MOSQUITO BREEDING ATTACK Spread of bots using Peer

MOSQUITO BREEDING ATTACK: Spread of bots using Peer To Peer INSTRUCTOR: Dr. Cliff Zou PRESENTED BY : BHARAT SOUNDARARAJAN & AMIT SHRIVATSAVA
INTRODUCTION • Major threat to the security of internet • Botnet is a collection of compromised computer under a control of single identity known as the bot controller • Botnet uses vulnerability like other malwares to infect other machines in the network • Different types of bots: Agobot, Sdbot, Spybot, GTbot
HOW BOTNETS WORK • A botnet operator sends worm continuously infecting ordinary users • The bot on the infected PC logs into a web server called Command & Control server(C&C) • The botnet operator send instructions via server to the infected PC’s • Used as a platform for DDOS and Spam attacks
Different types of Bot communication § Centralized Communication Group of bots connected to C&C server Weaknesses: § They can be easier because many clients connect the same point § Discovery of the central location can compromise the whole system
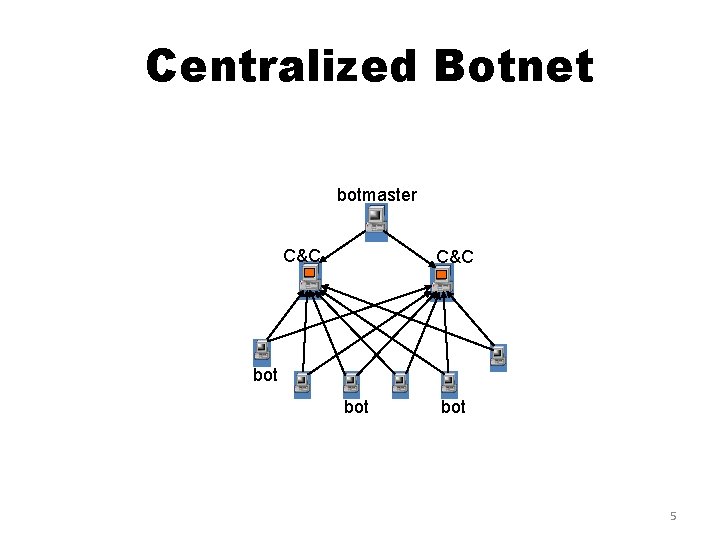
Centralized Botnet botmaster C&C bot bot 5
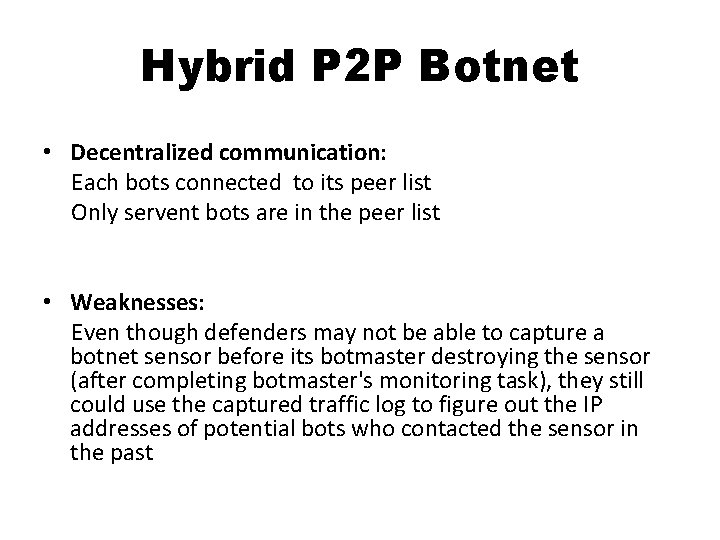
Hybrid P 2 P Botnet • Decentralized communication: Each bots connected to its peer list Only servent bots are in the peer list • Weaknesses: Even though defenders may not be able to capture a botnet sensor before its botmaster destroying the sensor (after completing botmaster's monitoring task), they still could use the captured traffic log to figure out the IP addresses of potential bots who contacted the sensor in the past
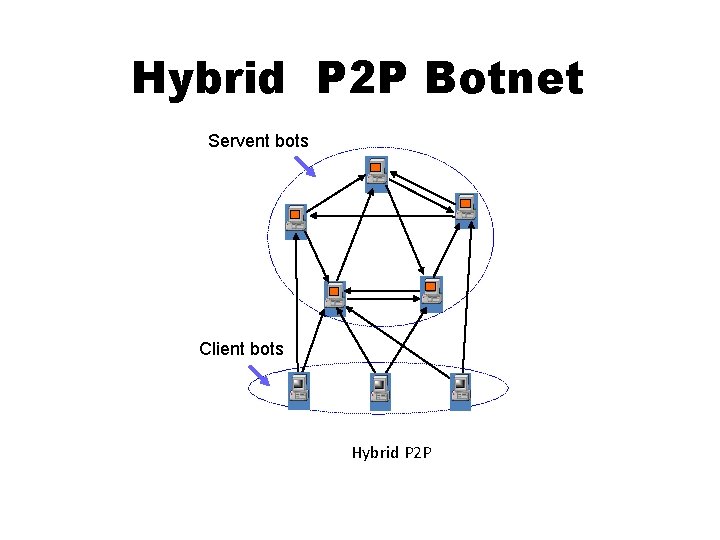
Hybrid P 2 P Botnet Servent bots Client bots Hybrid P 2 P
Mosquito Breeding Attack • New attack using both Peer 2 Peer architecture and centralized architecture • A centralized bots will generate many P 2 P bots inside the internet • These P 2 P bots will start a separate network and get new peers for its new network
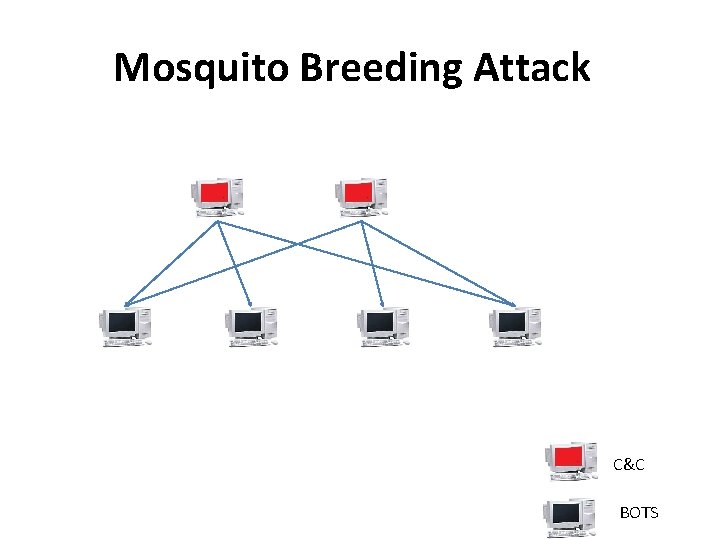
Mosquito Breeding Attack C&C BOTS
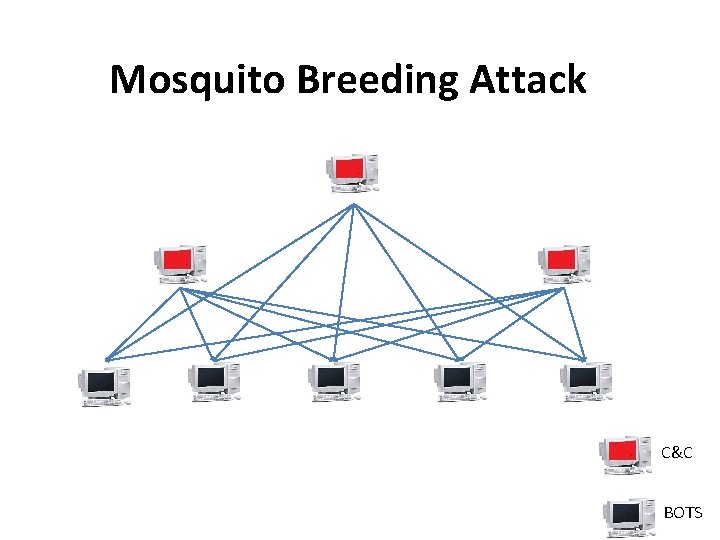
Mosquito Breeding Attack C&C BOTS

