MSG 329 Controlling Viruses with Exchange Server and

















































- Slides: 90

MSG 329 Controlling Viruses with Exchange Server and Outlook Jan De Clercq Senior Member of Technical Staff Hewlett-Packard Technology Leadership Group

Agenda Defining the Virus Problem Virus ‘Lifecycle’ Known Exploits + Prevention Virus Detection & Prevention Protecting Points of Entry & Attack Exchange Server - Specific Detection & Scanning Methods – Test Results What’s new: Exchange Server 2003 enhancements

What is a Virus? Code that exploits existing systems Intrusion into system Self-replication & propagation Benefits from automation Can carry payload Can be harmful or benign Without user consent Resides in specific security context Payload can be nuisance message or much, much worse

Escalating Payloads PCs Networks Systems Services Companies

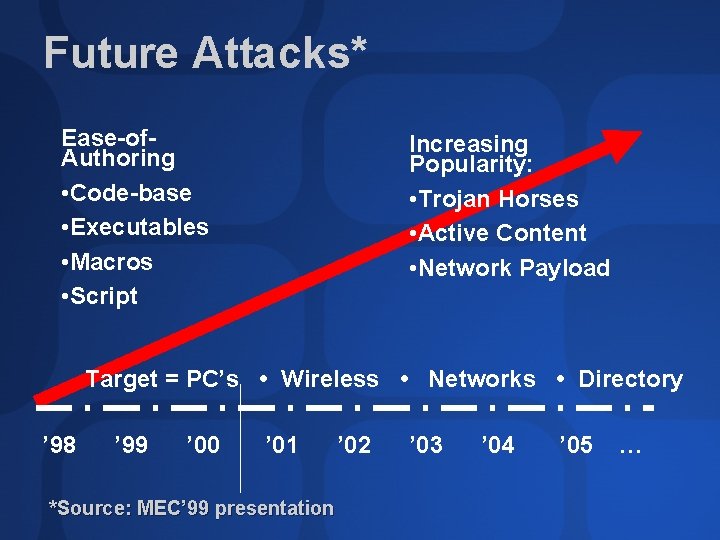
Future Attacks* Ease-of. Authoring • Code-base • Executables • Macros • Script Increasing Popularity: • Trojan Horses • Active Content • Network Payload Target = PC’s • Wireless • Networks • Directory ’ 98 ’ 99 ’ 00 ’ 01 *Source: MEC’ 99 presentation ’ 02 ’ 03 ’ 04 ’ 05 …

Virus Terminology Virus, Worm, Trojan Horse, etc. Polymorphic, Stealth, Variants, etc. Scanning, Signatures, Recursive Decompression, Heuristics, etc. Payload, Transmission Vectors Disturbing Trends Transmission Rate & Vectors Up Payload Latency Down Payload Potency Up

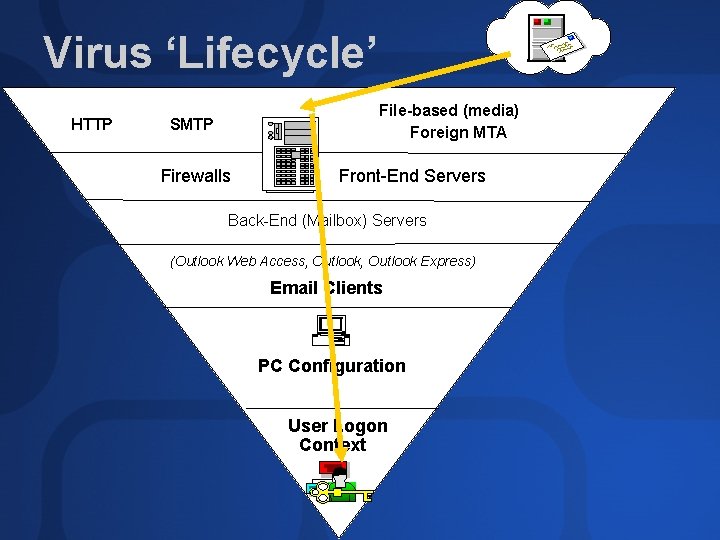
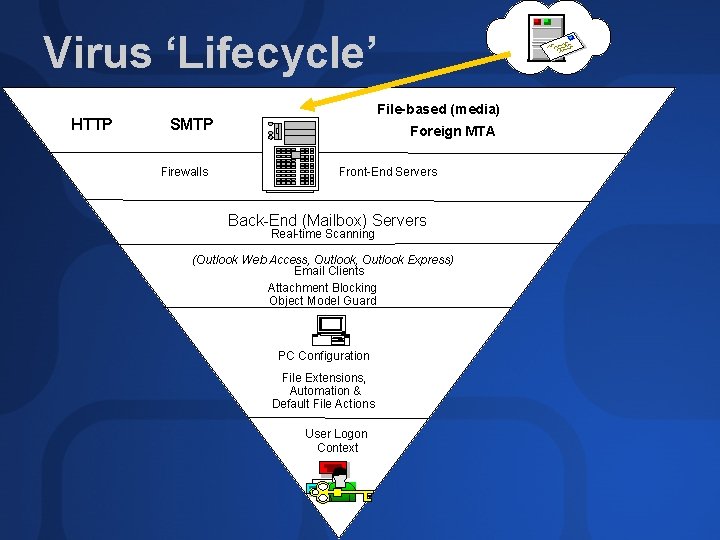
Virus ‘Lifecycle’ HTTP File-based (media) Foreign MTA SMTP Firewalls Front-End Servers Back-End (Mailbox) Servers (Outlook Web Access, Outlook Express) Email Clients PC Configuration User Logon Context

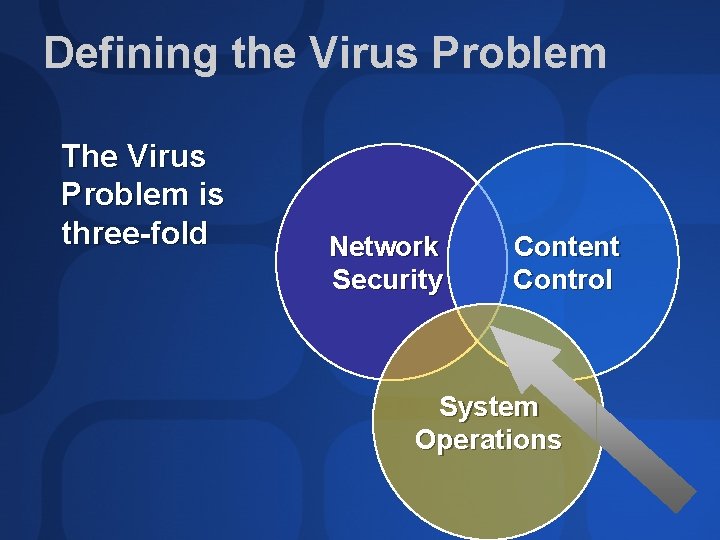
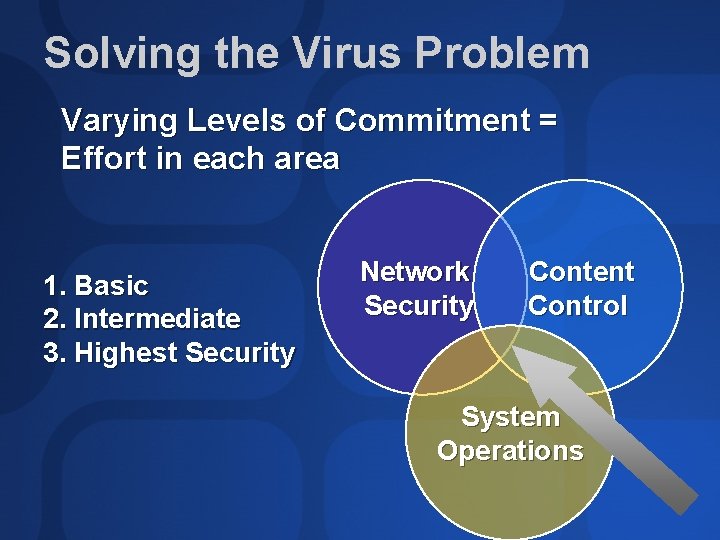
Defining the Virus Problem The Virus Problem is three-fold Network Security Content Control System Operations

