Microsoft MVP Enterprise Security Microsoft Certified Trainer 18


























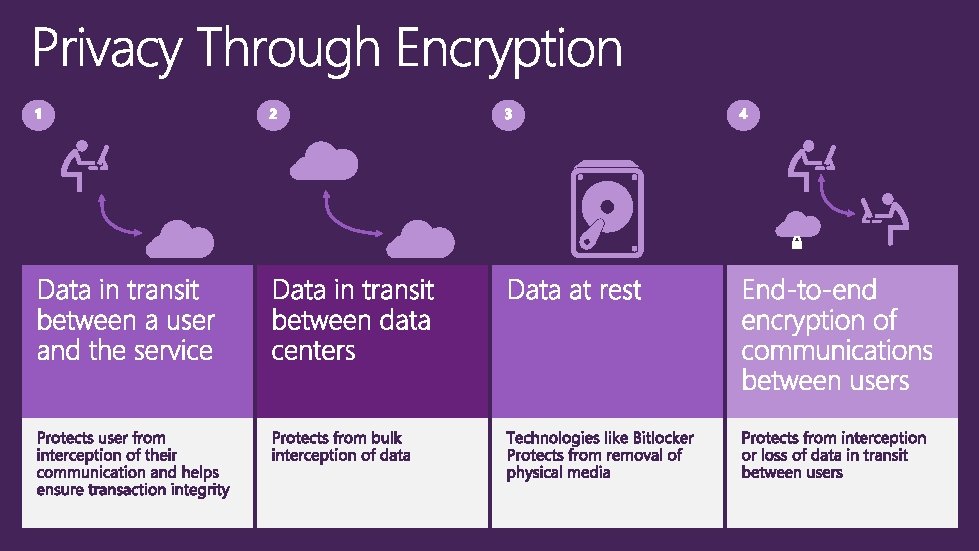













- Slides: 66



Microsoft MVP (Enterprise Security) Microsoft Certified Trainer (18 years) Founder: Cybercrime Security Forum! Author: The Seventh Day Andy Malone (United Kingdom) Follow me on Twitter @Andy. Malone www. Andymalone. org





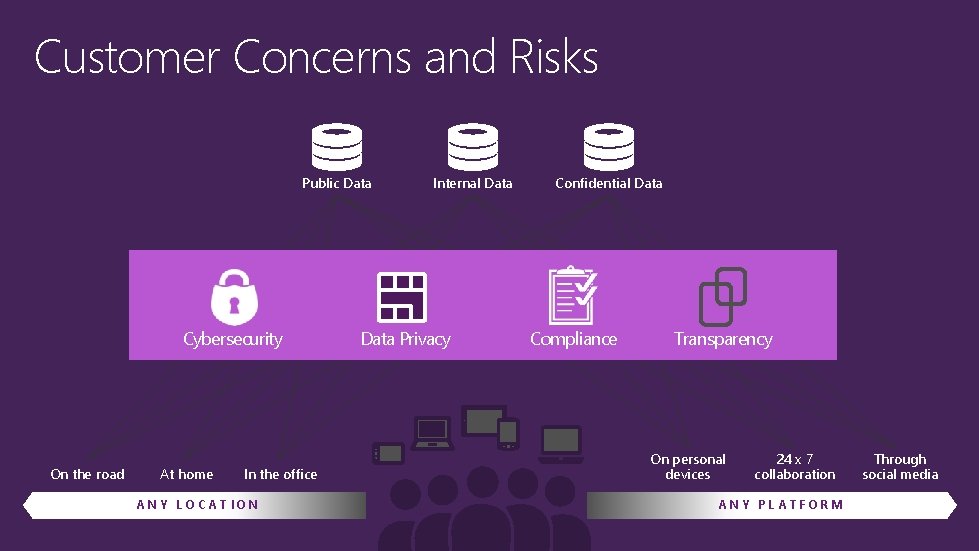
Customer Concerns and Risks Public Data Cybersecurity On the road At home In the office ANY LOCATION Internal Data Privacy Confidential Data Compliance Transparency On personal devices 24 x 7 collaboration ANY PLATFORM Through social media







