Mobile Computing and Wireless Communication 2170710 Unit 4

Mobile Computing and Wireless Communication (2170710) Unit – 4: Wireless LAN Prof. Maulik Trivedi � 9998265805 � maulik. trivedi@darshan. ac. in Computer Engineering Darshan Institute of Engineering & Technology

Topics to be covered § § § Introduction of WAN Advantages of Wireless LAN Applications of WLAN IEEE WLAN Standard Type of WLAN Ad-hoc Vs. Infrastructure Mode IEEE 802. 11 Architecture Wired Equivalent Privacy (WEP) WEP Algorithm 802. 1 X Authentication 3 G vs. WIFI Unit: 4 – Mobile Computing and Wireless Communication 2 Darshan Institute of Engineering & Technology
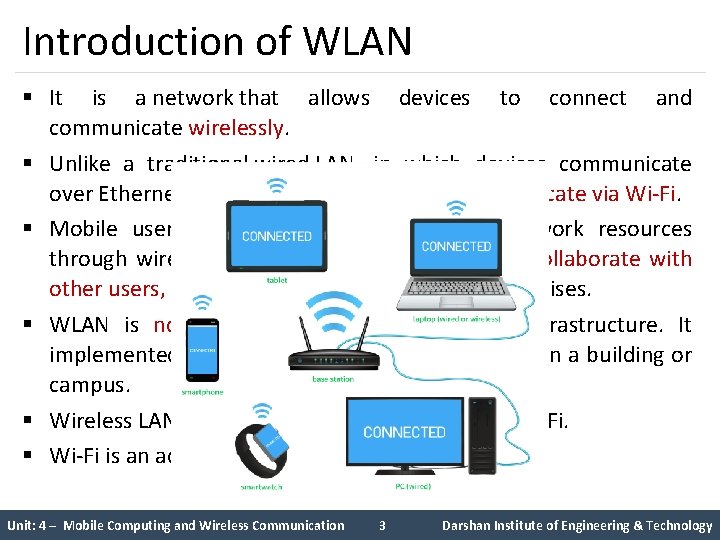
Introduction of WLAN § It is a network that allows devices to connect and communicate wirelessly. § Unlike a traditional wired LAN, in which devices communicate over Ethernet cables, devices on a WLAN communicate via Wi-Fi. § Mobile users can access information and network resources through wireless LAN as they attend meetings, collaborate with other users, or move to other locations in the premises. § WLAN is not a replacement for the wired infrastructure. It implemented as an extension to a wired LAN within a building or campus. § Wireless LAN is commercially known as WIFI or Wi-Fi. § Wi-Fi is an acronym for Wireless Fidelity. Unit: 4 – Mobile Computing and Wireless Communication 3 Darshan Institute of Engineering & Technology
Advantages of WLAN § Mobility § Low Implementation Cost § Installation Speed and Simplicity § Network Expansion § Reduced Cost-of-Ownership § Reliability § Scalability § Usage of ISM band Unit: 4 – Mobile Computing and Wireless Communication 4 Darshan Institute of Engineering & Technology
Applications of WLAN § Office/Campus Environment § Factory Shop Floor § Home § Workgroup Environment § Heritage Buildings § Public Places § War/Defense Sites Unit: 4 – Mobile Computing and Wireless Communication 5 Darshan Institute of Engineering & Technology
IEEE 802. 11 Wireless LAN Standard § IEEE 802. 11 standard for wireless LAN operations at a data rate up to 2 Mbps in the 2. 4 GHz Industrial, Scientific, and Medical(ISM) band. § 802. 11 and 802. 11 x refer to a family of specifications developed by the IEEE for wireless LAN (WLAN) technology. § 802. 11 specifies an over-the-air interface between a wireless client and a base station or between two wireless clients. § The IEEE accepted the specification in the year 1997. Unit: 4 – Mobile Computing and Wireless Communication 6 Darshan Institute of Engineering & Technology
