Module 9 Planning Network Access Overview Introducing Network










- Slides: 36

Module 9: Planning Network Access

Overview Introducing Network Access Selecting Network Access Connection Methods Selecting a Remote Access Policy Strategy Selecting a Network Access Authentication Method Planning a Network Access Strategy

Lesson: Introducing Network Access Requirements Network Access Connections Network Access Authentication Protocols Connection Security Best Practices Security Hosts

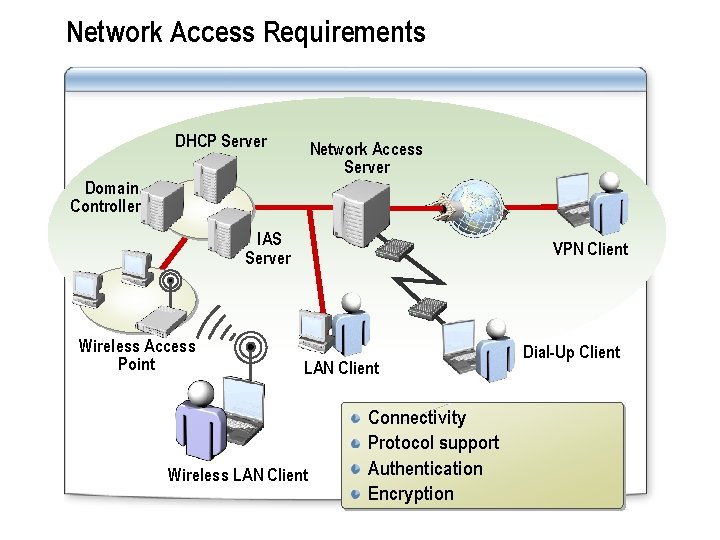
Network Access Requirements DHCP Server Network Access Server Domain Controller IAS Server Wireless Access Point VPN Client LAN Client Wireless LAN Client Connectivity Protocol support Authentication Encryption Dial-Up Client

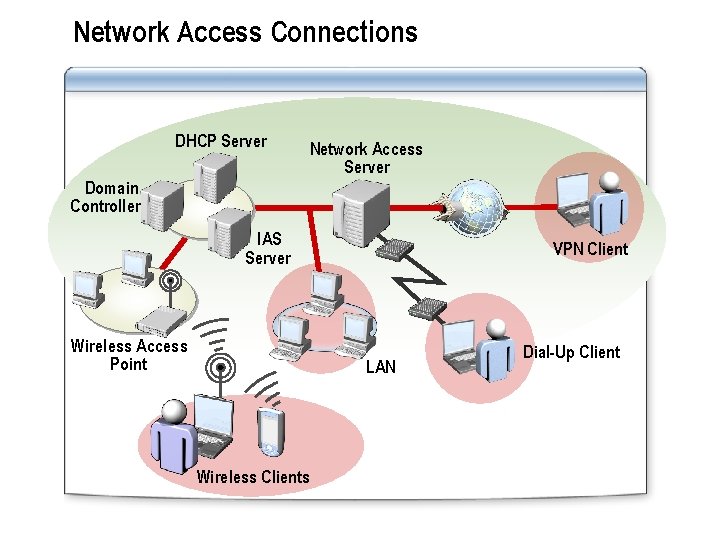
Network Access Connections DHCP Server Network Access Server Domain Controller IAS Server Wireless Access Point VPN Client LAN Wireless Clients Dial-Up Client

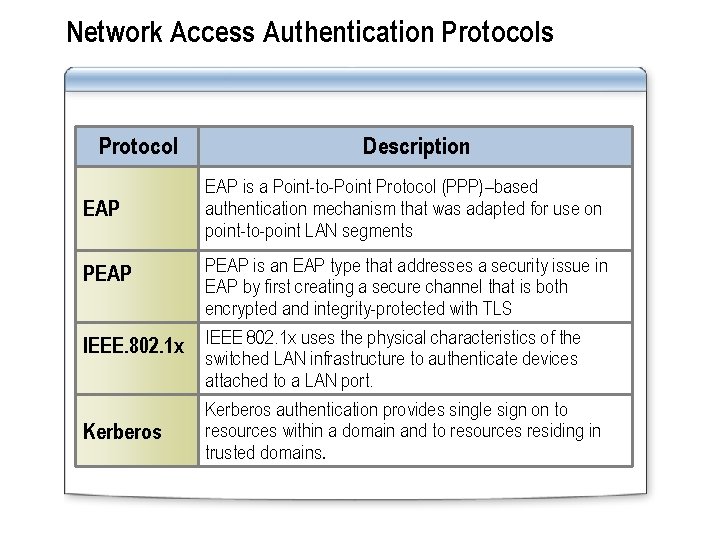
Network Access Authentication Protocols Protocol EAP PEAP IEEE. 802. 1 x Kerberos Description EAP is a Point-to-Point Protocol (PPP)–based authentication mechanism that was adapted for use on point-to-point LAN segments PEAP is an EAP type that addresses a security issue in EAP by first creating a secure channel that is both encrypted and integrity-protected with TLS IEEE 802. 1 x uses the physical characteristics of the switched LAN infrastructure to authenticate devices attached to a LAN port. Kerberos authentication provides single sign on to resources within a domain and to resources residing in trusted domains.

