Modeling Early Detection and Mitigation of Internet Worm














- Slides: 36

Modeling, Early Detection, and Mitigation of Internet Worm Attacks Cliff C. Zou Assistant professor School of Computer Science University of Central Florida Orlando, FL Email: czou@eecs. ucf. edu Web: http: //www. cs. ucf. edu/~czou 1

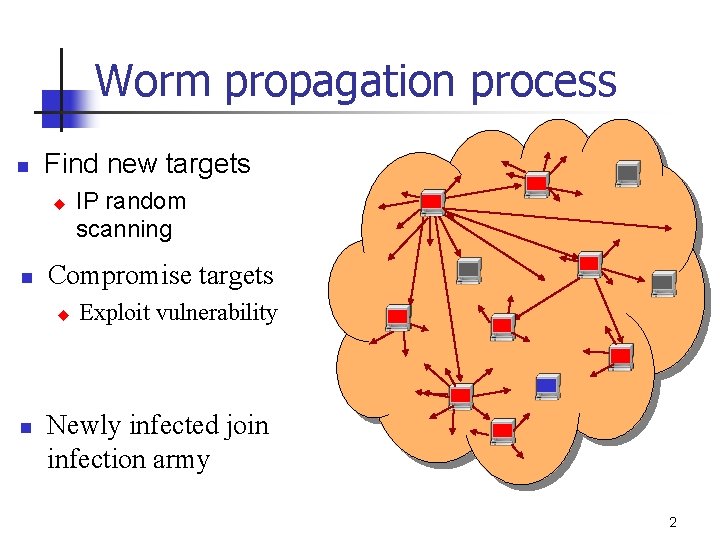
Worm propagation process n Find new targets u n Compromise targets u n IP random scanning Exploit vulnerability Newly infected join infection army 2

Worm research motivation n Code Red (Jul. 2001) : 360, 000 infected in 14 hours n Slammer (Jan. 2003) : 75, 000 infected in 10 minutes Congested parts of Internet (ATMs down…) n Blaster (Aug. 2003) : 150, 000 ~ 8 million infected DDOS attack (shut down domain windowsupdate. com) n Witty (Mar. 2004) : 12, 000 infected in half an hour Attack vulnerability in ISS security products n Sasser (May 2004) : 500, 000 infected within two days Infection faster than human response ! 3

How to defend against worm attack? n Automatic response required n First, understanding worm behavior u n Basis for worm detection/defense Next, early warning of an unknown worm Detection based on worm model u Prediction of worm damage scale u n Last, autonomous defense Dynamic quarantine u Self-tuning defense u 4

Outline n Worm propagation modeling n Early warning of an unknown worm n Autonomous defense n Summary and current work 5

Outline n Worm propagation modeling n Early warning of an unknown worm n Autonomous defense n Summary and current work 6

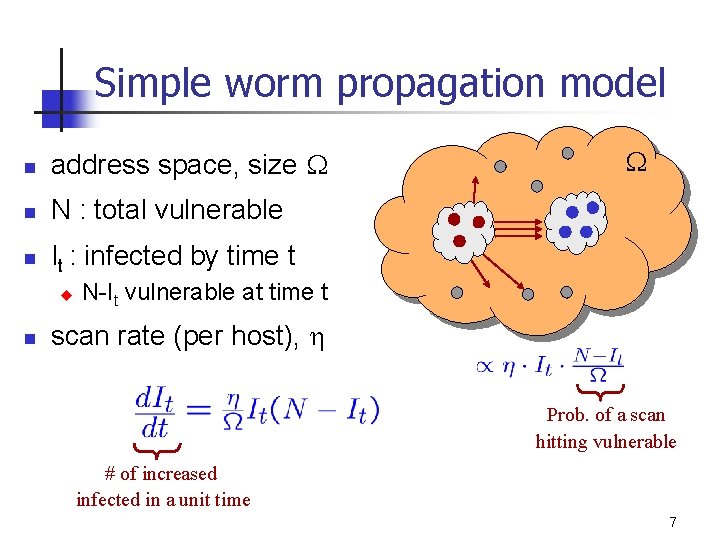
Simple worm propagation model n address space, size W n N : total vulnerable n It : infected by time t u n W N-It vulnerable at time t scan rate (per host), h Prob. of a scan hitting vulnerable # of increased infected in a unit time 7

