NERC CIP Implementation Lessons Learned and Path Forward







- Slides: 21

NERC CIP Implementation – Lessons Learned and Path Forward Anfield Summit August 5 -6, 2015 By Jeremy Anderson Manager, Sales Engineering Nova. Tech, LLC

NERC CIP Implementation – Lessons Learned and Path Forward • NERC CIP Version 5: Quick Overview • The “Intermediate System” – Why Needed, and Design Suggestions • Reliable Broadband-based Networking System – Not an Option • The Importance of a Standards-based approach • Manual, Semi-Automatic or Fully Automatic Design?

Current NERC CIP Documents CIP– 002– 3 — Cyber Security— Critical Cyber Asset Identification CIP– 003– 3 — Cyber Security — Security Management Controls CIP– 004– 3 — Cyber Security — Personnel and Training CIP– 005– 3 — Cyber Security — Electronic Security Perimeter(s) CIP– 006– 3 — Cyber Security — Physical Security CIP– 007– 3 — Cyber Security — Systems Security Management CIP– 008– 3 — Cyber Security — Incident Reporting and Response Planning CIP– 009– 3 — Cyber Security — Recovery Plans for Critical Cyber Assets

NERC CIP Documents “Version 5” CIP– 002– 5 — Cyber Security — BES Cyber System Categorization CIP– 003– 5 — Cyber Security — Security Management Controls CIP– 004– 5 — Cyber Security — Personnel and Training CIP– 005– 5 — Cyber Security — Electronic Security Perimeter(s) CIP– 006– 5 — Cyber Security — Physical Security of BES Cyber Systems CIP– 007– 5 — Cyber Security — Systems Security Management CIP– 008– 5 — Cyber Security — Incident Reporting and Response Planning CIP– 009– 5 — Cyber Security — Recovery Plans for BES Cyber Systems (new) CIP– 010– 1 — Cyber Security — Configuration Change Mgmt. and Vulnerability Assessments (new) CIP– 011– 1 — Cyber Security — Information Protection (new) CIP– 014– 1 — Cyber Security — Physical Security

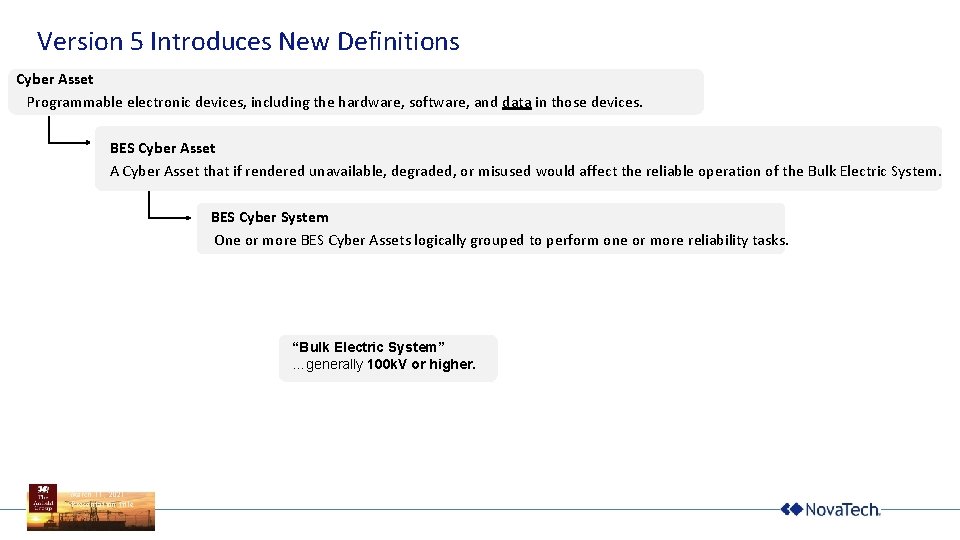
Version 5 Introduces New Definitions Cyber Asset Programmable electronic devices, including the hardware, software, and data in those devices. BES Cyber Asset A Cyber Asset that if rendered unavailable, degraded, or misused would affect the reliable operation of the Bulk Electric System. BES Cyber System One or more BES Cyber Assets logically grouped to perform one or more reliability tasks. “Bulk Electric System” …generally 100 k. V or higher. March 11, 2021 Presentation title

