Module 3 Nautical Science Unit 5 Physical Science







































































- Slides: 105

Module 3 – Nautical Science Unit 5 – Physical Science Chapter 22 – Computers and the Internet Section 1 – Computers and the Internet

What You Will Learn to Do Demonstrate understanding of Physical Science

Objectives 1. Define the concept of a computer 2. Discuss how modern computers evolved 3. Explain the basics of computer architecture 4. Describe the evolution of the modern internet

Objectives 5. Describe the attributes of a computer server 6. Explain how the internet is organized, controlled and accessed 7. Explain the concepts of cyberspace and the importance of internet security

Key Term Questions Slide Index Click any link below to go directly to polling that question. 1. Device, exchanging data between computers 2. Connects to computer, add functionality 4. Circuit on a small piece of semiconducting material 5. Compact computer, uses microprocessor 3. Part of a computer, operations 6. Personal computer, portable are controlled 7. Data processing system, by large organization Click here to return to this index.

Key Term Questions Slide Index Click any link below to go directly to polling that question. 8. Software, manages computer hardware and software 9. Physical components of computer 12. Group of binary digits or bits 13. Data storage, rotating disks coated with magnetic material 14. Volatile storage area on 10. Programs, operate hardware 11. Method of representing numbers has 2 as base computer 15. Program that operates a particular type of device Click here to return to this index.

Key Term Questions Slide Index Click any link below to go directly to polling that question. 16. Computer, represents data by 19. Agency responsible for measurable quantities 17. System, manages computer development of new technologies files, responds to requests from 20. Messages distributed by electronic means remote devices 21. System, Internet names and 18. Global system of interconnected networks addresses are regulated Click here to return to this index.

Key Term Questions Slide Index Click any link below to go directly to polling that question. 22. Location connected to Internet 25. Graphical user interface for 23. Rules governing format of data displaying HTML files 26. Program for finding particular sent over Internet 24. System on Internet, documents sites on World Wide Web connected to other documents 27. Broadcasting through the by hypertext links Internet Click here to return to this index.

Key Term Questions Slide Index Click any link below to go directly to polling that question. 28. Company, provides access to Internet to subscribers 32. Environment, communication over computer network occurs 29. Using remote servers hosted on 33. Person who uses computers to Internet to store data gain unauthorized access 30. High-capacity transmission 34. Fraudulent acquisition and use of a person's private identifying technique 31. Study or use of systems information Click here to return to this index.

Key Term Questions Slide Index Click any link below to go directly to polling that question. 35. Politically motivated use of information technology to cause severe disruption 36. Use of computers to attack an enemy's information systems Click here to return to this index.

A device for exchanging digital data between computers or other devices A. B. C. D. Browser Search engine Device driver Modem 1 1 (NS 2 -M 3 C 22 S 1: KT 1)

Connects to a computer system to add functionality, such as a mouse, keyboard or printer A. B. C. D. Device driver Peripheral device Hard drive Hardware 1 1 (NS 2 -M 3 C 22 S 1: KT 2)

The part of a computer in which operations are controlled and executed A. B. C. D. Central Processing Unit (CPU) Integrated circuits Main frame Computer operating system 1 1 (NS 2 -M 3 C 22 S 1: KT 3)

An electronic circuit formed on a small piece of semiconducting material. Performing the same function as a larger circuit made from discrete components A. B. C. D. Electronic circuits Binary circuits Integrated circuits Device circuits 1 1 (NS 2 -M 3 C 22 S 1: KT 4)

A compact computer that uses a microprocessor, designed for use by one person at a time A. B. C. D. Desk top Laptop computer Personal computer (PC) Device driver 1 1 (NS 2 -M 3 C 22 S 1: KT 5)

A personal computer that is easily portable A. B. C. D. Personal computer (PC) Laptop computer Device Driver Peripheral device 1 1 (NS 2 -M 3 C 22 S 1: KT 6)

A data processing system employed mainly by a large organization for managing information A. B. C. D. Subframe Mainframe Data System Software 1 1 (NS 2 -M 3 C 22 S 1: KT 7)

