MPC Secure Multiparty Computation Yuval Ishai Technion Cryptography



![Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] • Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] •](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-10.jpg)
![Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] Real Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] Real](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-11.jpg)
![Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] Real Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] Real](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-12.jpg)
![Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] Real Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] Real](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-13.jpg)




![A simple MPC protocol [IKMOP 13] Trusted Dealer RA RB Alice (x) f(x, y) A simple MPC protocol [IKMOP 13] Trusted Dealer RA RB Alice (x) f(x, y)](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-22.jpg)



![Approaches to passive MPC • Using homomorphic encryption – Linear-homomorphic [FH 93, CDN 01] Approaches to passive MPC • Using homomorphic encryption – Linear-homomorphic [FH 93, CDN 01]](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-30.jpg)

![Back to the 1980 s • Zero-knowledge proofs for NP [GMR 85, GMW 86] Back to the 1980 s • Zero-knowledge proofs for NP [GMR 85, GMW 86]](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-33.jpg)


![MPC ZK [IKOS 07] P 1 Pn P 2 V w 11 Vw 22 MPC ZK [IKOS 07] P 1 Pn P 2 V w 11 Vw 22](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-36.jpg)
![General 2 -party protocols [IPS 08] • Life is easier when everyone follows instructions… General 2 -party protocols [IPS 08] • Life is easier when everyone follows instructions…](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-41.jpg)






![[KT 00] [IK 04] 1990 1995 2000 • The three problems are closely related [KT 00] [IK 04] 1990 1995 2000 • The three problems are closely related](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-56.jpg)
![Private Information Retrieval [Chor-Goldreich-Kushilevitz-Sudan 95] database x∈{0, 1}n ? Main question: minimize communication (logn Private Information Retrieval [Chor-Goldreich-Kushilevitz-Sudan 95] database x∈{0, 1}n ? Main question: minimize communication (logn](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-57.jpg)
![A Simple Computational PIR Protocol [Kushilevitz-Ostrovsky 97] Tool: (linear) homomorphic encryption a b Protocol: A Simple Computational PIR Protocol [Kushilevitz-Ostrovsky 97] Tool: (linear) homomorphic encryption a b Protocol:](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-59.jpg)
![From I. T. PIR to LDC [Katz-Trevisan 00] Simplifying assumptions: • Servers compute same From I. T. PIR to LDC [Katz-Trevisan 00] Simplifying assumptions: • Servers compute same](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-61.jpg)

![Tool: Matching Vectors [Yek 07, Efr 09, DGY 10] • Vectors u 1, …, Tool: Matching Vectors [Yek 07, Efr 09, DGY 10] • Vectors u 1, …,](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-65.jpg)
![Tool: Matching Vectors [Yek 07, Efr 09, DGY 10] • Matching vectors can be Tool: Matching Vectors [Yek 07, Efr 09, DGY 10] • Matching vectors can be](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-66.jpg)

- Slides: 75

MPC Secure Multiparty Computation Yuval Ishai Technion Cryptography Boot Camp May 21, 2015

Talk Outline • • Gentle introduction to MPC Definitions Protocols Open problems – and why we will never run out of them…

MPC is more general than you think • Can capture problems from many areas – Error-correcting codes – Distributed algorithms – Interactive proofs, PCPs, randomness extractors – Encryption, signatures, ZK proofs – Obfuscation, functional encryption – Anything that involves “good guys” trying to achieve a common goal in the presence of “bad guys” • Too big to fail… • Rest of talk: secure function evaluation

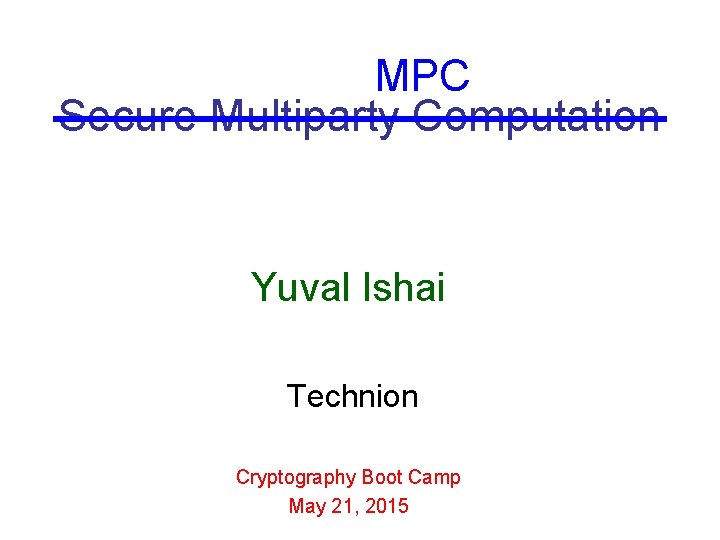
How much do we earn? x 4 x 3 x 5 xi x 2 x 6 x 1 Goal: compute xi without revealing anything else

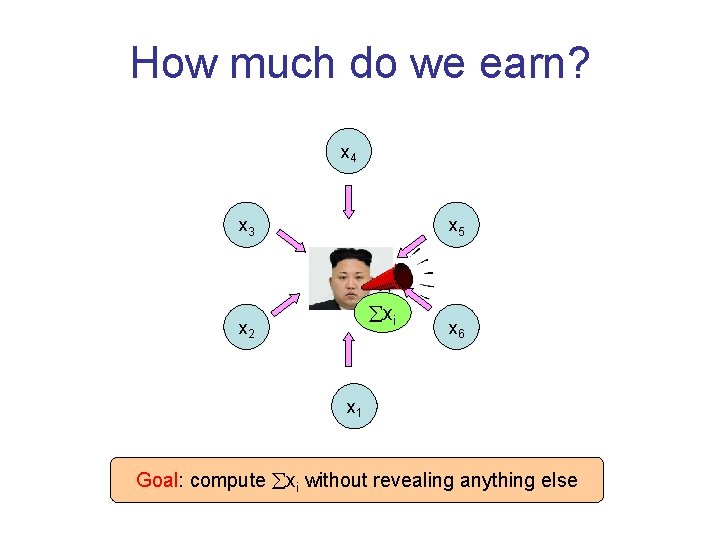
A better way? m 3=m 2+x 3 x 4 x 3 m 4=m 3+x 4 x 5 m 5=m 4+x 5 m 2=m 1+x 2 m 1=r+x 1 m 6 -r x 6 m 6=m 5+x 6 x 1 11) 0≤r<M Assumption: xi<M (say, M=10 (+ and – operations carried modulo M)

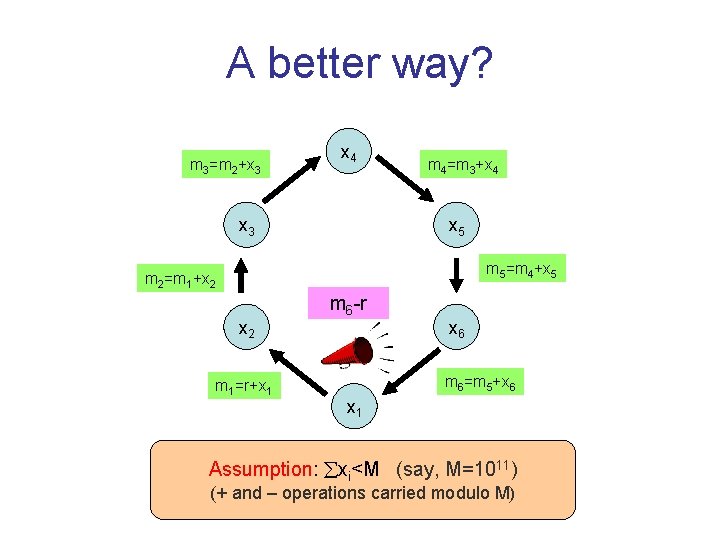
A security concern x 4 x 3 x 5 x 2 x 6 m 2=m 1+x 2 m 1 x 1

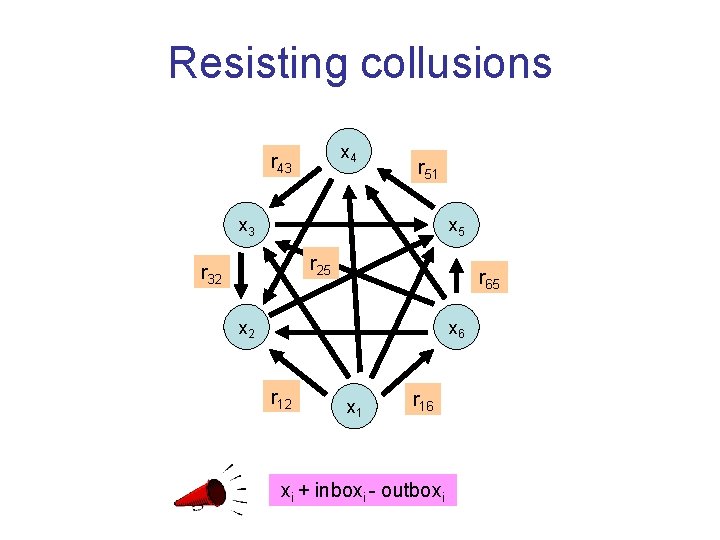
Resisting collusions x 4 r 43 r 51 x 3 x 5 r 25 r 32 r 65 x 2 x 6 r 12 x 1 r 16 xi + inboxi - outboxi