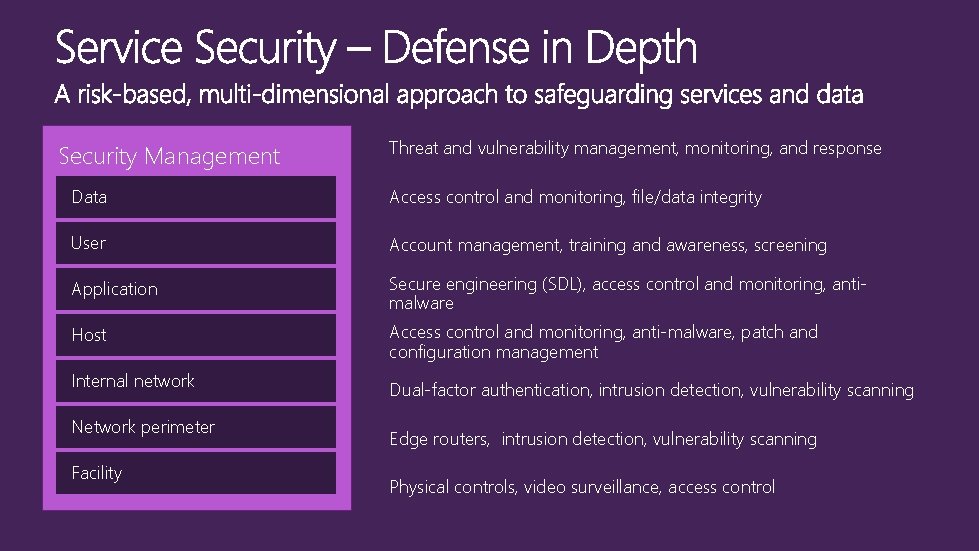
Security Management Threat and vulnerability management, monitoring, and response Data Access control and monitoring, file/data integrity User Account management, training and awareness, screening Application Secure engineering (SDL), access control and monitoring, antimalware Host Access control and monitoring, anti-malware, patch and configuration management Internal network Network perimeter Facility Dual-factor authentication, intrusion detection, vulnerability scanning Edge routers, intrusion detection, vulnerability scanning Physical controls, video surveillance, access control

Highly Secured Physical Environment Multiple Redundancy Model Small number of Staff Separation of Duties & Roles Strict Security Policies & Procedures (Failure=Dismissal) Managed Data Destruction Policies PII & Non PII Stored Separately Free & Paid services Stored Separately

