Mobile Computing Security Issues Advisor Dr Celeste Team

Mobile Computing - Security Issues Advisor : Dr. Celeste Team Number : 6 941633 張耕瑋 941634 黃峻亨 941636 楊銘鴻 941641 李昌諭 941718 吳政穎 941635 陳建廷

Outline Introduction to Mobile Computing Security Issues of Mobile Computing Security Policies Security Prevent Applications and Enterprise Case
Introduction Definition ◦ Mobile computing & Ubiquitous computing Features ◦ Technical and other limitations of mobile computing 9 Insufficient bandwidth 9 Security standards 9 Power consumption 9 Transmission interferences 9 Potential health hazards 9 Human interface with device 。Wireless communication and network
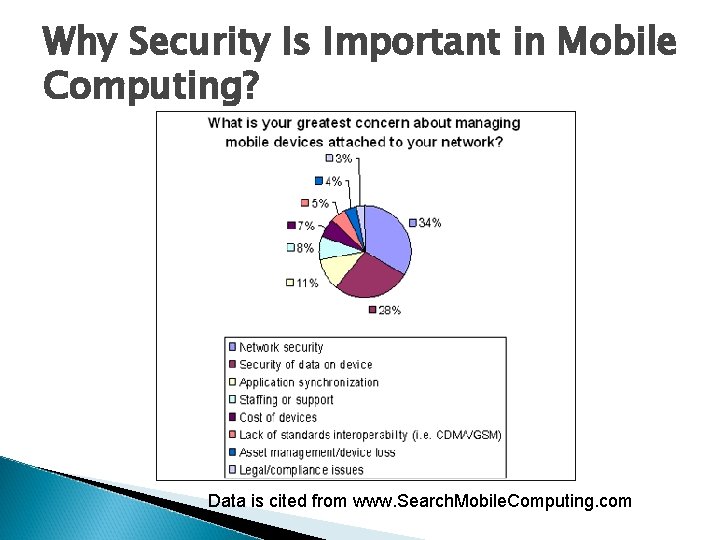
Why Security Is Important in Mobile Computing? Data is cited from www. Search. Mobile. Computing. com
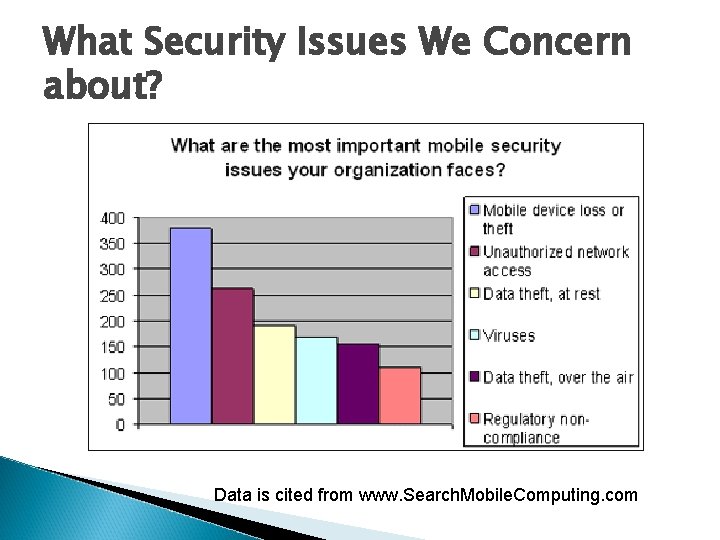
What Security Issues We Concern about? Data is cited from www. Search. Mobile. Computing. com

Security Issues of Wireless Network Security is major issue ◦ Protection of Mobile Devices ◦ Software Security – program vulnerabilities ◦ Security Protocols - authentication Different architecture has different security vulnerabilities

Information Security Threat Common security threat in wireless network can be categorized into two types: ◦ Passive - difficult to detect ◦ Active – possible to detect

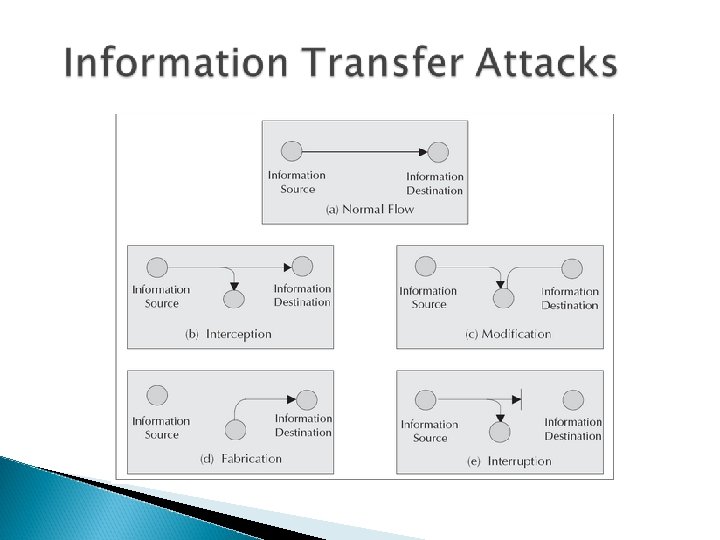
Information Transfer Attacks Interception Modification Fabrication Interruption

