Modern Operation System Kernels Microsoft Windows Internals 4




































- Slides: 80

Modern Operation System Kernels (Microsoft Windows Internals 4 th ed. ) Chapter 3 part-2 Windows System Mechanisms Group 3 組員: 徐裕量 王貞力 葉怡群 左昌國

Outline • Windows Error Reporting • System Service Dispatching ▫ ▫ 32 -Bit System Service Dispatching 64 -Bit System Service Dispatching Kernel-Mode System Service Dispatching Service Descriptor Tables

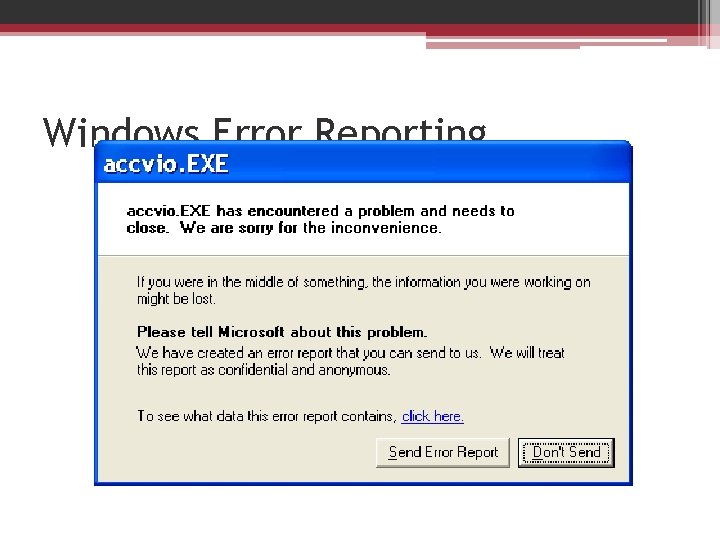
Windows Error Reporting • Windows Error Reporting automates the submission of both user-mode process crashes as well as kernel-mode system crashes. (Chapter 14) • These settings are stored in the registry under the Key HKLMSoftwareMicrosoftPCHealthError. Rep orting.

Windows Error Reporting

Windows Error Reporting

Windows Error Reporting • If the registry value HKLMSOFTWAREMicrosoftWindows NTCurrent. VersionAe. DebugAuto is set to zero or the Debugger string contains the text “Drwtsn 32”, the unhandled exception filter loads WindowsSystemFaultrep. dll into failing process and calls its Report. Fault function.

Windows Error Reporting

Windows Error Reporting • The error report (a minidump and a text file with details on the DLL version numbers loaded in the process)is sent to Microsoft’s online crash analysis server. • Microsoft provides to qualified customers a tool set called Corporate Error Reporting that the administrator with the option to take selective error reports and submit them to Microsoft.

System Service Dispatching • A system service dispatch is triggered as a result of executing an instruction assigned to system service dispatching. • The instruction that Windows uses for system service dispatching depends on the processor in which it’s executing.

32 -Bit System Service Dispatching • A numeric argument passed in the EAX processor register indicates the system service number being requested. • The EBX register points to the list of parameters the caller passes to the system service.

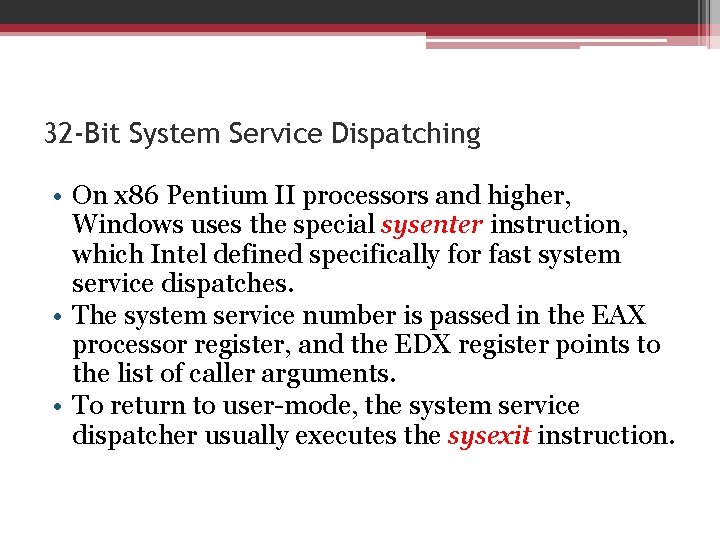
32 -Bit System Service Dispatching • On x 86 Pentium II processors and higher, Windows uses the special sysenter instruction, which Intel defined specifically for fast system service dispatches. • The system service number is passed in the EAX processor register, and the EDX register points to the list of caller arguments. • To return to user-mode, the system service dispatcher usually executes the sysexit instruction.

32 -Bit System Service Dispatching • On K 6 and higher 32 -bit AMD processors, Windows uses the special syscall instruction, which functions similar to the x 86 sysenter instruction. • The system call number is passed in the EAX register, and the stack stores the caller arguments. • After completing the dispatch, the kernel executes the sysret instruction.

32 -Bit System Service Dispatching ntdll!Nt. Read. File: 77 f 5 bfa 8 b 8 b 7000000 mov eax, 0 xb 7 77 f 5 bfad ba 0003 fe 7 f mov edx, 0 x 7 ffe 0300 77 f 5 bfb 2 ffd 2 call edx 77 f 5 bfb 4 c 22400 ret 0 x 24 Shared. User. Data!System. Call. Stub: 7 ffe 0300 8 bd 4 mov edx, esp 7 ffe 0302 0 f 34 sysenter 7 ffe 0304 c 3 ret

64 -Bit System Service Dispatching • On the x 64 architecture, Windows uses the syscall instruction, which functions like the AMD K 6's syscall instruction, for system service dispatching, passing the system call number in the EAX register, the first four parameters in registers, and any parameters beyond those four on the stack:

64 -Bit System Service Dispatching • On the IA 64 architecture, Windows uses the epc (Enter Privileged Mode) instruction. The first eight system call arguments are passed in registers, and the rest are passed on the stack.

