Modeling Role Based Access Control in UML Based
Modeling Role Based Access Control in UML Based on 1. Towards A UML based approach to Role Engineering, by P. Epstein and R. Sandhu 2. UML-Based representation of RBAC, by Eonsuk Shin and Gail-Joon Ahn 3. RBAC Constraints Specification using OCL by Gail-Joon Ahn and Eonsuk Shin Precise Modeling UML Security 3 1

A Brief Introduction to RBAC • Permissions assigned to roles • Users play roles, and then they are bestowed with all permissions assigned to roles • Conflict exists between – Roles – Users – Permissions • Objective is to be able to play roles without conflicts Precise Modeling UML Security 3 2
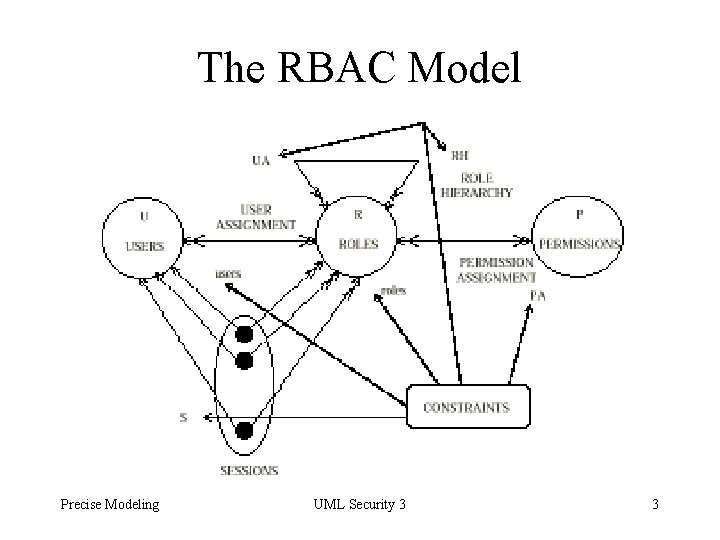
The RBAC Model Precise Modeling UML Security 3 3
