National Cyber Exercise Cyber Storm National Cyber Security

National Cyber Exercise: Cyber Storm National Cyber Security Division New York City Metro ISSA Meeting June 21, 2006 This document is FOR OFFICIAL USE ONLY (FOUO). It contains information that may be exempt from public release under the Freedom of Information Act (5 U. S. C. 552). It is to be controlled, stored, handled, transmitted, distributed, and disposed of in accordance with DHS policy relating to FOUO information and is not to be released to the public or other personnel who do not have a valid “need-to-know” without prior approval of FOR OFFICIAL USE ONLY an authorized DHS official.

Agenda Cyber Storm Overview § Exercise Objectives § Exercise Construct § Player Universe § Scenario Context and Scope § Scenario and Adversary § Scope and Scale Overarching Lessons Learned Way Ahead Cyber Storm II FOR OFFICIAL USE ONLY 1

Cyber Storm FOR OFFICIAL USE ONLY 2

Cyber Storm Overview What: § Provided a controlled environment to exercise State, Federal, International, and Private Sector response to a cyber related incident of national significance § Large scale exercise through simulated incident reporting only – no actual impact or attacks on live networks § Specifically directed by Congress in FY 05 appropriations language and coordinated with DHS National Exercise Program Who: 300+ participants from § § Federal D/As: Agencies States: International: Private Sector – IT: – Energy: – Airlines: – ISACs: Support and/or participation by 8 Departments and 3 Michigan, Montana, New York, Washington (Exercise Control) Australia, Canada, New Zealand, UK 9 major IT firms 6 electric utility firms (generation, transmission & grid operations) 2 major air carriers Multi-State, IT, Energy, Finance (off the record participant) (Nebraska, North Carolina, South Carolina, Texas @ MS-ISAC) When: February 6 -10, 2006 Where: distributed participation from ~ 60 locations including US, Canada, and UK FOR OFFICIAL USE ONLY 3

Exercise Objectives Exercise the national cyber incident response community with a focus on: § § § Interagency coordination under the Cyber Annex to the National Response Plan: – Interagency Incident Management Group (IIMG) – National Cyber Response Coordination Group (NCRCG) Intergovernmental coordination and incident response: – Domestic: State – Federal – International: Australia, Canada, NZ, UK & US Identification and improvement of public-private collaboration, procedures and processes Identification of policies/issues that affect cyber response & recovery Identification of critical information sharing paths and mechanisms Raise awareness of the economic and national security impacts associated with a significant cyber incident FOR OFFICIAL USE ONLY 4
![Exercise Construct Feb. 6 Feb. 7 Feb. 8 Build-Up [D-300 - D 14] Build-Up Exercise Construct Feb. 6 Feb. 7 Feb. 8 Build-Up [D-300 - D 14] Build-Up](http://slidetodoc.com/presentation_image_h/e6bd780b6790e6205c0e41a1a394b240/image-6.jpg)
Exercise Construct Feb. 6 Feb. 7 Feb. 8 Build-Up [D-300 - D 14] Build-Up [D-7&D 1] Crisis Phase [D Day] Mon. 4 hrs Tue. 8 hrs Feb. 9 Feb. 10 Response & Recovery [D+1] Wed. -Thurs. 36 hrs Fri. 4 hrs TTX & Hotwash Live Play State Prep Response & Recovery [D+5 -7] State Play & Hotwash Aus & NZ TTXs Thurs Canada Federal Players United Kingdom Private Sector Players State Government Players International Players US Exercise Control Australia FOR OFFICIAL USE ONLY New Zealand 5
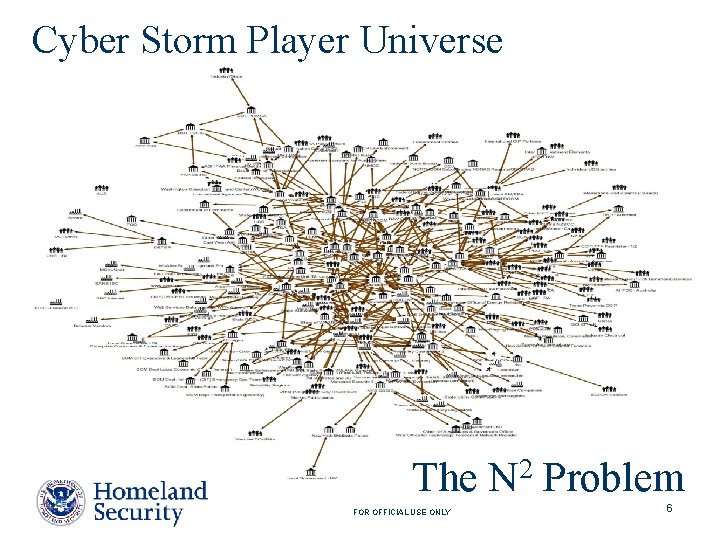
Cyber Storm Player Universe The N 2 Problem FOR OFFICIAL USE ONLY 6

