MSS Chapter 3 Shopping carts Payment gateways Mc













- Slides: 19

MSS*: Chapter 3 Shopping carts & Payment gateways * Mc. Clure, Stuart, Saumil Shah, and Shreeraj Shah. Web Hacking: attacks and defense. Addison Wesley. 2003. Web Security

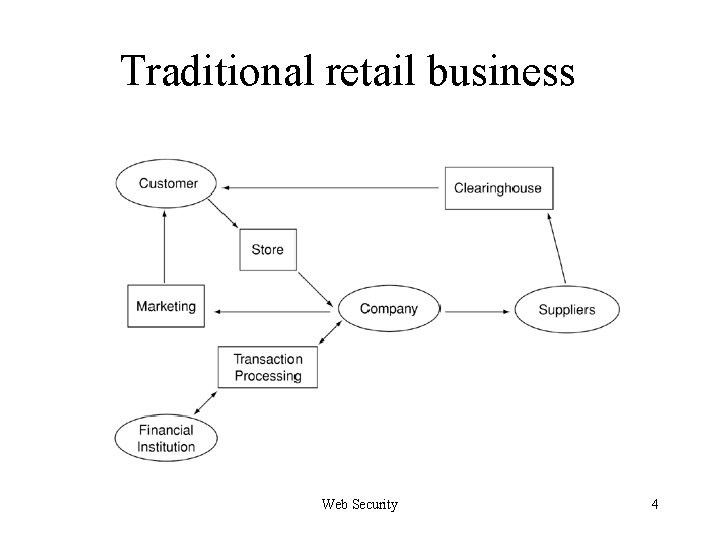
Evolution of Shopping Farmers’ market Store shopping Supermarket Catalog shopping q On-line shopping: combines the experience of both in-store shopping and catalog shopping q + Web-based applications offer more interactivity and multimedia presentation than a printed catalog. + Web-based applications typically provide searching capabilities, which are not available in the traditional in -store shopping or catalog shopping. + Web-based applications can be tailored to different shopping styles. “no-pressure” shopping experience Q: Are there any drawbacks or specific requirements? Web Security 2

Evolution of Shopping q What are the factors that may drive potential customers away from web-based shopping? Is concern over security real? - Ease of use - Anything else? - Web Security 3

Traditional retail business Web Security 4

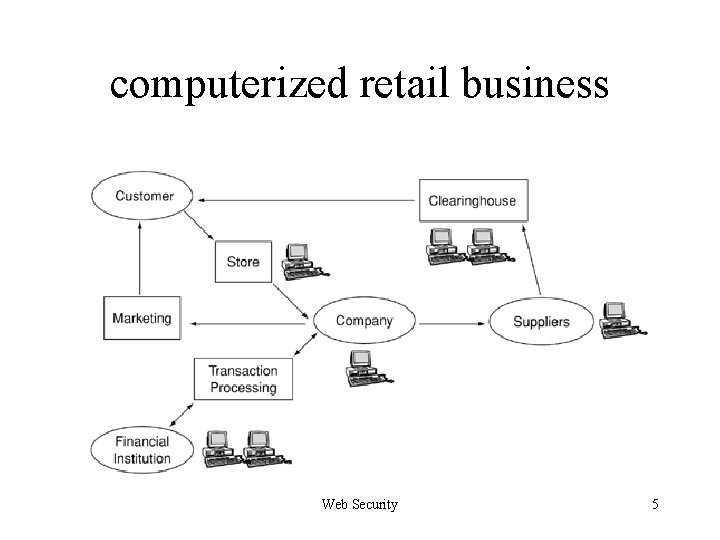
computerized retail business Web Security 5

E-commerce model Web Security 6

E-commerce model q Characteristics: § A web portal represents the company’s web identity. § The portal serves as an entry into the electronic store. § A web site hosting multiple applications that interact with an array of servers (other web sites, financial processing, transaction processing, back-end databases, etc. ) q Q: What makes an e-commerce different from a computerized retail business? Web Security 7

E-commerce model q An exercise: The e-commerce model diagram is not really an ER diagram. Modify/refine the model and turn it into a real ER or EER diagram. q Hint: Add relationships q Part of your project: preliminary design Web Security 8

E-commerce model q The need for peer-to-peer communications q An extranet is an inter-network linking different companies’ internal network. q What are the requirements of an intercompany web-based application? Trust! § Authentication § Non-repudiation § Anything else? § q Web-services Web Security 9

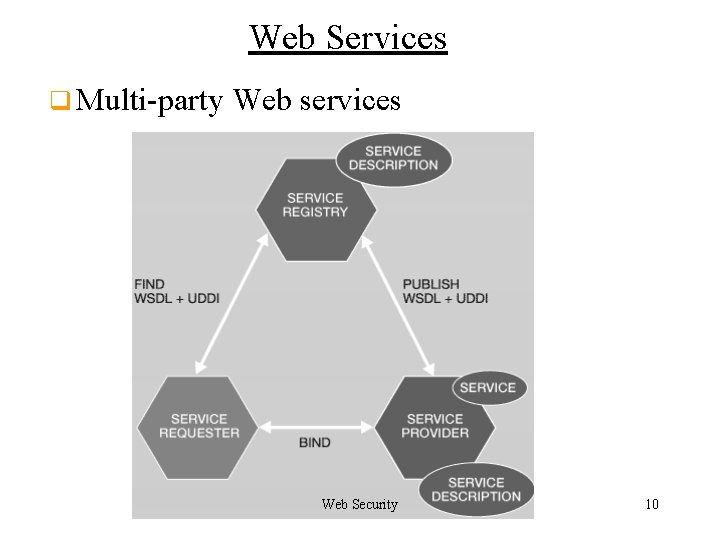
Web Services q Multi-party Web services Web Security 10