Simple worm propagation 8

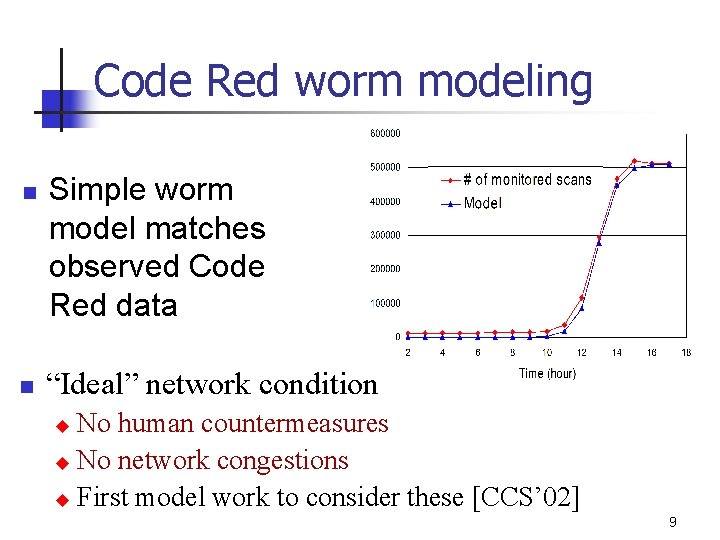
Code Red worm modeling n n Simple worm model matches observed Code Red data “Ideal” network condition No human countermeasures u No network congestions u First model work to consider these [CCS’ 02] u 9

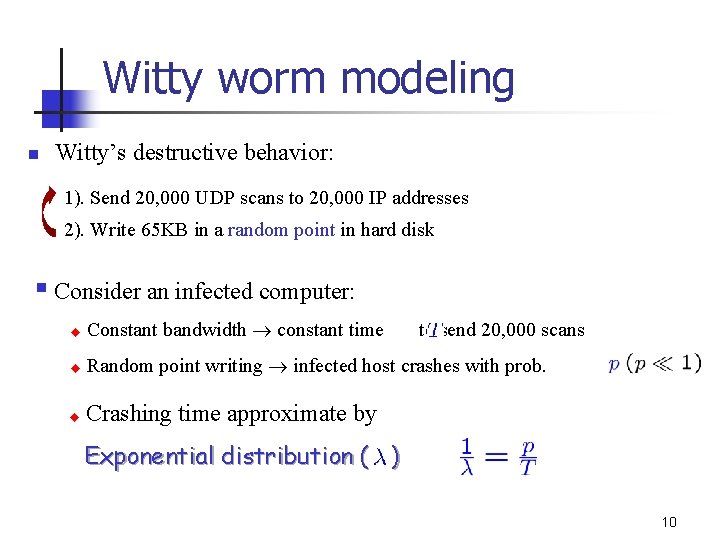
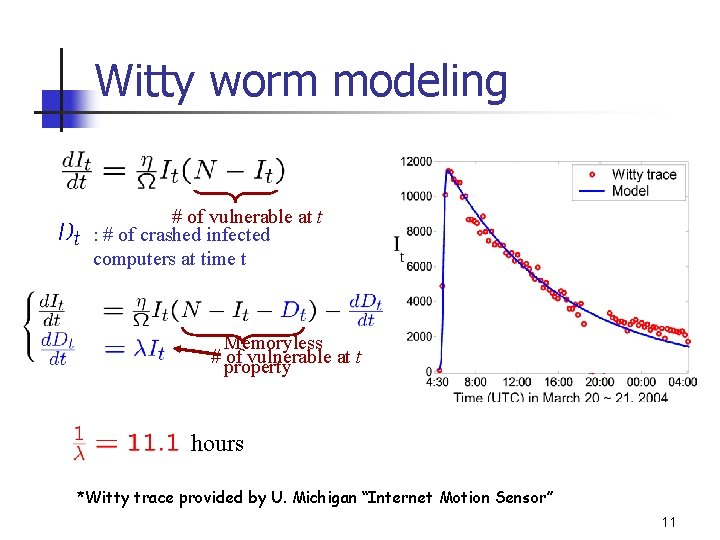
Witty worm modeling n Witty’s destructive behavior: 1). Send 20, 000 UDP scans to 20, 000 IP addresses 2). Write 65 KB in a random point in hard disk § Consider an infected computer: u Constant bandwidth constant time u Random point writing infected host crashes with prob. u Crashing time approximate by to send 20, 000 scans Exponential distribution ( ) 10

