Ministry of Electronics Information Technology National Informatics Centre








- Slides: 38

Ministry of Electronics & Information Technology National Informatics Centre Network Security 12/5/2020

Constantly Increasing Threats (nos. ) and Threat Severity 2 12/5/2020

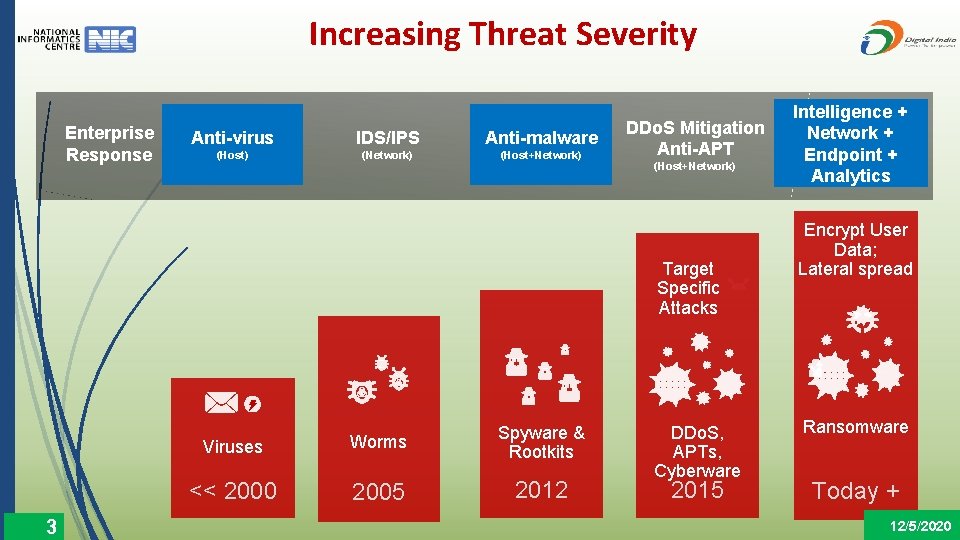
Increasing Threat Severity Enterprise Response Anti-virus IDS/IPS Anti-malware (Host) (Network) (Host+Network) DDo. S Mitigation Anti-APT (Host+Network) Target Specific Attacks 3 Viruses Worms Spyware & Rootkits << 2000 2005 2012 DDo. S, APTs, Cyberware 2015 Intelligence + Network + Endpoint + Analytics Encrypt User Data; Lateral spread Ransomware Today + 12/5/2020

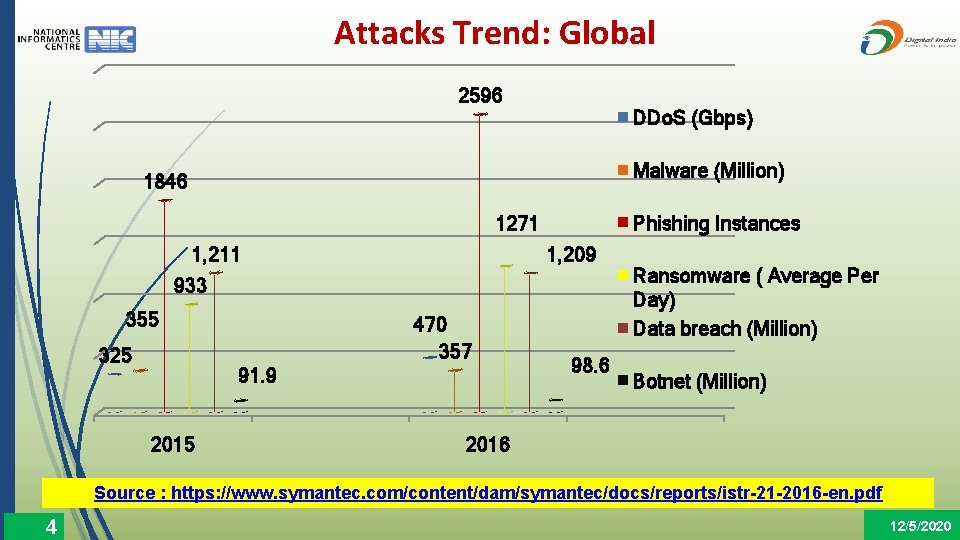
Attacks Trend: Global 2596 DDo. S (Gbps) Malware (Million) 1846 Phishing Instances 1271 1, 211 1, 209 933 355 325 470 357 91. 9 2015 98. 6 Ransomware ( Average Per Day) Data breach (Million) Botnet (Million) 2016 Source : https: //www. symantec. com/content/dam/symantec/docs/reports/istr-21 -2016 -en. pdf 4 12/5/2020

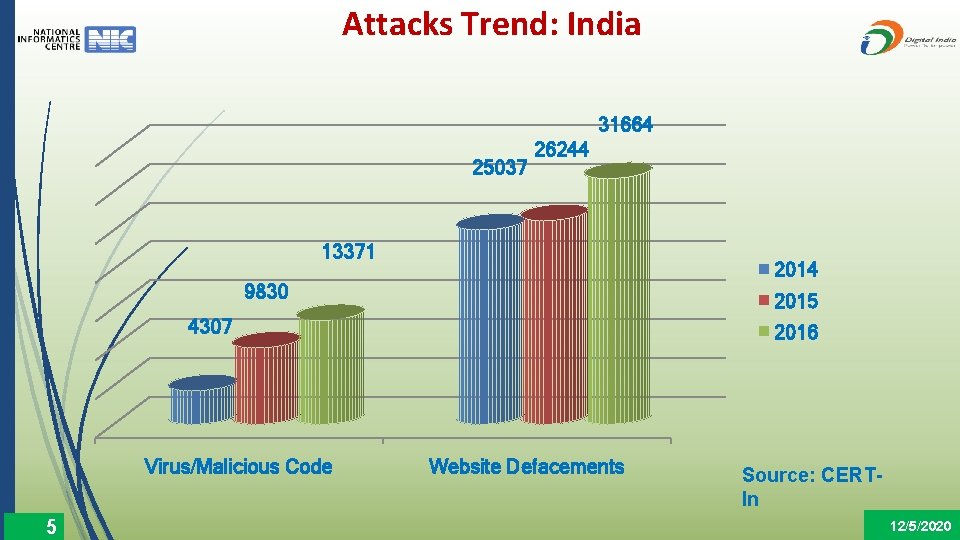
Attacks Trend: India 31664 25037 26244 13371 2014 9830 2015 4307 Virus/Malicious Code 5 2016 Website Defacements Source: CERTIn 12/5/2020