You’re always in Control

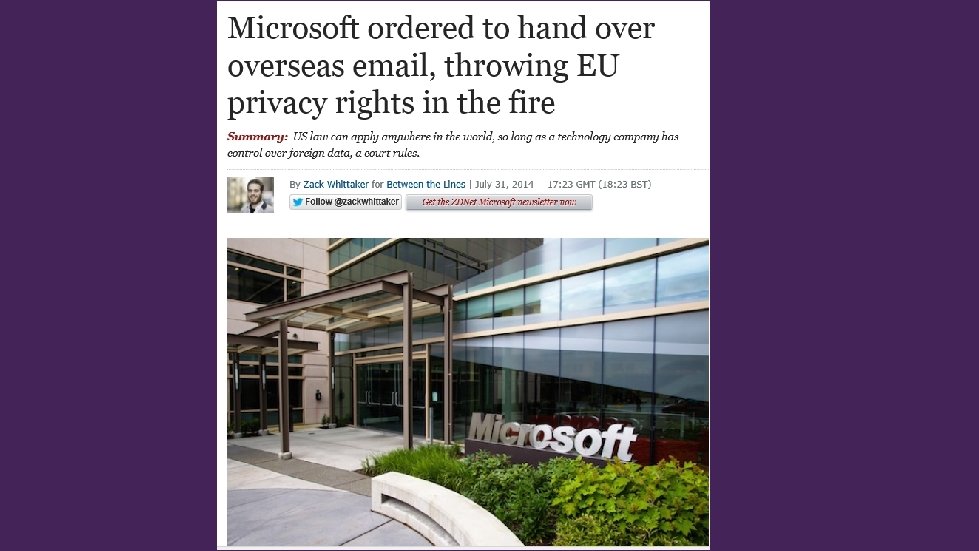
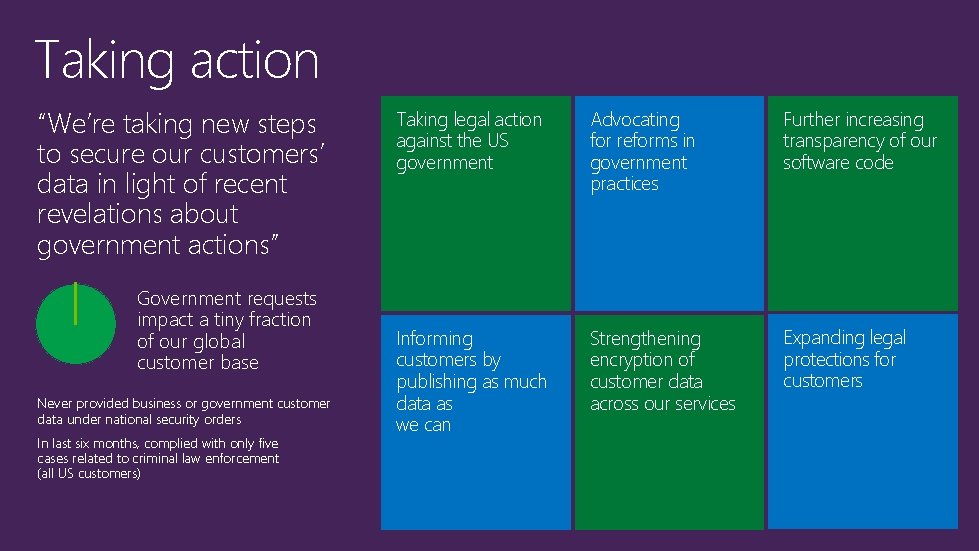
Taking action “We’re taking new steps to secure our customers’ data in light of recent revelations about government actions” Government requests impact a tiny fraction of our global customer base Never provided business or government customer data under national security orders In last six months, complied with only five cases related to criminal law enforcement (all US customers) Taking legal action against the US government Advocating for reforms in government practices Further increasing transparency of our software code Informing customers by publishing as much data as we can Strengthening encryption of customer data across our services Expanding legal protections for customers

Law enforcement request report Microsoft follows clear principles in responding to government legal demands for customer data We require a valid subpoena or legal equivalent before we consider releasing a customer’s non-content data to law enforcement We require a court order or warrant before we consider releasing a customer’s content data In each instance, we carefully examine the requests we receive for a customer’s information to make sure they are in accord with the laws, rules, and procedures that apply

