MODULE 14 SECURING THE STORAGE INFRASTRUCTURE EMC Proven











- Slides: 42

MODULE – 14 SECURING THE STORAGE INFRASTRUCTURE EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 1

Module 14: Securing the Storage Infrastructure Upon completion of this module, you should be able to: • Describe information security framework • Explain various storage security domains • Discuss security implementations in SAN, NAS, and IP SAN • Explain security in virtualized and cloud environments EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 2

Module 14: Securing the Storage Infrastructure Lesson 1: Information Security Framework During this lesson the following topics are covered: • Building information security framework • Risk triad • Security elements • Security controls EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 3

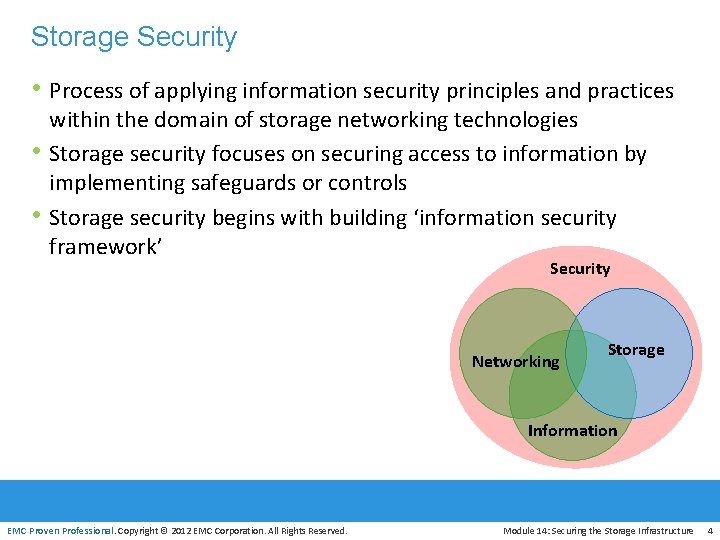
Storage Security • Process of applying information security principles and practices • • within the domain of storage networking technologies Storage security focuses on securing access to information by implementing safeguards or controls Storage security begins with building ‘information security framework’ Security Networking Storage Information EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 4

Information Security Framework • A systematic way of defining security requirements • Framework should incorporate: 4 Anticipated security attacks 8 Actions that compromise the security of information 4 Security measures 8 Control designed to protect from these security attacks EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 5

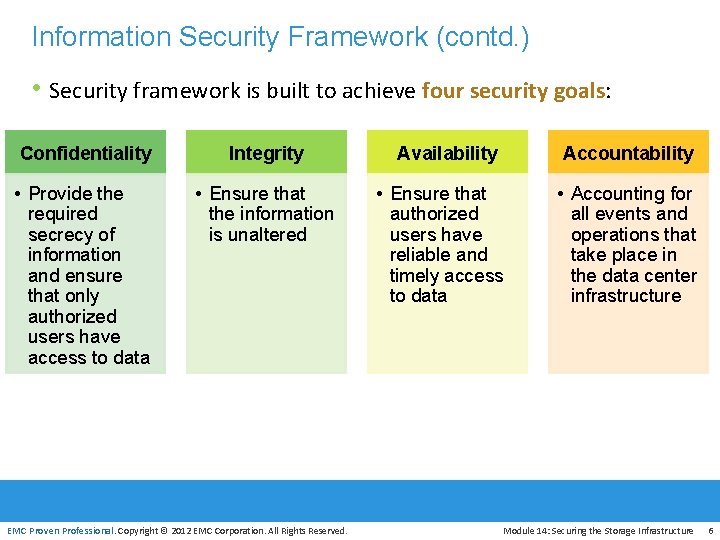
Information Security Framework (contd. ) • Security framework is built to achieve four security goals: Confidentiality Integrity • Provide the required secrecy of information and ensure that only authorized users have access to data • Ensure that the information is unaltered EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Availability Accountability • Ensure that authorized users have reliable and timely access to data • Accounting for all events and operations that take place in the data center infrastructure Module 14: Securing the Storage Infrastructure 6

Risk Triad • Securing infrastructure begins with understanding the risk • Defines risk in terms of threats, assets, and vulnerabilities Risk Triad Wish to abuse and/or may damage Threat Agent Give rise to Threats Threat Risk Assets That exploit Vulnerabilities Leading to Risk To To reduce Countermeasure Asset EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Impose Owner Value Module 14: Securing the Storage Infrastructure 7