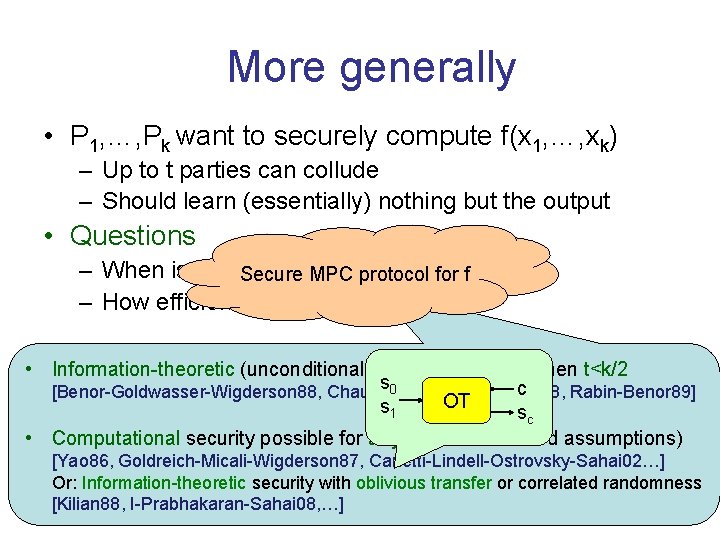
More generally • P 1, …, Pk want to securely compute f(x 1, …, xk) – Up to t parties can collude – Should learn (essentially) nothing but the output • Questions – When is this at all possible? Secure MPC protocol for f – How efficiently? • Information-theoretic (unconditional) security possible when t<k/2 s 0 c [Benor-Goldwasser-Wigderson 88, Chaum-Crepeau-Damgard 88, Rabin-Benor 89] OT s 1 sc • Computational security possible for any t (under standard assumptions) [Yao 86, Goldreich-Micali-Wigderson 87, Canetti-Lindell-Ostrovsky-Sahai 02…] Or: Information-theoretic security with oblivious transfer or correlated randomness [Kilian 88, I-Prabhakaran-Sahai 08, …]

More generally • P 1, …, Pk want to securely compute f(x 1, …, xk) – Up to t parties can collude – Should learn (essentially) nothing but the output • Questions – When is this at all possible? – How efficiently? • Several efficiency measures: communication, rounds, computation, randomness • Known results depend on the type of security and assumptions • Active area of research • Relatively small gap between “provable” and “heuristic” security • Strong synergy between theory and implementation efforts
![RealIdeal Paradigm GM 82 GMR 85 GMW 87 Can 00 Can 01 Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] •](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-10.jpg)
Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] • “Whatever an adversary can achieve by attacking the real protocol, it could have also achieved by attacking an ideal protocol that employs a trusted party. ” • Achieve = learn + influence • Formalized via a simulator • Captures privacy, correctness, independence of inputs.
![RealIdeal Paradigm GM 82 GMR 85 GMW 87 Can 00 Can 01 Real Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] Real](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-11.jpg)
Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] Real protocol Ideal protocol Trusted party computing f Honest parties Adversary X 2>7 Honest parties Simulator X 2>7
![RealIdeal Paradigm GM 82 GMR 85 GMW 87 Can 00 Can 01 Real Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] Real](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-12.jpg)
Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] Real protocol Ideal protocol Trusted party computing f Honest parties Simulator Adversary Environment Z 0/1
![RealIdeal Paradigm GM 82 GMR 85 GMW 87 Can 00 Can 01 Real Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] Real](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-13.jpg)
Real/Ideal Paradigm [GM 82, GMR 85, GMW 87, …, Can 00, Can 01] Real protocol Ideal protocol Protocol π securely realizes f if: Trusted party For every A there is S such that for every Z, computing f Pr[Real(Z, A, π)=1] ≅ Pr[Ideal(Z, S, f)=1] Honest Standalone MPC: Z only sends inputs and receives outputs parties UC MPC: Z arbitrarily interacts with A/S parties Simulator Adversary Environment Z 0/1

Definitions • Many different models… but: – answers to most natural questions are only sensitive to very few aspects of model – general connections between models – few “standard” models • Defining an MPC task involves specifying – – Functionality: what do we want to achieve? Network model: how are we going to do this? Adversary: who do we need to protect against? Security type: what kind of protection do we want?

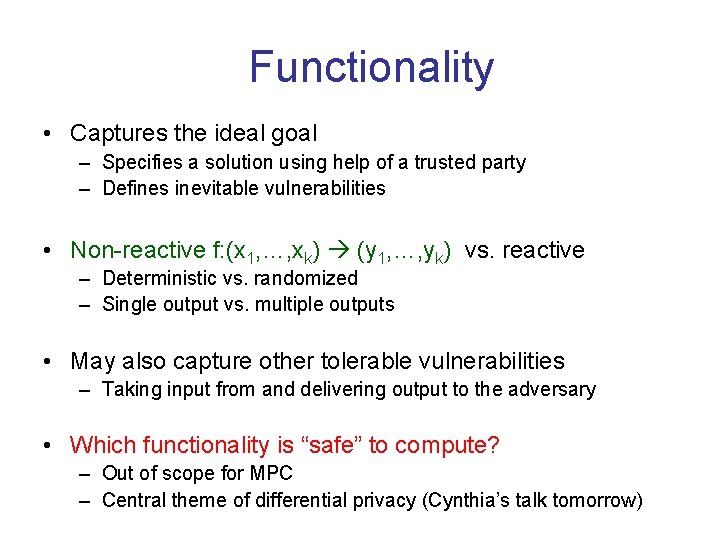
Functionality • Captures the ideal goal – Specifies a solution using help of a trusted party – Defines inevitable vulnerabilities • Non-reactive f: (x 1, …, xk) (y 1, …, yk) vs. reactive – Deterministic vs. randomized – Single output vs. multiple outputs • May also capture other tolerable vulnerabilities – Taking input from and delivering output to the adversary • Which functionality is “safe” to compute? – Out of scope for MPC – Central theme of differential privacy (Cynthia’s talk tomorrow)

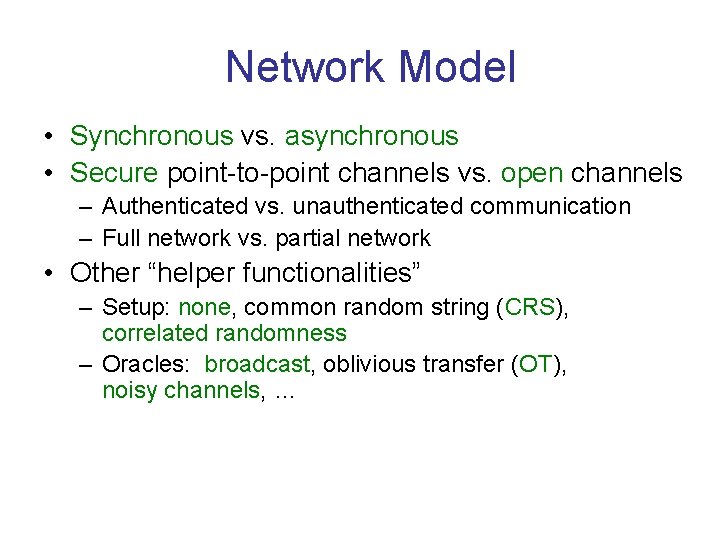
Network Model • Synchronous vs. asynchronous • Secure point-to-point channels vs. open channels – Authenticated vs. unauthenticated communication – Full network vs. partial network • Other “helper functionalities” – Setup: none, common random string (CRS), correlated randomness – Oracles: broadcast, oblivious transfer (OT), noisy channels, …

Adversary • Which sets of parties may be corrupted? – Typically: threshold t on number of corrupted parties – Honest majority vs. no honest majority • Passive (semi-honest) vs. active (malicious) • Computationally bounded vs. unbounded • Static vs. adaptive vs. mobile