Compliance

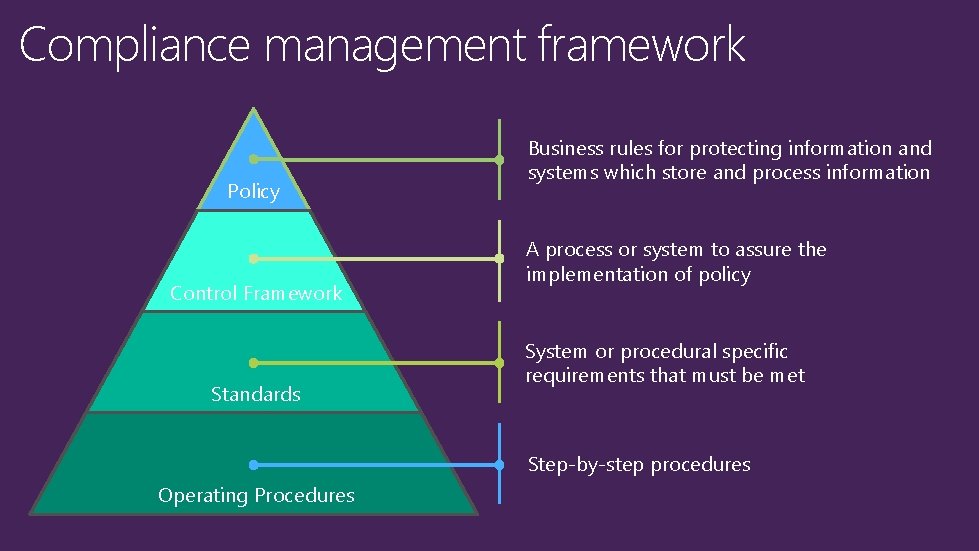
Compliance management framework Policy Control Framework Standards Business rules for protecting information and systems which store and process information A process or system to assure the implementation of policy System or procedural specific requirements that must be met Step-by-step procedures Operating Procedures

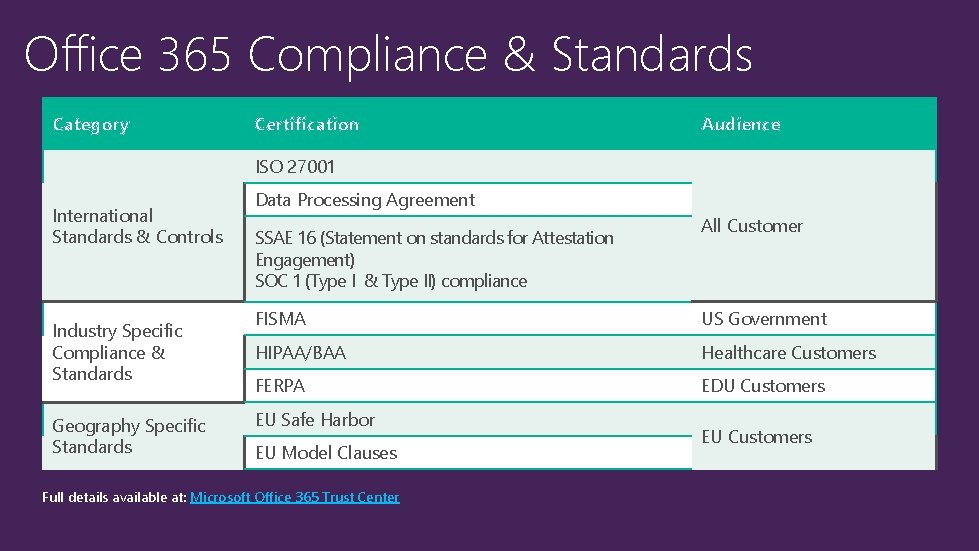
Office 365 Compliance & Standards Category Certification Audience ISO 27001 International Standards & Controls Industry Specific Compliance & Standards Geography Specific Standards Data Processing Agreement SSAE 16 (Statement on standards for Attestation Engagement) SOC 1 (Type I & Type II) compliance All Customer FISMA US Government HIPAA/BAA Healthcare Customers FERPA EDU Customers EU Safe Harbor EU Model Clauses Full details available at: Microsoft Office 365 Trust Center EU Customers