Present Security Scenario 6 12/5/2020

Cyber Attacks / Attempts • Do. S / DDo. S Attack attempts: Volumetric, Network level, Application level • Ransomware: Locky, Crypto. Wall, Wanna. Cry, Petya • Malicious Emails Ø Phishing, Spear Phishing Ø Malware Spreading Ø C&C, Bot. Net • SSL traffic Attacks • Browser Attacks • DNS, SMTP attacks • P 2 P: Bit. Torrent, Team. Viewer, Tor-Privoxy • Attempts to compromise vulnerable systems - obsolete / unpatched software, w/o AV • Zero day, Targeted attacks attempts, APTs • Unauthorized access attempts, Probes, Scans, policy violations% 7 12/5/2020

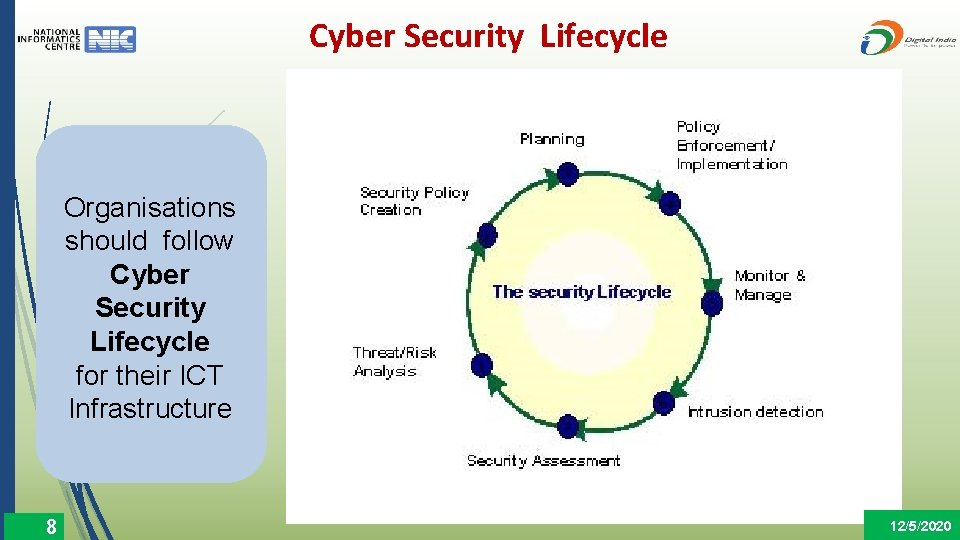
Cyber Security Lifecycle Organisations should follow Cyber Security Lifecycle for their ICT Infrastructure 8 12/5/2020

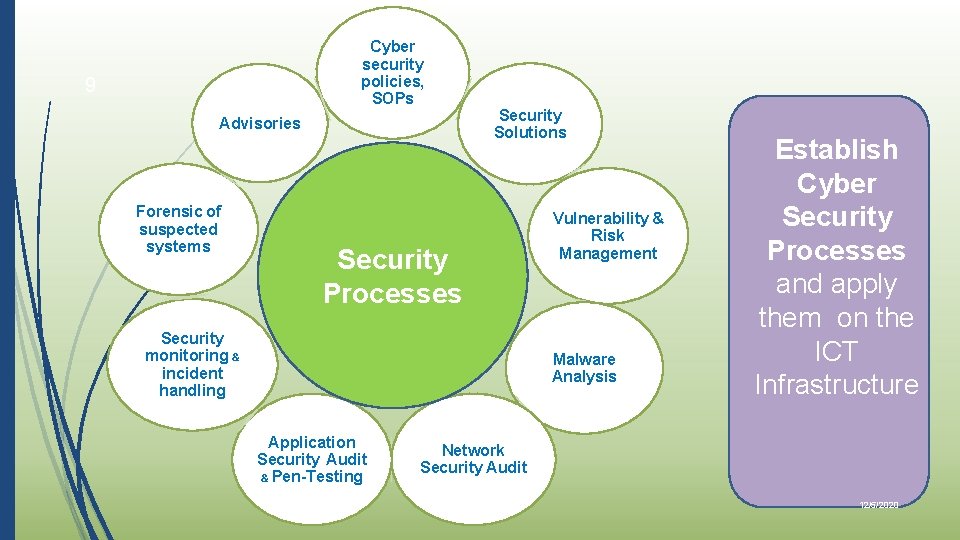
Cyber security policies, SOPs 9 Advisories Forensic of suspected systems Security Solutions Security Processes Security monitoring & incident handling Vulnerability & Risk Management Malware Analysis Application Security Audit & Pen-Testing Establish Cyber Security Processes and apply them on the ICT Infrastructure Network Security Audit 12/5/2020