Solving the Virus Problem Varying Levels of Commitment = Effort in each area 1. Basic 2. Intermediate 3. Highest Security Network Security Content Control System Operations

What is your commitment to solution? 99% AV Screening @ Gateways / Mailboxes 99. 9% Above + Content restrictions + OS Config 99. 99% Above + Sandbox + Client lockdown . . or Outsource the Problem

Known Exploits + Prevention Learning from Previous Outbreaks Virus Case Studies: Past Exploits What have we learned? What can we predict? (lead time…) Where are we exposed? Exploit Head Hits Steering Wheel Example Bad crash Chronological Order Solution(s) Air Bag

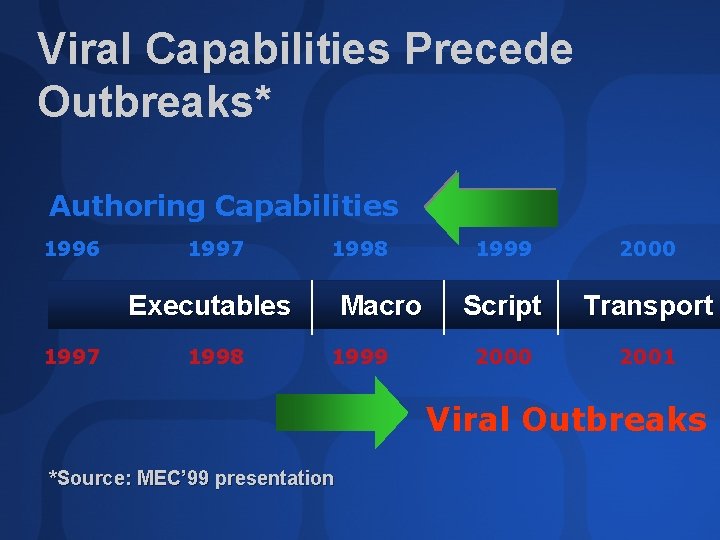
Viral Capabilities Precede Outbreaks* Authoring Capabilities 1996 1997 1998 Executables 1997 1998 Macro 1999 2000 Script Transport 2000 2001 Viral Outbreaks *Source: MEC’ 99 presentation

Outbreak Response Advance preparation Detection Systems & Notification On Outbreak Unplug infected system(s) Shut down SMTP outbound* Shut down MTAs / Hubs Download new signatures Run A/V or cleanup utilties Determine when OK to re-connect * Exchange 2003 Enhancement

Well-known exploits Exploit Example Exploited known Morris Worm / patched 11. 2. 88 vulnerability Solution(s) Stay current e. g. via Windows Update & Office Update

Get Secure, Stay Secure microsoft. com/security Security Tools Bulletins and Virus Alerts Windows + Office Update Windows + Office Integration E. g. issue with ‘SQL Slammer’ Automatic Updates But what about Change Control? Software Update Server (SUS)

HTML script and email Exploit Example ‘Demo’ First known: HTML virus HTML. Internal 11. 10. 98 Solution(s) Set IE zone security to "Medium" or higher • For truly paranoid: • Outlook Key –ZAPHTML from slipstick. com –

Outlook 2002 Plain Text Convert all incoming HTML non-digitallysigned or nonencrypted email to plain text - See Q 307594 Can still view in OWA

Social Engineering Exploit Example Here is that document you asked for. . . don't show anyone else ; -) Melissa 03. 26. 99 Solution(s) • User Education “Trust nothing” –Disable Macros –

Ongoing User Education IDC survey: more than a third (37 per cent) of business email users would still open the attachment of an email titled 'ILOVEYOU' The report found that on any day of the year users would open an email appearing to be from someone they know if the following appeared in the subject line: Great Joke (54 per cent), Look at this (50 per cent), Message (46 per cent), No title (40 per cent) or special offer (39 per cent). Source: http: //www. theregister. co. uk/content/8/16668. html 2/6/2001

User Education Learn with each Attack Social Engineering Unsafe attachments Active content Hidden extensions Save & scan if unsure Unsafe messages Open = launch Leave ‘suspicious’ incoming messages alone for a few hours or days Opening Unprotected Points of Entry E. g. POP email, Web email etc.

Mass email generator Exploit Example Programmatic access to address book Melissa 03. 26. 99 Solution(s) Admin Education: e. g. Dummy entries in GAL (weak) • Outlook Security Update • Need for purging worm generated emails •

Outlook Security Update These are live hyperlinks in the Power. Point email-borne deck viruses “The Most Powerful Anti-Virus Tool on the Planet” The vast majority of (such as ILOVEYOU, Melissa, and Goner) can be stopped in their tracks by taking one simple action -- installing the Outlook E-mail Security Update today. Updates are available for Outlook 2000 and Outlook 98. The update is built into Outlook 2002 in Office XP. http: //www. microsoft. com/technet/security/virus. asp

Outlook Security Update Outlook 98 Service pack 2 and onward Viruses are prevented from programmatically accessing the address book Certain attachment types are restricted Level 1, Level 2 http: //www. microsoft. com/office/outlook/evaluation/s ecurity. asp Internet Security Zone to Restricted Sites by default

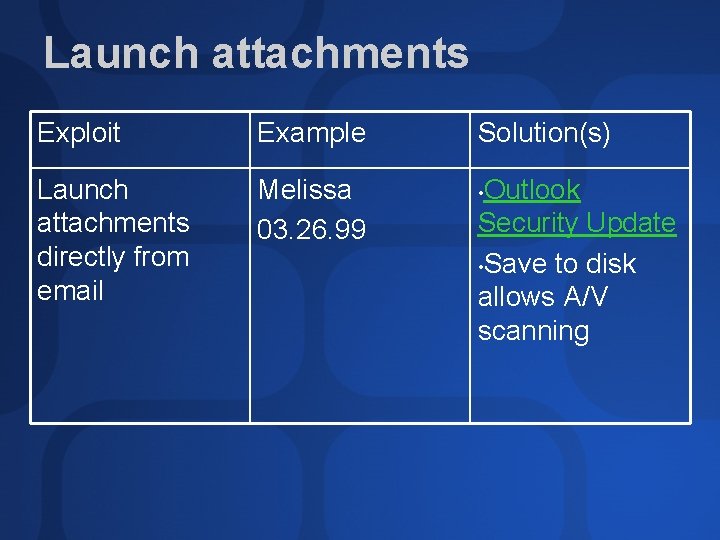
Launch attachments Exploit Example Launch attachments directly from email Melissa 03. 26. 99 Solution(s) Outlook Security Update • Save to disk allows A/V scanning •

Hidden extensions Exploit Example Solution(s) E. g. Worm. Explore. Zi • ‘Hide extensions’ Executable p (Explorer default) appears as 06. 99 must be changed zip or text or • Attachment picture blocking • Outlook Security Update

