Modes of Operation INSTRUCTOR DANIA ALOMAR Modes of




![Advantages and Limitations of CBC • C 1 = E(K, [IV P 1]) • Advantages and Limitations of CBC • C 1 = E(K, [IV P 1]) •](https://slidetodoc.com/presentation_image_h2/473fd4e3698bde1e6be4afe551617a74/image-10.jpg)


- Slides: 15

Modes of Operation INSTRUCTOR: DANIA ALOMAR

Modes of Operation • A block cipher can be used in various methods for data encryption and decryption; these methods are called modes of operation. • Five well-known o o o block cipher modes of operation are: Electronic Codebook (ECB) Ciphertext Block Chaining (CBC) Ciphertext Feedback (CFB) Output Feedback (OFB) Counter (CTR) • The same key is used for the block cipher regardless of the mode of operation (i. e. , mode of operations never change the key used for encryption or decryption)

ECB Mode Encryption • The message is divided into blocks and each block is encrypted separately.

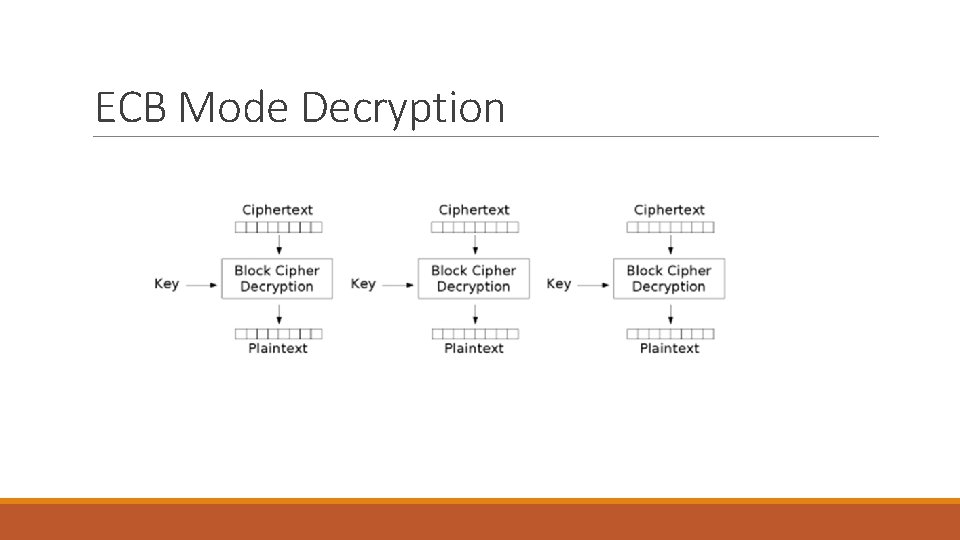
ECB Mode Decryption

Advantages and Limitations of ECB • This mode is the fastest and easiest o Use to encrypt small amounts of data, such as PINs, challenge-response values in authentication processes, and encrypting keys. • Helpful when using encryption in databases. o Any record or table can be added, encrypted, deleted, or decrypted independently of any other table or record. • Each block can be encrypted/decrypted in parallel. • Noise in one block affects no other block. • The disadvantage o Gain Information about repeated blocks o Can rearrange or modify blocks to his own advantage

