Module 11 Designing Security for Network Perimeters Overview






- Slides: 13

Module 11: Designing Security for Network Perimeters

Overview Creating a Security Plan for the Perimeter of a Network Creating a Design for Security of Network Perimeters

Lesson 1: Creating a Security Plan for the Perimeter of a Network MSF and Security of Network Perimeters Defense in Depth and Security of Network Perimeters Resources to Protect with Network Perimeters Security STRIDE Threat Model and Security of Network Perimeters

MSF and Security of Network Perimeters The MSFwhich envisioning and planning Decide locations your plan willphases help to help you to: protect Ensure that appropriate countermeasures are applied Identify your perimeter points. These can include: Direct Internet connections Envisio n Dedicated WAN links Perimeter Networks 5 Plan VPN client computers Applications Wireless connections 4 3

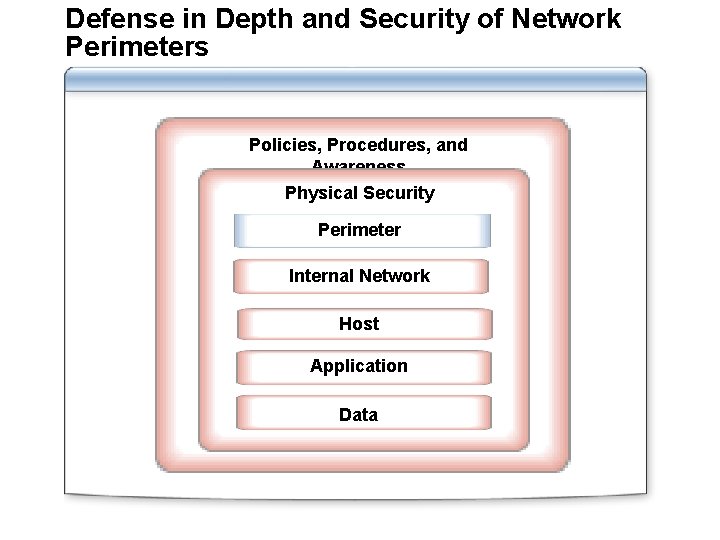
Defense in Depth and Security of Network Perimeters Policies, Procedures, and Awareness Physical Security Perimeter Internal Network Host Application Data

Resources to Protect with Network Perimeters Security Attacker External Internal Threat Information disclosure Denial of service Example An attacker runs a series of port scans on a network and creates a network diagram and vulnerability list. The attacker uses this information to systematically attack the network. An employee opens an e-mail from an external Web-based e-mail account that contains a new worm virus. The virus infects the internal network from inside the perimeter.

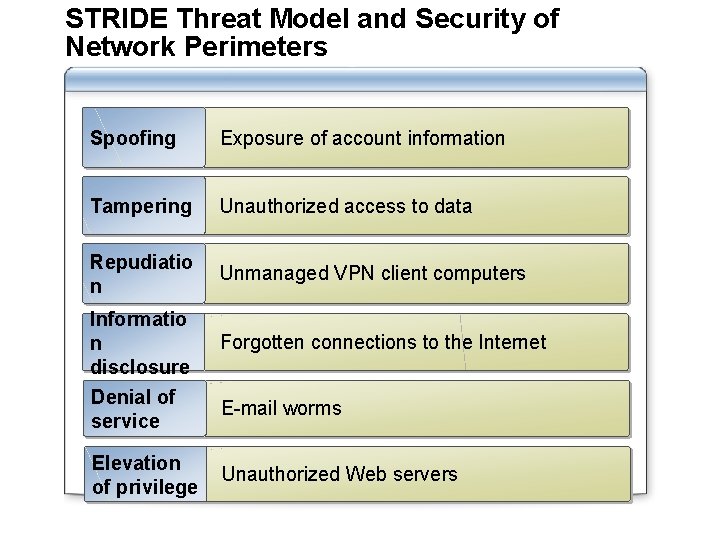
STRIDE Threat Model and Security of Network Perimeters Spoofing Exposure of account information Tampering Unauthorized access to data Repudiatio n Unmanaged VPN client computers Informatio n disclosure Denial of service Elevation of privilege Forgotten connections to the Internet E-mail worms Unauthorized Web servers

Lesson 2: Creating a Design for Security of Network Perimeters Methods for Securing Network Perimeters Process for Designing Secure Perimeter Networks Methods for Securing Perimeter Networks Guidelines for Protecting Computers on the Perimeter

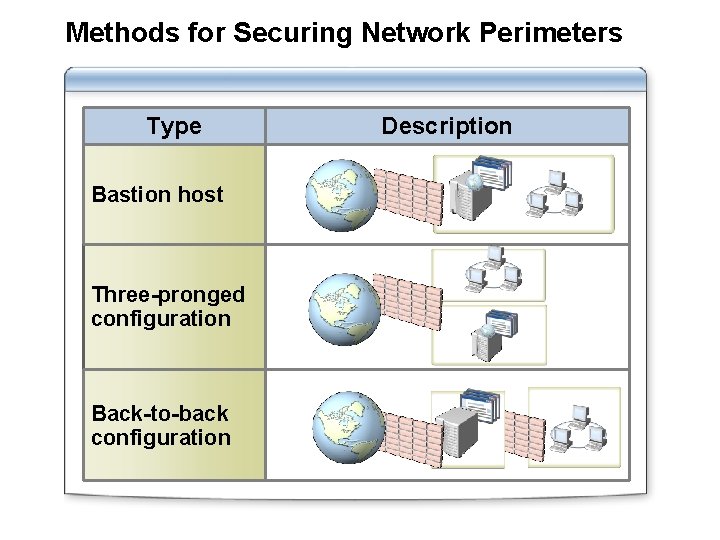
Methods for Securing Network Perimeters Type Bastion host Three-pronged configuration Back-to-back configuration Description