Player Universe NCC IT-ISAC DNI NSA IT/Telecom US-CERT LE/ Intell DHS I&A Comms ISAC ISP/Telco Sim Cell MSV 1 CA MHV 1 MSV 3 HITRAC State/Local Energy Michigan DHS & Interagency FBI IIMG HSOC NCSD NICC Trans LE/Intell PA/Media Montana ES-ISAC Utility 1 DHS OMB DOC DOD Fed. Reserve Bank FDIC HSC Treasury DOJ DOT TCIRC NSC Ag Red Cross FAA CSIRC Air Carrier 1 Regional Pwr Admins DOS FOR OFFICIAL USE ONLY Utility 4 Utility 3 TSA TSOC Air Carrier 2 IMC DOE Utility 2 Transportation Sector Federal Department/Agencies NCS Energy Fed D/As IT/Telcom NCRCG IP OPA Main Exercise Control (75 / 20) Internat’l States New York USSS MSSP MSV 2 MS-ISAC CIA Utility 6 Utility 5 International New Zealand Canada 13 Players 11 Sim. Cell Australia United Kingdom 3 Players 7

Scenario Context and Scope A simulated large-scale cyber incident affecting Energy, Information Technology (IT), Telecommunications and Transportation infrastructure sectors. Cyber Storm scenario included: § § Cyber attacks through control systems, networks, software, and social engineering to disrupt transportation and energy infrastructure elements Cyber attacks targeted at the IT infrastructure of State, US Federal and International Government agencies intended to: – degrade government operations/delivery of public services – diminish the ability to remediate impacts on other infrastructure sectors – undermine public confidence The exercise was NOT focused on the consequence management of the physical infrastructures affected by the attacks § Physical consequence management aspects largely provided to players via robust Exercise Control cell FOR OFFICIAL USE ONLY 8
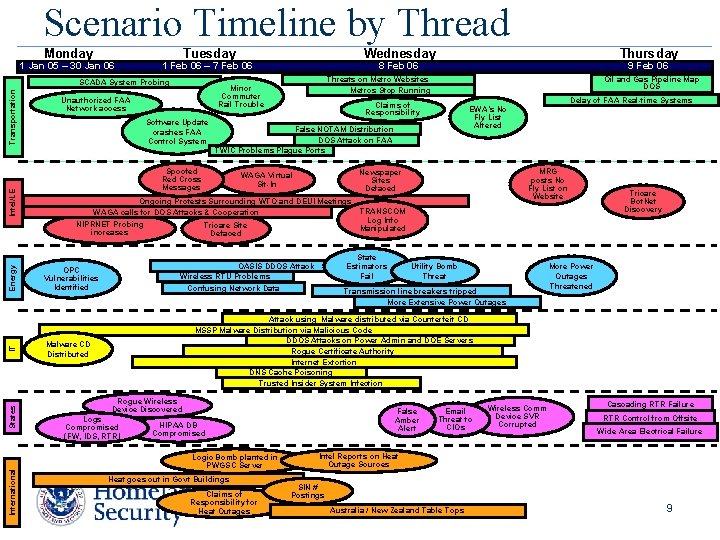
Scenario Timeline by Thread Monday 1 Jan 05 – 30 Jan 06 Tuesday States IT Energy Intel/LE Transportation SCADA System Probing International Wednesday 1 Feb 06 – 7 Feb 06 Software Update crashes FAA Control System 9 Feb 06 Oil and Gas Pipeline Map DOS Threats on Metro Websites Metros Stop Running Minor Commuter Rail Trouble Unauthorized FAA Network access Thursday 8 Feb 06 Delay of FAA Real-time Systems Claims of Responsibility EWA’s No Fly List Altered False NOTAM Distribution DOS Attack on FAA TWIC Problems Plague Ports Spoofed Red Cross Messages MRG posts No Fly List on Website Newspaper Sites Defaced WAGA Virtual Sit-In Ongoing Protests Surrounding WTO and DEUI Meetings TRANSCOM WAGA calls for DOS Attacks & Cooperation Log Info NIPRNET Probing Tricare Site Manipulated increases Defaced State Estimators Fail OASIS DDOS Attack Wireless RTU Problems Confusing Network Data OPC Vulnerabilities Identified Utility Bomb Threat Transmission line breakers tripped More Extensive Power Outages Tricare Bot. Net Discovery More Power Outages Threatened Attack using Malware distributed via Counterfeit CD MSSP Malware Distribution via Malicious Code DDOS Attacks on Power Admin and DOE Servers Rogue Certificate Authority Internet Extortion DNS Cache Poisoning Trusted Insider System Infection Malware CD Distributed Rogue Wireless Device Discovered Logs Compromised (FW, IDS, RTR) False Amber Alert HIPAA DB Compromised Logic Bomb planted in PWGSC Server Heat goes out in Govt Buildings Claims of Responsibility for Heat Outages Email Threat to CIOs Wireless Comm Device SVR Corrupted Cascading RTR Failure RTR Control from Offsite Wide Area Electrical Failure Intel Reports on Heat Outage Sources SIN # Postings Australia Zealand Table Tops FOR/ New OFFICIAL USE ONLY 9
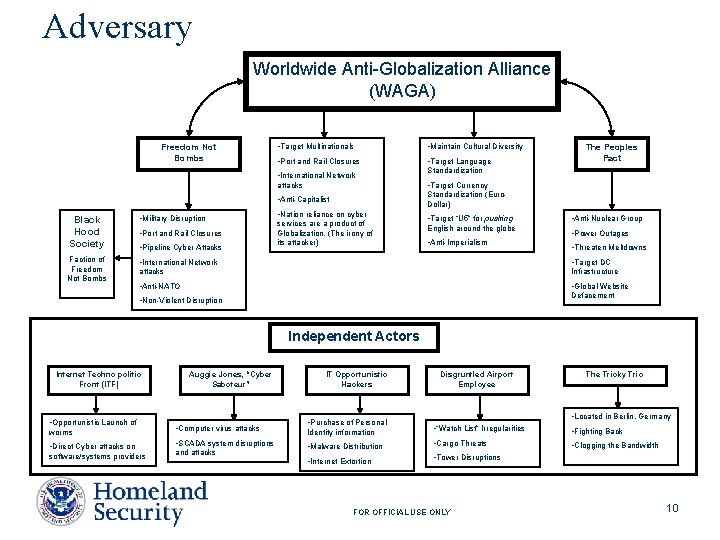
