MPLS VPN Technology Introducing VPNs 2006 Cisco Systems


- Slides: 20

MPLS VPN Technology Introducing VPNs © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -1

Outline • Overview • Traditional Router-Based Network Connectivity • Advantages of VPNs • VPN Terminology • What Are the VPN Implementation Models? • What Are Overlay VPN Technologies? • What Are Peer-to-Peer VPN Technologies? • What Are the Benefits of VPNs? • What Are the Drawbacks of VPNs? • Summary © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -2

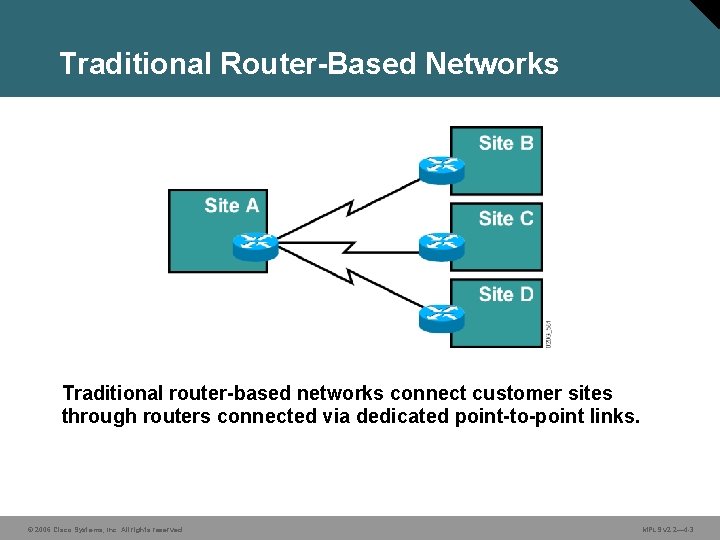
Traditional Router-Based Networks Traditional router-based networks connect customer sites through routers connected via dedicated point-to-point links. © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -3

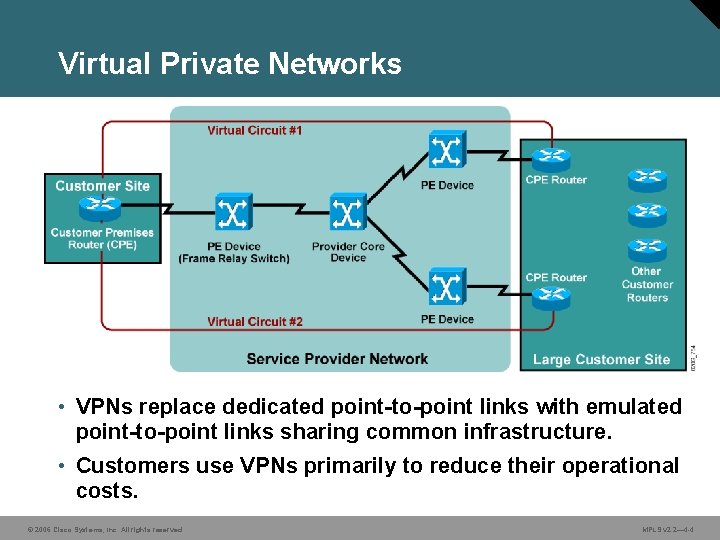
Virtual Private Networks • VPNs replace dedicated point-to-point links with emulated point-to-point links sharing common infrastructure. • Customers use VPNs primarily to reduce their operational costs. © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -4

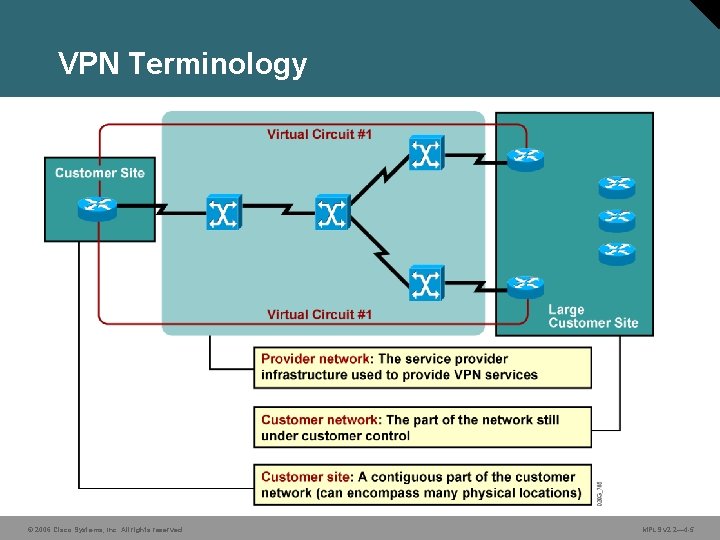
VPN Terminology © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -5