Specification in IEEE 802. 11 There are several specifications in the 802. 11 families: § 802. 11 a − This is an extension to 802. 11 that pertains to wireless LANs and goes as fast as 54 Mbps in the 5 -GHz band. § 802. 11 b − The 802. 11 high rate Wi. Fi is an extension to 802. 11 that pertains to wireless LANs and yields a connection as fast as 11 Mbps transmission (with a fallback to 5. 5, 2, and 1 Mbps depending on the strength of signal) in the 2. 4 -GHz band. § 802. 11 g − This pertains to wireless LANs and provides 20+ Mbps in the 2. 4 -GHz band. Unit: 4 – Mobile Computing and Wireless Communication 7 Darshan Institute of Engineering & Technology
Types of WLAN § 802. 11 § Hyper. LAN (or Hiper. LAN) § Home. RF § Ad-hoc Network § Bluetooth Unit: 4 – Mobile Computing and Wireless Communication 8 Darshan Institute of Engineering & Technology
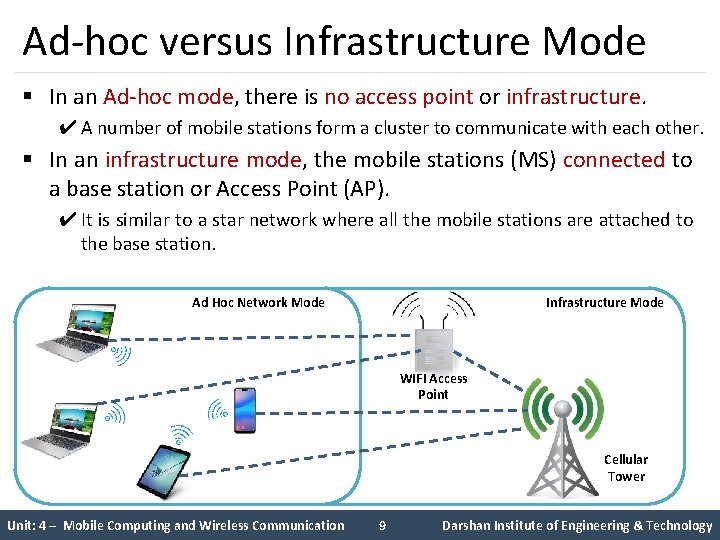
Ad-hoc versus Infrastructure Mode § In an Ad-hoc mode, there is no access point or infrastructure. ✔ A number of mobile stations form a cluster to communicate with each other. § In an infrastructure mode, the mobile stations (MS) connected to a base station or Access Point (AP). ✔ It is similar to a star network where all the mobile stations are attached to the base station. Ad Hoc Network Mode Infrastructure Mode WIFI Access Point Cellular Tower Unit: 4 – Mobile Computing and Wireless Communication 9 Darshan Institute of Engineering & Technology
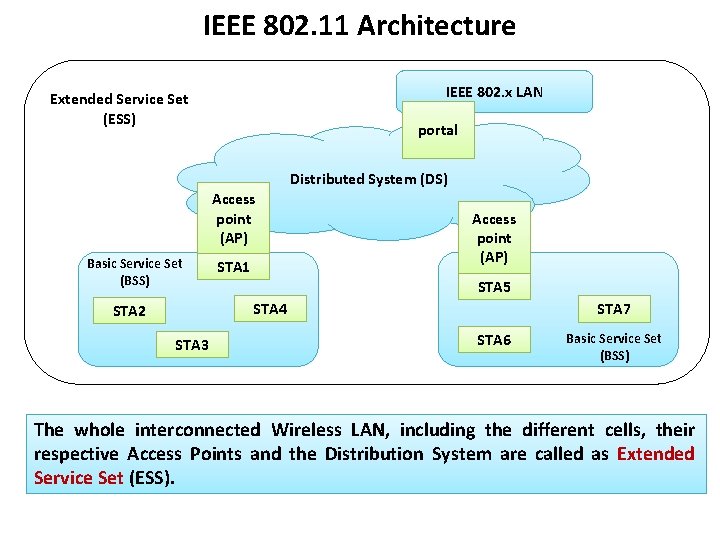
IEEE 802. 11 Architecture IEEE 802. x LAN Extended Service Set (ESS) portal Distributed System (DS) Access point (AP) Basic Service Set (BSS) STA 1 Access point (AP) STA 5 STA 4 STA 2 STA 3 STA 7 STA 6 Basic Service Set (BSS) The whole In the 802. 11 architecture, one cell or a BSS is controlled by one Base Station. Although This backbone is called Distribution System (or DS). a wireless interconnected LAN may Wireless be formed LAN, by including a single cell, the different with a single cells, Access their This base station is called Access Point or AP in short. Point, most installations will be formed by several cells, where the access points This backbone is typically Ethernet and, in some cases, is wireless itself. respective Access Points and the Distribution System are called as Extended are connected through some kind of backbone. Service Set (ESS).