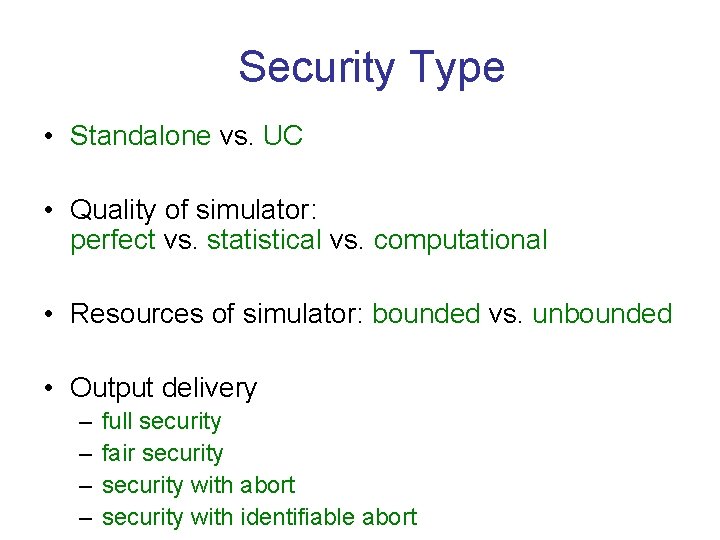
Security Type • Standalone vs. UC • Quality of simulator: perfect vs. statistical vs. computational • Resources of simulator: bounded vs. unbounded • Output delivery – – full security fair security with abort security with identifiable abort

Information-Theoretic Security • Unbounded adversary – Passive or active • Honest majority – Alternatively: OT oracle or correlated randomness • Secure point-to-point channels – Broadcast if adversary is active and t<k/2 • Security is typically (not always) – Unconditional – Universally composable – Adaptive

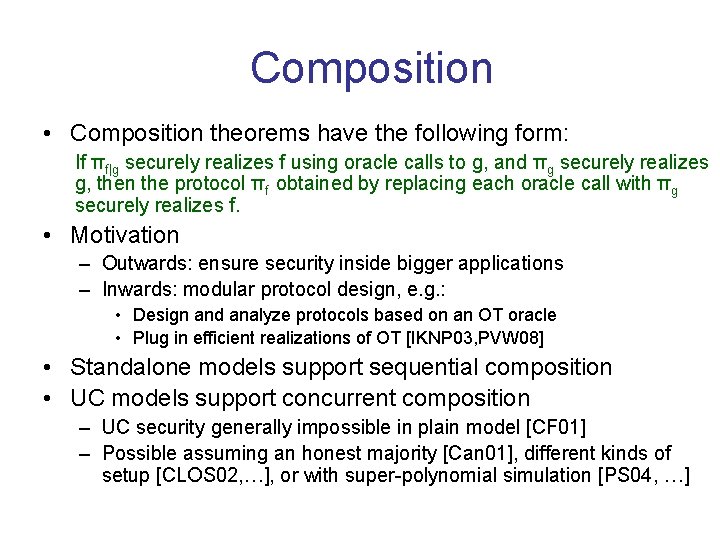
Composition • Composition theorems have the following form: If πf|g securely realizes f using oracle calls to g, and πg securely realizes g, then the protocol πf obtained by replacing each oracle call with πg securely realizes f. • Motivation – Outwards: ensure security inside bigger applications – Inwards: modular protocol design, e. g. : • Design and analyze protocols based on an OT oracle • Plug in efficient realizations of OT [IKNP 03, PVW 08] • Standalone models support sequential composition • UC models support concurrent composition – UC security generally impossible in plain model [CF 01] – Possible assuming an honest majority [Can 01], different kinds of setup [CLOS 02, …], or with super-polynomial simulation [PS 04, …]

Feasibility: open questions • Which functions can be computed fairly? – Some cannot [Cleve 86] – A lot of recent activity [GHKL 08, …, ABMO 15] • Which functions can be computed with information theoretic security? – What assumptions are needed for those that cannot? – Under what assumptions can f be reduced to g? – Large body of works [Kus 89, Bea 89, …, KMPS 14] • Composable security – Different ways around impossibility results (e. g. , “environmentally friendly” protocols [CLP 13]) – Simpler versions of UC model [CCL 15] • Find new ways for deriving feasibility results
![A simple MPC protocol IKMOP 13 Trusted Dealer RA RB Alice x fx y A simple MPC protocol [IKMOP 13] Trusted Dealer RA RB Alice (x) f(x, y)](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-22.jpg)
A simple MPC protocol [IKMOP 13] Trusted Dealer RA RB Alice (x) f(x, y) (y) Bob f(x, y) • Offline: – Set G[u, v] = f[u-dx, v-dy] for random dx, dy – Pick random RA, RB such that G = RA+RB – Alice gets RA, dx Bob gets RB, dy • Protocol on inputs (x, y): – Alice sends u=x+dx, Bob sends v=y+dy – Alice sends z. A= RA[u, v], Bob sends z. B= RB[u, v] – Both output z=z. A+z. B 0 1 1 0 1 2 1 0 2 0 1 2 0 0 1 1 0 1 dx dy

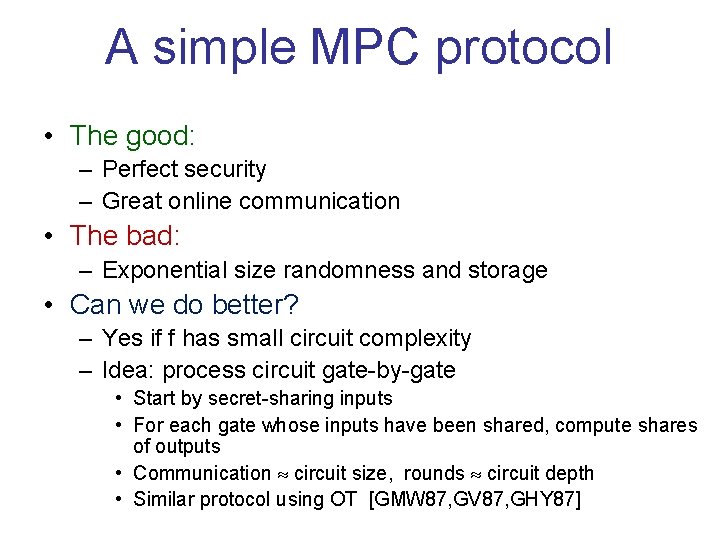
A simple MPC protocol • The good: – Perfect security – Great online communication • The bad: – Exponential size randomness and storage • Can we do better? – Yes if f has small circuit complexity – Idea: process circuit gate-by-gate • Start by secret-sharing inputs • For each gate whose inputs have been shared, compute shares of outputs • Communication circuit size, rounds circuit depth • Similar protocol using OT [GMW 87, GV 87, GHY 87]

A simple MPC protocol • The good: – Perfect security – Great online communication • The bad: – Exponential size randomness and storage • Can we use less randomness for every f?

A simple MPC protocol • The good: – Perfect security – Great online communication • The bad: – Exponential size randomness and storage • Can we use less randomness for every f? – Yes! – Best upper bound: 2 O~(√n) [BIKK 14] – Obtained via “computationally simple” 3 -server PIR or 3 query LDC [Yek 07, Efr 09] – Minimal randomness complexity wide open

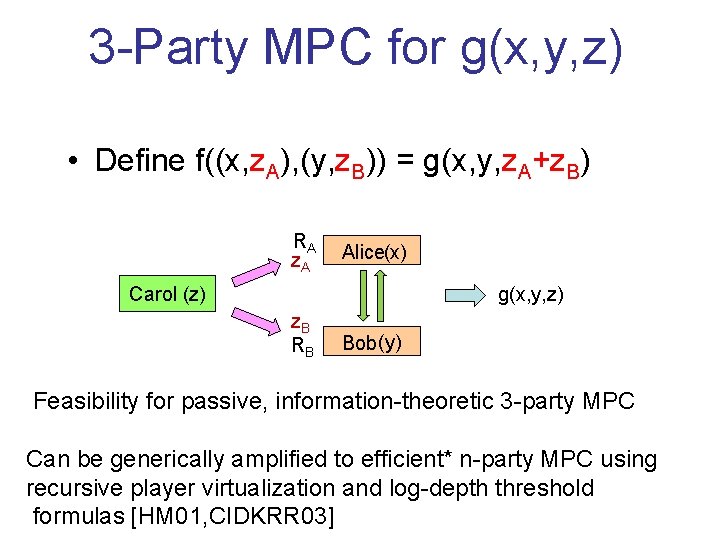
3 -Party MPC for g(x, y, z) • Define f((x, z. A), (y, z. B)) = g(x, y, z. A+z. B) RA (x) z. A Alice Carol (z) g(x, y, z) z. B (y) RB Bob Feasibility for passive, information-theoretic 3 -party MPC Can be generically amplified to efficient* n-party MPC using recursive player virtualization and log-depth threshold formulas [HM 01, CIDKRR 03]

