More on Programs and Processes Jeff Chase Duke


![cpu. c (OSTEP) int main(int argc, char *argv[]) { if (argc != 2) { cpu. c (OSTEP) int main(int argc, char *argv[]) { if (argc != 2) {](https://slidetodoc.com/presentation_image_h2/95d3c582669b46e5a353726b787b7c84/image-8.jpg)
![mem. c (OSTEP) data p int main(int argc, char *argv[]) { int *p; p mem. c (OSTEP) data p int main(int argc, char *argv[]) { int *p; p](https://slidetodoc.com/presentation_image_h2/95d3c582669b46e5a353726b787b7c84/image-9.jpg)


![Alignment p + 0 x 0 X char p[] char *p int p[] int* Alignment p + 0 x 0 X char p[] char *p int p[] int*](https://slidetodoc.com/presentation_image_h2/95d3c582669b46e5a353726b787b7c84/image-16.jpg)



![Simple I/O: args and printf #include <stdio. h> int main(int argc, char* argv[]) { Simple I/O: args and printf #include <stdio. h> int main(int argc, char* argv[]) {](https://slidetodoc.com/presentation_image_h2/95d3c582669b46e5a353726b787b7c84/image-24.jpg)
![Environment variables #include <stdio. h> #include <stdlib. h> int main(int argc, char* argv[], char* Environment variables #include <stdio. h> #include <stdlib. h> int main(int argc, char* argv[], char*](https://slidetodoc.com/presentation_image_h2/95d3c582669b46e5a353726b787b7c84/image-25.jpg)

- Slides: 27

More on Programs and Processes Jeff Chase Duke University

Today • What does the machine/OS look like to a program? – (continued) • How is the machine shared among processes? • How are processes protected?

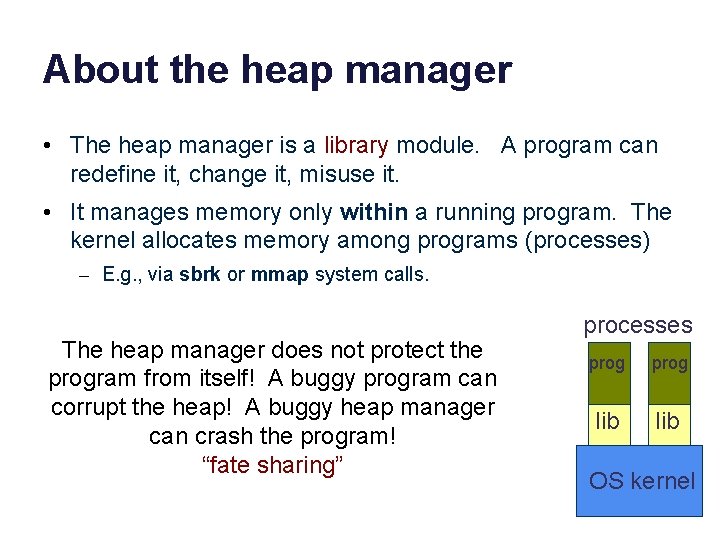
About the heap manager • The heap manager is a library module. A program can redefine it, change it, misuse it. • It manages memory only within a running program. The kernel allocates memory among programs (processes) – E. g. , via sbrk or mmap system calls. The heap manager does not protect the program from itself! A buggy program can corrupt the heap! A buggy heap manager can crash the program! “fate sharing” processes prog lib OS kernel

