Module 4 Components of the NIST Cybersecurity Framework

Module 4 Components of the NIST Cybersecurity Framework ®
Module Summary • Review of the NIST CSF major components • Tiers and Tier selection • Current and Target Profiles and the Framework Core • Deep dive in Informative References • Supply Chain Risk Management in the Enterprise ®
Framework Component Review • Three primary components • Implementation or Improvement Methodology POCCCDI ®
Framework Component Review (continued) • Framework Core • Five functions, 23 categories, 108 subcategories • Informative references • “provides a set of desired cybersecurity activities and outcomes using common language that is easy to understand” ®
Framework Component Review (continued) • Framework Implementation Tiers • Four tiers • A measurement of risk management decisions • “ (provide) context on how an organization views cybersecurity risk management…often used as a communication tool to discuss risk appetite, mission priority, and budget” ®
Framework Component Review (continued) • Framework Profiles • Two profiles • Measurement and alignment of previous and current cybersecurity activities to the Core • “primarily used to identify and prioritize opportunities for improving cybersecurity at an organization” ®
Framework Component Review (continued) • Implementation or Improvement Methodology – POCCCDI • Specific method for creating or implementing a cybersecurity program using the Framework • Seven step process • • Prioritize and Scope Orient Create a Current Profile Conduct a Risk Assessment Create a Target Profile Determine, Analyze, and Prioritize Gaps Implement an Action Plan ®

Tiers and Tier Selection • Tiers are a qualitative measure of organizational cybersecurity risk management practices • Tiers provide context on how an organization views cybersecurity risk management • Tiers guide organizations to consider the appropriate level of rigor for their cybersecurity program • Tiers are often used as a communication tool to discuss risk appetite, determine mission priority, and effectively allocate resources to reach cybersecurity objectives ®

The Four Tiers (continued) • Tiers are generally determined at the Subcategory level • Each Subcategory is at Tier 1, 2, 3, or 4 due to past cybersecurity activities • Based on the Target Profile an organization may implement or modify controls to achieve a higher Tier • Tier 4 is often not the appropriate goal ®

Components of the Tiers • Determination of Tier level depends on implementation of three components • Each Tier level has all three components • The three components are • Risk Management Process • Integrated Risk Management Program • External Participation ®
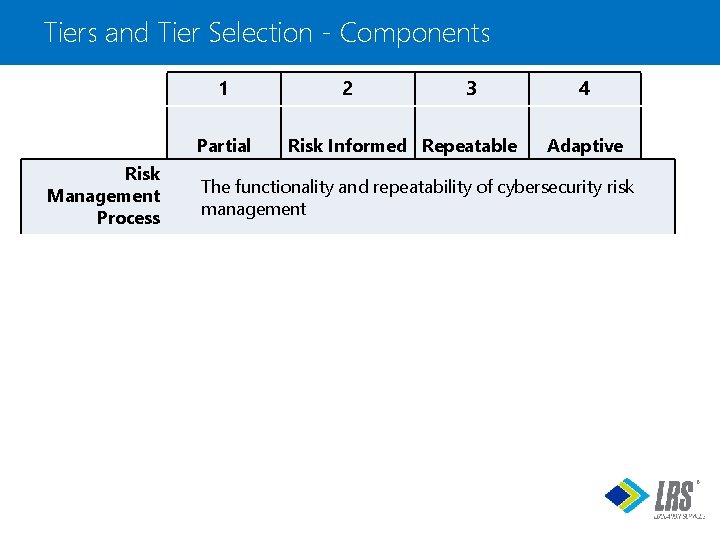
Tiers and Tier Selection - Components 1 Partial Risk Management Process Integrated Risk Management Program External Participation 2 3 Risk Informed Repeatable 4 Adaptive The functionality and repeatability of cybersecurity risk management The extent to which cybersecurity is considered in broader risk management decisions The degree to which the organization: • monitors and manages supply chain risk • benefits by sharing or receiving information from outside parties ®

Tiers and Tier Selection • Tier selection depends upon organizational requirements and constraints • Requirements may include: • • Organizational risk tolerance Organizational policies Regulatory mandates Compliance obligations Contractual commitments Organizational agreements Stakeholder expectations ®

Tiers and Tier Selection • Tier selection depends upon organizational requirements and constraints • Constraints may include: • • • Financial resources Technical personnel Executive support and or participation Risk assessment results Risk management expertise ®

Tier 1 Partial: Example • Subcategory: ID. RA-3: Threats to organizational assets are identified and documented • Risk Management Process: • No formal method for identifying threats • Each new threat treated as a stand-alone event • Integrated Risk Management Program: • Outside of IT, the risk posed by threats is unknown • Details of threats not disseminated internally • External Participation: • No knowledge of threats from vendors or business partners • No receiving of threat information from outside sources ®

Tier 2 Risk Informed: Example • Risk Management Process: • Security has a threat management process, but other departments don’t always follow it • Security has created the process based on what they recognize as what is critical to the organization • Integrated Risk Management Program: • CIO knows threats are a major problem, but hasn’t been able to convince executive leadership to adopt formal policies • Assessing risks from threats is only done when demanded by auditors • External Participation: • Concern for partner threats exists, but no monitoring or accountability • Security staff receive threat information from colleagues at other organizations, often informally ®

Tier 3 Repeatable: Example • Risk Management Process: • Threat management process approved by executive leadership and as used organization-wide policy • Policy updated regularly as threats change and rapidly for major emergent threats • Integrated Risk Management Program: • CIO updates executive leadership monthly on risk management activities • Threat management training for all staff commensurate with roles • Security Information and Event Management (SIEM) solution in place • External Participation: • Threat information shared with other industry organizations • Partnership and vendor agreements include threat monitoring/management clauses with non-compliance consequences ®

Tier 4 Adaptive: Example • Risk Management Process: • After-Action Reports (AARs) follow all significant security events and include lessons learned to integrate into policy changes • SIEM and threat hunters search for unrealized threats and adjust controls • Continuous improvement process in the Security department • Integrated Risk Management Program: • • • Executive leadership considers threat risk same as financial risk Major initiatives consider threat effects Threat management budget is an inviolable fixed cost Consistent threat management training for all staff Threat management promoted by executive leadership ®

Tier 4 Adaptive: Example (cont. ) • External Participation: • Executive leadership recognizes the critical role the organization plays • Aids industry organizations in understanding threat management • Security staff creates and shares content to support the threat management efforts of vendors, business partners, and the industry as a whole • Automated systems monitor vendor and business partner-based threats to insure rapid detection and elimination threats. • All agreements with vendors and business partners include monitoring and management clauses with consequences for non-compliance ®

Current and Target Profiles and the Framework Core • Framework Profiles are the alignment of the Functions, Categories, and Subcategories with the business requirements, risk tolerance, and resources of the organization • Profiles enable organizations to establish a roadmap for reducing cybersecurity risk • Profiles can be created for various stages in the creation or improvement of a cybersecurity program ®

The Two Profiles • Profiles support business/mission requirements and aid in communicating risk within and between organizations. • Profiles describe the as is or to be state of a component, system, service, process, team, individual, Subcategory, Category, Function, or any other aspect of risk or cybersecurity management • The two profiles are: • Current Profile • Target Profile ®

The Two Profiles (continued) – Current Profile • The Current Profile • Indicates cybersecurity outcomes currently being achieved • Is the result of past or currently unaltered cybersecurity activities • May or may not meet risk management and or cybersecurity goals and requirements • Must be maintained or modified to ensure risk does not increase due to changing threat and technology environments ®

