Multiple Schemes for Mobile Payment Authentication Using QR

Multiple Schemes for Mobile Payment Authentication Using QR Code and Visual Cryptography Source: Mobile Information Systems, vol. 2017, 2017. Authors: Lu Jianfeng, Yang Zaorang, Li Lina, Yuan Wenqiang, Li Li, Chang Chin-Chen Speaker: Huang. Peng-Cheng Date: 1/16/2022
Outline • Introduction • Related Works • Proposed Scheme • Scheme I Based on QR Module and XOR Mechanism of RS • Scheme II Based on VCS and Fusion Strategy of Background Image by XOR Mechanism of RS • Scheme III Based on VCS and Fusion Strategy of Background Image with Error Correction Mechanism of QR • Conclusions • Comments
Introduction—motivation(1/2)
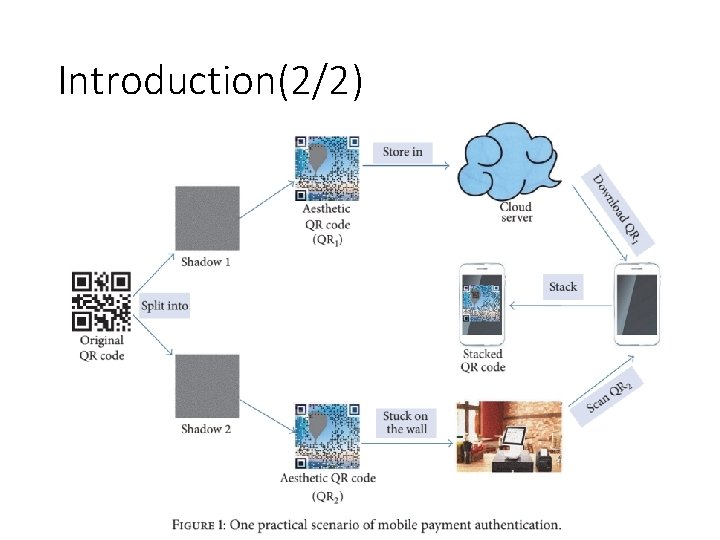
Introduction(2/2)
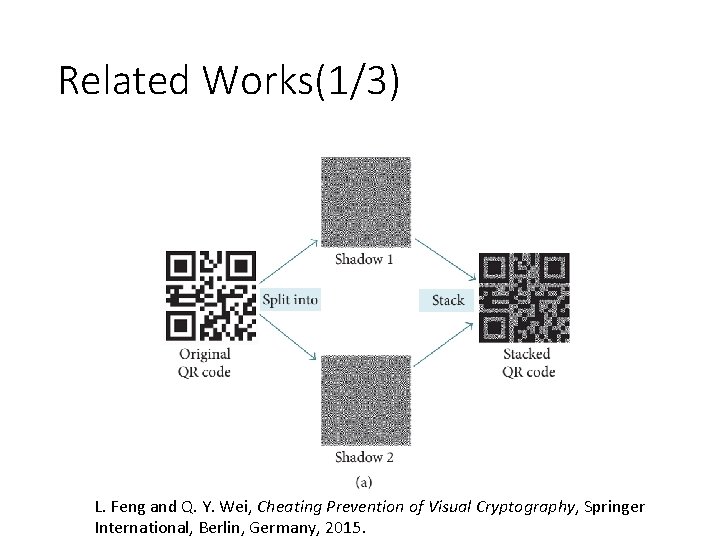
Related Works(1/3) L. Feng and Q. Y. Wei, Cheating Prevention of Visual Cryptography, Springer International, Berlin, Germany, 2015.