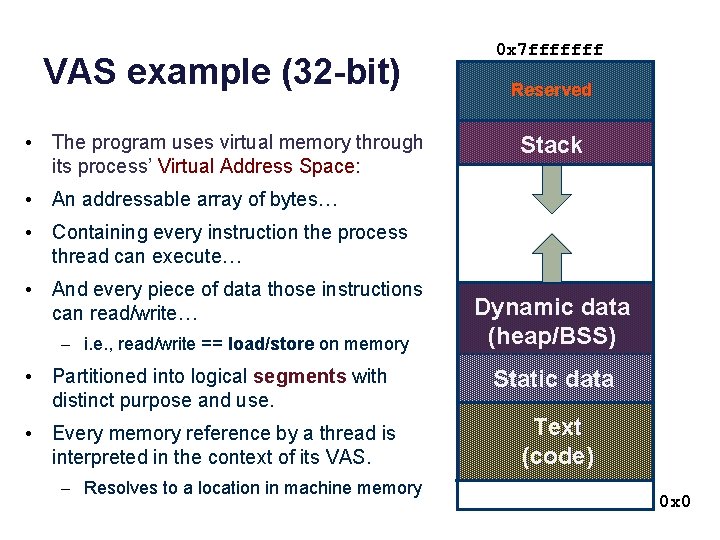
VAS example (32 -bit) • The program uses virtual memory through its process’ Virtual Address Space: 0 x 7 fffffff Reserved Stack • An addressable array of bytes… • Containing every instruction the process thread can execute… • And every piece of data those instructions can read/write… – i. e. , read/write == load/store on memory Dynamic data (heap/BSS) • Partitioned into logical segments with distinct purpose and use. Static data • Every memory reference by a thread is interpreted in the context of its VAS. Text (code) – Resolves to a location in machine memory 0 x 0

0 x 7 fffffff Reserved Stack Dynamic data (heap/BSS) Static data Text (code) 0 x 0

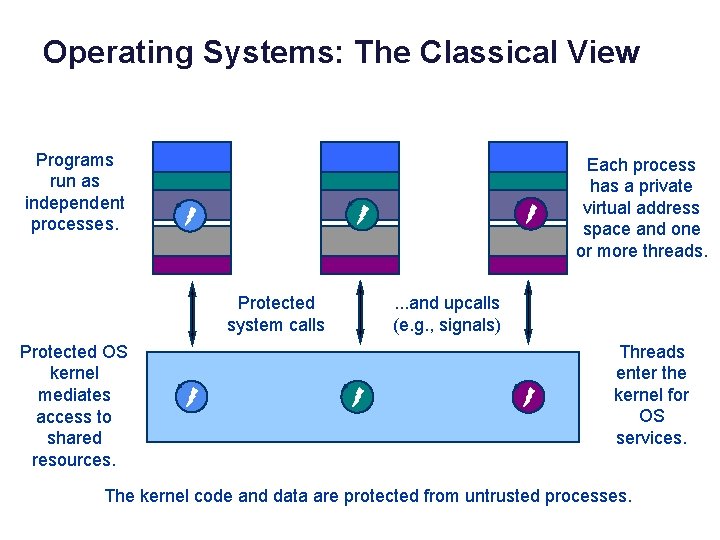
Operating Systems: The Classical View Programs run as independent processes. data Protected system calls Protected OS kernel mediates access to shared resources. Each process has a private virtual address space and one or more threads. . and upcalls (e. g. , signals) Threads enter the kernel for OS services. The kernel code and data are protected from untrusted processes.