Connection Security Best Practices Configure Ethernet network adapters Smart card Protected EAP MD 5 -Challenge Support public key interactive logon Use IPSec Use a RADIUS infrastructure

Security Hosts Compare security hosts Security host that performs authentication checks during a connection request Security host that is called during the authentication process of the connection Use an interactive logon model

Lesson: Selecting Network Access Connection Methods LAN Solution Considerations VPN Solution Considerations Dial-Up Solution Considerations Multimedia: Planning for VPN and Dial-Up Clients Wireless Solution Considerations RADIUS Authentication Infrastructure Guidelines for Selecting Network Access Connection Methods

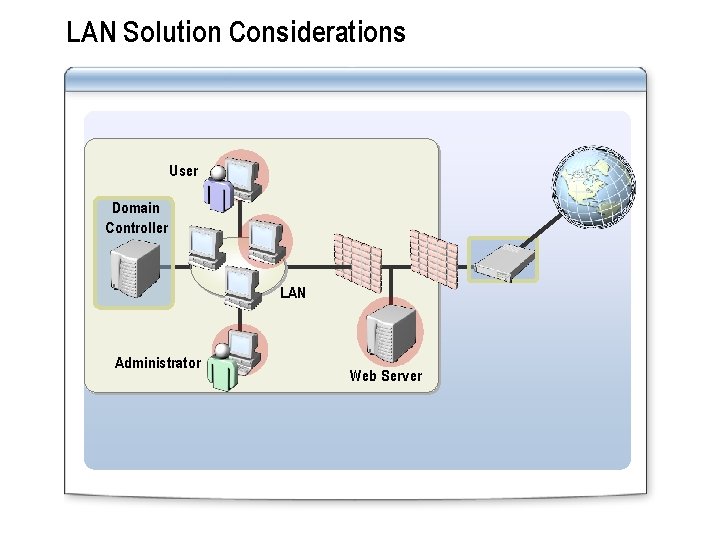
LAN Solution Considerations User Domain Controller LAN Administrator Web Server

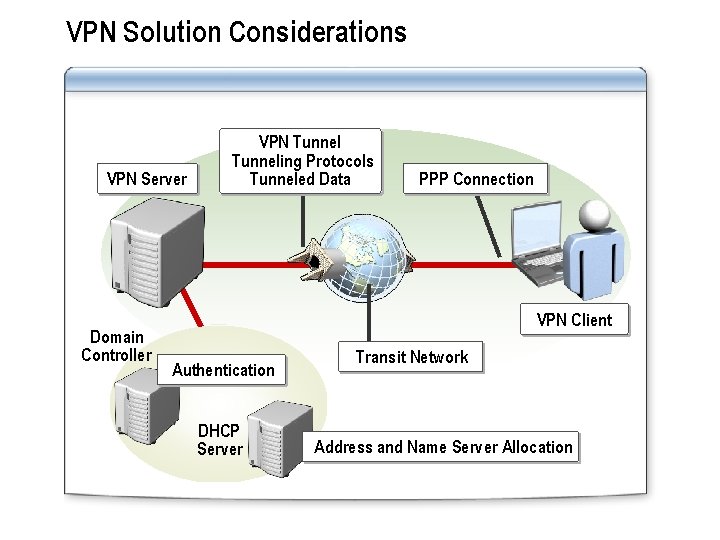
VPN Solution Considerations VPN Server Domain Controller VPN Tunneling Protocols Tunneled Data PPP Connection VPN Client Authentication DHCP Server Transit Network Address and Name Server Allocation

