Multiple Access Covert Channels Ira Moskowitz Naval Research









- Slides: 18

Multiple Access Covert Channels Ira Moskowitz Naval Research Lab Richard Newman Univ. of Florida moskowitz@nrl. itd. navy. mil nemo@cise. ufl. edu

Focus • Review covert channels from high assurance computing and anonymity • Define quasi-anonymous channel • Review analysis of single sender DMC • Analyze 2 -sender DMC

Covert Channels • CC = communication contrary to design • Storage channels and timing channels • Storage channel capacity given by mutual information, in bits per symbol • Timing channel capacity analysis requires optimizing ratio of mutual information to expected time cost

Storage Channel Example • File system full/not full • High fills/leaves space in FS to signal 1 or 0 • Low tries to obtain space and fails or succeeds to “read” 1 or 0 • Low returns system to previous state

Timing Channel Example • High uses full time quantum in time sharing host to send 1, gives up CPU early to send 0 • Low measures time gaps between accesses to “read” 1 or 0

Anonymity Systems • • • Started with Chaum Mixes Mix receives encrypted, padded msg Decrypts/re-encrypts padded msg Delays forwarding msg Scrambles order of msg forwarding

Mixes • Mix may be timed (count number of msgs forwarded each time it fires) • Mix may fire when threshold reached (count time between firings) • Mixes may be chained • Studied timed Mix-firewalls and covert channels – now for threshold Mix-firewalls

Mix-firewall CC Model • • Alice behind M-F Eve listening to output of M-F Clueless senders behind M-F Each sender (Alice or Clueless) may either send or not send a msg each tick • Alice modulates her behavior to try to communicate with Eve

Channel Model • • • Discrete storage channel Each clueless sends 0 or 1 msg per tick Clueless are i. i. d. Bernouli random vars Alice sends 0 or 1 msg per tick Eve counts msgs per Mix firing Clueless act as noise, rate decreases to zero as N increases (for fixed p)

Two Transmitter Model • Now two Alices, Alice 1 and Alice 2 • Each Alice has a quasi-anomymous channel to Eve • Alices act as noise with respect to each other

NRL Pump • NRL Network Pump considered multiple senders before • Lows send to Highs, with the timing of ACKs forming a CC from Highs to Lows • Pump modulates ACK timing to reduce the CC rate (but not eliminate it) • Highs interfere with each other’s timing • Pump uses timing channels – can’t apply

Degree of Collusion • If Alices work perfectly together, then can achieve C=log 3 bits/tick data rate (assuming no clueless) • “Existence assumption” - assume Alices know of each other (stationary), and prearrange coding, but do not collude once transmission begins

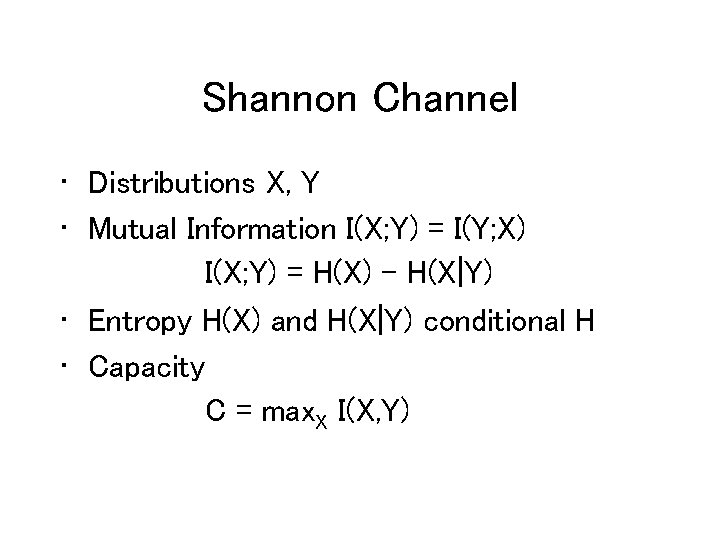
Shannon Channel • Distributions X, Y • Mutual Information I(X; Y) = I(Y; X) I(X; Y) = H(X) – H(X|Y) • Entropy H(X) and H(X|Y) conditional H • Capacity C = max. X I(X, Y)