Assets • “Information” – the most important asset for any organization 4 Other assets include hardware, software, and network infrastructure • Protecting assets is the primary concern • Security considerations 4 Must provide easy access to assets for authorized users 4 Cost of securing the assets should be a fraction of the value of the assets 4 Make it difficult for potential attackers to access and compromise the assets 8 Should cost heavily to a potential attacker in terms of money, effort, and time EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 8

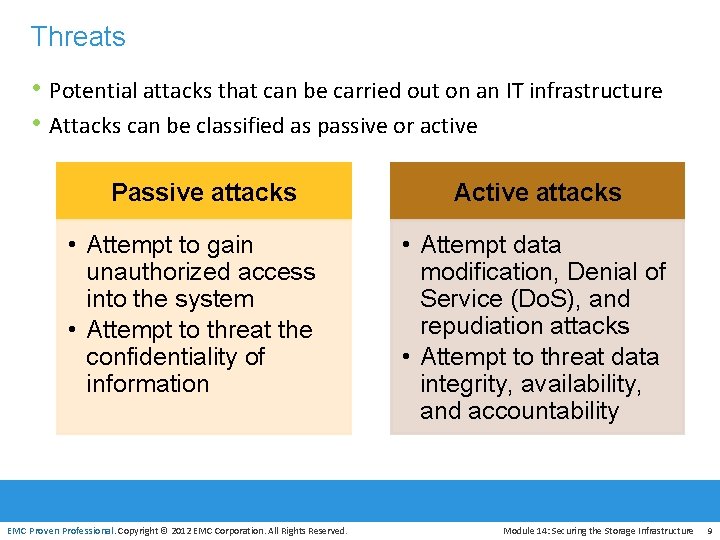
Threats • Potential attacks that can be carried out on an IT infrastructure • Attacks can be classified as passive or active Passive attacks • Attempt to gain unauthorized access into the system • Attempt to threat the confidentiality of information EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Active attacks • Attempt data modification, Denial of Service (Do. S), and repudiation attacks • Attempt to threat data integrity, availability, and accountability Module 14: Securing the Storage Infrastructure 9

Vulnerabilities • Paths that provide access to information are vulnerable to • • potential attacks Requires implementation of “defense in depth” Factors to consider when assessing the extent to which an environment is vulnerable: 4 Attack surface – various entry points that attacker can use to launch attack 4 Attack vectors – steps to complete attack 4 Work factor – amount of time and effort required to exploit attack vector • Managing vulnerabilities 4 Minimize the attack surface and maximize the work factor 4 Install controls (or countermeasures) EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 10

Security Controls • Reduces the impact of vulnerabilities • Any control measure should involve all the three aspects of infrastructure 4 People, process, and technology • Controls can be technical or non-technical 4 Technical: antivirus, firewalls, and intrusion detection system 4 Non-technical: administrative policies and physical controls • Controls are categorized as: 4 Preventive: prevent an attack from being exploited 4 Detective: detect whether an attack is in progress 4 Corrective: after an attack is discovered, reduce the effect of an attack EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 11

Module 14: Securing the Storage Infrastructure Lesson 2: Storage Security Domains During this lesson the following topics are covered: • Storage security domains • Security threats in each domain • Controls applied to reduce the risk in each domain EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 12

Storage Security Domains Application Access Management Access Backup, Replication, and Archive Storage Network Secondary Storage Data Storage To identify threats that apply to a storage network, access paths to data storage can be categorized into: • Application Access • Management Access • Backup, Replication and Archive EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 13

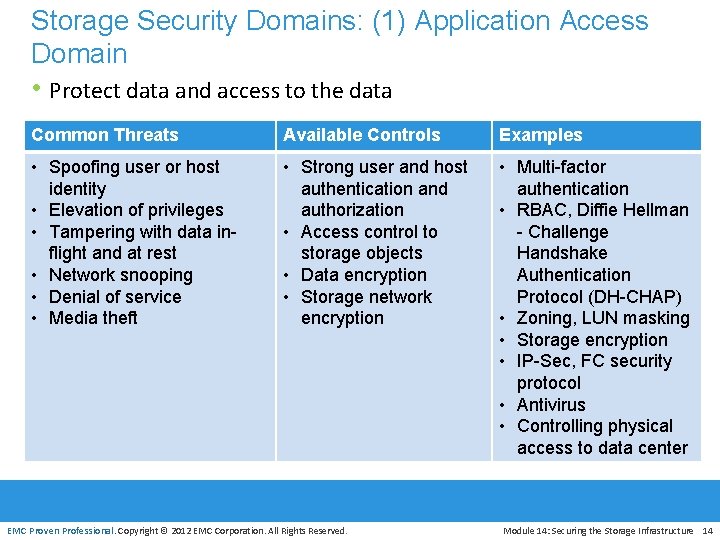
Storage Security Domains: (1) Application Access Domain • Protect data and access to the data Common Threats Available Controls Examples • Spoofing user or host identity • Elevation of privileges • Tampering with data inflight and at rest • Network snooping • Denial of service • Media theft • Strong user and host authentication and authorization • Access control to storage objects • Data encryption • Storage network encryption • Multi-factor authentication • RBAC, Diffie Hellman - Challenge Handshake Authentication Protocol (DH-CHAP) • Zoning, LUN masking • Storage encryption • IP-Sec, FC security protocol • Antivirus • Controlling physical access to data center EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 14

