Multimodal Graph Analysis of Cyber Attacks Nirnimesh Ghose
Multimodal Graph Analysis of Cyber Attacks Nirnimesh Ghose, Loukas Lazos, and Jerzy Rozenblit Ronald Breiger Electrical and Computer Engineering, University of Arizona, Tucson School of Sociology, University of Arizona, Tucson 2019 Spring Simulation Conference Tucson, AZ
Cyber Attacks – Web Application Attacks Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 2
Cyber Attack – Ransomware Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 3
Cyber Attack – Espionage Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 4
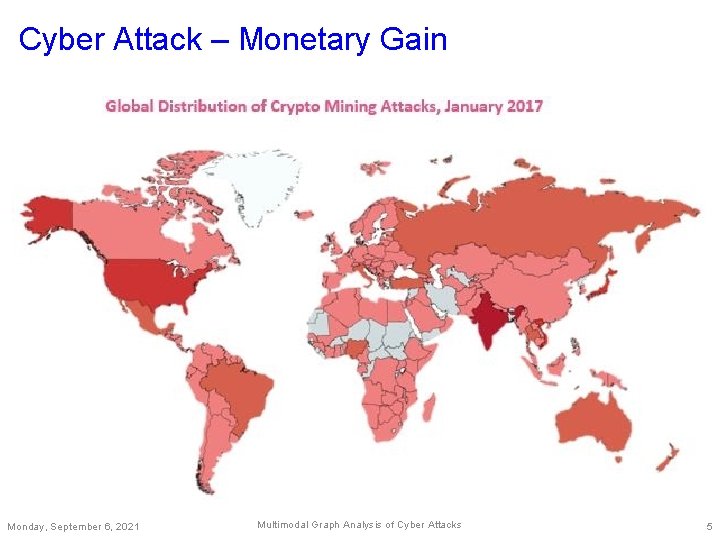
Cyber Attack – Monetary Gain Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 5
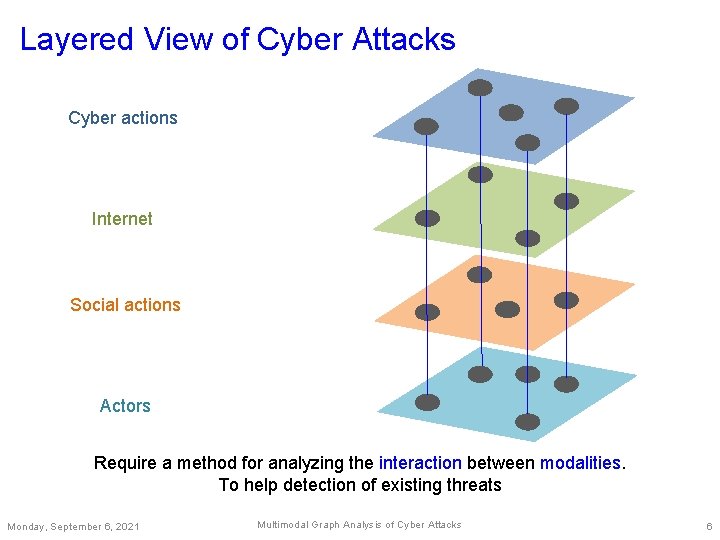
Layered View of Cyber Attacks Cyber actions Internet Social actions Actors Require a method for analyzing the interaction between modalities. To help detection of existing threats Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 6

Challenges in Analyzing Cyber Attacks Point-based analyzing approach manually scrutinizing evidence time elapsed during analysis renders the results useless State-of-the-art of cyber-analysis methods have limited predictive and attribution capabilities* relies