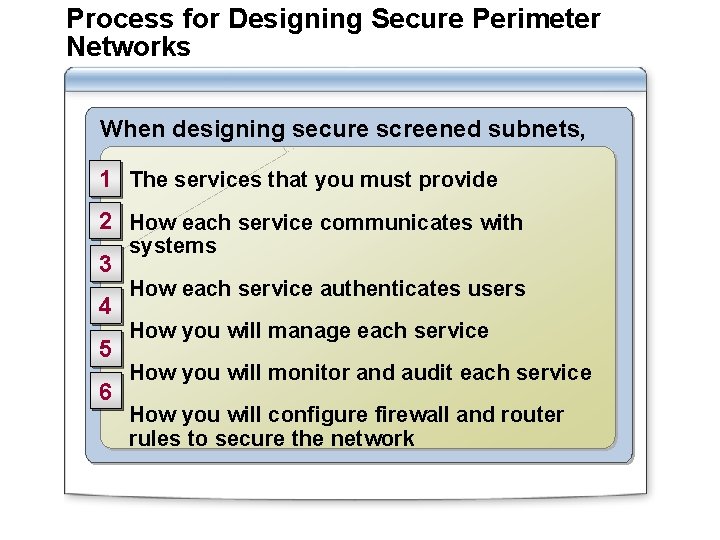
Process for Designing Secure Perimeter Networks When designing secure screened subnets, determine: 1 The services that you must provide 2 How each service communicates with 3 4 5 6 systems How each service authenticates users How you will manage each service How you will monitor and audit each service How you will configure firewall and router rules to secure the network

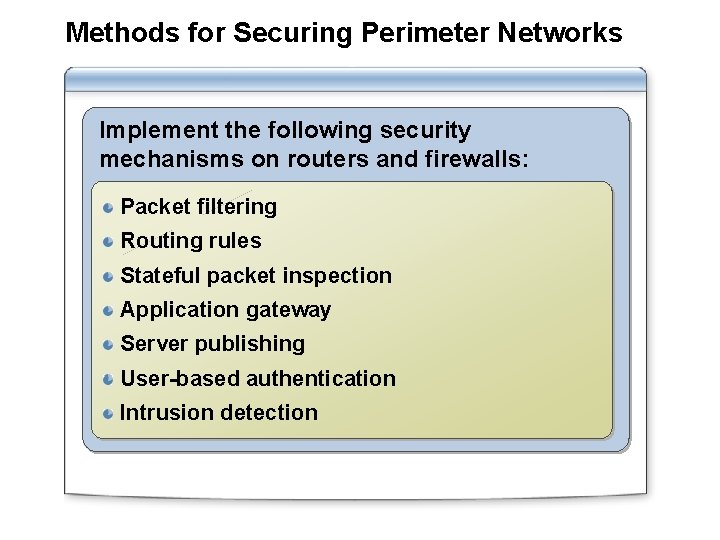
Methods for Securing Perimeter Networks Implement the following security mechanisms on routers and firewalls: Packet filtering Routing rules Stateful packet inspection Application gateway Server publishing User-based authentication Intrusion detection

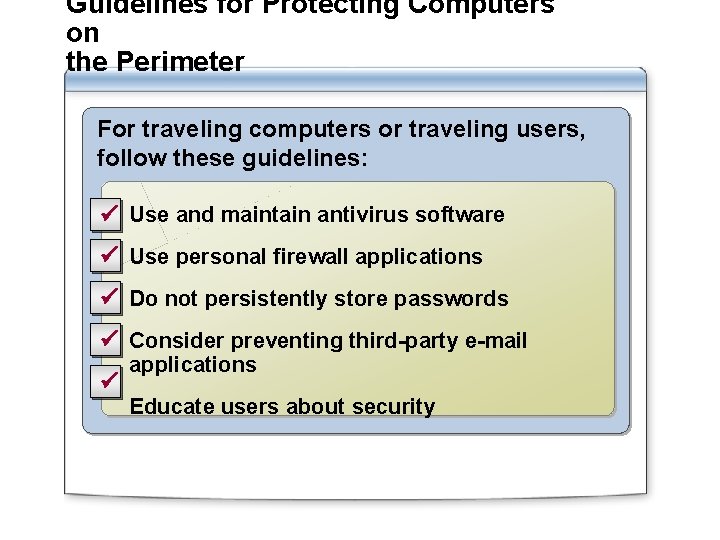
Guidelines for Protecting Computers on the Perimeter For traveling computers or traveling users, follow these guidelines: ü Use and maintain antivirus software ü Use personal firewall applications ü Do not persistently store passwords ü Consider preventing third-party e-mail ü applications Educate users about security

Lab: Designing Security for Network Perimeters Exercise 1 Identifying Potential Perimeter Network Vulnerabilities Exercise 2 Implementing Countermeasures