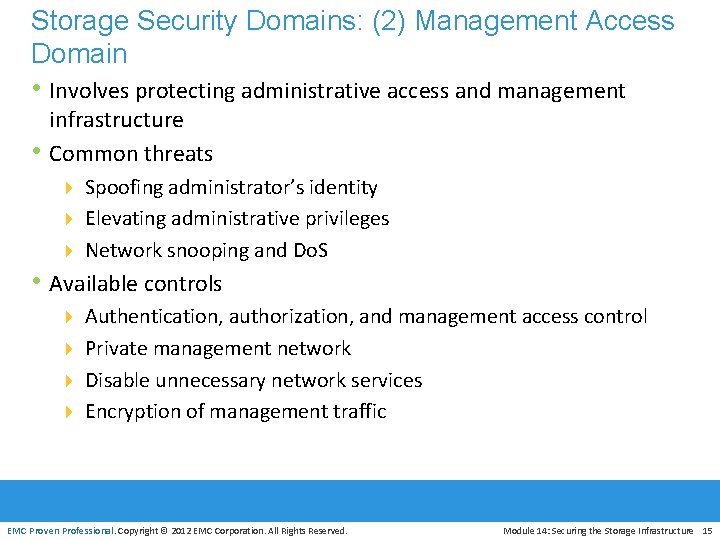
Storage Security Domains: (2) Management Access Domain • Involves protecting administrative access and management • infrastructure Common threats 4 Spoofing administrator’s identity 4 Elevating administrative privileges 4 Network snooping and Do. S • Available controls 4 Authentication, authorization, and management access control 4 Private management network 4 Disable unnecessary network services 4 Encryption of management traffic EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 15

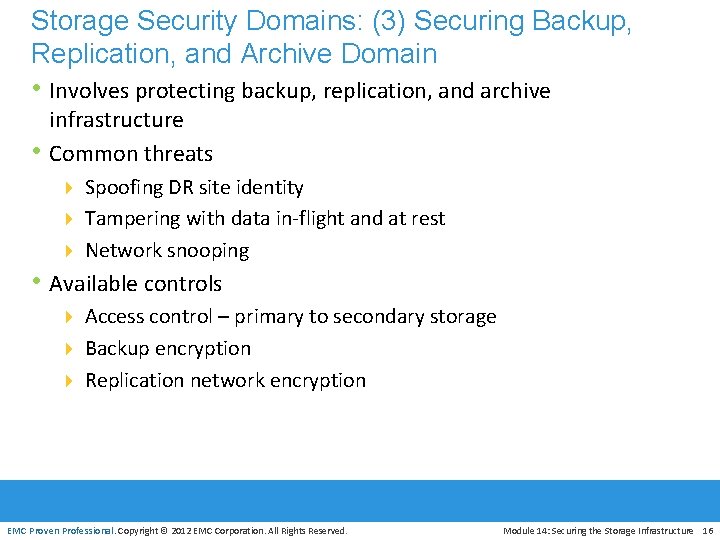
Storage Security Domains: (3) Securing Backup, Replication, and Archive Domain • Involves protecting backup, replication, and archive • infrastructure Common threats 4 Spoofing DR site identity 4 Tampering with data in-flight and at rest 4 Network snooping • Available controls 4 Access control – primary to secondary storage 4 Backup encryption 4 Replication network encryption EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 16

Module 14: Securing the Storage Infrastructure Lesson 3: Security Implementations in Storage Networking During this lesson the following topics are covered: • SAN security implementations • NAS security implementations • IP SAN security implementations EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 17

Security Implementation in SAN • Common SAN security mechanisms are: 4 LUN masking and zoning 4 Securing FC switch ports 4 Switch-wide and fabric-wide access control 4 Logical partitioning of a fabric: VSAN EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 18

