Models of Information Security Analysis CERT Centers Software







- Slides: 14

Models of Information Security Analysis CERT Centers, Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 -3890 SEI is sponsored by the U. S. Department of Defense © 2000 by Carnegie Mellon University 95 -752: 8 -1

Outline Definitions Analysis framework Cautionary factors Sample analysis © 2002 by Carnegie Mellon University Model - 2

Definitions Trend: 1. to extend in a general direction: follow a general course or veer in a new direction 2. to show a tendency for example, to incline or trend upwards or to become deflected or shift Trend analysis: search for patterns over time in order to identify the ways in which they change and develop, veer in new directions, or shift Incident - Any event that harms security at one or more sites © 2002 by Carnegie Mellon University Model - 3

Analysis Framework Types of trends Sources of data Interpretation of results © 2002 by Carnegie Mellon University Model - 4

Types of Trends Internal and External patterns Temporal trends Spatial trends Associational trends Compound trends © 2002 by Carnegie Mellon University Model - 5

Sources of Data CERT/CC Data • Year 2000 - 21, 756 Incidents reported to CERT/CC • Year 2001 (Q 1) - 7, 457 Incidents reported to CERT/CC • Profiled 1654 incidents, all active during July 2000 - Feb 2001 (plus some preliminary June data) Open Source Data: • Web page defacement mirrors • Lexus/Nexus • Full disclosure sites • Social data © 2002 by Carnegie Mellon University Model - 6

Limits of Trending Inherently partial data Baseline in dynamic environment Correlation vs. Causation Implications • Need to be cautious in kinds of conclusions • Consider strategies for dealing with trends gone wrong © 2002 by Carnegie Mellon University Model - 7

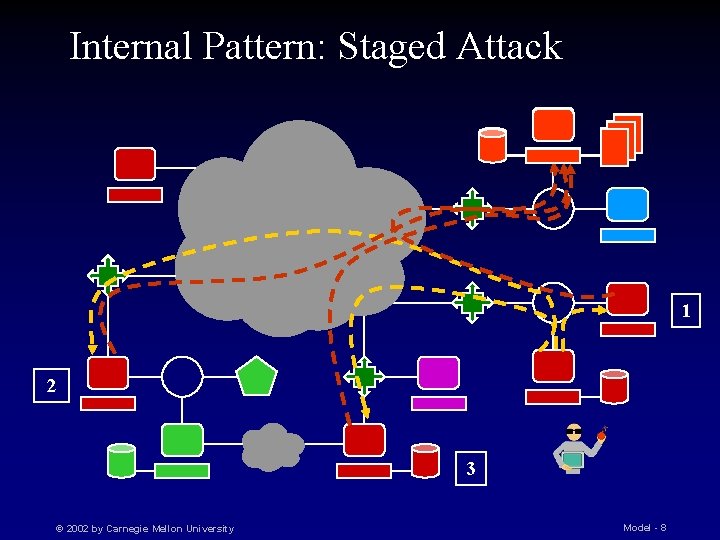
Internal Pattern: Staged Attack 1 2 3 © 2002 by Carnegie Mellon University Model - 8

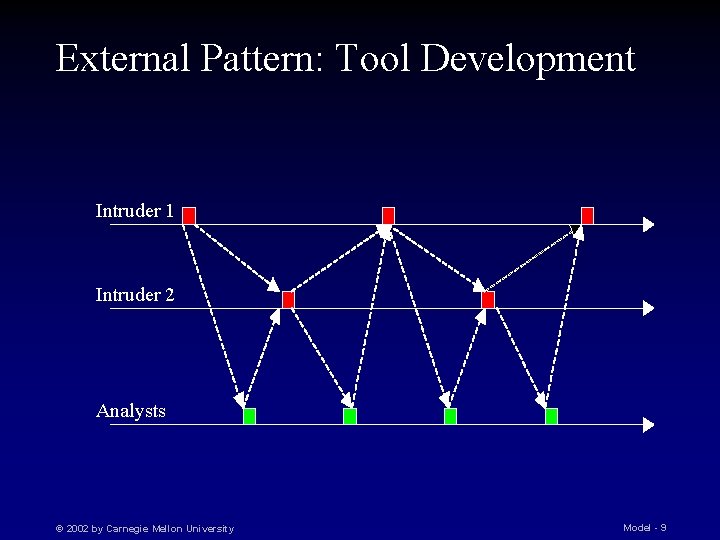
External Pattern: Tool Development Intruder 1 Intruder 2 Analysts © 2002 by Carnegie Mellon University Model - 9