Information Attacks Virus and Worms Denial of Service Intrusion

Instances 911 Virus Palm. OS/Liberty. Crack

How to Prevent? Security policies! Symbian: Protect your data, not just your device Technical support

Basic Concepts in Security Confidentiality Integrity Availability Authorization Dependability and Reliability Accountability

Securities Policies We need A process when devices be stole Security policy between wired network and wireless network A mechanism to manage carrier who has secret data Standard to control virus, worm… Hierarchy certificate mechanism

Security Policies Information security Network security Device security People training

Security Policy in Hotspot ◦ Hotspot is the location supply LAN that is open for public. ◦ Data transfer don’t encrypt. Hotspot Security ◦ Establish system to prevent fake Hotspot Service ◦ Turn off the Ad-hoc network mode ◦ Don’t set auto-connect to AP ◦ Pre-set to use VPN Mobile Computing Security ◦ Don’t use trusted network and un-trusted network at same time
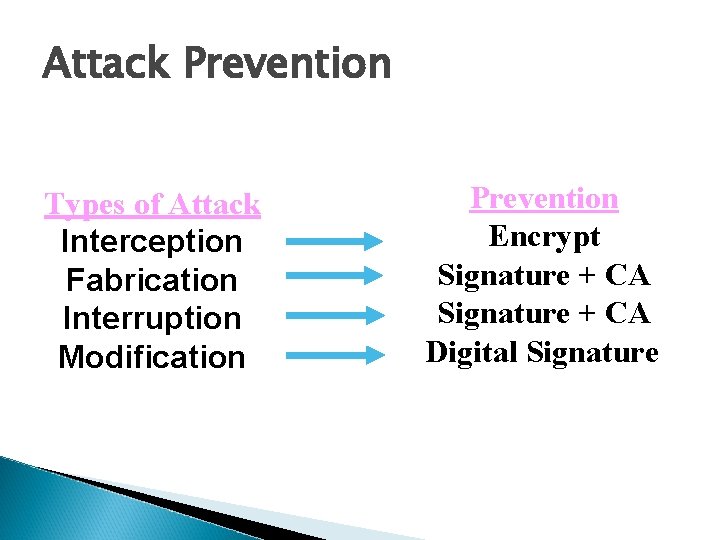
Attack Prevention Types of Attack Interception Fabrication Interruption Modification Prevention Encrypt Signature + CA Digital Signature
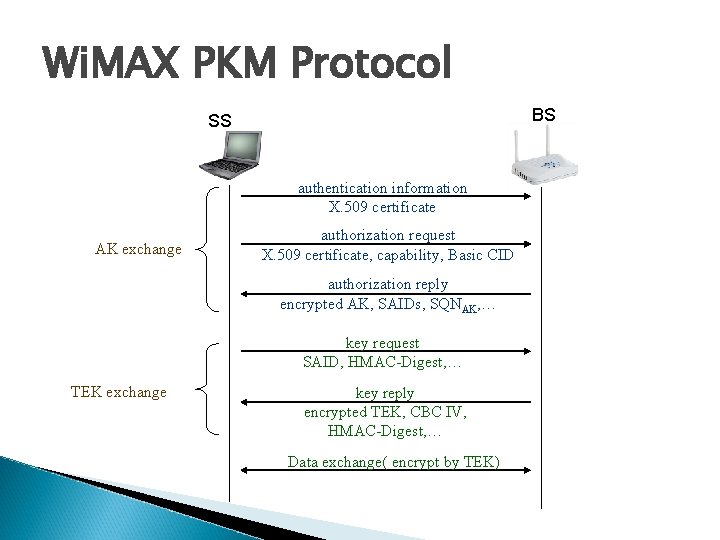
Wi. MAX PKM Protocol BS SS authentication information X. 509 certificate AK exchange authorization request X. 509 certificate, capability, Basic CID authorization reply encrypted AK, SAIDs, SQNAK, … key request SAID, HMAC-Digest, … TEK exchange key reply encrypted TEK, CBC IV, HMAC-Digest, … Data exchange( encrypt by TEK)

WAYs To Prevent Encrypt Separate risks Firewall Redact
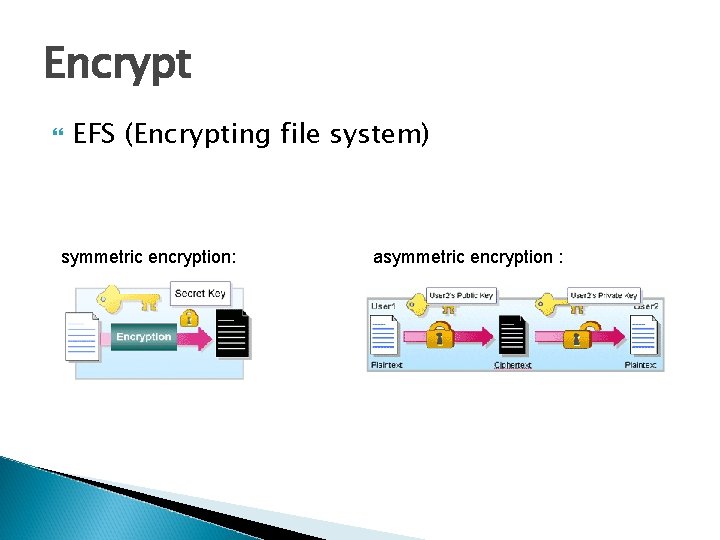
Encrypt EFS (Encrypting file system) symmetric encryption: asymmetric encryption :