on evidence produced by post-event electronic trace analysis** As a result, cyber-attacks in most cases, are discovered well after the attack has terminated. *Xie, Peng, et al. "Using Bayesian networks for cyber security analysis. " 2010 IEEE/IFIP International Conference on Dependable Systems & Networks (DSN). IEEE, 2010. *Michael, James Bret, Thomas C. Wingfield, and Duminda Wijesekera. "Measured responses to cyber attacks using Schmitt analysis: a case study of attack scenarios for a software-intensive system. " Proceedings 27 th Annual International Computer Software and Applications Conference. COMPAC 2003. IEEE, 2003. **Choo, Kim-Kwang Raymond. "The cyber threat landscape: Challenges and future research directions. " Computers & Security 30. 8 (2011): 719 -731. **Hutchings, Alice. "Crime from the keyboard: organised cybercrime, co-offending, initiation and knowledge transmission. " Crime, Law and Social Change 62. 1 (2014): 1 -20. Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 7

Goals and Contributions Goals: Understand why a cyber-attack has occurred, when it occured and by whom it was perpetrated Determine the identities, values, incentives, and communication modes of the involved individuals Contributions: Developed comprehensive models of cyber-attack features using featureextraction techniques on diverse data sources Classified adversarial groups based on their feature similarities Enhanced the group classification using analytic techniques from social network science Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 8
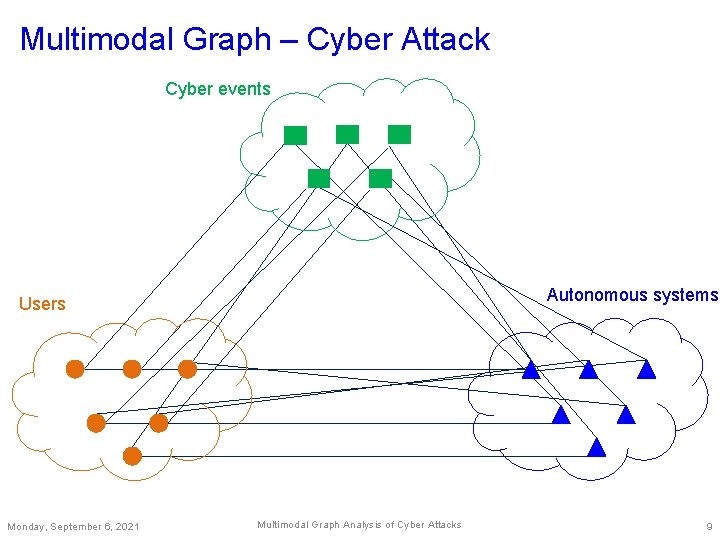
Multimodal Graph – Cyber Attack Cyber events Autonomous systems Users Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 9
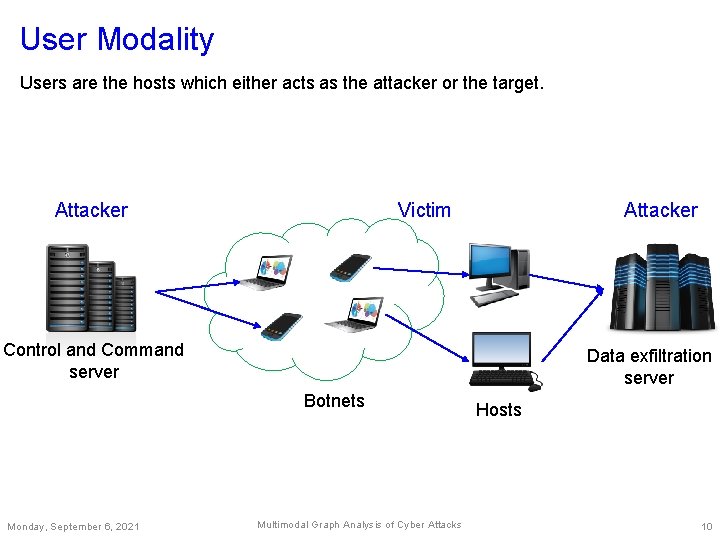
User Modality Users are the hosts which either acts as the attacker or the target. Attacker Victim Control and Command server Data exfiltration server Botnets Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks Hosts 10
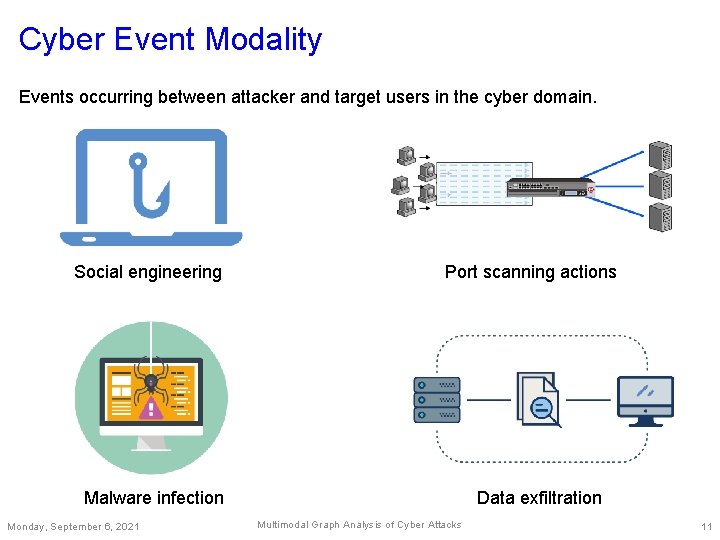
Cyber Event Modality Events occurring between attacker and target users in the cyber domain. Social engineering Port scanning actions Malware infection Monday, September 6, 2021 Data exfiltration Multimodal Graph Analysis of Cyber Attacks 11
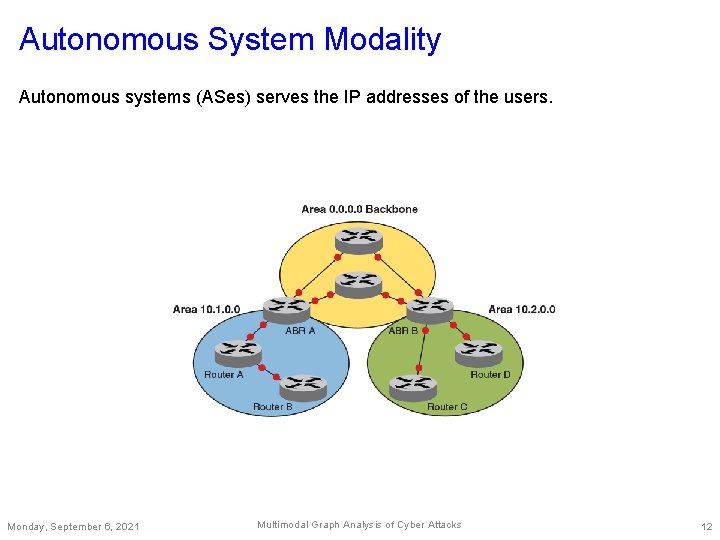
Autonomous System Modality Autonomous systems (ASes) serves the IP addresses of the users. Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 12