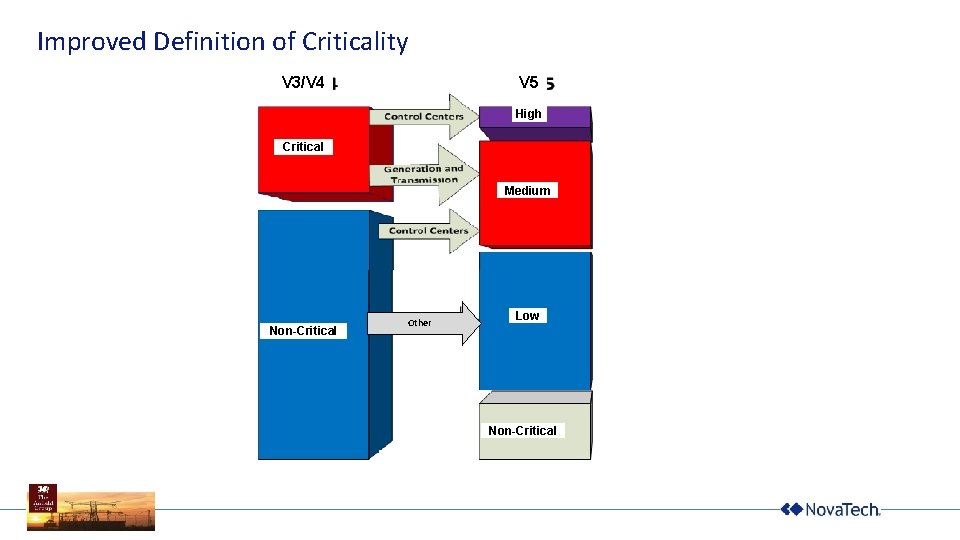
Improved Definition of Criticality V 5 V 3/V 4 High Critical Medium Non-Critical Other Low Non-Critical

Version 5 Expands Definition of “Applicable Systems” • Electronic Access Control or Monitoring Systems (EACMS) – Applies to each Electronic Access Control or Monitoring System associated with a referenced high impact BES Cyber System or medium impact BES Cyber System. Examples may include, but are not limited to, firewalls, authentication servers, and log monitoring and alerting systems. • Physical Access Control Systems (PACS) – Applies to each Physical Access Control System associated with a referenced high impact BES Cyber System or medium impact BES Cyber System with External Routable Connectivity. • Protected Cyber Assets (PCA)– Applies to each Protected Cyber Asset associated with a referenced high impact BES Cyber System or medium impact BES Cyber System

Other Significant Changes V 3/4 to V 5 • Must now use an “intermediate device” between User and Critical Asset • The complete exemption of Cyber Assets from applicability to the NERC CIP standards based on communication characteristics no longer applies. • Must remove/disable both unused “software ports” and unused “hardware points” • Improved definition for patching – Defines the source of the “patches” (also “hot fixes” and “updates”) – Provides better definition of “release date” and “availability date” – If installing the patch introduces more risk than the vulnerability represents, an alternate process is defined • Does not mandate anti-virus software • Requires security monitoring • …and more.

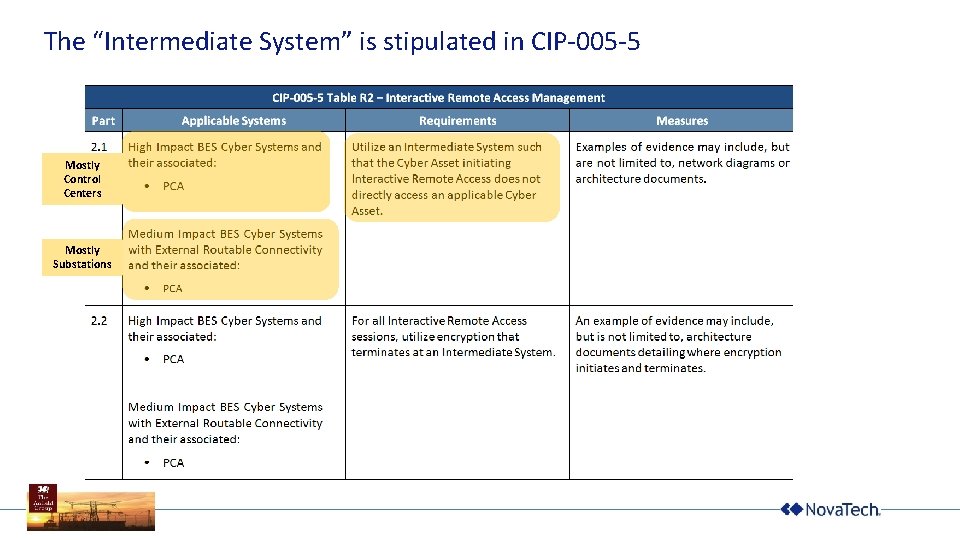
The “Intermediate System” is stipulated in CIP-005 -5 Mostly Control Centers Mostly Substations