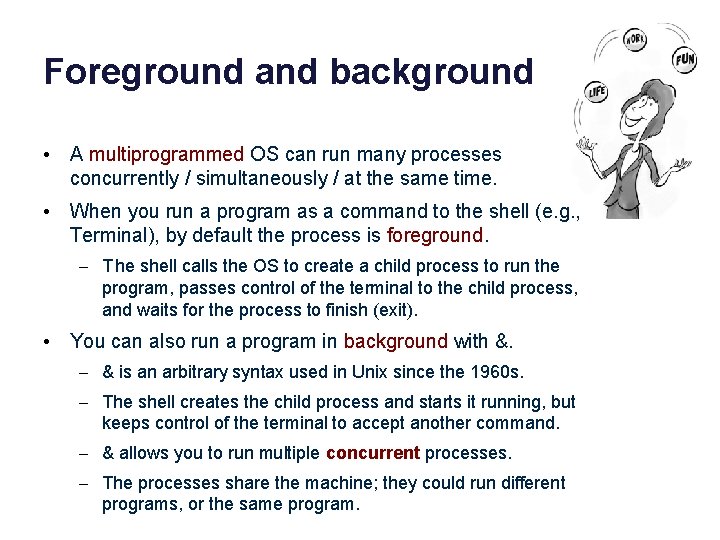
Foreground and background • A multiprogrammed OS can run many processes concurrently / simultaneously / at the same time. • When you run a program as a command to the shell (e. g. , Terminal), by default the process is foreground. – T he shell calls the OS to create a child process to run the program, passes control of the terminal to the child process, and waits for the process to finish (exit). • You can also run a program in background with &. – & is an arbitrary syntax used in Unix since the 1960 s. – The shell creates the child process and starts it running, but keeps control of the terminal to accept another command. – & allows you to run multiple concurrent processes. – The processes share the machine; they could run different programs, or the same program.
![cpu c OSTEP int mainint argc char argv if argc 2 cpu. c (OSTEP) int main(int argc, char *argv[]) { if (argc != 2) {](https://slidetodoc.com/presentation_image_h2/95d3c582669b46e5a353726b787b7c84/image-8.jpg)
cpu. c (OSTEP) int main(int argc, char *argv[]) { if (argc != 2) { fprintf(stderr, "usage: cpu <string>n"); exit(1); } char *str = argv[1]; while (1) { printf("%sn", str); Spin(1); } return 0; } time chase$ cc -o cpu. c chase$. /cpu A & chase$. /cpu B & A A B B B A B …
![mem c OSTEP data p int mainint argc char argv int p p mem. c (OSTEP) data p int main(int argc, char *argv[]) { int *p; p](https://slidetodoc.com/presentation_image_h2/95d3c582669b46e5a353726b787b7c84/image-9.jpg)
mem. c (OSTEP) data p int main(int argc, char *argv[]) { int *p; p = malloc(sizeof(int)); *p = atoi(argv[1]); while (1) { Spin(1); *p = *p + 1; printf("(pid: %d) value of p: %dn”, getpid(), *p); } } pid: 5587 pid: 5588 chase$ cc -o mem. c chase$. /mem 21 & chase$. /mem 42 & (pid: 5587) value of p: 22 (pid: 5587) value of p: 23 (pid: 5587) value of p: 24 (pid: 5588) value of p: 43 (pid: 5588) value of p: 44 (pid: 5587) value of p: 25 (pid: 5587) value of p: 26 …

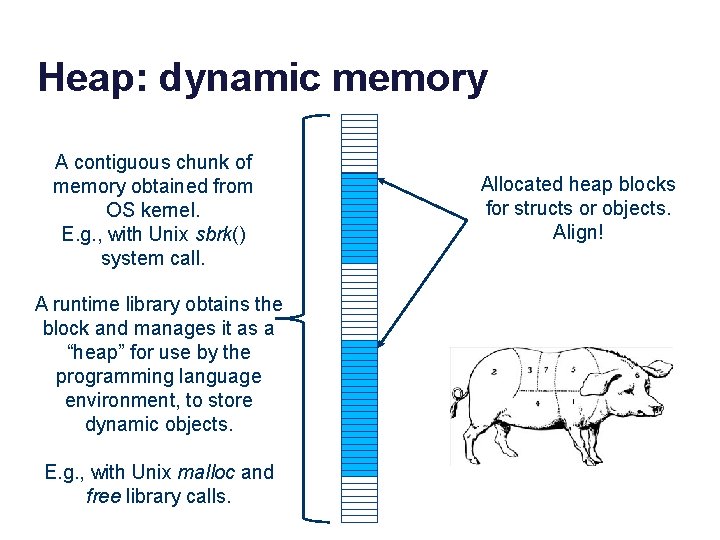
Heap: dynamic memory A contiguous chunk of memory obtained from OS kernel. E. g. , with Unix sbrk() system call. A runtime library obtains the block and manages it as a “heap” for use by the programming language environment, to store dynamic objects. E. g. , with Unix malloc and free library calls. Allocated heap blocks for structs or objects. Align!