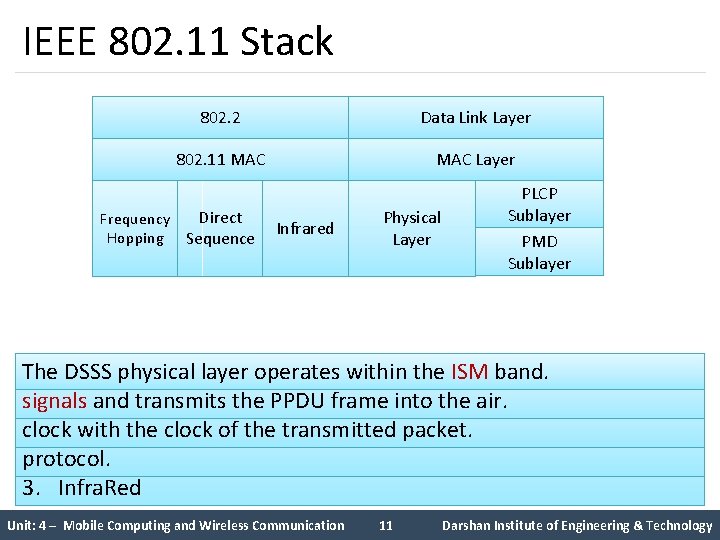
IEEE 802. 11 Stack 802. 2 Data Link Layer 802. 11 MAC Layer Direct Frequency Hopping Sequence Infrared Physical Layer PLCP Sublayer PMD Sublayer The DSSS physical layer operates within the ISM band. PLCP The Physical Medium Dependent (PMD): PMD Frequency Hopping Spread Spectrum (FHSS) Layer: FHSS PMD is responsible for converting the binary bit sequence into DSSS PLCP is responsible for synchronizing and receiving the data bits FHSS PMD does this using the frequency hopping technique. DSSS standard 802. 11 PLCP PMD layer sub also translates layer prepares standards currently delivers provides the cover defines the binary MAC the incoming definitions a modulation/demodulation digital Protocol single sequence frames MAC, for Data both which from Unit into MAC interacts the analog (MPDU) (Medium wireless of radio with the for The architecture of the Physical layer comprises of the two sub layers Physical Layer Convergence Procedure (PLCP): Access Control) and Physical Layer. three Physical Sublayers: transmission. medium to the MAC layer. The PMD provides the actual transmission and reception of physical transmission. The layer carries the clocking information to synchronize the receiver analog signal and transmit the PPDU frame into the air. correctly. signals and transmits the PPDU frame into the air. for each station: PLCP sub layer is responsible for the Carrier Sense (CS) part of the layer entities between stations through the wireless media. clock with the clock of the transmitted packet. Frequency Hopping Spread Spectrum 1. Physical Layer Convergence Procedure (PLCP) Carrier Sense Multiple Access/Collision Avoidance (CSMA/CA) Direct Sequence Spread Spectrum 2. Physical Medium Dependent (PMD) protocol. 3. Infra. Red Unit: 4 – Mobile Computing and Wireless Communication 11 Darshan Institute of Engineering & Technology
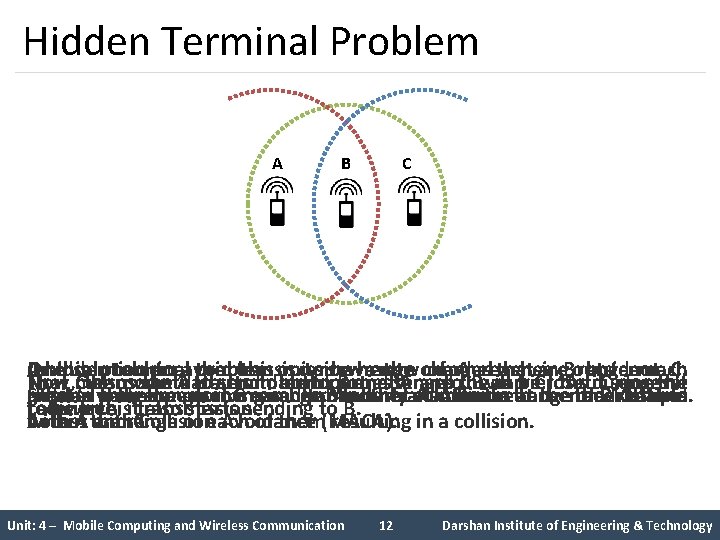
