Monitoring Architecture for Lawful Interception in Vo IP





- Slides: 13

Monitoring Architecture for Lawful Interception in Vo. IP Networks Author: Balamurugan Karpagavinayagam, Radu State, Olivier Festor Internet Monitoring and Protection, 2007. ICIMP 2007. Second International Conference Speaker: Po-Chou Chen 10/23/2021 1

Outline Introduction n Challenges in LI n Monitoring Architecture n Configuration setup n Prototype Implementation n Conclusion n 10/23/2021 2

Introduction n n Lawful Interception (LI) is well implemented in the PSTN networks Voice over Internet Protocol (Vo. IP) has made the LI for the Law Enforcement Agencies (LEA) a more challenging issue because of the diverse use of protocols PSTN networks is centralized network architecture ¨ In Vo. IP networks the voice traffic are carried over IP ¨ PSTN have a fixed path for the phone and circuit switched ¨ Vo. IP do not have a fixed path for the call and packet switched ¨ 10/23/2021 3

Challenges in LI n In Vo. IP networks ¨ Signal and data messages travel in different paths ¨ Users can be anywhere in the internet ¨ Use of Multiple protocols from different standard bodies ¨ Use of Security Mechanisms at various protocol levels Convergence of diverse technologies (fiber optics, ADSL, etc. , ) n One another issue ¨ if the target lies in another service provider network , then the monitoring of RTP packets could not be done. ¨ Because lack of information 4 10/23/2021

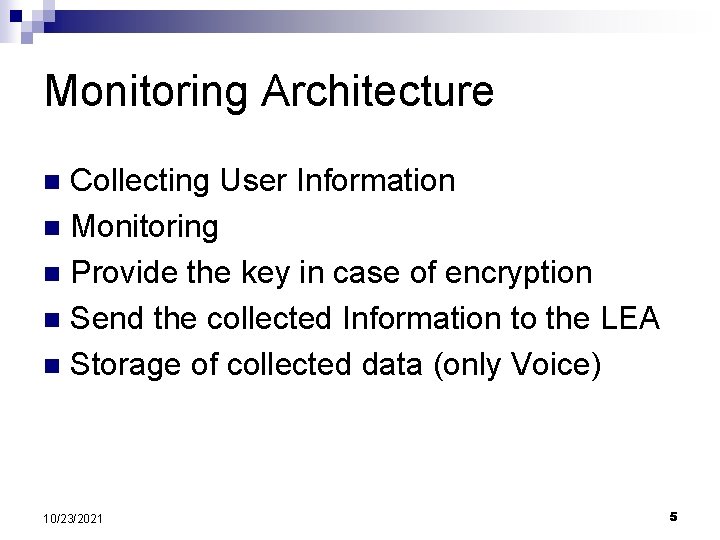
Monitoring Architecture Collecting User Information n Monitoring n Provide the key in case of encryption n Send the collected Information to the LEA n Storage of collected data (only Voice) n 10/23/2021 5