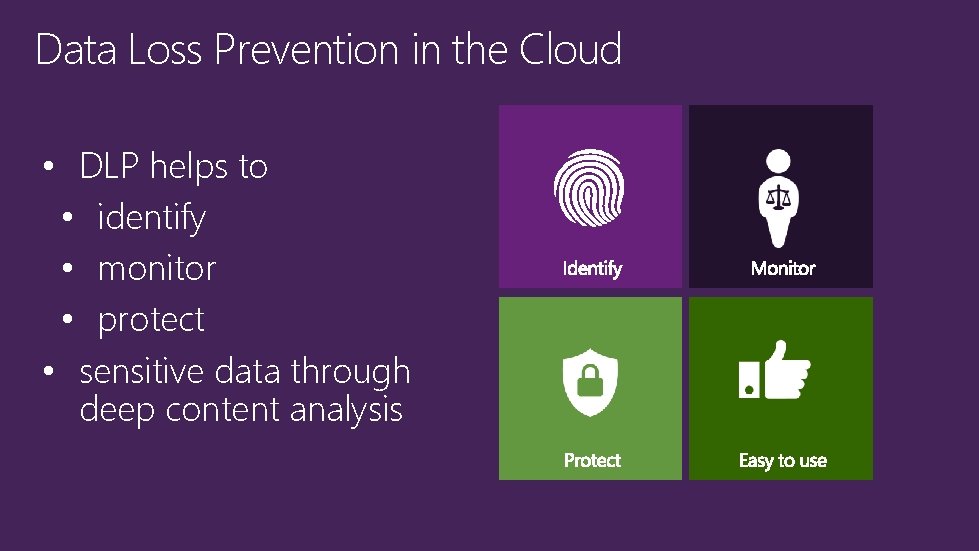
Data Loss Prevention in the Cloud • DLP helps to • identify • monitor • protect • sensitive data through deep content analysis

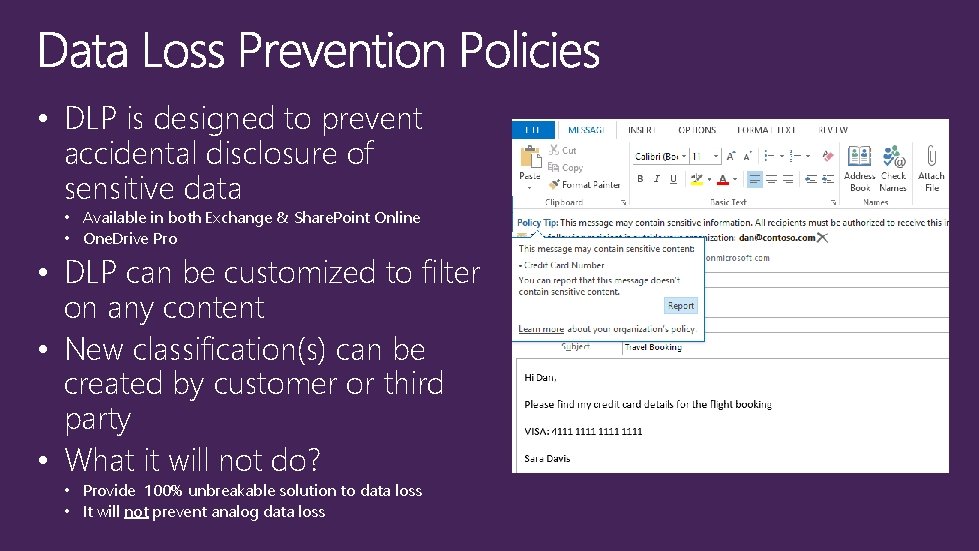
• DLP is designed to prevent accidental disclosure of sensitive data • Available in both Exchange & Share. Point Online • One. Drive Pro • DLP can be customized to filter on any content • New classification(s) can be created by customer or third party • What it will not do? • Provide 100% unbreakable solution to data loss • It will not prevent analog data loss