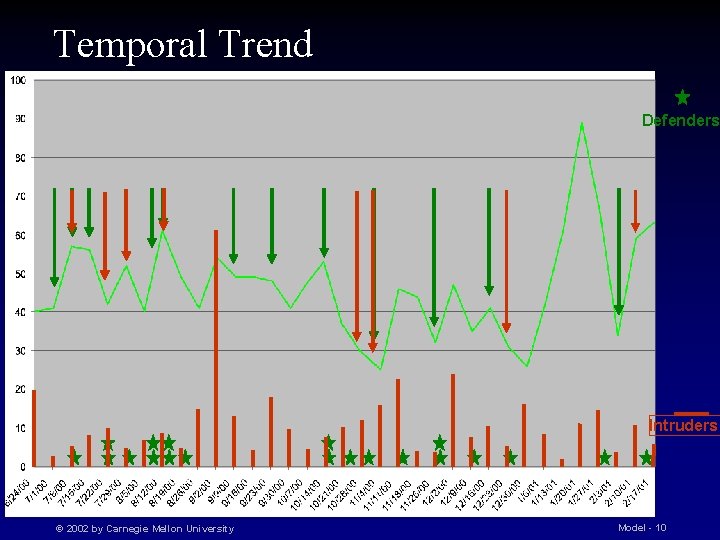
Temporal Trend Defenders Intruders © 2002 by Carnegie Mellon University Model - 10

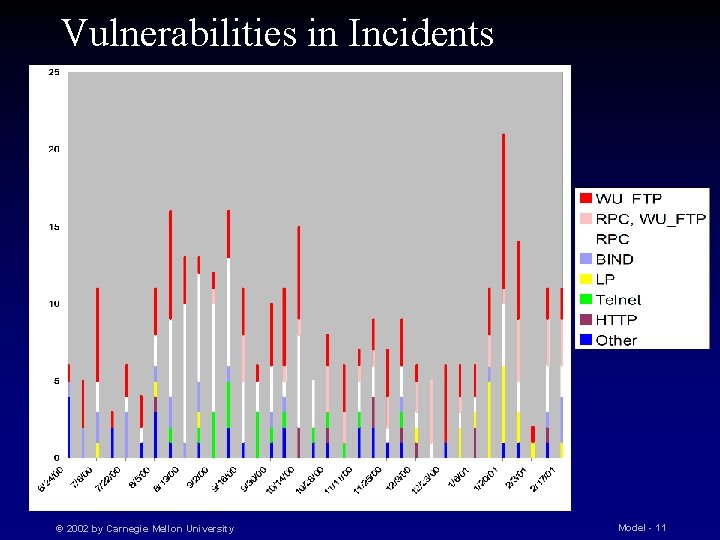
Vulnerabilities in Incidents © 2002 by Carnegie Mellon University Model - 11

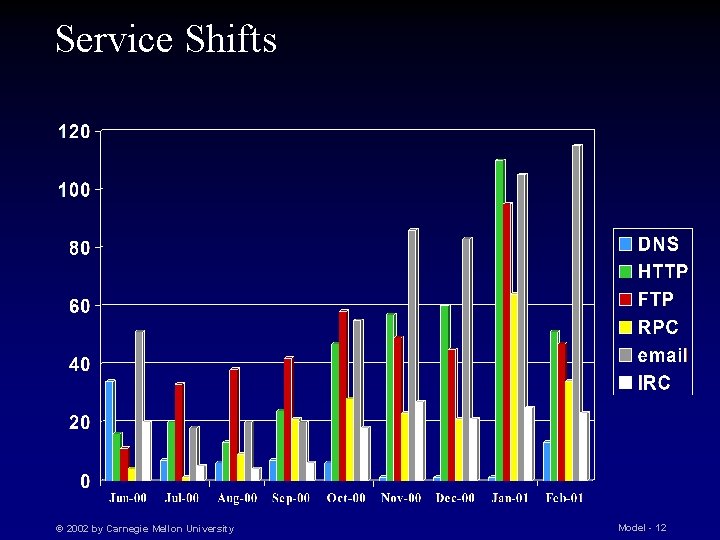
Service Shifts © 2002 by Carnegie Mellon University Model - 12

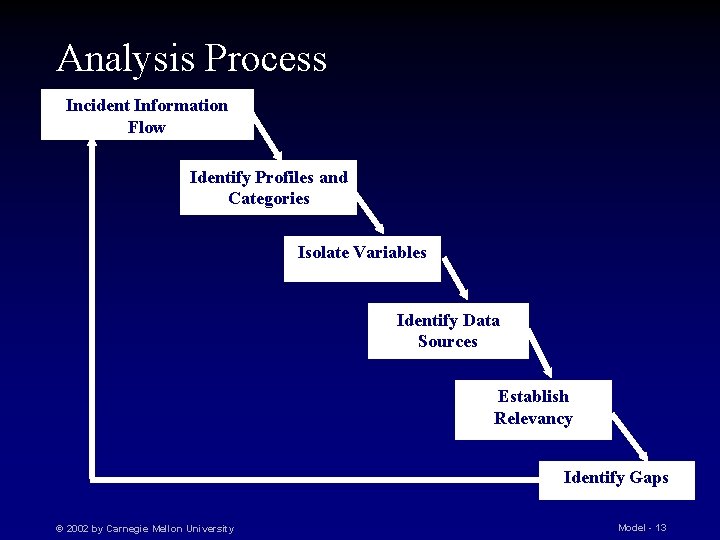
Analysis Process Incident Information Flow Identify Profiles and Categories Isolate Variables Identify Data Sources Establish Relevancy Identify Gaps © 2002 by Carnegie Mellon University Model - 13

Conclusions Typifying trends simplifies interpretation • Clarification of goals • Identification of relative importance of characteristics Understanding cyber security is growing in importance © 2002 by Carnegie Mellon University Model - 14