Module 20 Module 20 1 Module 20 2

























- Slides: 39



Module 20:軟硬體正規驗證 • Module 20 -1:邏輯分析 • Module 20 -2: Temporal Logic and Model Checking 系統安全 20 -3






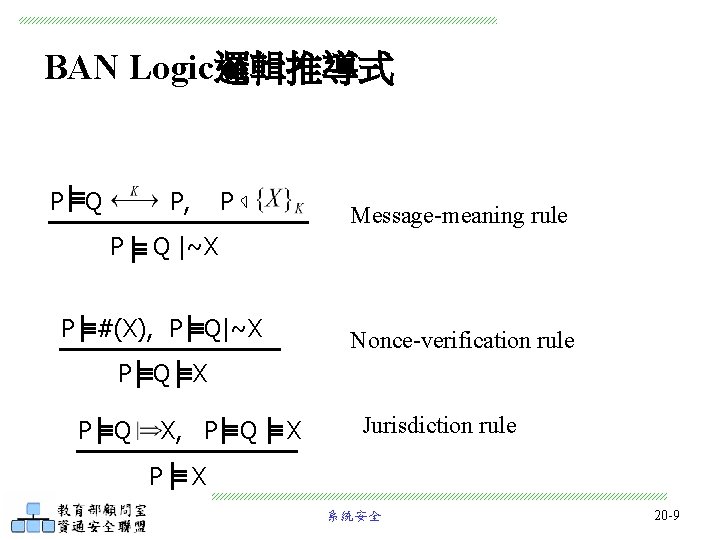
BAN Logic邏輯推導式 P Q P, P P Message-meaning rule Q |~X P #(X), P Q|~X Nonce-verification rule P Q X, P Q P X Jurisdiction rule X 系統安全 20 -9

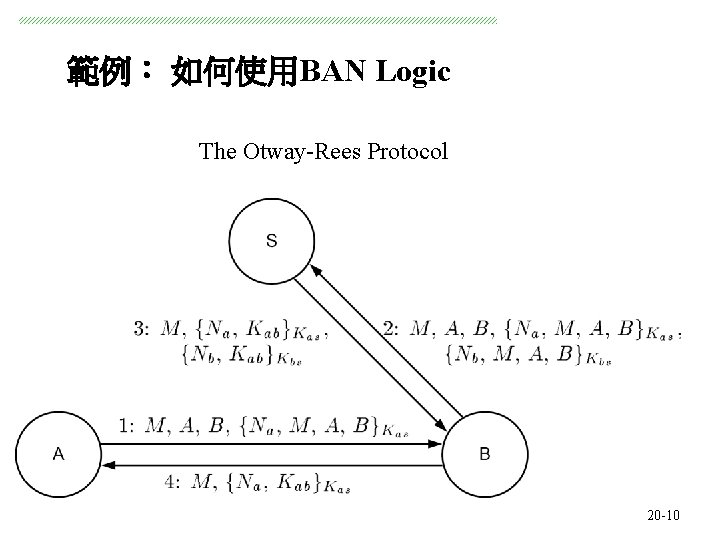
範例: 如何使用BAN Logic The Otway-Rees Protocol 系統安全 20 -10