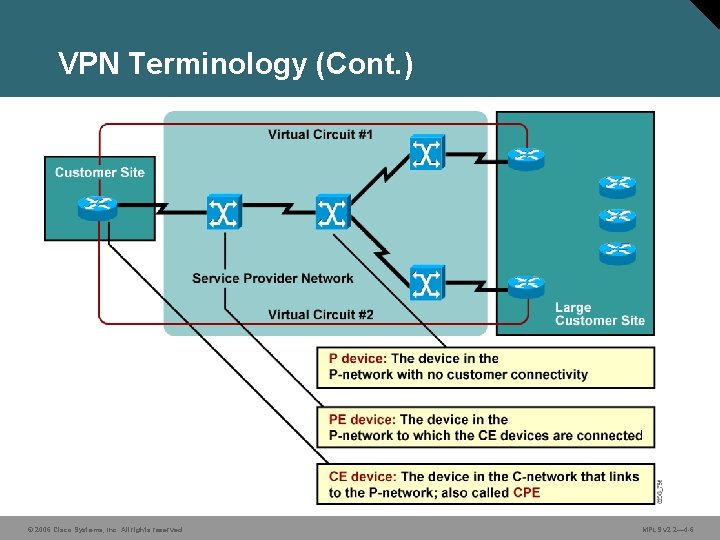
VPN Terminology (Cont. ) © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -6

VPN Implementation Models VPN services can be offered based on two major models: • Overlay VPNs, in which the service provider provides virtual point-to-point links between customer sites • Peer-to-peer VPNs, in which the service provider participates in the customer routing © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -7

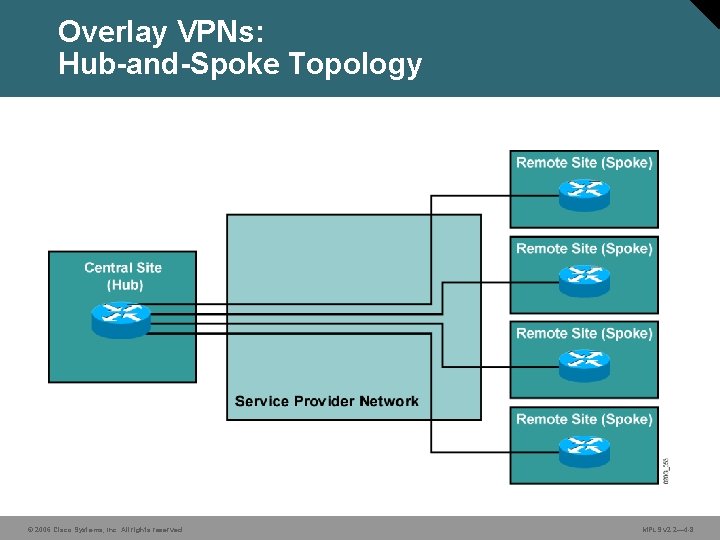
Overlay VPNs: Hub-and-Spoke Topology © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -8

