Multiuser CDMA Enhancing capacity of wireless cellular CDMA

- Slides: 27

Multi-user CDMA Enhancing capacity of wireless cellular CDMA

Topics Today n n Dealing without multi-user reception: asynchronous CDMA u SNR u power balance - near-far effect Multi-user detection (MUD) classification and properties u The conventional detector (non-MUD, denotations) u Maximum likelihood sequence detection u Linear detectors F Decorrelating detector F Minimum mean-square error detector F Polynomial expansion detector u Subtractive interference cancellation F Serial and parallel cancellation techniques Timo O. Korhonen, Helsinki University of Technology 2

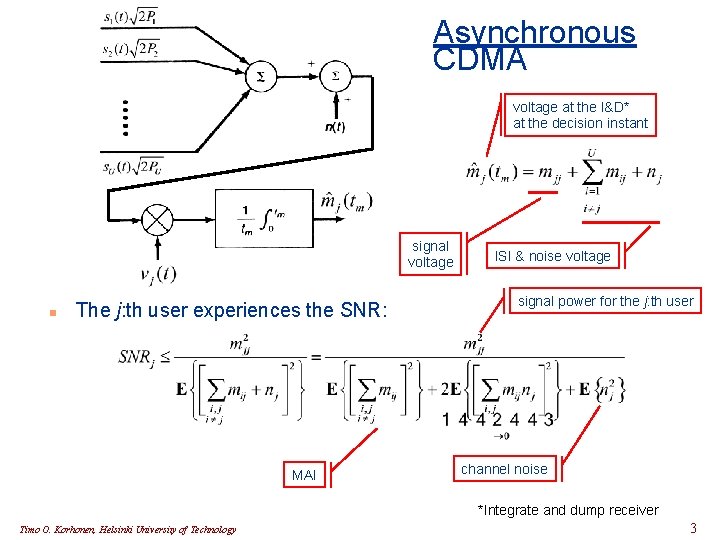
Asynchronous CDMA voltage at the I&D* at the decision instant signal voltage n The j: th user experiences the SNR: MAI ISI & noise voltage signal power for the j: th user channel noise *Integrate and dump receiver Timo O. Korhonen, Helsinki University of Technology 3

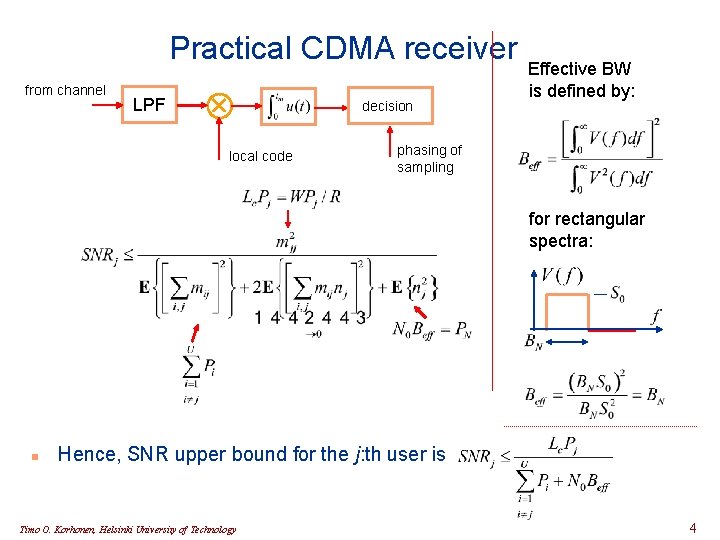
Practical CDMA receiver from channel LPF decision local code Effective BW is defined by: phasing of sampling for rectangular spectra: n Hence, SNR upper bound for the j: th user is Timo O. Korhonen, Helsinki University of Technology 4