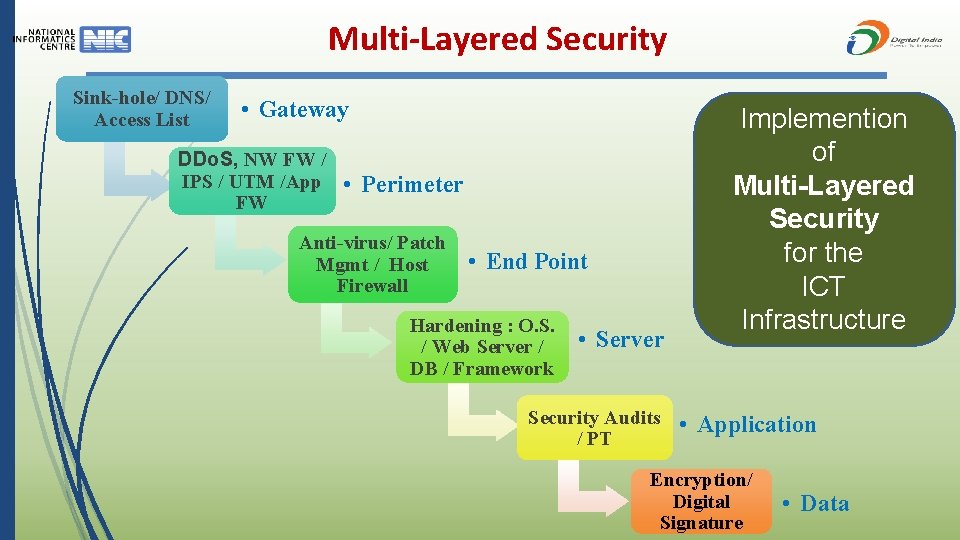
Multi-Layered Security Sink-hole/ DNS/ Access List • Gateway DDo. S, NW FW / IPS / UTM /App FW • Perimeter Anti-virus/ Patch Mgmt / Host Firewall • End Point Hardening : O. S. / Web Server / DB / Framework • Server Security Audits / PT Implemention of Multi-Layered Security for the ICT Infrastructure • Application Encryption/ Digital Signature • Data

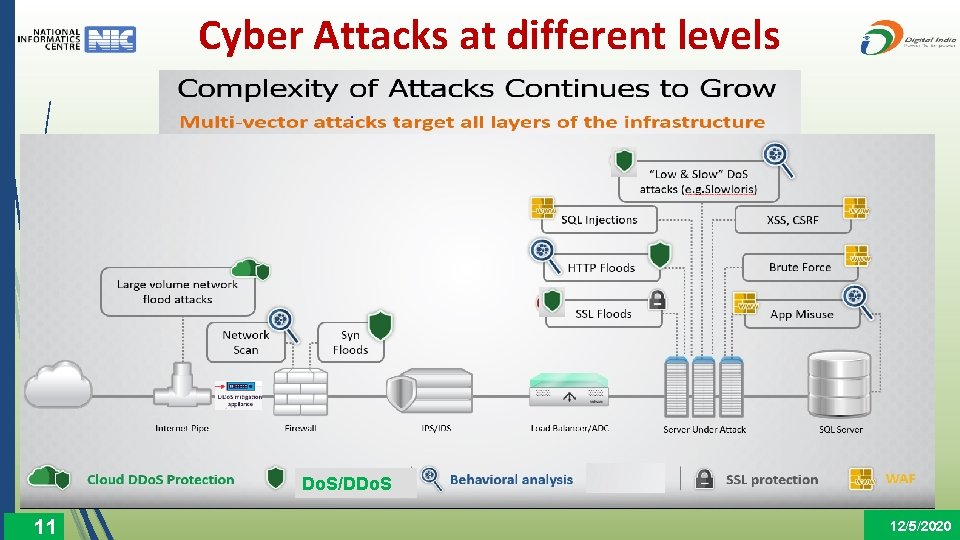
Cyber Attacks at different levels Do. S/DDo. S 11 12/5/2020

DDo. S Mitigation 12 12/5/2020

Distributed Denial Of Service Attack A DDo. S attack involves multiple connected online devices, collectively known as a botnet, which are used to overwhelm a target website with fake traffic Unlike other kinds of cyber attacks, DDo. S assaults don't attempt to breach your security perimeter. Rather, they aim to make your website and servers unavailable to legitimate users. Types of DDo. S Attacks: Ø Volumetric Ø Network Layer Ø Application Layer 13 12/5/2020