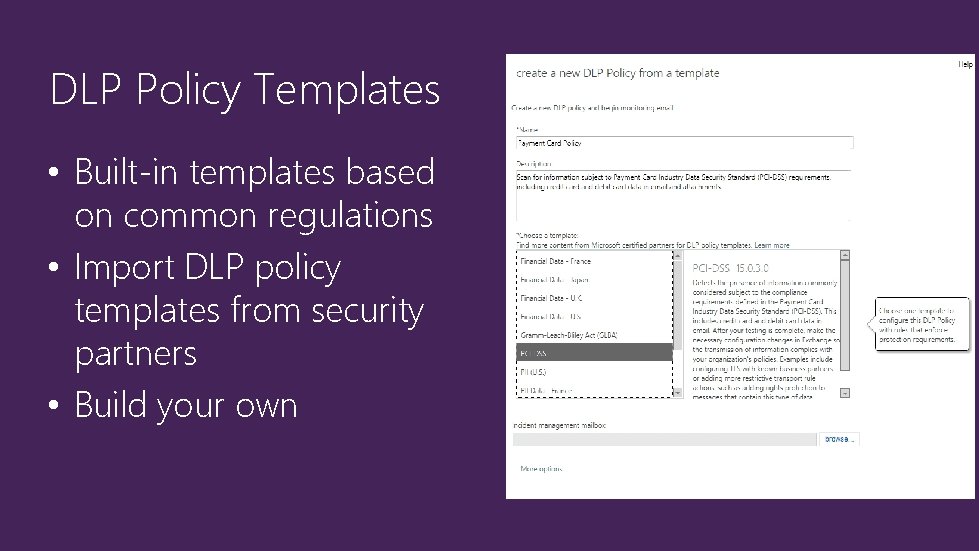
DLP Policy Templates • Built-in templates based on common regulations • Import DLP policy templates from security partners • Build your own

Preventing Data Loss

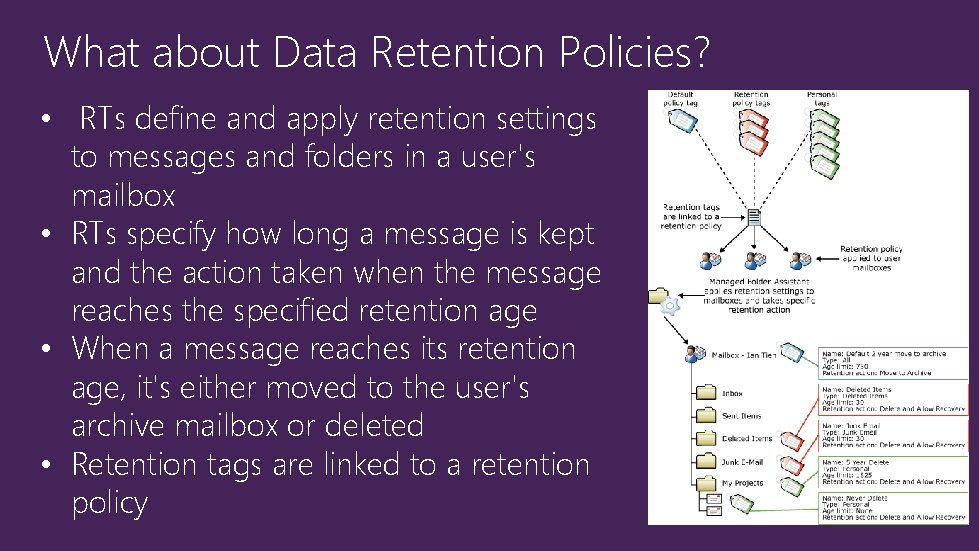
What about Data Retention Policies? • RTs define and apply retention settings to messages and folders in a user's mailbox • RTs specify how long a message is kept and the action taken when the message reaches the specified retention age • When a message reaches its retention age, it's either moved to the user's archive mailbox or deleted • Retention tags are linked to a retention policy

What about Deleted Item Retention (DIR) • The DIR Period is how long an items remain in the “Recoverable Items” folder after it’s been deleted by the user • Either by empting the Deleted Items folder in the mailbox, or by pressing SHIFT-DELETE when deleting • This retention period has nothing to do with retention tags per se • It allows the user a second chance to recover items for a limited period (default: 14 days)