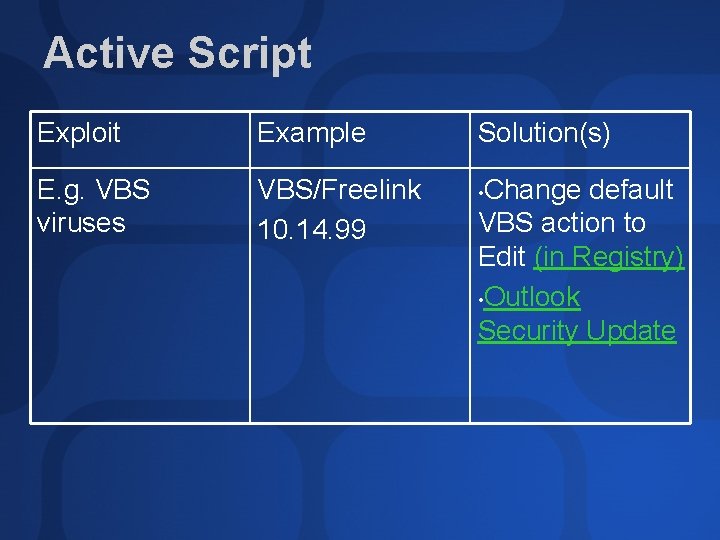
Active Script Exploit Example E. g. VBS viruses VBS/Freelink 10. 14. 99 Solution(s) Change default VBS action to Edit (in Registry) • Outlook Security Update •

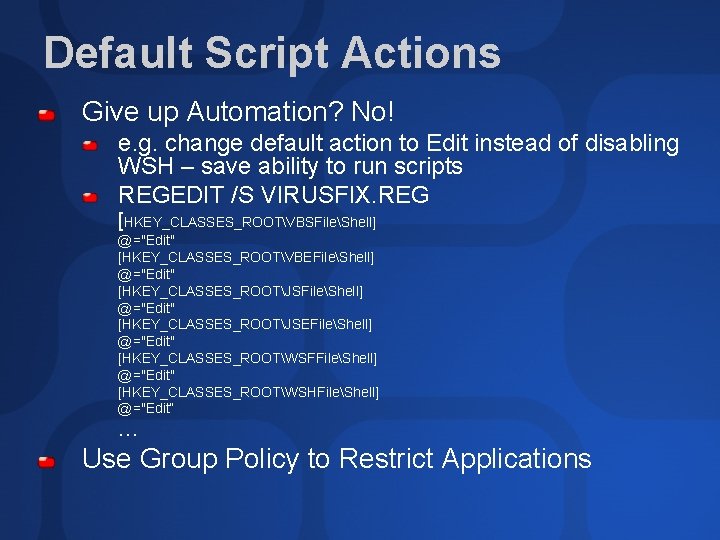
Default Script Actions Give up Automation? No! e. g. change default action to Edit instead of disabling WSH – save ability to run scripts REGEDIT /S VIRUSFIX. REG [HKEY_CLASSES_ROOTVBSFileShell] @="Edit" [HKEY_CLASSES_ROOTVBEFileShell] @="Edit" [HKEY_CLASSES_ROOTJSEFileShell] @="Edit" [HKEY_CLASSES_ROOTWSFFileShell] @="Edit" [HKEY_CLASSES_ROOTWSHFileShell] @="Edit“ … Use Group Policy to Restrict Applications

Auto-launch attachment Exploit Example Solution(s) Auto-launch attachments runs when email opened Bubbleboy 11. 09. 99 Microsoft Security Bulletin (MS 99 -032): Patch Available for "scriptlet. typelib/Eyed og" Vulnerability

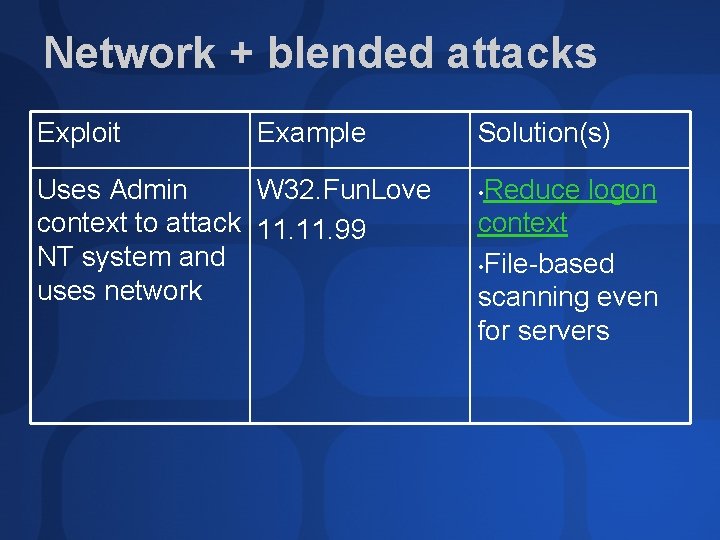
Network + blended attacks Exploit Example Uses Admin W 32. Fun. Love context to attack 11. 99 NT system and uses network Solution(s) Reduce logon context • File-based scanning even for servers •

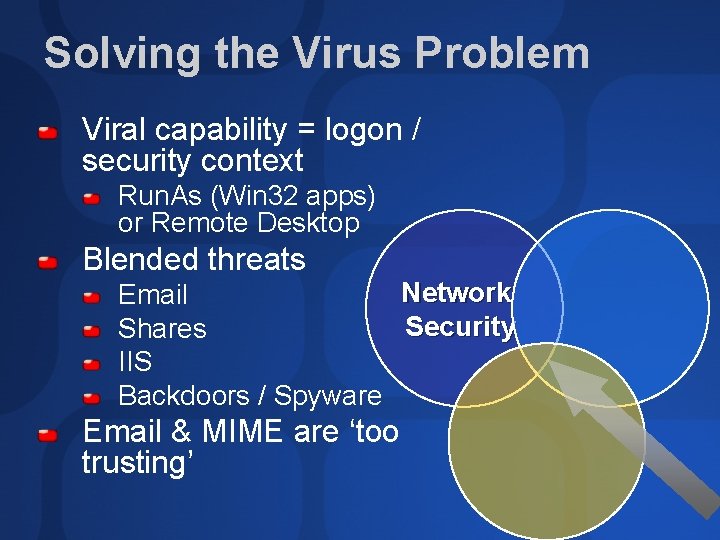
Solving the Virus Problem Viral capability = logon / security context Run. As (Win 32 apps) or Remote Desktop Blended threats Network Email Security Shares IIS Backdoors / Spyware Email & MIME are ‘too trusting’

Fool me once, fool me twice Exploit Example Solution(s) "kindly check ILOVEYOU. txt. v • ‘Hide extensions’ the attached bs (Explorer default) LOVELETTER 05. 04. 2000 must be changed coming from • Change default me. “ VBS action to Edit (in Registry) • Outlook Security Update

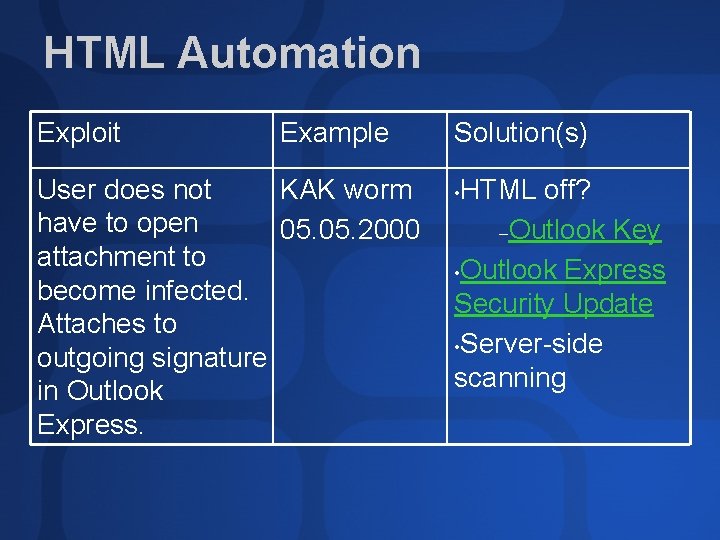
HTML Automation Exploit Example User does not KAK worm have to open 05. 2000 attachment to become infected. Attaches to outgoing signature in Outlook Express. Solution(s) HTML off? –Outlook Key • Outlook Express Security Update • Server-side scanning •

