Navigating the Risk Management Framework Process and the








- Slides: 18

Navigating the Risk Management Framework Process and the NISP e. MASS NAO 28 March 2019

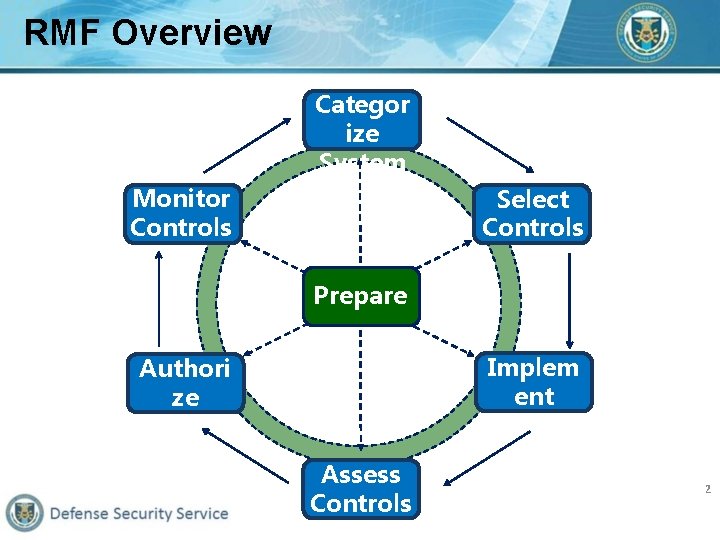
RMF Overview Categor ize System Monitor Controls Select Controls Prepare Implem ent Controls Authori ze System Assess Controls 2

Enterprise Mission Assurance Support Service (e. MASS) Benefits • e. MASS has direct correlation to RMF Capabilities • Simplifies the management of the entire Assessment & Authorization process • Enterprise level visibility of all authorization packages offering comprehensive organizational security postures. • Provides automated workflow • Management of all cybersecurity compliance activities and automation of the workflow process from system registration through system decommissioning. • Standardizes the exchange of information • Monitors system security during the entire system life cycle • Reports on cybersecurity compliance • Provides real-time metrics on Authorization activities • Overlays and artifacts are easily accessible • Provides management an accurate and timely dashboard on risk health • Data driven – policy and validation security controls • Maintenance of an enterprise baseline for security controls, which is stored in the e. MASS repository and updated with industry standards. • Fully automated inheritance allows systems to inherit security control statuses, artifacts, test results, and view system security postures from other systems. • Allows product teams, testers, and 3

e. MASS Access To obtain an e. MASS account users must: 1. Possess an External Certificate Authority (ECA) 2. Acquire ISSP sponsorship to obtain access to the Do. D RMF Knowledge Service (KS) 3. Complete e. MASS Computer Based Training (CBT) on RMF KS (Completion certificate submission required for account request) 4. Complete Do. D Cyber Awareness Challenge Training (Completion certificate submission required for account request) 5. Complete a DD Form 2875 SAAR for NISP e. MASS (Completed form submission required for account request) 6. Email artifacts from Steps 3 -5 to the DSS Knowledge Center to: dss. quantico. dss. mbx. emass@mail. mil Helpful Hint: See NISP-e. MASS Job Aid for guidance on e. MASS Training, ECA sponsorship and System Access on the RMF website. 4

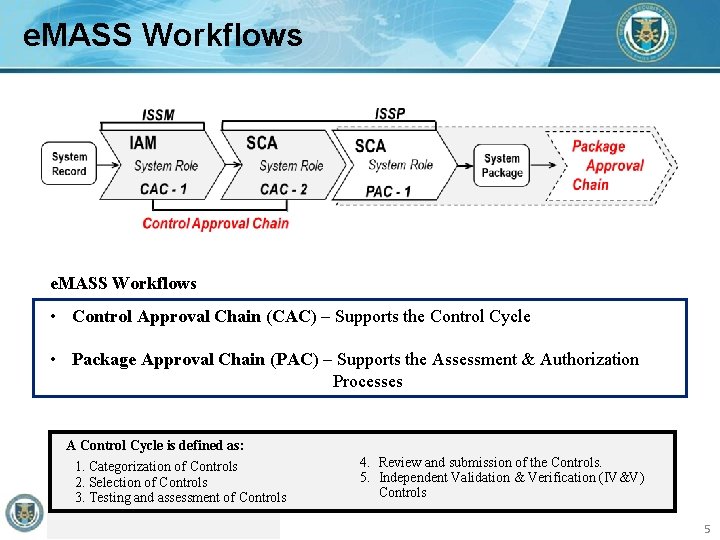
e. MASS Workflows • Control Approval Chain (CAC) – Supports the Control Cycle • Package Approval Chain (PAC) – Supports the Assessment & Authorization Processes A Control Cycle is defined as: 1. Categorization of Controls 2. Selection of Controls 3. Testing and assessment of Controls 4. Review and submission of the Controls. 5. Independent Validation & Verification (IV&V) Controls 5

