Midterm Review Physical Layer Physical layer design goal








- Slides: 15

Midterm Review

Physical Layer • Physical layer design goal: send out bits as fast as possible with acceptable low error ratio • C=B*log(1+S/N) – C is the capacity of the channel, B is the bandwidth of the channel, S is power of the signal and N is the power of the noise – Channel capacity means how many bits you can send out per second reliably – Bandwidth means how fast you can change the voltage. More precisely, the range of frequencies pass the channel. – Noise: anything other than the intended signal. Added to the signal.

Detection – with Noise • • Detection really depends on the noise. In the binary case when the transmitted signal is either 0 or 5 V with equal probability, if we know that noise takes values 3 V and 2 V with probability 0. 7 and 0. 3, respectively. How would you design the detector? First step, check the possible outcomes: – If send 0 V, two possible outcomes: • -3 V. Prob: 0. 7. • 2 V. Prob: 0. 3. – If send 5 V, two possible outcomes: • 2 V. Prob: 0. 7. • 7 V. Prob: 0. 3. – So, a total of only 3 possible outcomes. • Second step, check for each outcome, what should the output be. – No ambiguity when received -3 V and 7 V, 0 and 1, respectively. – What should we say when received 2 v? From 0 V, probability 0. 5*0. 3= 0. 15. From 5 V, 0. 5*0. 7=0. 35. So will say when received 2 V, the bit is 1. – What is the probability that we give the wrong detection result? When received 2 V and was from bit 0 and we say it is from bit 1, so it is 0. 15.

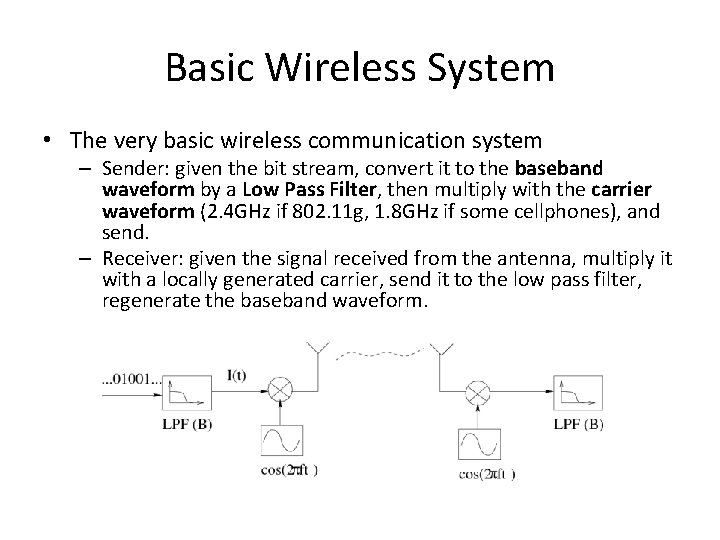
Basic Wireless System • The very basic wireless communication system – Sender: given the bit stream, convert it to the baseband waveform by a Low Pass Filter, then multiply with the carrier waveform (2. 4 GHz if 802. 11 g, 1. 8 GHz if some cellphones), and send. – Receiver: given the signal received from the antenna, multiply it with a locally generated carrier, send it to the low pass filter, regenerate the baseband waveform.

Some Important Concepts • • • Bandwidth – How fast can signals change. Or, the width of the frequency range that can pass the system. Noise – Will be added to the signal. Random, but some statistics can be known with which we make our detection rules. Data rate – How fast can we send bits, can be measured in bps. Upper bounded by the Shannon’s theorem given the bandwidth and noise. Propagation delay – How long does it take for the symbol to reach to the destination. Symbol – A point on the plane to represent one bit or multiple bits. Sample – A reading of the received signal at some time instant. Usually a corrupted version of the symbol. Filter – Some device or software that can remove certain frequency components in the received waveform. Carrier – A sine wave to be multiplied with the baseband waveform. Baseband waveform – The waveform that is a smoothed version of the square waveform after the low pass filter. To be multiplied with the carrier.

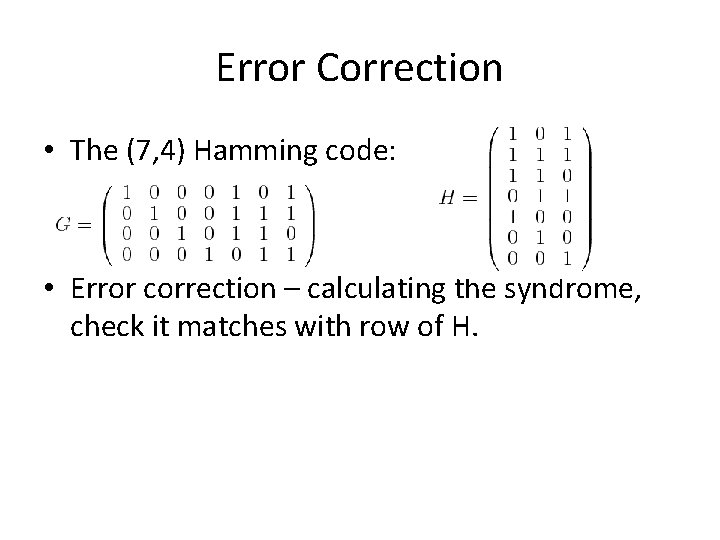
Error Correction • The (7, 4) Hamming code: • Error correction – calculating the syndrome, check it matches with row of H.