What is Interactive Remote Access? • user-initiated access by a person employing a remote access client or other remote access technology using a routable protocol. Remote access originates from a Cyber Asset that is not an Intermediate System and not located within any of the Responsible Entity's Electronic Security Perimeter(s) or at a defined Electronic Access Point (EAP). Remote access may be initiated from: 1) Cyber Assets used or owned by the Responsible Entity, 2) Cyber Assets used or owned by employees, and 3) Cyber Assets used or owned by vendors, contractors, or consultants. Interactive remote access does not include system-to-system process communications.

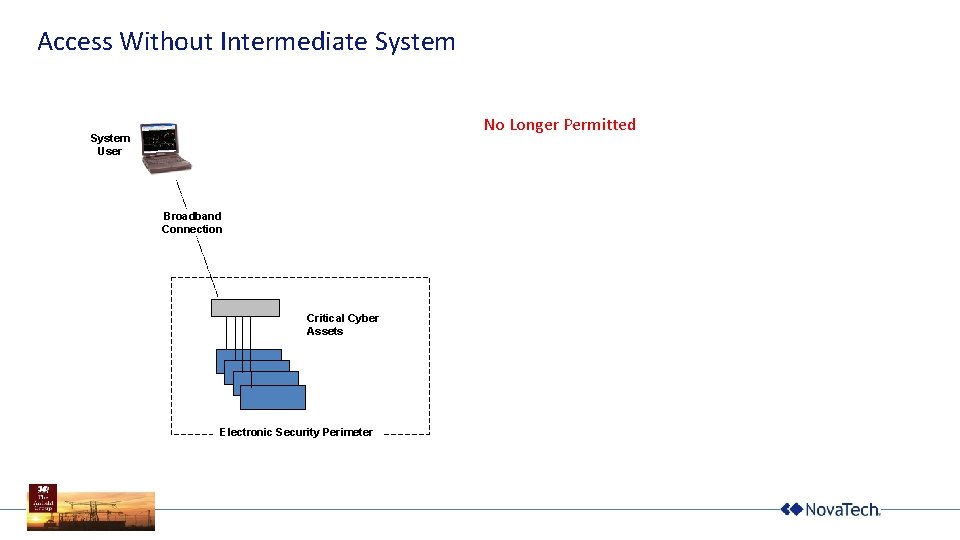
Access Without Intermediate System No Longer Permitted System User Broadband Connection Critical Cyber Assets Electronic Security Perimeter

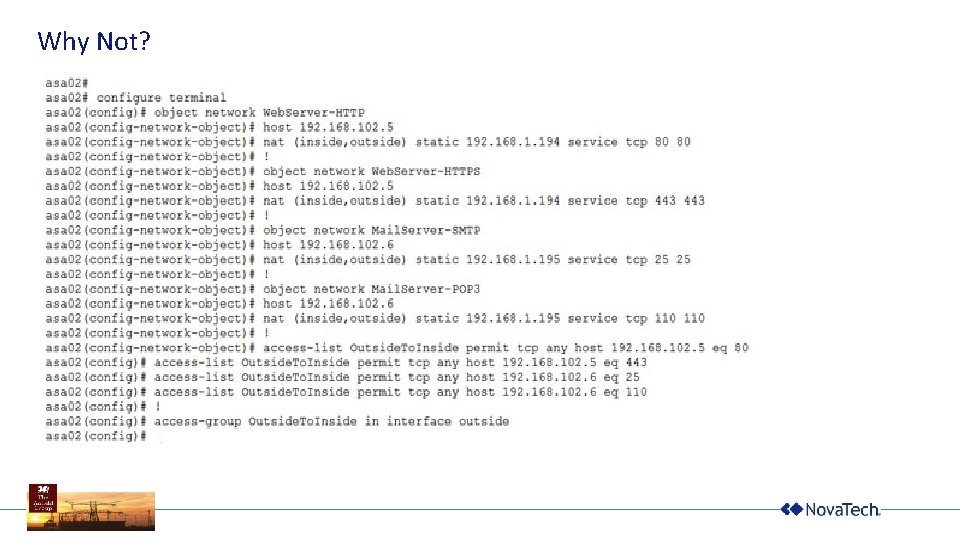
Why Not?