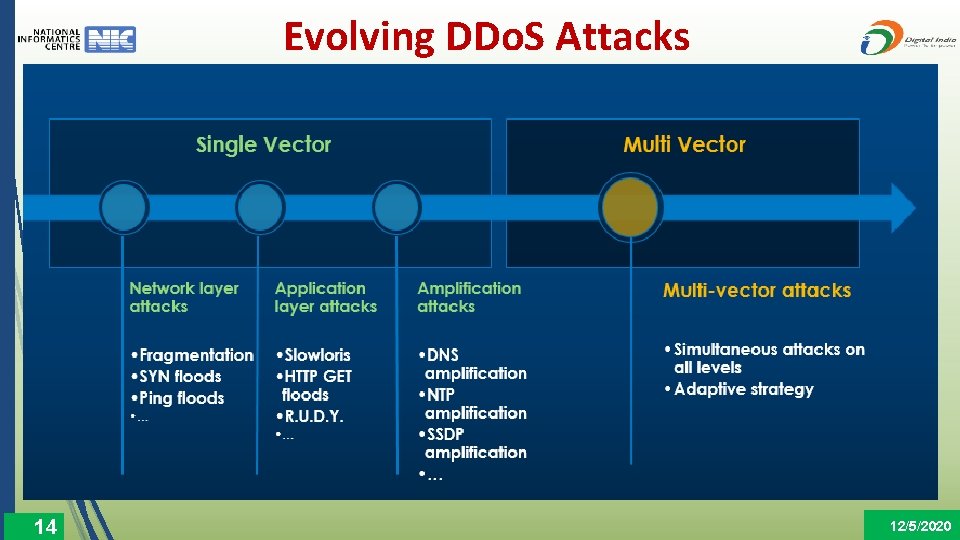
Evolving DDo. S Attacks 14 12/5/2020

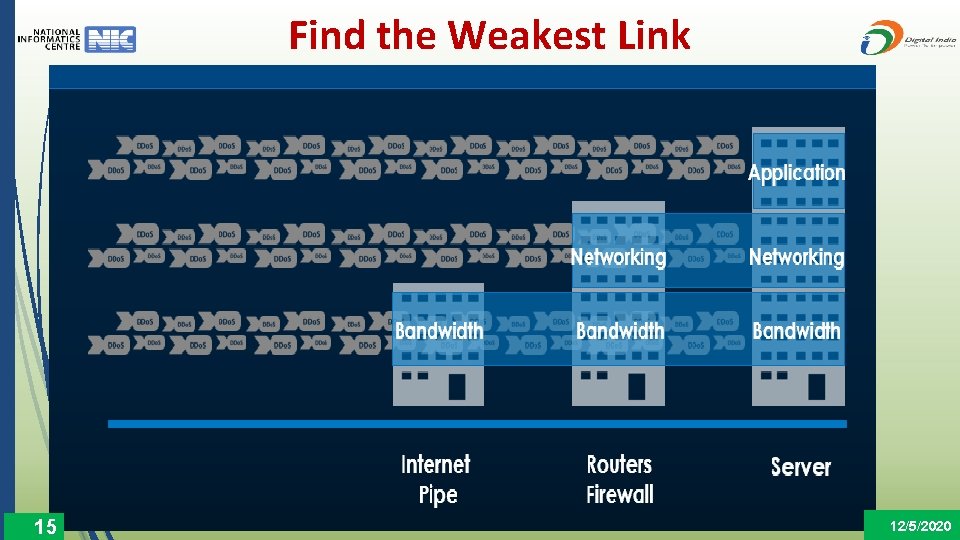
Find the Weakest Link 15 12/5/2020

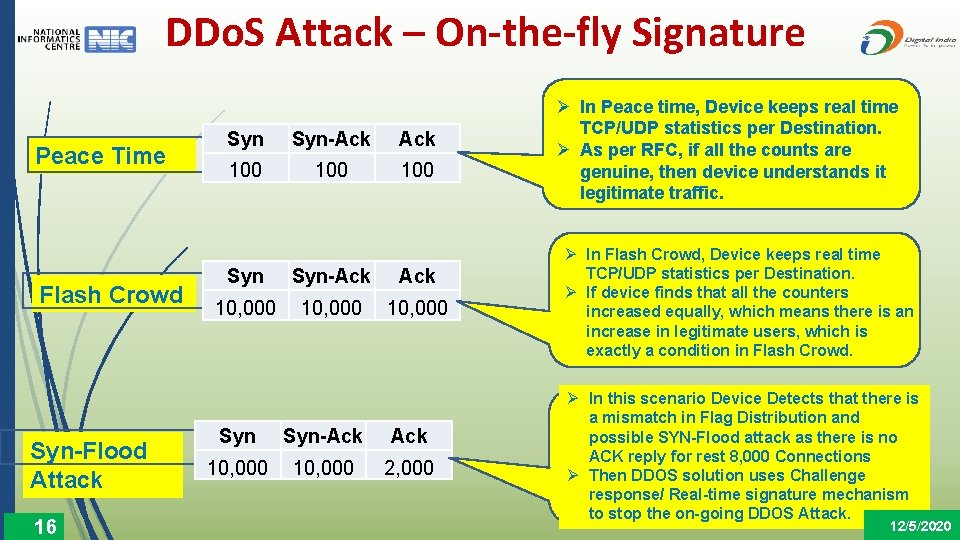
DDo. S Attack – On-the-fly Signature Peace Time Flash Crowd Syn-Flood Attack 16 Syn-Ack 100 100 Syn-Ack 10, 000 Syn-Ack 10, 000 2, 000 Ø In Peace time, Device keeps real time TCP/UDP statistics per Destination. Ø As per RFC, if all the counts are genuine, then device understands it legitimate traffic. Ø In Flash Crowd, Device keeps real time TCP/UDP statistics per Destination. Ø If device finds that all the counters increased equally, which means there is an increase in legitimate users, which is exactly a condition in Flash Crowd. Ø In this scenario Device Detects that there is a mismatch in Flag Distribution and possible SYN-Flood attack as there is no ACK reply for rest 8, 000 Connections Ø Then DDOS solution uses Challenge response/ Real-time signature mechanism to stop the on-going DDOS Attack. 12/5/2020

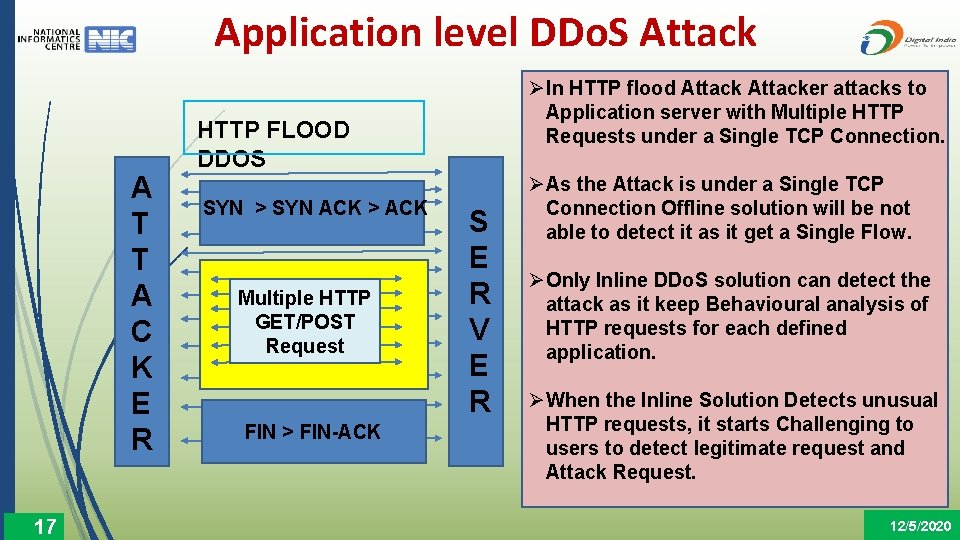
Application level DDo. S Attack A T T A C K E R 17 HTTP FLOOD DDOS SYN > SYN ACK > ACK Multiple HTTP GET/POST Request FIN > FIN-ACK S E R V E R ØIn HTTP flood Attacker attacks to Application server with Multiple HTTP Requests under a Single TCP Connection. ØAs the Attack is under a Single TCP Connection Offline solution will be not able to detect it as it get a Single Flow. ØOnly Inline DDo. S solution can detect the attack as it keep Behavioural analysis of HTTP requests for each defined application. ØWhen the Inline Solution Detects unusual HTTP requests, it starts Challenging to users to detect legitimate request and Attack Request. 12/5/2020