RBAC Continued • Users belong to groups • Groups, roles and objects may belong to hierarchies • Generally (but not always) senior roles have all permissions assigned to junior roles • Permissions can be + or • RCL 2000 is a language designed for RBAC specifications Precise Modeling UML Security 3 4

Towards A UML based approach to Role Engineering P. Epstein and R. Sandhu Precise Modeling UML Security 3 5
RBAC for Network Enterprises • Two groups – Application developers – Local system administrator • Application developer responsible for 1. Objects 2. Application Constraints 2. Object Handles 4. Application keys • Local System Administrator responsible for 5. Enterprise keys 7. Enterprise constraints Precise Modeling 6. Key chains UML Security 3 6
Layers for Application Developer 1. Objects: Attributes+ methods 2. Object handles: Set of objects 3. Application constraints: pre-requisite for granting access permissions 4. Application keys: Associates a role with objects 5. Application keys can be a leaf node of the hierarchy or a non-leaf (considered abstract) Precise Modeling UML Security 3 7
Layers for System Administrator 5. Enterprise Keys: Each application key is mapped to an enterprise key or a key chain. 6. Key Chains: Sets of enterprise keys 7. Enterprise Constraints: Enterprise key permits user to access methods of the object, if application constraints are satisfied Precise Modeling UML Security 3 8
Layers Continued • A user can be assigned enterprise keys that are part of different application key hierarchies • If a key inherits methods more than key, then in worse case the key contains the same method with different constraint • FNE Policy: constraints are logically “ored” Precise Modeling UML Security 3 9
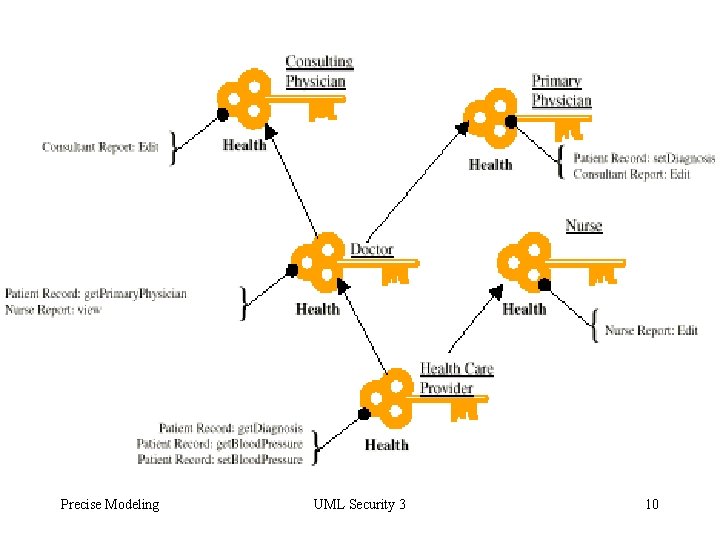
Precise Modeling UML Security 3 10