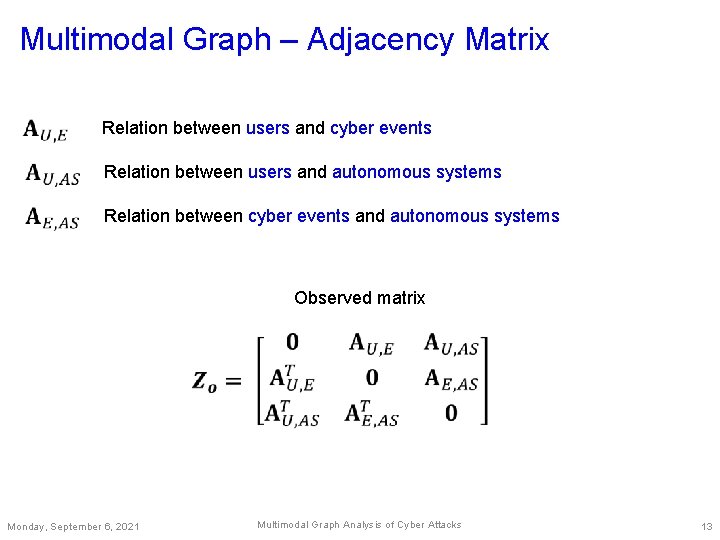
Multimodal Graph – Adjacency Matrix Relation between users and cyber events Relation between users and autonomous systems Relation between cyber events and autonomous systems Observed matrix Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 13
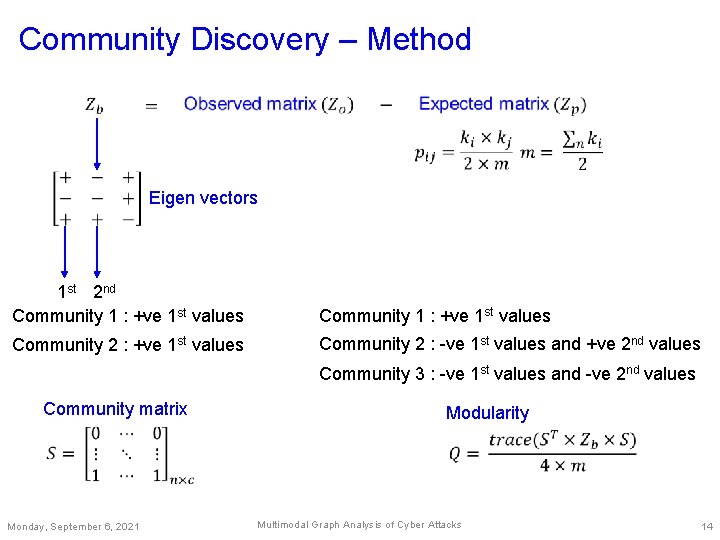
Community Discovery – Method Eigen vectors 1 st 2 nd Community 1 : +ve 1 st values Community 2 : -ve 1 st values and +ve 2 nd values Community 3 : -ve 1 st values and -ve 2 nd values Community matrix Monday, September 6, 2021 Modularity Multimodal Graph Analysis of Cyber Attacks 14
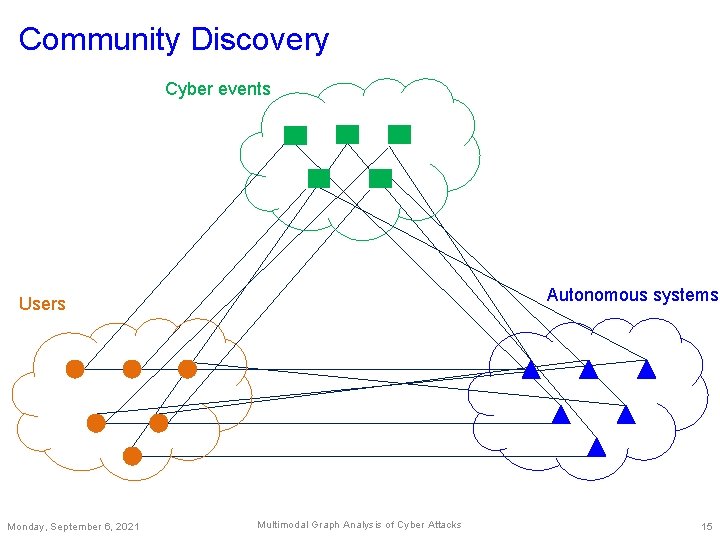
Community Discovery Cyber events Autonomous systems Users Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 15
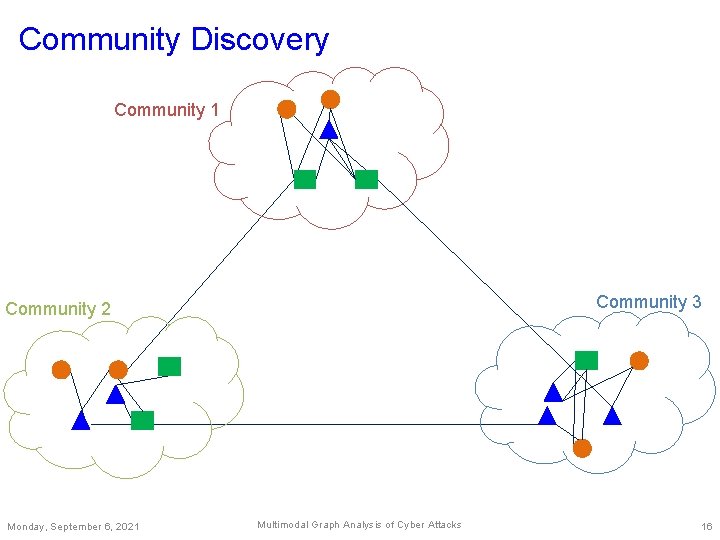
Community Discovery Community 1 Community 3 Community 2 Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 16
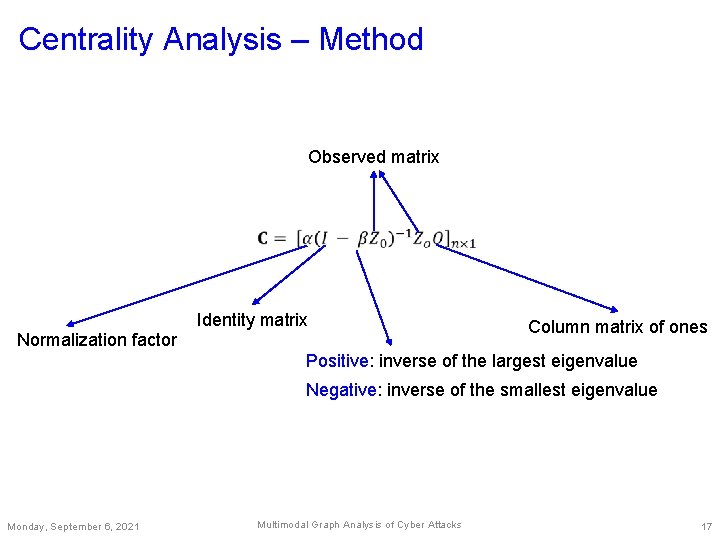
Centrality Analysis – Method Observed matrix Identity matrix Normalization factor Column matrix of ones Positive: inverse of the largest eigenvalue Negative: inverse of the smallest eigenvalue Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 17
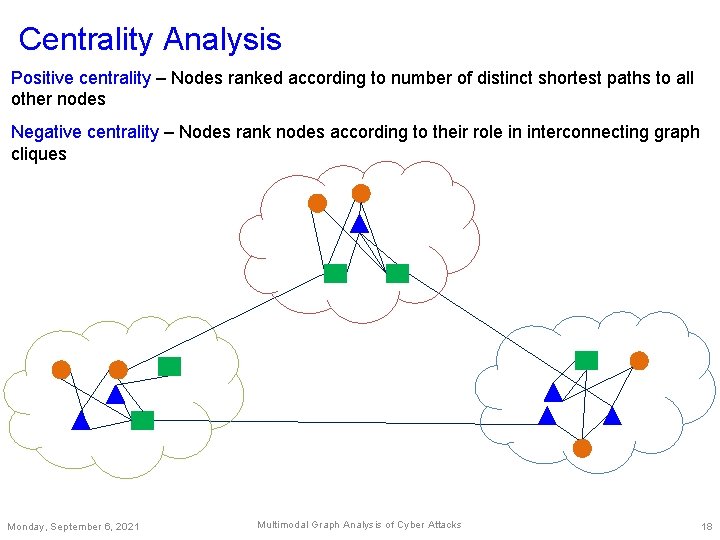