Securing FC Switch Ports • Port binding 4 Restricts devices that can attach to a particular switch port 8 Allows only the corresponding switch port to connect to a node for fabric access • Port lockdown and port lockout 4 Restricts a switch port’s type of initialization • Persistent port disable 4 Prevents a switch port from being enabled even after a switch reboot EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 19

Switch-wide and Fabric-wide Access Control • Access control lists (ACLs) 4 Include device connection and switch connection control policies 8 Device connection control policy specifies which HBAs, storage ports can be connected to a particular switch 8 Switch connection control policy prevents unauthorized switches to join a particular switch • Fabric Binding 4 Prevents unauthorized switch from joining a fabric • Role-based access control (RBAC) 4 Enables assigning roles to users that explicitly specify access rights EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 20

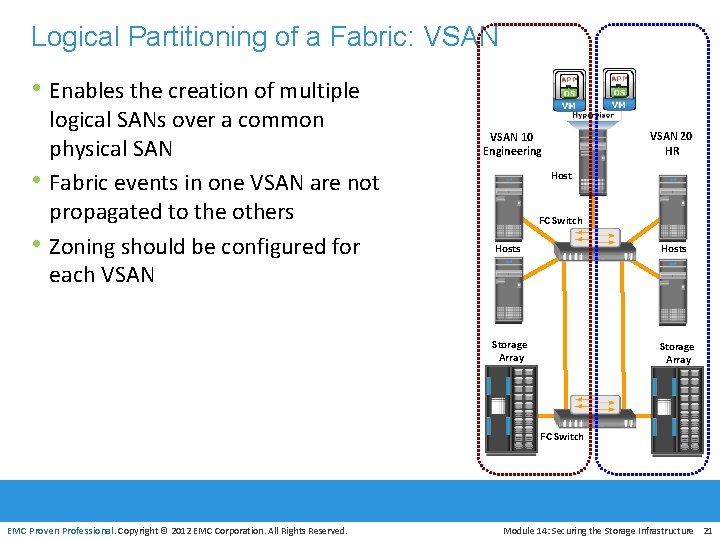
Logical Partitioning of a Fabric: VSAN • Enables the creation of multiple • • logical SANs over a common physical SAN Fabric events in one VSAN are not propagated to the others Zoning should be configured for each VSAN 20 HR VSAN 10 Engineering Host FC Switch Hosts Storage Array FC Switch EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 21

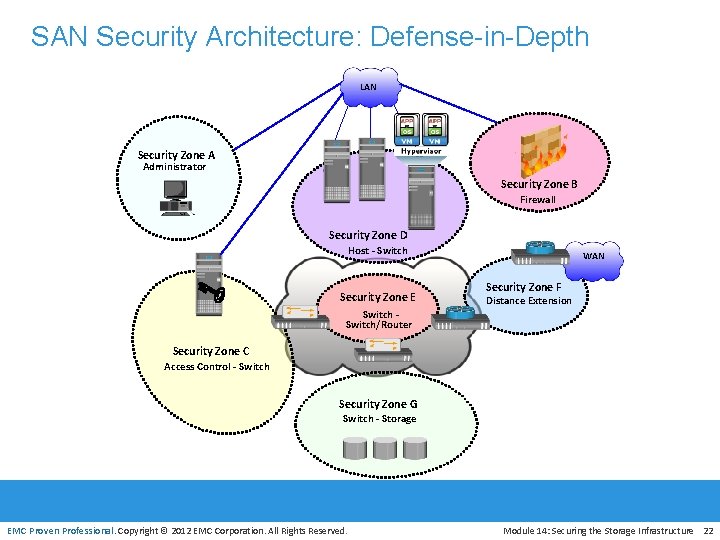
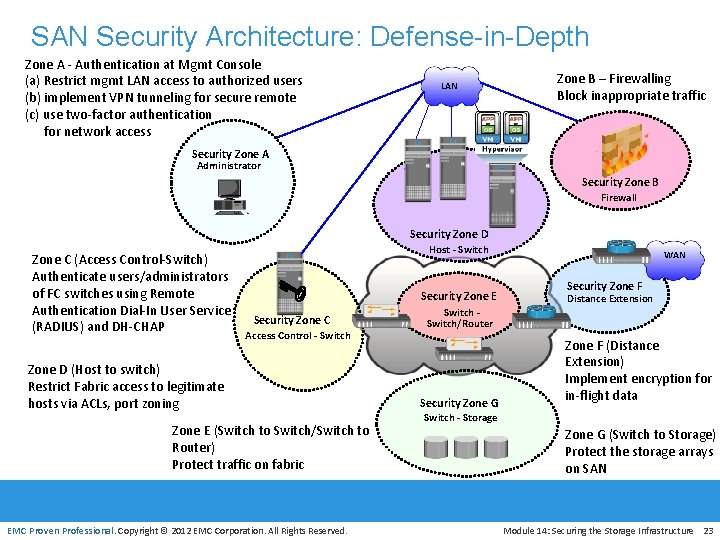
SAN Security Architecture: Defense-in-Depth LAN Security Zone A Administrator Security Zone B Firewall Security Zone D Host - Switch Security Zone E WAN Security Zone F Distance Extension Switch/Router Security Zone C Access Control - Switch Security Zone G Switch - Storage EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 22