Outlook Express Security Update Q 291387 OLEXP: Using Virus Protection Features in Outlook Express 6 Security tab of the Tools, Options Disable Active Content in HTML E-mail OE 6 uses Restricted Zone instead of Internet Zone Warn me when other applications try to send mail as me Do not allow attachments to be saved or opened that could potentially be a virus Managed via Control Panel: Folder Options Confirm open after download checkbox POP Email Proxy Scanning

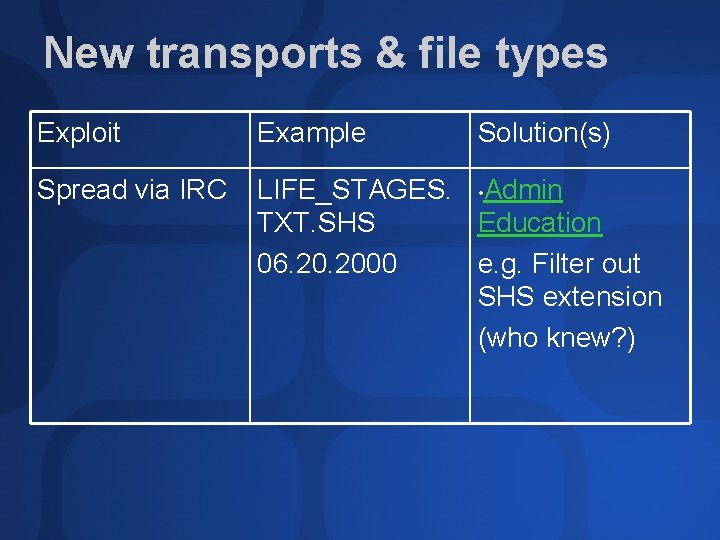
New transports & file types Exploit Example Solution(s) Spread via IRC LIFE_STAGES. • Admin TXT. SHS Education 06. 2000 e. g. Filter out SHS extension (who knew? )

Admin Education Learn with each Attack Address Book / GAL access Active Content & Unwanted content types ? ? _, 00? , 386, ACM, ADT, APP, ARC, ARJ, ASP, AX? , BAT, BIN, BO? , CAB, CBT, CDR, CHM, CLA, CMD, COM, CNV, CPL, CSC, DL? , DEV, DOC, DOT, DRV, EXE, GMS, GZ? , HLP, HT? , ICE, IM? , INI, JS? , LZH, MB? , MD? , MPD, MPP, MPT, MSI, MSG, MSM, MSO, MSP, MST, OBD, OBT, OCX, OLE, OV? , PCI, POT, PP? , QLB, QPW, RAR, REG, RTF, SCR, SHS, SMM, SYS, TAR, TD 0, TLB, TSP, VBS, VS? , VWP, VXD, WBK, WIZ, WPC, WPD, WSI, XL? , XML, XSL, XTP, ZIP DO NOT RELY ON SCANNING BY EXTENSION! Desktop & Outlook Deployments Security Patches (e. g. Outlook via Internet) IE Security Zones Windows settings (file extensions, scripts) Admin Logon context Run As or Remote Admin (Terminal Server)

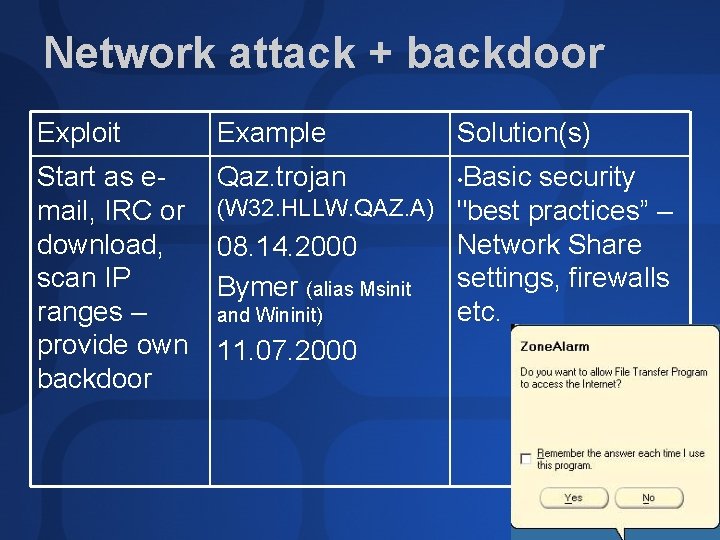
Network attack + backdoor Exploit Example Solution(s) Start as email, IRC or download, scan IP ranges – provide own backdoor Qaz. trojan • Basic security (W 32. HLLW. QAZ. A) "best practices” – Network Share 08. 14. 2000 settings, firewalls Bymer (alias Msinit etc. and Wininit) 11. 07. 2000

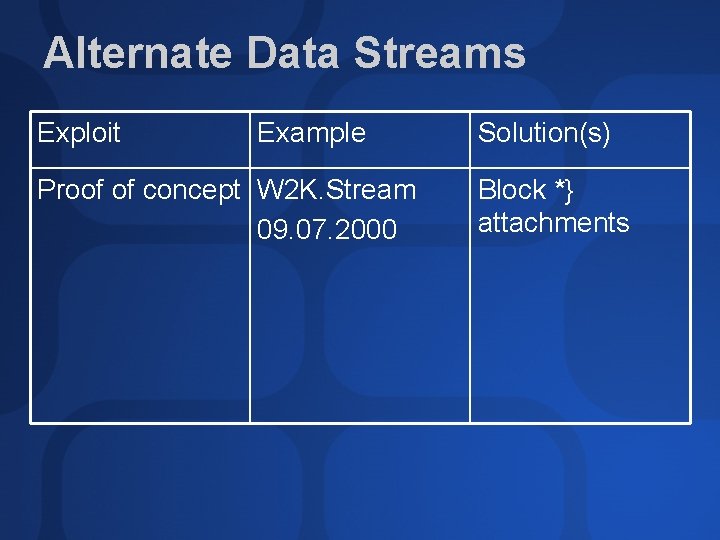
Alternate Data Streams Exploit Example Proof of concept W 2 K. Stream 09. 07. 2000 Solution(s) Block *} attachments

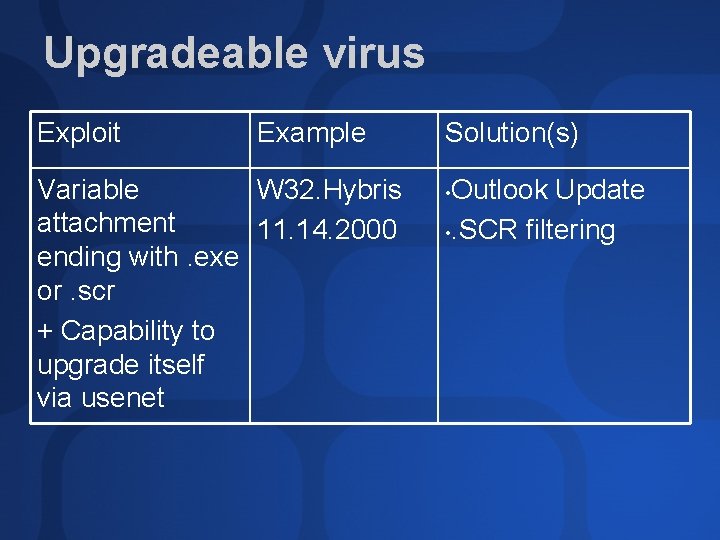
Upgradeable virus Exploit Example Variable W 32. Hybris attachment 11. 14. 2000 ending with. exe or. scr + Capability to upgrade itself via usenet Solution(s) Outlook Update • . SCR filtering •

