Minimising ID Theft when Sharing Personal Data using



- Slides: 14

Minimising ID Theft when Sharing Personal Data using Pseudonymisation

ID Crime – Home Office definitions • False ID An invented or modified genuine identity • ID Fraud Using someone else's ID details or a False ID to support unlawful activities or avoiding liabilities by claiming to be an ID Fraud victim • ID Theft Acquiring sufficient identifying information to commit ID Fraud • ID Crime Any of the above

Essence of ID Theft “Private information collection” This implies ID Theft can be minimised if: 1. Difficult to guess/synthesize identifying data & 2. Difficult to re-use identifying data

Minimising ID Theft of shared data Complicate guessing/synthesis of identifying data: 1. Complex algorithm 2. Require extra information for use (e. g. expiry date, card verification code etc. ) Complicate re-use of identifying data: 1. Restrict acceptable use i. e. compartmentalise & prevent linkage 2. De-sensitise the identifying data 3. Constantly changing/short lifetime (e. g. always moving 4. house, disposable email address, single-use CC number) Need extra data to “unlock” or validate it (e. g. encryption key or chip card PIN or biometrics/ID-card*, last bill amount, RBAC)

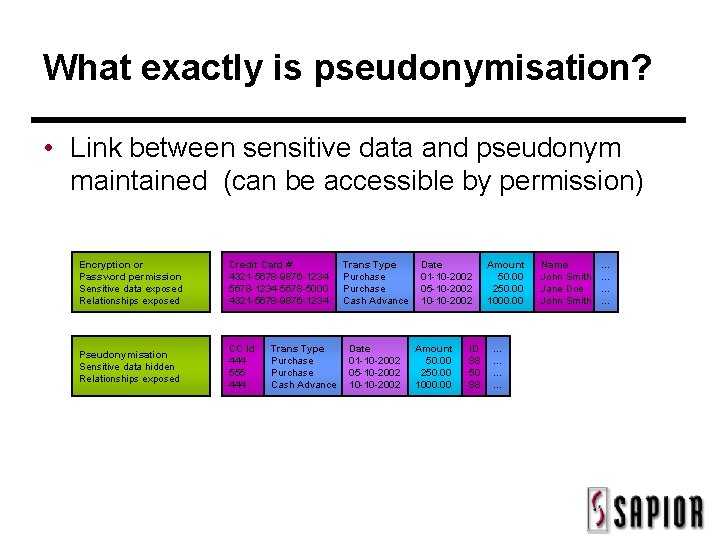
What exactly is pseudonymisation? • Link between sensitive data and pseudonym maintained (can be accessible by permission) Encryption or Password permission Sensitive data exposed Relationships exposed Credit Card # 4321 -5678 -9876 -1234 5678 -1234 -5678 -5000 4321 -5678 -9876 -1234 Pseudonymisation Sensitive data hidden Relationships exposed CC Id 444 555 444 Trans Type Purchase Cash Advance Date 01 -10 -2002 05 -10 -2002 10 -10 -2002 Amount 50. 00 250. 00 1000. 00 ID 88 50 88 Amount 50. 00 250. 00 1000. 00 . . . Name John Smith Jane Doe John Smith . . .

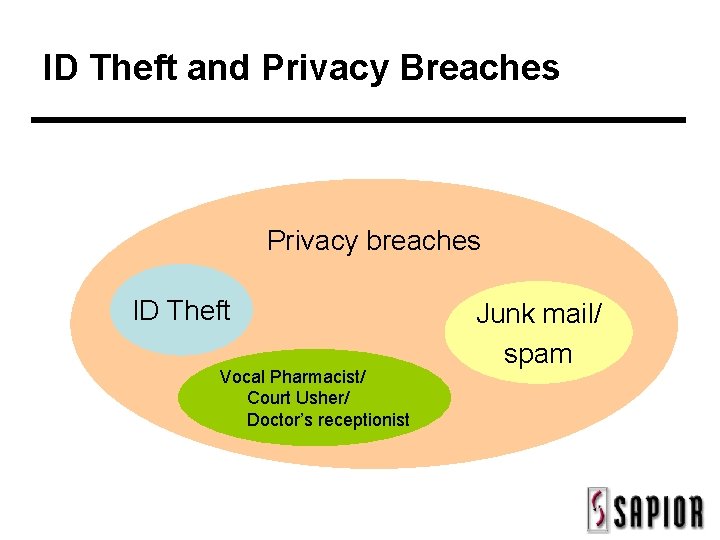
ID Theft and Privacy Breaches Privacy breaches ID Theft Vocal Pharmacist/ Court Usher/ Doctor’s receptionist Junk mail/ spam