Witty worm modeling # of vulnerable at t : # of crashed infected computers at time t Memoryless # of vulnerable at t property hours *Witty trace provided by U. Michigan “Internet Motion Sensor” 11

Advanced worm modeling — hitlist, routing worm n Hitlist worm — increase I 0 Contains a list of known vulnerable hosts u Infects hit-list hosts first, then randomly scans u Lasts less than a minute n Routing worm — decrease W Only scan BGP routable space 32 u BGP table information: W =. 32£ 2 u Ø 32% of IPv 4 space is Internet routable 12

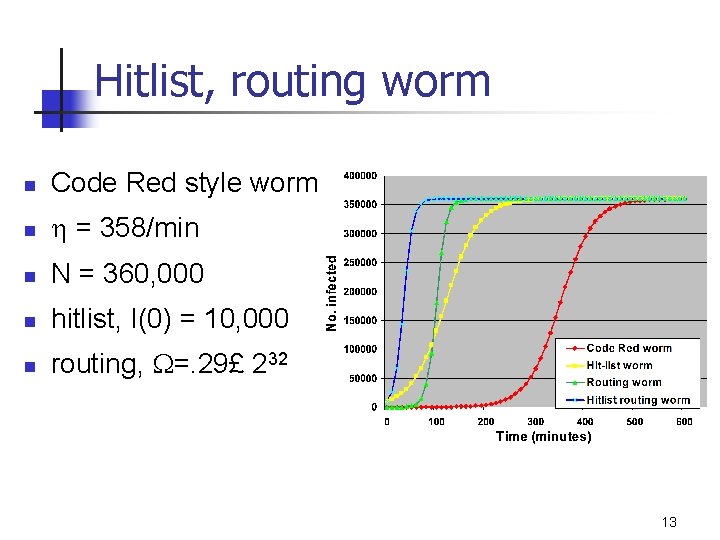
Hitlist, routing worm n Code Red style worm n h = 358/min n N = 360, 000 n hitlist, I(0) = 10, 000 n routing, W=. 29£ 232 13

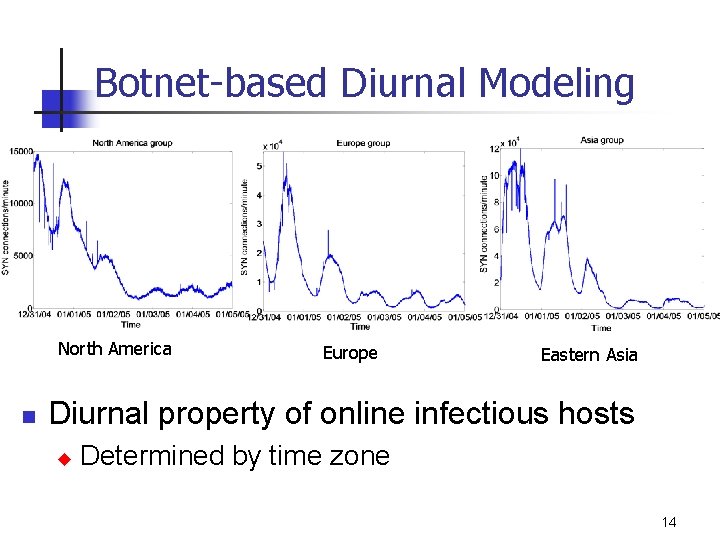
Botnet-based Diurnal Modeling North America n Europe Eastern Asia Diurnal property of online infectious hosts u Determined by time zone 14