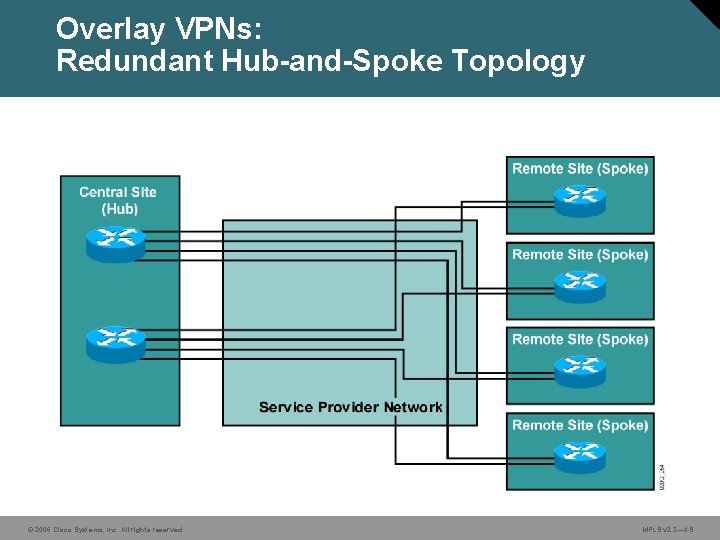
Overlay VPNs: Redundant Hub-and-Spoke Topology © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -9

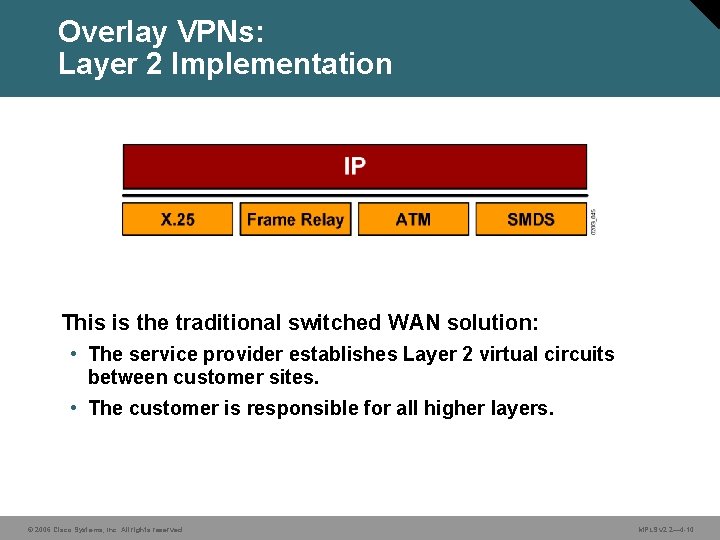
Overlay VPNs: Layer 2 Implementation This is the traditional switched WAN solution: • The service provider establishes Layer 2 virtual circuits between customer sites. • The customer is responsible for all higher layers. © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -10

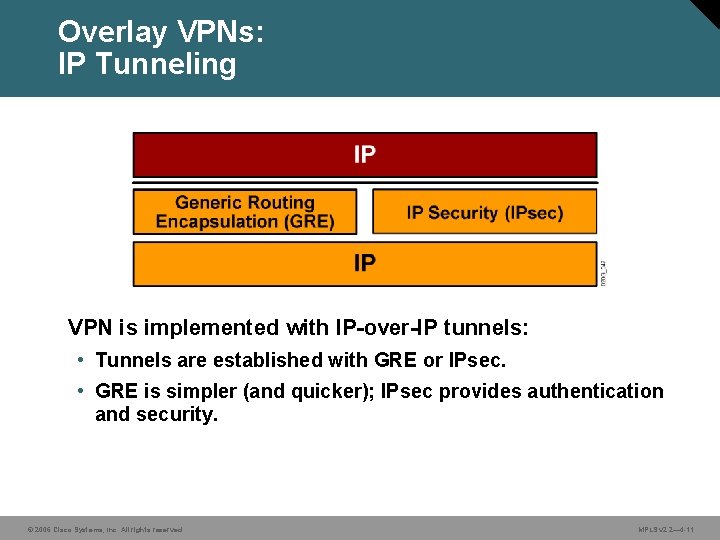
Overlay VPNs: IP Tunneling VPN is implemented with IP-over-IP tunnels: • Tunnels are established with GRE or IPsec. • GRE is simpler (and quicker); IPsec provides authentication and security. © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -11