64 -Bit System Service Dispatching ntdll!Nt. Read. File: 0000'77 f 9 fc 60 4 c 8 bd 1 mov r 10, rcx 0000'77 f 9 fc 63 b 8 bf 000000 mov eax, 0 xbf 0000'77 f 9 fc 68 0 f 05 syscall 0000'77 f 9 fc 6 a c 3 ret

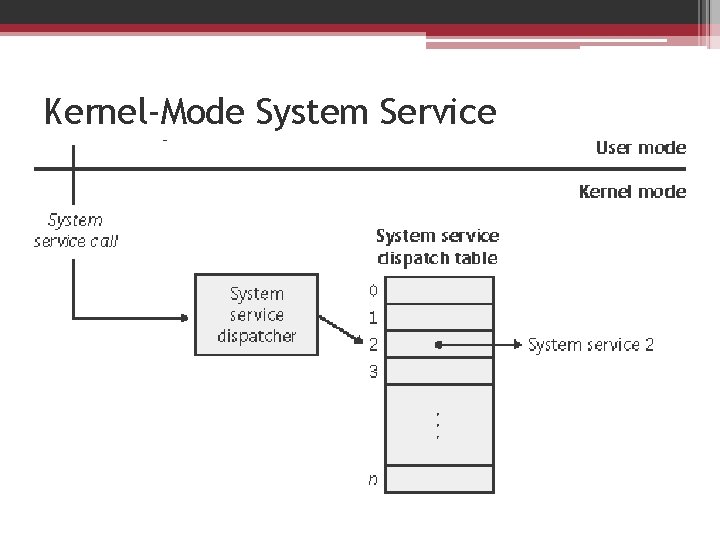
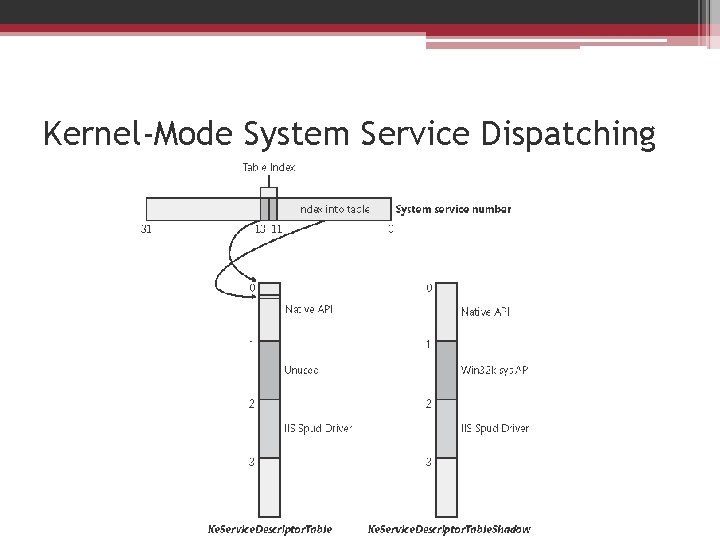
Kernel-Mode System Service Dispatching • The kernel uses this argument to locate the system service information in the system service dispatch table. • Copies the caller's arguments from the thread's user-mode stack to its kernel-mode stack ), and then executes the system service.

Kernel-Mode System Service Dispatching

Kernel-Mode System Service Dispatching

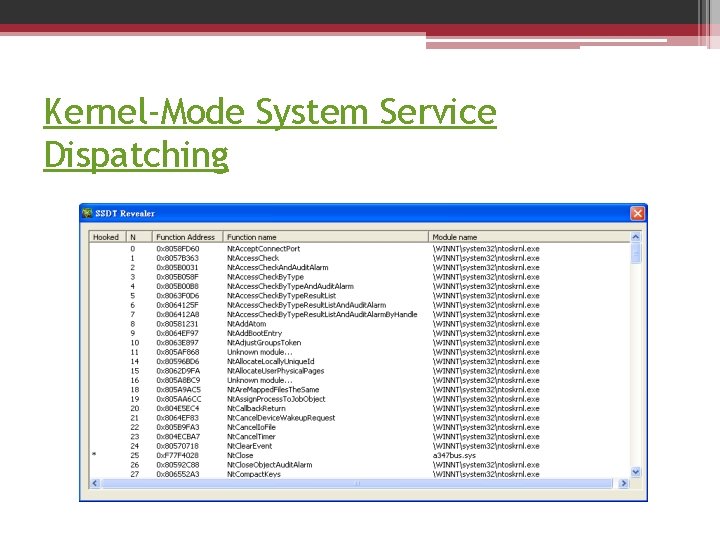
Kernel-Mode System Service Dispatching • Each thread has a pointer to its system service table. • Windows has two built-in system service tables, but up to four are supported. • The system service dispatcher determines which table contains the requested service by interpreting a 2 -bit field in the 32 -bit system service number as a table index. • The low 12 bits of the system service number serve as the index into the table specified by the table index.

Kernel-Mode System Service Dispatching

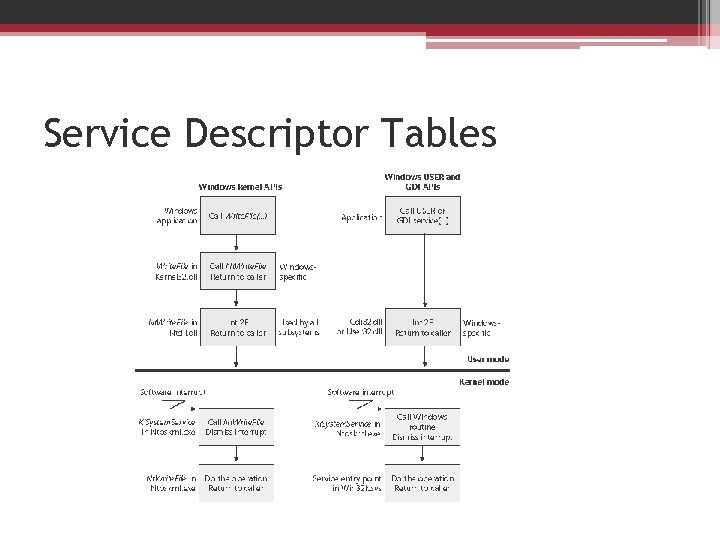
Service Descriptor Tables • Ke. Service. Descriptor. Table, defines the core executive system services implemented in Ntosrknl. exe • Ke. Service. Descriptor. Table. Shadow, includes the Windows USER and GDI services implemented in the kernel-mode part of the Windows subsystem, Win 32 k. sys.

Service Descriptor Tables • The Ke. Add. System. Service. Table function allows Win 32 k. sys and other device drivers to add system service tables. • With the exception of the Win 32 k. sys service table, a service table added with Ke. Add. System. Service. Table is copied into both the Ke. Service. Descriptor. Table array and the Ke. Service. Descriptor. Table. Shadow array.

