Module 5 3 Internet Control Message Protocol Why
- Slides: 21

Module 5. 3: Internet Control Message Protocol • • • Why need ICMP? IP and ICMP Message Format ICMP Error Reporting messages ICMP Query messages ICMPv 6 K. Salah 1

ICMP • • IP provides an unreliable, connectionless datagram delivery service. • Question is: What happens if a gateway cannot route or deliver a datagram or if the gateway detects an unusual condition like network congestion? • What mechanisms are there in TCP/IP suite for a gateway to inform the sender about an error in the IP Datagram deliver? • How do gateways use the mechanism to report delivery problems and how do hosts use it to test whether or not destinations are reachable? • In a connectionless system each gateway operates autonomously, routing or delivering datagrams without any coordination from the sender. • Failures to communication lines and processors, or the expiry of time-to-live counter, or the congestion of intermediate gateways could disrupt the whole operation. • The IP itself contains nothing to help sender test connectivity or learn about such failures. So we use ICMP. Datagram travels from gateway to gateway until it reaches the destination host’s network, where it would be sent directly. K. Salah 2

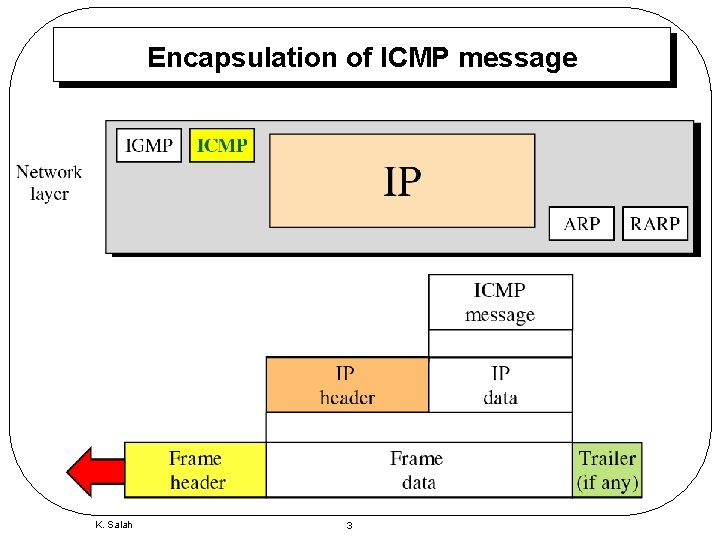
Encapsulation of ICMP message K. Salah 3

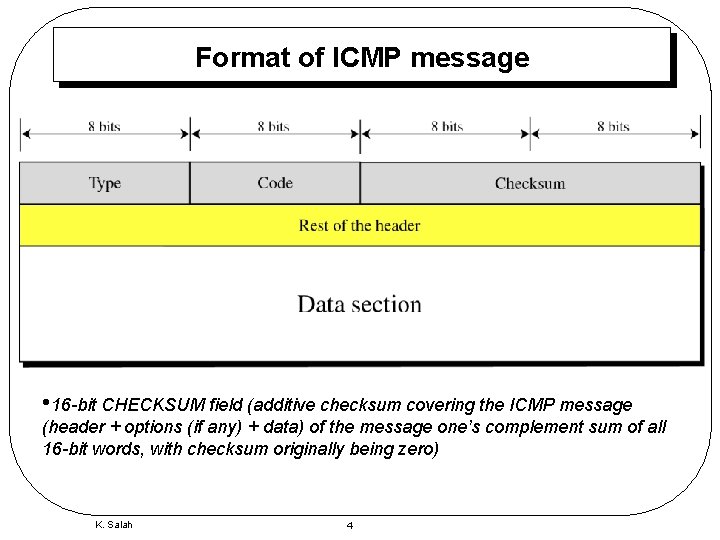
Format of ICMP message • 16 -bit CHECKSUM field (additive checksum covering the ICMP message (header + options (if any) + data) of the message one’s complement sum of all 16 -bit words, with checksum originally being zero) K. Salah 4