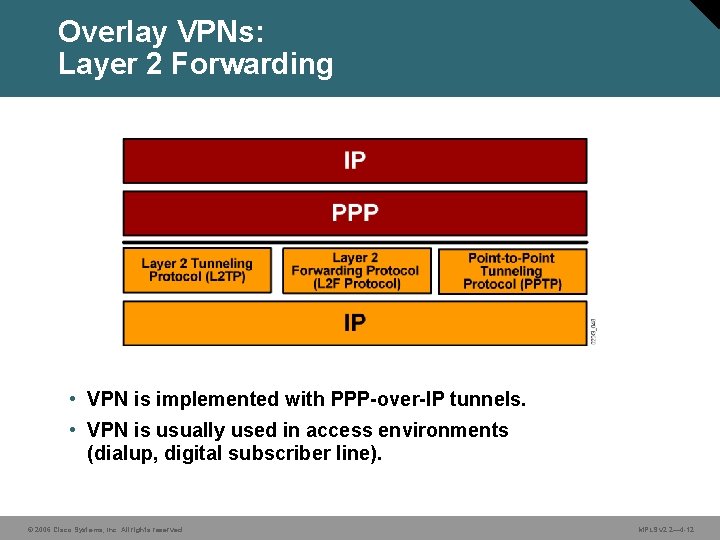
Overlay VPNs: Layer 2 Forwarding • VPN is implemented with PPP-over-IP tunnels. • VPN is usually used in access environments (dialup, digital subscriber line). © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -12

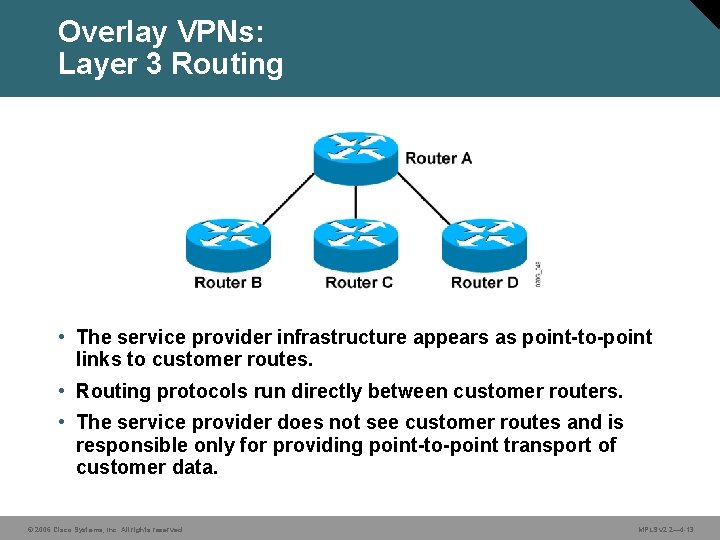
Overlay VPNs: Layer 3 Routing • The service provider infrastructure appears as point-to-point links to customer routes. • Routing protocols run directly between customer routers. • The service provider does not see customer routes and is responsible only for providing point-to-point transport of customer data. © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -13

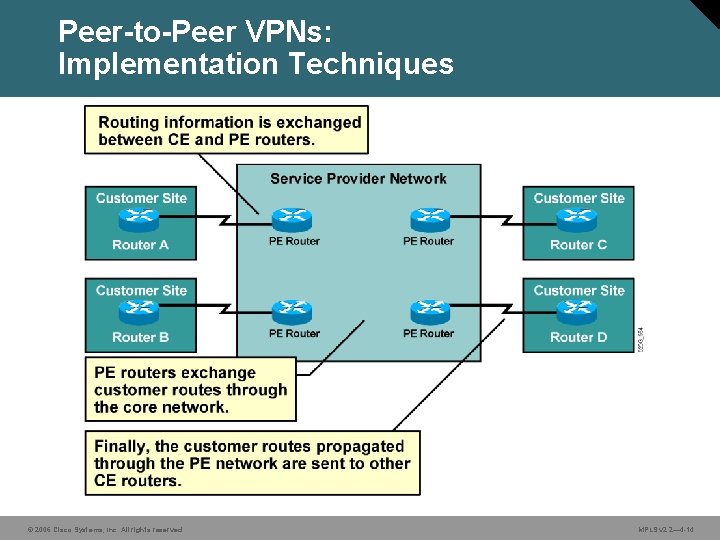
Peer-to-Peer VPNs: Implementation Techniques © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -14