Service Descriptor Tables • The system service dispatch instructions for Windows executive services exist in the system library Ntdll. • Subsystem DLLs call functions in Ntdll to implement their documented functions. • The exception is Windows USER and GDI functions, in which the system service dispatch instructions are implemented directly in User 32. dll and Gdi 32. dll—there is no Ntdll. dll involved.

Service Descriptor Tables

Chapter 3 Windows System Mechanisms Object Manager

• Windows object manager • Object manager creates, managers, and delete Windows executive object and abstract data types that are use to represent operating system resources such as processes, threads, and the various synchronization objects.

Object manager GOAL(1/2) • Provide a common, uniform mechanism for using system resources • Isolate object protection to one location in the operating system so that C 2 security compliance can be achieved • Establish an object-naming scheme that can readily incorporate existing objects, such as the devices, files, and directories of a file system, or other independent collections of objects

Object manager GOAL(2/2) • Support the requirements of various operating system environments la process to inherit resources from a parent process lcreate case-sensitive filenames • Establish uniform rules for object retention (for keeping an object available until all processes have finished using it)

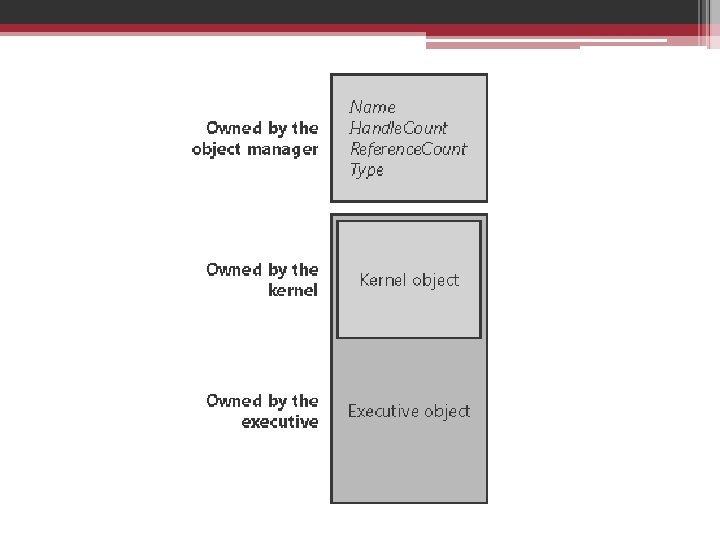
Kinds of objects • Executive objects implemented by various components of the executive (the process manager, memory manager, I/O subsystem) • Kernel object limplemented by the Windows kernel l. Not visible to user-mode l. Created and used only within executive l. Provide fundamental capabilities(e. g. synchronization)


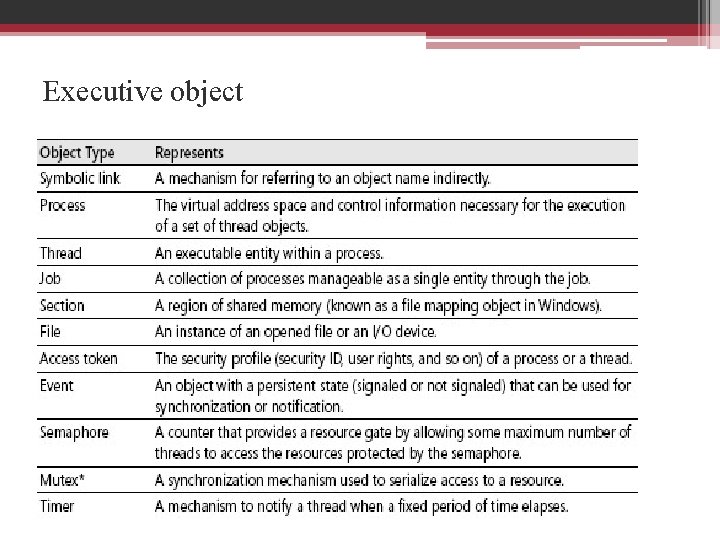
Executive object • The executive objects and object services are primitives that the environment subsystems use to construct their own versions of objects and other resources. • Executive objects are created ▫ By an environment subsystem on behalf of a user application ▫ By various components of the operating system as part of their normal operation. ▫ E. g. create a file

Executive object

• A thread can synchronize with executive object job, process, thread, file, event, semaphore, mutex, and timer objects. • Other executive objects don't support synchronize

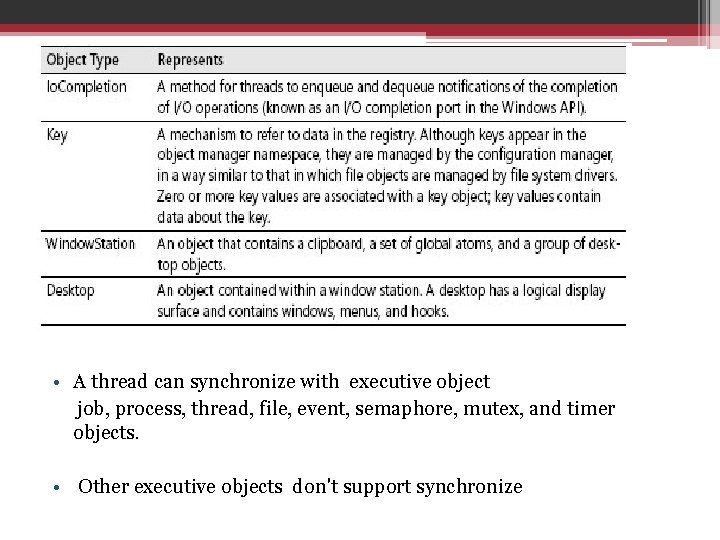
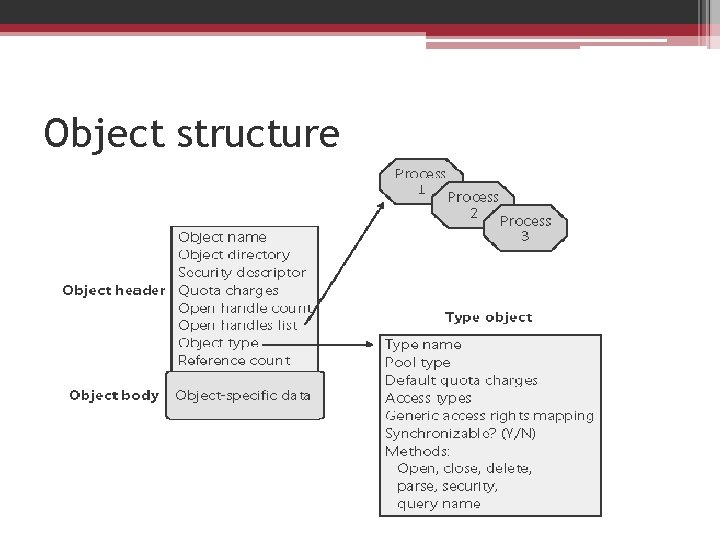
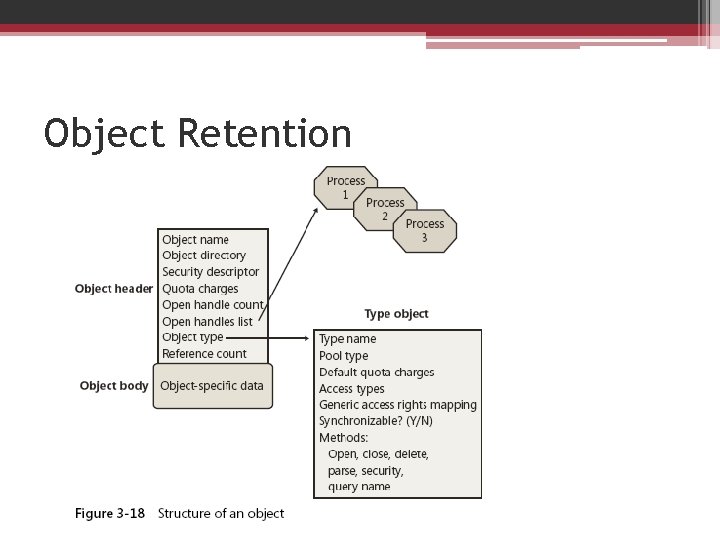
Object structure