Software that manages computer hardware and software, central to all processing A. B. C. D. Computer operating system Random access memory (RAM) Search engine Broadband 1 1 (NS 2 -M 3 C 22 S 1: KT 8)

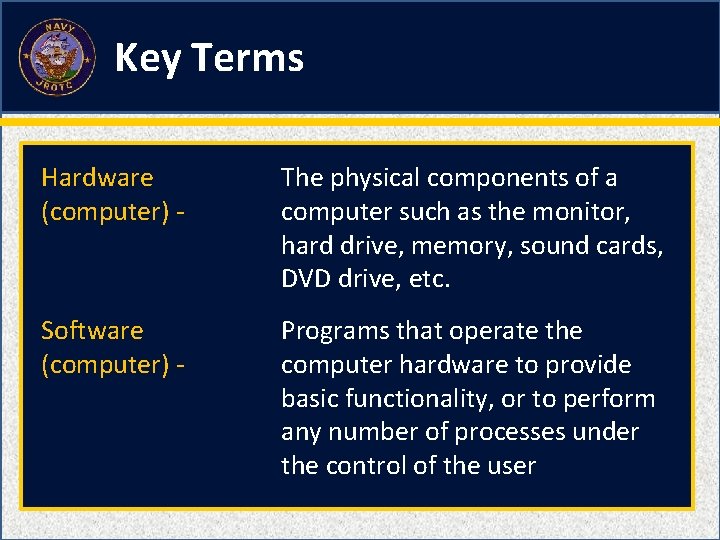
The physical components of a computer such as the monitor, hard drive, memory, sound cards, DVD drive, etc. A. B. C. D. Device drivers Server Hardware Software 1 1 (NS 2 -M 3 C 22 S 1: KT 9)

Programs that operate the computer hardware to provide basic functionality, or to perform any number of processes under the control of the user A. B. C. D. Hardware Software Hard drive Hacker 1 1 (NS 2 -M 3 C 22 S 1: KT 10)

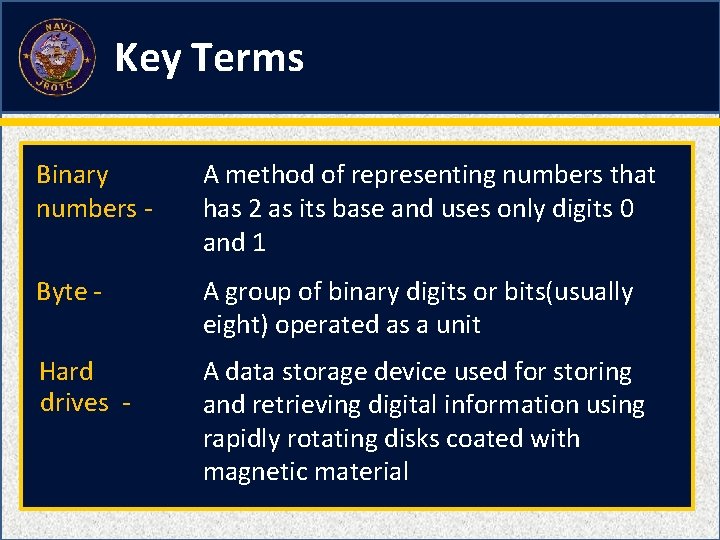
A method of representing numbers that has 2 as its base and uses only digits 0 and 1 A. B. C. D. Byte Binary numbers Broadband Browser 1 1 (NS 2 -M 3 C 22 S 1: KT 11)

A group of binary digits or bits (usually eight) operated as a unit A. B. C. D. Ballast Broadband Byte Bynamite 1 1 (NS 2 -M 3 C 22 S 1: KT 12)

A data storage device used for storing and retrieving digital information using rapidly rotating disks coated with magnetic material A. B. C. D. Data drives Storage drives Soft drives Hard drives 1 1 (NS 2 -M 3 C 22 S 1: KT 13)