SAN Security Architecture: Defense-in-Depth Zone A - Authentication at Mgmt Console (a) Restrict mgmt LAN access to authorized users (b) implement VPN tunneling for secure remote (c) use two-factor authentication for network access LAN Zone B – Firewalling Block inappropriate traffic Security Zone A Administrator Security Zone B Firewall Security Zone D Zone C (Access Control-Switch) Authenticate users/administrators of FC switches using Remote Authentication Dial-In User Service (RADIUS) and DH-CHAP Host - Switch Security Zone E Security Zone C Access Control - Switch Zone D (Host to switch) Restrict Fabric access to legitimate hosts via ACLs, port zoning Zone E (Switch to Switch/Switch to Router) Protect traffic on fabric EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. WAN Security Zone F Distance Extension Switch/Router Security Zone G Zone F (Distance Extension) Implement encryption for in-flight data Switch - Storage Zone G (Switch to Storage) Protect the storage arrays on SAN Module 14: Securing the Storage Infrastructure 23

Security Implementation in NAS • Permissions and ACLs 4 Protection to NAS resources by restricting access • Other authentication and authorization mechanisms 4 Kerberos and Directory services 8 Implemented to verify the identity of network users and define their privileges 4 Firewalls 8 To protect the storage infrastructure from unauthorized access and malicious attacks EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 24

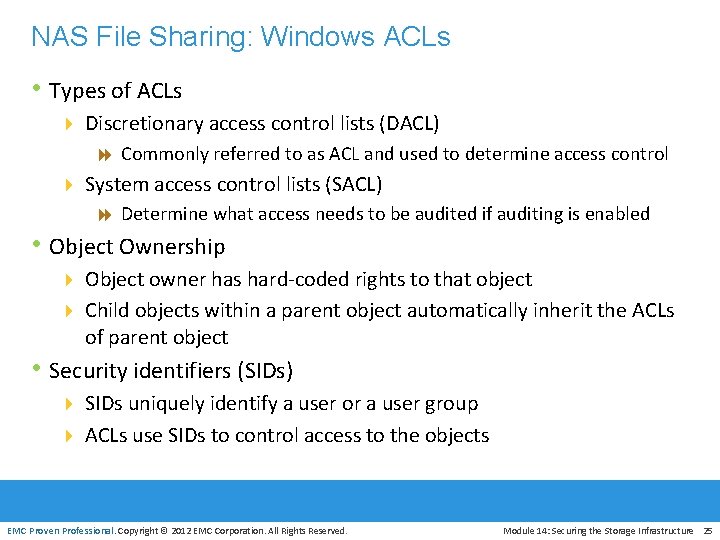
NAS File Sharing: Windows ACLs • Types of ACLs 4 Discretionary access control lists (DACL) 8 Commonly referred to as ACL and used to determine access control 4 System access control lists (SACL) 8 Determine what access needs to be audited if auditing is enabled • Object Ownership 4 Object owner has hard-coded rights to that object 4 Child objects within a parent object automatically inherit the ACLs of parent object • Security identifiers (SIDs) 4 SIDs uniquely identify a user or a user group 4 ACLs use SIDs to control access to the objects EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 25

NAS File Sharing: UNIX Permissions • UNIX permissions specify what can be done to a file and by whom 4 Common permissions: Read/Write/Execute • Every file and directory (folder) has three ownership relations: 4 Rights for the file owner 4 Rights for the group the user belong to 4 Rights for all other users EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 26