What about Deleted Item Retention (DIR) *RPTs don’t support a retention action that moves items to the user’s archive mailbox. The only retention action for RPTs is to delete items By Default DIR defaults to 14 Days Set-Mailbox -Identity “Andy Malone" -Retain. Deleted. Items. For 30 Get-Mailbox -Result. Size unlimited -Filter {(Recipient. Type. Details -eq 'User. Mailbox')} | Set-Mailbox -Retain. Deleted. Items. For 30 Get-Mailbox <Name> | FL Retain. Deleted. Items. For

How does DIR affect or work with Retention Tags? • Delete and allow recovery retention action for a retention tag, item will be deleted and user will be able to recover until 14 days, after which item will be purged • Permanently delete action, item will be deleted permanently – i. e. purged from the mailbox database. Neither the user nor the admin will be able to recover • Exception: If the mailbox is on In-Place Hold or Litigation Hold, items are preserved based on hold parameters. If the hold doesn’t specify a duration, items are preserved indefinitely or until hold is removed

Can I Have a 1 Year Retention Policy? • Customer can set a 1 -year retention policy, regardless of the Deleted Item Retention period • If they want to not provide their users with a second chance to recover items and definitely delete in 1 year, set the Deleted Item Retention period to zero days

Points to Remember • Retention policies are included in all plans • Remember that policies don’t really “retain” items. They delete items (or move them to archive) • In-Place Hold & Litigation Hold are the two features that preserve data – either indefinitely or for a specified period • E. e, if you want to preserve all data for 1 year and delete all data after 1 year, you can apply a Retention Policy (with a single retention tag) to delete items in 1 year, and either use an In-Place Hold or Litigation Hold to preserve items for 1 year • Need Exchange Online Plan 2 for this!

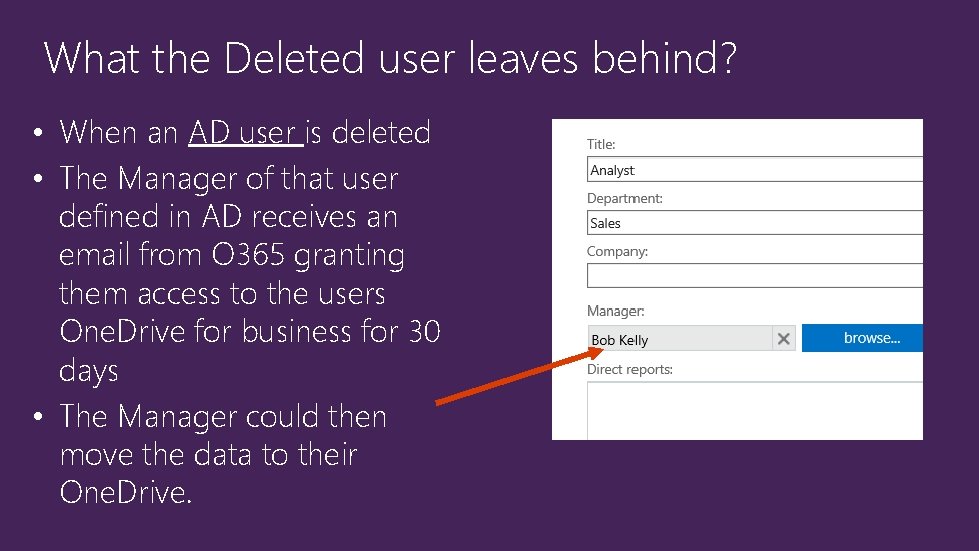
What the Deleted user leaves behind? • When an AD user is deleted • The Manager of that user defined in AD receives an email from O 365 granting them access to the users One. Drive for business for 30 days • The Manager could then move the data to their One. Drive.