Error Correction • How is G chosen such that it can correct one error? • The key is – • First: • ANY linear combinations of the row vectors of G has weight at least 3 (having at least three `1’s) • ANY codeword is a linear combination of the row vectors • So a codeword has weight at least 3. • Second: • The sum of any two codeword is still a codeword • So the distance (number of bits that differ) is also at least 3. • So if one bit is wrong, won’t confuse it with other codeword. • Because if there is only one bit wrong, the received vector will have one bit difference with the original codeword C 0. If it is also only one bit away from another codeword C 1, it means that C 0 and C 1 have at most two bit difference, a contradiction.

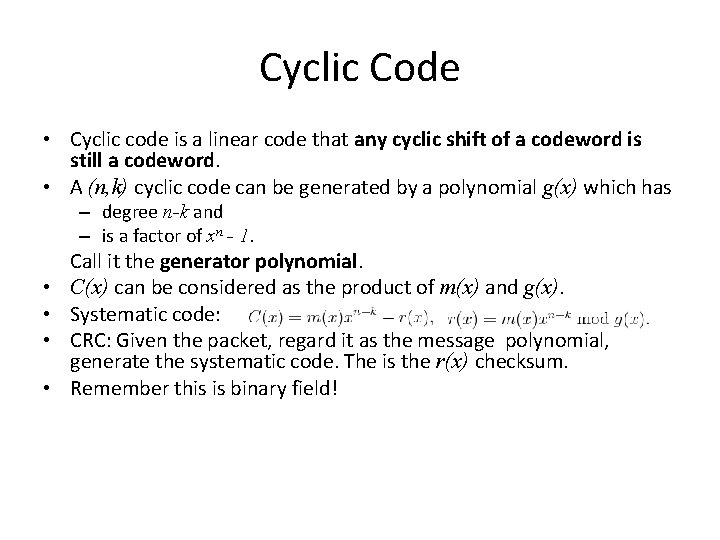
Cyclic Code • Cyclic code is a linear code that any cyclic shift of a codeword is still a codeword. • A (n, k) cyclic code can be generated by a polynomial g(x) which has – degree n-k and – is a factor of xn - 1. • • Call it the generator polynomial. C(x) can be considered as the product of m(x) and g(x). Systematic code: CRC: Given the packet, regard it as the message polynomial, generate the systematic code. The is the r(x) checksum. Remember this is binary field!

Stop-and-Wait • Sender (maintains “m” as the current sequence number , i. e. , up to m-1 has been ACKed) 1. 2. 3. • • Grab data from the network layer. Send to physical layer with the current sequence number , i. e. , m, and start timer. Wait for ACK. If get ACKm, m: =m+1, repeat 1. Else, timeout, repeat 2. • Receiver (maintains “m” as the current sequence number, i. e. , up m-1 has been received) 1. 2. • 3. Wait for data from the physical layer. Get data from the physical layer. If it is with the expected sequence number, i. e. , m, give it to the network layer when the network layer is ready, m: =m+1. Send ACKm-1. Goto 1.

Go-Back-N Sender. Assume the current window is m+1 to m+n. while (1) { If network layer has data and if current window not full yet: read data, send to physical layer with the current sending frame ID, start timer, increment sending ID. If got ACKw: if w is outside the window, don’t do anything; if w is inside the window, consider all frames in the window with ID no more than w acked and let m=w. If timeout for frame w: start to resend all frames in the window with frame ID no less than w. } Receiver. Assume the expected sequence number is m. while (1){ Wait to get data from the physical layer (blocked here until data received). (1) If the data has frame ID m, give it to the network layer, m=m+1; (2) Send ACKm-1. } • Note: assuming the sequence number is the frame ID. • Note: for simplicity, assume the receiver network layer is always ready. 3/6/2021 6: 53: 47 PM