SIMULATION • • Platform: Windows/Linux Tools: Eclipse Source Code: Java/Applet File: Random. java

Algorithm • Step 1: Simulate Arbitrary Servers/Attackers • Step 2: Simulate Random Number Of clients(bots) • Step 3: Generate Botnet attacks from the attackers to the client • Step 4: The server loads the code into any randomly chosen client • Step 5: The client inturn becomes the server • Step 6: New bot continues breeding the code among the new clients

DEMO FOR THE SIMULATION
Bot Conversion Model • Bots gets converted from client to server is identified • Time taken for each bot to change from client to server is calculated • A graph is drawn using bots in the X-axis and time taken for conversion in the Y-axis
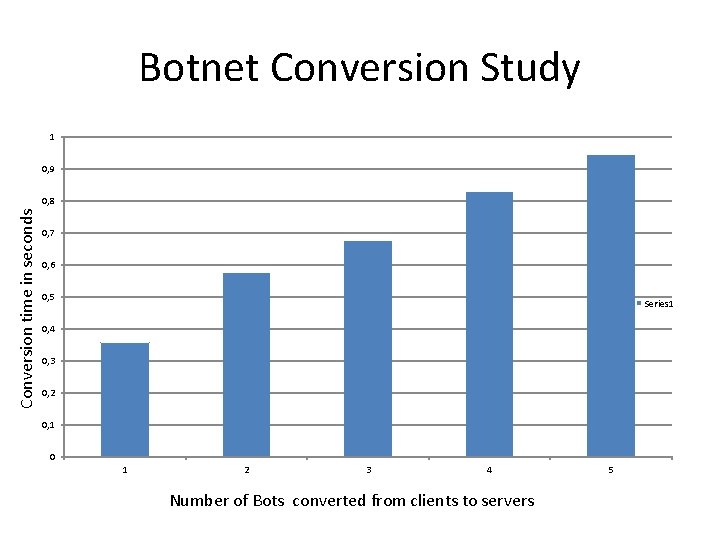
Botnet Conversion Study 1 0, 9 Conversion time in seconds 0, 8 0, 7 0, 6 0, 5 Series 1 0, 4 0, 3 0, 2 0, 1 0 1 2 3 4 Number of Bots converted from clients to servers 5

ADVANTAGES • To overcome the problem of C&C center in botnet • Capturing of one C&C doesn’t affect the architecture • It works independently • More robust and more probing
CONCLUSION • This shows how bots may work in the future • We have shown by simulation how attack propagate • We have also shown the conversion time of bots into c&c server

THANK YOU
- Slides: 18