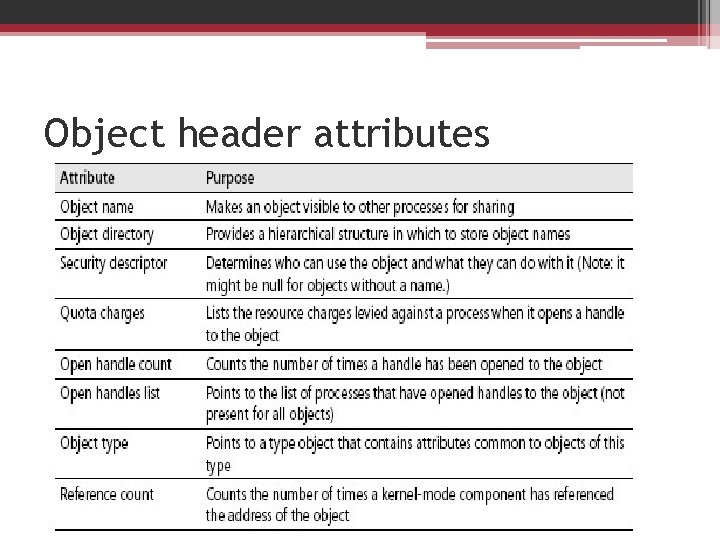
Object header attributes

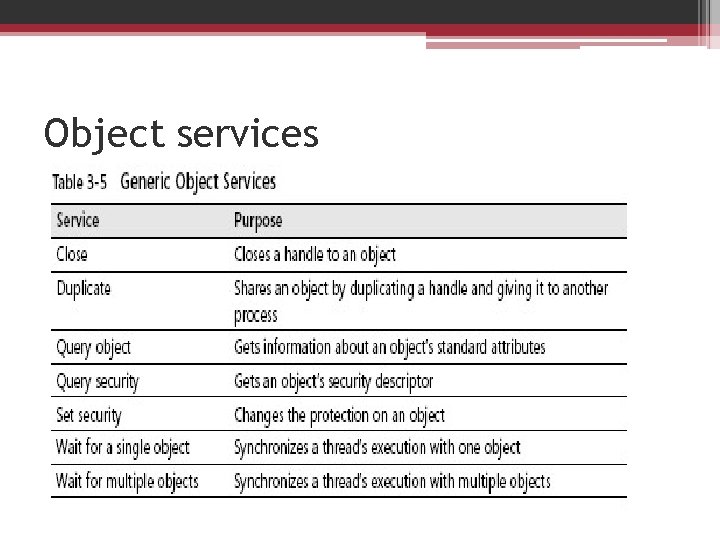
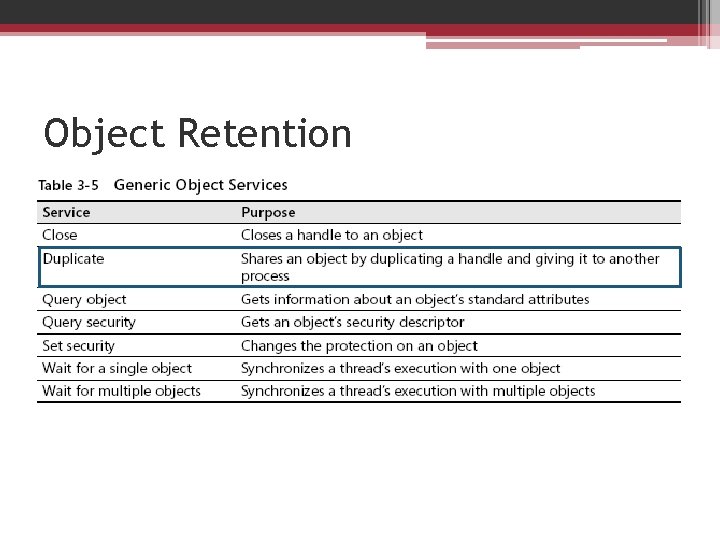
• All objects of the same type share the same object body format • The object manager provides a small set of generic services that operate on the attributes stored in an object's header and can be used on objects of any type • Although these generic object services are supported for all object types, each object has its own create, open, and query services