e. MASS Workflow Roles Control Approval Chain (CAC) Roles CAC-1 Role (Industry) Primary Tasks are to: • Select or tailor controls in e. MASS • Test and Assess Controls as: Compliant Unofficial, Non-Compliant Unofficial, or Not Applicable Unofficial • Submit Controls individually or aggregated for Bulk Processing to the CAC-2 Role (ISSP) Primary Tasks are to: • Review, approve, or return any submitted control Note: Returned controls may be reworked and resubmitted with updates or adjustments for validation. Package Approval Chain (PAC) Roles PAC-1 Role (ISSP) Primary Tasks are to: • Create the system package - a static snapshot of the system security posture at that specific point in time • Submit the system package to the PAC reviewers 6

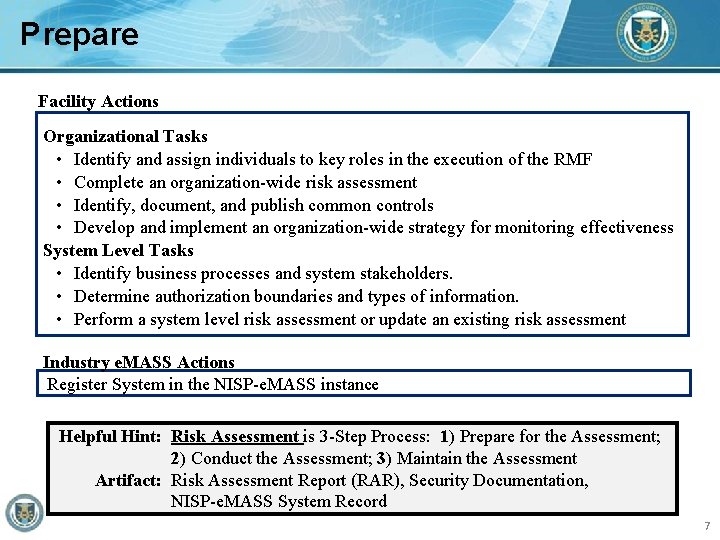
Prepare Facility Actions Organizational Tasks • Identify and assign individuals to key roles in the execution of the RMF • Complete an organization-wide risk assessment • Identify, document, and publish common controls • Develop and implement an organization-wide strategy for monitoring effectiveness System Level Tasks • Identify business processes and system stakeholders. • Determine authorization boundaries and types of information. • Perform a system level risk assessment or update an existing risk assessment Industry e. MASS Actions Register System in the NISP-e. MASS instance Helpful Hint: Risk Assessment is 3 -Step Process: 1) Prepare for the Assessment; 2) Conduct the Assessment; 3) Maintain the Assessment Artifact: Risk Assessment Report (RAR), Security Documentation, NISP-e. MASS System Record 7