Encrypt Two-factor authentication password IC Card + Or others :
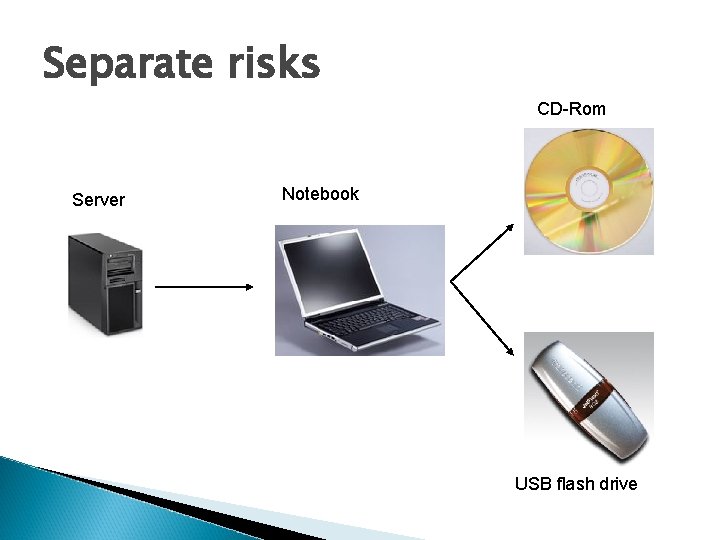
Separate risks CD-Rom Server Notebook USB flash drive
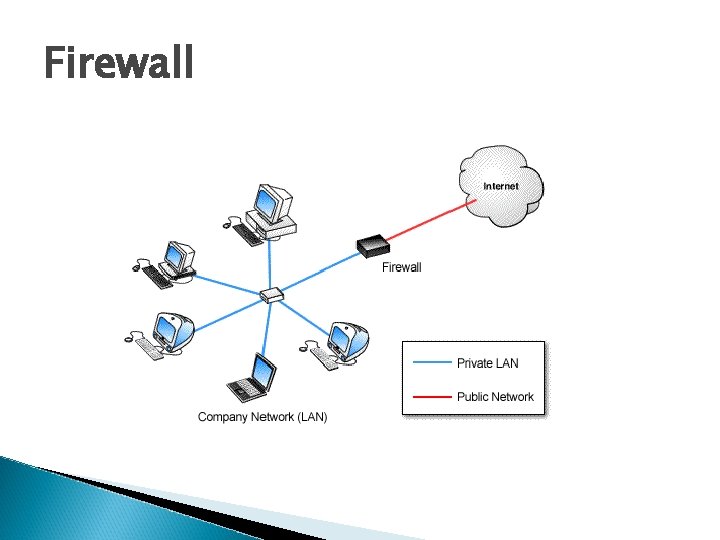
Firewall
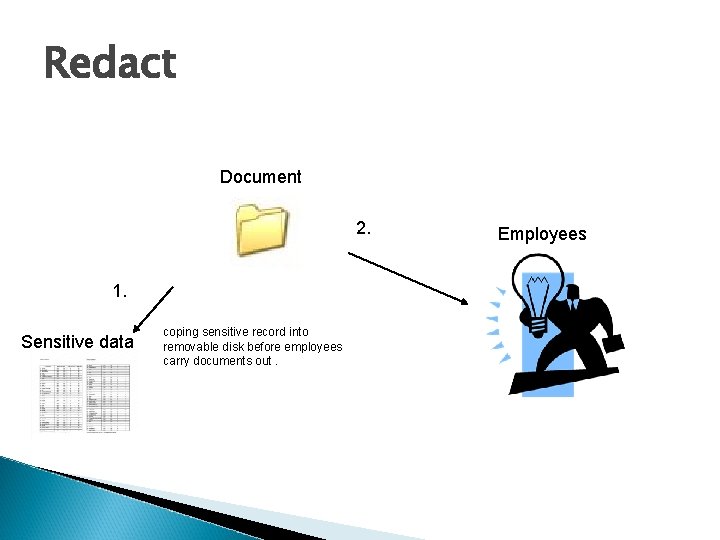
Redact Document 2. 1. Sensitive data coping sensitive record into removable disk before employees carry documents out. Employees

Enterprise case Notebook computer PDA

The Security in Mobile Phone Beginning of Mobile Phone Virus Recent Viruses The Way Viruses Infect Problems of Anti-Virus

Main Reference Wikipedia www. searchmobilecomputing. com www. zdnet. com. tw Security in Distributed, Grid, Mobile, and Pervasive Computing by Yang Xiao www. cert. org. tw/index. php www. cio. com

Thank you for listening!
- Slides: 28