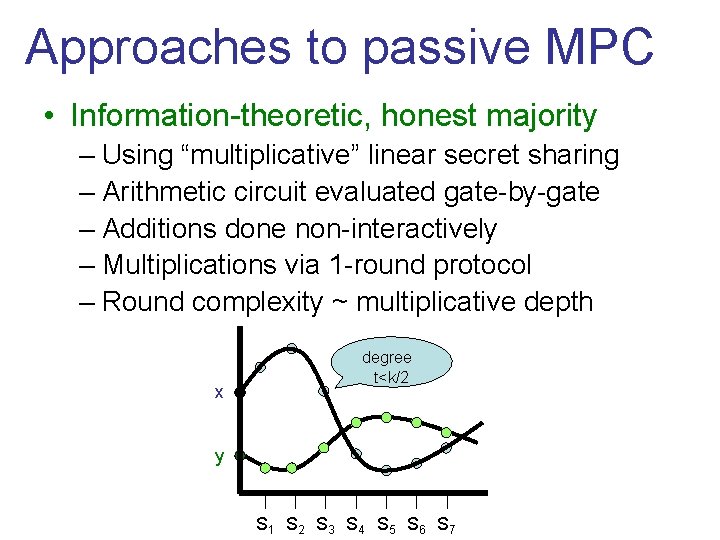
Approaches to passive MPC • Information-theoretic, honest majority – Using “multiplicative” linear secret sharing – Arithmetic circuit evaluated gate-by-gate – Additions done non-interactively – Multiplications via 1 -round protocol – Round complexity ~ multiplicative depth x degree t<k/2 y S 1 S 2 S 3 S 4 S 5 S 6 S 7

Approaches to passive MPC • Information-theoretic, t<k, OT-hybrid model – Using additive secret sharing over Z 2 – Boolean circuit evaluated gate-by-gate – XOR / NOT gates evaluated non-interactively – AND/OR: via one round of OT calls – Round complexity ~ multiplicative depth

Approaches to passive MPC • Boosting efficiency via randomized encodings / garbling schemes – Encode “complex” f by “simple” randomized f’ • Encoding can be information-theoretic or computational • Apply previous protocols to f’ – Typically used to reduce round complexity • 2 -round (3 -round) i. t. protocols with t<k/3 (t<k/2), 2 -round (4 -round) computational 2 PC (MPC) • Recent i. O-based constructions can also reduce communication, rebalance computation – Much recent work on optimizing Yao-style garbled circuits
![Approaches to passive MPC Using homomorphic encryption Linearhomomorphic FH 93 CDN 01 Approaches to passive MPC • Using homomorphic encryption – Linear-homomorphic [FH 93, CDN 01]](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-30.jpg)
Approaches to passive MPC • Using homomorphic encryption – Linear-homomorphic [FH 93, CDN 01] – FHE [Gen 09] – TFHE [AJLT 12] – Multi-key FHE [ATV 12, MW 15] • Using i. O [GGHR 14]

Active-Secure MPC • Security against active attacks is much more challenging. • Common paradigm: passive security active security – GMW compiler: use ZK proofs [GMW 87, …] – Make sub-protocols verifiable [BGW 88, CCD 88, …] – Ad-hoc cut-and-choose techniques […, LP 07, …] – AMD circuits [GIPST 14, IKST 14, GIP 15] – “MPC in the Head” [IKOS 07, IPS 08]

MPC in the Head
![Back to the 1980 s Zeroknowledge proofs for NP GMR 85 GMW 86 Back to the 1980 s • Zero-knowledge proofs for NP [GMR 85, GMW 86]](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-33.jpg)
Back to the 1980 s • Zero-knowledge proofs for NP [GMR 85, GMW 86] • Computational MPC with no honest majority [Yao 86, GMW 87] • Unconditional MPC with honest majority [BGW 88, CCD 88, RB 89] • Unconditional MPC with no honest majority assuming ideal OT [Kilian 88] • Are these unrelated?

Message of this part of talk • Honest-majority MPC is useful even when there is no honest majority! • Establishes unexpected relations between classical results • New results for MPC with no honest majority • New application domains for algebraic geometric codes – Support “constant rate” honest-majority MPC [CC 06, DI 06]

Zero-knowledge proofs • Goal: ZK proof for an NP-relation R(x, w) – Completeness – Soundness – Zero-knowledge • Towards using MPC: – define n-party functionality g(x; w 1, . . . , wn) = R(x, w 1. . . wn) – use any 2 -secure, perfectly correct protocol for g • security in passive model • honest majority when n 5
![MPC ZK IKOS 07 P 1 Pn P 2 V w 11 Vw 22 MPC ZK [IKOS 07] P 1 Pn P 2 V w 11 Vw 22](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-36.jpg)
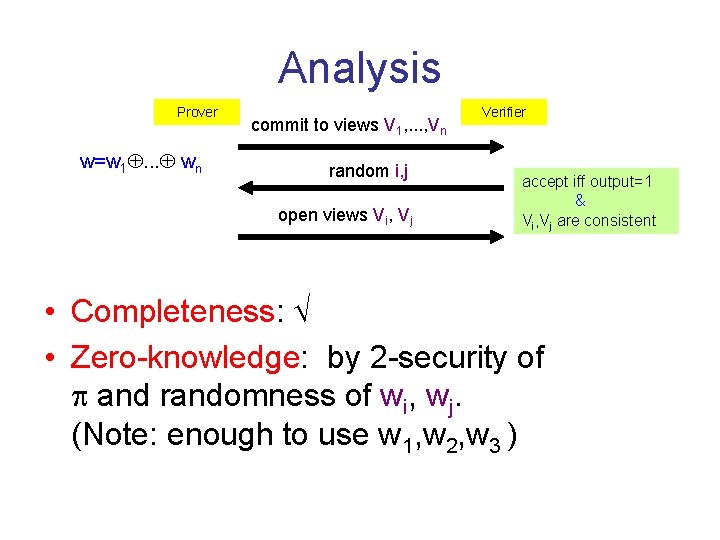
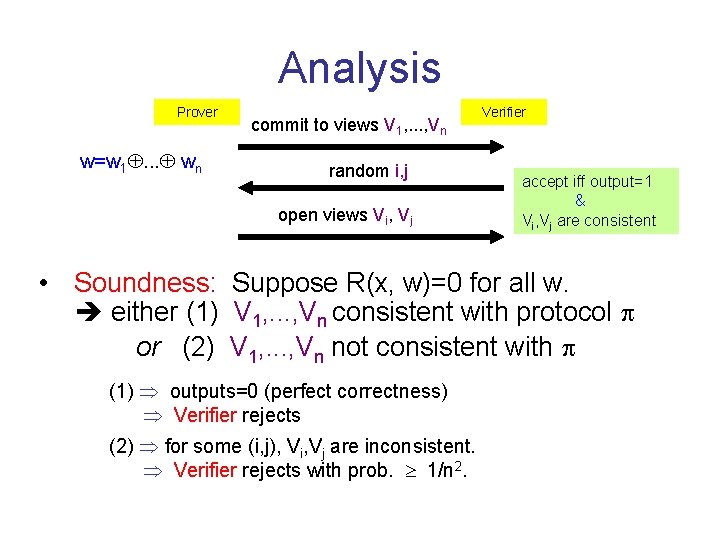
MPC ZK [IKOS 07] P 1 Pn P 2 V w 11 Vw 22 views V ww=w 1. . . w Vw 33 n P 3 nn V w 55 Vw 44 w P 5 P 4 Prover Given MPC protocol for g(x; w 1, . . . , wn) = R(x, w 1. . . wn) accept iff output=1 & Vi, Vj are consistent Verifier commit to views V 1, . . . , Vn random i, j open views Vi, Vj

Analysis Prover w=w 1. . . wn commit to views V 1, . . . , Vn random i, j open views Vi, Vj Verifier accept iff output=1 & Vi, Vj are consistent • Completeness: • Zero-knowledge: by 2 -security of and randomness of wi, wj. (Note: enough to use w 1, w 2, w 3 )

Analysis Prover w=w 1. . . wn commit to views V 1, . . . , Vn random i, j open views Vi, Vj Verifier accept iff output=1 & Vi, Vj are consistent • Soundness: Suppose R(x, w)=0 for all w. either (1) V 1, . . . , Vn consistent with protocol or (2) V 1, . . . , Vn not consistent with (1) outputs=0 (perfect correctness) Verifier rejects (2) for some (i, j), Vi, Vj are inconsistent. Verifier rejects with prob. 1/n 2.