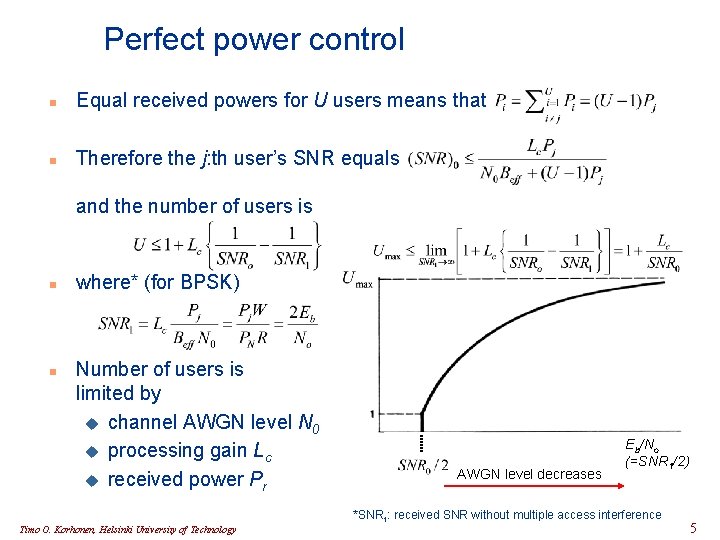
Perfect power control n Equal received powers for U users means that n Therefore the j: th user’s SNR equals and the number of users is n n where* (for BPSK) Number of users is limited by u channel AWGN level N 0 u processing gain Lc u received power Pr AWGN level decreases Eb/No (=SNR 1/2) *SNR 1: received SNR without multiple access interference Timo O. Korhonen, Helsinki University of Technology 5

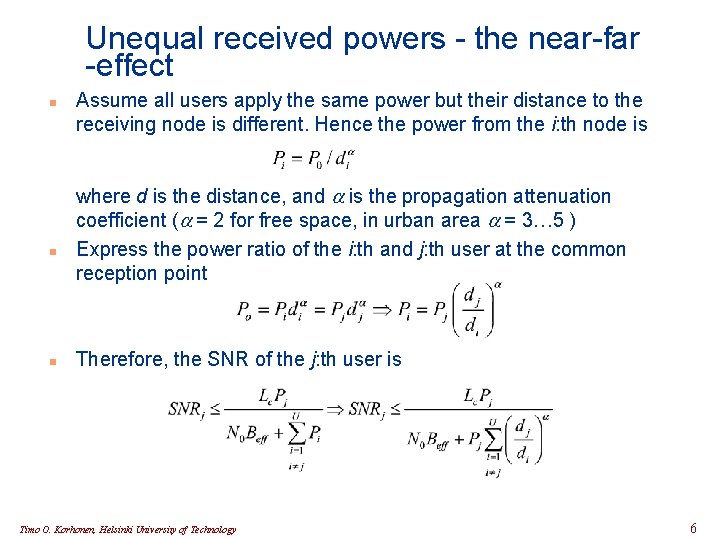
Unequal received powers - the near-far -effect n n n Assume all users apply the same power but their distance to the receiving node is different. Hence the power from the i: th node is where d is the distance, and a is the propagation attenuation coefficient (a = 2 for free space, in urban area a = 3… 5 ) Express the power ratio of the i: th and j: th user at the common reception point Therefore, the SNR of the j: th user is Timo O. Korhonen, Helsinki University of Technology 6

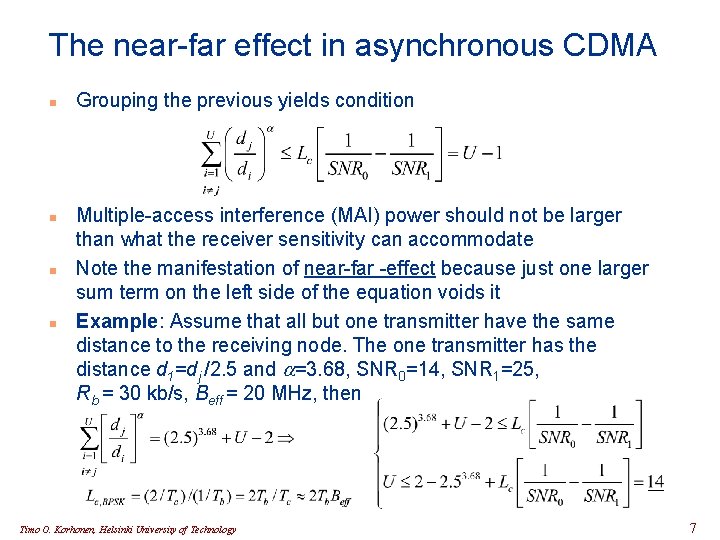
The near-far effect in asynchronous CDMA n n Grouping the previous yields condition Multiple-access interference (MAI) power should not be larger than what the receiver sensitivity can accommodate Note the manifestation of near-far -effect because just one larger sum term on the left side of the equation voids it Example: Assume that all but one transmitter have the same distance to the receiving node. The one transmitter has the distance d 1=dj /2. 5 and a=3. 68, SNR 0=14, SNR 1=25, Rb = 30 kb/s, Beff = 20 MHz, then Timo O. Korhonen, Helsinki University of Technology 7