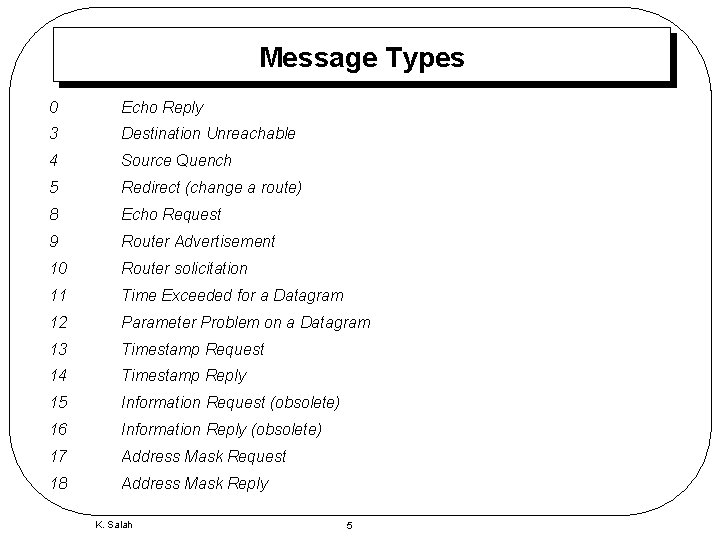
Message Types 0 Echo Reply 3 Destination Unreachable 4 Source Quench 5 Redirect (change a route) 8 Echo Request 9 Router Advertisement 10 Router solicitation 11 Time Exceeded for a Datagram 12 Parameter Problem on a Datagram 13 Timestamp Request 14 Timestamp Reply 15 Information Request (obsolete) 16 Information Reply (obsolete) 17 Address Mask Request 18 Address Mask Reply K. Salah 5

K. Salah 6

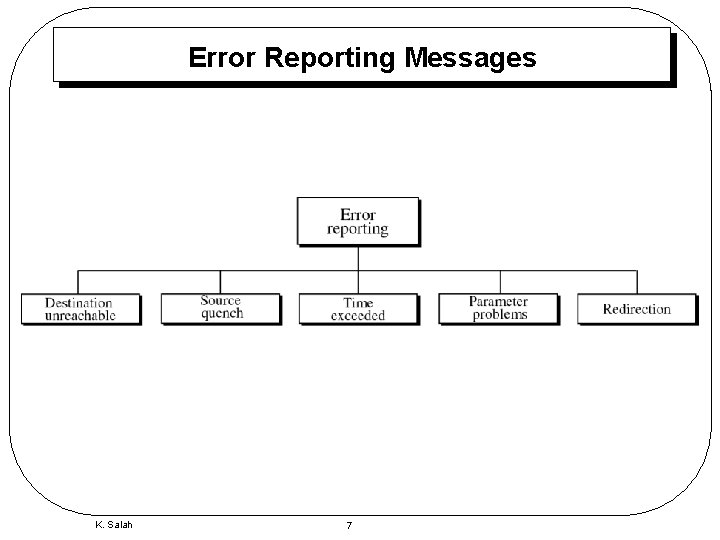
Error Reporting Messages K. Salah 7

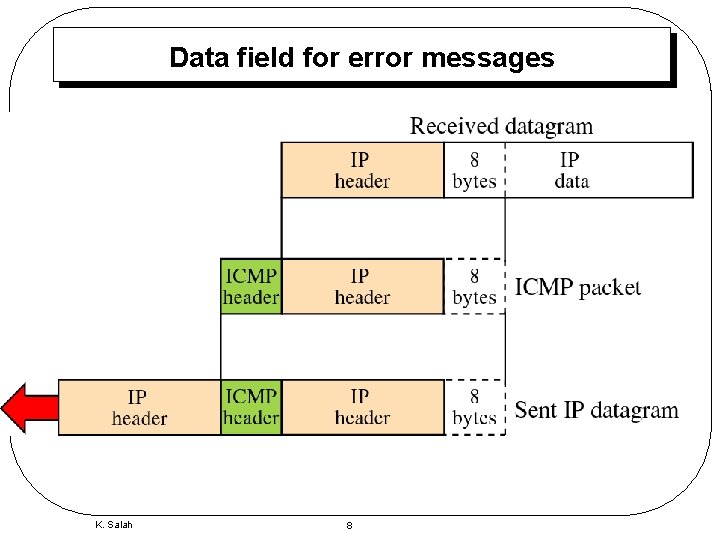
Data field for error messages K. Salah 8