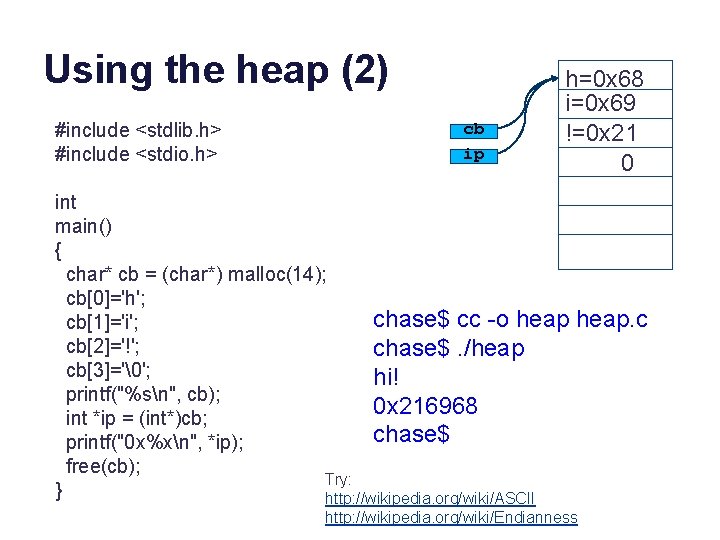
Using the heap (1) #include <stdlib. h> #include <stdio. h> int main() { char* cb = (char*) malloc(14); cb[0]='h'; cb[1]='i'; chase$ cc -o heap. c cb[2]='!'; chase$. /heap cb[3]='�'; hi! printf("%sn", cb); chase$ free(cb); }

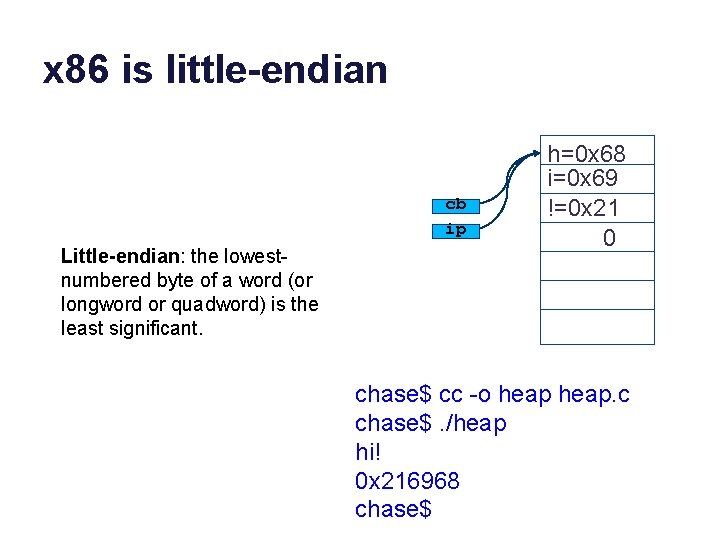
Using the heap (2) #include <stdlib. h> #include <stdio. h> cb ip h=0 x 68 i=0 x 69 !=0 x 21 0 int main() { char* cb = (char*) malloc(14); cb[0]='h'; chase$ cc -o heap cb[1]='i'; cb[2]='!'; chase$. /heap cb[3]='�'; hi! printf("%sn", cb); 0 x 216968 int *ip = (int*)cb; chase$ printf("0 x%xn", *ip); free(cb); Try: } http: //wikipedia. org/wiki/ASCII heap. c http: //wikipedia. org/wiki/Endianness

Endianness Lilliput and Blefuscu are at war over which end of a soft-boiled egg to crack. Gulliver’s Travel’s 1726 A silly difference among machine architectures creates a need for byte swapping when unlike machines exchange data over a network.

x 86 is little-endian cb ip Little-endian: the lowestnumbered byte of a word (or longword or quadword) is the least significant. h=0 x 68 i=0 x 69 !=0 x 21 0 chase$ cc -o heap. c chase$. /heap hi! 0 x 216968 chase$