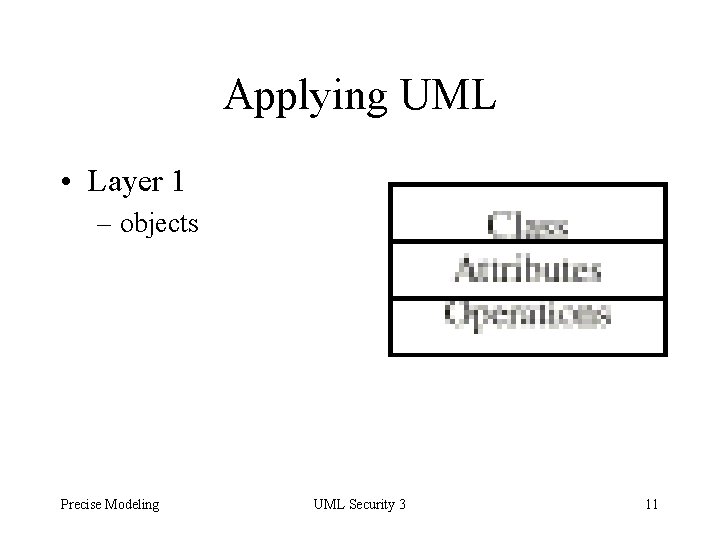
Applying UML • Layer 1 – objects Precise Modeling UML Security 3 11
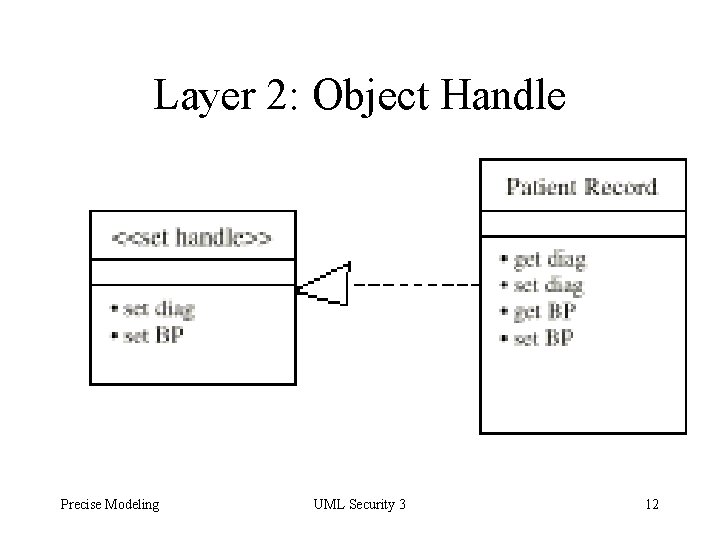
Layer 2: Object Handle Precise Modeling UML Security 3 12

Layer 3: Constraints Precise Modeling UML Security 3 13
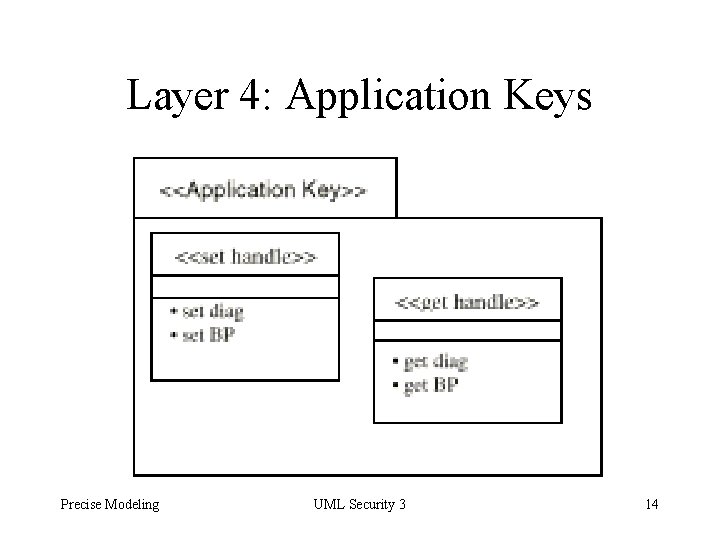
Layer 4: Application Keys Precise Modeling UML Security 3 14
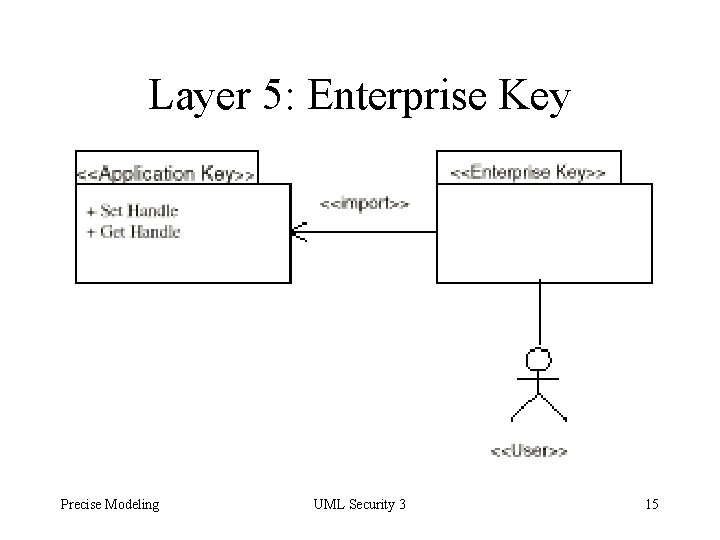
Layer 5: Enterprise Key Precise Modeling UML Security 3 15
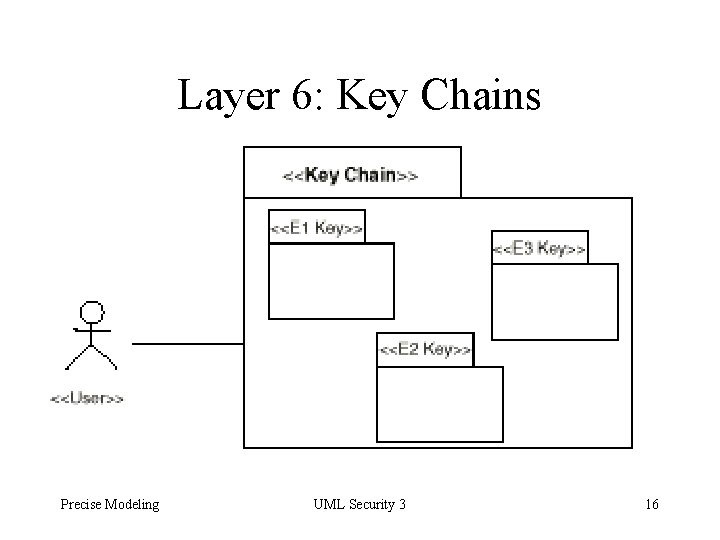
Layer 6: Key Chains Precise Modeling UML Security 3 16
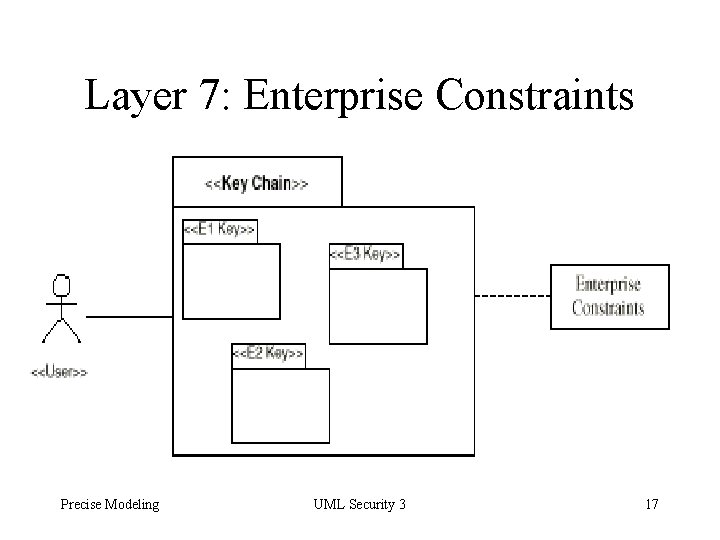
Layer 7: Enterprise Constraints Precise Modeling UML Security 3 17
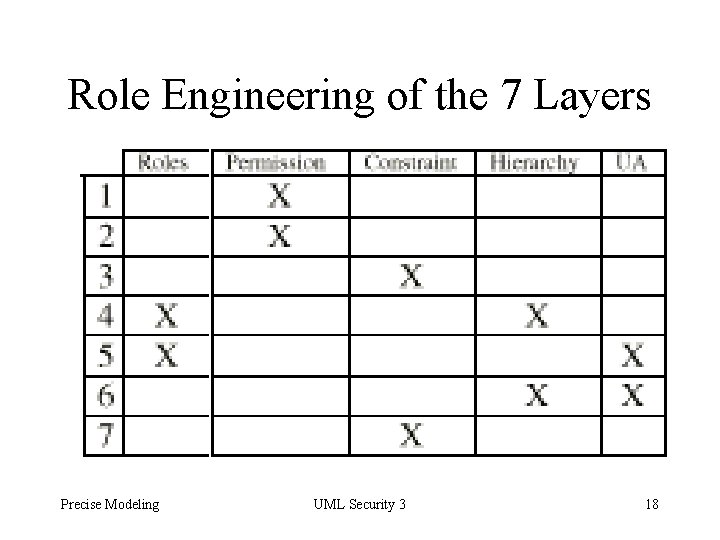
Role Engineering of the 7 Layers Precise Modeling UML Security 3 18
UML-Based Representation of RBAC By Eonsuk Shin and Gail-Joon Ahn Precise Modeling UML Security 3 19