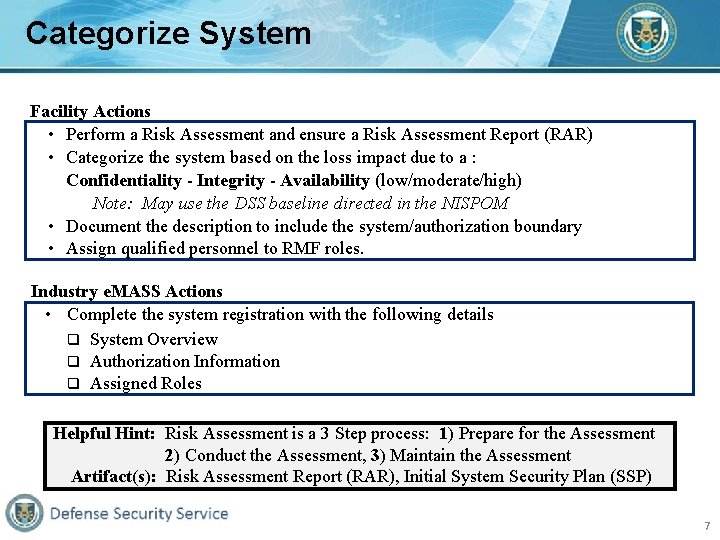
Categorize System Facility Actions • Perform a Risk Assessment and ensure a Risk Assessment Report (RAR) • Categorize the system based on the loss impact due to a : Confidentiality - Integrity - Availability (low/moderate/high) Note: May use the DSS baseline directed in the NISPOM • Document the description to include the system/authorization boundary • Assign qualified personnel to RMF roles. Industry e. MASS Actions • Complete the system registration with the following details System Overview Authorization Information Assigned Roles Helpful Hint: Risk Assessment is a 3 Step process: 1) Prepare for the Assessment 2) Conduct the Assessment, 3) Maintain the Assessment Artifact(s): Risk Assessment Report (RAR), Initial System Security Plan (SSP) 7

Select Security Controls Facility Actions • Select the security control baseline applicable to the system based the categorization • Tailor the controls as needed by supplementing, modifying, or tailoring out controls to effectively manage risk for any unique system conditions. • Develop a strategy for continuous monitoring of security control effectiveness. • Document the security controls selection in the SSP Industry e. MASS Actions 1) Select a registered system; 2) Go to System Details; 3) Populate the following: System Information Authorization Information Business Managing External Security Services Categorization Overlays Security Controls Helpful Hint: Standalone Systems categorized as M-L-L will use the DSS Overlay provided in the DSS RMF Resource Center (www. dss. mil/rmf) Artifact(s): Draft SSP w/ Controls, Continuous Monitoring Strategy and RAR 8

Implement Security Controls Facility Actions • Implement security controls • Revise the SSP to document the security control implementation. • Provide a functional description of the control implementation Include: Planned inputs, expected behavior, expected outputs, additional information necessary to describe how the security capability is achieved • Start a Plan of Action and Milestones as applicable • Conduct an initial assessment to identify weaknesses and deficiencies Industry e. MASS Actions 1) Navigate to the Controls Section; 2) Complete the Implementation Plan as follows: Critical Implementation Status Frequency Security Control Designation Method Estimated Completion Date Responsible Entities System-Level Continuous Monitoring Strategy (SLCM) Comments Helpful Hint: Read the Supplemental Guidance for the security controls (DAAPM Appendix A) Artifact(s): Updated SSP with a security control w/ functional implementation 9

Assess Security Controls Facility Actions • Conduct a self assessment of the security controls • Scan using: DISA SCAP Compliance Checker & STIG Viewer • Use the DSS Technical Assessment Job Aids as required Note: IS assessments that cannot be scanned using the tools must have justification documentation. • Complete the POA&M • Review the applicable Security Classification Guide(s) (SCG) • Verify classification level of all artifacts Note: If supporting artifacts are classified, contact assigned ISSP for guidance. • Update the security control state(s) based on the assessment vulnerabilities, reassessment, and remedial actions Industry e. MASS Actions 1) Navigate to the Controls Section; 2) Verify that the information is complete: Control Applicability Supporting Artifacts (unclassified) Security Control Procedure Implementation Plan & Risk Assessment Test Results Information Test Results Applied to the POA&M line item Helpful Hint: Each Control Family has Dash 1 (Xx-1) control policy. Some or all Dash 1 policies may be placed in a site specific overarching policy. Artifact(s): Final SSP; Certification Statement, RAR; POA&M; Artifacts 10