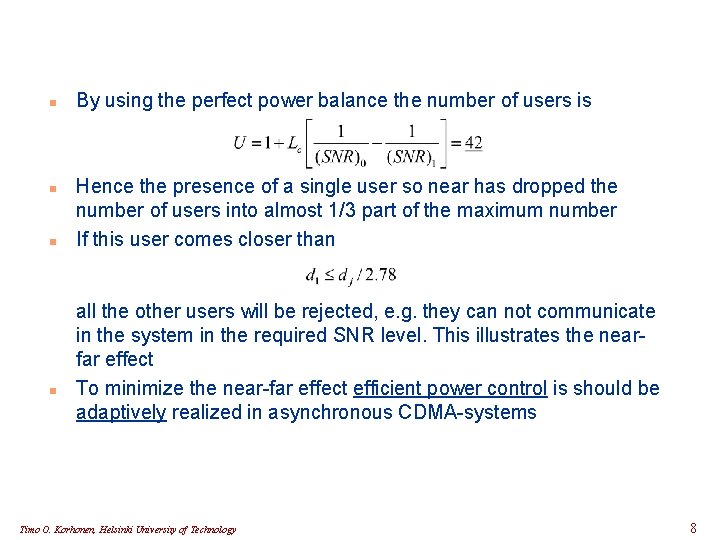
n n By using the perfect power balance the number of users is Hence the presence of a single user so near has dropped the number of users into almost 1/3 part of the maximum number If this user comes closer than all the other users will be rejected, e. g. they can not communicate in the system in the required SNR level. This illustrates the nearfar effect To minimize the near-far effect efficient power control is should be adaptively realized in asynchronous CDMA-systems Timo O. Korhonen, Helsinki University of Technology 8

Fighting against Multiple Access Interference n n n CDMA system can be realized by spreading codes having low cross -correlation as Gold codes (asynchronous usage) or Walsh codes (synchronous usage) Multipath channel with large delay spread can destroy code cross-correlation properties u a remedy: asynchronous systems with large code gain assume other users to behave as Gaussian noise (as just analyzed!) Additional compensation of MAI yields further capacity (increases receiver sensitivity). This can be achieved by u Code waveform design (BW-rate/trade-off) u Power control (minimizes near-far effect) u FEC- and ARQ-systems u Diversity-systems: - Spatial - Frequency - Time u multi-user detection Timo O. Korhonen, Helsinki University of Technology 9

MAI versus ISI (Inter-Symbolic Interference) u Note that there exists a strong parallelism between the problem of MAI and that of ISI: Asynchronous channel of K-users behaves the same way as a single user channel having ISI with *memory depth of K-1 u u Hence, a number of multi-user detectors have their equalizer counter parts as: F maximum likelihood F zero-forcing F minimum mean square F decision feedback General classification of multi-user detectors: F linear F subtractive *This could be generated for instance by a multipath channel having K-1 taps Timo O. Korhonen, Helsinki University of Technology 10

Maximum-likelihood sequence detection n Optimum multi-user detection applies maximum-likelihood principle: Considering the whole received sequence, find the estimate for the received sequence that has the minimum distance to the allowed sequences n n The ML principle u has the optimum performance provided transmitted symbols equal alike u has large computational complexity - In exhaustive search 2 NK vectors to be considered! (K users, N bits) u requires estimation of received amplitudes and phases that takes still more computational power u can be implemented by using Viterbi-decoder that is ‘practically optimum’ ML-detection scheme to reduce computational complexity by surviving path selections We discuss first the conventional detector (by following the approach we already had to familiarize to denotations) Timo O. Korhonen, Helsinki University of Technology 11