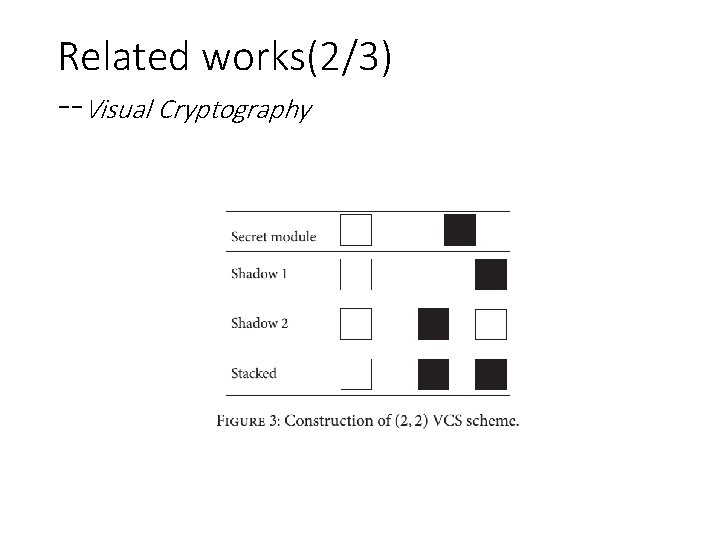
Related works(2/3) --Visual Cryptography
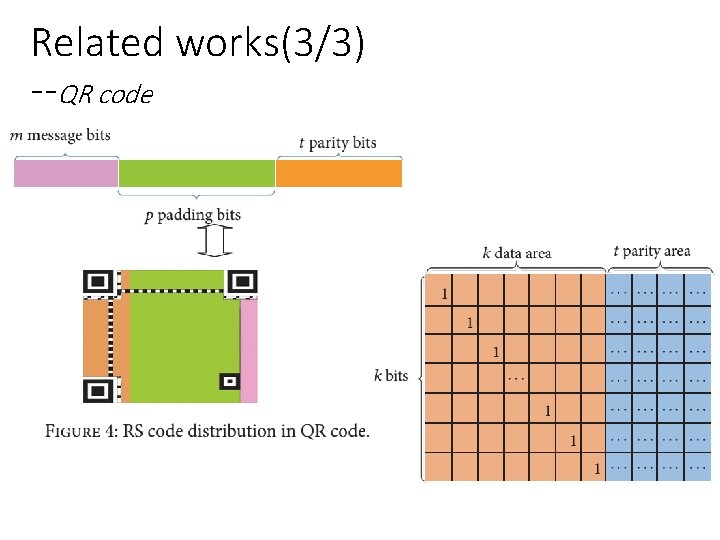
Related works(3/3) --QR code
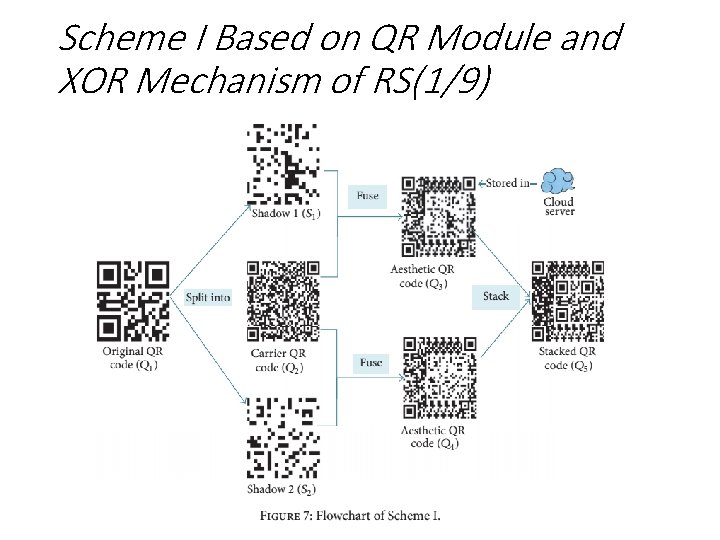
Scheme I Based on QR Module and XOR Mechanism of RS(1/9)
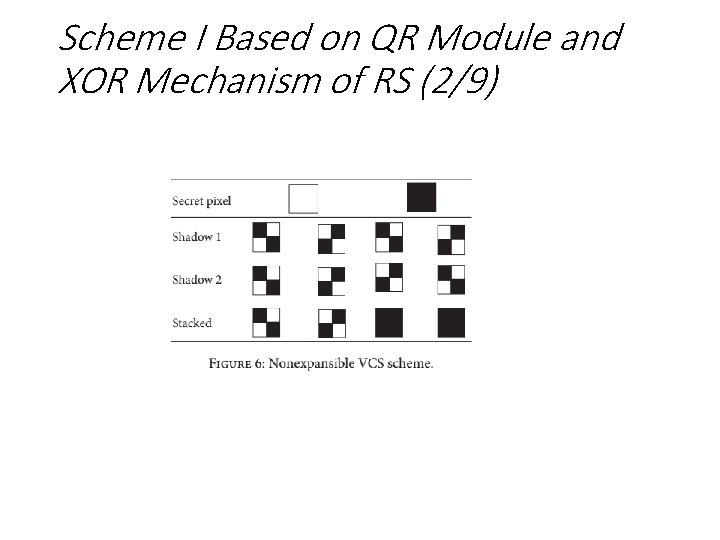
Scheme I Based on QR Module and XOR Mechanism of RS (2/9)
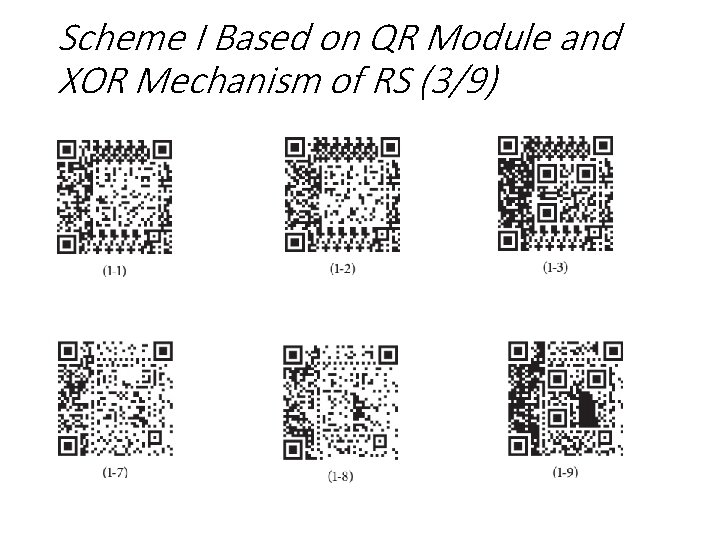
Scheme I Based on QR Module and XOR Mechanism of RS (3/9)
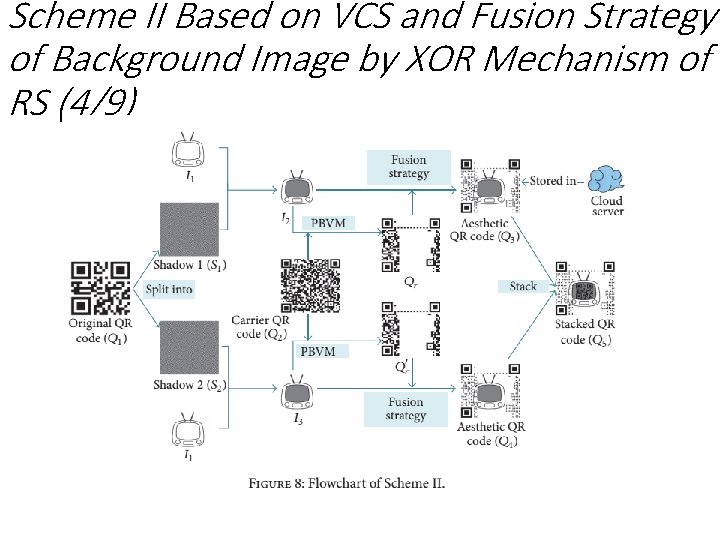