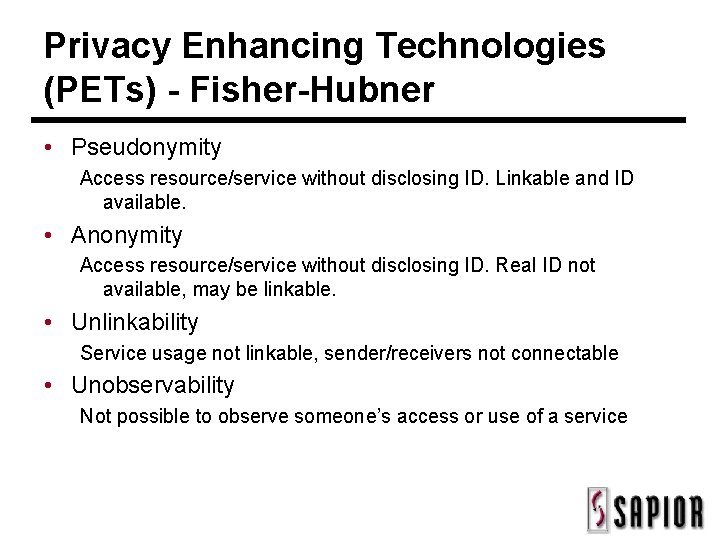
Privacy Enhancing Technologies (PETs) - Fisher-Hubner • Pseudonymity Access resource/service without disclosing ID. Linkable and ID available. • Anonymity Access resource/service without disclosing ID. Real ID not available, may be linkable. • Unlinkability Service usage not linkable, sender/receivers not connectable • Unobservability Not possible to observe someone’s access or use of a service

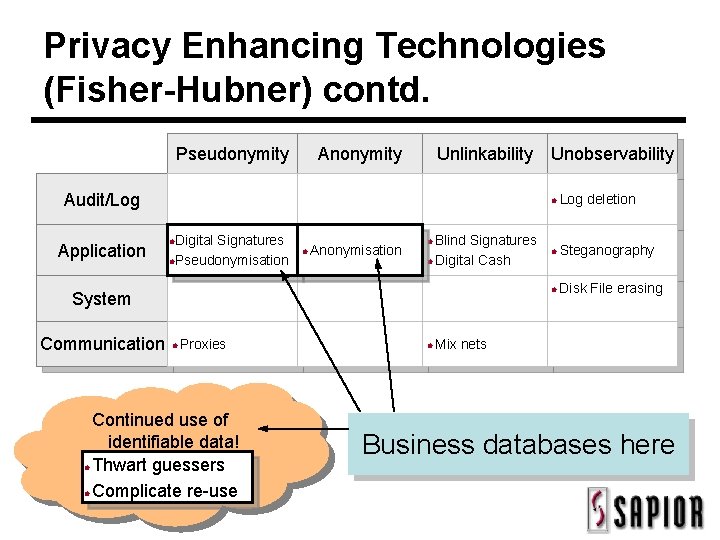
Privacy Enhancing Technologies (Fisher-Hubner) contd. Pseudonymity Anonymity Unlinkability Audit/Log Application Digital Signatures Pseudonymisation Anonymisation Blind Signatures Digital Cash Proxies Continued use of identifiable data! Thwart guessers Complicate re-use Log deletion Steganography Disk File erasing System Communication Unobservability Mix nets Business databases here

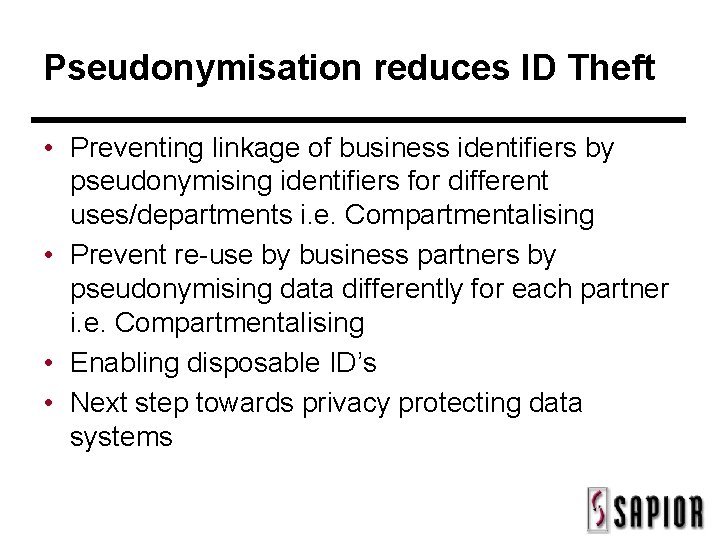
Pseudonymisation reduces ID Theft • Preventing linkage of business identifiers by pseudonymising identifiers for different uses/departments i. e. Compartmentalising • Prevent re-use by business partners by pseudonymising data differently for each partner i. e. Compartmentalising • Enabling disposable ID’s • Next step towards privacy protecting data systems