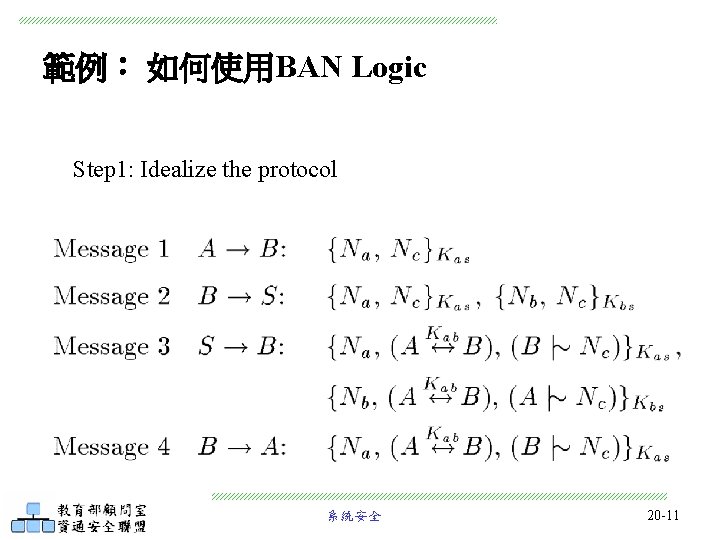
範例: 如何使用BAN Logic Step 1: Idealize the protocol 系統安全 20 -11

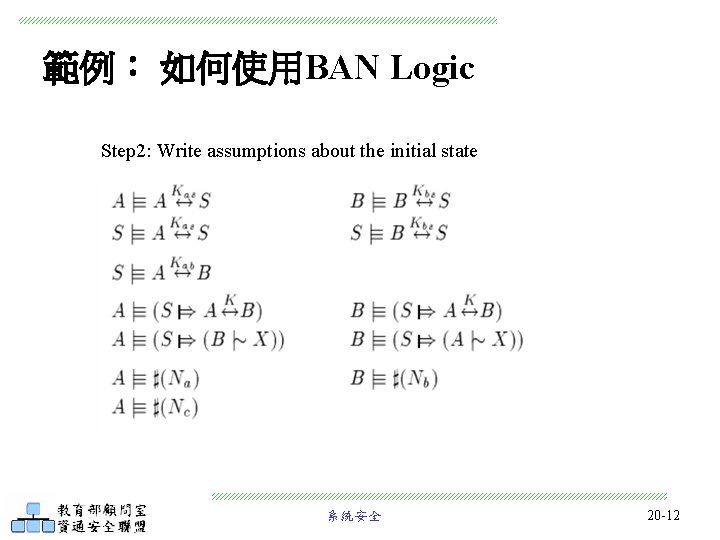
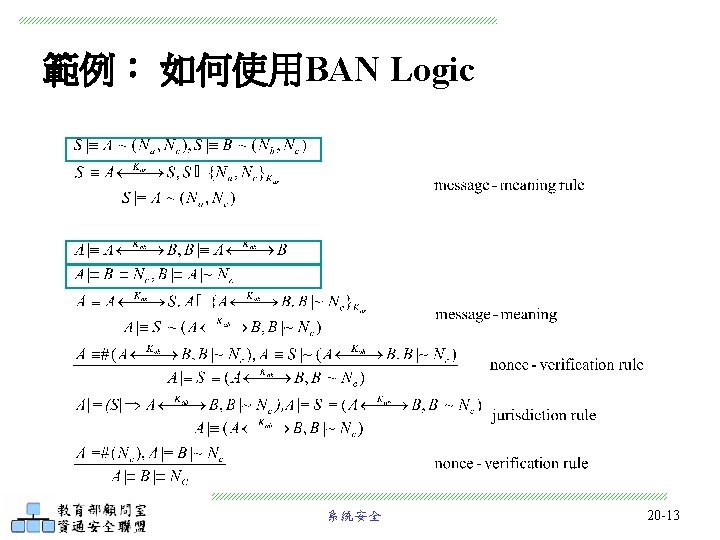
範例: 如何使用BAN Logic Step 2: Write assumptions about the initial state 系統安全 20 -12




GNY Logic介紹 GNY邏輯推導式 EX 1: • A principal is told a formula encrypted with a key. • He processes the key. • He has also been told the decrypted contents of the formula. 系統安全 20 -16