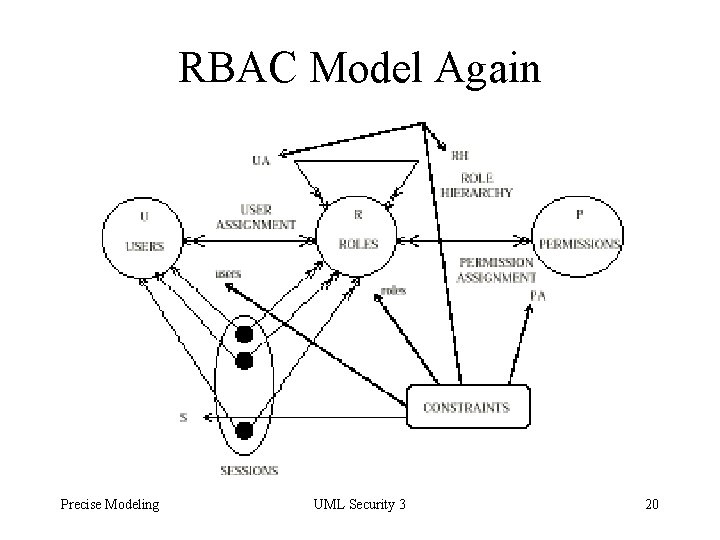
RBAC Model Again Precise Modeling UML Security 3 20
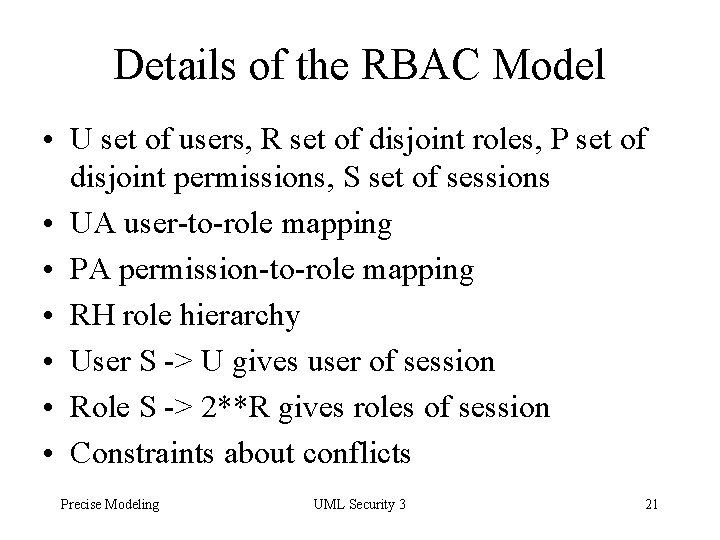
Details of the RBAC Model • U set of users, R set of disjoint roles, P set of disjoint permissions, S set of sessions • UA user-to-role mapping • PA permission-to-role mapping • RH role hierarchy • User S -> U gives user of session • Role S -> 2**R gives roles of session • Constraints about conflicts Precise Modeling UML Security 3 21
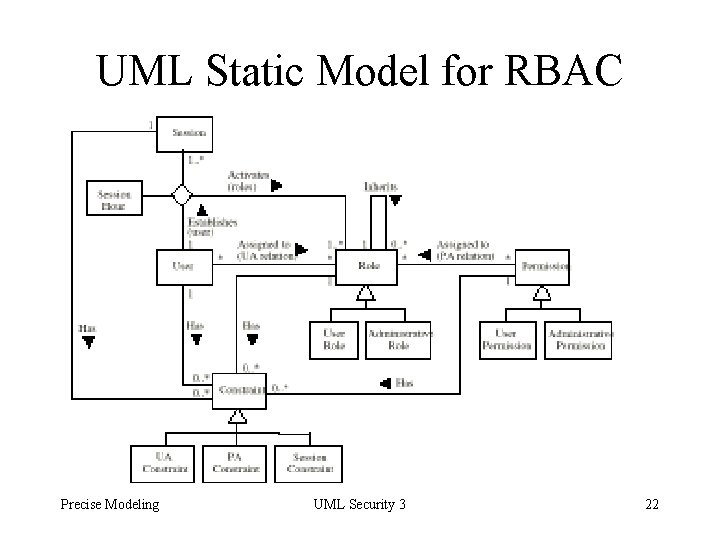
UML Static Model for RBAC Precise Modeling UML Security 3 22
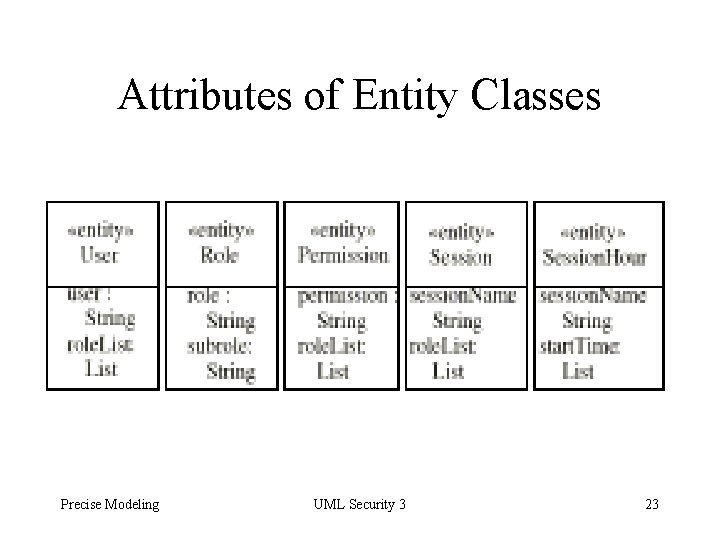
Attributes of Entity Classes Precise Modeling UML Security 3 23
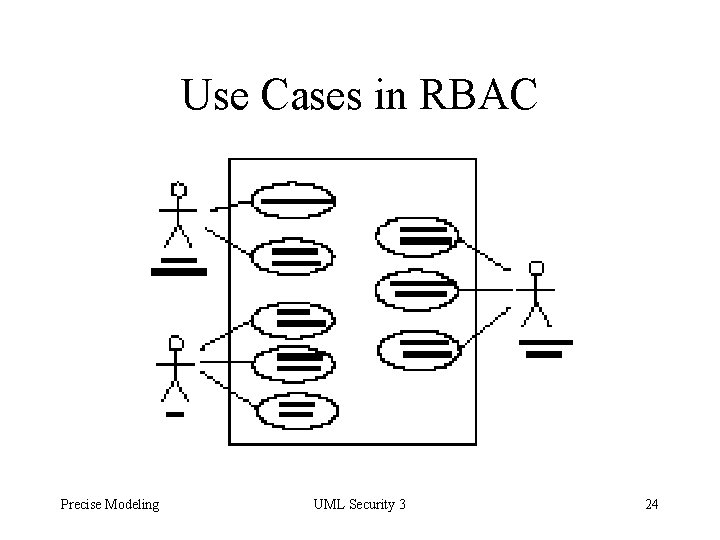
Use Cases in RBAC Precise Modeling UML Security 3 24