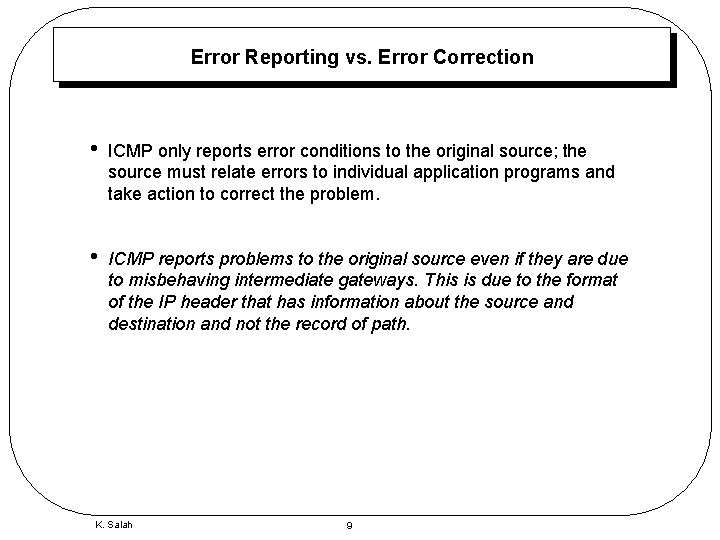
Error Reporting vs. Error Correction • ICMP only reports error conditions to the original source; the source must relate errors to individual application programs and take action to correct the problem. • ICMP reports problems to the original source even if they are due to misbehaving intermediate gateways. This is due to the format of the IP header that has information about the source and destination and not the record of path. K. Salah 9

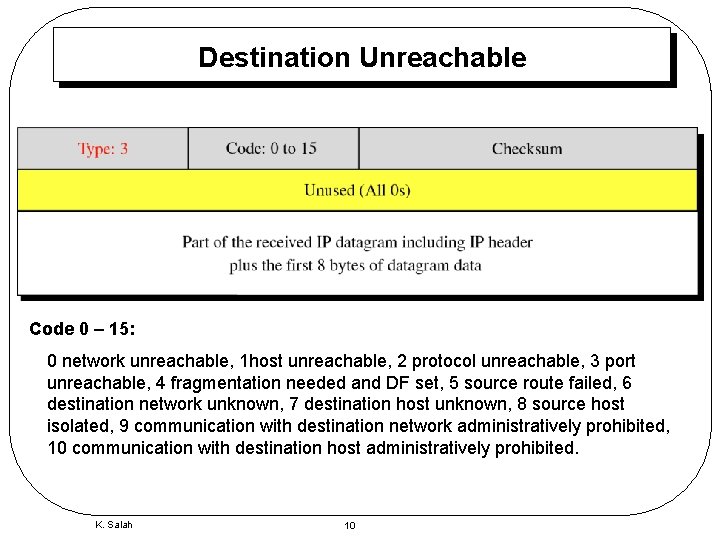
Destination Unreachable Code 0 – 15: 0 network unreachable, 1 host unreachable, 2 protocol unreachable, 3 port unreachable, 4 fragmentation needed and DF set, 5 source route failed, 6 destination network unknown, 7 destination host unknown, 8 source host isolated, 9 communication with destination network administratively prohibited, 10 communication with destination host administratively prohibited. K. Salah 10