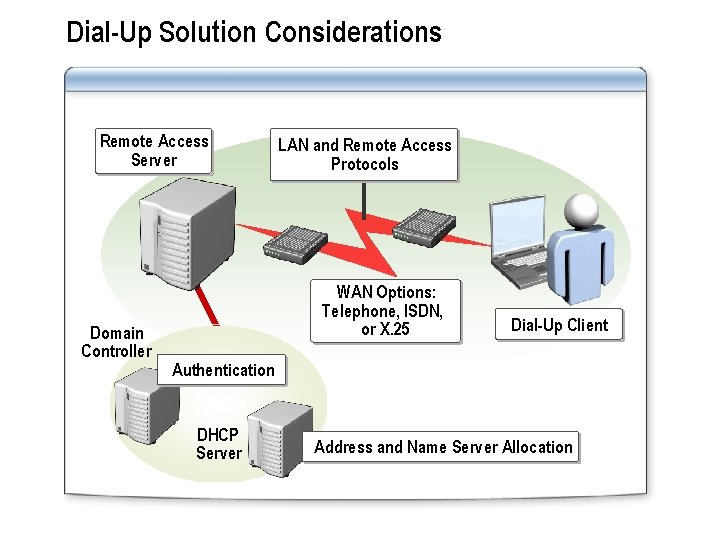
Dial-Up Solution Considerations Remote Access Server Domain Controller LAN and Remote Access Protocols WAN Options: Telephone, ISDN, or X. 25 Dial-Up Client Authentication DHCP Server Address and Name Server Allocation

Multimedia: Planning for VPN and Dial-Up Clients The objective of this presentation is to explain how to plan for VPN and dial-up clients You will learn how to: Plan a server running Routing and Remote Access to provide dial-up or VPN services Select a Routing and Remote Access configuration for dial-up or VPN services Choose between a dial-up and a VPN solution

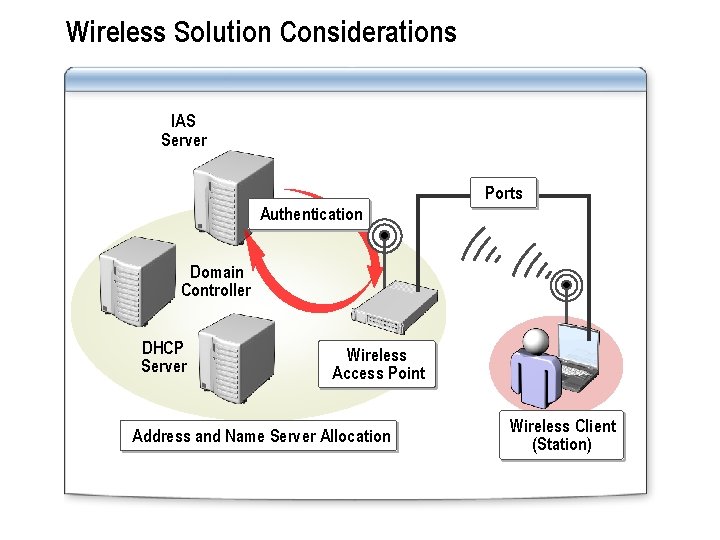
Wireless Solution Considerations IAS Server Ports Authentication Domain Controller DHCP Server Wireless Access Point Address and Name Server Allocation Wireless Client (Station)

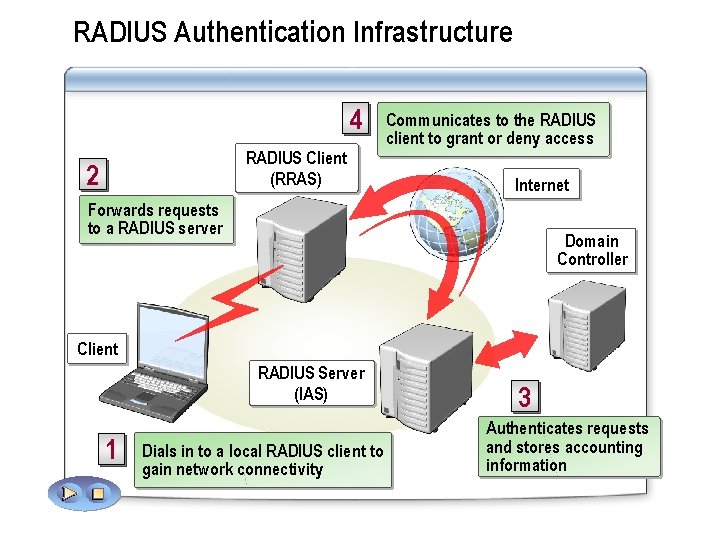
RADIUS Authentication Infrastructure 4 RADIUS Client (RRAS) 2 Communicates to the RADIUS client to grant or deny access Internet Forwards requests to a RADIUS server Domain Controller Client RADIUS Server (IAS) 1 Dials in to a local RADIUS client to gain network connectivity 3 Authenticates requests and stores accounting information