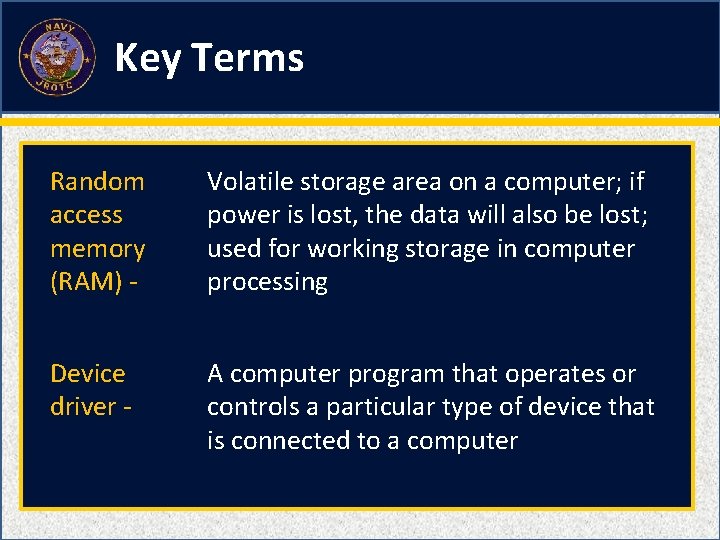
Volatile storage area on a computer; if power is lost, the data will also be lost; used for working storage in computer processing A. B. C. D. Server Hard drive Hardware Random access memory (RAM) 1 1 (NS 2 -M 3 C 22 S 1: KT 14)

A computer program that operates or controls a particular type of device that is connected to a computer A. B. C. D. Analog computer Memory driver Controller Device driver 1 1 (NS 2 -M 3 C 22 S 1: KT 15)

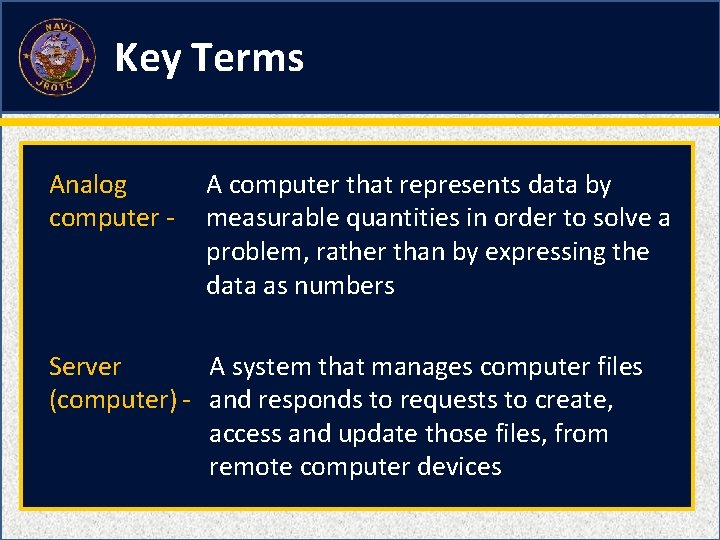
A computer that represents data by measurable quantities in order to solve a problem, rather than by expressing the data as numbers A. B. C. D. Analog computer Server (computer) Integrated circuits Personal computer (PC) 1 1 (NS 2 -M 3 C 22 S 1: KT 16)

A system that manages computer files and responds to requests to create, access and update those files, from remote computer devices A. B. C. D. Integrated circuits Random access memory (RAM) Server Device driver 1 1 (NS 2 -M 3 C 22 S 1: KT 17)

A global system of interconnected computer networks that use a standard protocol suite (TCP/IP) to link devices worldwide A. B. C. D. World Wide Web Internet Goggle MSN 1 1 (NS 2 -M 3 C 22 S 1: KT 18)

An agency of the Department of Defense responsible for the development of new technologies for use by the military A. B. C. D. CIA DNS ARPANET DARPA 1 1 (NS 2 -M 3 C 22 S 1: KT 19)

Messages distributed by electronic means from one computer user to one more recipients via a network A. B. C. D. Snail Mail E-mails Facetime Browsers 1 1 (NS 2 -M 3 C 22 S 1: KT 20)

The system by which Internet names and addresses are tracked and regulated A. B. C. D. Information Technology System Cyberspace System Internet Service System Domain Name System 1 1 (NS 2 -M 3 C 22 S 1: KT 21)