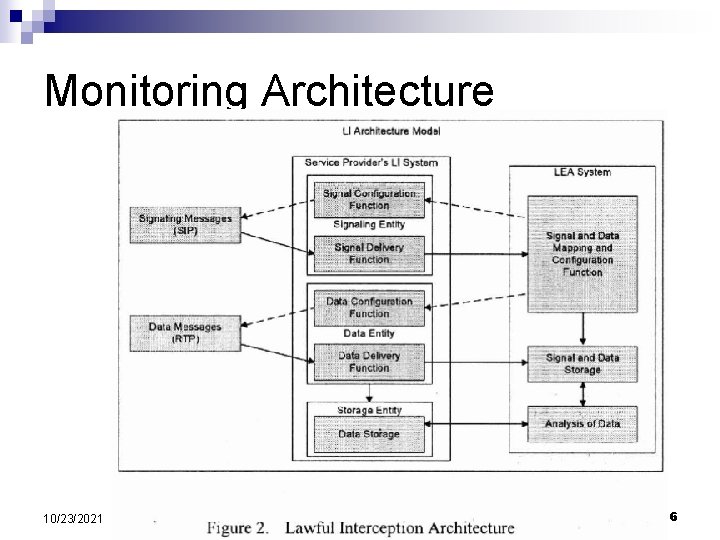
Monitoring Architecture 10/23/2021 6

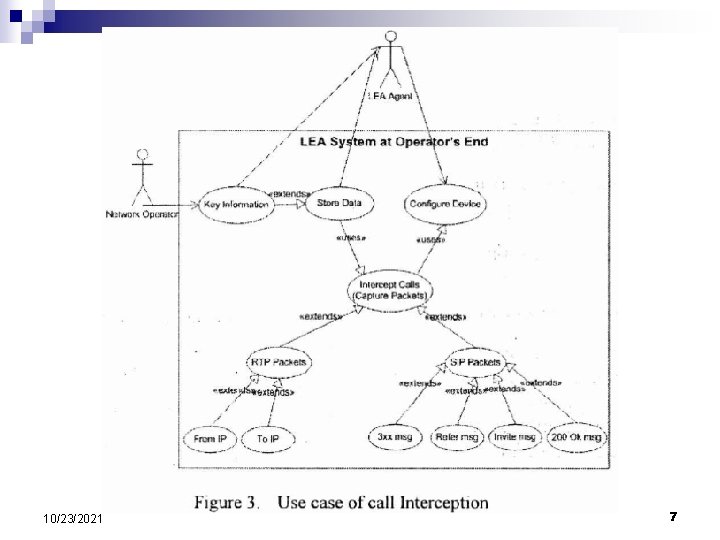
10/23/2021 7

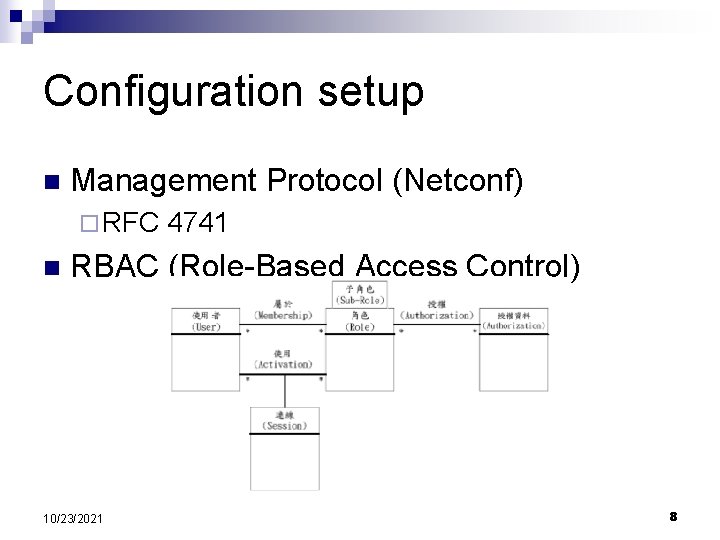
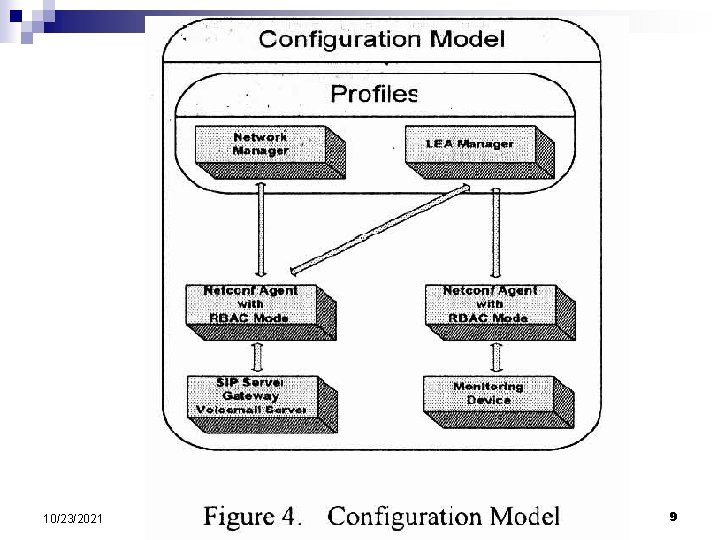
Configuration setup n Management Protocol (Netconf) ¨ RFC n 4741 RBAC (Role-Based Access Control) 10/23/2021 8