Scheme II Based on VCS and Fusion Strategy of Background Image by XOR Mechanism of RS (4/9)
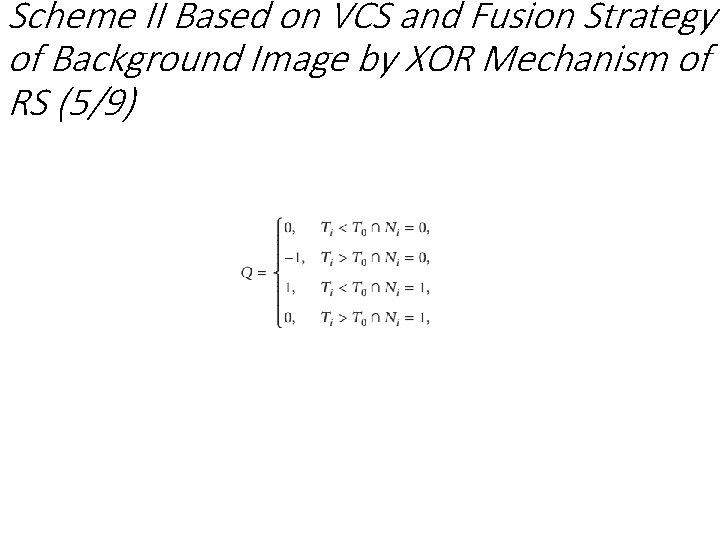
Scheme II Based on VCS and Fusion Strategy of Background Image by XOR Mechanism of RS (5/9)
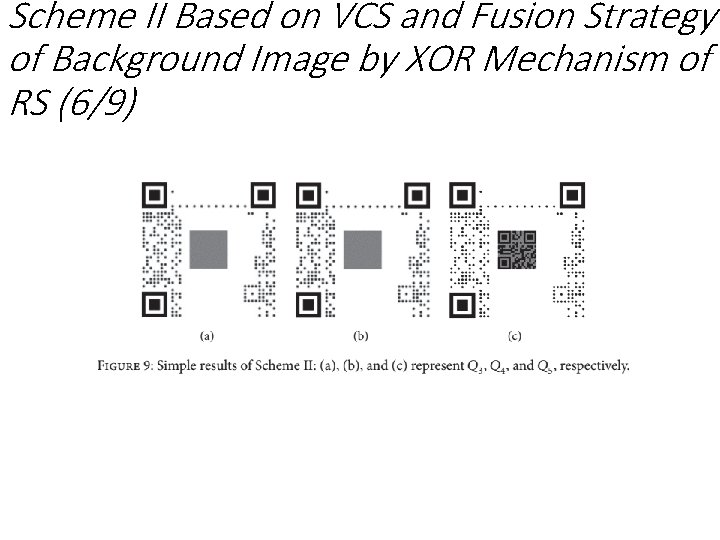
Scheme II Based on VCS and Fusion Strategy of Background Image by XOR Mechanism of RS (6/9)
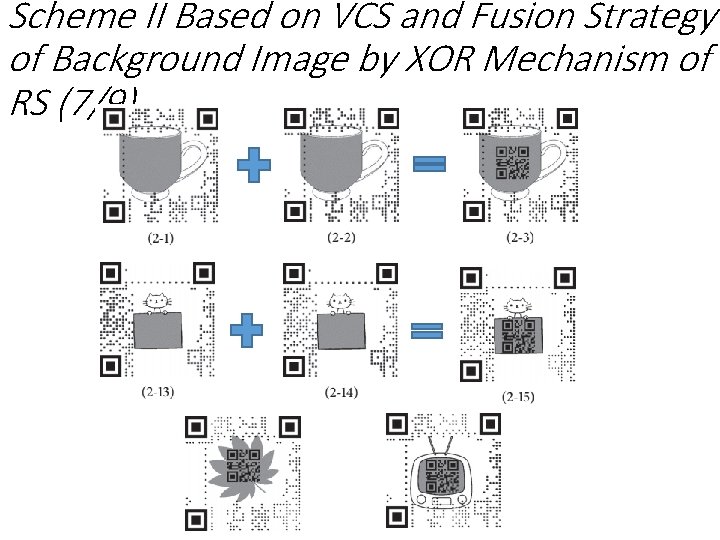
Scheme II Based on VCS and Fusion Strategy of Background Image by XOR Mechanism of RS (7/9)