Centrality Analysis Positive centrality – Nodes ranked according to number of distinct shortest paths to all other nodes Negative centrality – Nodes rank nodes according to their role in interconnecting graph cliques Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 18

Implementation of community and centrality to real world cyber attacks. Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 19
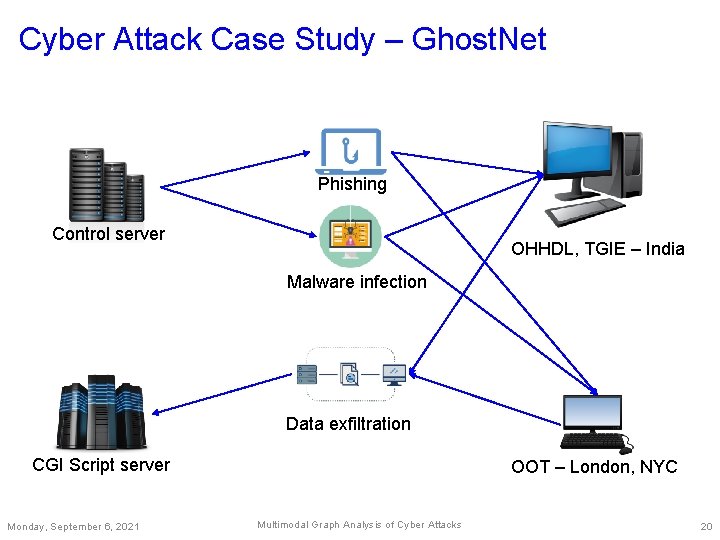
Cyber Attack Case Study – Ghost. Net Phishing Control server OHHDL, TGIE – India Malware infection Data exfiltration CGI Script server Monday, September 6, 2021 OOT – London, NYC Multimodal Graph Analysis of Cyber Attacks 20
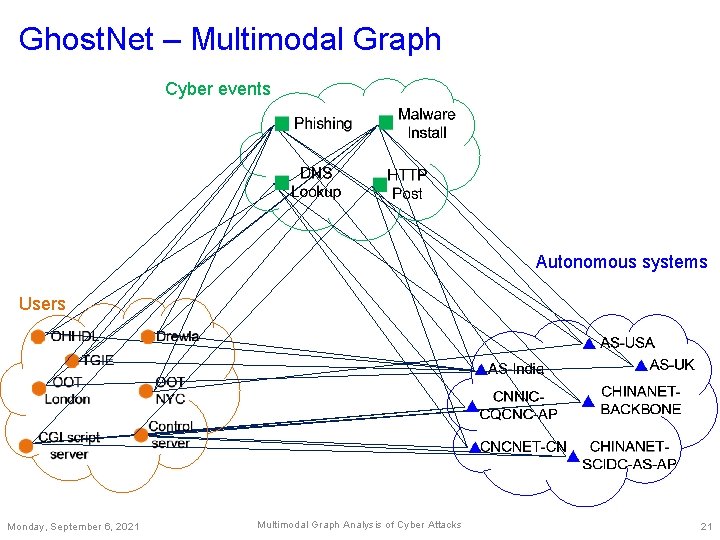
Ghost. Net – Multimodal Graph Cyber events Autonomous systems Users Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 21
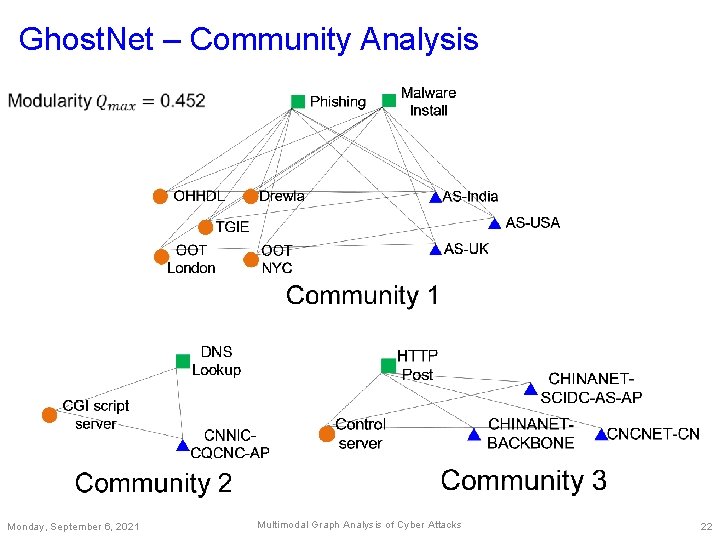
Ghost. Net – Community Analysis Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 22
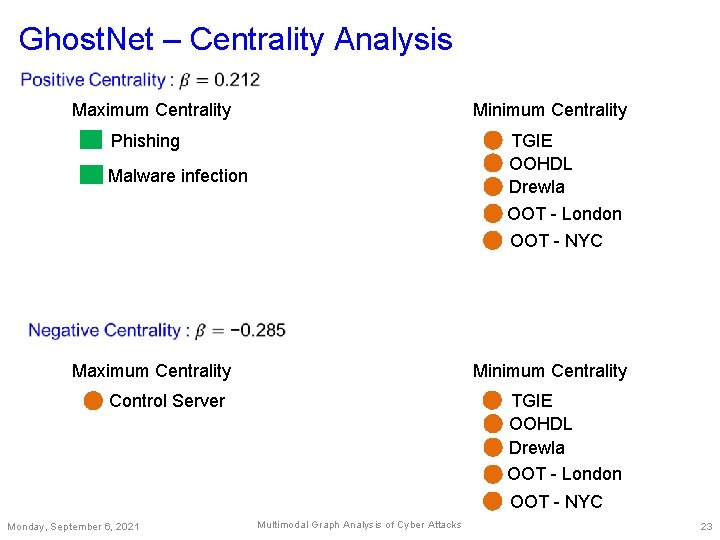
Ghost. Net – Centrality Analysis Maximum Centrality Minimum Centrality Phishing TGIE OOHDL Drewla OOT - London Malware infection OOT - NYC Maximum Centrality Minimum Centrality Control Server TGIE OOHDL Drewla OOT - London OOT - NYC Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 23