Object services

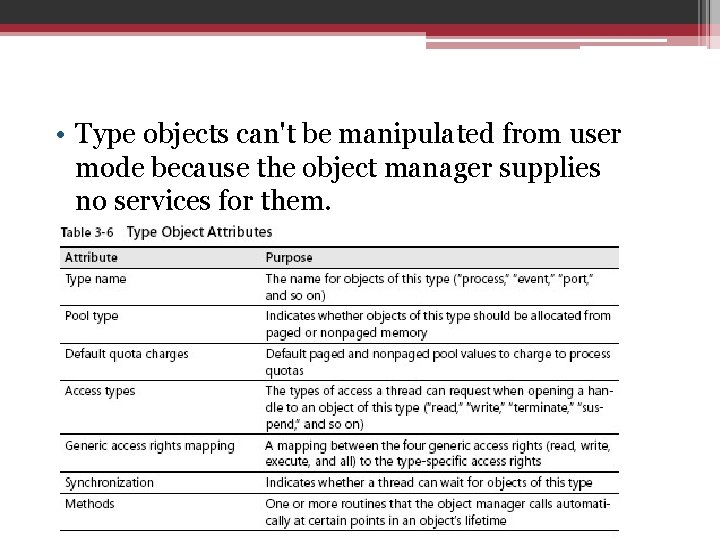
Type objects • Object headers contain data that is common to all objects but that can take on different values for each instance of an object ▫ each object has a unique name and can have a unique security descriptor • you can select from a set of access rights specific to a type of object when you open a handle to objects of that type, The executive supplies ▫ terminate and suspend access for thread objects ▫ read, write, append, and delete access for file objects

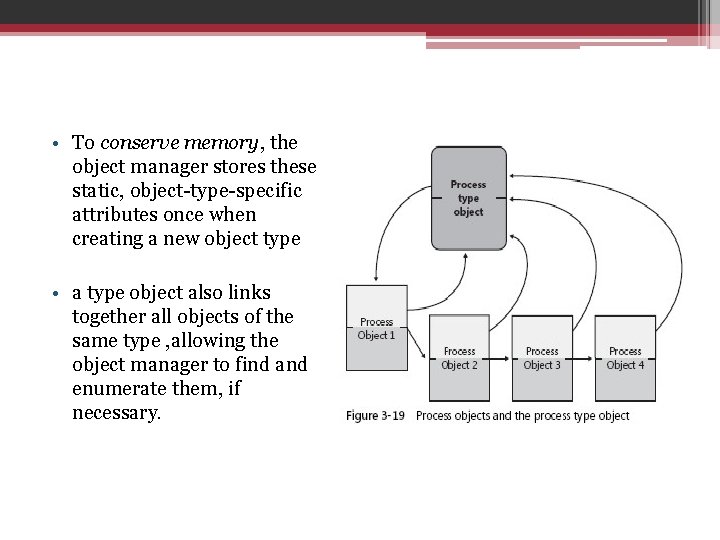
• To conserve memory, the object manager stores these static, object-type-specific attributes once when creating a new object type • a type object also links together all objects of the same type , allowing the object manager to find and enumerate them, if necessary.

• Type objects can't be manipulated from user mode because the object manager supplies no services for them.

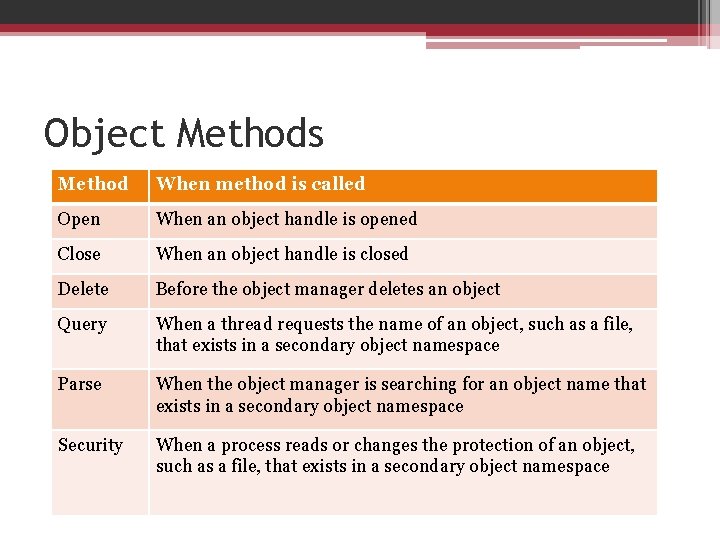
Object Methods

Object Methods Method When method is called Open When an object handle is opened Close When an object handle is closed Delete Before the object manager deletes an object Query When a thread requests the name of an object, such as a file, that exists in a secondary object namespace Parse When the object manager is searching for an object name that exists in a secondary object namespace Security When a process reads or changes the protection of an object, such as a file, that exists in a secondary object namespace

Object Handles and the Process Handle Table • When a process creates or opens an object by name, it receives a handle that represents its access to the object. • All user-mode processes must own a handle to an object before their threads can use the object. • Executive components and device drivers can access objects directly because they are running in kernel mode.

Object Handles and the Process Handle Table • An object handle is an index into a processspecific handle table, pointed to by the executive process (EPROCESS) block • A process's handle table contains pointers to all the objects that the process has opened a handle to.

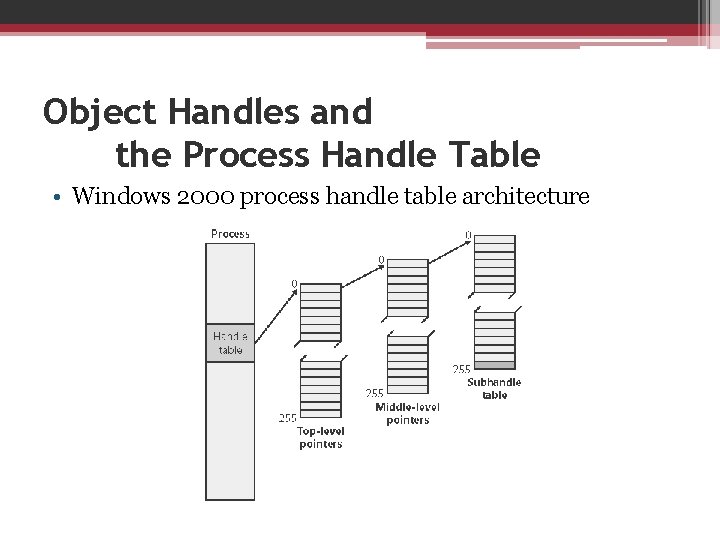
Object Handles and the Process Handle Table • The first handle index is 4, the second 8, and so on. • Handle tables are implemented as a 3 -level scheme, similar to the way that the x 86 memory management unit implements virtual-to-physical address translation

Object Handles and the Process Handle Table • Windows 2000 process handle table architecture