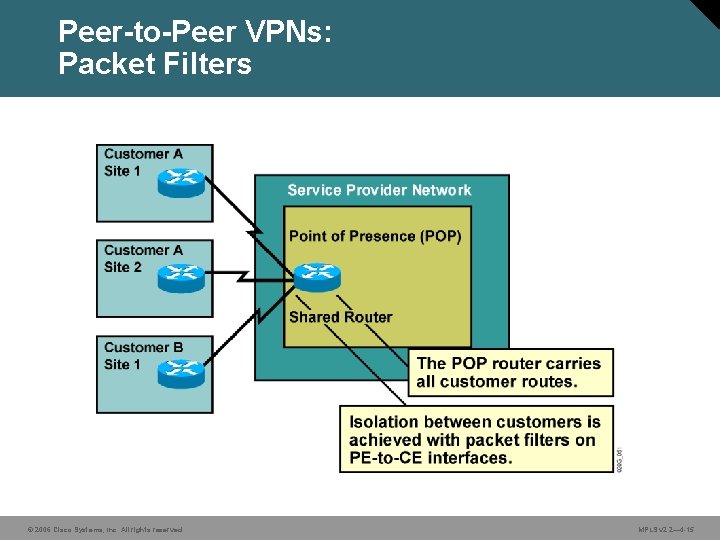
Peer-to-Peer VPNs: Packet Filters © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -15

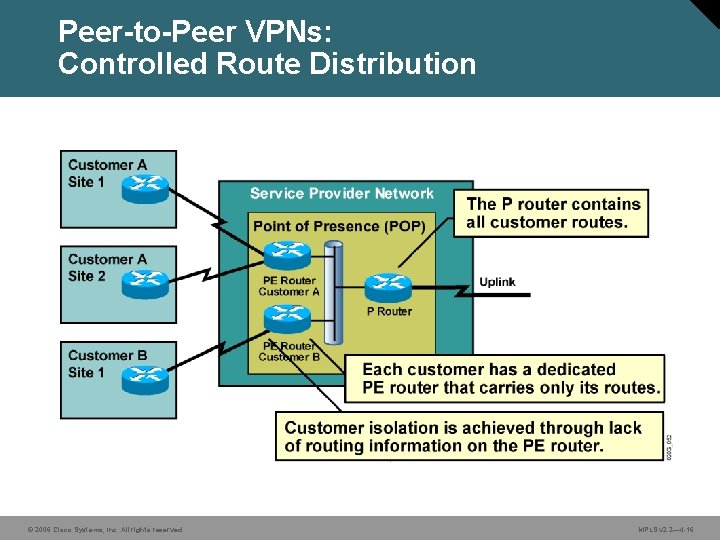
Peer-to-Peer VPNs: Controlled Route Distribution © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -16

Benefits of VPN Implementations • Overlay VPN: – Well-known and easy to implement – Service provider does not participate in customer routing – Customer network and service provider network are well-isolated • Peer-to-peer VPN: – Guarantees optimum routing between customer sites – Easier to provision an additional VPN – Only sites provisioned, not links between them © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -17

Drawbacks of VPN Implementations • Overlay VPN: – Implementing optimum routing requires a full mesh of virtual circuits. – Virtual circuits have to be provisioned manually. – Bandwidth must be provisioned on a site-to-site basis. – Overlay VPNs always incur encapsulation overhead. • Peer-to-peer VPN: – The service provider participates in customer routing. – The service provider becomes responsible for customer convergence. – PE routers carry all routes from all customers. – The service provider needs detailed IP routing knowledge. © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -18

Summary • Traditional router-based networks connect via dedicated point-to -point links. • VPNs use emulated point-to-point links sharing a common infrastructure. • The two major VPN models are overlay VPN and peer-to-peer VPN. – Overlay VPNs use well-known technologies and are easy to implement. – Overlay VPN virtual circuits must be provisioned manually. – Peer-to-peer VPNs guarantee optimum routing between customer sites. – Peer-to-peer VPNs require that the service provider participate in customer routing. © 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -19

© 2006 Cisco Systems, Inc. All rights reserved. MPLS v 2. 2— 4 -20