Adversary Worldwide Anti-Globalization Alliance (WAGA) Freedom Not Bombs • Target Multinationals • Maintain Cultural Diversity • Port and Rail Closures • Target Language • International Network Standardization attacks • Target Currency • Anti-Capitalist Standardization (Euro. Dollar) • Nation reliance on cyber The Peoples Pact Black Hood Society • Military Disruption Faction of Freedom Not Bombs • International Network • Target DC attacks Infrastructure • Anti-NATO • Global Website • Port and Rail Closures • Pipeline Cyber Attacks services are a product of Globalization. (The irony of its attacker) • Target “U 5” for pushing English around the globe • Anti-Imperialism • Anti-Nuclear Group • Power Outages • Threaten Meltdowns Defacement • Non-Violent Disruption Independent Actors Internet Techno politic Front (ITF) • Opportunistic Launch of Auggie Jones, “Cyber Saboteur” worms • Computer virus attacks • Direct Cyber attacks on • SCADA system disruptions software/systems providers and attacks IT Opportunistic Hackers • Purchase of Personal Disgruntled Airport Employee The Tricky Trio • Located in Berlin, Germany Identity information • “Watch List” Irregularities • Fighting Back • Malware Distribution • Cargo Threats • Clogging the Bandwidth • Internet Extortion • Tower Disruptions FOR OFFICIAL USE ONLY 10
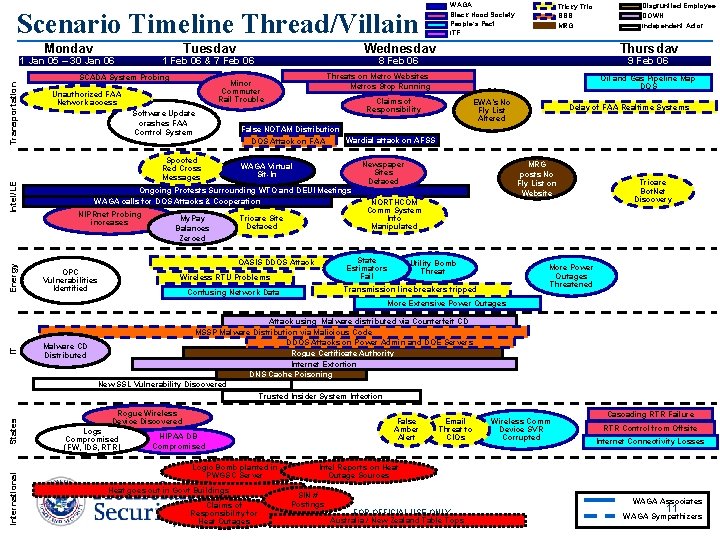
Scenario Timeline Thread/Villain Monday Tuesday 1 Jan 05 – 30 Jan 06 Transportation Intel/LE Energy Software Update crashes FAA Control System Spoofed Red Cross Messages My. Pay Balances Zeroed Oil and Gas Pipeline Map DOS Claims of Responsibility EWA’s No Fly List Altered Delay of FAA Realtime Systems False NOTAM Distribution DOS Attack on FAA Wardial attack on AFSS MRG posts No Fly List on Website Newspaper Sites Defaced WAGA Virtual Sit-In Tricare Site Defaced NORTHCOM Comm System Info Manipulated State Estimators Fail OASIS DDOS Attack OPC Vulnerabilities Identified Feb 06 06 99 Feb Threats on Metro Websites Metros Stop Running Ongoing Protests Surrounding WTO and DEUI Meetings WAGA calls for DOS Attacks & Cooperation NIPRnet Probing increases Disgruntled Employee DOWN Independent Actor Thursday 8 8 Feb 06 06 Minor Commuter Rail Trouble Unauthorized FAA Network access Tricky Trio BBB MRG Wednesday 1 Feb 06 & 7 Feb 06 SCADA System Probing WAGA Black Hood Society People’s Pact ITF Wireless RTU Problems Utility Bomb Threat More Power Outages Threatened Transmission line breakers tripped Confusing Network Data Tricare Bot. Net Discovery International States IT More Extensive Power Outages Malware CD Distributed Attack using Malware distributed via Counterfeit CD MSSP Malware Distribution via Malicious Code DDOS Attacks on Power Admin and DOE Servers Rogue Certificate Authority Internet Extortion DNS Cache Poisoning New SSL Vulnerability Discovered Trusted Insider System Infection Rogue Wireless Device Discovered Logs Compromised (FW, IDS, RTR) False Amber Alert HIPAA DB Compromised Logic Bomb planted in PWGSC Server Heat goes out in Govt Buildings Claims of Responsibility for Heat Outages Email Threat to CIOs Wireless Comm Device SVR Corrupted Cascading RTR Failure RTR Control from Offsite Internet Connectivity Losses Intel Reports on Heat Outage Sources SIN # Postings WAGA Associates FOR OFFICIAL USE ONLY Australia / New Zealand Table Tops 11 WAGA Sympathizers
Scope and Scale Planning: 18 months § § § 5 major planning conferences 100 -150 participants @ each 5 AAR conferences Ex. Con: ~100 § § § § Exercise network & workstations NXMSEL, web and email servers Simulate media website Hacker websites Physical build Observer group Observation database Players: 300+ Scenario: 800+ injects Player emails: 21, 000+ captured Cost: $$ Exercise Management Team: peaked @ ~20 FTEs FOR OFFICIAL USE ONLY 12