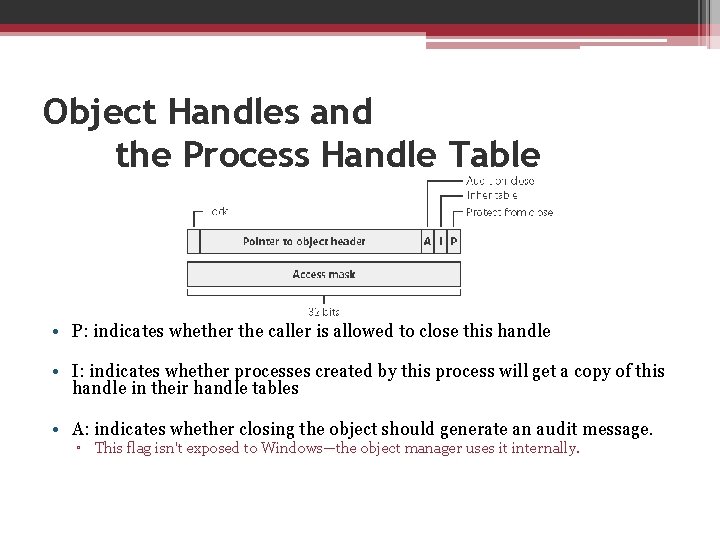
Object Handles and the Process Handle Table • P: indicates whether the caller is allowed to close this handle • I: indicates whether processes created by this process will get a copy of this handle in their handle tables • A: indicates whether closing the object should generate an audit message. ▫ This flag isn't exposed to Windows—the object manager uses it internally.

Object Handles and the Process Handle Table • System components and device drivers often need to open handles to objects that user-mode applications shouldn't have access to. • This is done by creating handles in the kernel handle table ▫ referenced internally with the name Obp. Kernel. Handle. Table • The handles in this table are accessible only from kernel mode and in any process context.

Object Security • In the executive, when a process creates an object or opens a handle to an existing object, the process must specify a set of desired access rights ▫ that is, what it wants to do with the object

Object Security • It can request either a set of standard access rights (such as read, write, and execute) that apply to all object types or specific access rights that vary depending on the object type.

Object Security • When a process opens a handle to an object, the object manager calls the security reference monitor, sending it the process's set of desired access rights. • The security reference monitor checks whether the object's security descriptor permits the type of access the process is requesting. • If it does, the reference monitor returns a set of granted access rights that the process is allowed, and the object manager stores them in the object handle it creates.

I will present… • Microsoft Windows Internals – Microsoft Windows Server 2003, Windows XP, and Windows 2000, 4 th ed. • Chapter 3: System Mechanisms Object Structure 1. 2. 3. 4. 5. Object Retention Resource Accounting Object Names Session Namespace, and Two Experiments • Page 141 ~ 149

Outline • • • Object Retention Resource Accounting Object Names Experiment: Looking at the Base Named Objects Session Namespace Experiment: Viewing Namespace Instancing

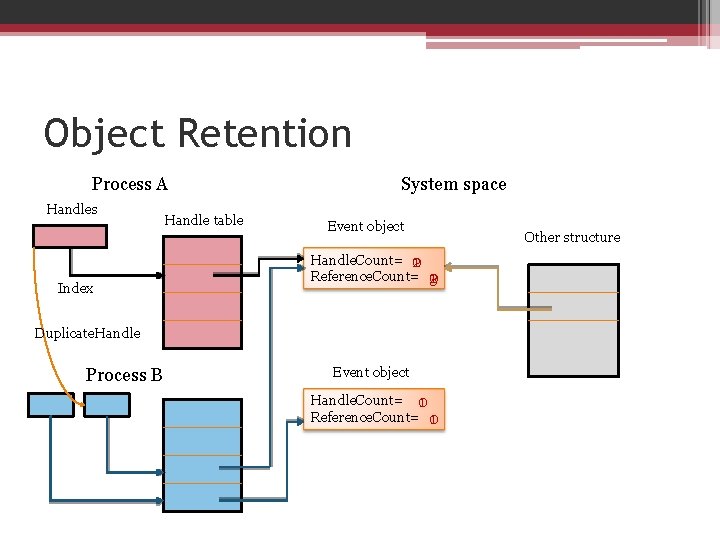
Object Retention • 2 types of objects ▫ Temporary – remain while in use ▫ Permanent – remain until explicitly freed • Object retention ▫ retains “temporary” objects only when they’re in use ▫ 2 phases 1. Name retention 2. Object deletion • DDK Documentation OSR(MSDN ver. )

Object Retention

Object Retention Process A Handles Index Handle table System space Event object Handle. Count= 2 10 Reference. Count= 3 10 2 Duplicate. Handle Process B Event object Handle. Count= 10 Reference. Count= 10 Other structure

Object Retention

Object Retention

Object Retention • Programmers need not be concerned that one process might delete an object before the other process has finished using it. • How about “permanent” object?

Object retention • An object is permanent if it was created with the OBJ_PERMANENT object attribute flag specified. • A permanent object is created with a reference count of one. • Use the following steps to delete a permanent object that you created: 1. 2. 3. 4. Call Ob. Dereference. Object. Call the appropriate Zw. Open. Xxx or Zw. Create. Xxx routine to get a handle for the object, if necessary. Call Zw. Make. Temporary. Object with the handle obtained in step 2. Call Zw. Close with the handle obtained in step 2.

Outline • • • Object Retention Resource Accounting Object Names Experiment: Looking at the Base Named Objects Session Namespace Experiment: Viewing Namespace Instancing

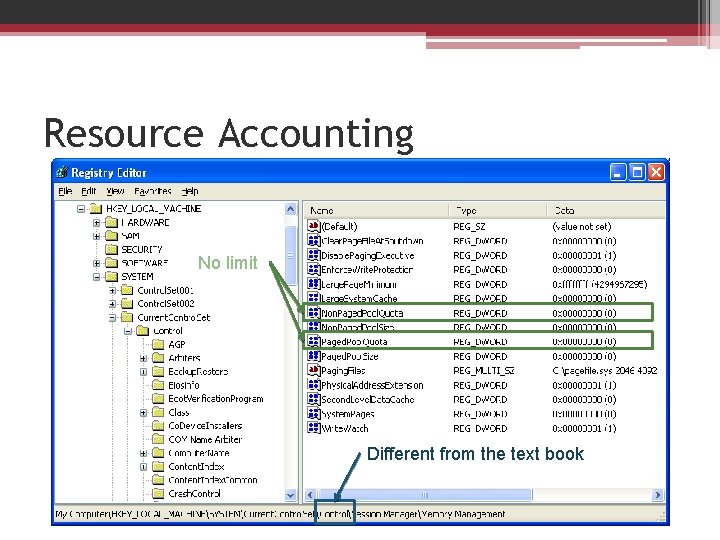
Resource Accounting • Like object retention, resource accounting is closely related to the use of object handles. • Quota system? ▫ complicated • Resource accounting ▫ Quota charges : record how much memory will be subtracted from pool quota when opening a handle to an object.