The Two Profiles (continued) – Target Profile • The Target Profile • Indicates the outcomes needed to achieve the desired cybersecurity risk management goals • Is the result of planned and controlled intentional changes to cybersecurity activities • Is selected based on business needs to reduce risk by understanding aspects of the organizational mission, objectives, goals, obligations, controls, technologies, vulnerabilities, risks, threat environment, and Current Profile ®

Interrelationships between the Framework Components • Cybersecurity and risk management activities occur and are documented in the Core • Risk management rigor and results are qualitatively measured in the Tiers • Alignment of the Core with business requirements, risk tolerance, and resources occurs in the Profiles ®
Interrelationships between the Framework Components (continued) • The Core contains 5 Functions, 23 Categories, and 108 Subcategories • Each Category and Subcategory has a Current and Target Profile • The Current Profile is the Tier measured by existing risk management results • The Target Profile is the desired Tier based on planned and controlled intentional changes to cybersecurity activities ®

Current Profile: Example • Subcategory: ID. RA-3: Threats to organizational assets are identified and documented • Based on the Seven Step Process for Creating or Improving a Cybersecurity Program: • Step 3: Create a Current Profile tells the organization the current state (or Current Profile) • Current Profile for our example is Tier 2: • Existing threat management process based on critical organizational objectives, but only followed by Security Department • Only executive buy-in is from CIO and threat risk assessments only when forced by auditors • Concern exists for supply chain threats, but no action and threat information only received informally ®

Target Profile: Example • Subcategory: ID. RA-3: Threats to organizational assets are identified and documented • Based on the Seven Step Process for Creating or Improving a Cybersecurity Program: • Step 5: Create a Target Profile tells the organization the desired state • Target Profile Tier 3: • Get threat management policy for all departments approved by full executive leadership • Keep policy updated for new or changed threats • Have CIO update executive leadership monthly threat management activities • Train all staff on threat management • Install and tune a SIEM ®

Deep dive in Informative References • Part of the Framework Core • All or part of selected detailed technical and business standards, guidance, and publications • Not a checklist • Starting point for implementing subcategory outcomes • Organizations can use none, some, or all the Informative References to achieve desired subcategory outcomes ®

CIS Controls • Published by the Center for Internet Security with input from over 100 contributing entities • 20 controls with 171 sub controls detailing specific actionable recommendations • Designed to block or mitigate attacks • Expectation is to use primarily automated methods to implement, enforce, and monitor the controls ®
CIS Controls • • • Blocking initial attack if possible Reduce attack surface Device hardening Detect compromised systems Prevent or disrupt command control Adaptive continuous defense and response ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Controls The CIS Controls are based on five tenets of an effective cyber defense: • • • Offense informs defense Prioritization Measurements and metrics Continuous diagnostics and mitigation Automation ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Controls: Implementation Groups • Previous versions of the CIS Controls used the order of the controls to focus cybersecurity activities • Implementation of the first six, and all subcontrols was considered basic cyber hygiene • Real-world experience shows this is not practical or applicable to organizations with more constrained resources • To better apply the CIS Controls, Version 7. 1 includes Implementation Groups (IGs) ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Controls: Implementation Groups • IGs are self-assessed categories • Based on cybersecurity attributes • An IG identifies a subset of CIS Controls for an organization in the IG • Each IG includes controls from lower IGs • In some cases an organization may need to implement specific controls from a higher IG • For NIST CSF alignment, controls to implement should lead to the Target Profile ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Controls: Implementation Groups • Prioritize Controls and Sub-Controls starting with IG 1 • All organizations should implement IG 1 • Depending on self-assessment move to IG 2 and or IG 3 • Characteristics for IG determination: 1. Data sensitivity and criticality of services offered by the organization 2. Expected level of technical expertise exhibited by staff or on contract 3. Resources available and dedicated toward cybersecurity activities © 2020 Center for Internet Security, Inc. Used with permission ®

CIS Controls: Implementation Group 1 IG 1 characteristics: • SMB • Limited IT and or cybersecurity expertise • Principal concern to maintain operations due to limited downtime tolerance • Low amount of sensitive data, primarily employee PII and organizational financials • Often use off the shelf cybersecurity solutions • May need controls from higher IGs based on types of business activity or position in critical infrastructure © 2020 Center for Internet Security, Inc. Used with permission ®

CIS Controls: Implementation Group 2 IG 2 characteristics: • Full time IT/cybersecurity staff • Multiple departments with different risk profiles • May have compliance obligations • Sensitive organizational and client data • Capability to withstand short service interruptions • A major concern, loss of public confidence due to security breach • More complex environment requires specialized cybersecurity skills and possible enterprise level solutions © 2020 Center for Internet Security, Inc. Used with permission ®

CIS Controls: Implementation Group 3 IG 3 characteristics: • Full time cybersecurity staff with specialized skills • Regulatory and compliance obligations • Expectation of high availability for critical services • Data confidentiality and integrity must be maintained • Possibility of a breach affecting public welfare • Often subject to targeted, sophisticated attacks (including APT campaigns) • Must have controls in place to reduce impact of zero-day attacks © 2020 Center for Internet Security, Inc. Used with permission ®