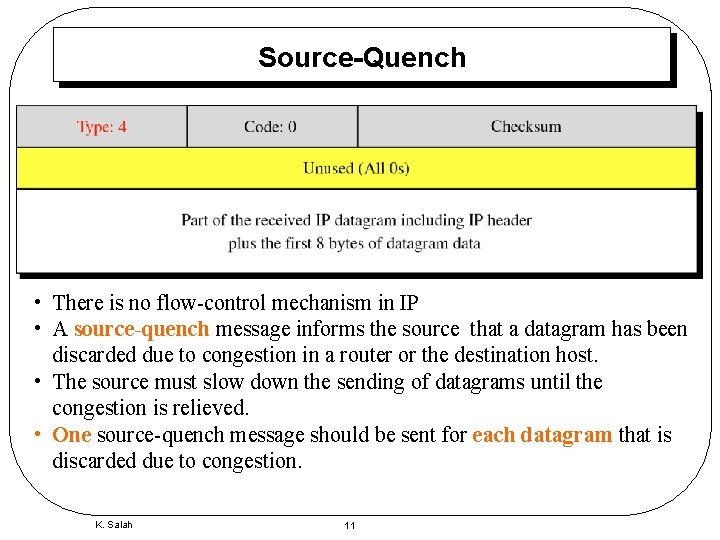
Source-Quench • There is no flow-control mechanism in IP • A source-quench message informs the source that a datagram has been discarded due to congestion in a router or the destination host. • The source must slow down the sending of datagrams until the congestion is relieved. • One source-quench message should be sent for each datagram that is discarded due to congestion. K. Salah 11

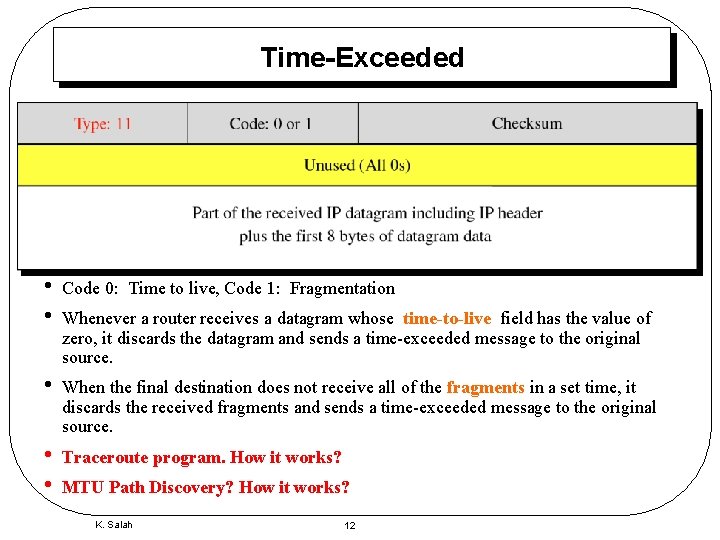
Time-Exceeded • • Code 0: Time to live, Code 1: Fragmentation • When the final destination does not receive all of the fragments in a set time, it discards the received fragments and sends a time-exceeded message to the original source. • • Traceroute program. How it works? Whenever a router receives a datagram whose time-to-live field has the value of zero, it discards the datagram and sends a time-exceeded message to the original source. MTU Path Discovery? How it works? K. Salah 12

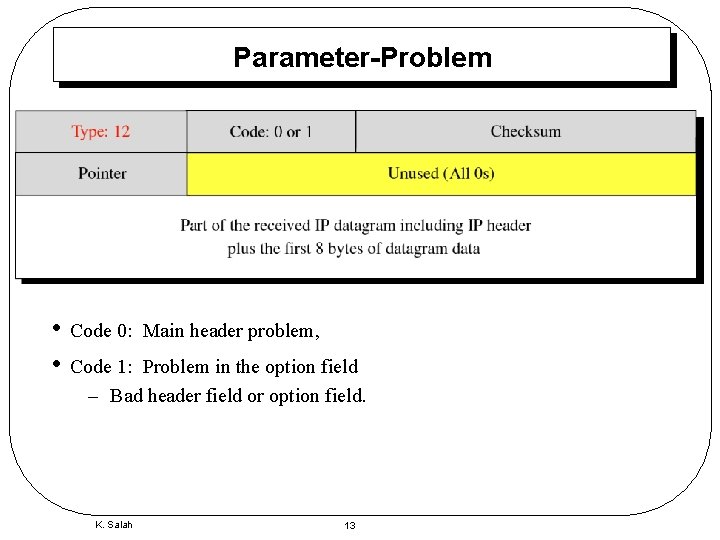
Parameter-Problem • Code 0: • Code 1: Main header problem, Problem in the option field – Bad header field or option field. K. Salah 13