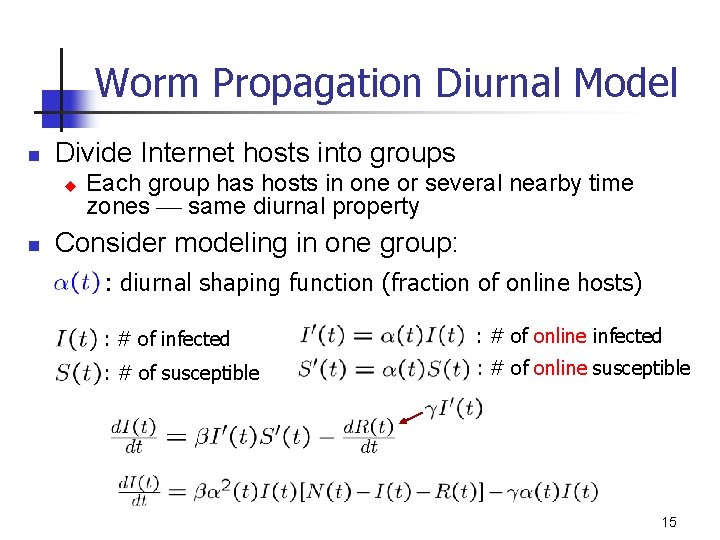
Worm Propagation Diurnal Model n Divide Internet hosts into groups u n Each group has hosts in one or several nearby time zones same diurnal property Consider modeling in one group: : diurnal shaping function (fraction of online hosts) : # of infected : # of online infected : # of susceptible : # of online susceptible 15

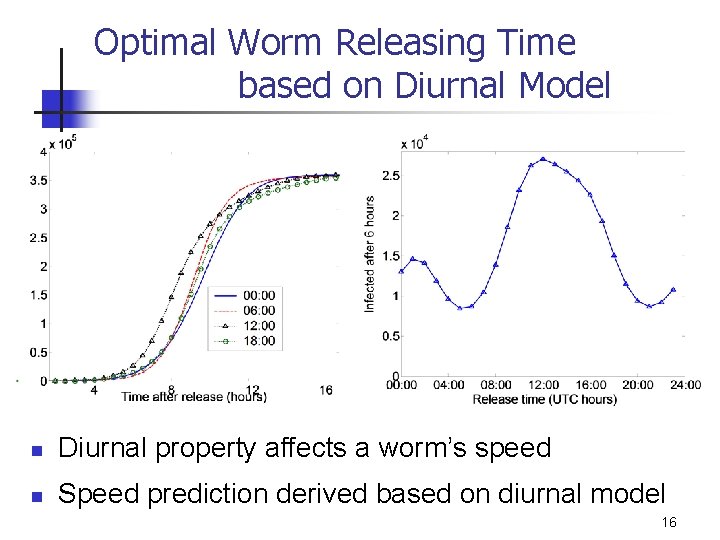
Optimal Worm Releasing Time based on Diurnal Model n Diurnal property affects a worm’s speed n Speed prediction derived based on diurnal model 16

Outline n Worm propagation modeling n Early warning of an unknown worm n Autonomous defense n Summary and current work 17

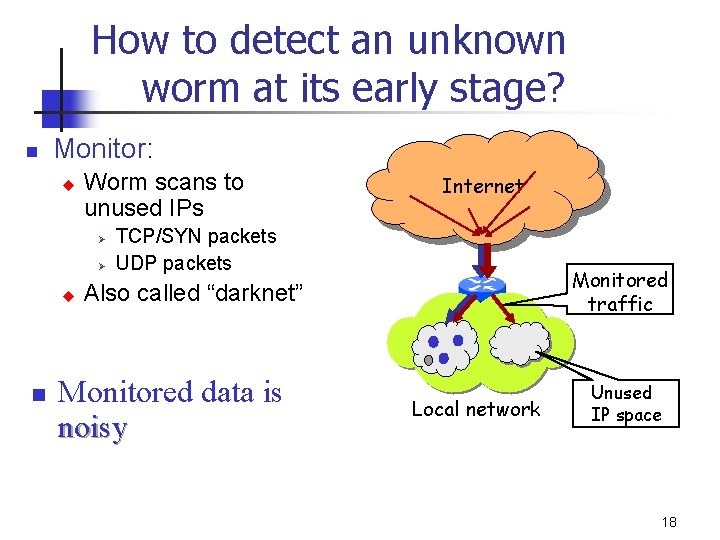
How to detect an unknown worm at its early stage? n Monitor: u Worm scans to unused IPs Ø Ø u n Internet TCP/SYN packets UDP packets Monitored traffic Also called “darknet” Monitored data is noisy Local network Unused IP space 18