CIS Control 1: Inventory and Control of Hardware Assets Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access ® © 2020 Center for Internet Security, Inc. Used with permission
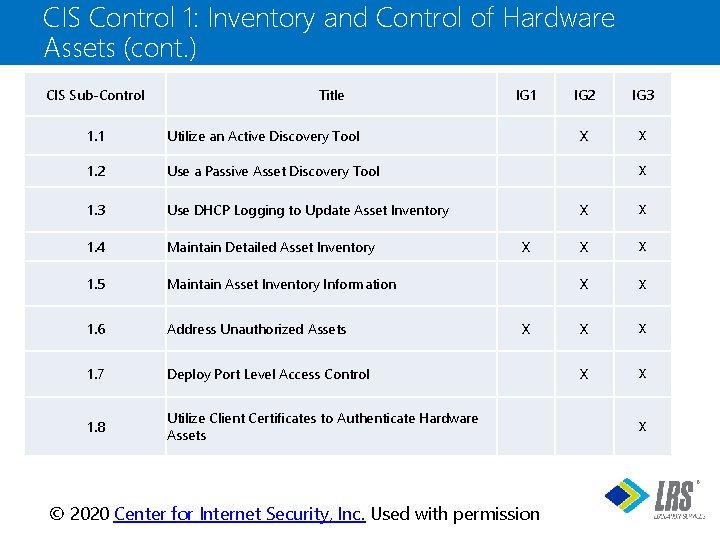
CIS Control 1: Inventory and Control of Hardware Assets (cont. ) CIS Sub-Control Title 1. 1 Utilize an Active Discovery Tool 1. 2 Use a Passive Asset Discovery Tool 1. 3 Use DHCP Logging to Update Asset Inventory 1. 4 Maintain Detailed Asset Inventory 1. 5 Maintain Asset Inventory Information 1. 6 Address Unauthorized Assets 1. 7 Deploy Port Level Access Control 1. 8 Utilize Client Certificates to Authenticate Hardware Assets IG 1 IG 2 IG 3 X X X X ® © 2020 Center for Internet Security, Inc. Used with permission
CIS Control 2: Inventory and Control of Software Assets Actively manage (inventory, track, and correct) all software on the network so that only authorized software is installed and can execute, and that unauthorized and unmanaged software is found and prevented from installation or execution ® © 2020 Center for Internet Security, Inc. Used with permission
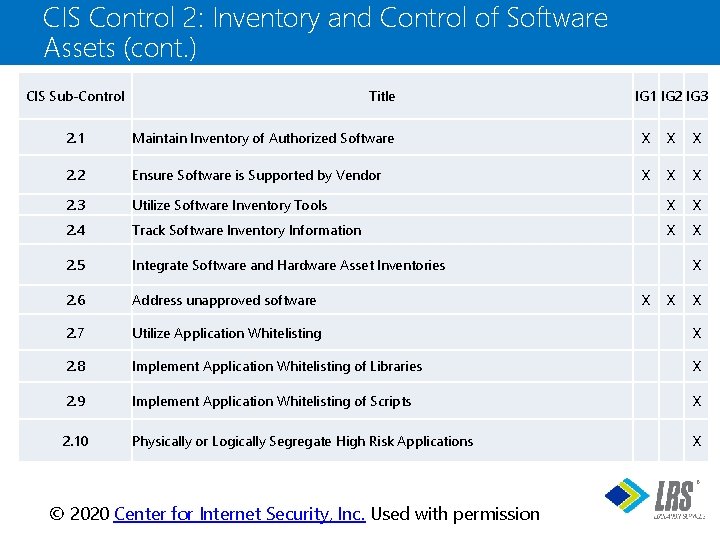
CIS Control 2: Inventory and Control of Software Assets (cont. ) CIS Sub-Control Title IG 1 IG 2 IG 3 2. 1 Maintain Inventory of Authorized Software X X X 2. 2 Ensure Software is Supported by Vendor X X X 2. 3 Utilize Software Inventory Tools X X 2. 4 Track Software Inventory Information X X 2. 5 Integrate Software and Hardware Asset Inventories 2. 6 Address unapproved software 2. 7 Utilize Application Whitelisting X 2. 8 Implement Application Whitelisting of Libraries X 2. 9 Implement Application Whitelisting of Scripts X 2. 10 Physically or Logically Segregate High Risk Applications X X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 3: Continuous Vulnerability Management Continuously acquire, assess, and take action on new information in order to identify vulnerabilities, remediate, and minimize the window of opportunity for attackers ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 3: Continuous Vulnerability Management (cont. ) CIS Sub-Control Title IG 1 IG 2 IG 3 3. 1 Run Automated Vulnerability Scanning Tools X X 3. 2 Perform Authenticated Vulnerability Scanning X X 3. 3 Protect Dedicated Assessment Accounts X X 3. 4 Deploy Automated Operating System Patch Management Tools X X X 3. 5 Deploy Automated Software Patch Management Tools X X X 3. 6 Compare Back-to-Back Vulnerability Scans X X 3. 7 Utilize a Risk-Rating Process X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 4: Controlled Use of Administrative Privileges The processes and tools used to track, control, prevent, correct the use, assignment, and configuration of administrative privileges on computers, networks, and applications ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 4: Controlled Use of Administrative Privileges (cont. ) CIS Sub-Control Title IG 1 IG 2 IG 3 4. 1 Maintain Inventory of Administrative Accounts 4. 2 Change Default Passwords X 4. 3 Ensure the Use of Dedicated Administrative Accounts X X X X 4. 4 Use Unique Passwords X X 4. 5 Use Multi-Factor Authentication for All Administrative Access X X 4. 6 Use Dedicated Workstations For All Administrative Tasks 4. 7 Limit Access to Script Tools X X 4. 8 Log and Alert on Changes to Administrative Group Membership X X 4. 9 Log and Alert on Unsuccessful Administrative Account Login X X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 5: Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers Establish, implement, and actively manage (track, report on, correct) the security configuration of mobile devices, laptops, servers, and workstations using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings ® © 2020 Center for Internet Security, Inc. Used with permission
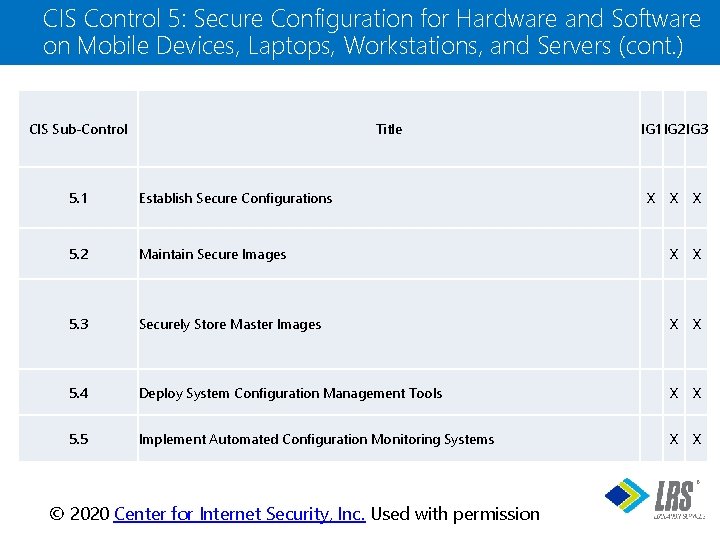
CIS Control 5: Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers (cont. ) CIS Sub-Control Title 5. 1 Establish Secure Configurations 5. 2 IG 1 IG 2 IG 3 X X X Maintain Secure Images X X 5. 3 Securely Store Master Images X X 5. 4 Deploy System Configuration Management Tools X X 5. 5 Implement Automated Configuration Monitoring Systems X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 6: Maintenance, Monitoring, and Analysis of Audit Logs Collect, manage, and analyze audit logs of events that could help detect, understand, or recover from an attack ® © 2020 Center for Internet Security, Inc. Used with permission
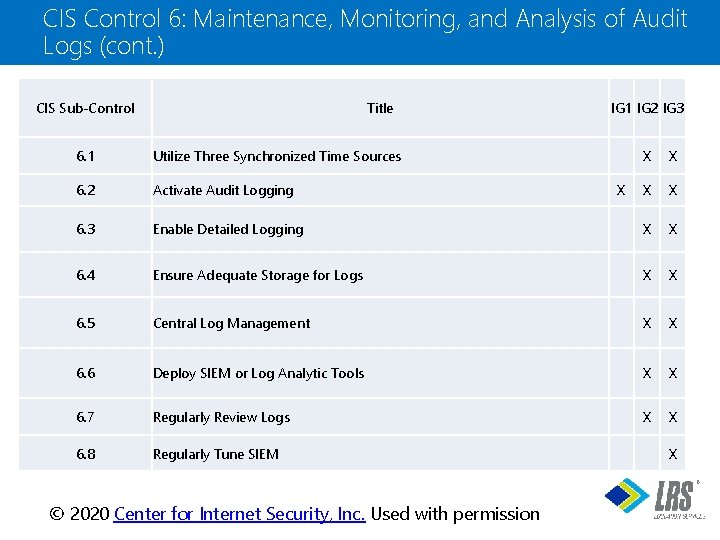