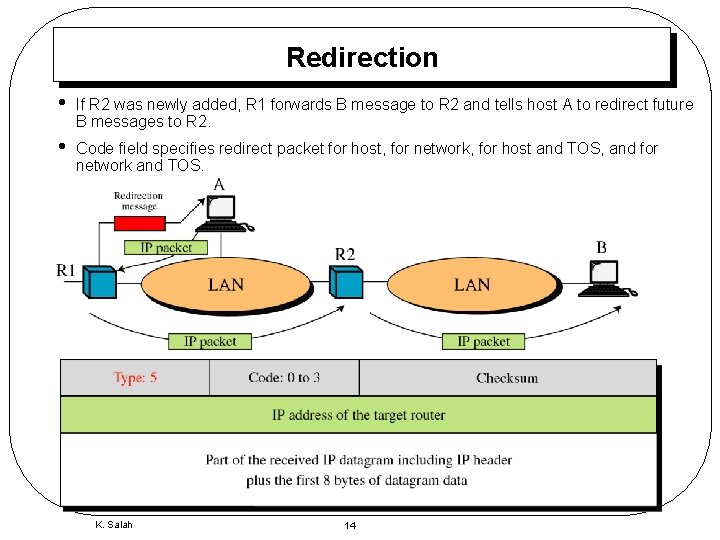
Redirection • If R 2 was newly added, R 1 forwards B message to R 2 and tells host A to redirect future B messages to R 2. • Code field specifies redirect packet for host, for network, for host and TOS, and for network and TOS. K. Salah 14

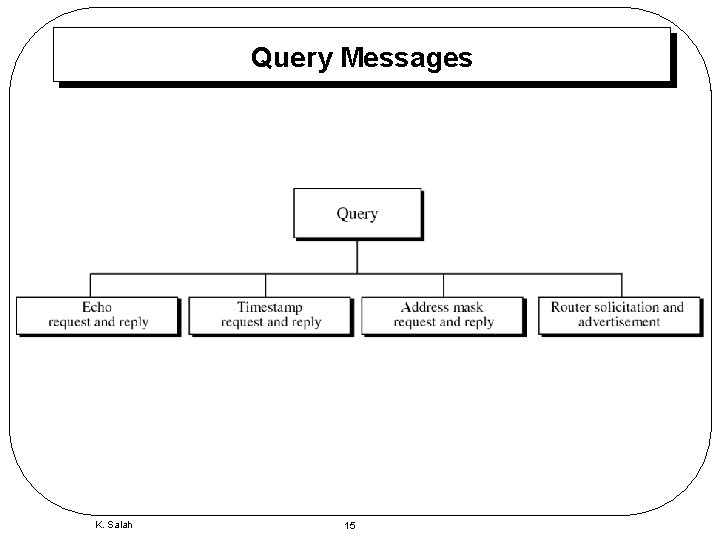
Query Messages K. Salah 15

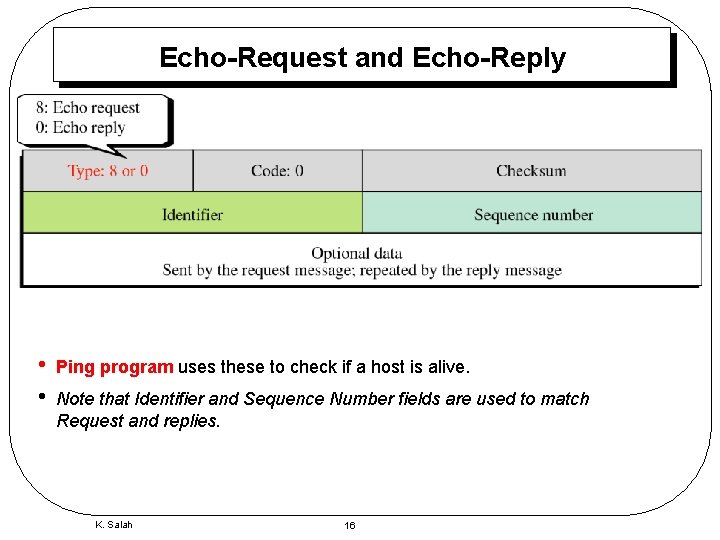
Echo-Request and Echo-Reply • • Ping program uses these to check if a host is alive. Note that Identifier and Sequence Number fields are used to match Request and replies. K. Salah 16