A location connected to the Internet that maintains one or more pages on the World Wide Web A. B. C. D. E-mail Website Address Browser Broadband 1 1 (NS 2 -M 3 C 22 S 1: KT 22)

A set of rules governing the format of data sent over the Internet or other network A. B. C. D. World Wide Web rules Cyber Laws Internet Protocol Webcasting 1 1 (NS 2 -M 3 C 22 S 1: KT 23)

An information system on the Internet that allows documents to be connected to other documents by hypertext links, enabling the user to search for information by moving from one document to another A. B. C. D. ARPANET Internet service provider DARPA World Wide Web 1 1 (NS 2 -M 3 C 22 S 1: KT 24)

A program with a graphical user interface for displaying HTML files, used to navigate the World Wide Web A. B. C. D. Server Browser Hacker E-mails 1 1 (NS 2 -M 3 C 22 S 1: KT 25)

A program that searches for and identifies items in a database that correspond to keywords or characters specified by the user, especially for finding particular sites on the World Wide Web A. B. C. D. Website address Internet Browser Search engine 1 1 (NS 2 -M 3 C 22 S 1: KT 26)

Broadcasting through the Internet A. B. C. D. Cyber warfare Hacking Cloud computing Webcasting 1 1 (NS 2 -M 3 C 22 S 1: KT 27)

A company that provides access to the Internet to subscriber-based customers A. B. C. D. DARPA WWW ISP RAM 1 1 (NS 2 -M 3 C 22 S 1: KT 28)

The practice of using a network of remote servers hosted on the Internet to store, manage and process data, rather than a local server or a personal computer A. B. C. D. Browsing Broadband Searching Cloud computing Cyberterrorism 1 1 (NS 2 -M 3 C 22 S 1: KT 29)

A high-capacity transmission technique using a wide range of frequencies, which enables a large number of messages to be communicated simultaneously A. B. C. D. Bandwidth Broadband Frequency range Frequency band 1 1 (NS 2 -M 3 C 22 S 1: KT 30)

The study or use of systems (especially computers and telecommunications) for storing, retrieving and sending information A. B. C. D. Cyber technology Information technology Internet technology Instant Messaging 1 1 (NS 2 -M 3 C 22 S 1: KT 31)

The notational environment in which communication over computer network occurs A. B. C. D. Innerspace Browser Cyberspace Broadband 1 1 (NS 2 -M 3 C 22 S 1: KT 32)

A person who uses computers to gain unauthorized access to data A. B. C. D. Internet thief Cyber Bully Identity thief Hacker 1 1 (NS 2 -M 3 C 22 S 1: KT 33)

The fraudulent acquisition and use of a person's private identifying information, usually for financial gain A. B. C. D. Cyber bullying Cyber warfare Cyberterrorism Identity theft 1 1 (NS 2 -M 3 C 22 S 1: KT 34)

The politically motivated use of computers and information technology to cause severe disruption or widespread fear in society A. B. C. D. Cyber warfare Cyberterrorism Hacking Identity Theft 1 1 (NS 2 -M 3 C 22 S 1: KT 35)

The use of computers and other devices to attack an enemy's information systems as opposed to an enemy's armies or factories A. B. C. D. Hacking Cyberterrorism Cyber warfare Identity Theft 1 1 (NS 2 -M 3 C 22 S 1: KT 36)

Key Terms Modem - A device for exchanging digital data between computers or other devices Peripheral device - Connects to a computer system to add functionality, such as a mouse, keyboard or printer Central The part of a computer in which Processing operations are controlled and executed Unit (CPU) -

Key Terms Personal computer (PC) - A compact computer that uses a microprocessor, designed for use by one person at a time Laptop computer - A personal computer that is easily portable Integrated circuits - An electronic circuit formed on a small piece of semiconducting material, Performing the same function as a larger circuit made from discrete components

Key Terms Main frame - A data processing system employed mainly by a large organization for managing information Computer operating system - Software that manages computer hardware and software, central to all processing

Key Terms Hardware (computer) - The physical components of a computer such as the monitor, hard drive, memory, sound cards, DVD drive, etc. Software (computer) - Programs that operate the computer hardware to provide basic functionality, or to perform any number of processes under the control of the user