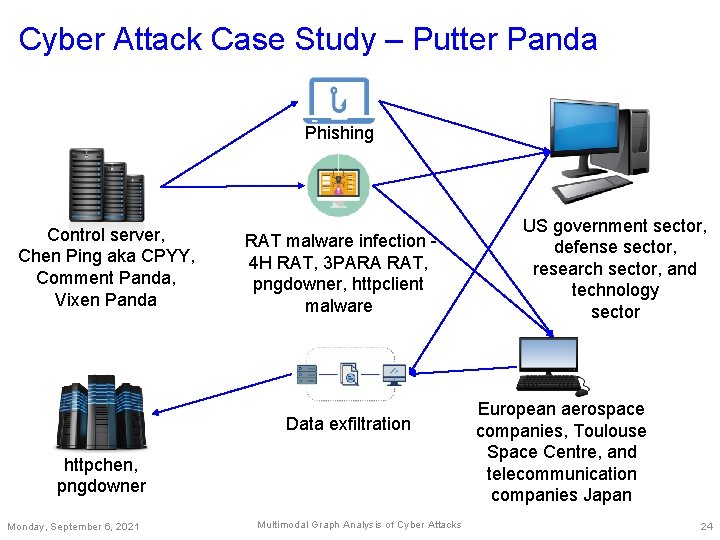
Cyber Attack Case Study – Putter Panda Phishing Control server, Chen Ping aka CPYY, Comment Panda, Vixen Panda RAT malware infection 4 H RAT, 3 PARA RAT, pngdowner, httpclient malware Data exfiltration httpchen, pngdowner Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks US government sector, defense sector, research sector, and technology sector European aerospace companies, Toulouse Space Centre, and telecommunication companies Japan 24

Putter Panda – Multimodal Graph Users – Victims: US government sector, defense sector, the US research sector and technology sector, European aerospace companies, the Toulouse Space Centre, and telecommunication companies Japan Attackers: C 2 server, Chen Ping aka CPYY, httpchen, Comment Panda, Vixen Panda, and pngdowner Cyber events – RAT malware including 4 H RAT, 3 PARA RAT, pngdowner and httpclient malware (39 event nodes) Autonomous systems – Victim: AS-USA, AS-Europe, and AS-Japan Attackers: 15 ASes in the USA 5 in the Taiwan 4 in the Korean peninsula, 2 in the Netherlands 1 each in Denmark, Kazakhstan, Fiji, Thailand, China, Japan, Russia, Great Britain, and Indonesia Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 25