Reflection n Worm anomaly other anomalies? u n A worm has its own propagation dynamics Deterministic models appropriate for worms Can we take advantage of worm model to detect a worm? 19

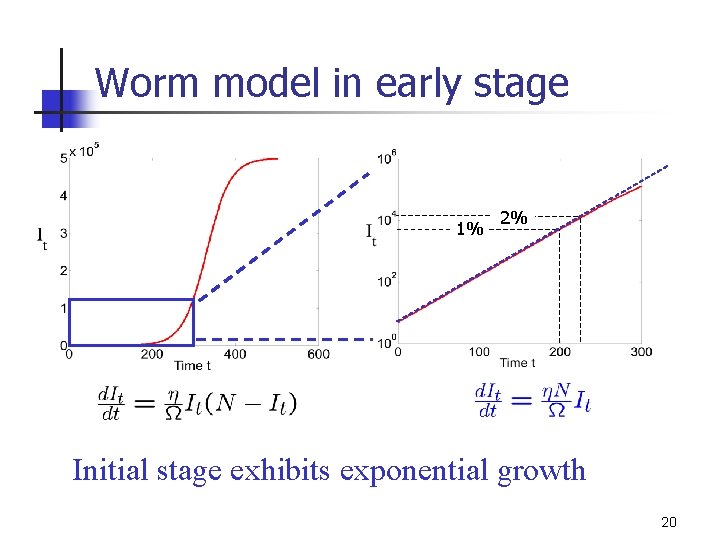
Worm model in early stage 1% 2% Initial stage exhibits exponential growth 20

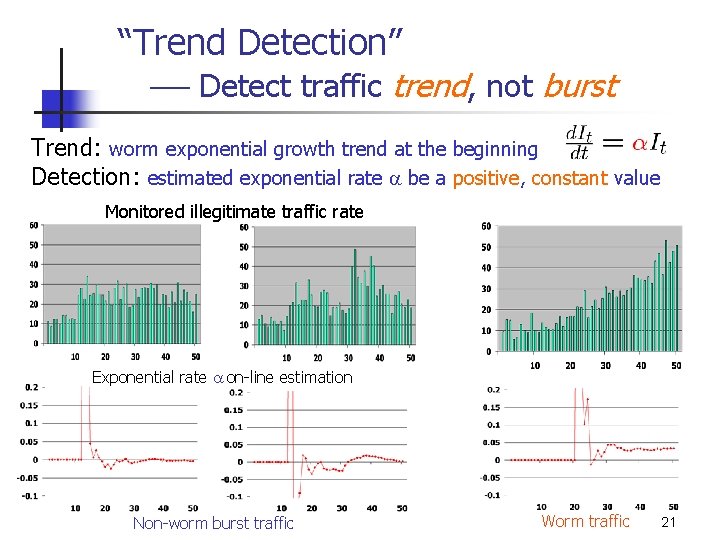
“Trend Detection” Detect traffic trend, not burst Trend: worm exponential growth trend at the beginning Detection: estimated exponential rate a be a positive, constant value Monitored illegitimate traffic rate Exponential rate a on-line estimation Non-worm burst traffic Worm traffic 21

Why exponential growth at the beginning? n n n Attacker’s incentive: infect as many as possible before people’s counteractions If not, a worm does not reach its spreading speed limit Slow spreading worm detected by other ways u Security experts manual check u Honeypot, … 22