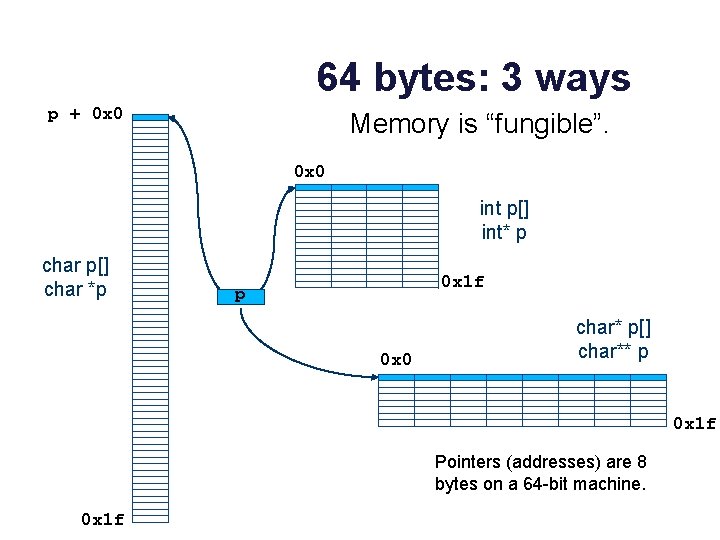
64 bytes: 3 ways p + 0 x 0 Memory is “fungible”. 0 x 0 int p[] int* p char p[] char *p 0 x 1 f p 0 x 0 char* p[] char** p 0 x 1 f Pointers (addresses) are 8 bytes on a 64 -bit machine. 0 x 1 f
![Alignment p 0 x 0 X char p char p int p int Alignment p + 0 x 0 X char p[] char *p int p[] int*](https://slidetodoc.com/presentation_image_h2/95d3c582669b46e5a353726b787b7c84/image-16.jpg)
Alignment p + 0 x 0 X char p[] char *p int p[] int* p X 0 x 1 f p char* p[] char** p 0 x 0 X 0 x 1 f Machines desire/require that an n-byte type is aligned on an n-byte boundary. n = 2 i 0 x 1 f

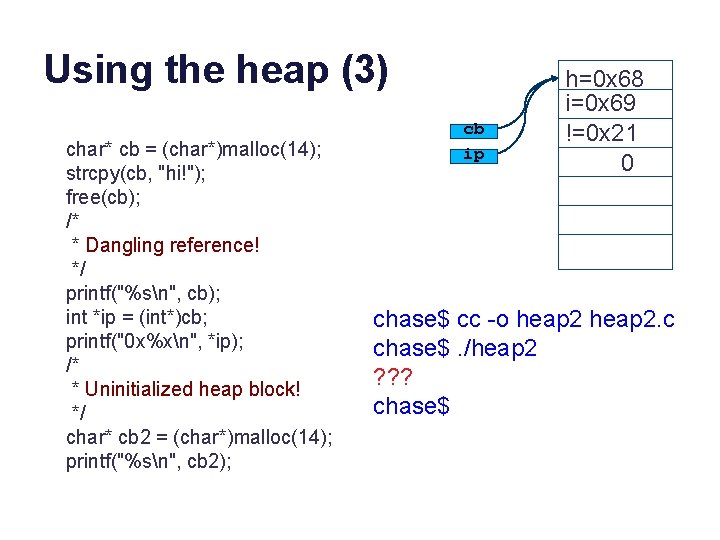
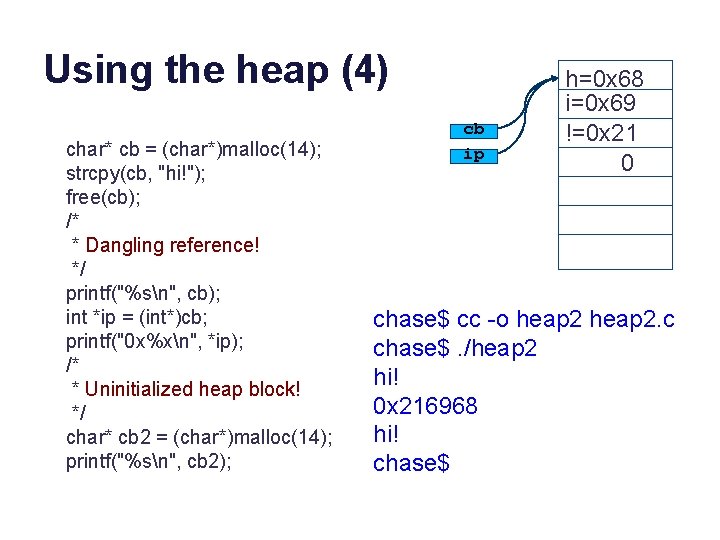
Using the heap (3) char* cb = (char*)malloc(14); strcpy(cb, "hi!"); free(cb); /* * Dangling reference! */ printf("%sn", cb); int *ip = (int*)cb; printf("0 x%xn", *ip); /* * Uninitialized heap block! */ char* cb 2 = (char*)malloc(14); printf("%sn", cb 2); cb ip h=0 x 68 i=0 x 69 !=0 x 21 0 chase$ cc -o heap 2. c chase$. /heap 2 ? ? ? chase$