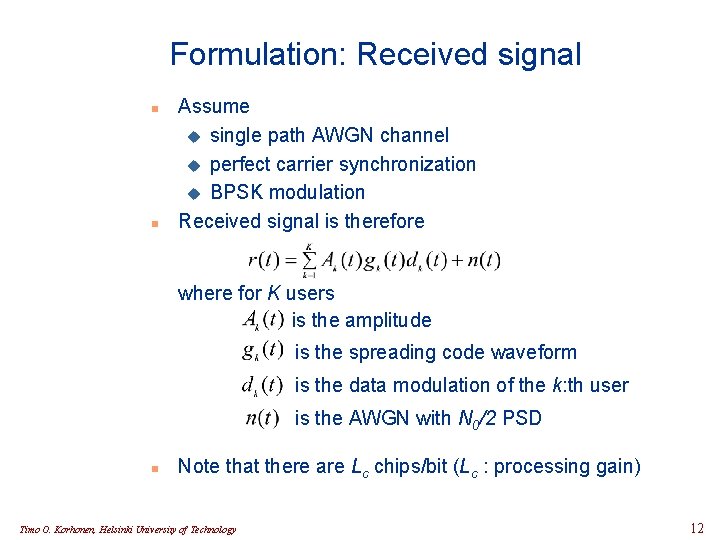
Formulation: Received signal n n Assume u single path AWGN channel u perfect carrier synchronization u BPSK modulation Received signal is therefore where for K users is the amplitude is the spreading code waveform is the data modulation of the k: th user is the AWGN with N 0/2 PSD n Note that there are Lc chips/bit (Lc : processing gain) Timo O. Korhonen, Helsinki University of Technology 12

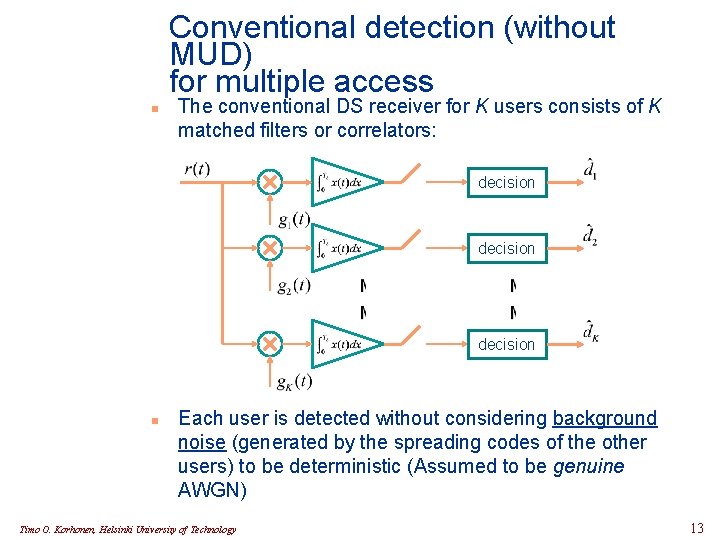
Conventional detection (without MUD) for multiple access n The conventional DS receiver for K users consists of K matched filters or correlators: decision n Each user is detected without considering background noise (generated by the spreading codes of the other users) to be deterministic (Assumed to be genuine AWGN) Timo O. Korhonen, Helsinki University of Technology 13

Output for the K: th user without MUD n n Detection quality depends on code cross- and autocorrelation Hence we require a large autocorrelation and small crosscorrelation (small ISI) The output for the K: th user consist of the signal, MAI and filtered Gaussian noise terms (as discussed earlier) Received SNR of this was considered earlier in this lecture Timo O. Korhonen, Helsinki University of Technology 14

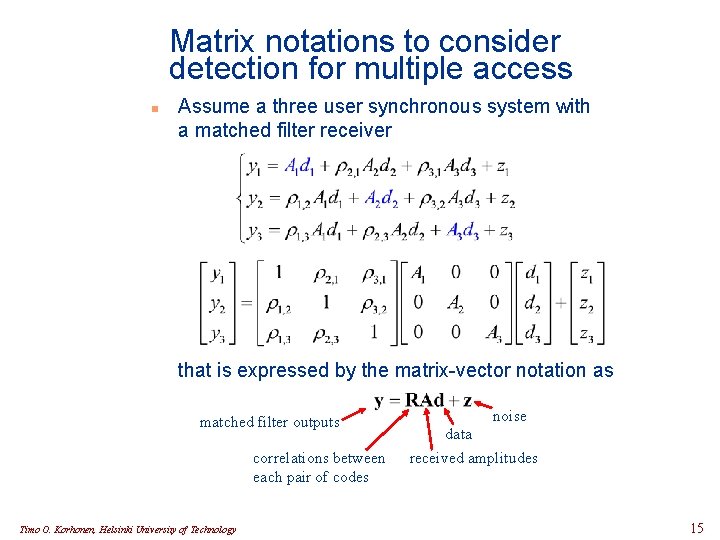
Matrix notations to consider detection for multiple access n Assume a three user synchronous system with a matched filter receiver that is expressed by the matrix-vector notation as matched filter outputs correlations between each pair of codes Timo O. Korhonen, Helsinki University of Technology noise data received amplitudes 15

