Mustansiriyah University Faculty of Engineering Computer Engineering Dep


- Slides: 3

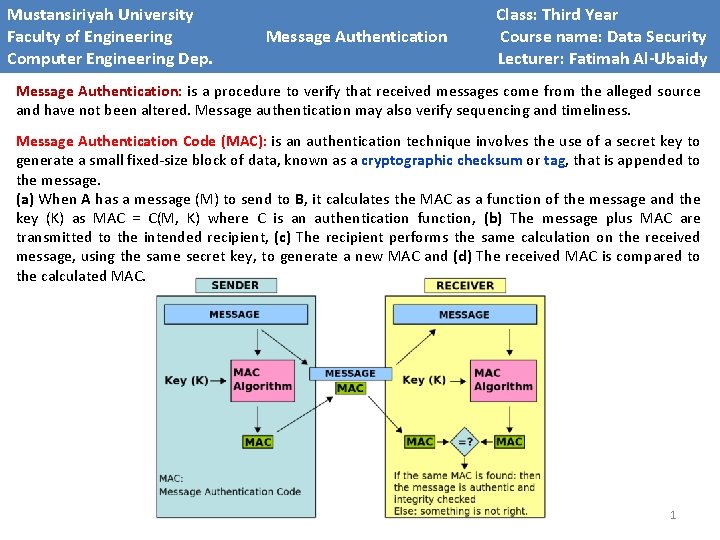
Mustansiriyah University Faculty of Engineering Computer Engineering Dep. Message Authentication Class: Third Year Course name: Data Security Lecturer: Fatimah Al-Ubaidy Message Authentication: is a procedure to verify that received messages come from the alleged source and have not been altered. Message authentication may also verify sequencing and timeliness. Message Authentication Code (MAC): is an authentication technique involves the use of a secret key to generate a small fixed-size block of data, known as a cryptographic checksum or tag, that is appended to the message. (a) When A has a message (M) to send to B, it calculates the MAC as a function of the message and the key (K) as MAC = C(M, K) where C is an authentication function, (b) The message plus MAC are transmitted to the intended recipient, (c) The recipient performs the same calculation on the received message, using the same secret key, to generate a new MAC and (d) The received MAC is compared to the calculated MAC. 1

Mustansiriyah University Faculty of Engineering Computer Engineering Dep. Message Authentication Class: Third Year Course name: Data Security Lecturer: Fatimah Al-Ubaidy Message Security Requirements: The possible attacks in the context of communication across a network and their security measures: Attack Security Measure (1) Disclosure: Release of message contents to any person or process. Message Confidentiality (2) Traffic Analysis: Discovery of the pattern of traffic between parties. Message Confidentiality (3) Masquerade: Insertion of messages into the network from a fraudulent source. Message Authentication (4) Content Modification: Changes to the contents of a message. Message Authentication (5) Sequence Modification: Any modification to a sequence of messages between parties. Message Authentication (6) Timing Modification: Delay or replay of messages. Message Authentication (7) Source Repudiation: Denial of transmission of message by source. (8) Destination Repudiation: Denial of receipt of message by destination. Digital Signature + Special Protocol 2

Mustansiriyah University Engineering College Computer Engineering Dep. Message Authentication Class: Third Year Course name: Data Security Lecturer: Fatimah Al-Ubaidy The MAC can satisfy the following goals: (1) The receiver is assured that the message has not been altered, (2) The receiver is assured that the message is from the alleged sender, (3) If the message includes a sequence number, then the receiver can be assured of the proper sequence. Security of MAC (1) Brute Force Attack (2) Cryptanalysis Properties/Security Requirements of MAC: 1. It is infeasible to find another message with same MAC. 2. MACs should be uniformly distributed. 3. MAC should depend equally on all bits of the message. * MAC versus Encryption: MAC algorithm need not be reversible as it must to be for decryption. * MAC does not provide digital signature because both sender and receiver must share the same key. * MAC versus Hash function is that hash function does not rely on a secret key. MACs Based on Hash Functions: HMAC q HMAC has been chosen as the mandatory-to-implement MAC for IP security, and is used in other Internet protocols, such as SSL. q HMAC has also been issued as a NIST standard. q It uses hash function on the message: 3