Testing, Testing… Exploit Example Solution(s) EXE that is not a Flash movie Shockwave worm 11. 30. 2000 Outlook Update

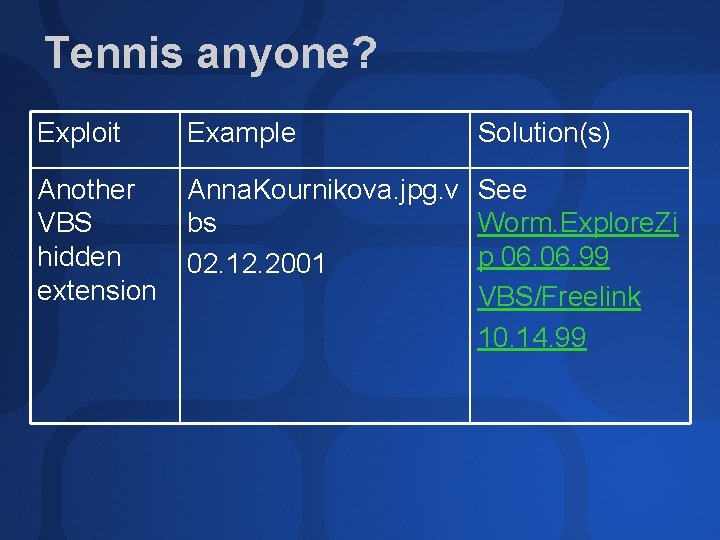
Tennis anyone? Exploit Example Solution(s) Another VBS hidden extension Anna. Kournikova. jpg. v See bs Worm. Explore. Zi p 06. 99 02. 12. 2001 VBS/Freelink 10. 14. 99

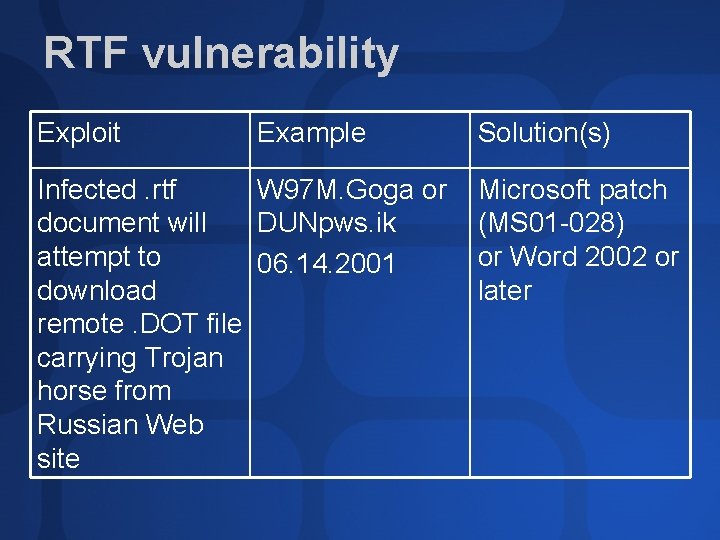
RTF vulnerability Exploit Example Infected. rtf W 97 M. Goga or document will DUNpws. ik attempt to 06. 14. 2001 download remote. DOT file carrying Trojan horse from Russian Web site Solution(s) Microsoft patch (MS 01 -028) or Word 2002 or later

Another blended threat Exploit Example Attempt at randomizing email contents + Infect files shared over an open network Sir. Cam worm 07. 18. 2001 Solution(s) Basic security "best practices" • Bug in random number generator, file deleting, space filling payloads likely not activated •

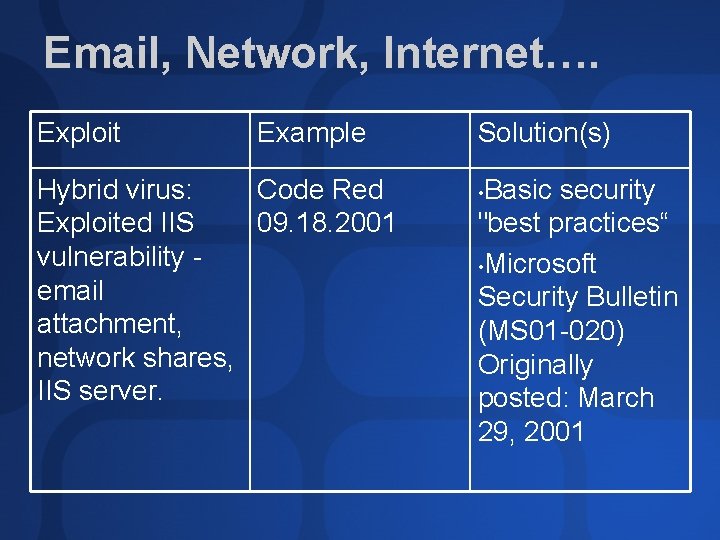
Email, Network, Internet…. Exploit Example Hybrid virus: Code Red Exploited IIS 09. 18. 2001 vulnerability email attachment, network shares, IIS server. Solution(s) Basic security "best practices“ • Microsoft Security Bulletin (MS 01 -020) Originally posted: March 29, 2001 •

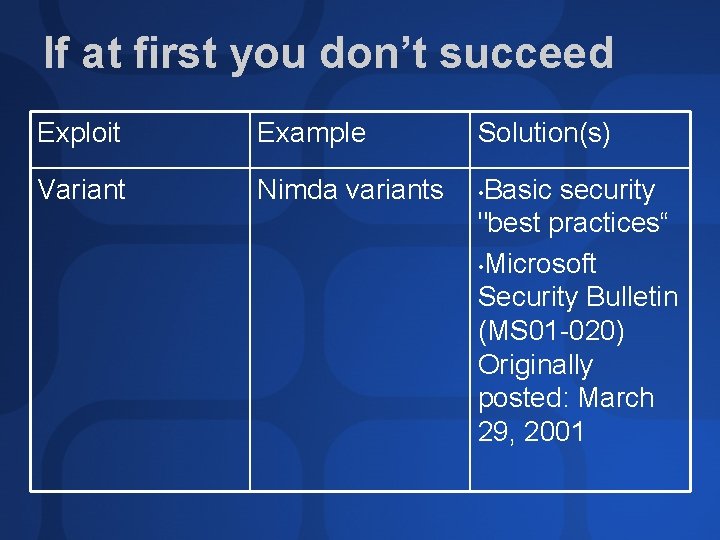
If at first you don’t succeed Exploit Example Solution(s) Variant Nimda variants • Basic security "best practices“ • Microsoft Security Bulletin (MS 01 -020) Originally posted: March 29, 2001

Email spoofing + randomization Exploit Example Well known: Klez &. E variant See MS 01 -020 10. 25. 2001 and/or MS 01027 Solution(s) Outlook Security Patch