Putter Panda – Community Analysis Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 26
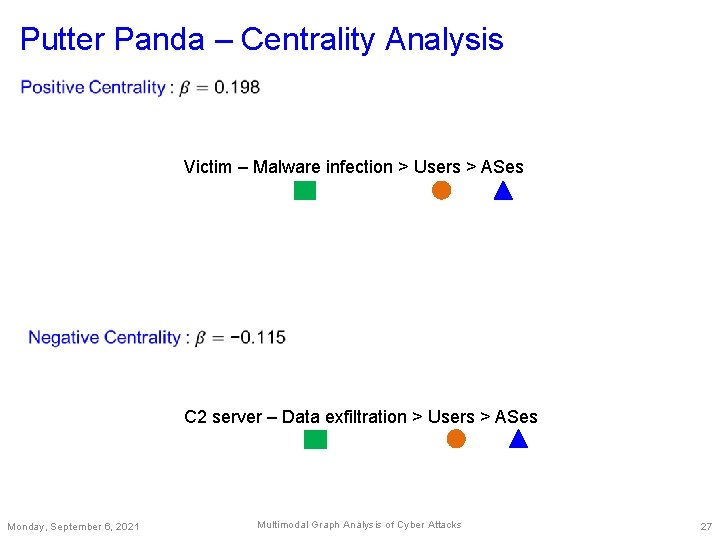
Putter Panda – Centrality Analysis Victim – Malware infection > Users > ASes C 2 server – Data exfiltration > Users > ASes Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 27

Summary Modeled analyzed cyber attacks using a tripartite graph – users, cyber events and autonomous systems Analyzed community identify nodes of different modalities that exhibited strong correlation and centrality to rank the nodes according to their importance in the attack Findings demonstrated a clear distinction between the victim hosts and the ASes that serve them, the C 2 servers that regulated the attack, and the data exfiltration process. Centrality analysis revealed the key nodes that facilitated the attack, a role assumed by the C 2 servers Future work - Propose to embed the derived properties as ground truth to generate synthetic data, and study the data to derive new techniques for detecting attacks in realtime. Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 28

Thank you! & Questions? Monday, September 6, 2021 Multimodal Graph Analysis of Cyber Attacks 29
- Slides: 29