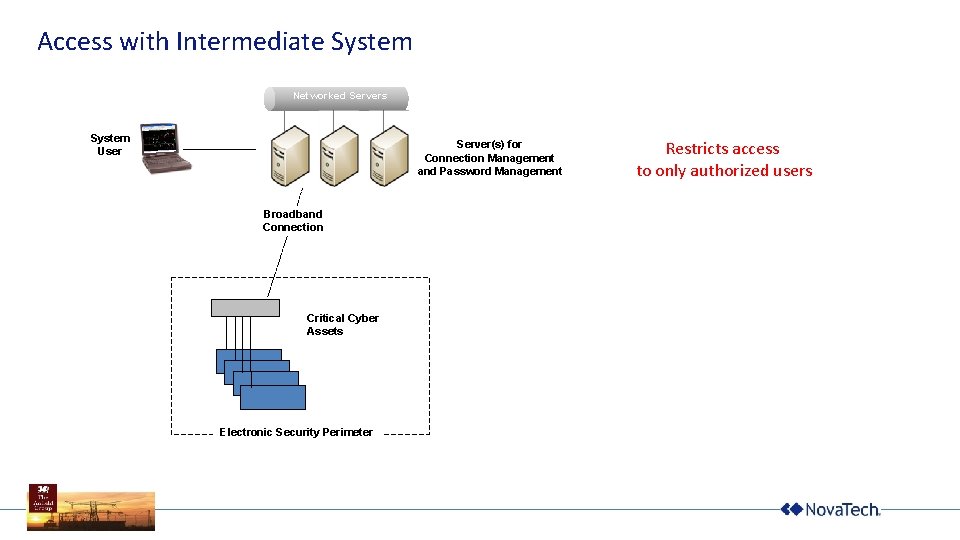
Access with Intermediate System Networked Servers Server(s) for Connection Management and Password Management System User Broadband Connection Critical Cyber Assets Electronic Security Perimeter Restricts access to only authorized users

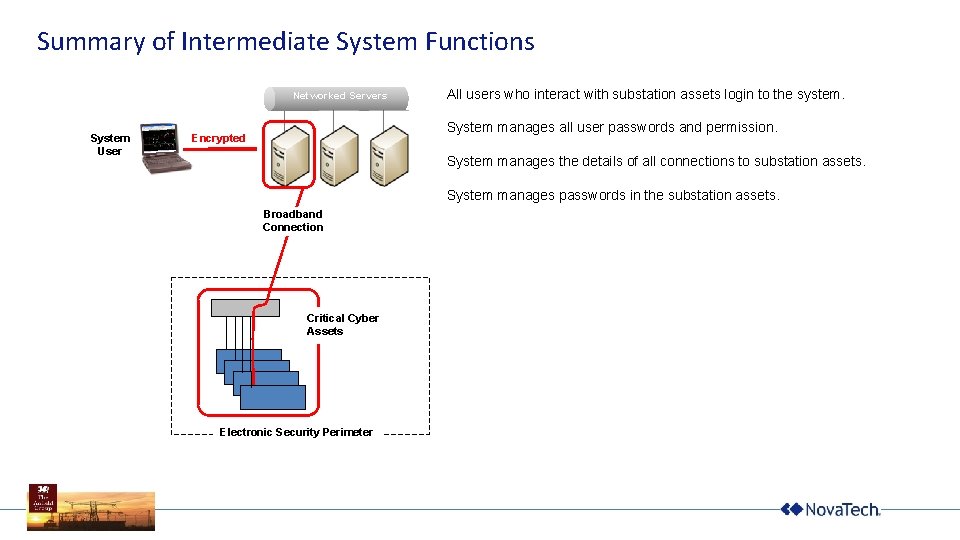
Summary of Intermediate System Functions Networked Servers System User All users who interact with substation assets login to the system. System manages all user passwords and permission. Encrypted System manages the details of all connections to substation assets. System manages passwords in the substation assets. Broadband Connection Critical Cyber Assets Electronic Security Perimeter

Reliable Broadband-based Networking System – Not an Option • Broadband is the solution for… …securely transferring files (e. g. for NERC CIP-10) …efficiently accessing syslog events …implementing LDAP and Active Directory for remote, centralized authentication …simplifying access and management of substation assets • Serial approaches are highly compromised for the above tasks and not a sustainable approach. • 99. 999% broadband uptime can be achieved

The Importance of a Standards-based Approach • The standards have been developed already, and they work: Secure Protocols: Security Event Access: System Management: Identity Management: SSH, SSL, TLS, HTTPS, SFTP Syslog SNMP Active Directory, LDAP, IPA • No need for Utility-specific, homegrown or proprietary approaches