Extensions • Works also with OT-based MPC – Simple consistency check • Variant: Use 1 -secure MPC – Open one view and one incident channel • Extends to MPC with error • Variant: Directly get 2 -s soundness error via security in active model active adversary – Two clients, n=O(s) servers – (n)-security with abort – Broadcast is “free” • Realize Com using OWF

Applications • Simple ZK proofs using: – (1, 3) semi-honest MPC [BGW 88, CCD 88] or [Mau 02] – (2, 3) semi-honest MPCOT [GMW 87, GV 87, GHY 87] • ZK proofs with O(|R|)+poly(k) communication – Using AG codes • Many good ZK protocols implied by MPC literature – ZK for linear algebra [CD 01, …]
![General 2 party protocols IPS 08 Life is easier when everyone follows instructions General 2 -party protocols [IPS 08] • Life is easier when everyone follows instructions…](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-41.jpg)
General 2 -party protocols [IPS 08] • Life is easier when everyone follows instructions… • GMW paradigm [GMW 87]: – passive-secure active-secure ’ – use ZK proofs to prove “sticking to protocol” • Non-black-box: ZK proofs in ’ involve code of – Typically considered “impractical” – Not applicable at all when uses an oracle • Functionality oracle: OT-hybrid model • Crypto primitive oracle: black-box PRG • Arithmetic oracle: black-box field or ring • Is there a “black-box alternative” to GMW?

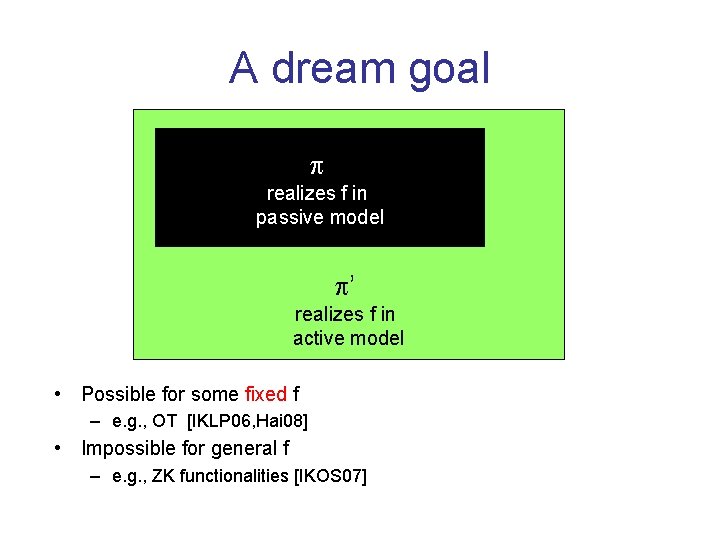
A dream goal realizes f in passive model ’ realizes f in active model • Possible for some fixed f – e. g. , OT [IKLP 06, Hai 08] • Impossible for general f – e. g. , ZK functionalities [IKOS 07]

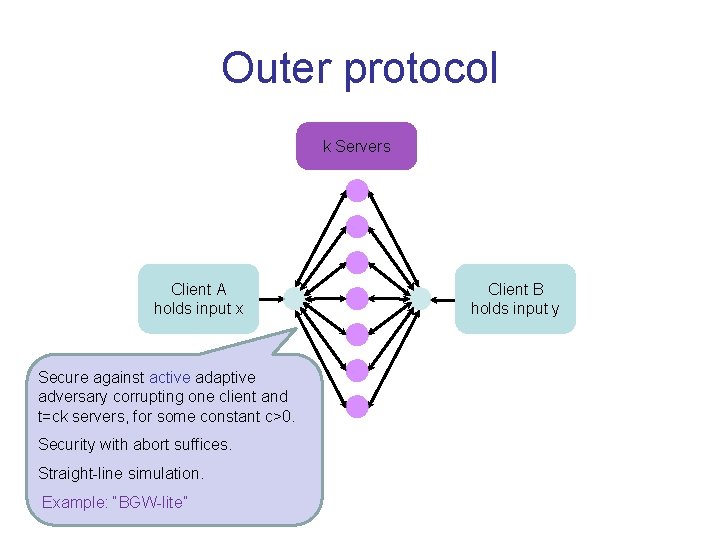
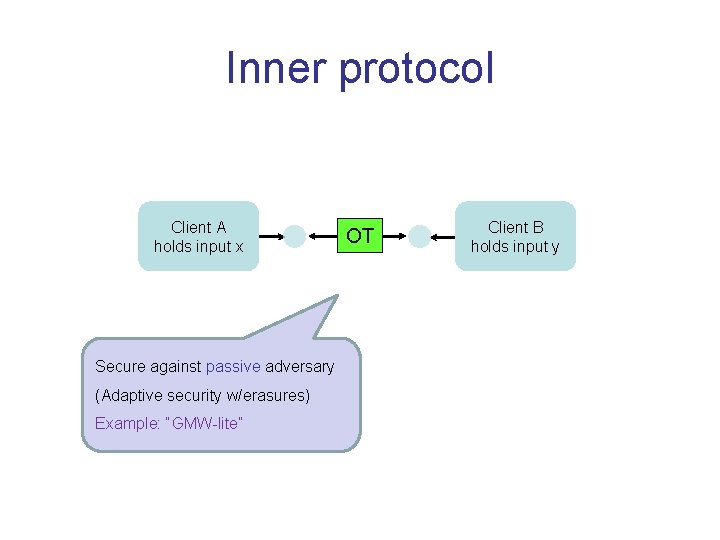
Idea • Combine two types of “easy” protocols: – Outer protocol: honest-majority active-secure MPC – Inner protocol: passive-secure 2 -party protocol • possibly in OT-hybrid model • Both are considerably easier than our goal • Both can have information-theoretic security

Outer protocol k Servers Client A holds input x Secure against active adaptive adversary corrupting one client and t=ck servers, for some constant c>0. Security with abort suffices. Straight-line simulation. Example: “BGW-lite” 44 Client B holds input y

Inner protocol Client A holds input x Secure against passive adversary (Adaptive security w/erasures) Example: “GMW-lite” OT Client B holds input y

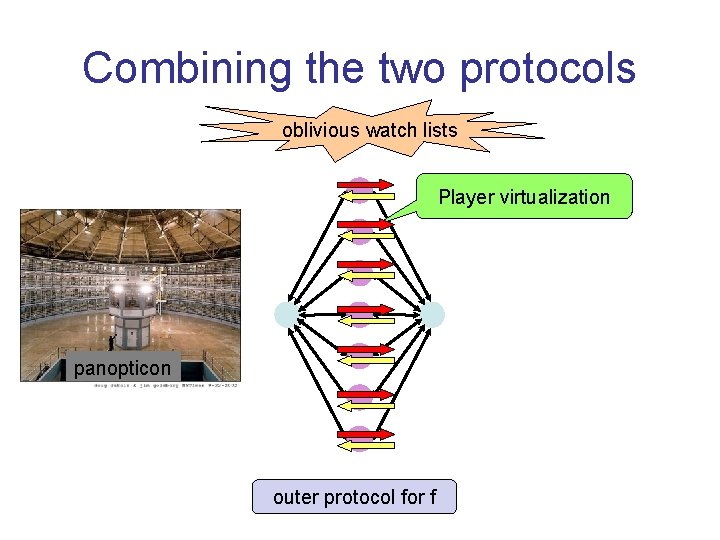
Combining the two protocols oblivious watch lists Player virtualization panopticon outer protocol for f

A closer look at server emulation • Assume servers are deterministic – This is already the case for natural protocols – Can be ensured in general with small overhead • In outer protocol, server i – gets messages from A and B – sends messages to A and B – may update a secret state • Captured by reactive 2 -party functionality Fi – Inputs = incoming messages – Outputs = outgoing messages • Use passive-secure protocol for Fi – Distribute server between clients – “Local” computations do not need to be distributed.