Selective Repeat Sender. Assume the current window is m+1 to m+n. while (1) { If network layer has data and if current window not full yet: read data, send to physical layer with the current sending frame ID, start timer, increment sending ID. If got ACKw: if w is outside the window, don’t do anything; if w is inside the window, consider all frames in the window with ID no more than w acked and let m=w. If timeout for frame w, resend frame w. } Receiver. Assume the current window is m+1 to m+n. while (1) { Wait (blocked here) and get frame from the physical layer. If it is within the receiver window and hasn’t been received before, fill in the slot, forward the beginning of the receiver window if necessary, and deliver to the network layer all frames between the beginning of the old receiver window and the new receiver window – 1, inclusive. Send ACKm (m+1= the beginning of the current receiver window). } • Note: assuming the sequence number is the frame ID. • Note: for simplicity, assume the receiver network layer is always ready. 3/6/2021 6: 53: 47 PM

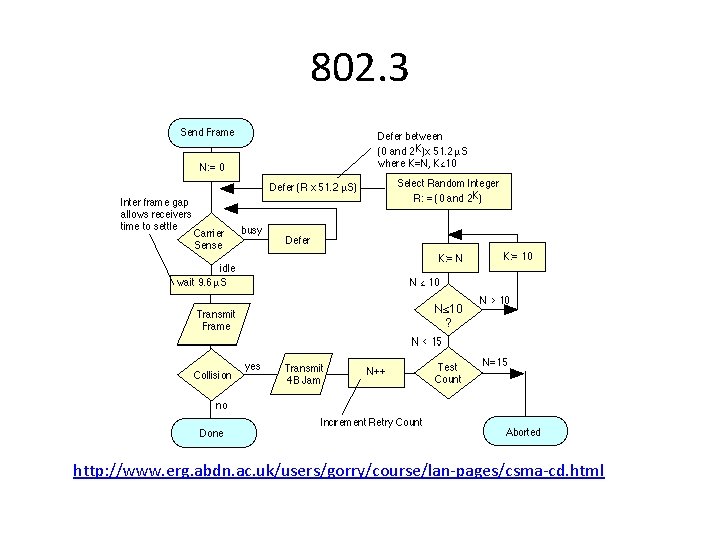
MAC • In broadcast channels/multiaccess channels/random access channels, multiple sources may compete for a shared channel. Two properties: • When one station transmits, anyone can hear (something) • When more than station transmit, collision • The biggest problem now is how to determine who gets the channel. • ALOHA as the starting point. • Then tricks such as – CSMA: listen before transmit – CD: collision detection. Early abort. – CA: collision avoidance. Minimize the probability of collision. Wait for a random time after the medium is free. – Exponential backoff: If collision, double the window size. Adaptively adjust the contention window based on the local belief about the number of contending stations. – Ethernet: CSMA/CD/ Exponential backoff. – Wi-Fi: CSMA/CA/ Exponential backoff.

802. 3 http: //www. erg. abdn. ac. uk/users/gorry/course/lan-pages/csma-cd. html

DCF’s Main Idea • When get a packet to send, sense the channel. If channel is busy, wait until the channel is free for DIFS. Start to backoff for a random time. If busy before reaching zero, freeze bo counter, and reactivate when idle for DIFS again. If counted to 0 and channel is still idle, send. • After receives a packet, send ACK. • If no ACK received, double the window and retry.

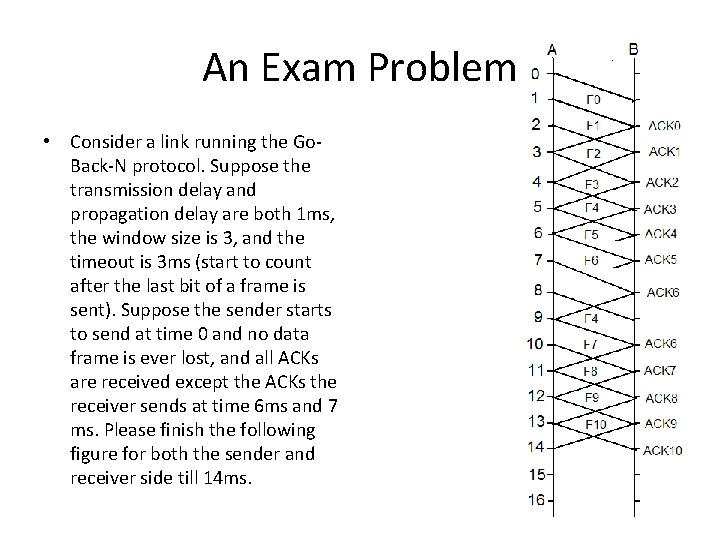
An Exam Problem • Consider a link running the Go. Back-N protocol. Suppose the transmission delay and propagation delay are both 1 ms, the window size is 3, and the timeout is 3 ms (start to count after the last bit of a frame is sent). Suppose the sender starts to send at time 0 and no data frame is ever lost, and all ACKs are received except the ACKs the receiver sends at time 6 ms and 7 ms. Please finish the following figure for both the sender and receiver side till 14 ms.