Intrusion Prevention System 18 12/5/2020

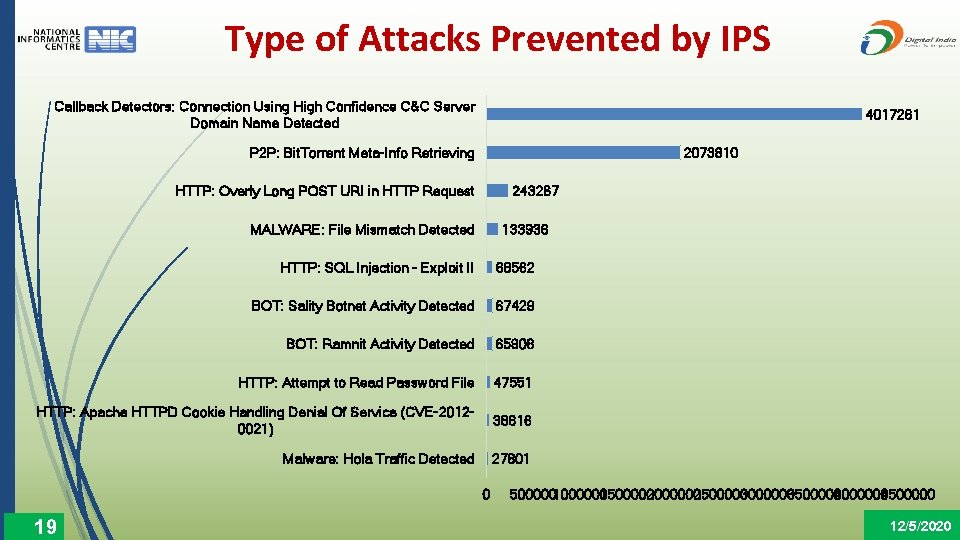
Type of Attacks Prevented by IPS Callback Detectors: Connection Using High Confidence C&C Server Domain Name Detected 4017261 2073810 P 2 P: Bit. Torrent Meta-Info Retrieving HTTP: Overly Long POST URI in HTTP Request 243267 133936 MALWARE: File Mismatch Detected HTTP: SQL Injection - Exploit II 68562 BOT: Sality Botnet Activity Detected 67429 BOT: Ramnit Activity Detected 65908 HTTP: Attempt to Read Password File 47551 HTTP: Apache HTTPD Cookie Handling Denial Of Service (CVE-20120021) 38616 Malware: Hola Traffic Detected 27801 0 19 5000001000000 1500000 2000000 2500000 3000000 3500000 4000000 4500000 12/5/2020

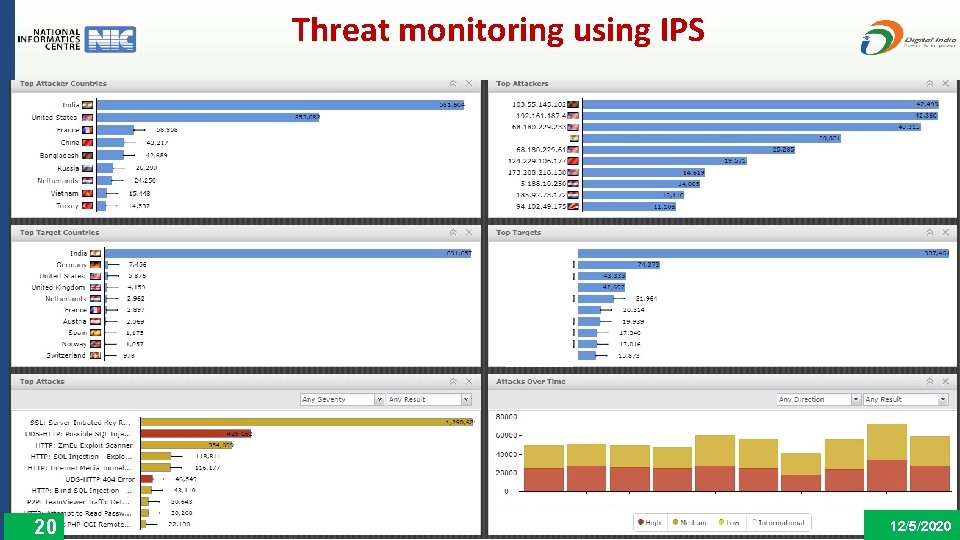
Threat monitoring using IPS 20 12/5/2020

Network Firewall 21 12/5/2020

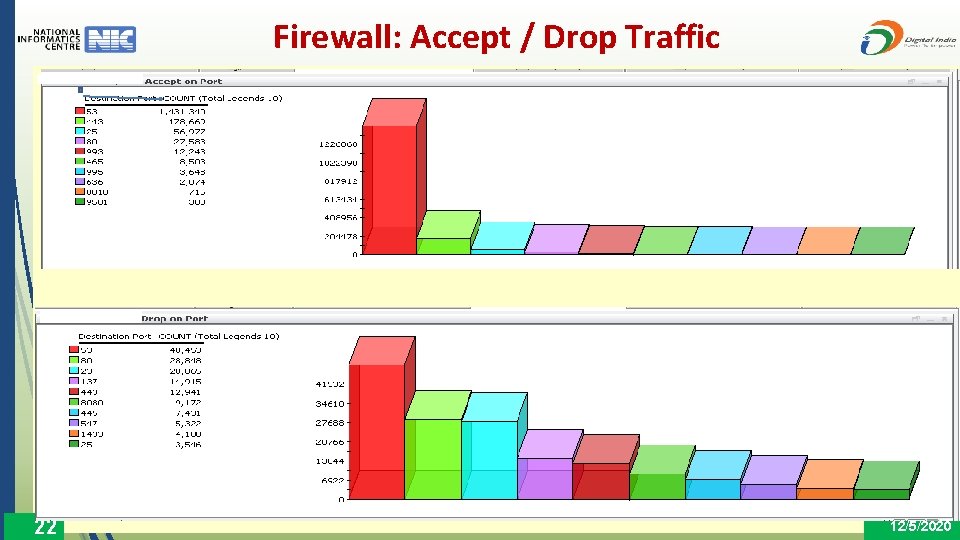
Firewall: Accept / Drop Traffic 22 12/5/2020