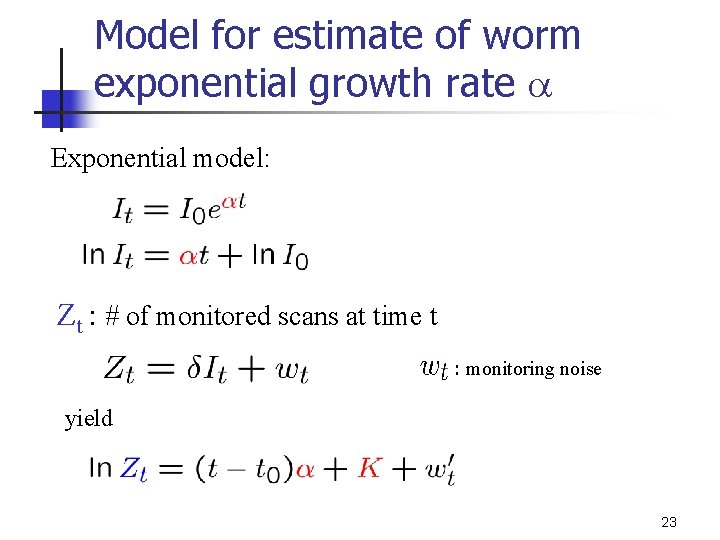
Model for estimate of worm exponential growth rate a Exponential model: Zt : # of monitored scans at time t : monitoring noise yield 23

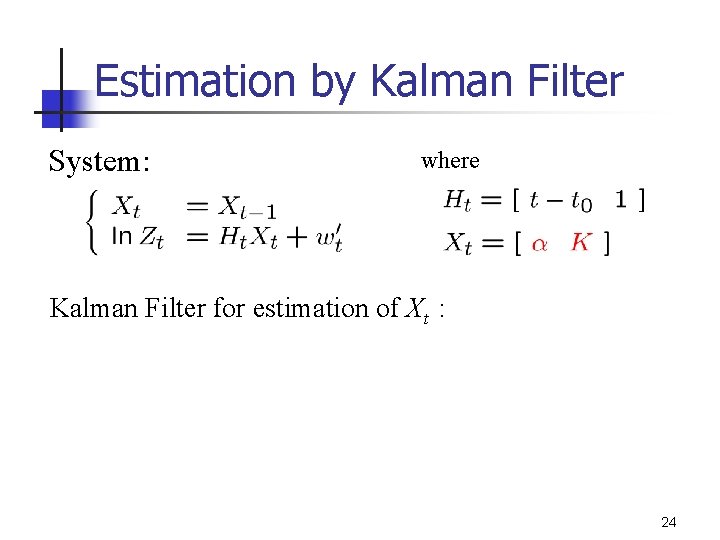
Estimation by Kalman Filter System: where Kalman Filter for estimation of Xt : 24

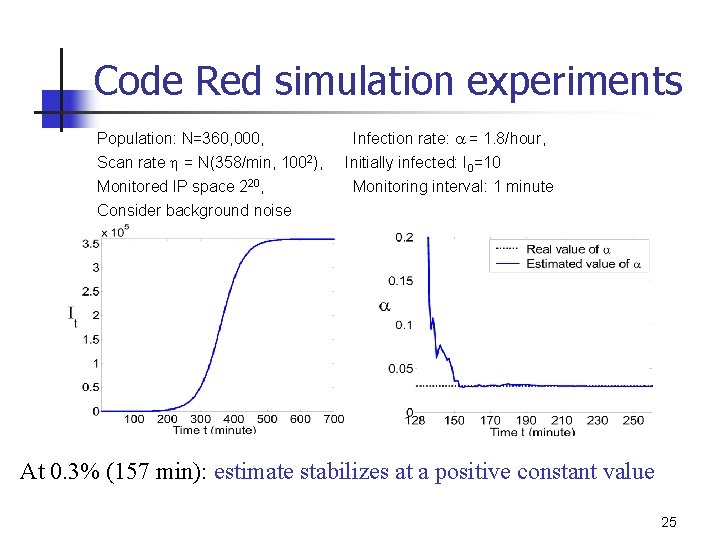
Code Red simulation experiments Population: N=360, 000, Scan rate h = N(358/min, 1002), Monitored IP space 220, Infection rate: a = 1. 8/hour, Initially infected: I 0=10 Monitoring interval: 1 minute Consider background noise At 0. 3% (157 min): estimate stabilizes at a positive constant value 25