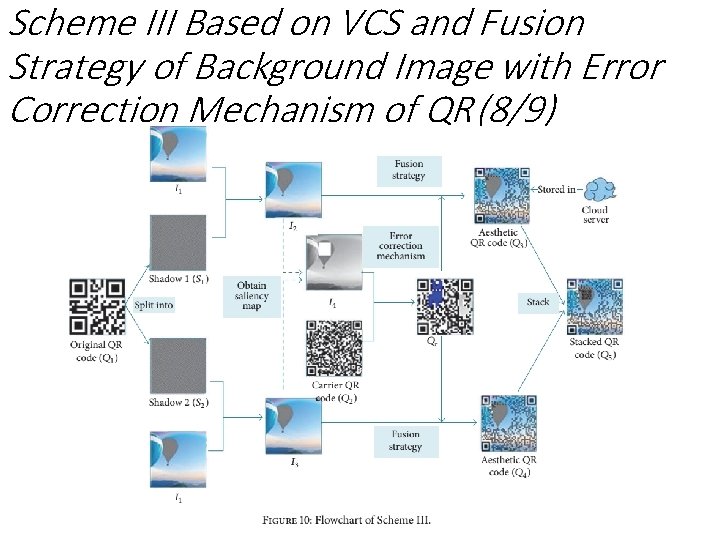
Scheme III Based on VCS and Fusion Strategy of Background Image with Error Correction Mechanism of QR (8/9)

Scheme III Based on VCS and Fusion Strategy of Background Image with Error Correction Mechanism of QR (9/9)

Conclusions The hiding region looks like garbled. Attackers are impossible to recover the secret information from each individual shadow.
comments 1. Low capacity.
- Slides: 18