Key Terms Binary numbers - A method of representing numbers that has 2 as its base and uses only digits 0 and 1 Byte - A group of binary digits or bits(usually eight) operated as a unit Hard drives - A data storage device used for storing and retrieving digital information using rapidly rotating disks coated with magnetic material

Key Terms Random access memory (RAM) - Volatile storage area on a computer; if power is lost, the data will also be lost; used for working storage in computer processing Device driver - A computer program that operates or controls a particular type of device that is connected to a computer

Key Terms Analog computer - A computer that represents data by measurable quantities in order to solve a problem, rather than by expressing the data as numbers Server A system that manages computer files (computer) - and responds to requests to create, access and update those files, from remote computer devices

Key Terms Internet - A global system of interconnected computer networks that use the standard internet protocol suite(TCP/IP) to link devices worldwide DARPA - Defense Advanced Research Projects Agency; an agency of the US Department of Defense responsible for the development of new technologies for use by the military

Key Terms E-mails - Messages distributed by electronic means from one computer user to one or more recipients via a network Website Address - A location connected to the internet that maintains one or more pages on the World Wide Web Domain Name System - The system by which internet domain names and addresses are tracked and regulated

Key Terms Internet A set of rules governing the format of Protocol (IP) - data sent over the Internet or other network World Wide Web - An information system on the Internet that allows documents to be connected to other documents by hypertext links, enabling the user to search for information by moving from one document to another

Key Terms Browser - A program with a graphical user interface for displaying HTML files, used to navigate the World Wide Web Search engine - A program that searches for and identifies items in a database that correspond to keywords or characters specified by the user, especially for finding particular sites on the World Wide Web

Key Terms Internet A company that provides access to the service internet to subscriber-based provider (ISP) - customers Cloud computing - Webcasting - The practice of using a network of remote servers hosted on the Internet to store, manage and process data, rather than a local server or a personal computer Broadcasting through the internet

Key Terms Broadband - A high-capacity transmission technique using a wide range of frequencies, which enables a large number of messages to be communicated simultaneously Information technology (IT) - The study or use of systems(especially computers and telecommunications) for storing, retrieving and sending information

Key Terms Cyberspace - The notational environment in which communication over computer network occurs Hacker - A person who uses computers to gain unauthorized access to data Identity theft - The fraudulent acquisition and use of a person’s private identifying information, usually for financial gain

Key Terms Cyberterrorism - The politically motivated use of computers and information technology to cause severe disruption or widespread fear in society Cyber warfare - The use of computers and other devices to attack an enemy’s information systems as opposed to an enemy’s armies or factories

How do you think computers all over the world connect via the internet? 1. 2. 3. Note to Instructors: Click the Show/Hide Response Display Button

How much have you used computers and the internet? A. Expert - So much, I can make them do whatever I want! B. Knowledgeable – I’ve used them quite a bit, but cant claim to know everything. C. Rookie – I’ve used computers and the internet for basic things. D. Novice - I haven’t had much experience. 1 1 (NS 2 -M 3 C 22 S 1: LQ 1)

When were the first U. K. and U. S. digital computers developed? A. B. C. D. 1940's 1950's 1960's 1970's 1 1 (NS 2 -M 3 C 22 S 1: LQ 2)

Introduction A computer is a device that can carry out a finite set of arithmetic or logical instructions. The electronic digital computer always contains a central processing unit(CPU) and some form of memory. It may also have other internal components, and/or peripheral devices which are attached either wirelessly or with cables.