E-shopping cart systems q Uses of an e-shopping cart: Temporarily stores what the customer has picked; § Provides a summary of the items (prices, S&H cost, etc. ) in the cart when needed (per the customer’s request or at the time of checkout); § The customer may replace items in the cart until the transaction is finalized. § Web Security 11

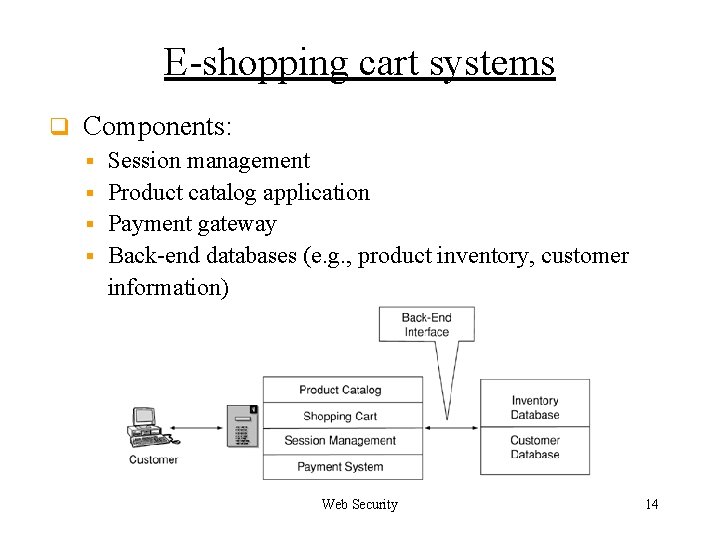
E-shopping cart systems q The e-shopping cart application forms the heart of the e-shopping application. q It binds the customer, the product catalog, the inventory system, and the payment system together. Web Security 12

E-shopping cart systems q Implementation requirements: § Accuracy: It correctly records what the customer has picked and changed. § Flexibility: It allows the customer to freely replace items in the cart. § Integration: with the product catalog, the inventory system, and the payment gateway. § Integrity: No tampering of the cart’s content, whether by malicious 3 rd party or programming errors (e. g. , across two different carts) Web Security 13

E-shopping cart systems q Components: Session management § Product catalog application § Payment gateway § Back-end databases (e. g. , product inventory, customer information) § Web Security 14

E-shopping cart systems q Sample problems with insecure shopping carts: Remote command execution over HTTP § Unprotected sensitive information retrievable via HTTP § Improper or no ‘input sanitization’ results in remote command execution § Modified hidden HTML form fields § Web Security 15

Payment processing system The checkout process: q 1. 2. 3. 4. 5. 6. Finalize the order Choose method of payment Verify of the chosen payment method Log all transactions Fulfill the order Generate a receipt Web Security 16

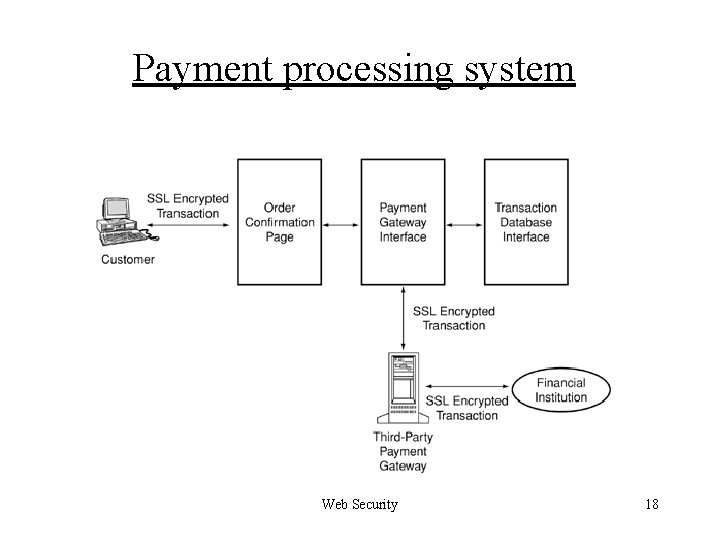
Payment processing system The payment gateway interface: Figure next page q § § Interacts with the order information page, the backend databases, and the payment gateway Provided by the institution that hosts the payment gateway (e. g. , Verisign or Pay. Pal) Integrated into the e-shopping application and invoked by the electronic storefront app. SSL encrypted interface with the payment gateway (Q: how about i/f with other components? ) Web Security 17

Payment processing system Web Security 18

Payment processing system Payment system implementation issues: q § § § Never trust “sensitive” data passed from the client side. Why? Do not store temporary info within the Web server’s document folder. Why? Temporary info should be destroyed after its use. Use SSL to encrypt communication links. Why? Carefully protect user profiles! Web Security 19