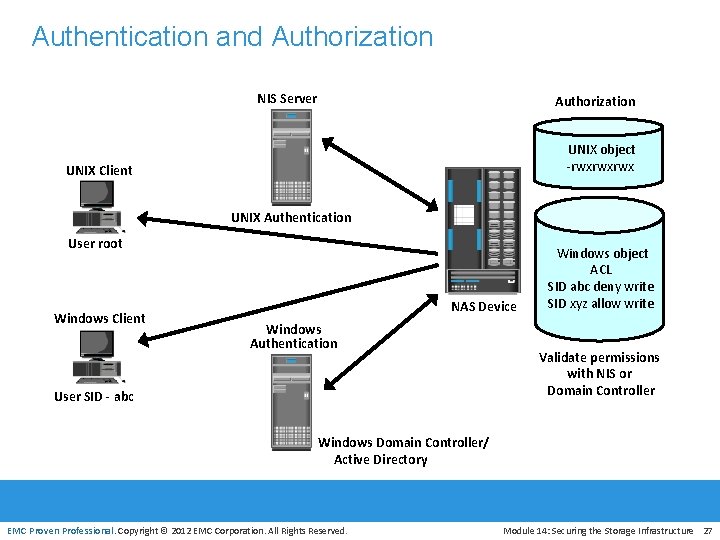
Authentication and Authorization NIS Server Authorization UNIX object -rwxrwxrwx UNIX Client UNIX Authentication User root Windows Client NAS Device Windows Authentication User SID - abc Windows object ACL SID abc deny write SID xyz allow write Validate permissions with NIS or Domain Controller Windows Domain Controller/ Active Directory EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 27

Kerberos – Network Authentication Protocol • Uses secret-key cryptography • A client can prove its identity to a server (and vice versa) across • an insecure network connection Kerberos client 4 An entity that gets a service ticket for a Kerberos service • Kerberos server 4 Refers to the Key Distribution Center (KDC) 4 Implements the Authentication Service (AS) and the Ticket Granting Service (TGS) EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 28

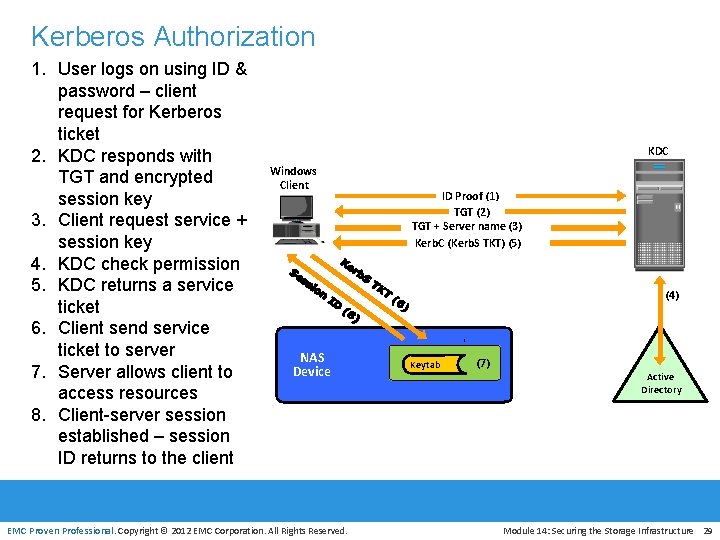
Kerberos Authorization 1. User logs on using ID & password – client request for Kerberos ticket 2. KDC responds with TGT and encrypted session key 3. Client request service + session key 4. KDC check permission 5. KDC returns a service ticket 6. Client send service ticket to server 7. Server allows client to access resources 8. Client-server session established – session ID returns to the client KDC Windows Client ID Proof (1) TGT (2) TGT + Server name (3) Kerb. C (Kerb. S TKT) (5) (4) NAS Device EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Keytab (7) Active Directory Module 14: Securing the Storage Infrastructure 29

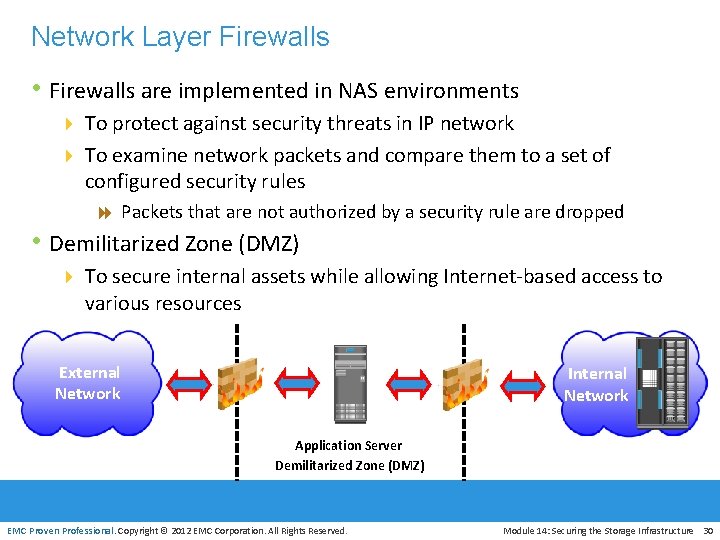
Network Layer Firewalls • Firewalls are implemented in NAS environments 4 To protect against security threats in IP network 4 To examine network packets and compare them to a set of configured security rules 8 Packets that are not authorized by a security rule are dropped • Demilitarized Zone (DMZ) 4 To secure internal assets while allowing Internet-based access to various resources External Network Internal Network Application Server Demilitarized Zone (DMZ) EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 30