Guidelines for Selecting Network Access Connection Methods Determine client requirements Determine infrastructure requirements Select network access connection methods for your enterprise

Practice: Selecting Network Access Connection Methods In this practice, you will select network access connection methods based on the provided scenario

Lesson: Selecting a Remote Access Policy Strategy Remote Access Policies Remote Access Policy Conditions User Account Dial-in Properties User Profile Options Guidelines for Selecting a Remote Access Policy Strategy

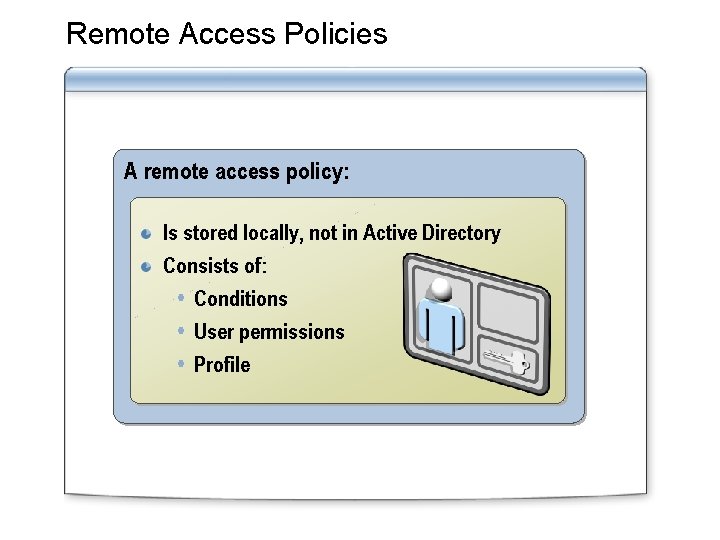
Remote Access Policies A remote access policy: Is stored locally, not in Active Directory Consists of: Conditions User permissions Profile

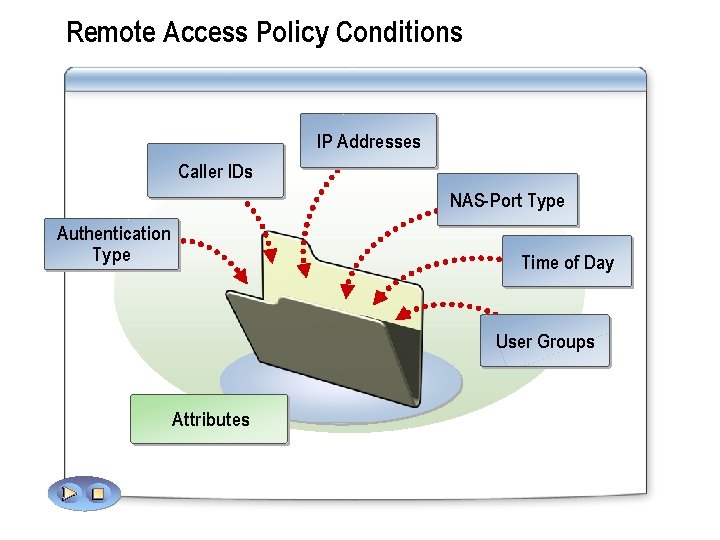
Remote Access Policy Conditions IP Addresses Caller IDs NAS-Port Type Authentication Type Time of Day User Groups Attributes