Resource Accounting No limit Different from the text book

Outline • • • Object Retention Resource Accounting Object Names Experiment: Looking at the Base Named Objects Session Namespace Experiment: Viewing Namespace Instancing

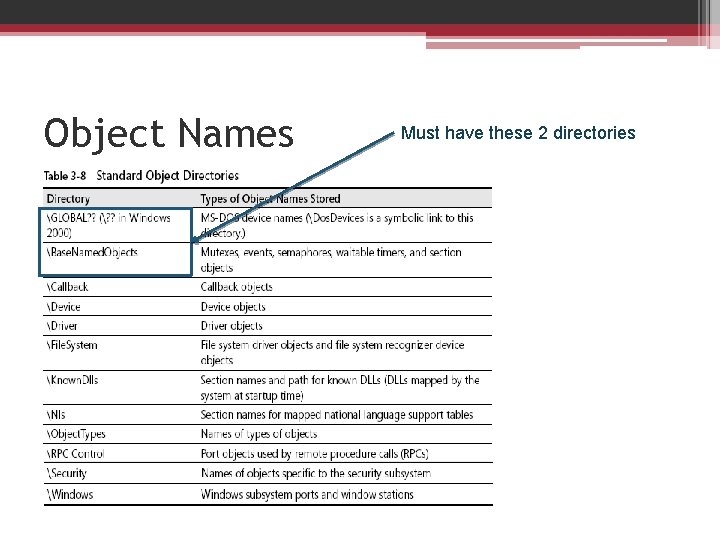
Object Names • Object manager requires the following information to help track objects ▫ A way to distinguish one object from another ▫ A method for finding and retrieving a particular object • Allow processes to share objects • Look up timing ▫ When a process creates a named object ▫ When a process opens a handle to a named object

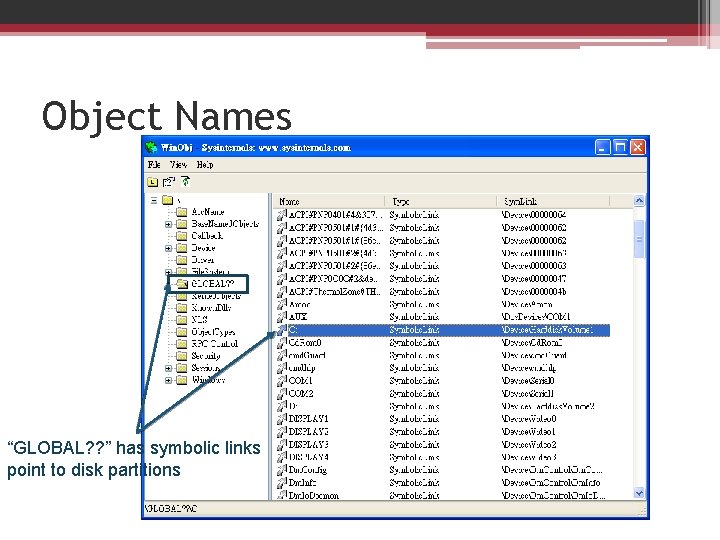
Object Names • Case-sensitive or case-insensitive? • Unique name : won’t collide with others • Global, but can not across a network ▫ Parse method • Object directories (object directory object) ▫ Like file system directories • Symbolic links (symbolic link object) ▫ A: , B: , C: floppy, hard disk

Object Names Must have these 2 directories

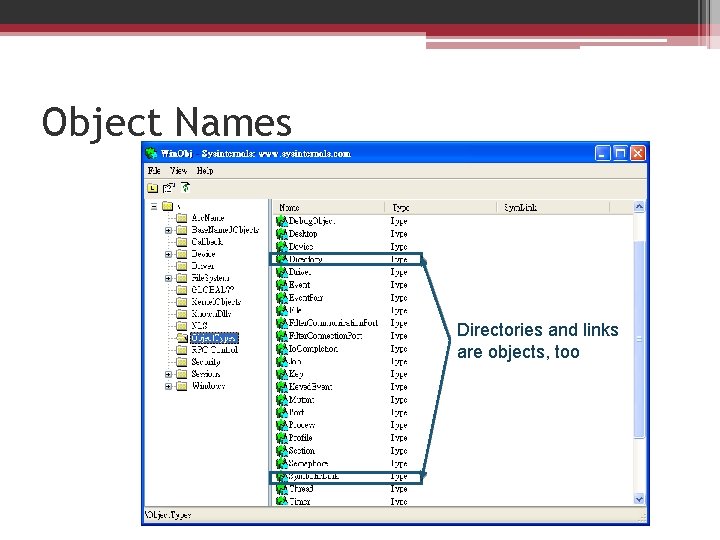
Object Names Directories and links are objects, too

Object Names “GLOBAL? ? ” has symbolic links point to disk partitions

Outline • • • Object Retention Resource Accounting Object Names Experiment: Looking at the Base Named Objects Session Namespace Experiment: Viewing Namespace Instancing

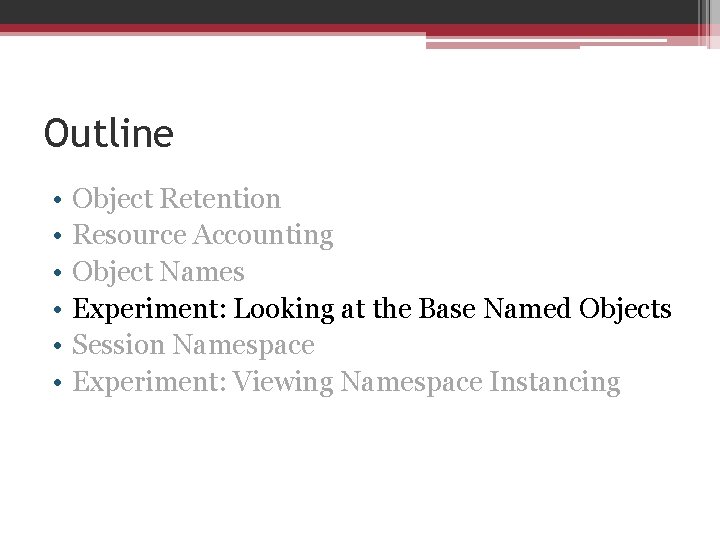
Experiment: Looking at the Base Named Objects