Using the heap (4) char* cb = (char*)malloc(14); strcpy(cb, "hi!"); free(cb); /* * Dangling reference! */ printf("%sn", cb); int *ip = (int*)cb; printf("0 x%xn", *ip); /* * Uninitialized heap block! */ char* cb 2 = (char*)malloc(14); printf("%sn", cb 2); cb ip h=0 x 68 i=0 x 69 !=0 x 21 0 chase$ cc -o heap 2. c chase$. /heap 2 hi! 0 x 216968 hi! chase$

WARNING • These behaviors are undefined. • Any program whose behavior relies on the meaning of a dangling reference is incorrect. • For example, a change in the allocation policy of the heap manager could result in different behavior. • Can a program stay safe from dangling references by just never calling free?

Another way • Java’s new operator calls malloc “under the hood”. – Allocate a heap block for each new object. – How big should the heap block be? Who decides? – Java initializes the block by automatically calling a type-specific constructor defined by the program. – C++ is the same. • But in Java there is no free (or delete)! – No dangling references! • How does Java avoid memory leaks?

Digression: Garbage collection • Java has new but no free (or delete)! – No dangling references! • Q: How does Java avoid memory leaks? • A: automatic garbage collection • Java is strongly typed: e. g. , it tracks and controls pointers, and it knows where all of them are and what object types they reference. • Java knows if an object has no references pointing to it, and it calls free for you! • But Java has no pointer arithmetic: your program cannot manipulate virtual addresses as numbers, as in C.