The pseudonymisation leap The next step… Pseudonymised Identifiable data

NHS Case Study • Care Record Service (CRS) National database providing a live, interactive patient record service accessible 24 hours a day, seven days a week, by health professionals whether they work in hospital, primary care or community services. • CRS Secondary Uses Service Enables investigation of trends and emerging health needs which can inform public health policy. The data extracted will provide better information to support performance improvement and assessment, clinical audit and governance, monitoring and benchmarking, surveillance, research and planning

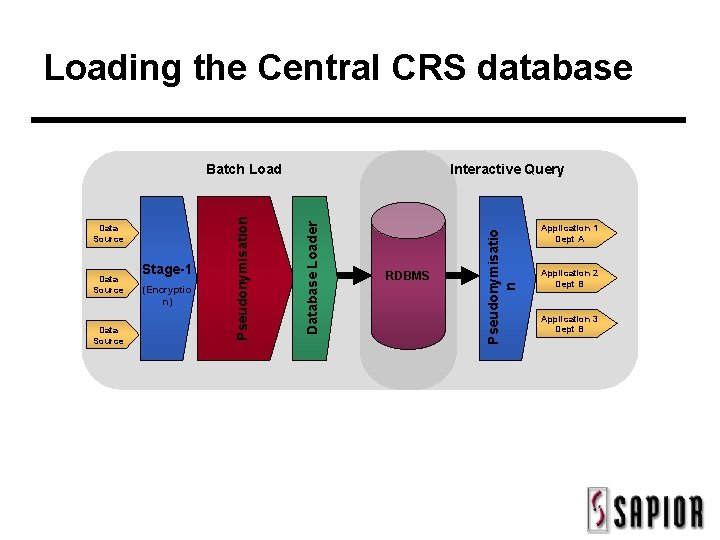
Loading the Central CRS database Data Source Stage-1 (Encryptio n) Database Loader Data Source Pseudonymisation Data Source RDBMS Pseudonymisatio n Interactive Query Batch Load Application 1 Dept A Application 2 Dept B Application 3 Dept B

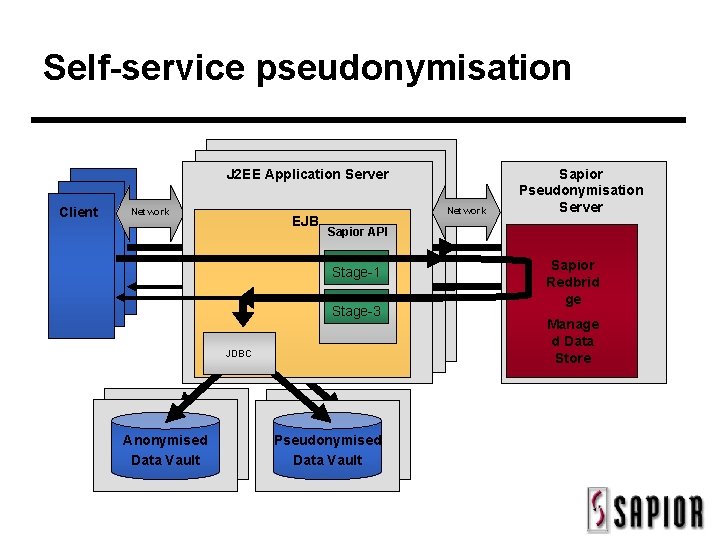
Self-service pseudonymisation J 2 EE Application Server Client Network EJB Network Sapior API Stage-1 Stage-3 JDBC Anonymised Data Vault Sapior Pseudonymisation Server Pseudonymised Data Vault Sapior Redbrid ge Manage d Data Store

Take-home Message If you share data and need to minimise ID Theft risk, then you must consider pseudonymisation • Contact: www. sapior. com +44 -(0)20 -7060 -2965