Outline • • • Object Retention Resource Accounting Object Names Experiment: Looking at the Base Named Objects Session Namespace Experiment: Viewing Namespace Instancing

Session Namespace • How many user would log on to the system interactively? (review Chapter 1. ) • A user logged on to the console session ▫ First instance of namespace global namespace • Additional sessions ▫ Session-private view local namespace ▫ Dos. Devices , Windows , and Base. Named. Objects

Outline • • • Object Retention Resource Accounting Object Names Experiment: Looking at the Base Named Objects Session Namespace Experiment: Viewing Namespace Instancing

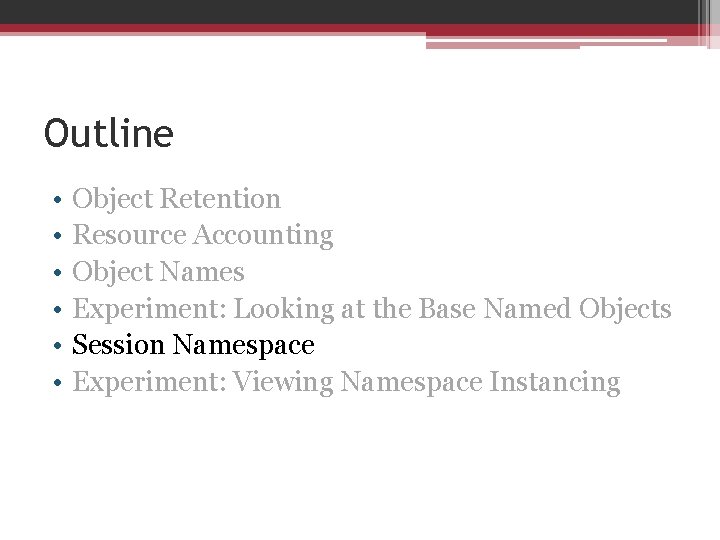
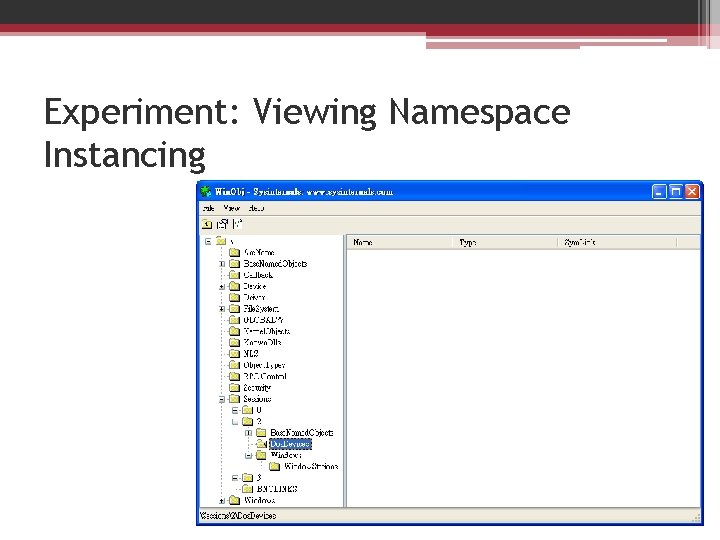
Experiment: Viewing Namespace Instancing There is a link to Global in Session

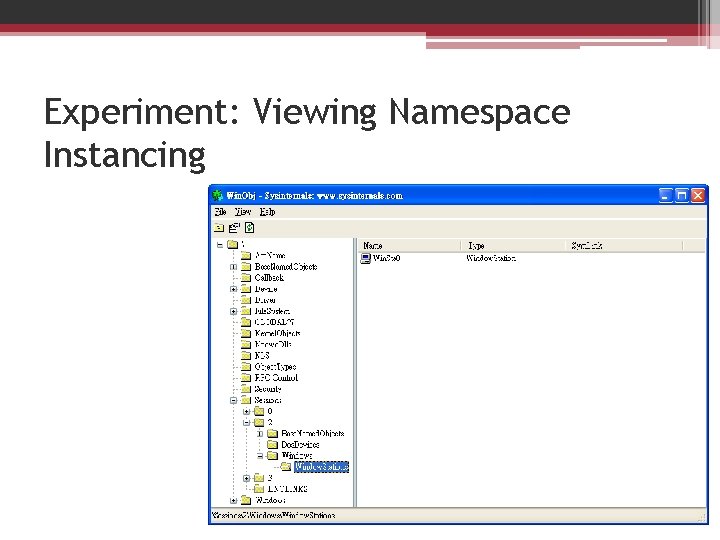
Experiment: Viewing Namespace Instancing

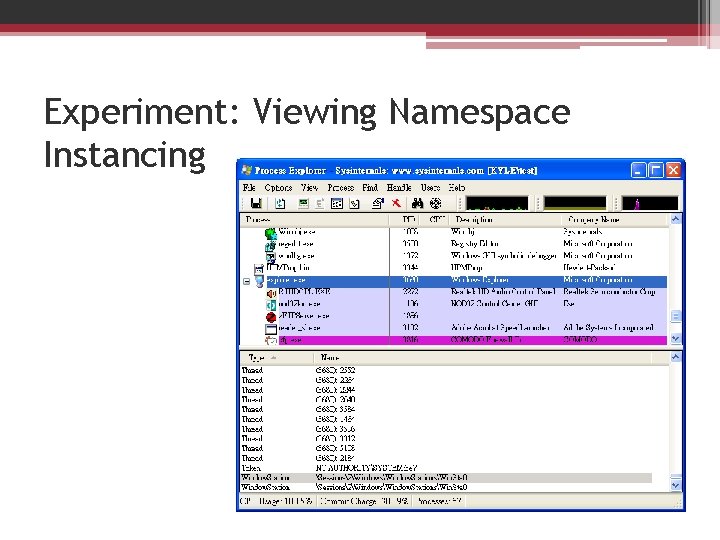
Experiment: Viewing Namespace Instancing

Experiment: Viewing Namespace Instancing

Related Resource • Windows, NT Object Manager (download wmv, 160 MB, about 40 min) ▫ Adrian Marinescu • DDK Documentation OSR(MSDN ver. )