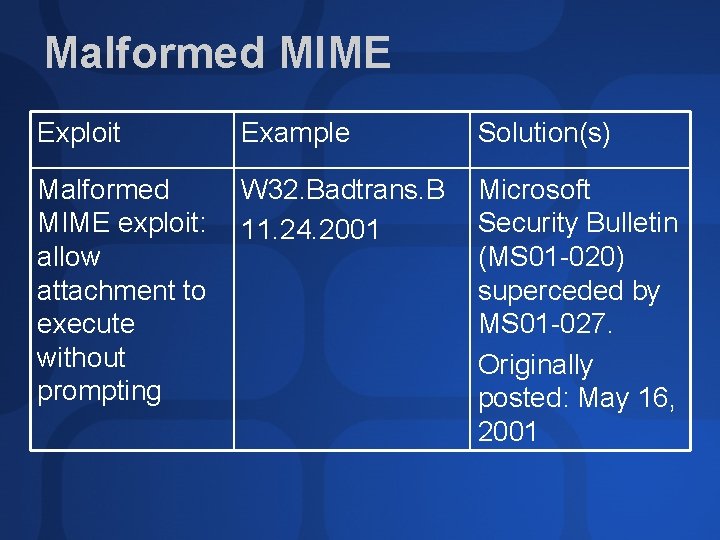
Malformed MIME Exploit Example Solution(s) Malformed MIME exploit: allow attachment to execute without prompting W 32. Badtrans. B 11. 24. 2001 Microsoft Security Bulletin (MS 01 -020) superceded by MS 01 -027. Originally posted: May 16, 2001

Social Engineering Exploit Example Q 216309. exe – Gibe SMTP engine 03. 04. 2002 disguised as Internet Security Update. Attacks mapped drives Solution(s) Outlook Update • User Education: Microsoft DOES NOT send patches via email •

AP headline: “New virus can infect photo files” Exploit Example Claims to infect Perrun JPG files – once 06. 14. 2002 you install the EXE Solution(s) Ummm, don’t install the EXE

I’m getting tired… Exploit Example Mass-mailing, W 32. Lirva. A@mm Termination January 10, 2003 of Antivirus Programs and Firewalls, Compromise of Cached Passwords Solution(s) • Outlook Update • User Education • Microsoft DOES NOT send patches via email

What’s next? Exploit Well-known exploits: "about: " or "javascript: " IFRAME tag Example See ntbugtraq. com Solution(s) Outlook Security Update or get Outlook 2002 or later

Illegal MIME Exploit RFC 822 standards for MIME, wide variety of interpretations of multipart structure Example Content-Type: text/plain; name==? usascii? Q? eicar. com? = name=eicar. com name=””eicar. com name=. ”eicar. com” name=eicar. com name=”eicar. com name==? usascii? Q? eicar. com? = name==? usascii? Q? eicar? =. com name==? us-ascii? Q? eicar? = =? us-ascii? Q? . com? = name=”eicar. =? usascii? Q? com? =” name=”eicar. =? usascii? Q? com? = name=eicar. =? usascii? Q? co? =m Solution(s) • Outlook Security Update • Block. DAT

What’s next? Exploit <Your network here> Example <Your name here> Solution(s) Look for exploit opportunities in your own environment (to prevent!)

Agenda Defining the Virus Problem Virus ‘Lifecycle’ Known Exploits + Prevention Virus Detection & Prevention Protecting Points of Entry & Attack Exchange Server - Specific Detection & Scanning Methods – Test Results What’s new: Exchange Server 2003 enhancements

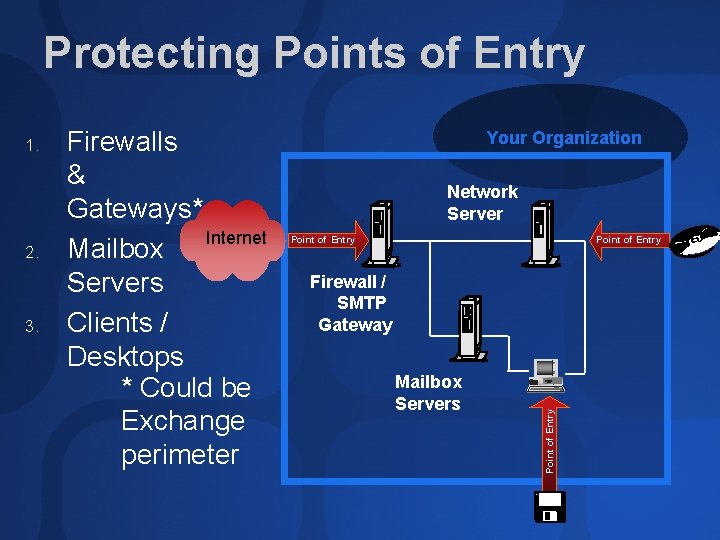
Protecting Points of Entry 2. 3. Firewalls & Gateways* Internet Mailbox Servers Clients / Desktops * Could be Exchange perimeter Your Organization Network Server Point of Entry Firewall / SMTP Gateway Mailbox Servers Point of Entry 1.

1: Firewalls & Gateways Content & Virus Scanning ISA e. g. Trend Inter. Scan Virus. Wall, GFI Download. Security for ISA Server, Finjan Surfin. Gate - See isaserver. org Windows Server 2003 SMTP products Port watch products http: //msdn. microsoft. com/msdnmag/issues/02/0 9/New. Stuff/default. aspx MSDN Magazine > September 2002 Also File-based Scanning

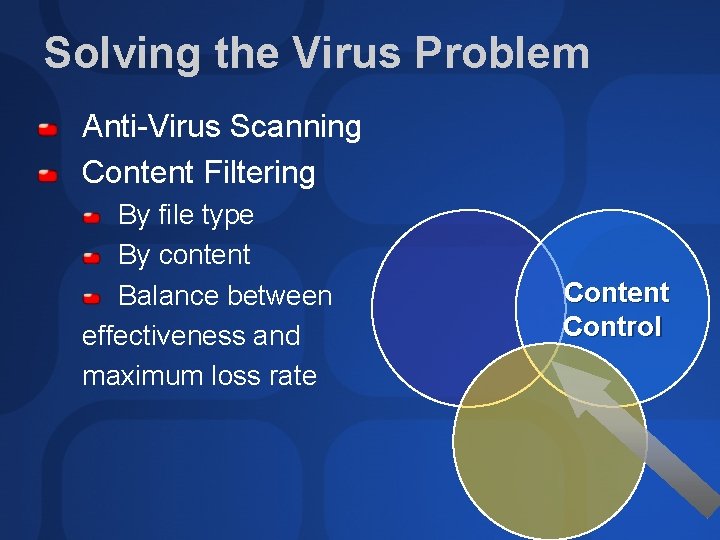
Solving the Virus Problem Anti-Virus Scanning Content Filtering By file type By content Balance between effectiveness and maximum loss rate Content Control

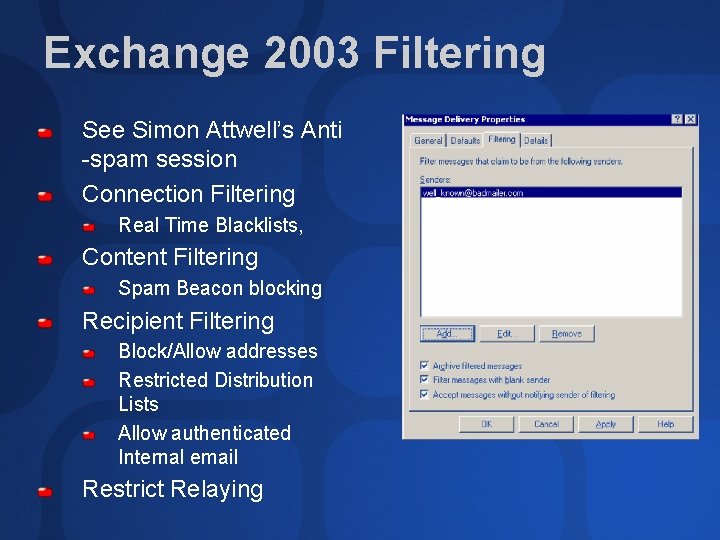
Exchange 2003 Filtering See Simon Attwell’s Anti -spam session Connection Filtering Real Time Blacklists, Content Filtering Spam Beacon blocking Recipient Filtering Block/Allow addresses Restricted Distribution Lists Allow authenticated Internal email Restrict Relaying