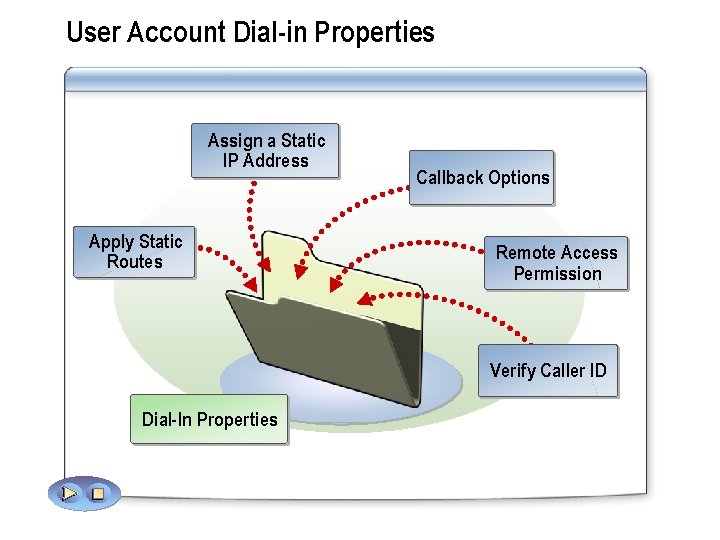
User Account Dial-in Properties Assign a Static IP Address Apply Static Routes Callback Options Remote Access Permission Verify Caller ID Dial-In Properties

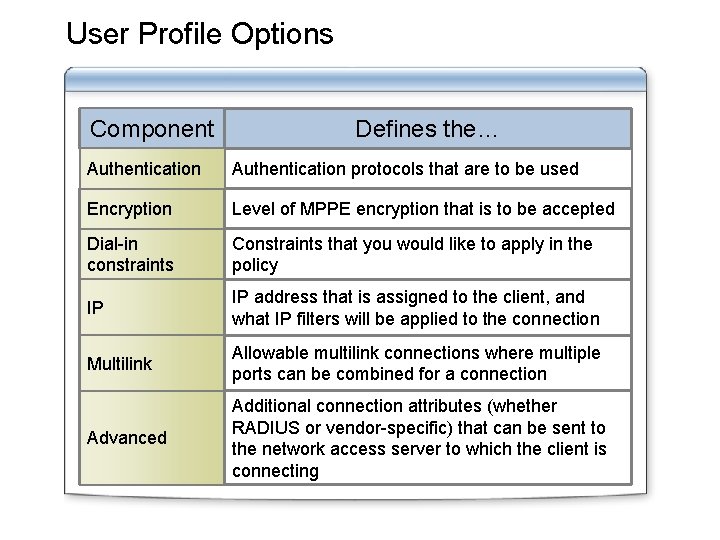
User Profile Options Component Defines the… Authentication protocols that are to be used Encryption Level of MPPE encryption that is to be accepted Dial-in constraints Constraints that you would like to apply in the policy IP IP address that is assigned to the client, and what IP filters will be applied to the connection Multilink Allowable multilink connections where multiple ports can be combined for a connection Advanced Additional connection attributes (whether RADIUS or vendor-specific) that can be sent to the network access server to which the client is connecting

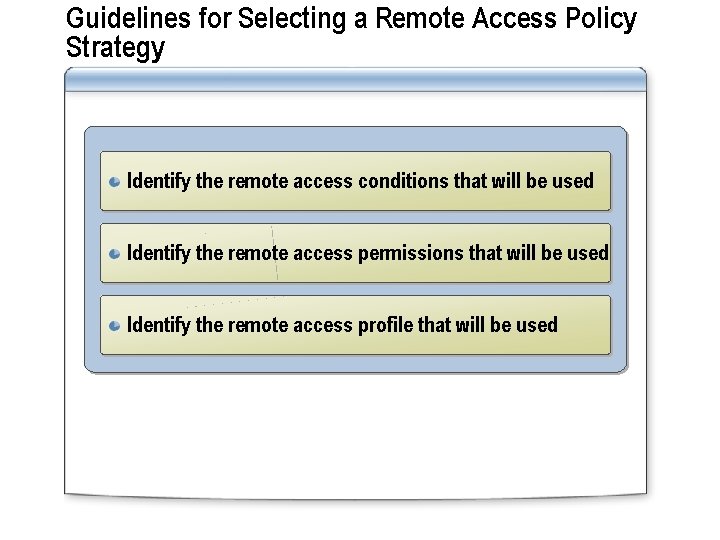
Guidelines for Selecting a Remote Access Policy Strategy Identify the remote access conditions that will be used Identify the remote access permissions that will be used Identify the remote access profile that will be used

Practice: Determining a Remote Access Policy Strategy In this practice, you will plan a remote access strategy by using the provided scenario to define the required remote access options