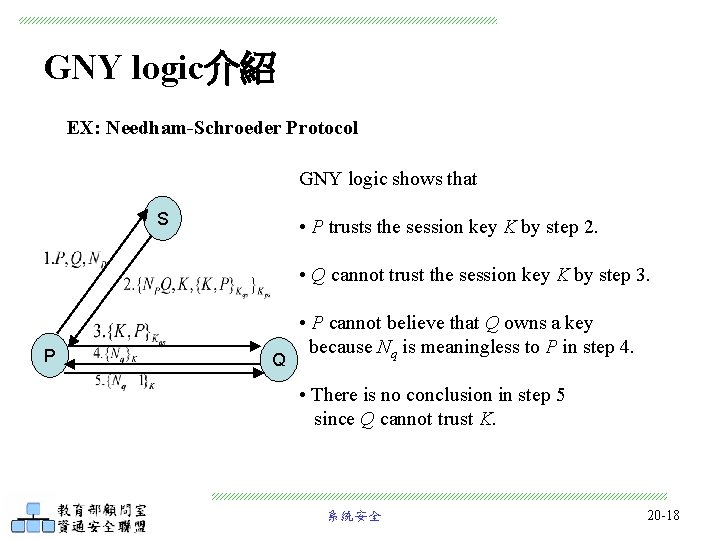
GNY logic介紹 EX: Needham-Schroeder Protocol GNY logic shows that S • P trusts the session key K by step 2. • Q cannot trust the session key K by step 3. P Q • P cannot believe that Q owns a key because Nq is meaningless to P in step 4. • There is no conclusion in step 5 since Q cannot trust K. 系統安全 20 -18

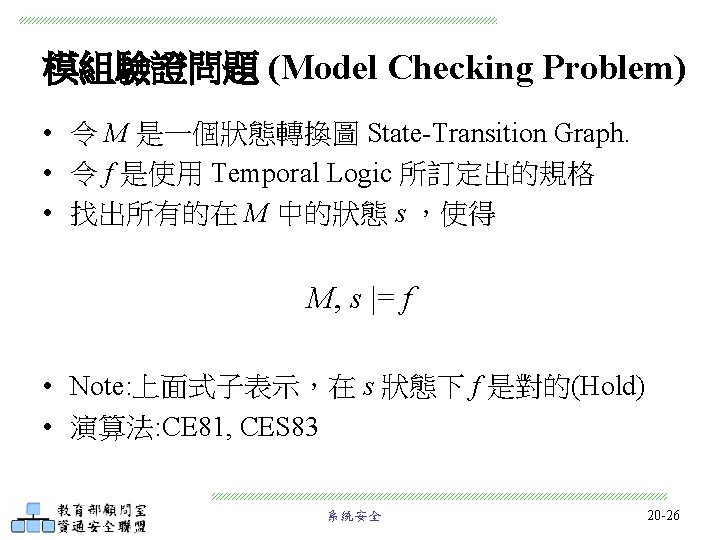
Module 20 -2: Temporal Logic and Model Checking 系統安全 20 -

Temporal Logic and Model Checking • Model Checking 在安全協定上的應用 • Model Checking 在網路安全上的應用 系統安全 20 -20




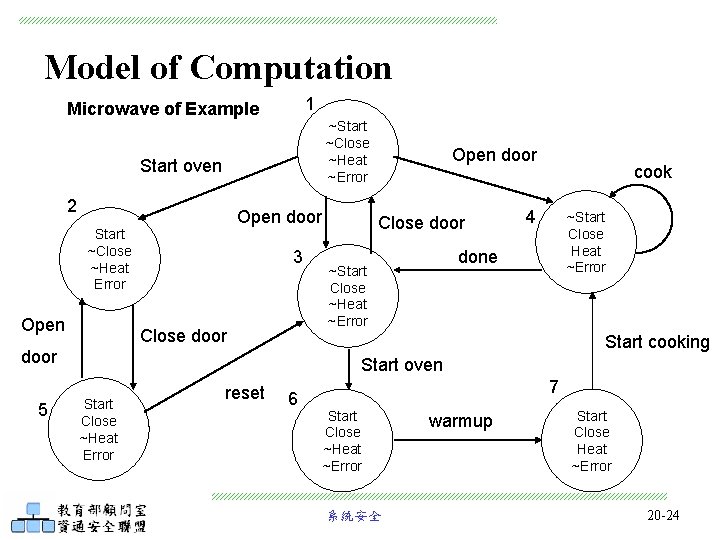
Model of Computation 1 Microwave of Example ~Start ~Close ~Heat ~Error Start oven 2 Open door Start ~Close ~Heat Error Open 3 Close door cook 4 ~Start Close Heat ~Error done ~Start Close ~Heat ~Error Start cooking door 5 Open door Start oven Start Close ~Heat Error reset 6 7 Start Close ~Heat ~Error 系統安全 warmup Start Close Heat ~Error 20 -24