CIS Control 6: Maintenance, Monitoring, and Analysis of Audit Logs (cont. ) CIS Sub-Control Title 6. 1 Utilize Three Synchronized Time Sources 6. 2 Activate Audit Logging 6. 3 IG 1 IG 2 IG 3 X X Enable Detailed Logging X X 6. 4 Ensure Adequate Storage for Logs X X 6. 5 Central Log Management X X 6. 6 Deploy SIEM or Log Analytic Tools X X 6. 7 Regularly Review Logs X X 6. 8 Regularly Tune SIEM X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 7: Email and Web Browser Protections Minimize the attack surface and the opportunities for attackers to manipulate human behavior though their interaction with web browsers and email systems ® © 2020 Center for Internet Security, Inc. Used with permission
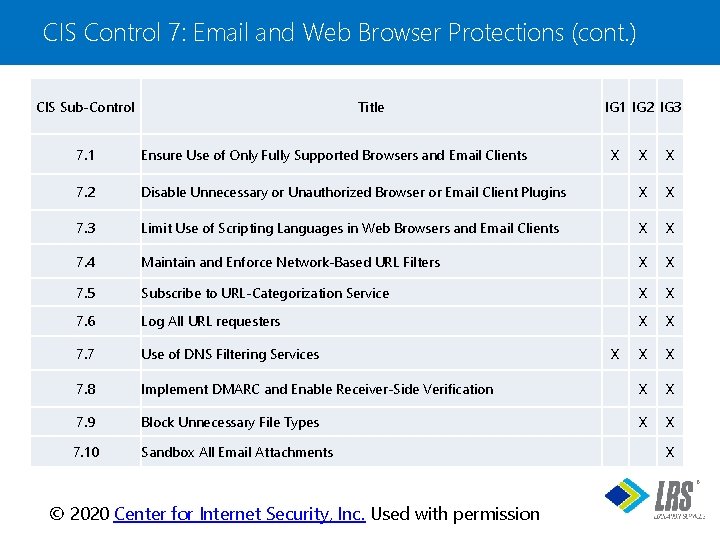
CIS Control 7: Email and Web Browser Protections (cont. ) CIS Sub-Control Title 7. 1 Ensure Use of Only Fully Supported Browsers and Email Clients 7. 2 IG 1 IG 2 IG 3 X X X Disable Unnecessary or Unauthorized Browser or Email Client Plugins X X 7. 3 Limit Use of Scripting Languages in Web Browsers and Email Clients X X 7. 4 Maintain and Enforce Network-Based URL Filters X X 7. 5 Subscribe to URL-Categorization Service X X 7. 6 Log All URL requesters X X 7. 7 Use of DNS Filtering Services X X 7. 8 Implement DMARC and Enable Receiver-Side Verification X X 7. 9 Block Unnecessary File Types X X 7. 10 Sandbox All Email Attachments X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 8: Malware Defenses Control the installation, spread, and execution of malicious code at multiple points in the enterprise, while optimizing the use of automation to enable rapid updating of defense, data gathering, and corrective action ® © 2020 Center for Internet Security, Inc. Used with permission
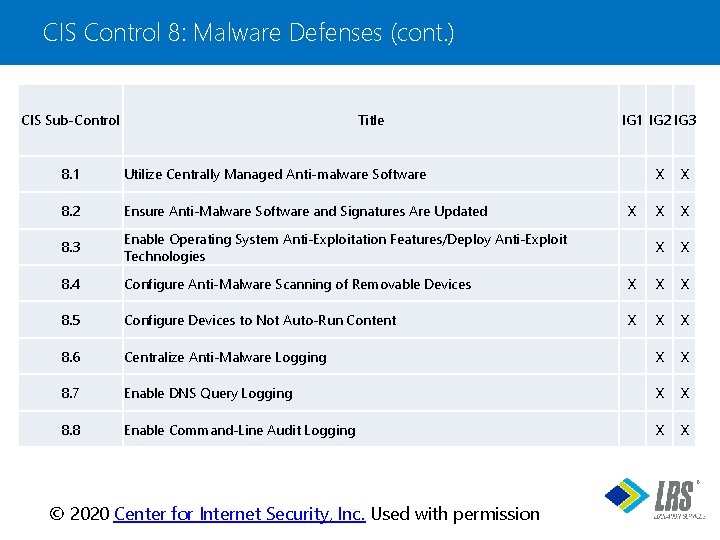
CIS Control 8: Malware Defenses (cont. ) CIS Sub-Control Title 8. 1 Utilize Centrally Managed Anti-malware Software 8. 2 Ensure Anti-Malware Software and Signatures Are Updated 8. 3 Enable Operating System Anti-Exploitation Features/Deploy Anti-Exploit Technologies 8. 4 Configure Anti-Malware Scanning of Removable Devices 8. 5 Configure Devices to Not Auto-Run Content 8. 6 IG 1 IG 2 IG 3 X X X Centralize Anti-Malware Logging X X 8. 7 Enable DNS Query Logging X X 8. 8 Enable Command-Line Audit Logging X X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 9: Limitation and Control of Network Ports, Protocols, and Services Manage (track/control/correct) the ongoing operational use of ports, protocols, and services on networked devices in order to minimize windows of vulnerability available to attackers ® © 2020 Center for Internet Security, Inc. Used with permission
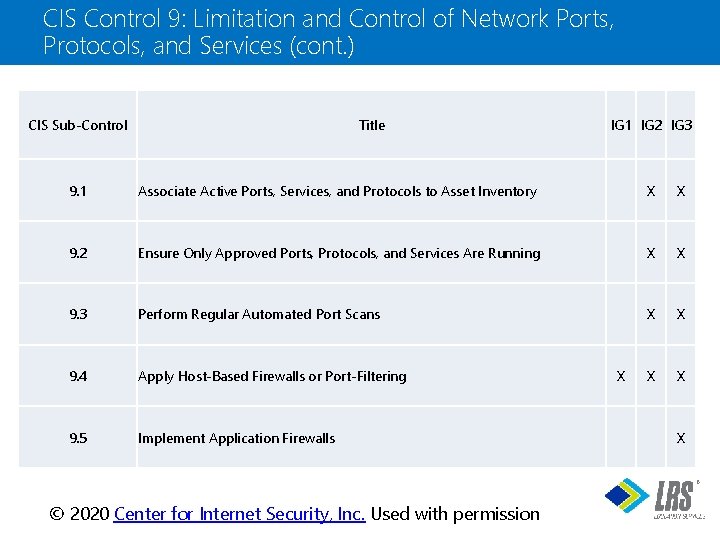
CIS Control 9: Limitation and Control of Network Ports, Protocols, and Services (cont. ) CIS Sub-Control Title IG 1 IG 2 IG 3 9. 1 Associate Active Ports, Services, and Protocols to Asset Inventory X X 9. 2 Ensure Only Approved Ports, Protocols, and Services Are Running X X 9. 3 Perform Regular Automated Port Scans X X 9. 4 Apply Host-Based Firewalls or Port-Filtering X X 9. 5 Implement Application Firewalls X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 10: Data Recovery Capabilities The processes and tools used to properly back up critical information with a proven methodology for timely recovery of it ® © 2020 Center for Internet Security, Inc. Used with permission
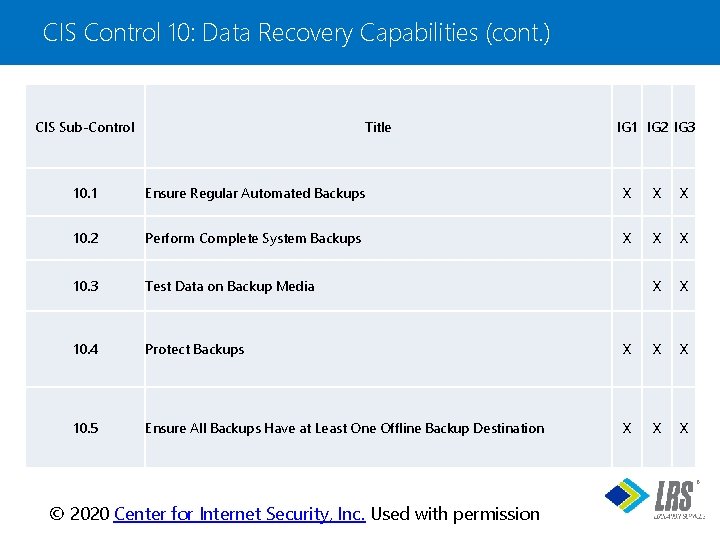
CIS Control 10: Data Recovery Capabilities (cont. ) CIS Sub-Control Title IG 1 IG 2 IG 3 10. 1 Ensure Regular Automated Backups X X X 10. 2 Perform Complete System Backups X X X 10. 3 Test Data on Backup Media X X 10. 4 Protect Backups X X X 10. 5 Ensure All Backups Have at Least One Offline Backup Destination X X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 11: Secure Configuration for Network Devices, such as Firewalls, Routers, and Switches Establish, implement, and actively manage (track, report on, correct) the security configuration of network infrastructure devices using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings ® © 2020 Center for Internet Security, Inc. Used with permission
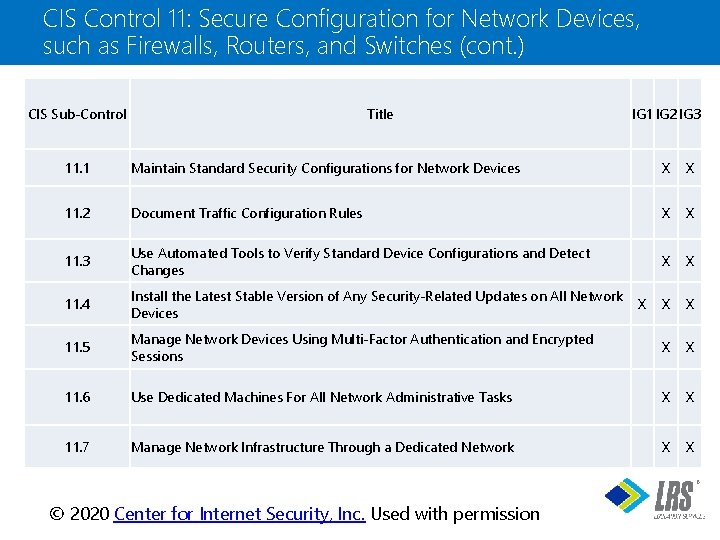
CIS Control 11: Secure Configuration for Network Devices, such as Firewalls, Routers, and Switches (cont. ) CIS Sub-Control Title IG 1 IG 2 IG 3 11. 1 Maintain Standard Security Configurations for Network Devices X X 11. 2 Document Traffic Configuration Rules X X 11. 3 Use Automated Tools to Verify Standard Device Configurations and Detect Changes X X 11. 4 Install the Latest Stable Version of Any Security-Related Updates on All Network Devices X X 11. 5 Manage Network Devices Using Multi-Factor Authentication and Encrypted Sessions X X 11. 6 Use Dedicated Machines For All Network Administrative Tasks X X 11. 7 Manage Network Infrastructure Through a Dedicated Network X X X ® © 2020 Center for Internet Security, Inc. Used with permission
