQL Server Profiler SQL Server Index Tuning Wizard SQL Server Query Analyzer

Scalability Framework/CLR Best Practices w Enable Web Garden: run applications in multiple worker processes (with processor affinity) w Use Early Binding: Late Binding requires work at runtime w “Pre-JIT” to start up faster (available in beta 2) w Make chunky and not chatty calls w Implement Dispose method on the object that cleans up your resources and release the reference (set to null) once you are done

Scalability Framework/CLR Best Practices w Use value type for small data w Do not cache strings or arrays length: Strings are immutable w For best inlining performance n n Minimize the use of virtual methods Use sealed types if possible

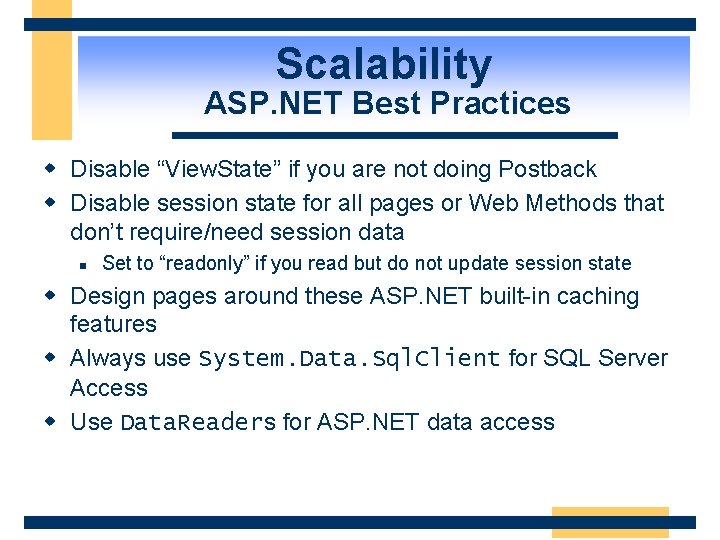
Scalability ASP. NET Best Practices w Disable “View. State” if you are not doing Postback w Disable session state for all pages or Web Methods that don’t require/need session data n Set to “readonly” if you read but do not update session state w Design pages around these ASP. NET built-in caching features w Always use System. Data. Sql. Client for SQL Server Access w Use Data. Readers for ASP. NET data access

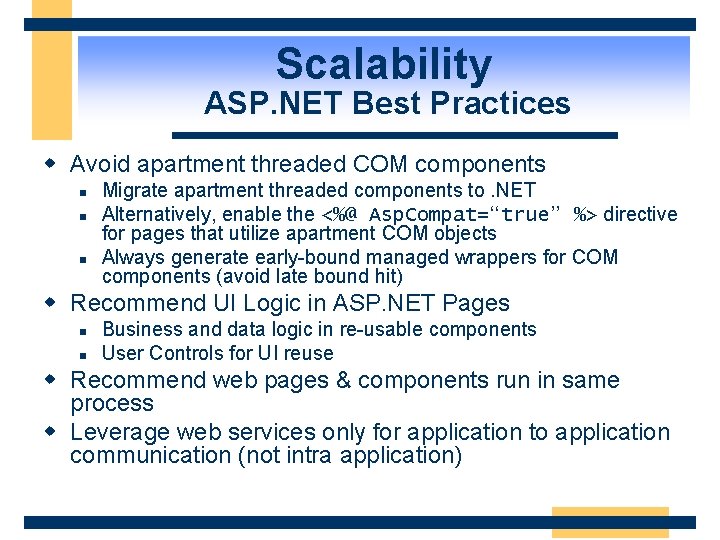
Scalability ASP. NET Best Practices w Avoid apartment threaded COM components n n n Migrate apartment threaded components to. NET Alternatively, enable the <%@ Asp. Compat=“true” %> directive for pages that utilize apartment COM objects Always generate early-bound managed wrappers for COM components (avoid late bound hit) w Recommend UI Logic in ASP. NET Pages n n Business and data logic in re-usable components User Controls for UI reuse w Recommend web pages & components run in same process w Leverage web services only for application to application communication (not intra application)

Agenda w w w Design Model and Process. NET System Architecture. NET Design Patterns Security Scalability Availability

Availability What Is High Availability? w The question you must ask yourself is: n How much downtime can my organization afford without losing productivity, profits, sales, etc. ? w It is a combination of people, process, AND technology

Availability High Availability Is Not … w Only a technology solution w A scalability solution