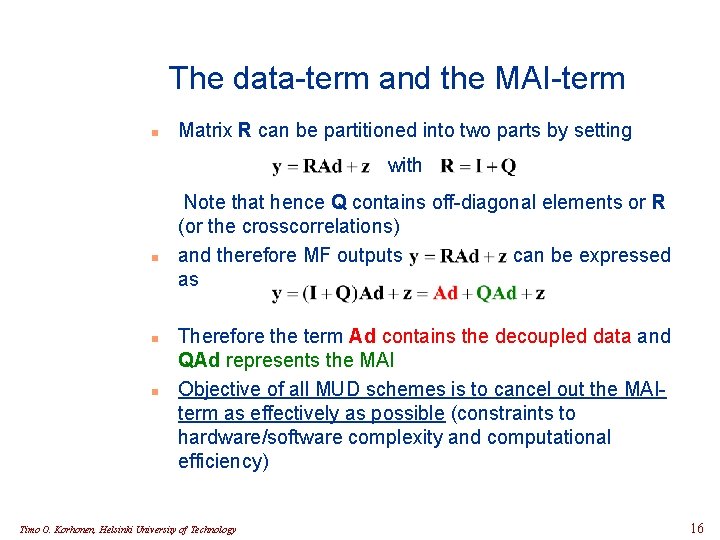
The data-term and the MAI-term n Matrix R can be partitioned into two parts by setting with n n n Note that hence Q contains off-diagonal elements or R (or the crosscorrelations) and therefore MF outputs can be expressed as Therefore the term Ad contains the decoupled data and QAd represents the MAI Objective of all MUD schemes is to cancel out the MAIterm as effectively as possible (constraints to hardware/software complexity and computational efficiency) Timo O. Korhonen, Helsinki University of Technology 16

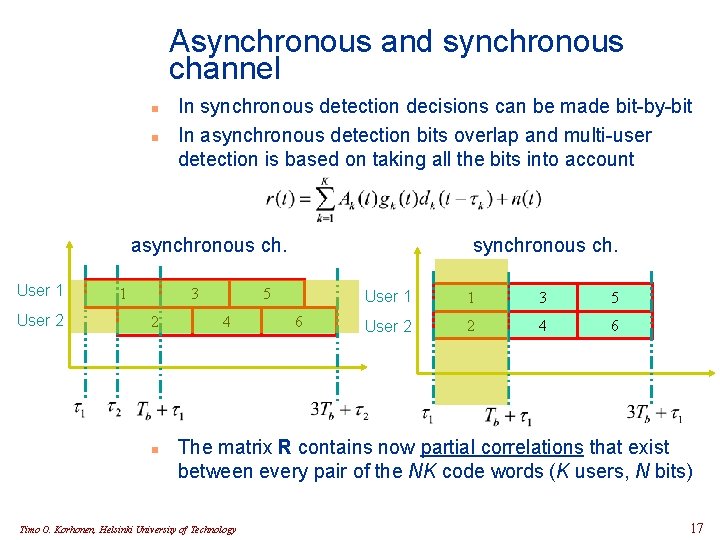
Asynchronous and synchronous channel n n In synchronous detection decisions can be made bit-by-bit In asynchronous detection bits overlap and multi-user detection is based on taking all the bits into account asynchronous ch. User 1 User 2 1 3 2 n synchronous ch. 5 4 6 User 1 1 3 5 User 2 2 4 6 The matrix R contains now partial correlations that exist between every pair of the NK code words (K users, N bits) Timo O. Korhonen, Helsinki University of Technology 17