A closer look at watchlists • Inner protocol can’t prevent clients from cheating by sending “bad messages” • Watchlist mechanism ensures that cheating does not occur too often – Client doesn’t know which instances of inner protocol are watched – Two cases: • Client cheats in t instances cheating is tolerated by t-security of outer protocol • Client cheats in >t instances will be caught with overwhelming probability • Non-interactive form of “cut-and-choose”

Applications • Revisiting the classics – BGW-lite + GMW-lite Kilian • Efficient MPC with no honest majority – O(1) bits per gate in OT-hybrid model (+ additive term) – All crypto can be pushed to preprocessing • Constant-round MPCOT (t<n) using black-box PRG – Extending 2 -party “cut-and-choose” Yao • Efficient OT extension in malicious model • Constant-rate b. b. reduction of OT to semi-honest OT • Secure arithmetic computation over black-box fields /rings • Protocols making black-box use of linear-homomorphic encryption

Communication Complexity

Fully Homomorphic Encryption Gentry ‘ 09 • Settles main communication complexity questions in complexity-based cryptography – Even under “nice” assumptions [BV 11, …] • Main open questions – Further improve assumptions – Improve practical computational overhead • FHE >> PKE >> SKE >> XOR

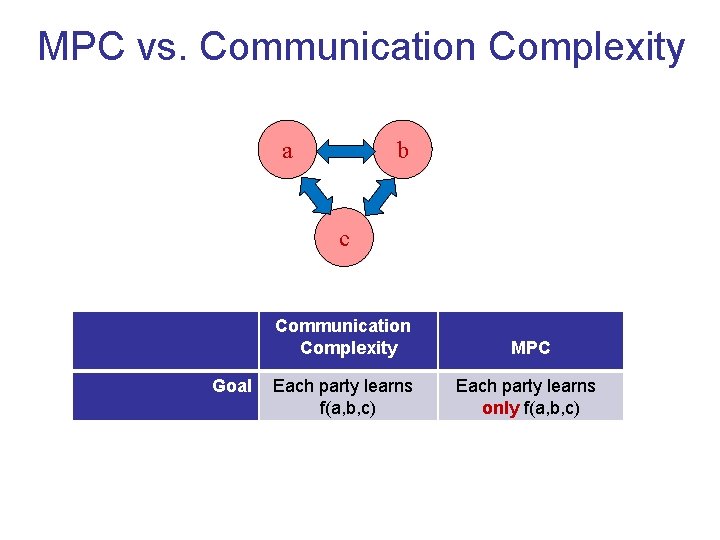
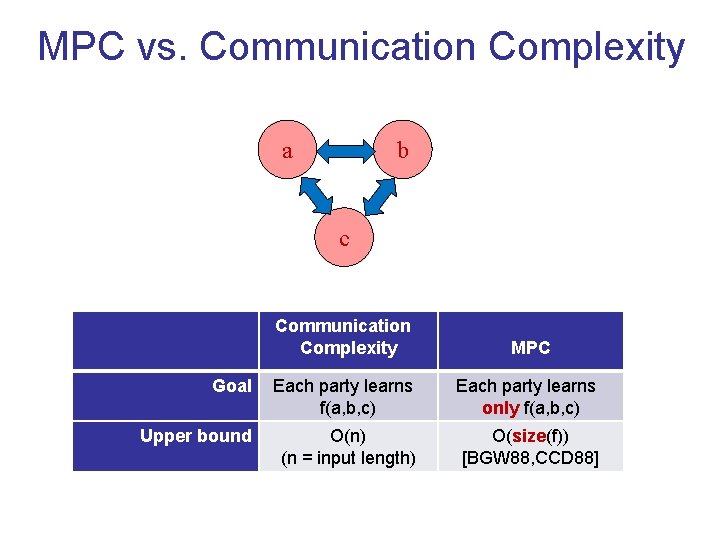
MPC vs. Communication Complexity a b c Goal Communication Complexity MPC Each party learns f(a, b, c) Each party learns only f(a, b, c)

MPC vs. Communication Complexity a b c Communication Complexity MPC Goal Each party learns f(a, b, c) Each party learns only f(a, b, c) Upper bound O(n) (n = input length) O(size(f)) [BGW 88, CCD 88]

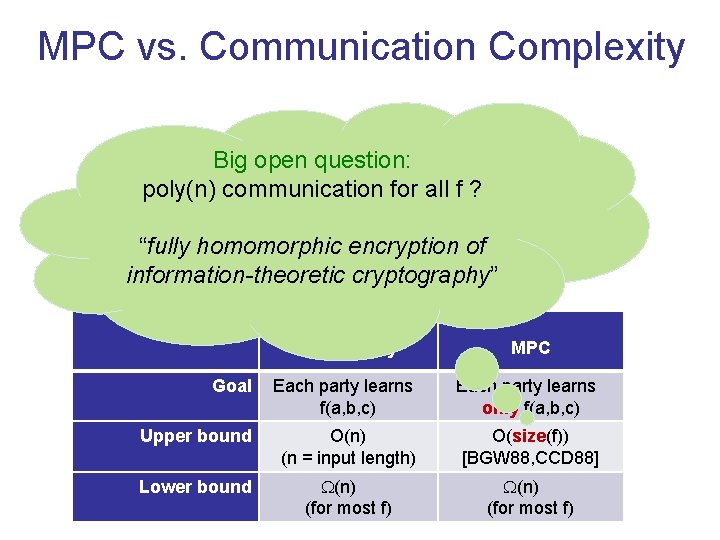
MPC vs. Communication Complexity a b Big open question: poly(n) communication for all f ? c “fully homomorphic encryption of information-theoretic cryptography” Communication Complexity MPC Goal Each party learns f(a, b, c) Each party learns only f(a, b, c) Upper bound O(n) (n = input length) O(size(f)) [BGW 88, CCD 88] Lower bound (n) (for most f)

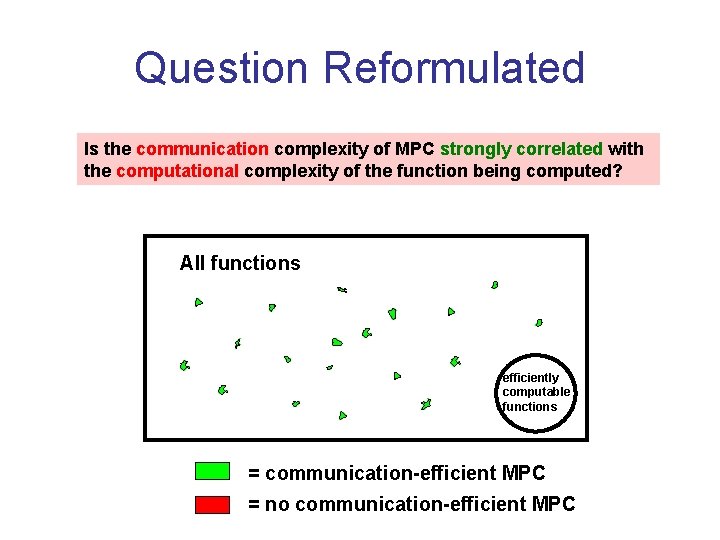
Question Reformulated Is the communication complexity of MPC strongly correlated with the computational complexity of the function being computed? All functions efficiently computable functions = communication-efficient MPC = no communication-efficient MPC
![KT 00 IK 04 1990 1995 2000 The three problems are closely related [KT 00] [IK 04] 1990 1995 2000 • The three problems are closely related](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-56.jpg)
[KT 00] [IK 04] 1990 1995 2000 • The three problems are closely related
![Private Information Retrieval ChorGoldreichKushilevitzSudan 95 database x0 1n Main question minimize communication logn Private Information Retrieval [Chor-Goldreich-Kushilevitz-Sudan 95] database x∈{0, 1}n ? Main question: minimize communication (logn](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-57.jpg)
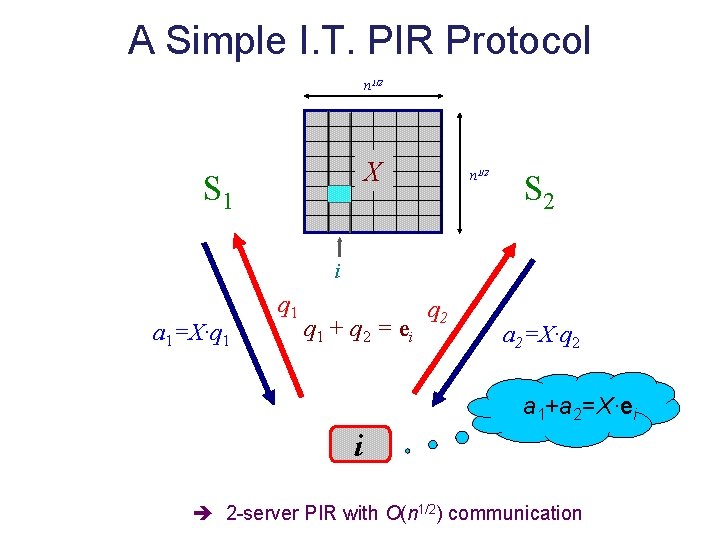
Private Information Retrieval [Chor-Goldreich-Kushilevitz-Sudan 95] database x∈{0, 1}n ? Main question: minimize communication (logn vs. n) ? ? xi “Information. Theoretic” vs. Computational