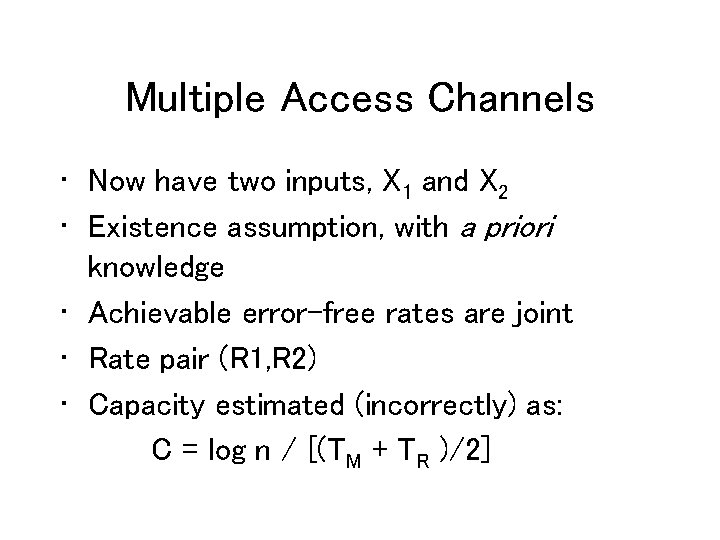
Multiple Access Channels • Now have two inputs, X 1 and X 2 • Existence assumption, with a priori knowledge • Achievable error-free rates are joint • Rate pair (R 1, R 2) • Capacity estimated (incorrectly) as: C = log n / [(TM + TR )/2]

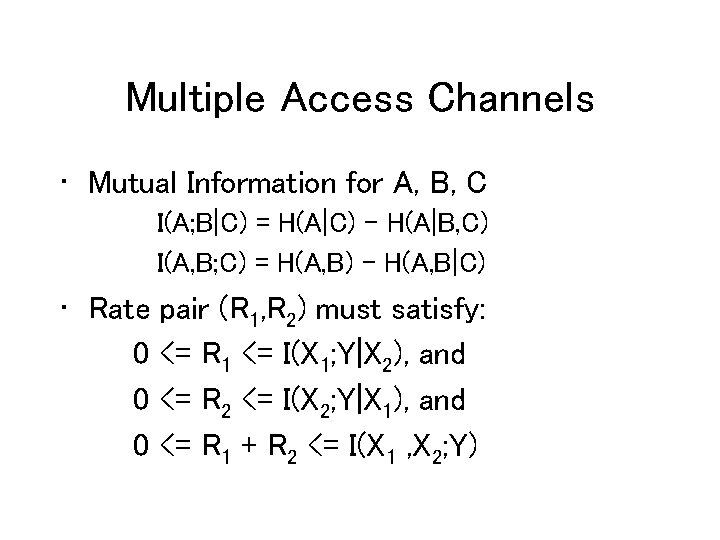
Multiple Access Channels • Mutual Information for A, B, C I(A; B|C) = H(A|C) – H(A|B, C) I(A, B; C) = H(A, B) – H(A, B|C) • Rate pair (R 1, R 2) must satisfy: 0 <= R 1 <= I(X 1; Y|X 2), and 0 <= R 2 <= I(X 2; Y|X 1), and 0 <= R 1 + R 2 <= I(X 1 , X 2; Y)

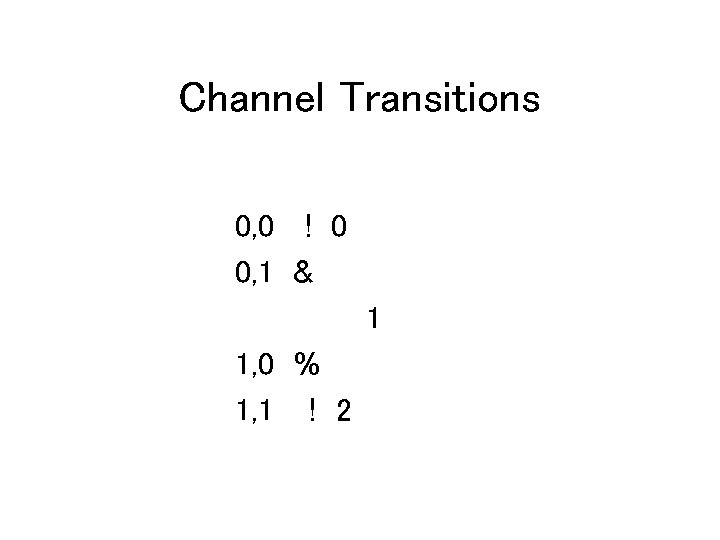
Channel Transitions 0, 0 ! 0 0, 1 & 1 1, 0 % 1, 1 ! 2

Collaborating Alices • Can conspire to send data at rate 3/2 • Max possible is log 2 3 = 1. 58 • With feedback, can do better than 3/2: each at rate. 76! (Gaarder & Wolf)

Conclusions • Introduced multiple access channels into analysis of covert channels • Analyzed simple (noiseless) channel with two Alices • Noted effects of varying levels of collusion • Noted difficulties with timing channels • Can’t study CCs in isolation!