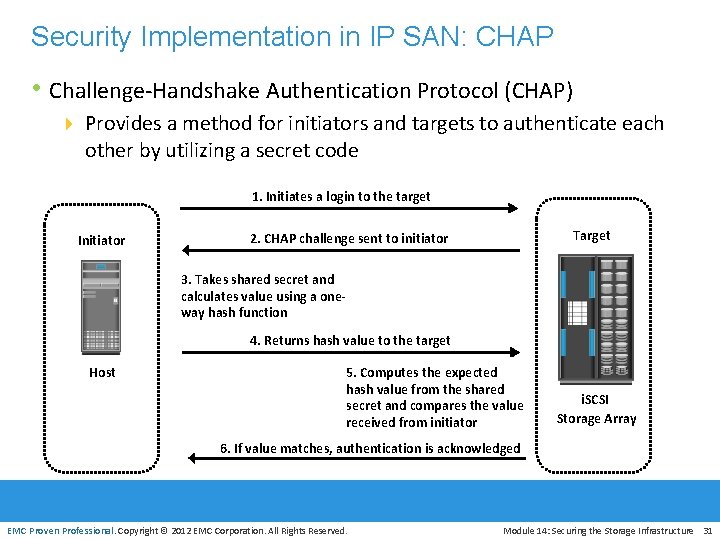
Security Implementation in IP SAN: CHAP • Challenge-Handshake Authentication Protocol (CHAP) 4 Provides a method for initiators and targets to authenticate each other by utilizing a secret code 1. Initiates a login to the target Initiator Target 2. CHAP challenge sent to initiator 3. Takes shared secret and calculates value using a oneway hash function 4. Returns hash value to the target Host 5. Computes the expected hash value from the shared secret and compares the value received from initiator i. SCSI Storage Array 6. If value matches, authentication is acknowledged EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 31

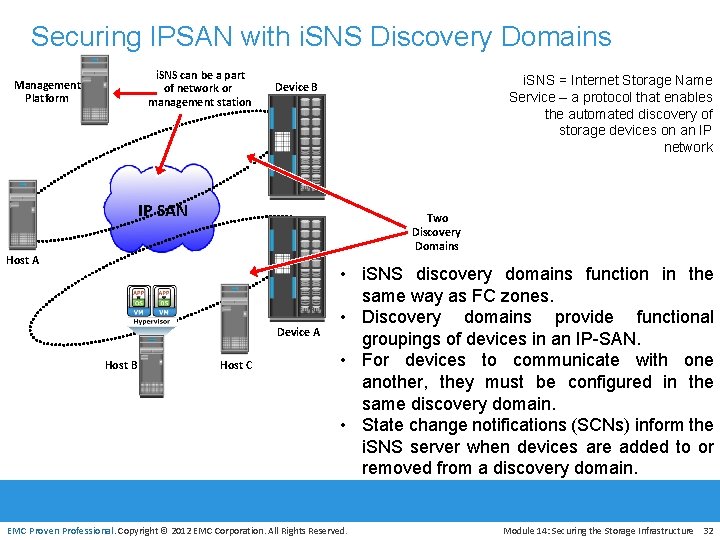
Securing IPSAN with i. SNS Discovery Domains i. SNS can be a part of network or management station Management Platform i. SNS = Internet Storage Name Service – a protocol that enables the automated discovery of storage devices on an IP network Device B IP SAN Two Discovery Domains Host A Device A Host B Host C • i. SNS discovery domains function in the same way as FC zones. • Discovery domains provide functional groupings of devices in an IP-SAN. • For devices to communicate with one another, they must be configured in the same discovery domain. • State change notifications (SCNs) inform the i. SNS server when devices are added to or removed from a discovery domain. EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 32