Assess Security Controls DSS Actions • Review the final package and artifacts • Conduct the onsite assessment DSS e. MASS Actions CAC-2 Role (ISSP): • Validate the controls • Submit Package to PAC (Package Approval Chain) • Return for Rework - Returns the system record back to the Industry CAC-1 Role Note: The Validate and Return for Rework actions require comments the text field. Helpful Hint: Use the following: 1) DISA Security Content Automation Protocol (SCAP) tool; 2) Security Technical Implementation Guide (STIG) Viewer; 3) Applicable STIGs; 4) SCAP Compliance Checker (SCC)* Artifacts: POA&M, SAR, and Submission of Finalized Package *Note: Content should be installed on all supported systems. If the system cannot be assessed using the specified scanning tools, Industry must document the justification and process for assessing the system in the system security authorization package. 11

Authorize DSS Actions - Assemble and submit the security authorization package (Automated in e. MASS) - Verify that the security authorization package is complete to include the risk based information for the system - Submit to AO for final review • Reviewing the relevant information to make an authorization decision • Consult other organizational officials as required • Issue an authorization decision for the system and the common controls Note: The AO has explicit risk acceptance responsibility for the system. e. MASS PAC Role Actions - Assess the package - Enter the Security Control Assessor Executive Summary and Assessment Date - Recommend one of the following: Approve, Disapprove and Move Forward, or Return for Rework • (AO) Apply an authorization decision Note: The Authorization Letter will be automatically generated in e. MASS. Helpful Hint: ISSMs cannot use conditions from multiple MSSPs for Type Authorization. The system must be an exact carbon copy. Artifact(s): Authorization Letter 12

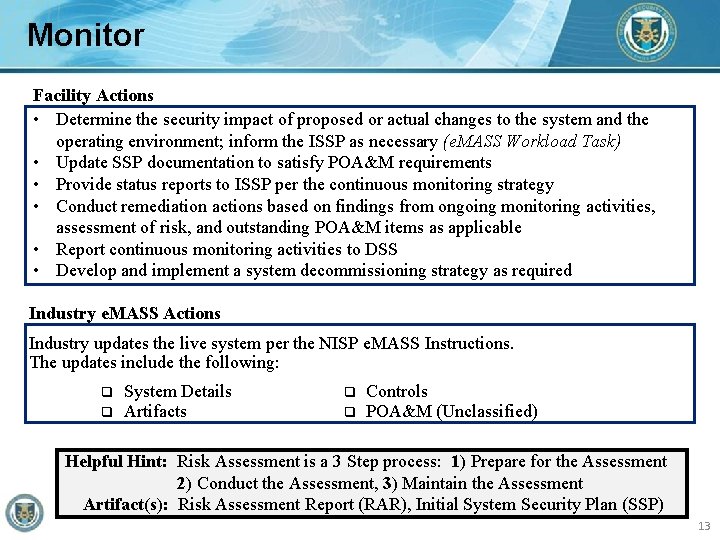
Monitor Facility Actions • Determine the security impact of proposed or actual changes to the system and the operating environment; inform the ISSP as necessary (e. MASS Workload Task) • Update SSP documentation to satisfy POA&M requirements • Provide status reports to ISSP per the continuous monitoring strategy • Conduct remediation actions based on findings from ongoing monitoring activities, assessment of risk, and outstanding POA&M items as applicable • Report continuous monitoring activities to DSS • Develop and implement a system decommissioning strategy as required Industry e. MASS Actions Industry updates the live system per the NISP e. MASS Instructions. The updates include the following: System Details Artifacts Controls POA&M (Unclassified) Helpful Hint: Risk Assessment is a 3 Step process: 1) Prepare for the Assessment 2) Conduct the Assessment, 3) Maintain the Assessment Artifact(s): Risk Assessment Report (RAR), Initial System Security Plan (SSP) 13