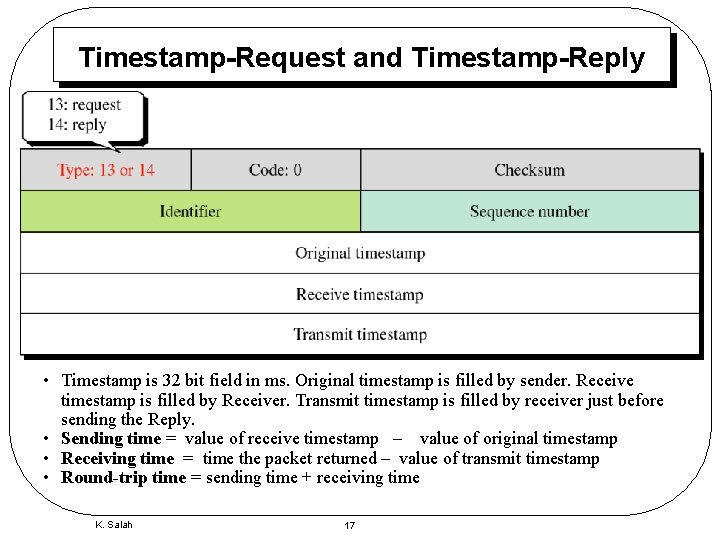
Timestamp-Request and Timestamp-Reply • Timestamp is 32 bit field in ms. Original timestamp is filled by sender. Receive timestamp is filled by Receiver. Transmit timestamp is filled by receiver just before sending the Reply. • Sending time = value of receive timestamp – value of original timestamp • Receiving time = time the packet returned – value of transmit timestamp • Round-trip time = sending time + receiving time K. Salah 17

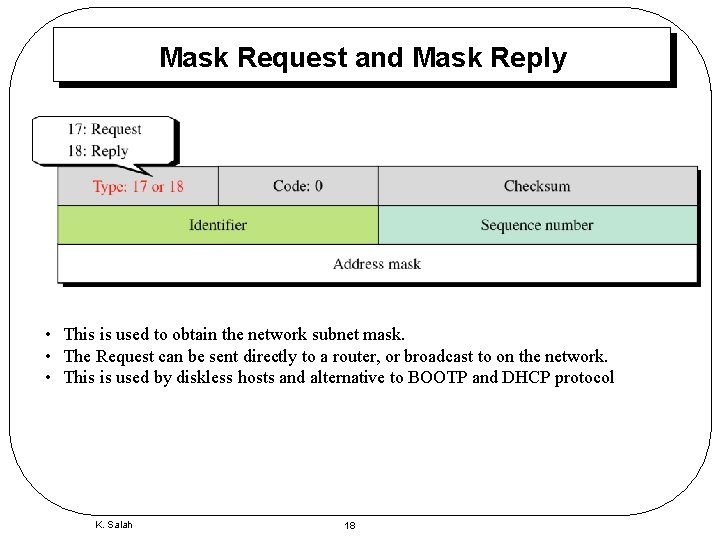
Mask Request and Mask Reply • This is used to obtain the network subnet mask. • The Request can be sent directly to a router, or broadcast to on the network. • This is used by diskless hosts and alternative to BOOTP and DHCP protocol K. Salah 18