CIS Control 12: Boundary Defense Detect/prevent/correct the flow of information transferring networks of different trust levels with a focus on security-damaging data ® © 2020 Center for Internet Security, Inc. Used with permission
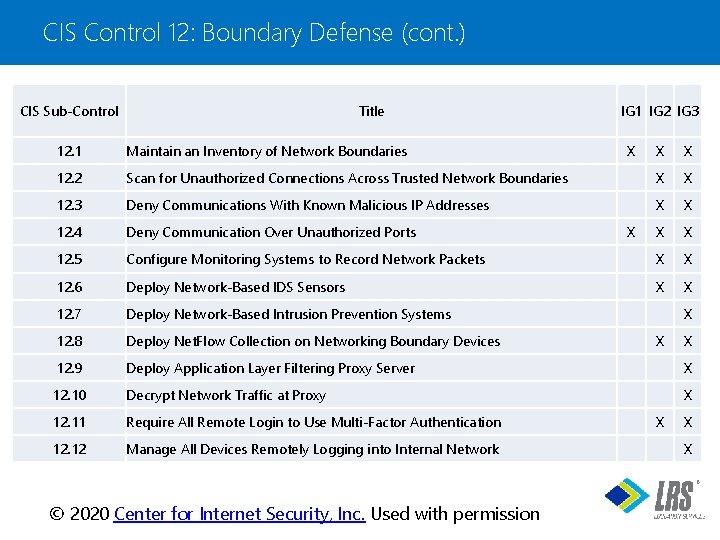
CIS Control 12: Boundary Defense (cont. ) CIS Sub-Control Title 12. 1 Maintain an Inventory of Network Boundaries 12. 2 IG 1 IG 2 IG 3 X X X Scan for Unauthorized Connections Across Trusted Network Boundaries X X 12. 3 Deny Communications With Known Malicious IP Addresses X X 12. 4 Deny Communication Over Unauthorized Ports X X 12. 5 Configure Monitoring Systems to Record Network Packets X X 12. 6 Deploy Network-Based IDS Sensors X X 12. 7 Deploy Network-Based Intrusion Prevention Systems 12. 8 Deploy Net. Flow Collection on Networking Boundary Devices 12. 9 Deploy Application Layer Filtering Proxy Server X 12. 10 Decrypt Network Traffic at Proxy X 12. 11 Require All Remote Login to Use Multi-Factor Authentication 12. 12 Manage All Devices Remotely Logging into Internal Network X X X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 13: Data Protection The processes and tools used to prevent data exfiltration, mitigate the effects of exfiltrated data, and ensure the privacy and integrity of sensitive information ® © 2020 Center for Internet Security, Inc. Used with permission
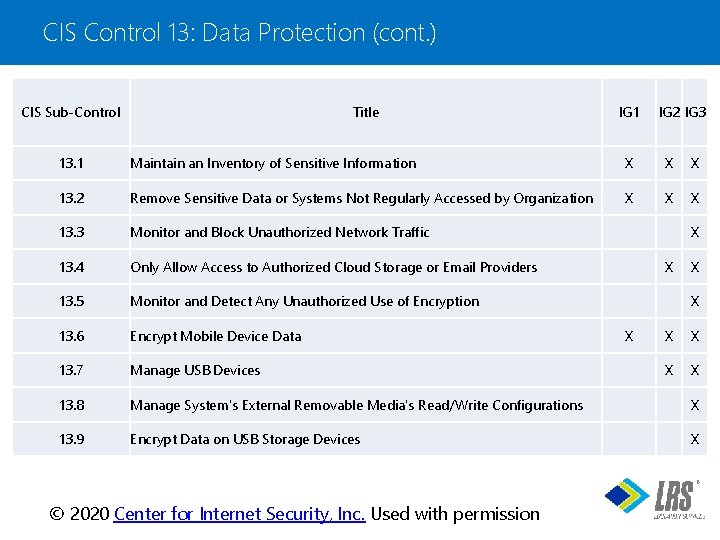
CIS Control 13: Data Protection (cont. ) CIS Sub-Control Title IG 1 IG 2 IG 3 13. 1 Maintain an Inventory of Sensitive Information X X X 13. 2 Remove Sensitive Data or Systems Not Regularly Accessed by Organization X X X 13. 3 Monitor and Block Unauthorized Network Traffic 13. 4 Only Allow Access to Authorized Cloud Storage or Email Providers 13. 5 Monitor and Detect Any Unauthorized Use of Encryption 13. 6 Encrypt Mobile Device Data 13. 7 Manage USB Devices 13. 8 Manage System's External Removable Media's Read/Write Configurations X 13. 9 Encrypt Data on USB Storage Devices X X X X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 14: Controlled Access Based on the Need to Know The processes and tools used to track/control/prevent/correct secure access to critical assets (e. g. , information, resources, systems) according to the formal determination of which persons, computers, and applications have a need and right to access these critical assets based on an approved classification ® © 2020 Center for Internet Security, Inc. Used with permission
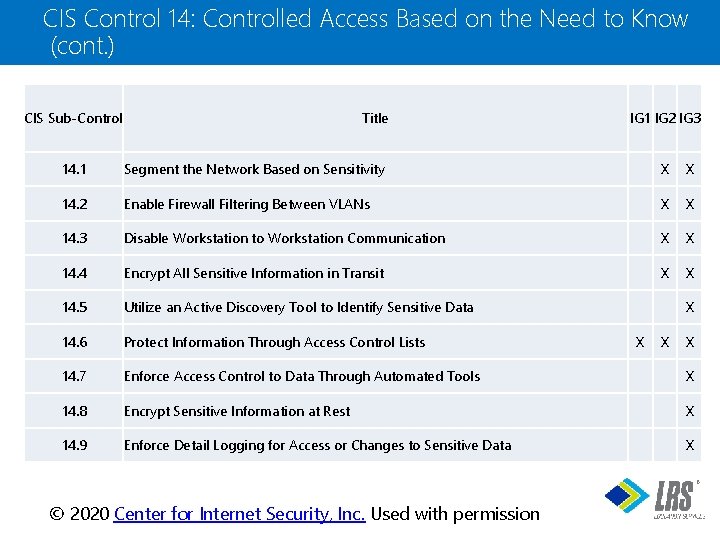
CIS Control 14: Controlled Access Based on the Need to Know (cont. ) CIS Sub-Control Title IG 1 IG 2 IG 3 14. 1 Segment the Network Based on Sensitivity X X 14. 2 Enable Firewall Filtering Between VLANs X X 14. 3 Disable Workstation to Workstation Communication X X 14. 4 Encrypt All Sensitive Information in Transit X X 14. 5 Utilize an Active Discovery Tool to Identify Sensitive Data 14. 6 Protect Information Through Access Control Lists 14. 7 Enforce Access Control to Data Through Automated Tools X 14. 8 Encrypt Sensitive Information at Rest X 14. 9 Enforce Detail Logging for Access or Changes to Sensitive Data X X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 15: Wireless Access Control The processes and tools used to track, control, prevent, and or correct the security use of wireless local area networks (WLANs), access points, and wireless client systems ® © 2020 Center for Internet Security, Inc. Used with permission
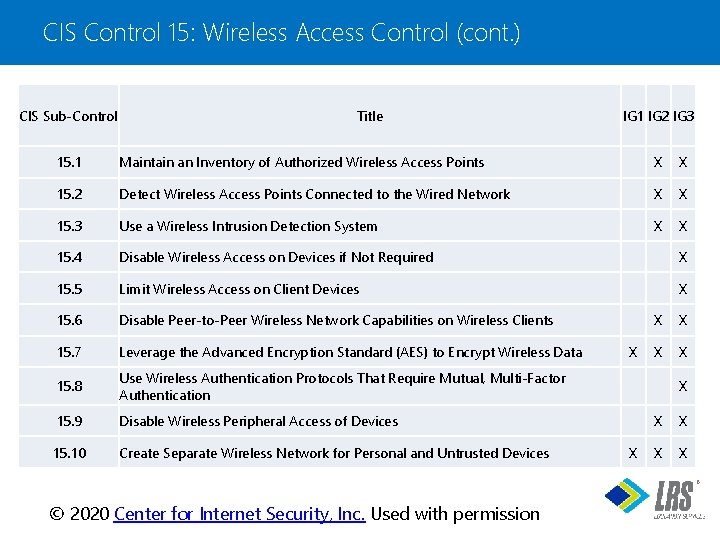
CIS Control 15: Wireless Access Control (cont. ) CIS Sub-Control Title IG 1 IG 2 IG 3 15. 1 Maintain an Inventory of Authorized Wireless Access Points X X 15. 2 Detect Wireless Access Points Connected to the Wired Network X X 15. 3 Use a Wireless Intrusion Detection System X X 15. 4 Disable Wireless Access on Devices if Not Required X 15. 5 Limit Wireless Access on Client Devices X 15. 6 Disable Peer-to-Peer Wireless Network Capabilities on Wireless Clients 15. 7 Leverage the Advanced Encryption Standard (AES) to Encrypt Wireless Data 15. 8 Use Wireless Authentication Protocols That Require Mutual, Multi-Factor Authentication 15. 9 Disable Wireless Peripheral Access of Devices 15. 10 Create Separate Wireless Network for Personal and Untrusted Devices X X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 16: Account Monitoring and Control Actively manage the life cycle of system and application accounts - their creation, use, dormancy, deletion - in order to minimize opportunities for attackers to leverage them ® © 2020 Center for Internet Security, Inc. Used with permission