UTM 23 12/5/2020

Threat Management using UTM Web Filtering - Blocking traffic based on website categories (Eg. BOT/Malware, Porn) URL Filtering – Blocking based on URL (Eg. facebook. com) Antivirus – Blocking traffic containing viruses (Eg. Trojan Horse malware, Ransomware) IPS – Blocking attacks based on IPS signatures (Eg. Exploit. Kits, Eternal. Blue) SSL Inspection – Deep Packet Inspection Application Control – Blocking applications such as proxy (Eg. Ultrasurf proxy) 24 12/5/2020

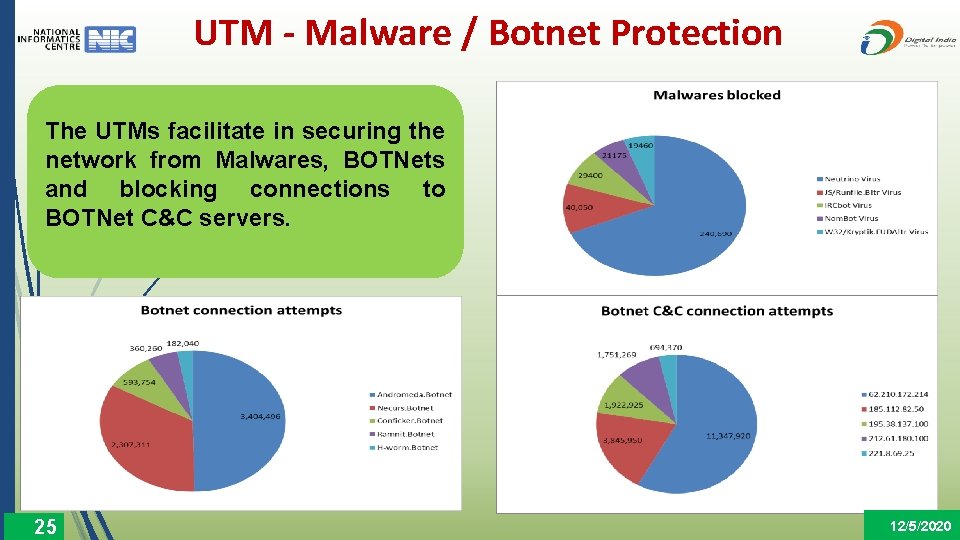
UTM - Malware / Botnet Protection The UTMs facilitate in securing the network from Malwares, BOTNets and blocking connections to BOTNet C&C servers. 25 12/5/2020

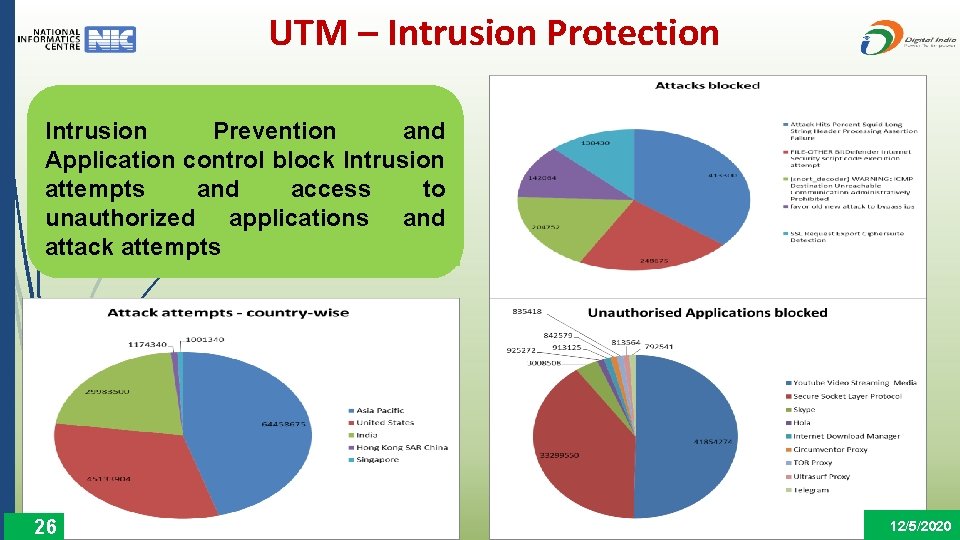
UTM – Intrusion Protection Intrusion Prevention and Application control block Intrusion attempts and access to unauthorized applications and attack attempts 26 12/5/2020

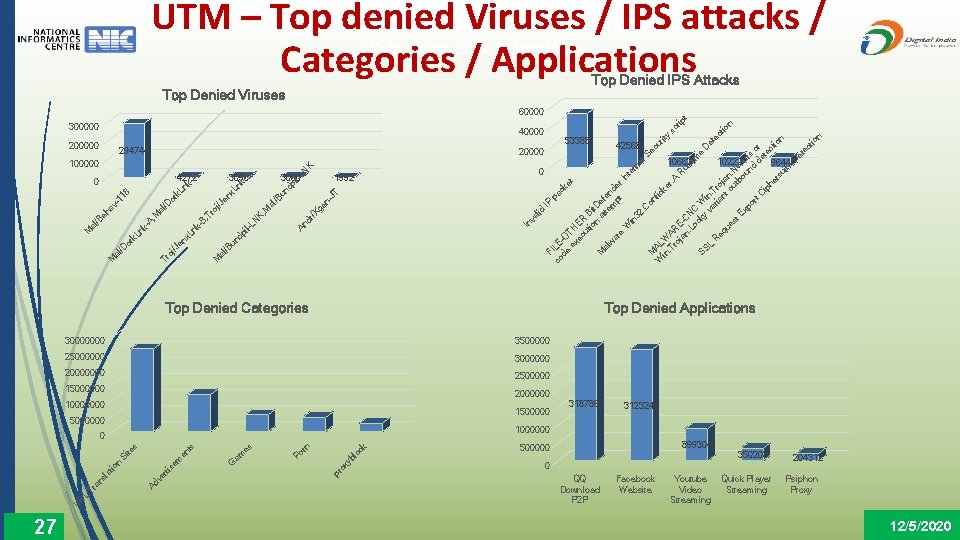
UTM Top 5 Threats Prevented By Cyberoam UTMs – Top denied Viruses / IPS attacks / Categories / Applications (Cyberoam, Last 1 Month) Top Denied IPS Attacks Top Denied Viruses 300000 IP F pa co ILE ck de -O et ex TH ec ER ut B io it n D M at ef al te en w m d ar pt er e In W te in rn 32 et. C Se on M cu fic W AL rit ke in W y. T A r. A sc ro RE rip R ja -C un t n. Lo NC tim c e ky W SS D va in. T L et R ec r r i an oj eq tio t o an ue n ut. Ne st bo c Ex un urs po d rt de or C ip te he ct io rs n ui te D et ec tio n 60000 40000 200000 294744 l-L T ge n. J al An d r/X K, M N M al /B un dp i l-L Ln k. B en x oj /J Tr 1992 nd pi /B u en x. L n j/J , T ro al , M k. L nk -A al /D or M k. B , Ln k. A /D or k 11 8 av /B eh al 3000 10663 0 Top Denied Categories 30000000 3500000 25000000 3000000 20000000 2500000 2000000 10000000 15000000 3187896 3123240 ck 899304 500000 pr ox yb lo rn Po es G en m se rti ve Ad am ts s Si te io n an sl at Tr L R 9644 1000000 0 U 10222 Top Denied Applications 15000000 27 42568 In va lid 3096 , 4272 0 N K 100000 M 53388 20000 350208 0 QQ Download P 2 P Facebook Website Youtube Video Streaming Quick Player Streaming 204312 Psiphon Proxy 12/5/2020