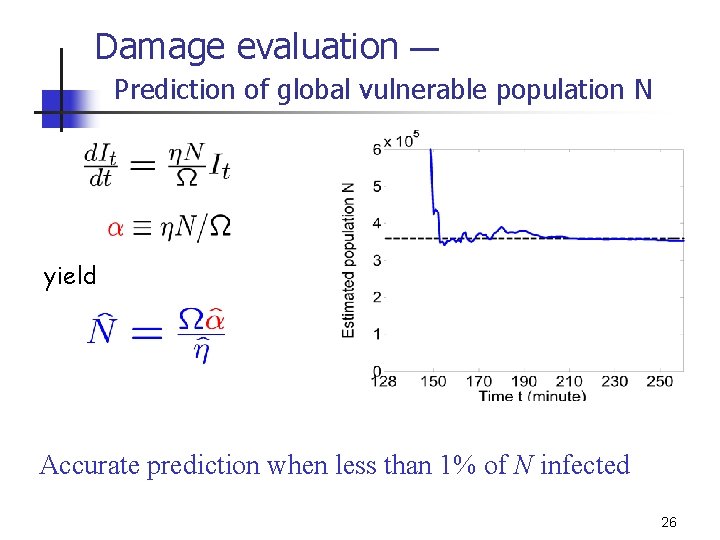
Damage evaluation — Prediction of global vulnerable population N yield Accurate prediction when less than 1% of N infected 26

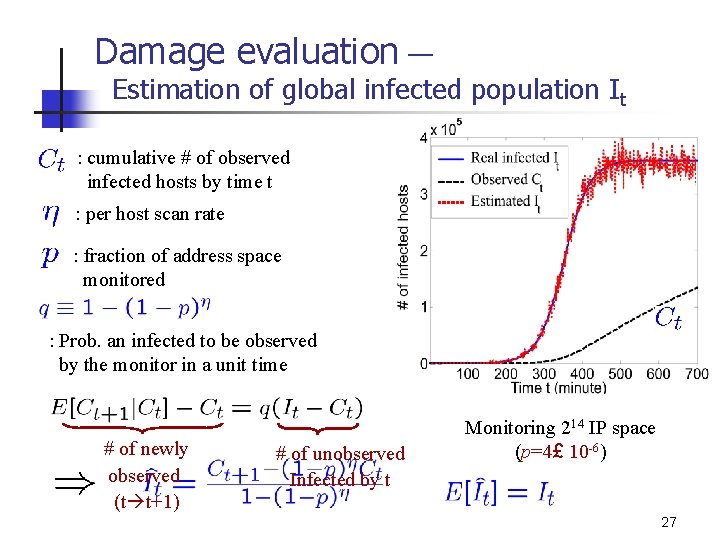
Damage evaluation — Estimation of global infected population It : cumulative # of observed infected hosts by time t : per host scan rate : fraction of address space monitored : Prob. an infected to be observed by the monitor in a unit time # of newly observed (t t+1) # of unobserved Infected by t Monitoring 214 IP space (p=4£ 10 -6) 27

Outline n Worm propagation modeling n Early warning of an unknown worm n Autonomous defense n Summary and current work 28

Autonomous defense principles n Principle #1 Preemptive Quarantine Compared to attack potential damage, we are willing to tolerate some false alarm cost u Quarantine upon suspicious, confirm later u Basis for our Dynamic Quarantine [WORM’ 03] u n Principle #2 Adaptive Adjustment More serious attack, more aggressive defense u At any time t, minimize: u (attack damage cost) + (false alarm cost) 29

Self-tuning defense against various network attacks n Principle #2 : Adaptive Adjustment u n More severe attack, more aggressive defense Self-tuning defense system designs: u u u SYN flood Distributed Denial-of-Service (DDo. S) attack Internet worm infection DDo. S attack with no source address spoofing 30