Temporal Logic • • 利用 Temporal Logic 來描述系統的規格 微波爐不會加熱(Heat)一直到門被關上(Close) Not heat_up holds until door_closed ~heat U close 系統安全 20 -25



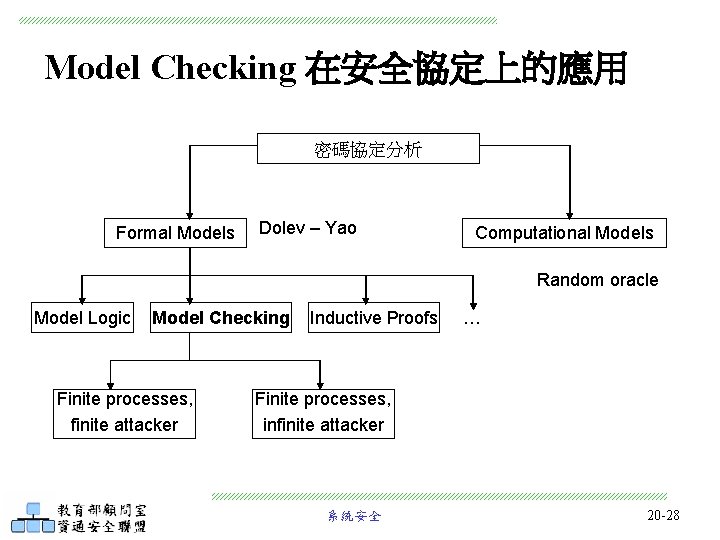
Model Checking 在安全協定上的應用 密碼協定分析 Formal Models Dolev – Yao Computational Models Random oracle Model Logic Model Checking Finite processes, finite attacker Inductive Proofs … Finite processes, infinite attacker 系統安全 20 -28



模組化密碼協定 • 範例 – A B: A. B. {Na. A}KB – B A: B. A. {Na. Nb}KA – A B: A. B. {Nb}KB • 將上例轉換為文字型式: – send {A, B, encrypt {KB , pair {Na. A}}} – send {B, A, encrypt {KA , pair {Na. Nb}}} – send {A, B, encrypt {KB , Nb}} 系統安全 20 -31








參考資料 • M. Burrows, M. Abadi, and R. Needham, “A logic of authentication, ” ACM Transactions on Computer Systems, Vol. 23, No. 5, pp. 1 -13, 1989. • L. Gong, Roger Needham, and Raphael Yahalom, “Reasoning about belief in cryptographic protocols, ” Proceedings of the 1990 IEEE Computer Society Symposim on Research in Security and Privacy, pp. 234 -246, 1990. • Edmund M. Clarke, Jr. , Orna Grumberg, and Doron A. Peled. Model Checking. The MIT Press. 1999 • R. Ritchey and P. Ammann. Using Model Checking to Analyze Network Vulnerabilities. Proceeding of IEEE symposium on Security and Privacy. 2001. • http: //www. cs. cmu. edu/afs/cs/usr/wing/www/publications/inde x. html 系統安全 20 -39