Hidden Terminal Problem A B C One In A hidden terminal problem occurs when two nodes that are outside each this solution problem, to avoid the transmission this is to have range the channel of A reaches sensing B range but not much C. Now, the node A starts to send something to B and C, but C doesn’t Now C also wants to send data to B and senses the carrier. As it senses it That means the data from both parties A and C will be lose during the Similarly, the range of C reaches B but not A. Also the range of B reaches other’s greater than the receiving range. Another solution is to use the Multiple range performs simultaneous transmission to a node that is Hidden nodes mean increased probability of collision at the receiver end. receive this transmission. to be free, it also starts sending to B. collision. both A and C. within the range of each of them resulting in a collision. Access with Collision Avoidance (MACA). Unit: 4 – Mobile Computing and Wireless Communication 12 Darshan Institute of Engineering & Technology
Wired Equivalent Privacy (WEP) § Wired Equivalent Privacy (WEP) is a security algorithm for IEEE 802. 11 wireless networks. § WEP was designed to protect users of a WLAN from casual eavesdropping. § It was intended to offer the following facilities: 1. Reasonably strong encryption - It relies on the difficulty of recovering the secret key through a brute force attack. The difficulty grows with the key length. 2. Self-synchronizing - Each packet contains the information required to decrypt it. There is no need to deal with lost packets. 3. Efficient - It can implement in software with reasonable efficiency. 4. Exportable - Limiting the key length leads to a greater possibility of export. Unit: 4 – Mobile Computing and Wireless Communication 13 Darshan Institute of Engineering & Technology
WEP – Cont… § The WEP algorithm is the RC 4 cryptographic algorithm from RSA data security. § RC 4 uses a stream cipher technique. § It is a symmetric algorithm and uses the same key for both enciphering and deciphering the data. § For each transmission, the plaintext is bitwise XORed with a pseudorandom keystream to produce ciphertext. § For decryption, the process reversed. Unit: 4 – Mobile Computing and Wireless Communication 14 Darshan Institute of Engineering & Technology