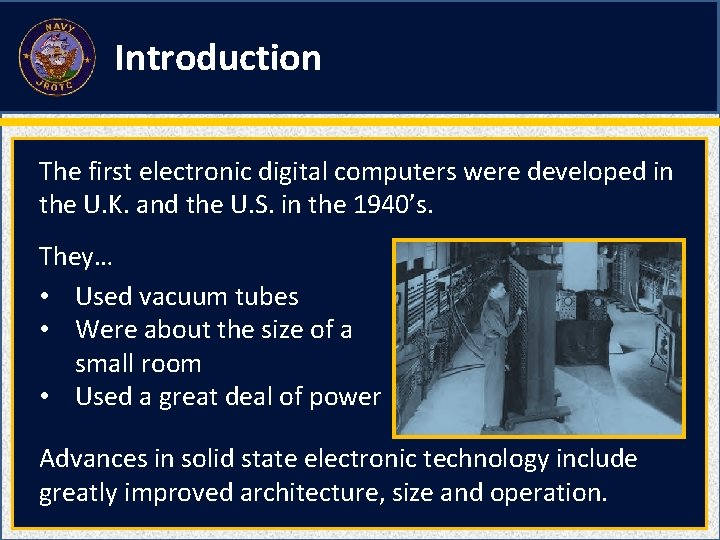
Introduction The first electronic digital computers were developed in the U. K. and the U. S. in the 1940’s. They… • Used vacuum tubes • Were about the size of a small room • Used a great deal of power Advances in solid state electronic technology include greatly improved architecture, size and operation.

Modern Digital Computers • Modern computers are based on integrated circuits. • Chips are combined with other electronic components on printed circuit boards. • Chips can process millions of times faster with more power than the computers of 40’s. the • Digital computers can be programmed using both machine language and computer language.

Modern Digital Computers Some common current uses for computers: Personal Computers Consumer electronics interfaces Large Mainframe Computers Corporate and government accounting Computation Transaction processing Social information networking Production and trans-mission of electrical power Communication such as email High-capacity data processing Manufacturing processes

Modern Digital Computers Microsoft Windows and Apple Mac OS are two common operating system programs. They are used to control a computer’s hardware and software and designed to be “user-friendly. ” Programming that controls computers and their concurrent processes is called software. All physical components of computers and devices attached to them are called hardware.

Computer Architecture Computers store data and use computation that are in the form of a binary number system, using only digits 0 (no charge) and 1(some charge). They are organized into groups of eight binary numbers, called bytes(B), each one capable of representing 28 or 256 different numbers. • Longer numbers need more consecutive bytes • Fractions are represented by digital representation of fractional powers • Negative numbers shown by an auxiliary data bit

Computer Architecture All input from a keyboard or mouse, or any multimedia objects(video, audio) or colors – are coded/linked to combinations of numbers defined by certain standards: • American Standard Code for Information Interchange(ASCII) for keyboard functions and characters • Joint Photographic Experts Group(JPEG) for images • Moving Picture Experts Group (MPEG) for video

Computer Architecture Computers are rated according to computational speed and capacity. Speed: number of computational cycles the CPU can perform per second, in Hertz(Hz), Milli. Hertz(MHz), Giga. Hertz(GHz) Capacity: Memory expressed in multiples of number of bytes that can be stored: • Kilobytes(KB) – a few thousand bytes • Megabytes(MB) – millions of bytes • Gigabytes(GB) – billions of bytes • Terrabytes(TB) – trillions of bytes

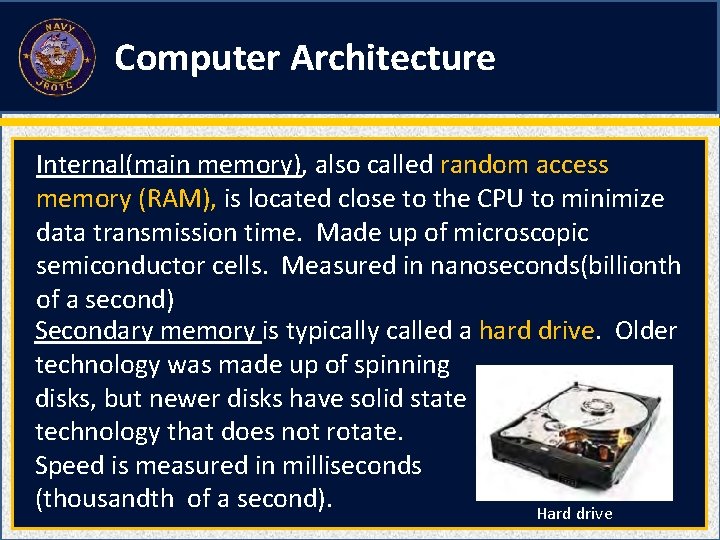
Computer Architecture Internal(main memory), also called random access memory (RAM), is located close to the CPU to minimize data transmission time. Made up of microscopic semiconductor cells. Measured in nanoseconds(billionth of a second) Secondary memory is typically called a hard drive. Older technology was made up of spinning disks, but newer disks have solid state technology that does not rotate. Speed is measured in milliseconds (thousandth of a second). Hard drive