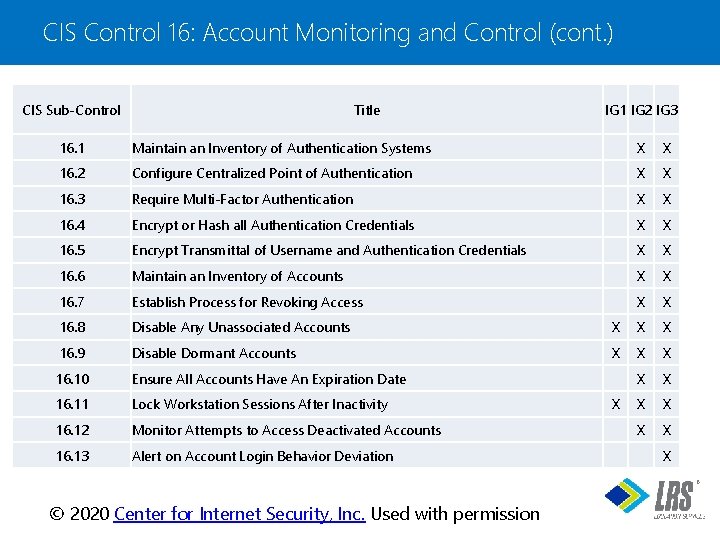
CIS Control 16: Account Monitoring and Control (cont. ) CIS Sub-Control Title IG 1 IG 2 IG 3 16. 1 Maintain an Inventory of Authentication Systems X X 16. 2 Configure Centralized Point of Authentication X X 16. 3 Require Multi-Factor Authentication X X 16. 4 Encrypt or Hash all Authentication Credentials X X 16. 5 Encrypt Transmittal of Username and Authentication Credentials X X 16. 6 Maintain an Inventory of Accounts X X 16. 7 Establish Process for Revoking Access X X 16. 8 Disable Any Unassociated Accounts X X X 16. 9 Disable Dormant Accounts X X X 16. 10 Ensure All Accounts Have An Expiration Date X X 16. 11 Lock Workstation Sessions After Inactivity X X 16. 12 Monitor Attempts to Access Deactivated Accounts X X 16. 13 Alert on Account Login Behavior Deviation X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 17: Implement a Security Awareness and Training Program For all functional roles in the organization (prioritizing those mission-critical to the business and its security): • Identify the specific knowledge, skills, and abilities (KSAs) needed to support defense of the enterprise; • Develop and execute an integrated plan to assess KSAs, identify gaps, and remediate gaps through policy, organizational planning, training, and awareness programs © 2020 Center for Internet Security, Inc. Used with permission ®
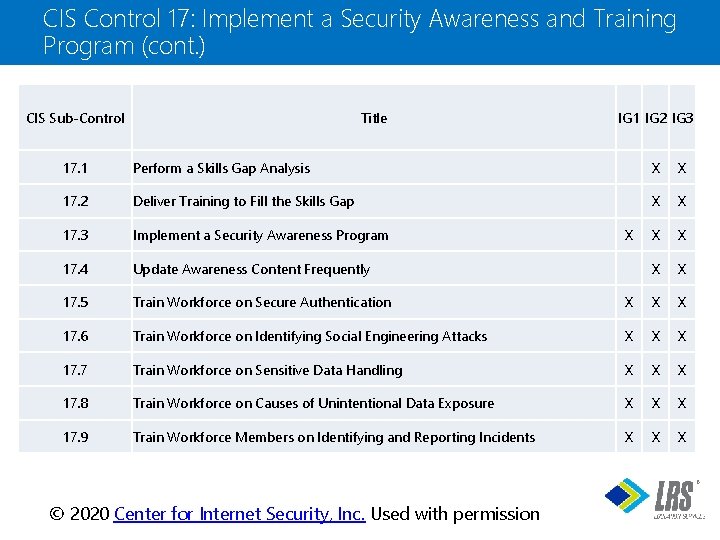
CIS Control 17: Implement a Security Awareness and Training Program (cont. ) CIS Sub-Control Title IG 1 IG 2 IG 3 17. 1 Perform a Skills Gap Analysis X X 17. 2 Deliver Training to Fill the Skills Gap X X 17. 3 Implement a Security Awareness Program X X 17. 4 Update Awareness Content Frequently X X 17. 5 Train Workforce on Secure Authentication X X X 17. 6 Train Workforce on Identifying Social Engineering Attacks X X X 17. 7 Train Workforce on Sensitive Data Handling X X X 17. 8 Train Workforce on Causes of Unintentional Data Exposure X X X 17. 9 Train Workforce Members on Identifying and Reporting Incidents X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 18: Application Software Security Manage the security life cycle of all in-house developed and acquired software in order to prevent, detect, and correct security weaknesses ® © 2020 Center for Internet Security, Inc. Used with permission
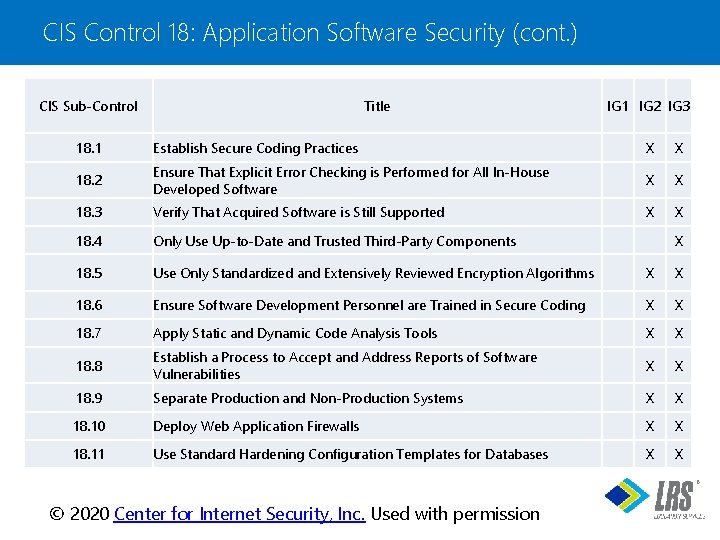
CIS Control 18: Application Software Security (cont. ) CIS Sub-Control Title IG 1 IG 2 IG 3 18. 1 Establish Secure Coding Practices X X 18. 2 Ensure That Explicit Error Checking is Performed for All In-House Developed Software X X 18. 3 Verify That Acquired Software is Still Supported X X 18. 4 Only Use Up-to-Date and Trusted Third-Party Components 18. 5 Use Only Standardized and Extensively Reviewed Encryption Algorithms X X 18. 6 Ensure Software Development Personnel are Trained in Secure Coding X X 18. 7 Apply Static and Dynamic Code Analysis Tools X X 18. 8 Establish a Process to Accept and Address Reports of Software Vulnerabilities X X 18. 9 Separate Production and Non-Production Systems X X 18. 10 Deploy Web Application Firewalls X X 18. 11 Use Standard Hardening Configuration Templates for Databases X X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 19: Incident Response and Management Protect the organization's information, as well as its reputation, by developing and implementing an incident response infrastructure (e. g. , plans, defined roles, training, communications, management oversight) The incident response infrastructure will allow for quickly discovering an attack and then effectively containing the damage, eradicating the attacker's presence, and restoring the integrity of the network and systems © 2020 Center for Internet Security, Inc. Used with permission ®
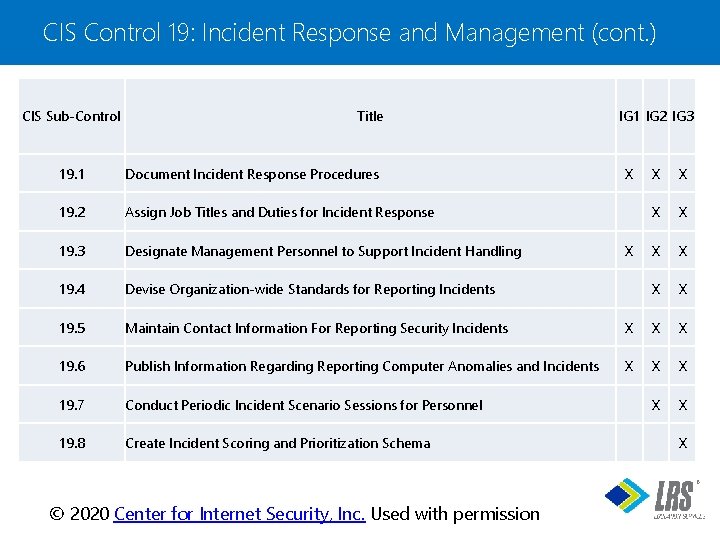
CIS Control 19: Incident Response and Management (cont. ) CIS Sub-Control Title 19. 1 Document Incident Response Procedures 19. 2 Assign Job Titles and Duties for Incident Response 19. 3 Designate Management Personnel to Support Incident Handling 19. 4 Devise Organization-wide Standards for Reporting Incidents 19. 5 Maintain Contact Information For Reporting Security Incidents 19. 6 Publish Information Regarding Reporting Computer Anomalies and Incidents 19. 7 Conduct Periodic Incident Scenario Sessions for Personnel 19. 8 Create Incident Scoring and Prioritization Schema IG 1 IG 2 IG 3 X X X X X ® © 2020 Center for Internet Security, Inc. Used with permission