Endpoint Security 28 12/5/2020

Centrally Managed Antivirus solutions Collection of suspicious files of infected systems Analysis of suspicious file Behavioral analysis of infected systems & developing antivirus signature Deployment of new signature on the endpoints Upgradation of Antivirus Solutions Deployment of Desktop Firewall on Endpoints Applying Outbreak Prevention policy in case of Emergency ( like Ransomware threat / malware attack) Applying Web reputation policy 29 12/5/2020

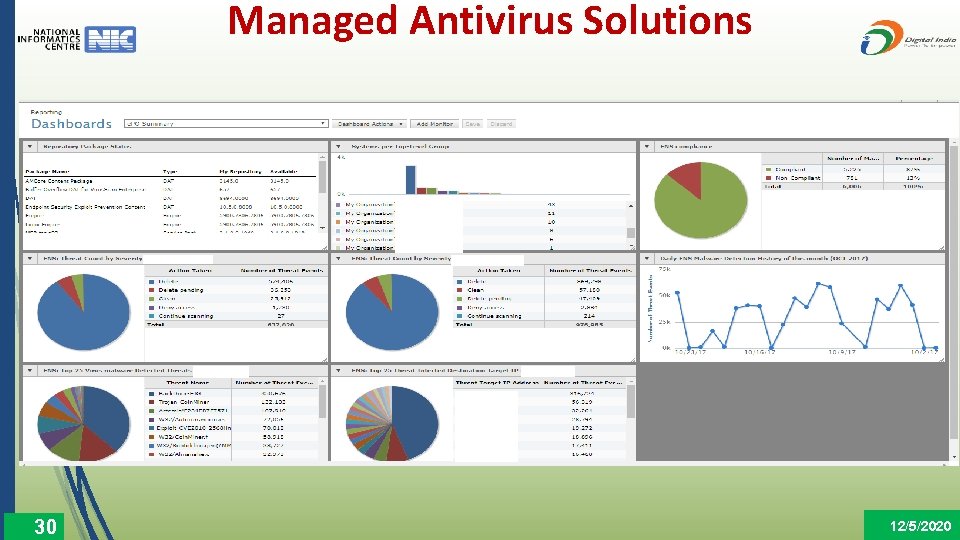
Managed Antivirus Solutions 30 12/5/2020