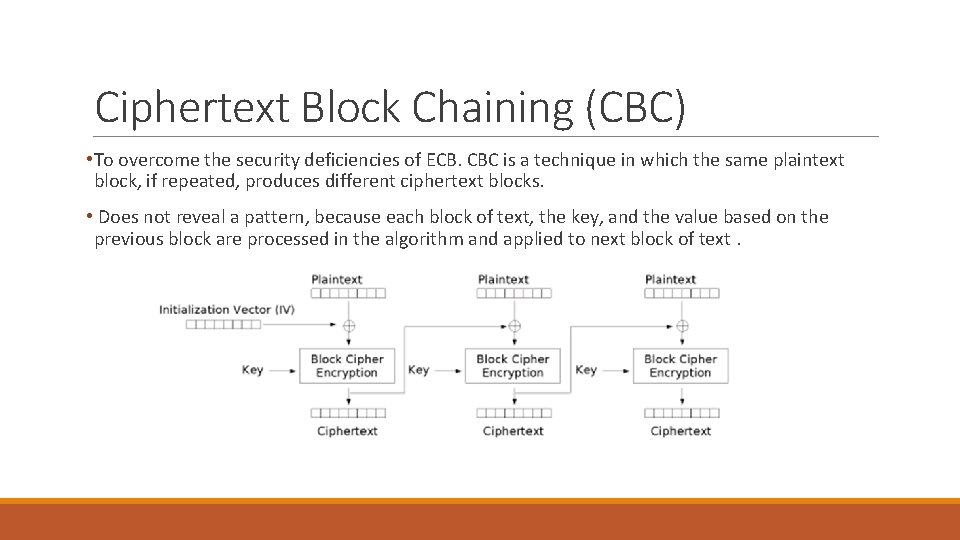
Ciphertext Block Chaining (CBC) • To overcome the security deficiencies of ECB. CBC is a technique in which the same plaintext block, if repeated, produces different ciphertext blocks. • Does not reveal a pattern, because each block of text, the key, and the value based on the previous block are processed in the algorithm and applied to next block of text.

Initialization Vector • A sort of 'dummy block' to kick off the process for the first real block, and also to provide some randomization for the process. • The IV is a data block that is that same size as the cipher block. • The IV must be known to both the sender and receiver. • For maximum security, the IV should be protected against unauthorized changes. This could be done by sending the IV using ECB encryption. • Never reused with the same key. • For CBC and CFB, reusing an IV leaks some information about the first block of plaintext, and about any common prefix shared by the two messages. • For OFB and CTR, reusing an IV completely destroys security. • In CBC mode, the IV must, in addition, be randomly generated at encryption time.

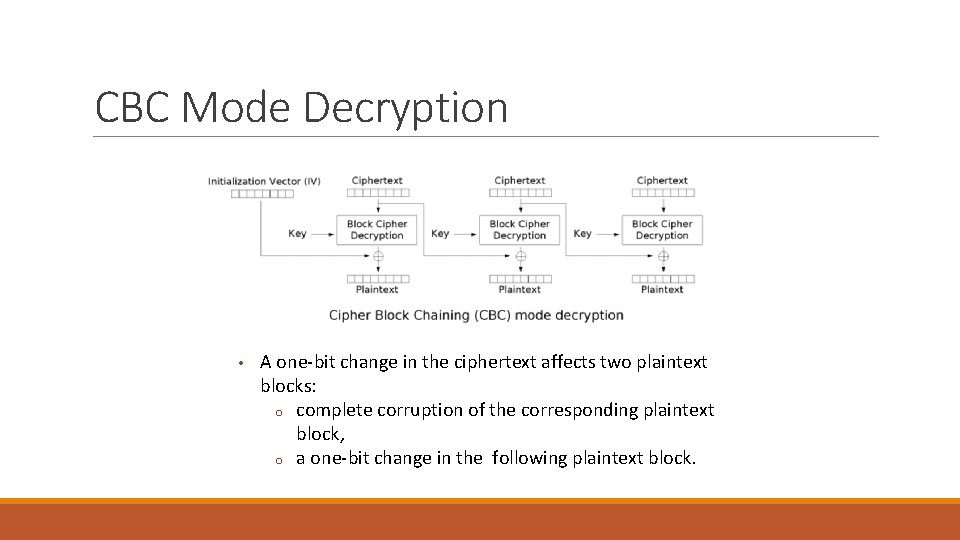
CBC Mode Decryption • A one-bit change in the ciphertext affects two plaintext blocks: o complete corruption of the corresponding plaintext block, o a one-bit change in the following plaintext block.