Manual, Semi-Automatic or Fully Automatic Design? • Not all IEDs were designed to support automatic access of configurations • Only a few IEDs were designed to support automatic password changes • Semi-automatic approach may be best • Simpler can be better

Manual System • Very time and paperwork intensive • Very easy to forget something

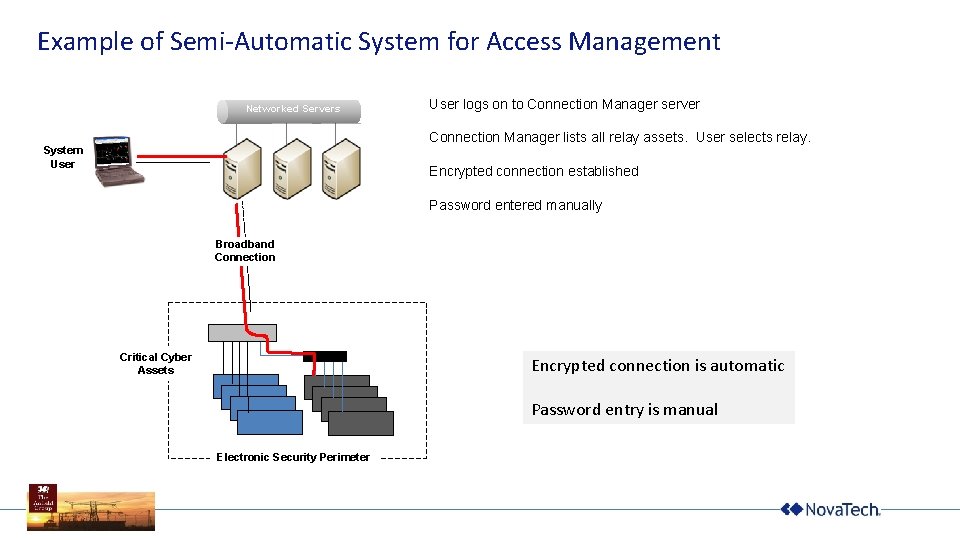
Example of Semi-Automatic System for Access Management Networked Servers User logs on to Connection Manager server Connection Manager lists all relay assets. User selects relay. System User Encrypted connection established Password entered manually Broadband Connection Critical Cyber Assets Encrypted connection is automatic Password entry is manual Electronic Security Perimeter

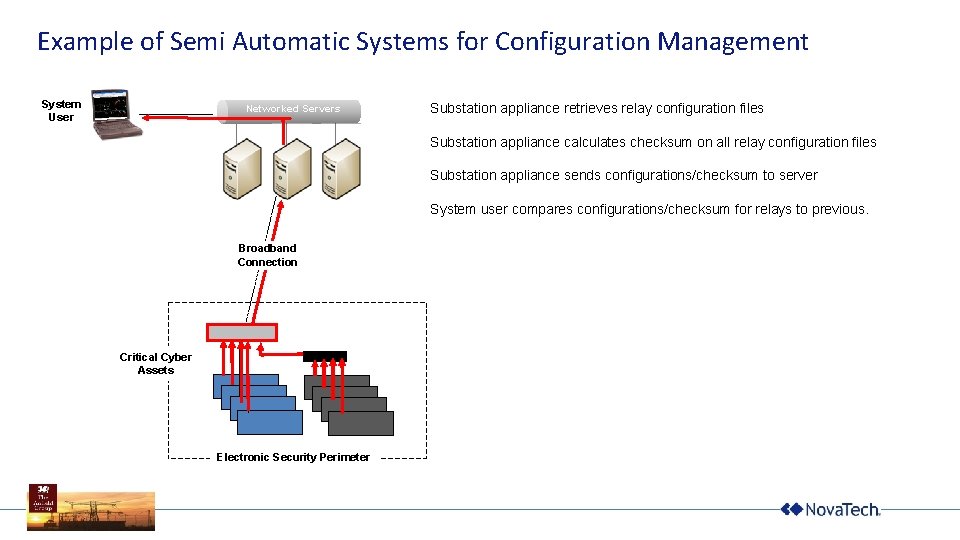
Example of Semi Automatic Systems for Configuration Management System User Networked Servers Substation appliance retrieves relay configuration files Substation appliance calculates checksum on all relay configuration files Substation appliance sends configurations/checksum to server System user compares configurations/checksum for relays to previous. Broadband Connection Critical Cyber Assets Electronic Security Perimeter

Contact Information Jeremy Anderson Manager, Sales Engineering Nova. Tech, LLC Jeremy. anderson@novatechweb. co m www. novatechweb. com