RBAC Constraints Specification using OCL By Gail-Joon Ahn and Eonsuk Shin Precise Modeling UML Security 3 25
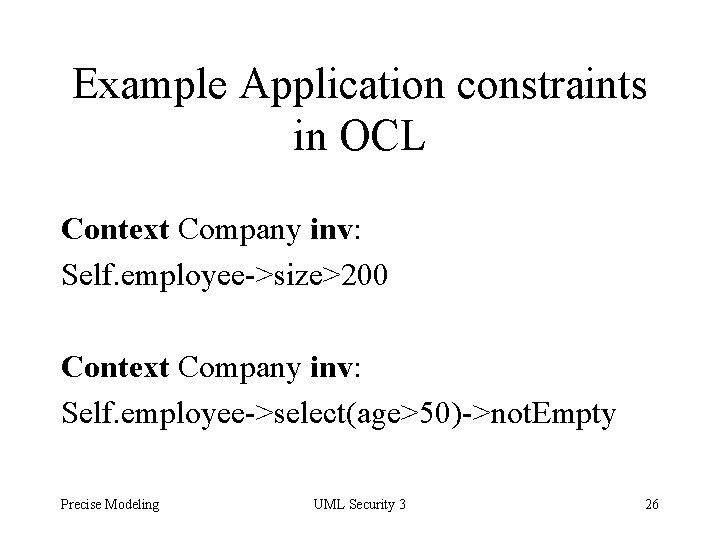
Example Application constraints in OCL Context Company inv: Self. employee->size>200 Context Company inv: Self. employee->select(age>50)->not. Empty Precise Modeling UML Security 3 26
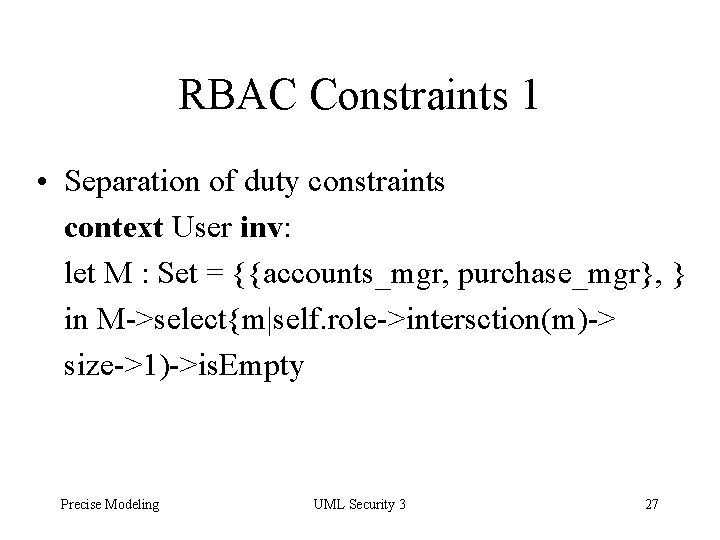
RBAC Constraints 1 • Separation of duty constraints context User inv: let M : Set = {{accounts_mgr, purchase_mgr}, } in M->select{m|self. role->intersction(m)-> size->1)->is. Empty Precise Modeling UML Security 3 27
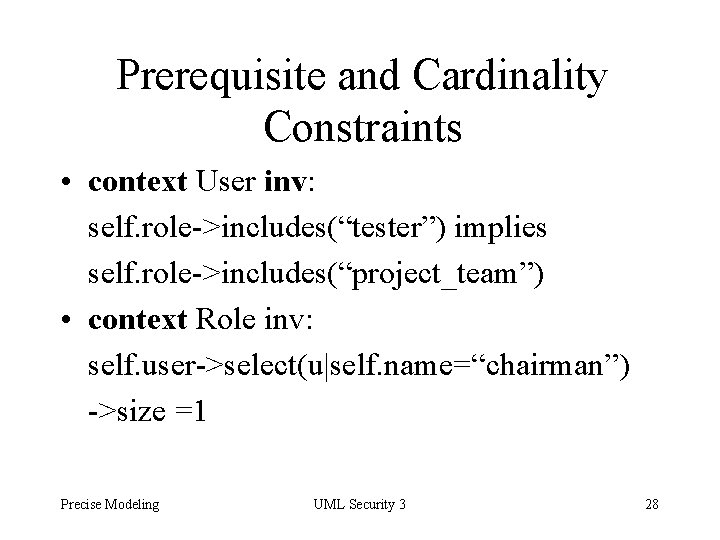
Prerequisite and Cardinality Constraints • context User inv: self. role->includes(“tester”) implies self. role->includes(“project_team”) • context Role inv: self. user->select(u|self. name=“chairman”) ->size =1 Precise Modeling UML Security 3 28
- Slides: 28