Overarching Lessons Learned Correlation of multiple incidents is challenging at all levels: § § Within enterprises / organizations Across critical infrastructure sectors Between states, federal agencies and countries Bridging public – private sector divide Communication provides the foundation for response § Processes and procedures must address communication protocols, means and methods Collaboration on vulnerabilities is rapidly becoming required § Reliance on information systems for situational awareness, process controls and communications means that infrastructures cannot operate in a vacuum Coordination of response is time critical § Cross-sector touch points, key organizations, and SOPs must be worked out in advance § Coordination between public-private sectors must include well articulated roles and responsibilities FOR OFFICIAL USE ONLY 13

Overarching Lessons Learned Strategic Communications / Public Messaging § Critical part of government response that should be coordinated with partners at all levels Policy Coordination § § Senior leadership / interagency bodies should develop more structured communication paths with international counterparts Strategic situational awareness picture cannot be built from a wholly federal or domestic perspective in the cyber realm Operational Cooperation § § True situational awareness will always include an external component Initial efforts at international cooperation during CS provided concrete insights into of near term development of way ahead for ops/tech info sharing Communication paths, methods, means and protocols must be solidified in advance of crisis/incident response – Who do I call? When do I call? How do I call them? – Secure and assured communications are critical in order to share sensitive information Cooperation must include ability to link into or share info in all streams: e. g. , Cyber, Physical, LE, Intelligence FOR OFFICIAL USE ONLY 14

Way Ahead– Cyber Storm II Tentatively scheduled for March 2008 Fall 2006, DHS and key stakeholders will begin development of CSII overall concept and scenario focus Spring 2007, CSII CONOPS will be finalized Based on the scenario focus areas, DHS will coordinate with the sector specific agencies and the relevant Information Sharing Analysis Centers and Private Sector Coordinating Councils (NIPP) for individual private sector participants. FOR OFFICIAL USE ONLY 15

FOR OFFICIAL USE ONLY
- Slides: 17