Module 14: Securing the Storage Infrastructure Lesson 4: Security in Virtualized and Cloud Environments During this lesson the following topics are covered: • Security concerns • Security measures EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 33

Security in Virtualized and Cloud Environments • These environments have additional threats due to multitenancy • • and lack of control over the cloud resources Virtualization-specific security concerns are common for all cloud models In public clouds, there additional security concerns, which demand specific countermeasures 4 Clients have less control to enforce security measures in public clouds 4 Difficult for cloud service provider(CSP) to meet the security needs of all the clients EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 34

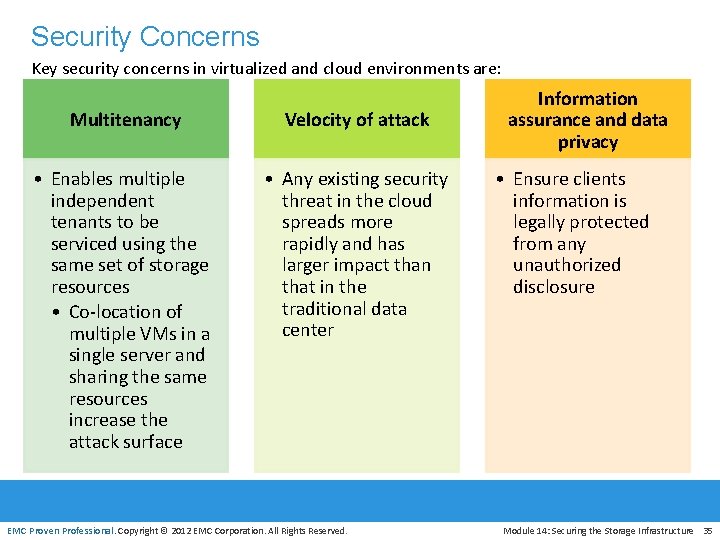
Security Concerns Key security concerns in virtualized and cloud environments are: Multitenancy Velocity of attack • Enables multiple independent tenants to be serviced using the same set of storage resources • Co-location of multiple VMs in a single server and sharing the same resources increase the attack surface • Any existing security threat in the cloud spreads more rapidly and has larger impact than that in the traditional data center EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Information assurance and data privacy • Ensure clients information is legally protected from any unauthorized disclosure Module 14: Securing the Storage Infrastructure 35

Security Measures Computer Network Storage EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 36

Security Measures (contd. ) • Securing computer: Enforce the security of physical server, VMs, and hypervisor 8 Physical server: user authentication and authorization mechanism 8 Hypervisor: security-critical hypervisor updates should be installed regularly • Securing network: To minimize vulnerabilities at the network layer: firewall, intrusion detection, DMZ, encryption. 8 Virtual firewall § Provides packet filtering and monitoring of the VM-to-VM traffic 8 DMZ and data encryption EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 37

Security Measures (contd. ) • Securing storage: Adequate security measures at computer & network levels helps to ensure storage security 8 Access control: to regulate which users and processes access data on storage system 8 Data encryption: encrypt backup, store encryption keys separately from data 8 Use separate LUNs for VM configuration files and VM data 8 Segregate VM traffic from management traffic EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 38

Module 14: Securing the Storage Infrastructure Concept in Practice • RSA security products • VMware v. Shield EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 39

RSA Security Products • RSA Secure. ID 4 Provides two-factor authentication 8 Based on something a user knows (a password or PIN) and something a user has (an authenticator device) 8 Authenticator device automatically changes passwords every 60 seconds • RSA Identity and Access Management 4 Provides identity, security, and access-control management for physical, virtual, and cloud-based environments • RSA Data Protection Manager 4 Enables deployment of encryption, tokenization, and enterprise key management EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 40

VMware v. Shield • VMware v. Shield family includes three products 4 v. Shield App 8 Hypervisor-based application-aware firewall solution 8 Observes network activity between virtual machines 4 v. Shield Edge 8 Provides comprehensive perimeter network security 8 Deployed as a virtual appliance and serves as a network security gateway for all the hosts 8 Provides many services including firewall, VPN, and DHCP 4 v. Shield Endpoint 8 Consists of a hardened special security VM with a third party antivirus software EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 41

Module 14: Summary Key points covered in this module: • Information security framework • Storage security domains • Controls that can be deployed against identified threats in each domain • SAN security architecture • Protection mechanisms in SAN, NAS, and IP SAN environments • Security in virtualized and cloud environments EMC Proven Professional. Copyright © 2012 EMC Corporation. All Rights Reserved. Module 14: Securing the Storage Infrastructure 42