Motivation of self-tuning defense : False positive prob. blocking normal traffic 1 Severe attack : False negative prob. missing attack traffic : Detection sensitivity Light attack : Fraction of attack in traffic 0 1 Q: Which operation point is “good”? A: All operation points are good Optimal one depends on attack severity p 31

Estimation of attack severity p Filter Passed Dropped Incoming : Fraction of detected traffic # of incoming attack traffic # of incoming normal traffic Unbiased 32

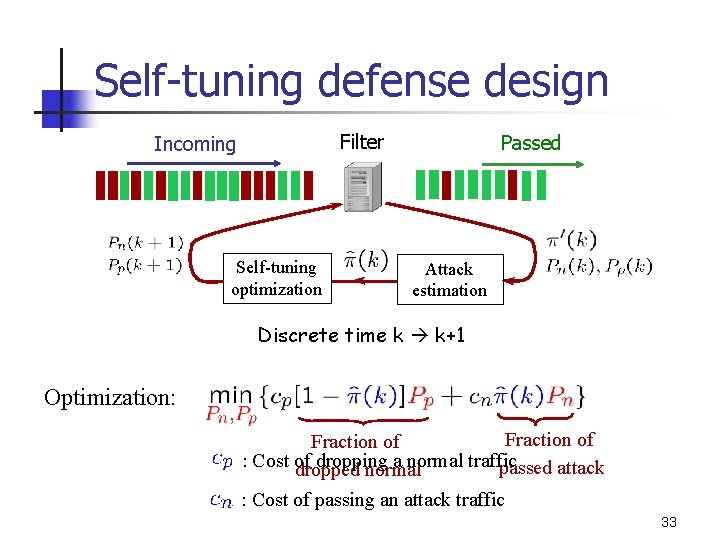
Self-tuning defense design Filter Incoming Self-tuning optimization Passed Attack estimation Discrete time k k+1 Optimization: Fraction of : Cost of dropping a normal traffic passed attack dropped normal : Cost of passing an attack traffic 33

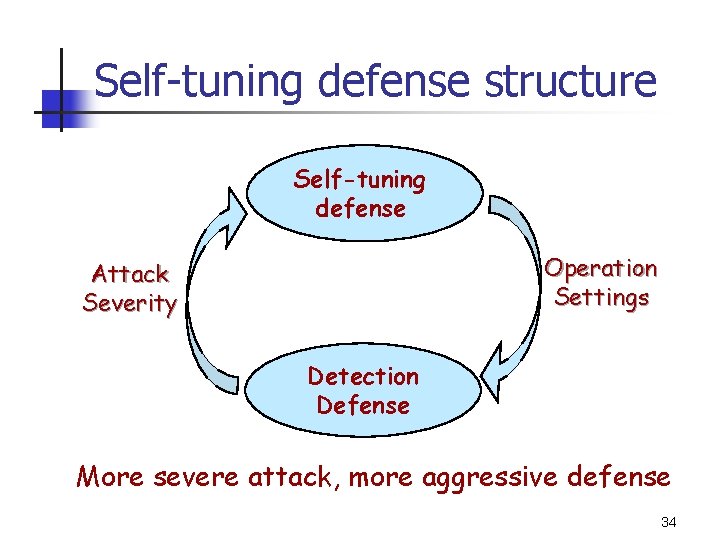
Self-tuning defense structure Self-tuning defense Operation Settings Attack Severity Detection Defense More severe attack, more aggressive defense 34

Outline n Worm propagation modeling n Early warning of an unknown worm n Autonomous defense n Summary and current work 35

Worm research contribution n Worm modeling: u u n Early detection: u u n Detection based on “exponential growth trend” Estimate/predict worm potential damage Autonomous defense: u u n Two-factor model: Human counteractions; network congestion Diurnal modeling; worm scanning strategies modeling Dynamic quarantine (interviewed by NPR) Self-tuning defense (patent filed by AT&T) Email-based worm modeling and defense 36