2: Mailbox Servers Store-based Content & Virus Scanning Exchange Scanning Methods <1998 2000 2001 2002 2003 MAPI AVAPI VSAPI 2. 5 Product Selection Criteria Warning: Exclude Exchange Binaries, Databases, Logs, etc. from File-based Scanning

Anti-Virus Resource Usage A/V Process uses CPU + drives up Store. exe Process Limits Server Scalability Solution / Options: Scale Vertically e. g. Add Processors “Surround” Mailbox Servers with A/V Scanning

3: Clients / Desktops User & Admin Education Outlook E-mail Security See Session SEC 360 Outlook Security and Virus Protection (Weds 9 am) Other Options: Turn off the email preview pane Tool, Options, Send tab, Mail Sending Format, Plain Text Desktop Anti-Virus Scans email attachments saved to temporary folder Q 49500 List of Antivirus Software Vendors Outlook Express E-mail Security

Agenda Defining the Virus Problem Virus ‘Lifecycle’ Known Exploits + Prevention Virus Detection & Prevention Protecting Points of Entry & Attack Exchange Server - Specific Detection & Scanning Methods – Test Results What’s new: Exchange Server 2003 enhancements

What’s new: Exchange Server 2003 Enhancements VSAPI 2. 5 OWA Attachment Blocking Filtering (Anti-Spam) MIME Handling Outlook Version Control Allows Patch Enforcement

VS API V 2. 0 in Ex 2 k SP 1 Scans messages and attachments Priority based Scanning Queue Proactive Message Scanning Enhanced Background Scanning Thread pooling Message Details Per-MDB Scanning EDK Gateway content scanning Message body and attachment scanning Native MAPI/MIME content scanning Scanner On-Demand Reload

VS API V 2. 5 in Ex 2003 Antivirus App can delete messages Antivirus App can send messages to the sender, and additional virus status messages thus allowing clients to better indicate the infection status of a given message

VSAPI Scanning Proactive Scanning As messages arrive inbound to the server On Access Scanning When messages are accessed via client or agent Background Scanning Ongoing scanning of messages Primarily used for re-scanning data when virus signatures are updated

Priority Scanning Queue One queue exist for entire Store process Maximum of 30 items Messages are submitted to queue with a high or low priority Requested item (i. e. Message Open) receives high priority Saves and Posted items receive low priority High priority messages are always scanned before low priority Item priority can be upgraded upon access

Proactive Scanning Proactively scans messages as they are submitted to Store Transport Submit, Client Submittal Gives item an opportunity to be scanned prior to access (i. e. Message Open) Proactive Items receive a low Priority. Maximum of 30 low priority items in queue. FIFO based removal of low priority items in queue If removed, then item will be scanned when accessed

On Access Scanning Process The item’s virus stamp is checked If item has not been scanned by current virus signature, the item is inserted into queue Items are assigned a high priority in queue If item was in low priority queue when accessed, item priority is upgraded to high Client waits to be “signaled” when scanning is complete or times out Essentially eliminates the need for traditional manual scanning

Background Scanning Opens Each corresponding Msg. Folder Table and walks contents ptag. Virus. Scanner. Stamp is now stamped on Folders, Msg. Folder, Msg, and Attachment table entries Optimiziation: If ptag. Virus. Scanner. Stamp is up-to -date on Folder entry, contents are not scanned. New items in folders will be scanned when submitted or accessed Sleeps until Store is restarted or Virus Interface is updated

Effectiveness Testing @hp Problem Files & Tests Settings: Scan All Attachments Types, Notify Sender, Admin and Recipient, Repair if possible, Quarantine if Not Detection: Start AV Service, send virus Performance & Detection: Run Load. Sim – Normal Load Mail. Storm – Push to Bottleneck

Sample Test Environment

Problem Files & Tests Viruses Known virus Macro Virus Disguised Virus Zip in Embedded Message Acknowledge ZIP Encrypted ZIP Problem Files Zero Byte. COM. com URL format Empty ZIP file > 2 GB unzipped file Illegal MIME e. g. UPPERCASE header Invalid filenames Syntax errors AV Service starting Signature Update Digital Signature & Encrypted To Uninitialized Mailbox Delayed Send With Invalid Return Address Embedded in Outlook Form To Distribution List To Public Folder via Post To Public Folder via SMTP address Drag & Drop File to PF Exchange Settings: Private. PST delivery (Client logged on) Invalid Address (create NDR) Invalid Address (NDR) with valid CC Message in Sent Items

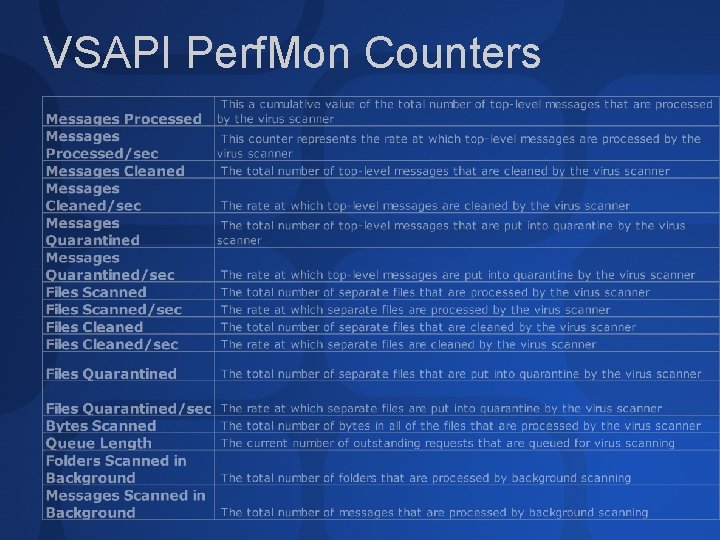
VSAPI Perf. Mon Counters

AV Test Suites Exchange 200 X Server Mailbox and Public Folder Store virus protection Test Suite 1: Normal Load Test Suite 2: Peak Load (Stress Test) Test Suite 3: Impact of RAID level, Multiple Storage Groups, and Stores SMTP Front-End virus protection Test Suite 4: Measure SMTP throughput and resource utilization with and without anti-virus scanning

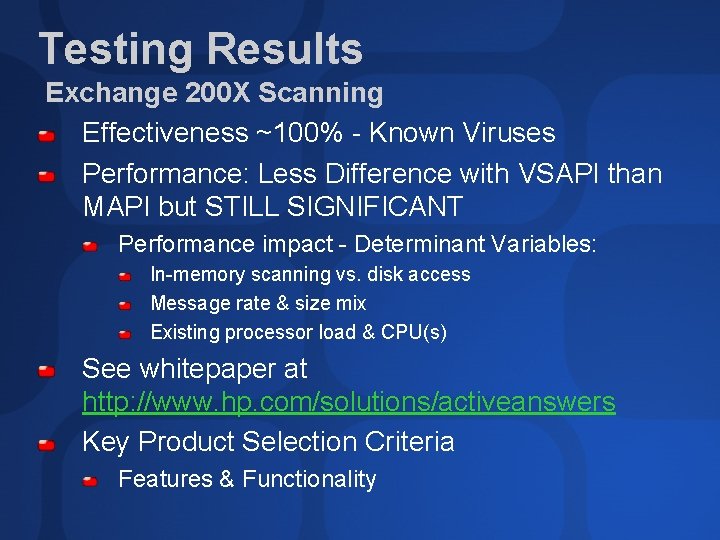
Testing Results Exchange 200 X Scanning Effectiveness ~100% - Known Viruses Performance: Less Difference with VSAPI than MAPI but STILL SIGNIFICANT Performance impact - Determinant Variables: In-memory scanning vs. disk access Message rate & size mix Existing processor load & CPU(s) See whitepaper at http: //www. hp. com/solutions/activeanswers Key Product Selection Criteria Features & Functionality