Computer Architecture Computer peripherals examples: • Keyboard • Mouse • Monitor These use device drivers; software which manages the • Printer • Microphone interface between computer and that device. • Speakers • Camera • DVD drive

Computer Architecture In contrast to digital computers, analog computers can simulate mathematical calculations or physical behavior by analogous current or fluid flow through an array of components, gear rotations or scale manipulations. Digital computers are far superior. Analog computers were once widely used for: • Thermostats • Military aircraft bombsights • Process control • Large-caliber naval gunfire control • Torpedo solutions on surface warships and submarines

Computer Architecture In both military and civilian world, computers are extensively used for a wide variety of operations and functions. They are integral parts of almost every major shipboard system and enable instant communication. Computers are used for many applications in naval aircraft, cruise missiles and guided munitions of all kinds.

Computer chips today can now process approximately how many times faster than the first chips of the 1940's? A. B. C. D. Two times Ten times Hundreds of times Millions of times 1 1 (NS 2 -M 3 C 22 S 1: LQ 3)

Put the following in order from smallest to largest. (Using the letters at the bottom of the buttons, input the answers in the correct sequence, then push the ENTER button. ) A. B. C. D. Terabytes Gigabytes Megabytes Kilobytes (NS 2 -M 3 C 22 S 1: LQ 4)

The Internet 1950’s: First attempts to link computers together 1960’s: Birth of modern internet with work funded by Defense Advanced Research Projects Agency (DARPA) ARPANET: First computer network intended to facilitate communication and research among various government agencies and contractors Late 1969: Four host computers linked; grew to hundreds in just a few years

The Internet Though initially restricted to DOD, interest in internet grew among other users. By late 1970’s, network standards were developed and implemented, guided by DARPA. Electronic mail(e-mail) was standardized and led to establishment of Domain Names System(DNS) in 1983.

The Internet DNS is a standardized system of addresses wherein various types of information (domains) are associated with multilevel domain names assigned to entities such as: • Individual computers • Servers • Websites

The Internet Domain name - A human-friendly linkage to corresponding 32 -bit numerical Internet Protocol (IP) addresses needed by computers access a location in the network. Examples of top-level domain names in the U. S. : . gov. com. org. edu. mil. net It must be registered with a domain name registrar. Recently added: • 1400 new domain types in different languages • 250 top-level two-letter country codes Lower level domain names fall to the left of the “dot. ”

The Internet Mid 1980 s: Interlinked computer systems continued to grow. “Internet” became standard term, short for internetworking Late 1980’s: Worldwide Web(WWW) coined by contractor at the CERN atomic research facility in Switzerland. Became prefix for all internet addresses

The Internet Hypertext Transfer Protocol(HTTP) – A set of procedures used by internet This protocol defines how transmissions on the web are formatted and transmitted, and how servers respond to user commands. A prefix of https: indicates a secure website; http: indicates a website that is NOT secure.

Servers A server is a system of software run on one or more linked computers, to provide a resource to a user through a network and/or the internet. They may serve a small group of users or general public. Examples of servers: • Database • Gaming • Email • Offsite storage • Web

Servers Any computer can function as a server but most are large main- frame computers with faster CPUs, huge memory capacity, multiple hard drives and redundant power supplies. Servers are accessed by using a numerical IP address.

What does HTTP stand for? A. B. C. D. Hyper Text Transfer Protocol Hyper Transfer Text Protocol Hypertest Transfer Protocol Hypertext Transfer Total Portal 1 1 (NS 2 -M 3 C 22 S 1: LQ 5)

Which of the following would be a secure website? (Input all the correct answers, then push the ENTER button. ) A. B. C. D. http: //www. findme. gov https: //www. google. com https: //www. uc. edu http: //www. navy. org 1 1 (NS 2 -M 3 C 22 S 1: LQ 6)

Internet Features Internet Milestone #1 - Browser: Late 1980’s: Development of first browser. Major milestone for locating information on web. 1993: Greatly improved browser developed at University of Illinois; basis for more sophisticated browsers and modern search engines developed in recent years.