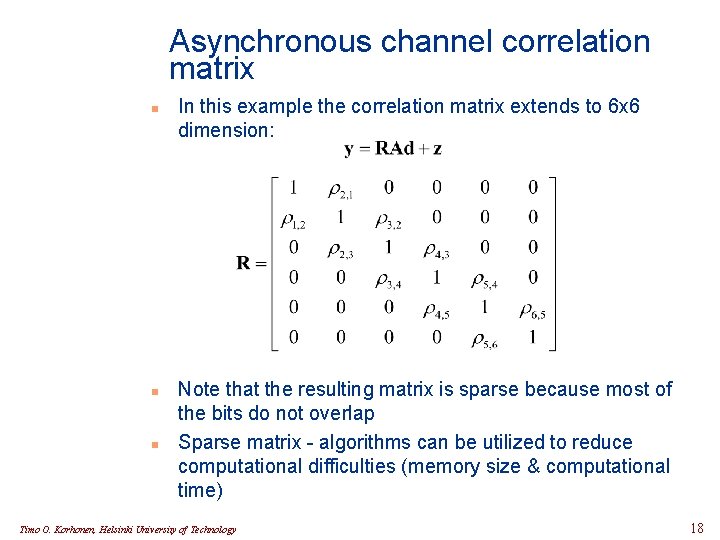
Asynchronous channel correlation matrix n n n In this example the correlation matrix extends to 6 x 6 dimension: Note that the resulting matrix is sparse because most of the bits do not overlap Sparse matrix - algorithms can be utilized to reduce computational difficulties (memory size & computational time) Timo O. Korhonen, Helsinki University of Technology 18

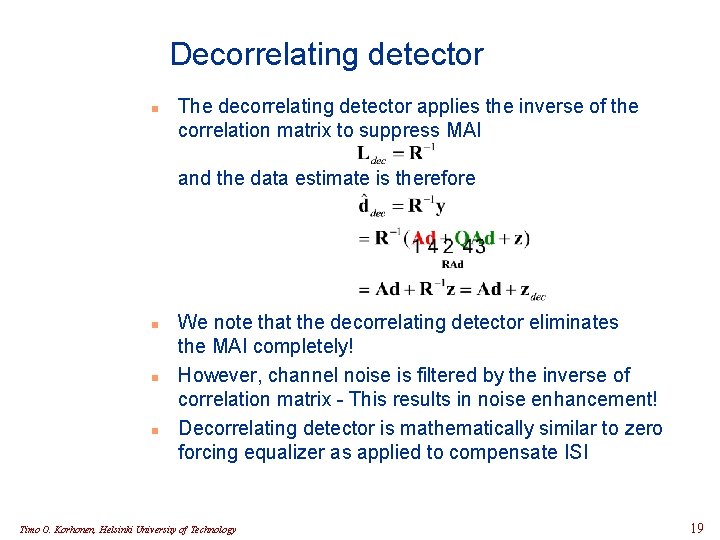
Decorrelating detector n The decorrelating detector applies the inverse of the correlation matrix to suppress MAI and the data estimate is therefore n n n We note that the decorrelating detector eliminates the MAI completely! However, channel noise is filtered by the inverse of correlation matrix - This results in noise enhancement! Decorrelating detector is mathematically similar to zero forcing equalizer as applied to compensate ISI Timo O. Korhonen, Helsinki University of Technology 19

Decorrelating detector properties summarized n n n PROS: Provides substantial performance improvement over conventional detector under most conditions Does not need received amplitude estimation Has computational complexity substantially lower that the ML detector (linear with respect of number of users) Corresponds ML detection when the energies of the users are not know at the receiver Has probability of error independent of the signal energies n n n CONS: Noise enhancement High computational complexity in inverting matrix R Timo O. Korhonen, Helsinki University of Technology 20