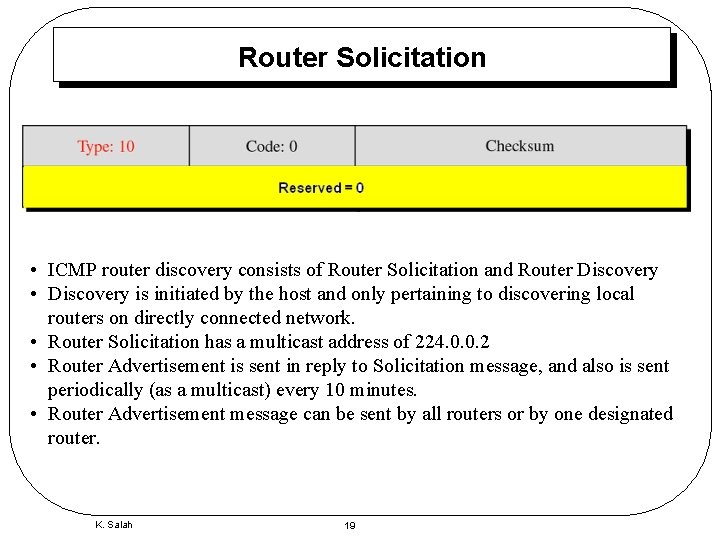
Router Solicitation • ICMP router discovery consists of Router Solicitation and Router Discovery • Discovery is initiated by the host and only pertaining to discovering local routers on directly connected network. • Router Solicitation has a multicast address of 224. 0. 0. 2 • Router Advertisement is sent in reply to Solicitation message, and also is sent periodically (as a multicast) every 10 minutes. • Router Advertisement message can be sent by all routers or by one designated router. K. Salah 19

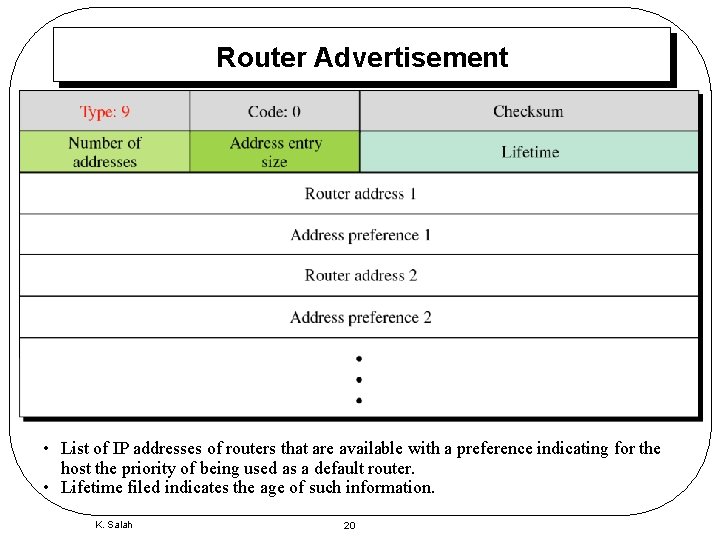
Router Advertisement • List of IP addresses of routers that are available with a preference indicating for the host the priority of being used as a default router. • Lifetime filed indicates the age of such information. K. Salah 20

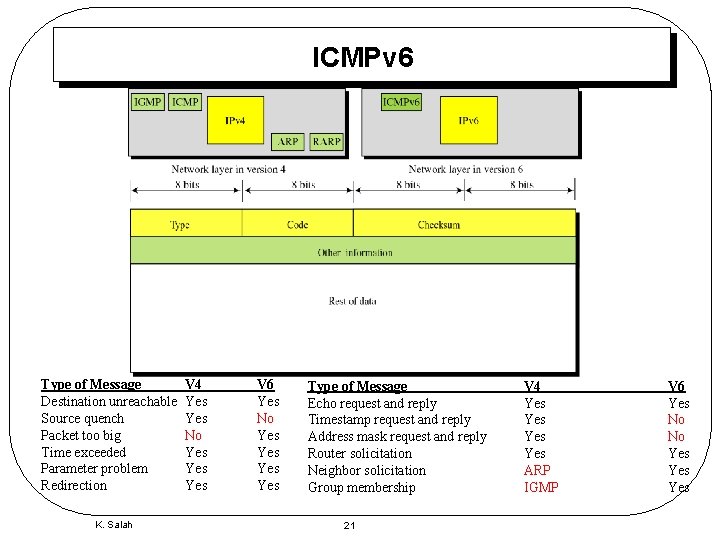
ICMPv 6 Type of Message Destination unreachable Source quench Packet too big Time exceeded Parameter problem Redirection K. Salah V 4 Yes No Yes Yes V 6 Yes No Yes Yes Type of Message Echo request and reply Timestamp request and reply Address mask request and reply Router solicitation Neighbor solicitation Group membership 21 V 4 Yes Yes ARP IGMP V 6 Yes No No Yes Yes