10/23/2021 9

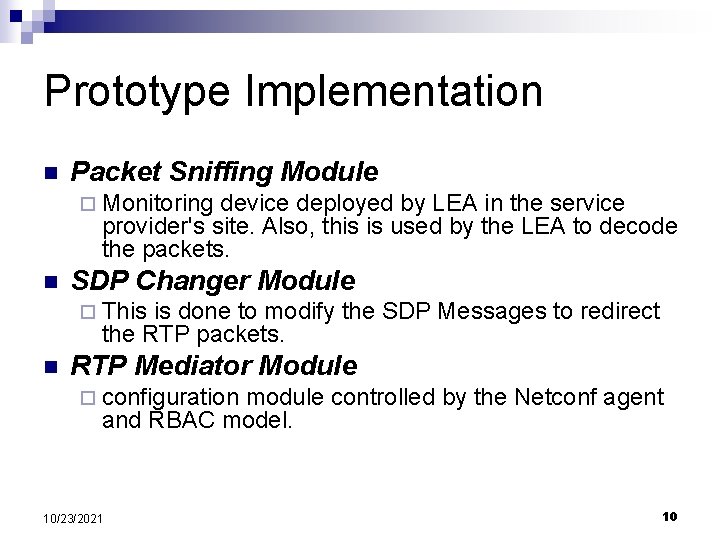
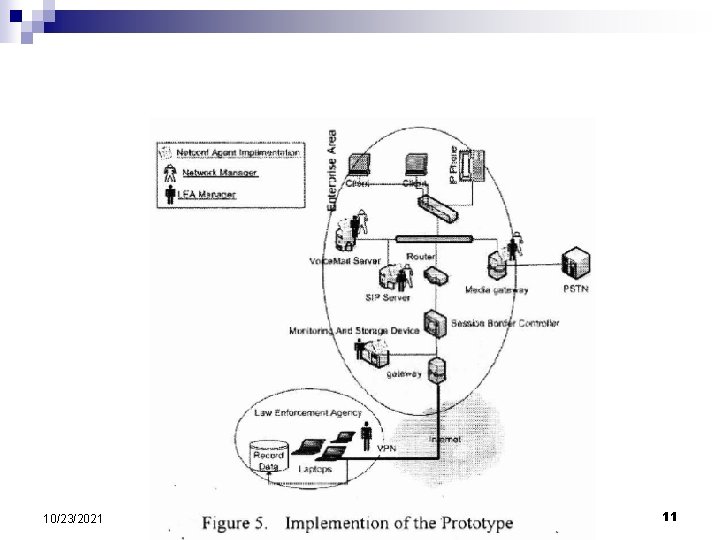
Prototype Implementation n Packet Sniffing Module ¨ Monitoring device deployed by LEA in the service provider's site. Also, this is used by the LEA to decode the packets. n SDP Changer Module ¨ This is done to modify the SDP Messages to redirect the RTP packets. n RTP Mediator Module ¨ configuration module controlled by the Netconf agent and RBAC model. 10/23/2021 10

10/23/2021 11

Conclusion n Possibility to monitor the target located anywhere on the internet The target cannot notice the interception, since we modify the SDP information from INVITE and ACK messages, before relying to the targets Has a better way of configuration of the devices with Netconf and RBAC for configuration data security 10/23/2021 12

Reference n Paper ¨ http: //ms 11. voip. edu. tw/~mac/research/paper/ Monitoring_Architecture_for_Lawful_Intercepti on_in_Vo. IP_Networks. pdf n RFC 4741 ¨ http: //www. ietf. org/rfc 4741. txt 10/23/2021 13