A Simple I. T. PIR Protocol n 1/2 X S 1 n 1/2 S 2 i a 1=X·q 1 q 1 + q 2 = ei q 2 a 2=X·q 2 a 1+a 2=X·ei i 2 -server PIR with O(n 1/2) communication
![A Simple Computational PIR Protocol KushilevitzOstrovsky 97 Tool linear homomorphic encryption a b Protocol A Simple Computational PIR Protocol [Kushilevitz-Ostrovsky 97] Tool: (linear) homomorphic encryption a b Protocol:](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-59.jpg)
A Simple Computational PIR Protocol [Kushilevitz-Ostrovsky 97] Tool: (linear) homomorphic encryption a b Protocol: = a+b Client sends E(ei) • E(0) E(1) E(0) (=c 1 c 2 c 3 c 4) n 1/2 0 1 1 0 1 1 1 0 n 1/2 X=1 1 0 0 0 1 Server replies with E(X·ei) • c 2 c 3 c 1 c 2 c 4 Client recovers ith column of X • i 1 -server CPIR with ~ O(n 1/2) communication

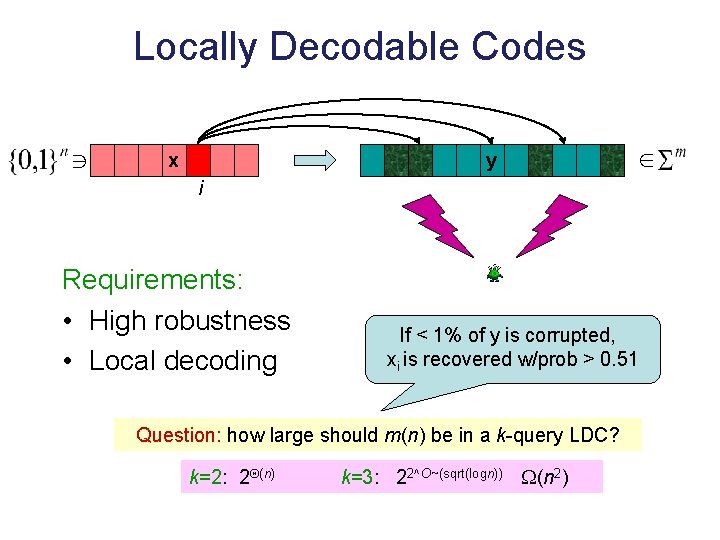
Locally Decodable Codes x y i Requirements: • High robustness • Local decoding If < 1% of y is corrupted, xi is recovered w/prob > 0. 51 Question: how large should m(n) be in a k-query LDC? k=2: 2 (n) k=3: 22^O~(sqrt(logn)) (n 2)
![From I T PIR to LDC KatzTrevisan 00 Simplifying assumptions Servers compute same From I. T. PIR to LDC [Katz-Trevisan 00] Simplifying assumptions: • Servers compute same](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-61.jpg)
From I. T. PIR to LDC [Katz-Trevisan 00] Simplifying assumptions: • Servers compute same function of (x, q) • Each query is uniform over its support set k-server PIR with -bit queries and -bit answers k-query LDC of length 2 over ={0, 1} y[q]=Answer(x, q) • Uniform PIR queries “smooth” LDC decoder Binary LDC PIR with one answer bit per server robustness • Arrows can be reversed

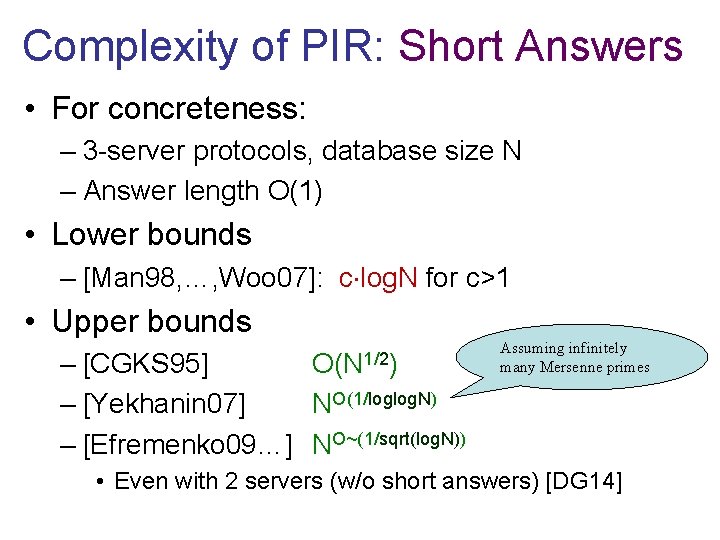
Complexity of PIR: Short Answers • For concreteness: – 3 -server protocols, database size N – Answer length O(1) • Lower bounds – [Man 98, …, Woo 07]: c log. N for c>1 • Upper bounds – [CGKS 95] – [Yekhanin 07] NO(1/loglog. N) – [Efremenko 09…] NO~(1/sqrt(log. N)) O(N 1/2) Assuming infinitely many Mersenne primes • Even with 2 servers (w/o short answers) [DG 14]

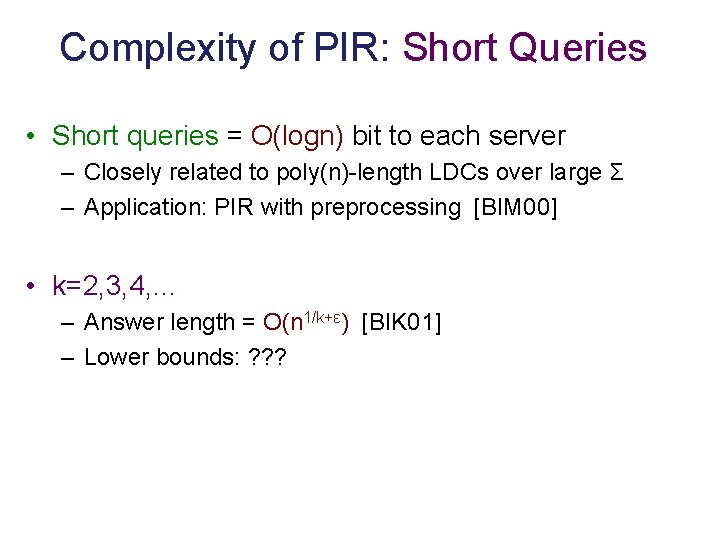
Complexity of PIR: Short Queries • Short queries = O(logn) bit to each server – Closely related to poly(n)-length LDCs over large Σ – Application: PIR with preprocessing [BIM 00] • k=2, 3, 4, … – Answer length = O(n 1/k+ε) [BIK 01] – Lower bounds: ? ? ?

Tool: Secret Sharing • Randomized mapping of secret s to shares (s 1, s 2, …, sk) – Linear secret sharing: shares = L(s, r 1, …, rm) • Useful examples for linear schemes – – Additive sharing: s=s 1+s 2+s 3 Shamir’s secret sharing: si=p(i) where p(x)=s+rx CNF secret sharing: s=r 1+r 2+r 3, s 1=(r 2, r 3), s 2=(r 1, r 3), s 3=(r 2, r 3) CNF is “maximal”, Additive is “minimal” • For any linear scheme: [v], x [<v, x>] (without interaction) – PIR with short answers reduces to client sharing [ei] while hiding i – Enough to share a multiple of [ei]
![Tool Matching Vectors Yek 07 Efr 09 DGY 10 Vectors u 1 Tool: Matching Vectors [Yek 07, Efr 09, DGY 10] • Vectors u 1, …,](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-65.jpg)
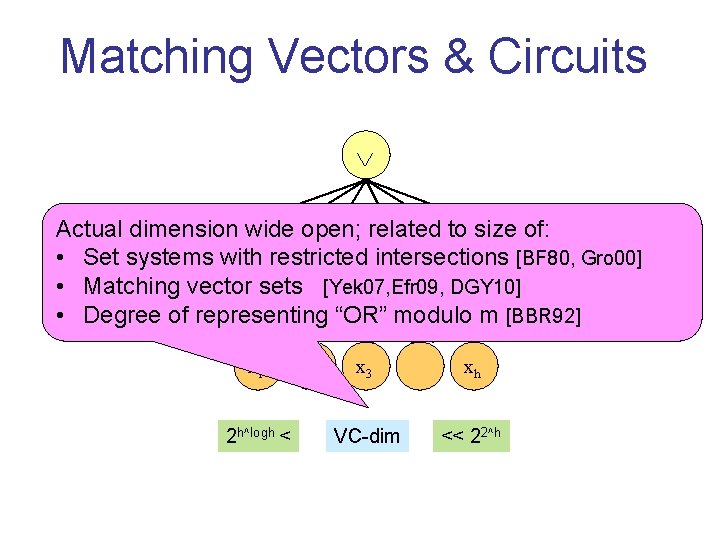
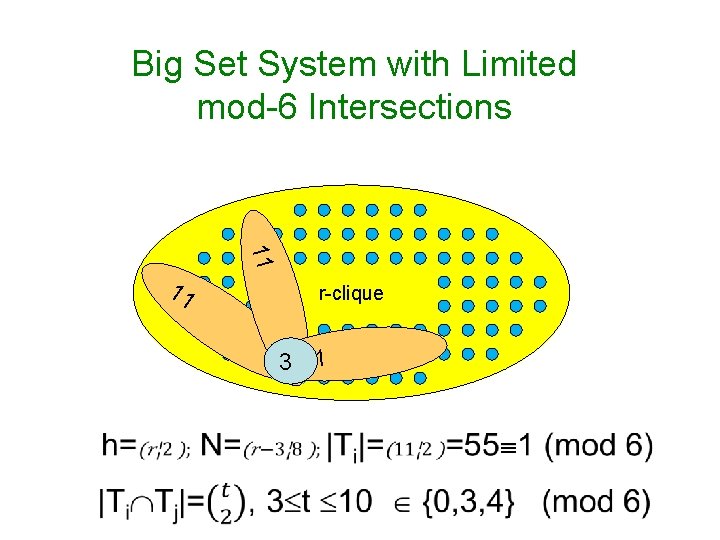
Tool: Matching Vectors [Yek 07, Efr 09, DGY 10] • Vectors u 1, …, un in Zmh are S-matching if: – <ui, ui> = 0 – <ui, uj> ∈ S (0∉S) • Surprising fact: super-polynomial n(h) when m is a composite – For instance, n=h. O(logh) for m=6, S={1, 3, 4} – Based on large set systems with restricted intersections modulo m [BF 80, Gro 00]
![Tool Matching Vectors Yek 07 Efr 09 DGY 10 Matching vectors can be Tool: Matching Vectors [Yek 07, Efr 09, DGY 10] • Matching vectors can be](https://slidetodoc.com/presentation_image_h/e4f34add7474a24df7acc4427df51f81/image-66.jpg)
Tool: Matching Vectors [Yek 07, Efr 09, DGY 10] • Matching vectors can be used to compress “negated” shared unit vector – [ui] locally expanded to [v] = [<ui, u 1>, <ui, u 2>, …, <ui, un>] – v is 0 only in i-th entry • Apply local share conversion to obtain shares of [v’], where v’ is nonzero only in i-th entry – Efremenko 09: share conversion from Shamir* to additive, requires large m – Beimel-I-Kushilevitz-Orlov 12: share conversions from CNF to additive, m=6, 15, …