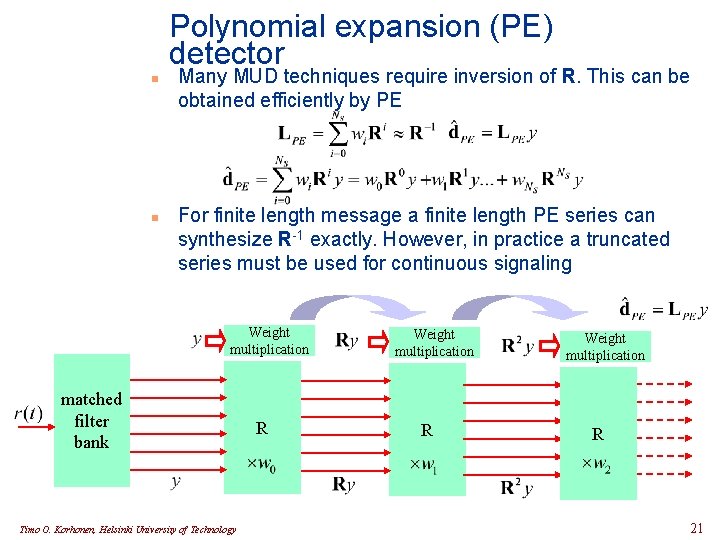
Polynomial expansion (PE) detector n n Many MUD techniques require inversion of R. This can be obtained efficiently by PE For finite length message a finite length PE series can synthesize R-1 exactly. However, in practice a truncated series must be used for continuous signaling Weight multiplication matched filter bank Timo O. Korhonen, Helsinki University of Technology R Weight multiplication R 21

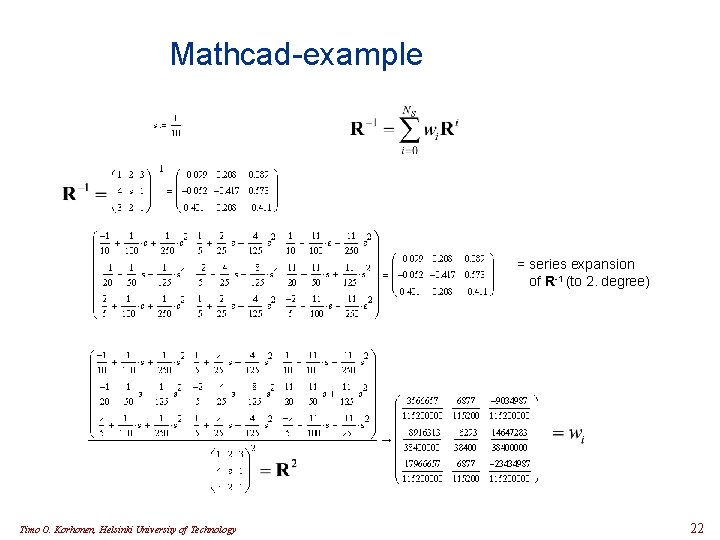
Mathcad-example = series expansion of R-1 (to 2. degree) Timo O. Korhonen, Helsinki University of Technology 22

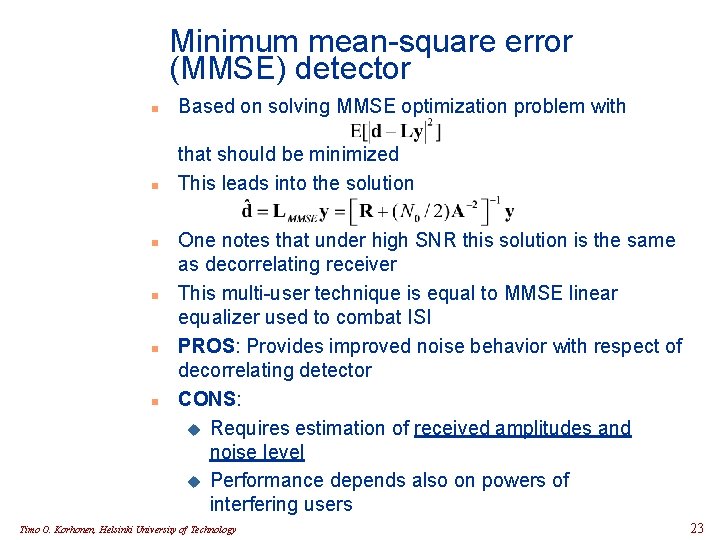
Minimum mean-square error (MMSE) detector n Based on solving MMSE optimization problem with n that should be minimized This leads into the solution n n One notes that under high SNR this solution is the same as decorrelating receiver This multi-user technique is equal to MMSE linear equalizer used to combat ISI PROS: Provides improved noise behavior with respect of decorrelating detector CONS: u Requires estimation of received amplitudes and noise level u Performance depends also on powers of interfering users Timo O. Korhonen, Helsinki University of Technology 23