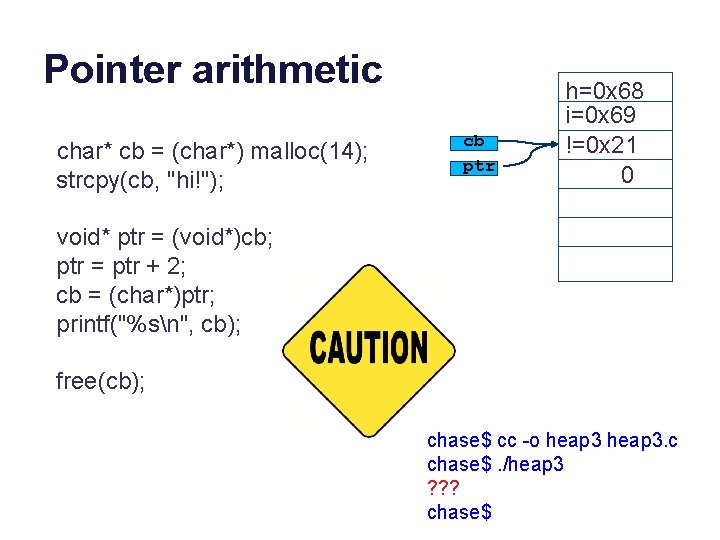
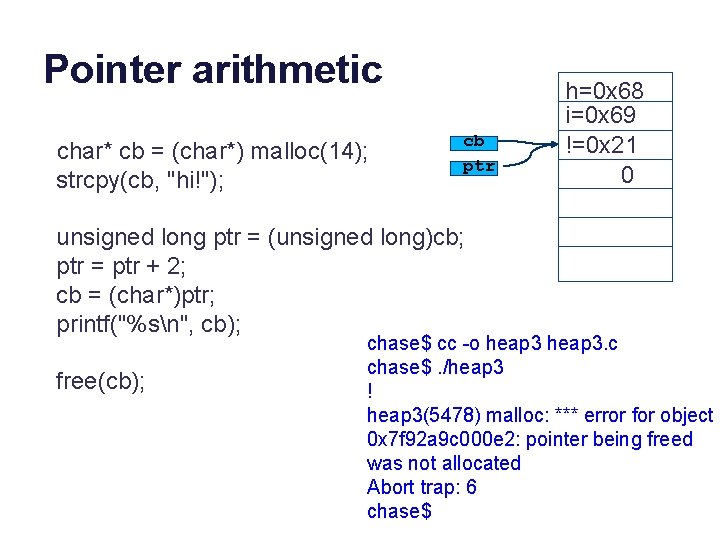
Pointer arithmetic char* cb = (char*) malloc(14); strcpy(cb, "hi!"); cb ptr h=0 x 68 i=0 x 69 !=0 x 21 0 void* ptr = (void*)cb; ptr = ptr + 2; cb = (char*)ptr; printf("%sn", cb); free(cb); chase$ cc -o heap 3. c chase$. /heap 3 ? ? ? chase$

Pointer arithmetic char* cb = (char*) malloc(14); strcpy(cb, "hi!"); cb ptr unsigned long ptr = (unsigned long)cb; ptr = ptr + 2; cb = (char*)ptr; printf("%sn", cb); free(cb); h=0 x 68 i=0 x 69 !=0 x 21 0 chase$ cc -o heap 3. c chase$. /heap 3 ! heap 3(5478) malloc: *** error for object 0 x 7 f 92 a 9 c 000 e 2: pointer being freed was not allocated Abort trap: 6 chase$
![Simple IO args and printf include stdio h int mainint argc char argv Simple I/O: args and printf #include <stdio. h> int main(int argc, char* argv[]) {](https://slidetodoc.com/presentation_image_h2/95d3c582669b46e5a353726b787b7c84/image-24.jpg)
Simple I/O: args and printf #include <stdio. h> int main(int argc, char* argv[]) { int i; printf("arguments: %dn", argc); for (i=0; i<argc; i++) { printf("%d: %sn", i, argv[i]); } }
![Environment variables include stdio h include stdlib h int mainint argc char argv char Environment variables #include <stdio. h> #include <stdlib. h> int main(int argc, char* argv[], char*](https://slidetodoc.com/presentation_image_h2/95d3c582669b46e5a353726b787b7c84/image-25.jpg)
Environment variables #include <stdio. h> #include <stdlib. h> int main(int argc, char* argv[], char* envp[]) { int i; int count = atoi(argv[1]); for (i=0; i < count; i++) { printf("env %d: %sn", i, envp[i]); } }

Libraries • Programs may incorporate (link to) libraries packaged with the OS or written by third parties. – E. g. , C standard library and standard I/O library • These libraries may even define a system API that applications use. (e. g. , heap manager malloc and free is in a library). • Libraries run as part of the program. Any failure in the library can interfere with other parts of the running program, and vice versa. • These libraries have no more privilege or power than any other part of the running program. • However, some libraries are merely wrappers for system calls that transfer control to the trusted operating system kernel.

Protection / isolation On most platforms, program execution contexts are isolated. They cannot interfere with one another, even if they are running the same program. I. e. , each context is its own sandbox/lockbox. The programs may fail independently. In classical OS, a context is called a process. Each has a private virtual address space. Butler Lampson’s definition: “I am isolated if anything that goes wrong is my fault (or my program’s fault). ” Isolation might not be absolute. E. g. , the program instances may choose to interact, or may access shared data.