CIS Control 20: Penetration Tests and Red Team Exercises Test the overall strength of an organization's defense (the technology, the processes, and the people) by simulating the objectives and actions of an attacker ® © 2020 Center for Internet Security, Inc. Used with permission
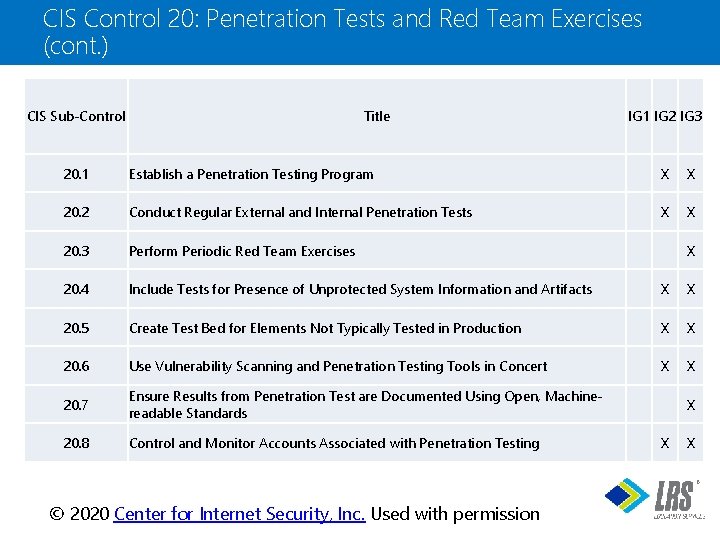
CIS Control 20: Penetration Tests and Red Team Exercises (cont. ) CIS Sub-Control Title IG 1 IG 2 IG 3 20. 1 Establish a Penetration Testing Program X X 20. 2 Conduct Regular External and Internal Penetration Tests X X 20. 3 Perform Periodic Red Team Exercises 20. 4 Include Tests for Presence of Unprotected System Information and Artifacts X X 20. 5 Create Test Bed for Elements Not Typically Tested in Production X X 20. 6 Use Vulnerability Scanning and Penetration Testing Tools in Concert X X 20. 7 Ensure Results from Penetration Test are Documented Using Open, Machinereadable Standards 20. 8 Control and Monitor Accounts Associated with Penetration Testing X X ® © 2020 Center for Internet Security, Inc. Used with permission