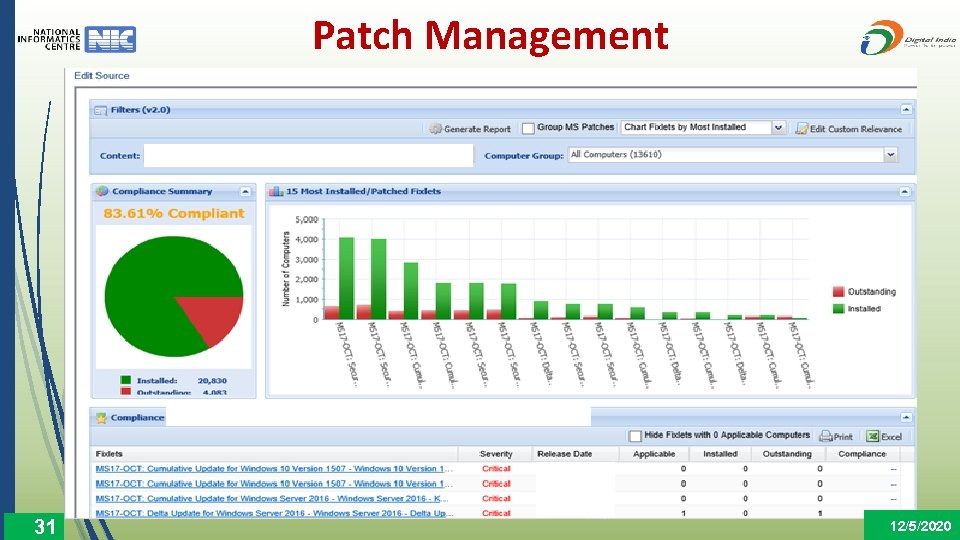
Patch Management 31 12/5/2020

Cyber Security Monitoring 32 12/5/2020

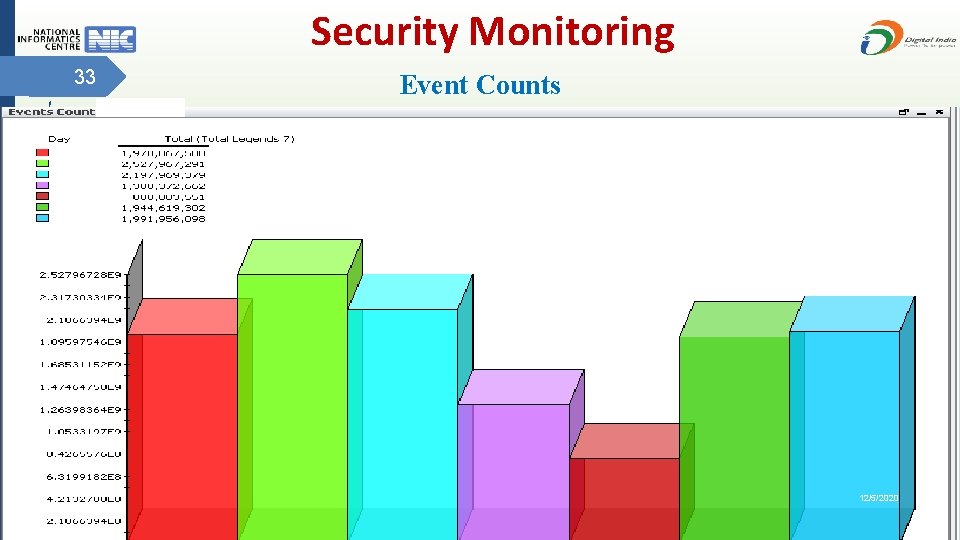
Security Monitoring 33 Event Counts 12/5/2020

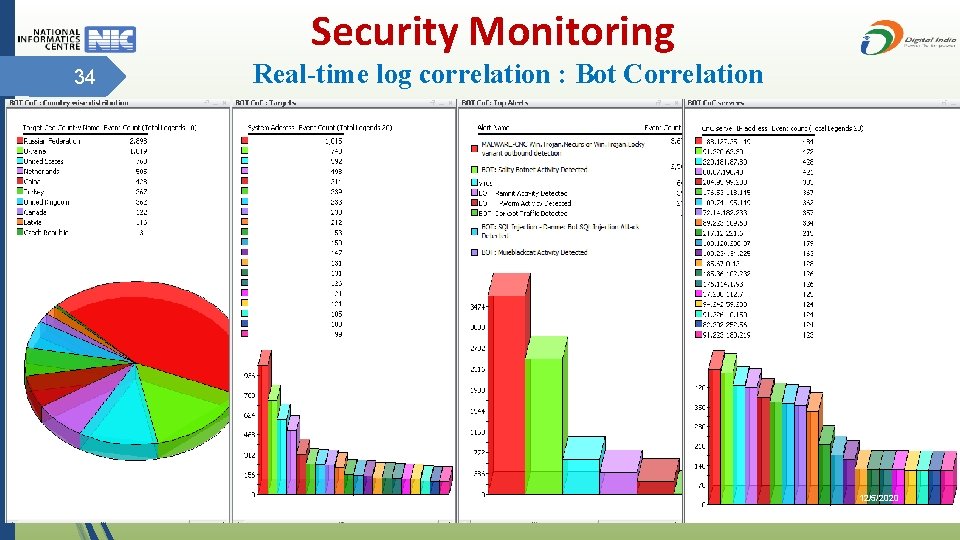
Security Monitoring 34 Real-time log correlation : Bot Correlation 12/5/2020

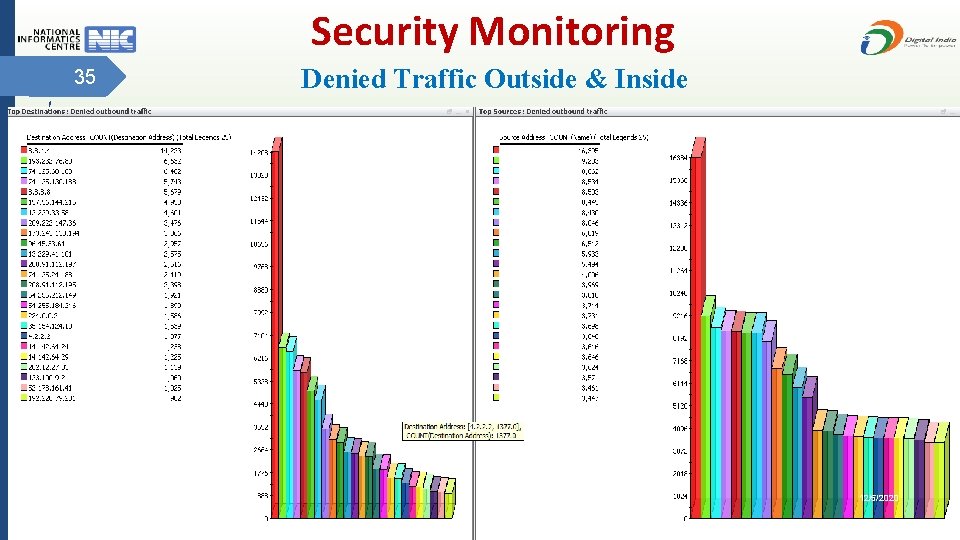
Security Monitoring 35 Denied Traffic Outside & Inside 12/5/2020

Root cause(s) of incidents Zero day attacks Malwares designed for targeted attacks on specific group of users. ØE-mail attachments ØPhishing Antivirus / Patch on systems ØNot installed ØNot up to date Policy Violations ØWrongly configured systems i. e. DNS/NTP/SMTP server configuration ØP 2 P applications on systems. ØDue to virus infection on systems & Cn. C callback Downloading contents from untrusted sources: Unsafe browsing over internet 36 12/5/2020

Mitigation steps Blocking malicious IPs & domains at perimeter security devices, Gateways, DNS servers Deploying User Defined Signatures on IPSs for detection/ blocking of attack Analysis of the perimeter logs to determine the infected systems in the network Install Antivirus / Patches on systems running w/o centrally managed solutions Collect antivirus logs from systems for further analysis & signature deployment Deployment of updated signatures across all systems Continuous real time monitoring of events for detecting any connection attempts to malicious destinations 37 12/5/2020

Thank You 38 38 12/5/2020