Availability How Much Availability Do I Need? w Understand the business need w Five nines (99. 999% uptime) is 5 minutes of downtime per year w Formulas for downtime: n n n % Uptime/year = (8760 - # of total hours down per year)/8760 % Uptime/month = ((24 * # of days in the month) - # of total hours down in that calendar month)/(24 * # of days in the month) % Uptime/week = (168 - # of total hours down in that week)/168

Availability How Do I Achieve High Availability? w It’s deceptively simple … n n Plan and prepare Deploy systems to create redundancy – this is the key to high availability from a technology standpoint l n n Use more than one method – avoid a single point of failure Test, test Monitor on a continuous basis

Availability Basic Questions To Ask w Who is the end user? What do they expect in terms of availability and performance? w What type of activity is going to be done within the database (i. e. OLTP, DSS, etc. )? w Are there any budget considerations? w How much will not having HA hurt the business? Calculate how much downtime will actually cost.

Availability SQL Server 2000 HA Technology w Failover Clustering w Log Shipping w Replication

Availability SQL Failover Clustering w w w Feature of SQL Server 2000 Enterprise Edition Not a scalability solution Automatic failover Always the method to lead with Requires specialized hardware solutions

Availability Log Shipping w New feature of SQL Server 2000 Enterprise Edition w Concept has been in use for a long time n Transaction logs from a primary database are applied to a secondary database w Great primary or secondary method even if you can’t afford failover clustering

Availability Replication w Not the traditional method of High Availability – technology has been around for a long time w Sometimes better than log shipping for transactional consistency w Easy to replicate read-only data w Possibly more complex, additional resources w Uses for replication n n Reporting, read-only data, possibly updates Partitioned data

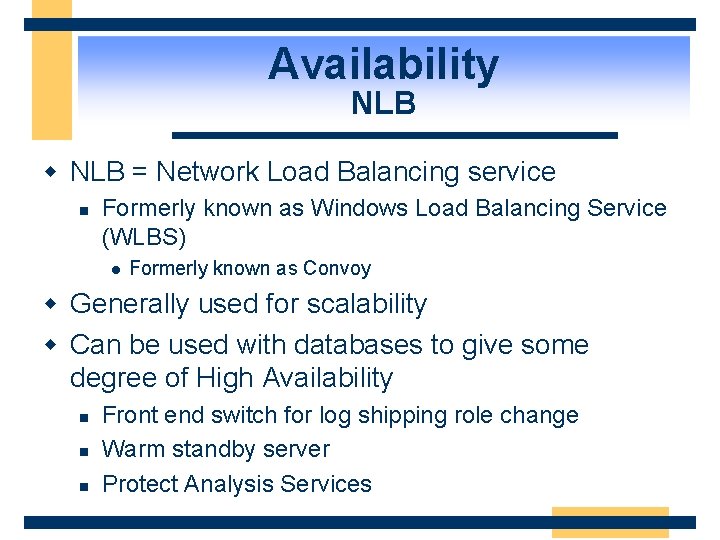
Availability NLB w NLB = Network Load Balancing service n Formerly known as Windows Load Balancing Service (WLBS) l Formerly known as Convoy w Generally used for scalability w Can be used with databases to give some degree of High Availability n n n Front end switch for log shipping role change Warm standby server Protect Analysis Services

Availability Design For High Availability w w Involve your programmers from the start Use versioning Use source control for all code – including SQL Take implementation into account – build programs with clean installs and uninstalls w Use the right technology

Availability Design For High Availability w Establish development, testing, staging environments, plus one that is an exact code copy of production (with current production data) w Take into account downtime, and how you will handle it – don’t leave it to IT w Read-only data should be cached if possible to speed up application performance

Availability Design For High Availability w Resolve any application issues that directly affect SQL Server n n n Locking/blocking Optimized queries/indexing schemes No ad hoc queries (If possible) Ensure no memory leaks or bad code will make an extended stored procedure unstable and cause availability problems Make sure statistics are up to date

Availability Improved Availability with ASP. NET w ASP. NET has been designed with assumption that failures will occur on systems n Designing for failure reduced fragility w Detects/recovers from common problems n Access violations, memory leaks, deadlocks w Preemptive cycling of applications n Time- and request-based settings w Net Result: Users should never think that an ASP. NET application is down or unavailable

Conclusion w Follow design process w Understand the architecture and design trade-offs w Study design patterns of other. NET applications w Build security into the overall design w Chose appropriate design patterns for scalability and availability

Resources w Microsoft Solutions Framework n http: //www. microsoft. com/business/micro soft/mcs/msf. asp w Microsoft Operations Framework n http: //www. microsoft. com/business/micro soft/mcs/mof. asp w General. NET information n http: //msdn. microsoft. com/net w. NET Framework SDK