Wi-Fi Protected Access - WPA § Wi-Fi Protected Access (WPA) is a security standard to secure computers connected to a Wi-Fi network. § It was developed in response to the weaknesses of WEP (Wired Equivalent Privacy) and therefore improves on WEP's authentication and encryption features. § WPA provides two algorithms: ✔ Temporal Key Integrity Protocol (TKIP) ✔ Advanced Encryption Standard (AES) § Wi-Fi Protected Access included a 128 -bit “temporary key integrity protocol” (TKIP) which dynamically produces a new key for each data packet. Unit: 4 – Mobile Computing and Wireless Communication 15 Darshan Institute of Engineering & Technology
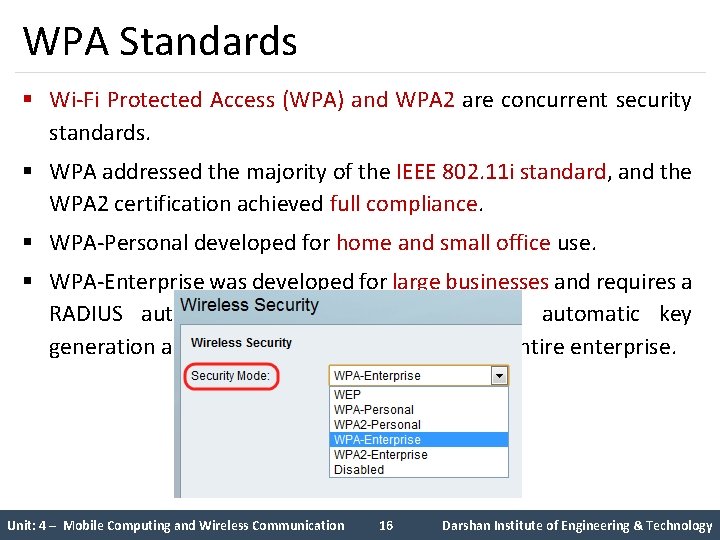
WPA Standards § Wi-Fi Protected Access (WPA) and WPA 2 are concurrent security standards. § WPA addressed the majority of the IEEE 802. 11 i standard, and the WPA 2 certification achieved full compliance. § WPA-Personal developed for home and small office use. § WPA-Enterprise was developed for large businesses and requires a RADIUS authentication server that provides automatic key generation and authentication throughout the entire enterprise. Unit: 4 – Mobile Computing and Wireless Communication 16 Darshan Institute of Engineering & Technology

Possible Attacks The possible security attacks on wireless LAN are: § Passive attack ✔ To decrypt traffic based on statistical analysis. § Active attack ✔ To inject new traffic from unauthorized mobile stations, based on known plaintext. ✔ To decrypt traffic, based on tricking the access point. § Dictionary-building attack ✔ After analysis of about a day’s worth of traffic, allows real-time automated decryption of all traffic. § Hijacking a session ✔ Following successful authentication, it is possible to perform them using the inexpensive off-the-shelf equipment. Unit: 4 – Mobile Computing and Wireless Communication 17 Darshan Institute of Engineering & Technology
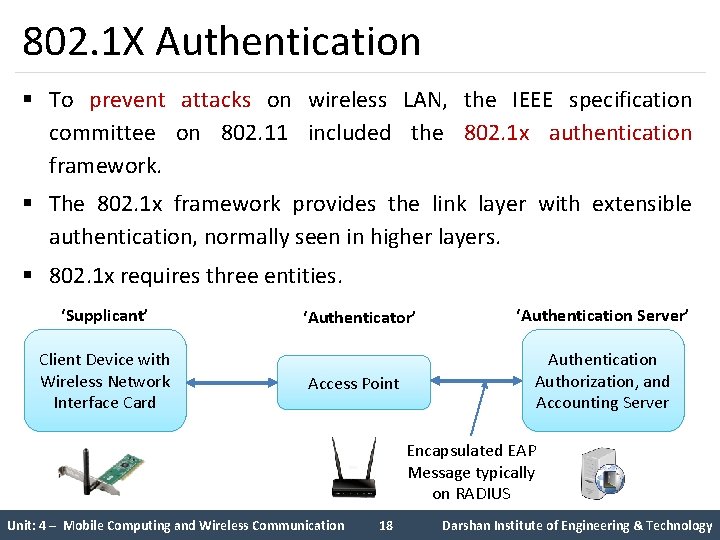