Matching Vectors & Circuits Actual dimension wide open; related to size of: • Set systems with restricted intersections [BF 80, Gro 00] mod mod mod • Matching vector sets [Yek 07, Efr 09, DGY 10] • Degree of representing “OR” modulo m [BBR 92] x 1 2 h^logh < 6 6 x 2 6 x 3 xh VC-dim << 22^h 6

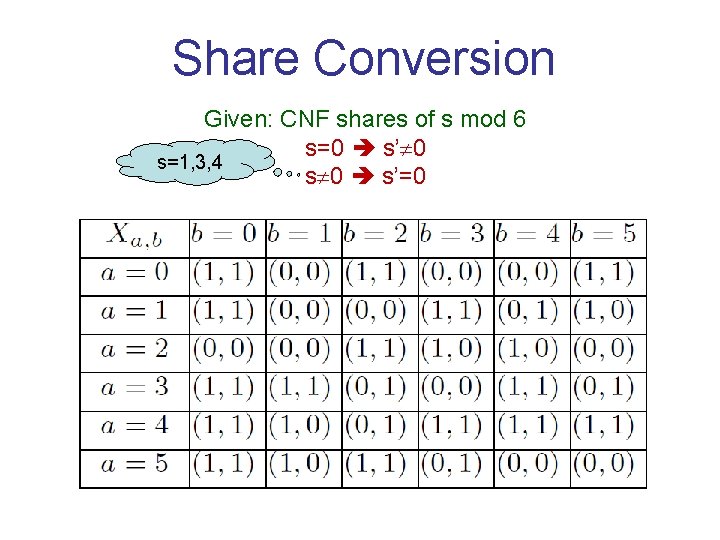
Share Conversion Given: CNF shares of s mod 6 s=0 s’ 0 s=1, 3, 4 s 0 s’=0

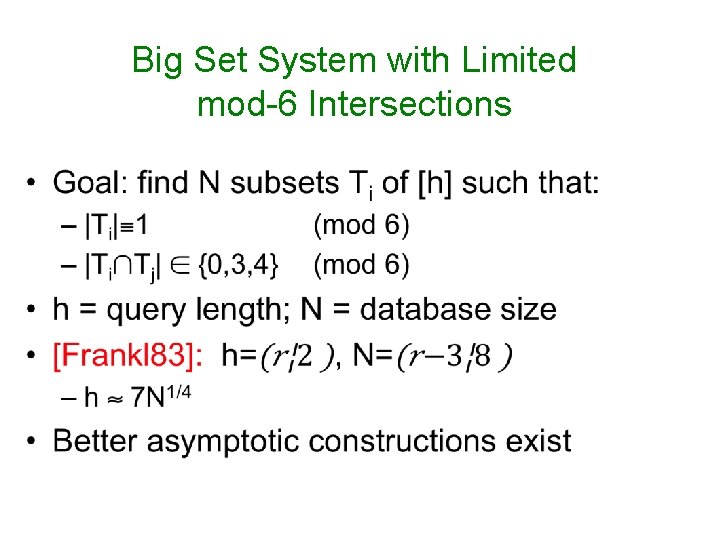
Big Set System with Limited mod-6 Intersections

Big Set System with Limited mod-6 Intersections 11 11 r-clique 3 11

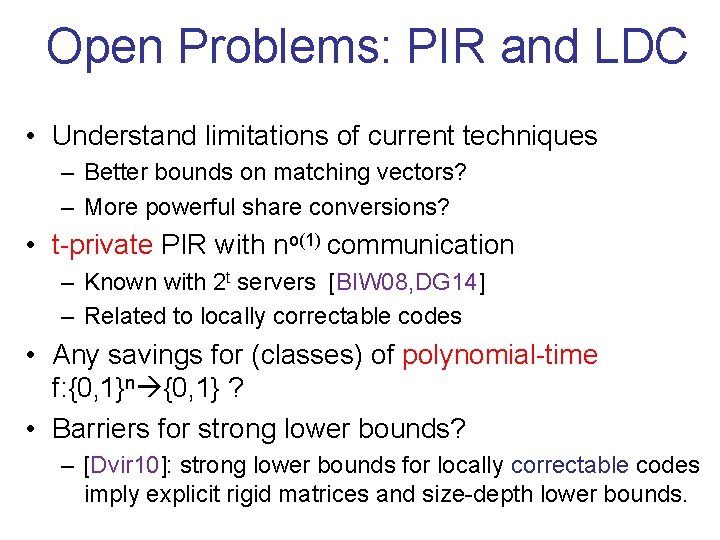
Open Problems: PIR and LDC • Understand limitations of current techniques – Better bounds on matching vectors? – More powerful share conversions? • t-private PIR with no(1) communication – Known with 2 t servers [BIW 08, DG 14] – Related to locally correctable codes • Any savings for (classes) of polynomial-time f: {0, 1}n {0, 1} ? • Barriers for strong lower bounds? – [Dvir 10]: strong lower bounds for locally correctable codes imply explicit rigid matrices and size-depth lower bounds.

Open Problems: IT MPC • Communication complexity – High end: understand complexity of “worst” f • O(2 n^ ) vs. (n) • Closely related to PIR and LDC – Mid range: nontrivial savings for “moderately hard” f? – Low end: bounds on amortized rate of finite f • In honest-majority setting • Given noisy channels

Open Problems: IT MPC • Round complexity – Known: efficient constant-round protocols for NC 1, NL – Big question: efficient constant-round protocols for P? – Smaller question: 2 -round, t<k/2, for • Computational complexity – Known: constant overhead with O(1) parties, polylog(k) with k parties – Constant overhead for k parties? – Will imply (under reasonable assumptions) constant-overhead computational ZK and active 2 PC

Open Problems: Computational MPC • Communication complexity – FHE from LWE? Is interaction helpful? – OWF => polylogarithmic 2 -private 3 -server PIR? • Yes in 2 -server case [GI 14, BGI 15] • Round complexity – 2 -round MPC from other assumptions – Eliminating CRS from recent 2 -round protocols [GGHR 14, MW 15] • Computational complexity – Better assumptions for passive 2 PC with constant overhead [IKOS 08, App 11] – Constant-overhead ZK under any assumption • Partial progress in [DMGN 14] • MPC in RAM model [OS 08, …] – tomorrow!

The research leading to these results has received funding from the European Union's Seventh Framework Programme (FP 7/2007 -2013) under grant agreement no. 259426 – ERC – Cryptography and Complexity