ISO/IEC 27001: 2013 • Defines requirements for certification of an Information Security Management System (ISMS) • Published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) • Consists of 114 controls in 14 clauses and 35 control categories • Focus is on the written polices for control design and implementation ®

ISO/IEC 27001: 2013 • ISO 27001: 2013 requires: • Systematic examination of IS risks • Design and implementation of controls and or other risk treatments • Create an overarching management process ®

ISO/IEC 27001: 2013 Control Clauses • ISO 27001: 2013 contains 14 Control Clauses, each with two or more controls: • A. 5: Information security policies (2 controls) • A. 6: Organization of information security (7 controls) • A. 7: Human resource security - 6 controls that are applied before, during, or after employment • A. 8: Asset management (10 controls) • A. 9: Access control (14 controls) • A. 10: Cryptography (2 controls) • A. 11: Physical and environmental security (15 controls) ®

ISO/IEC 27001: 2013 Control Clauses (cont. ) • ISO 27001: 2013 contains 14 Control Clauses, each with two or more controls: • A. 12: Operations security (14 controls) • A. 13: Communications security (7 controls) • A. 14: System acquisition, development and maintenance (13 controls) • A. 15: Supplier relationships (5 controls) • A. 16: Information security incident management (7 controls) • A. 17: Information security aspects of business continuity management (4 controls) • A. 18: Compliance; with internal requirements, such as policies, and with external requirements, such as laws (8 controls) ®

ISO/IEC 27002: 2013 • ISO 27002: 2013: • Is a listing of best practices for ISO 27001: 2013 controls and control clauses • Does not contain specific controls • Follows the layout of the ISO 27001: 2013 control clauses for listing best practices ®

ISO/IEC 27002: 2013 Example - Physical and Environmental Security • • • Physical access to premises and support infrastructure (communications, power, air conditioning etc. ) must be monitored and restricted to prevent, detect and minimize the effects of unauthorized and inappropriate access, tampering, vandalism, criminal damage, theft etc. The list of people authorized to access secure areas must be reviewed and approved periodically (at least once a year) by Administration or Physical Security Department, and crosschecked by their departmental managers Photography or video recording is forbidden inside Restricted Areas without prior permission from the designated authority ®

ISO/IEC 27002: 2013 Example - Physical and Environmental Security (cont. ) • • • Suitable video surveillance cameras must be located at all entrances and exits to the premises and other strategic points such as Restricted Areas, recorded and stored for at least one month, and monitored around the clock by trained personnel Access cards permitting time-limited access to general and/or specific areas may be provided to trainees, vendors, consultants, third parties and other personnel who have been identified, authenticated, and authorized to access those areas Other than in public areas such as the reception foyer, and private areas such as rest rooms, visitors should be escorted at all times by an employee while on the premises ®

ISO/IEC 27002: 2013 Example - Physical and Environmental Security (cont. ) • • • The date and time of entry and departure of visitors along with the purpose of visits must be recorded in a register maintained and controlled by Site Security or Reception Everyone on site (employees and visitors) must wear and display their valid pass at all times, and must present their pass for inspection on request by a manager, security guard or concerned employee Access control systems must themselves be adequately secured against unauthorized/inappropriate access and other compromises Fire/evacuation drills must be conducted periodically (at least once a year) Smoking is forbidden other than in designated Smoking Zones ®

ISO/IEC 27002: 2013 Example – Access Control • • • User access to corporate IT systems, networks, applications and information must be controlled in accordance with access requirements specified by the relevant Information Asset Owners, normally according to the user's role Generic or test IDs must not be created or enabled on production systems unless specifically authorized by the relevant Information Asset Owners After a predefined number of unsuccessful logon attempts, security log entries and (where appropriate) security alerts must be generated and user accounts must be locked out as required by the relevant Information Asset Owners ®

ISO/IEC 27002: 2013 Example – Access Control (cont. ) • • Passwords or pass phrases must be lengthy and complex, consisting of a mix of letters, numerals and special characters that would be difficult to guess Passwords or pass phrases must not be written down or stored in readable format Authentication information such as passwords, security logs, security configurations and so forth must be adequately secured against unauthorized or inappropriate access, modification, corruption or loss Privileged access rights typically required to administer, configure, manage, secure and monitor IT systems must be reviewed periodically (at least twice a year) by Information Security and cross-checked by the appropriate departmental managers ®

ISO/IEC 27002: 2013 Example – Access Control (cont. ) • • • Users must either log off or password-lock their sessions before leaving them unattended Password-protected screensavers with an inactivity timeout of no more than 10 minutes must be enabled on all workstations/PCs Write access to removable media (USB drives, CD/DVD writers etc. ) must be disabled on all desktops unless specifically authorized for legitimate business reasons ®

Supply Chain Risk Management in the Enterprise • • What is Supply Chain Risk Management (SCRM)? SCRM Processes and Resilience SCRM Risk Measurement SCRM Methods ®

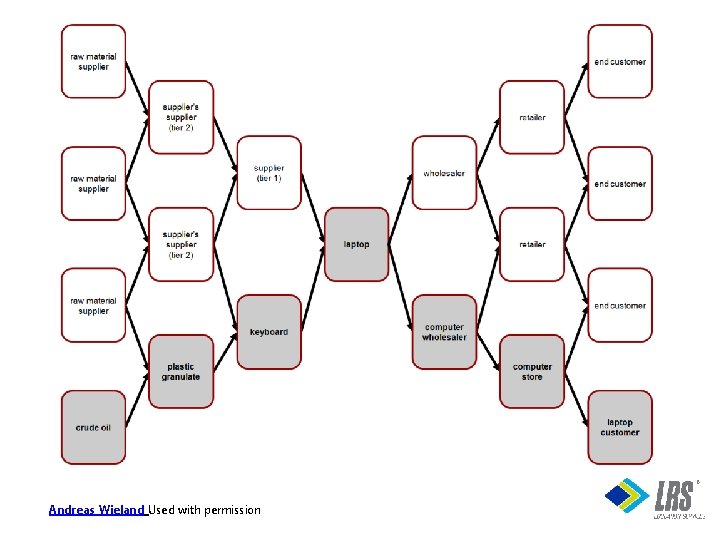
What is Supply Chain Risk Management? Supply Chain Risk Management (SCRM): • Involves all supply chain stakeholders to identify potential failure points • Implements strategies to manage risks from all links of the supply chain • Uses continuous risk assessment to reduce vulnerabilities and ensure continuity • Applies processes and tools to address risks related to resources and or logistics issues in the supply chain ®
® Andreas Wieland Used with permission

Supply Chain Risk Management Processes and Resilience • SCRM includes four processes: • • Identification of SC risk sources Assessment of SC risks Controlling SC risks Monitoring for conditions • Resilience is added to SCRM to measure the supply chain’s ability to recover from risks when they are realized ®

Supply Chain Risk Management Risk Measurement • SCRM Risk Measurement is calculation of the likelihood and impact of a particular risk • SCRM can include a very high number of risks • SCRM often focuses on risks per site, or per category of product/service • Depending on risk type calculation may be quantitative, qualitative, or semi-quantitative ®

Supply Chain Risk Management Methods Some methods to reach an acceptable risk level include: • • Managing stock Considering alternative sourcing arrangements Business interruption / contingency insurance Audits Awareness campaigns and training programs Redundancy optimization Postponement Collaboration ®

End of Module 4 Components of the NIST Cybersecurity Framework ®
- Slides: 94