802. 1 X Authentication § To prevent attacks on wireless LAN, the IEEE specification committee on 802. 11 included the 802. 1 x authentication framework. § The 802. 1 x framework provides the link layer with extensible authentication, normally seen in higher layers. § 802. 1 x requires three entities. ‘Supplicant’ Client Device with Wireless Network Interface Card ‘Authenticator’ Access Point ‘Authentication Server’ Authentication Authorization, and Accounting Server Encapsulated EAP Message typically on RADIUS Unit: 4 – Mobile Computing and Wireless Communication 18 Darshan Institute of Engineering & Technology
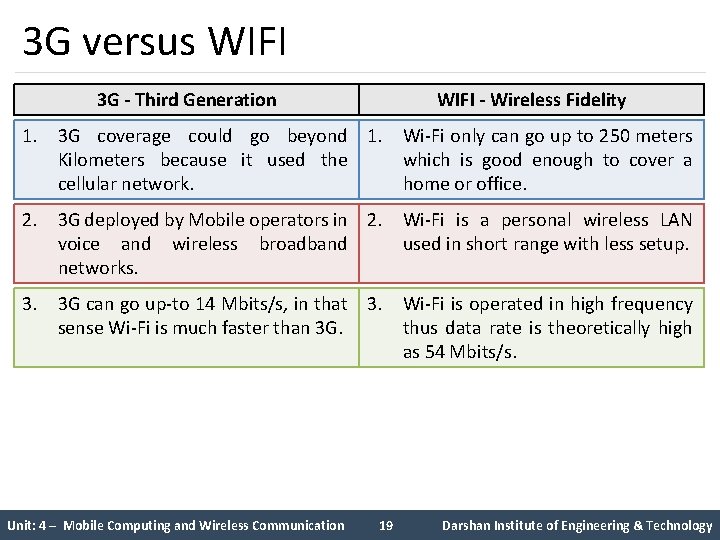
3 G versus WIFI 3 G - Third Generation WIFI - Wireless Fidelity 1. 3 G coverage could go beyond 1. Wi-Fi only can go up to 250 meters Kilometers because it used the which is good enough to cover a cellular network. home or office. 2. 3 G deployed by Mobile operators in 2. Wi-Fi is a personal wireless LAN voice and wireless broadband used in short range with less setup. networks. 3. 3 G can go up-to 14 Mbits/s, in that 3. Wi-Fi is operated in high frequency sense Wi-Fi is much faster than 3 G. thus data rate is theoretically high as 54 Mbits/s. Unit: 4 – Mobile Computing and Wireless Communication 19 Darshan Institute of Engineering & Technology
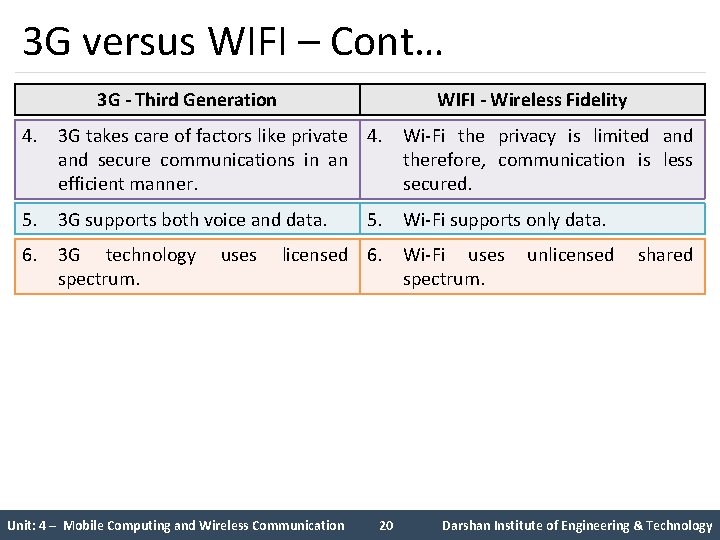
3 G versus WIFI – Cont… 3 G - Third Generation WIFI - Wireless Fidelity 4. 3 G takes care of factors like private 4. Wi-Fi the privacy is limited and secure communications in an therefore, communication is less efficient manner. secured. 5. 3 G supports both voice and data. 5. Wi-Fi supports only data. 6. 3 G technology uses licensed 6. Wi-Fi uses unlicensed shared spectrum. Unit: 4 – Mobile Computing and Wireless Communication 20 Darshan Institute of Engineering & Technology
Summary § § § Introduction (Wireless LAN) Advantages of Wireless LAN Applications of WLAN IEEE Standard Type of WLAN (802. 11, Hyper. LAN, Home. RF, Bluetooth, MANET) Adhoc Vs. Infrastructure Mode IEEE 802. 11 Architecture (IEEE 802. 11 Stack) Wired Equivalent Privacy (WEP) (Protect user of WLAN) Wi-Fi Protected Access - WPA 802. 1 X Authentication 3 G vs. WIFI Unit: 4 – Mobile Computing and Wireless Communication 21 Darshan Institute of Engineering & Technology

Thank You
- Slides: 22