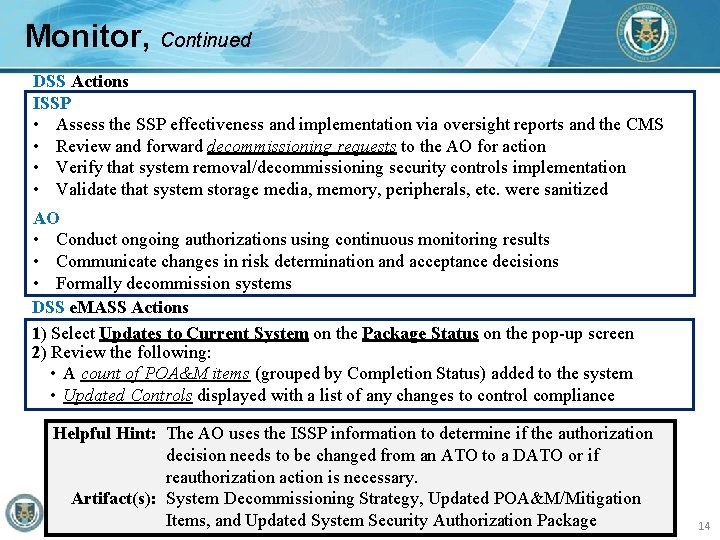
Monitor, Continued DSS Actions ISSP • Assess the SSP effectiveness and implementation via oversight reports and the CMS • Review and forward decommissioning requests to the AO for action • Verify that system removal/decommissioning security controls implementation • Validate that system storage media, memory, peripherals, etc. were sanitized AO • Conduct ongoing authorizations using continuous monitoring results • Communicate changes in risk determination and acceptance decisions • Formally decommission systems DSS e. MASS Actions 1) Select Updates to Current System on the Package Status on the pop-up screen 2) Review the following: • A count of POA&M items (grouped by Completion Status) added to the system • Updated Controls displayed with a list of any changes to control compliance Helpful Hint: The AO uses the ISSP information to determine if the authorization decision needs to be changed from an ATO to a DATO or if reauthorization action is necessary. Artifact(s): System Decommissioning Strategy, Updated POA&M/Mitigation Items, and Updated System Security Authorization Package 14

NISP RMF/e. MASS Summary RMF Action PREPARE (Industry) CATEGORIZ E (Industry) SELECT (Industry) IMPLEMENT (Industry) ASSESS (A. Industry B. DSS) AUTHORIZE (DSS) MONITOR (Industry & DSS) e. MASS Actions e. MASS Role / Workflow System Level Tasks Organizational Tasks System § execution Identify business processes and system stakeholders. § Identify and assign individuals to key RMF roles in the Registration § Determine authorization boundaries and types of information. § Complete an organization-wide risk assessment CAC-1 § Identify, document, and publish common controls § Perform a system level risk assessment or update the risk assessment § Develop and implement an organization-wide strategy for monitoring System Registration § Assign Roles § Input System Details IAM/CAC-1 § Baseline Security Control Selection § Overlay Selection § Input of Additional System Details IAM/CAC-1 § Implementation Plan § System-Level Continuous Monitoring (SLCM) Strategy IAM/CAC-1 § A - Self-Assessment of Security Controls Package ■ B - Review and Validation of Security Controls within Finalized § A - Generation of Automated POA&M ■ B - Document Weaknesses and/or Deficiencies in SAR § A - Review of finalized package ■ B - Approve/Return Package for Rework § A - Submission of Final Package to SCA ■ B - Submission of Finalized Package to the Package Approval Chain A. IAM/CAC 1 § SCA Generates Security Assessment Report Executive Summary § SCA Recommends Authorization Decision to AO ---------------------------§ AO Inputs Authorization Decision § Automated Authorization Letter is Generated SCA/PAC § Technical, Management, and Operational Security Controls are Assessed, Modified and Submitted for Approval According to Continuous Monitoring Strategy (CMS) § POA&M Remediation/Mitigation Items are Updated, Reviewed and Submitted to SCA for Approval § SCA Reviews Updated Security Controls and POA&M items in accordance to CMS IAM/PAC B. SCA/CAC 2 AO/PAC 16

Resources Resource Location DSS RMF Information Resource Center https: //www. dss. mil/ma/ctp/io/nao/rmf/ e. MASS Computer Based Training https: //rmfks. osd. mil/rmfresources/e. MASS/CB T_Sept 2018/index. aspx DSS NAO e. MASS Mailbox dss. quantico. dss. mbx. emass@mail. mil Do. D RMF Knowledge Service https: //rmfks. osd. mil/rmf/Pages/default. aspx 17

Questions? 18