Product Selection Basics Exchange 5. x, Exchange 2000, Exchange 2003 Compatibility Version (Front-End Exchange Server, Windows Server SMTP only, or Back-End Store version) Multiple stores and client access from MAPI, OWA, Internet protocols and the EXIFS (M: drive). API Method used: MAPI, AVAPI, VSAPI or Combination? Special Hardware Support, multi-processor, clusters, etc. Remote installation, configuration, monitoring, updating, and management? Enterprise (Multi-Server) Console and remote administration? Administrative Console type: Web, MMC, both? Scheduled, automatic updates of the virus signature files Push or pull? Firewall/proxy settings? Can it fan out from an internal http or \UNC share? Scan Engine used (or multiple scan engines) Does it scan in memory or must it write attachments to disk? Scans all message content (attachments and compressed files, message body, HTML) Heuristics or other technology to detect and prevent macro viruses and new viruses

Product Selection Criteria Features for dealing with virus outbreaks? Purging or deletion of entire worm messages? Customize alert messages to administrator(s), sender, and recipient? Distinguish between external and internal? Choice of transports or alerting mechanisms such as NET SEND as well as e-mail? Can it break or block digitally signed or encrypted emails to scan for viruses? Exclude folders from manual scanning (e. g. Organizational Forms Library)? Selective attachment blocking? Does it provide any other form of content filtering? Configure Quarantine thresholds Maximum number of items, Maximum size of Quarantine, Oldest message in Quarantine etc.

More Features… Anti-Virus Functionality Control over scanning ‘bias’ – certainty versus performance Delete Select Files: corrupted compressed, UUEncoded or Encrypted files Control over depth of scanning: maximum number of nested attachments or compressed archives and maximum scan time Scan Files Embedded in Documents Trusted Scanning Domain Content Control Functionality Control over outbound disclaimers Filter by file type, sender/domain, subject line, message contents Control over Encrypted files – quarantine or log event Provide sample policies or categories or weightings Simple, Centralized Reporting

Conclusions Solving the Virus Problem is three-fold 1. 2. 3. Network Security Content Control System Operations Commitment to Solution 99% 99. 99% Scanning, Filtering, Lockdown Pro-actively or Re-actively Learning from Previous Outbreaks Microsoft Responses Outlook Security Patch New, Improved VSAPI

Appendices Reference Slides follow

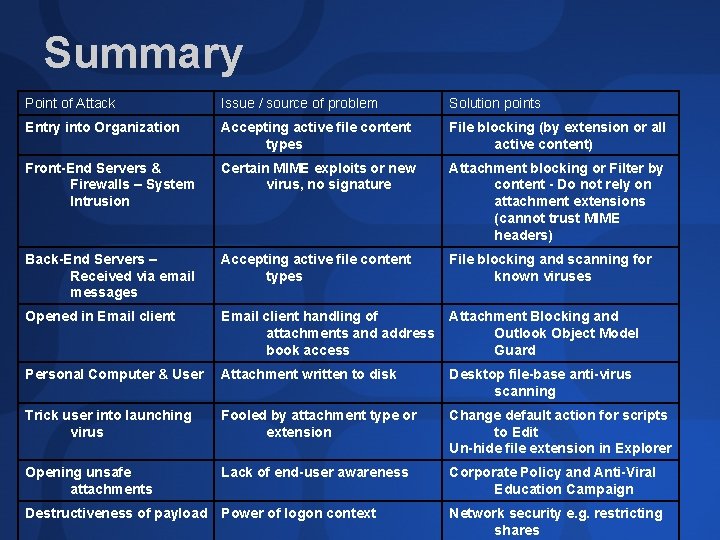
Summary Point of Attack Issue / source of problem Solution points Entry into Organization Accepting active file content types File blocking (by extension or all active content) Front-End Servers & Firewalls – System Intrusion Certain MIME exploits or new virus, no signature Attachment blocking or Filter by content - Do not rely on attachment extensions (cannot trust MIME headers) Back-End Servers – Received via email messages Accepting active file content types File blocking and scanning for known viruses Opened in Email client handling of attachments and address book access Attachment Blocking and Outlook Object Model Guard Personal Computer & User Attachment written to disk Desktop file-base anti-virus scanning Trick user into launching virus Fooled by attachment type or extension Change default action for scripts to Edit Un-hide file extension in Explorer Opening unsafe attachments Lack of end-user awareness Corporate Policy and Anti-Viral Education Campaign Destructiveness of payload Power of logon context Network security e. g. restricting shares

Links to More Information Active. Answers http: //www. hp. com/solutions/activeanswers AV Vendors http: //www. gfi. com/mailsecurity/msecpapers. htm “One virus engine is not enough: The case for maximizing network protection with multiple anti-virus scanners” “Why you need an email exploit detection engine: Companies must supplement anti-virus protection for maximum security” “Protecting your network against email threats: How to block email viruses and attacks” “Why anti-virus software is not enough: The urgent need for server-based email content checking” http: //www. symantec. com/avcenter/whitepapers. html http: //www. trendmicro. com/download/whitepapers/ http: //www. sybari. com/products/whitepapers. asp

Solving the Virus Problem Turning Down the Automation Default Script Actions Hidden File Extensions Outlook Security Updates + Windows Patches Client Configuration Hidden extensions Backdoors and Intrusion Detection Personal firewall e. g. Zone. Alarm System Operations

Virus ‘Lifecycle’ HTTP File-based (media) SMTP Firewalls Foreign MTA Front-End Servers Back-End (Mailbox) Servers Real-time Scanning (Outlook Web Access, Outlook Express) Email Clients Attachment Blocking Object Model Guard PC Configuration File Extensions, Automation & Default File Actions User Logon Context

Further Reading “Mission-Critical Active Directory”, Jan De Clercq, Micky Balladelli, Digital Press, ISBN 155558 -240 -0 “Windows Server 2003 Security Infrastructures” Jan De Clercq, To be published late 2003

Questions? Jan. De. Clercq@HP. com Evan. Morris@HP. com

Community Resources http: //www. microsoft. com/communities/default. mspx Most Valuable Professional (MVP) http: //www. mvp. support. microsoft. com/ Newsgroups Converse online with Microsoft Newsgroups, including Worldwide http: //www. microsoft. com/communities/newsgroups/default. mspx User Groups Meet and learn with your peers http: //www. microsoft. com/communities/usergroups/default. mspx

Suggested Reading And Resources The tools you need to put technology to work! TITLE Microsoft® Exchange Server 2003 Administrator's Companion: 07356 -1979 -4 Active Directory® for Microsoft® Windows® Server 2003 Technical Reference: 0 -73561577 -2 Available 9/24/03 Today Microsoft Press books are 20% off at the Tech. Ed Bookstore Also buy any TWO Microsoft Press books and get a FREE T-Shirt

evaluations

© 2003 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.