Internet Features Internet Milestone #2 - ISPs: Formation of commercial companies called Internet Service Providers(ISPs) in mid 1990’s, facilitating consumer access to internet • Initially via standard phone lines • Then high speed service via phone, tv cable or broadband wireless transmission • ISP’s assigned email addresses to their users and hosted email accounts • ISPs supported use of browsers and other services

Internet Features Internet Milestone #3 – Cloud computing: • Recent milestone is increasing use of cloud computing. Data and application programming stored at a remote location (the “cloud”) instead of user’s device • Increased capabilities of those devices, decreasing cost; making better, more efficient use of available internet resources

Internet Features Common means of connecting to internet: • Personal computers • Cell phones • Tablets Methods of connection to internet: 1. Traditional phone lines(dial-up and DSL) 2. Dedicated hardline wires(Ethernet) 3. TV coaxial cable service 4. Wireless radio(Wi. Fi) transmission *All above are broadband transmission, except Dial-up

Internet Features Broadband = simultaneous use of a broad range of carrier wave frequencies with bandwidths of 6 MHz. Allows at least 1. 5 Megabits (1. 5 millions bits) of information to be transmitted each second. In contrast… Narrowband uses single carrier-wave frequencies with a bandwidth of only 3 k. Hz. Allows a maximum of 56 kilobits, and 56, 000 bits per second.

Internet Features Fourth Generation (4 G) Wireless Fidelity (Wi. Fi) has peak download rates as high as 1 gigabit (1 billion bits) per second. This is 18, 000 times more bits per second than traditional voice phone service. Long Term Evolution (LTE) 4 G networks offer even faster transmission with new digital signal processing(DSP) technology.

Internet Features The internet has no formal international governing or regulating body, but all networks are required to confirm to established IP address and domain-name systems. An estimated 1/3 of the world’s current population uses the internet.

Internet Features Satellite-based communication systems facilitate internet use worldwide by military personnel on land, sea or in the air. Internet links were even installed onboard the International Space Station in 2010.

Internet Features Information technology (IT) refers to anything related to computing or networking technology. IT departments are an important part of any corporate or government organization.

Cyberspace and Security Cyberspace is the sum total of all the world’s computers, servers and networks interconnecting them. Security of cyberspace has become a huge and very sensitive issue, as “hackers” engage in illegal activity via the internet worldwide.

Cyberspace and Security Hacker activity might include: • Breaking into financial networks to steal personal information(identify theft) or divert funds for their own gain • Breaking into corporate, industrial or government systems to conduct espionage(spying) • Infecting various systems with viruses that impair or destroy systems or computers

Cyberspace and Security An attempt to damage computer systems by extremists or terrorists would be considered cyber terrorism. If these actions are done by foreign governments or other foreign entities on a large scale, they are called cyber warfare.

Cyberspace and Security Countermeasures known as cyber security, are taken to guard against cyber crimes, including: • Data encryption • Antivirus programs • Firewalling Federal, state and local government , as well as private organizations provide these security services, including the U. S. Cyber Command for military applications, and the Department of Homeland Security.

Identify and describe the major advances in computer technology that you think will be in place by the year 2100. 1. 2. 3. Note to Instructors: Click the Show/Hide Response Display Button

In what decade was the first internet browser developed? (Input the two numbers of the decade (ex. 50), then press enter. ) Note to Instructors: Click the Show/Hide Response Display Button (NS 2 -M 3 C 22 S 1: LQ 7)

Which of the following would be an example of cyber terrorism? A. A hacker starts a virus that spreads by inserting copies of itself into other executable code or documents damaging computers hardware. B. A computer hacker associated with the White Supremacist movement temporarily disables an ISP and damages part of the record keeping system. C. A computer programmer finds his way into a college university’s database, retrieving personal information. D. A hacker scans computer addresses of financial companies until he finds vulnerabilities and proceeds to compromise financial information. 1 1 (NS 2 -M 3 C 22 S 1: LQ 8)

Questions?