Mustansiriyah University Engineering College Computer Engineering Dep Introduction


- Slides: 4

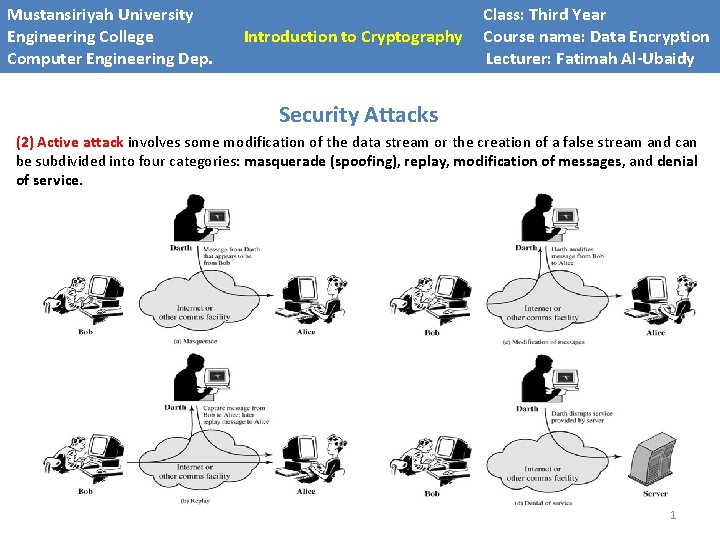
Mustansiriyah University Engineering College Computer Engineering Dep. Introduction to Cryptography Class: Third Year Introduction to Cryptography Course name: Data Encryption Introduction to Cryptography Lecturer: Fatimah Al-Ubaidy Security Attacks (2) Active attack involves some modification of the data stream or the creation of a false stream and can be subdivided into four categories: masquerade (spoofing), replay, modification of messages, and denial of service. 1

Mustansiriyah University Engineering College Computer Engineering Dep. Introduction to Cryptography Class: Third Year Introduction to Cryptography Course name: Data Encryption Introduction to Cryptography Lecturer: Fatimah Al-Ubaidy Security Attacks Release of message content: happens when an opponent learns the contents of transmitted messages. Traffic analysis: when an opponent is able to observe the pattern of the messages and can determine the location and identity of communicating hosts and could observe the frequency and length of messages being exchanged. Masquerade (spoofing): takes place when one entity pretends to be a different entity. Replay: involves the passive capture of a data unit and its subsequent retransmission to produce an unauthorized effect. Modification of messages: simply means that some portion of a legitimate message is altered. Denial of service: prevents or inhibits the normal use or management of communications facilities. For example, an entity may suppress all messages directed to a particular destination. Another example is the disruption of an entire network. * Passive attacks are very difficult to detect, because they do not involve any alteration of the data. However, it is feasible to prevent the success of passive attacks by means of encryption. * It is quite difficult to prevent active attacks absolutely because of the wide variety of potential physical, software, and network vulnerabilities. 2

Mustansiriyah University Engineering College Computer Engineering Dep. Introduction to Cryptography Class: Third Year Introduction to Cryptography Course name: Data Encryption Introduction to Cryptography Lecturer: Fatimah Al-Ubaidy Cryptographic System Characteristics Cryptographic systems are characterized along three independent dimensions: 1. The type of operations used for transforming plaintext to ciphertext. All encryption algorithms are based on two general principles: substitution, in which each element in the plaintext is mapped into another element, and transposition, in which elements in the plaintext are rearranged. Most systems, referred to as product systems, involve multiple stages of substitutions and transpositions. 2. The number of keys used. If both sender and receiver use the same key, the system is referred to as symmetric, single-key, secret-key, or conventional encryption. If the sender and receiver use different keys, the system is referred to as asymmetric, two-key, or public-key encryption. 3. The way in which the plaintext is processed. A block cipher processes the input one block of elements at a time, producing an output block for each input block. A stream cipher processes the input elements continuously, producing output one element at a time, as it goes along. Types of Attack on Encrypted Messages (Cryptanalysis Categories) 1 -Ciphertext only attack is a case in which only the encrypted message is available for attack. 2 -Known plaintext attack: both the plaintext and matching ciphertext are available for use in discovering the key. 3 -Chosen plaintext attack: the attacker runs various pieces of plaintext for encryption and attempt to derive the key. j 4 -Chosen ciphertext attack: the cryptanalyst can choose different ciphertexts to be decrypted and then using the results of these decryptions to discover the key. 5 -Chosen text attack: Provides protection against denial by one of the entities involved in a communication of having participated in all or part of the communication. 3

Mustansiriyah University Engineering College Computer Engineering Dep. Introduction to Cryptography Class: Third Year Introduction to Cryptography Course name: Data Encryption Introduction to Cryptography Lecturer: Fatimah Al-Ubaidy • Opponent can be human (e. g. hacker) or software (e. g. virus). • Computing resources can be processors, memories and I/O (e. g. printers). • Steganography and cryptography: The methods of steganography conceal the existence of the message, whereas the methods of cryptography process the message to outsiders by various transformations of the text. • Cryptanalysis: Cryptanalytic attacks rely on the nature of the algorithm plus some knowledge of the general characteristics of the plaintext or even some sample plaintext–ciphertext pairs. This type of attack exploits the characteristics of the algorithm to attempt to deduce a specific plaintext or to deduce the key being used. • Brute-force attack: The attacker tries every possible key on a piece of ciphertext until an intelligible translation into plaintext is obtained. On average, half of all possible keys must be tried to achieve success. Linear cryptanalysis is a general form of attack that is based on finding a linear relationship between the elements (characters or individual bits) of plaintext, the ciphertext, and the key. It therefore tries to find a linear approximation to the action of a cipher, i. e. if "ciphertext = f(plaintext, key)", then we are trying to find a linear approximation of f. It is used widely on block ciphers. Differential cryptanalysis is a general form of cryptanalysis applicable primarily to block ciphers, but also to stream ciphers and cryptographic hash functions. In the broadest sense, it is the study of how differences in information input can affect the resultant difference at the output, i. e. discovering where the cipher exhibits a non-random behavior and exploiting such properties to recover the secret key (cryptography key). 4