Advantages and Limitations of CBC • Each ciphertext block depends on all message blocks proceeding it • A change in the message affects all ciphertext blocks after the change as well as the original block • Initial Value (IV) need to be known to sender & receiver o If IV is sent in the clear, an attacker can change bits of the first block, and change IV to compensate § § Either it must be sent encrypted in ECB mode before rest of message Use different IV each time when encrypt a message. • Applications: bulk data encryption, authentication
![Advantages and Limitations of CBC C 1 EK IV P 1 Advantages and Limitations of CBC • C 1 = E(K, [IV P 1]) •](https://slidetodoc.com/presentation_image_h2/473fd4e3698bde1e6be4afe551617a74/image-10.jpg)
Advantages and Limitations of CBC • C 1 = E(K, [IV P 1]) • P 1 = IV D(K, C 1) • Now use the notation that X[i] denotes the ith bit of the b-bit quantity X. Then • P 1[i] = IV[i] D(K, C 1)[i] • Then, using the properties of XOR, we can state • P 1[i]' = IV[i]' D(K, C 1)[i] • This means that if an opponent can predictably change bits in IV, the corresponding bits of the received value of can be changed.

Ciphertext Feedback (CFB) • Message is treated as a stream of bits or bytes. • Result is feed back for next stage (hence name) • Standard allows any number of bit (1, 8, 64 or 128 etc) to be feed back o denoted CFB-1, CFB-8, CFB-64, CFB-128 etc • Most efficient to use all bits in block (64 or 128) Ci = Pi EK(Ci-1) C-1 = IV • Used for stream data encryption

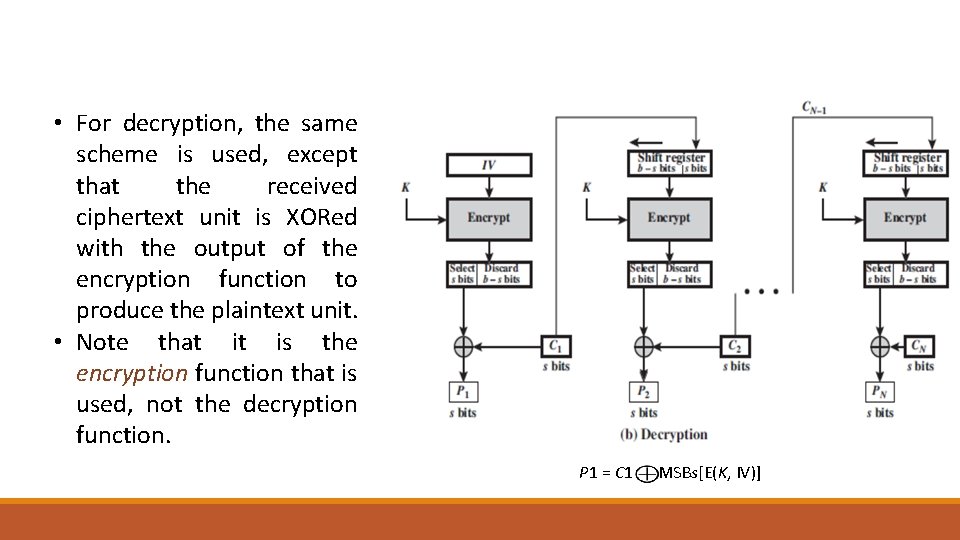
• The input to the encryption function is a b-bit shift register that is initially set to some initialization vector (IV). • The leftmost (most significant) s bits of the output of the encryption function are XORed with the first segment of plaintext P 1 to produce the first unit of ciphertext C 1. • The contents of the shift register are shifted left by s bits, and C 1 is placed in the rightmost (least significant) s bits of the shift register. C 1 = P 1 MSBs[E(K, IV)]

• For decryption, the same scheme is used, except that the received ciphertext unit is XORed with the output of the encryption function to produce the plaintext unit. • Note that it is the encryption function that is used, not the decryption function. P 1 = C 1 MSBs[E(K, IV)]

Advantages and Limitations of CFB • A one-bit change in the ciphertext affects two plaintext blocks: oa one-bit change in the corresponding plaintext block, oand complete corruption of the following plaintext block. • Appropriate when data arrives in bits/bytes. • Most common stream mode. • Limitation: need to pause while do block encryption after every n-bits • Applications: stream data encryption, authentication

Reading “Cryptography and Network Security Principles and Practices”, Fourth Edition by William Stallings Chapter 6