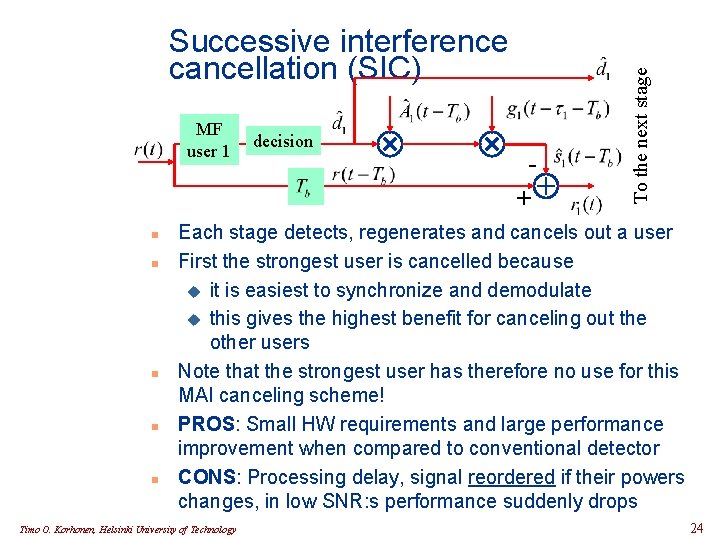
MF user 1 n n n decision + To the next stage Successive interference cancellation (SIC) Each stage detects, regenerates and cancels out a user First the strongest user is cancelled because u it is easiest to synchronize and demodulate u this gives the highest benefit for canceling out the other users Note that the strongest user has therefore no use for this MAI canceling scheme! PROS: Small HW requirements and large performance improvement when compared to conventional detector CONS: Processing delay, signal reordered if their powers changes, in low SNR: s performance suddenly drops Timo O. Korhonen, Helsinki University of Technology 24

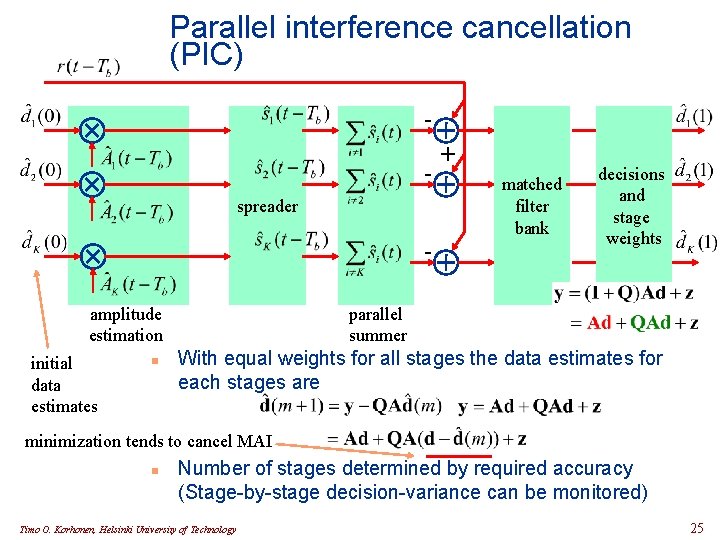
Parallel interference cancellation (PIC) spreader amplitude estimation initial data estimates n + matched filter bank decisions and stage weights parallel summer With equal weights for all stages the data estimates for each stages are minimization tends to cancel MAI n Number of stages determined by required accuracy (Stage-by-stage decision-variance can be monitored) Timo O. Korhonen, Helsinki University of Technology 25

PIC properties n n PIC variations n n SIC performs better in non-power controlled channels PIC performs better in power balanced channels Using decorrelating detector as the first stage u improving first estimates improves total performance u simplifies system analysis Doing a partial MAI cancellation at each stage with the amount of cancellation increasing for each successive stage u tentative decisions of the earlier stages are less reliable - hence they should have a lower weight u very large performance improvements have achieved by this method u probably the most promising suboptimal MUD Timo O. Korhonen, Helsinki University of Technology 26

Benefits and limitations of multiuser detection PROS: n n Significant capacity improvement - usually signals of the own cell are included More efficient uplink spectrum utilization - hence for downlink a wider spectrum may be allocated Reduced MAI and near-far effect - reduced precision requirements for power control More efficient power utilization because near-far effect is reduced CONS: n n If the neighboring cells are not included interference cancellation efficiency is greatly reduced Interference cancellation is very difficult to implement in downlink reception where, however, larger capacity requirements exist (DL traffic tends to be larger) Timo O. Korhonen, Helsinki University of Technology 27