Lesson: Selecting a Network Access Authentication Method Server Authentication Models and Methods IAS as an Authentication Server Guidelines for Selecting IAS as an Authentication Provider

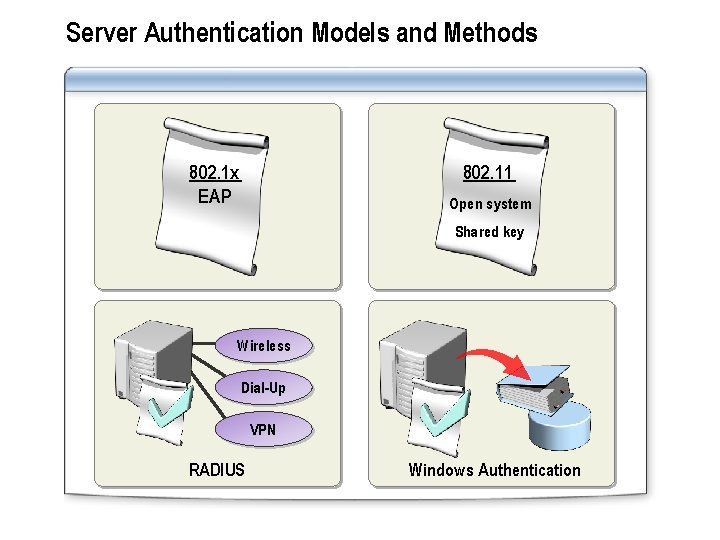
Server Authentication Models and Methods 802. 11 802. 1 x EAP Open system Shared key Wireless Dial-Up VPN RADIUS Windows Authentication

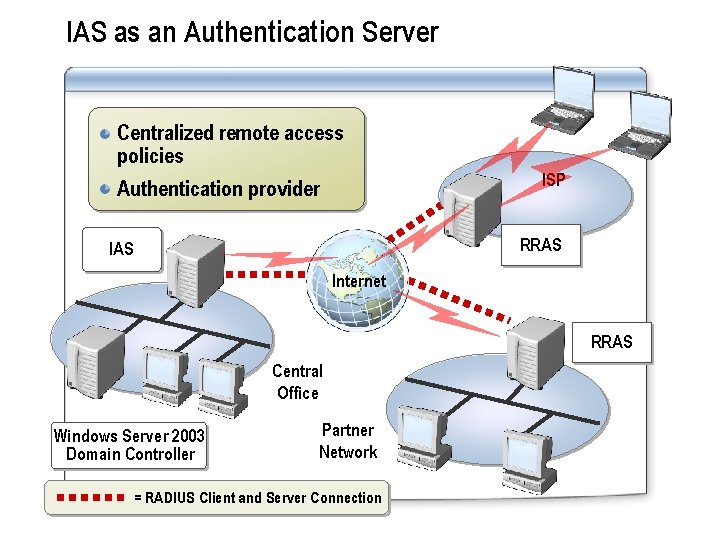
IAS as an Authentication Server Centralized remote access policies Authentication provider ISP RRAS Internet RRAS Central Office Windows Server 2003 Domain Controller Partner Network = RADIUS Client and Server Connection

Guidelines for Selecting IAS as an Authentication Provider Determine if you have multiple access servers Determine if you have third-party Internet access providers Determine if you have a heterogeneous environment to support Determine your authentication needs

Practice: Selecting Centralized Authentication for Network Access Using IAS In this practice, you will select a centralized authentication for network access by using IAS

Lesson: Planning a Network Access Strategy Network Access Connection Strategy Security-Based Authentication Methods Remote Access Policy Strategies Guidelines for Planning a Network Access Strategy

Network Access Connection Strategy Selecting a network access connection strategy includes: Evaluating enterprise requirements Creating a comprehensive network access plan

Security-Based Authentication Methods Security-based authentication requirements Secure network access Strong authentication and encryption

Remote Access Policy Strategies To determine a strategy: Determine connection request conditions that need policies Define policies to reflect requirements

Guidelines for Planning a Network Access Strategy Identify who will be allowed access to network resources Identify how the approved users will access the network Identify who will access the network and how they will access it Integrate your authentication strategy across all of the remote access methods

Lab A: Planning Network Access Exercise 1: Planning for the LAN and Wireless Environment Exercise 2: Planning for the WAN Environment

Course Evaluation