Exchange On-Line Litigation & Legal Hold

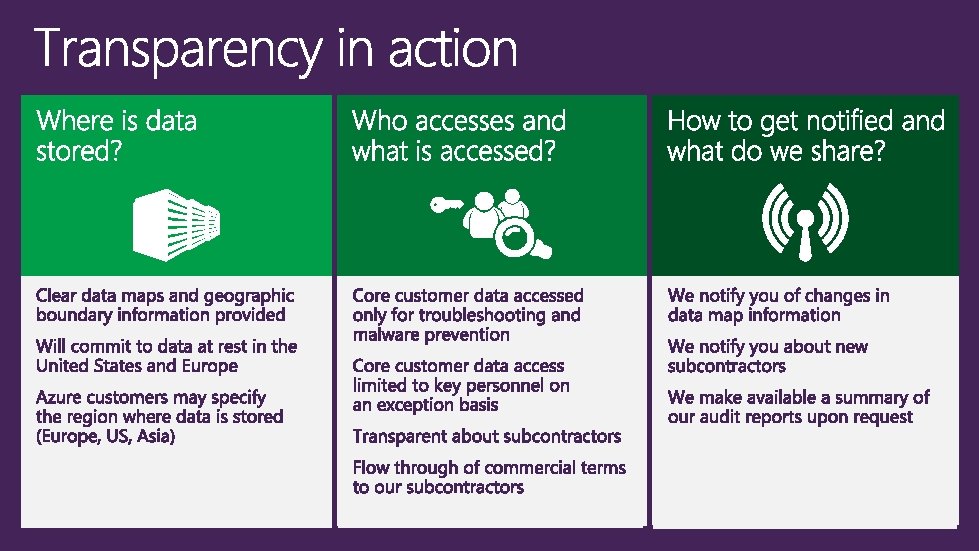
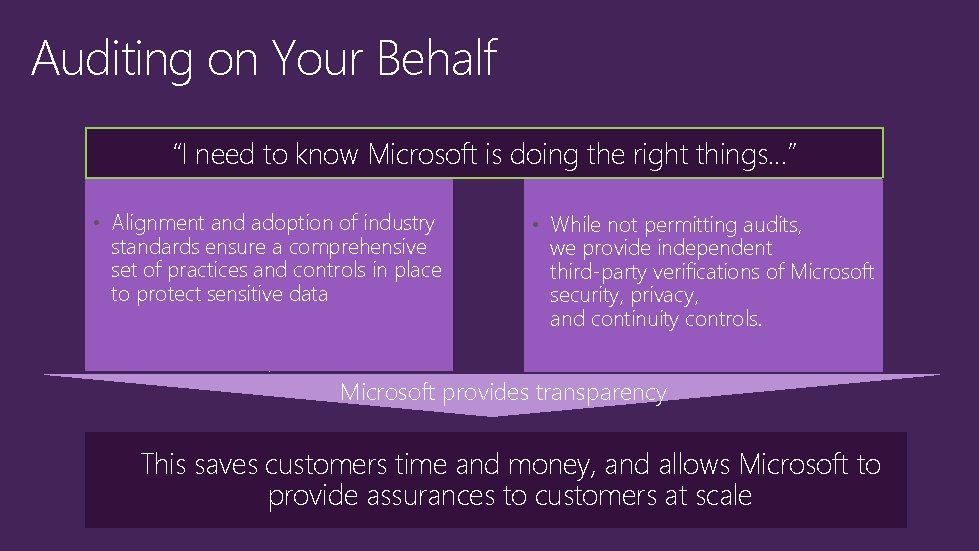
Auditing on Your Behalf “I need to know Microsoft is doing the right things…” • Alignment and adoption of industry standards ensure a comprehensive set of practices and controls in place to protect sensitive data • While not permitting audits, we provide independent third-party verifications of Microsoft security, privacy, and continuity controls. Microsoft provides transparency This saves customers time and money, and allows Microsoft to provide assurances to customers at scale


Auditing & Reporting


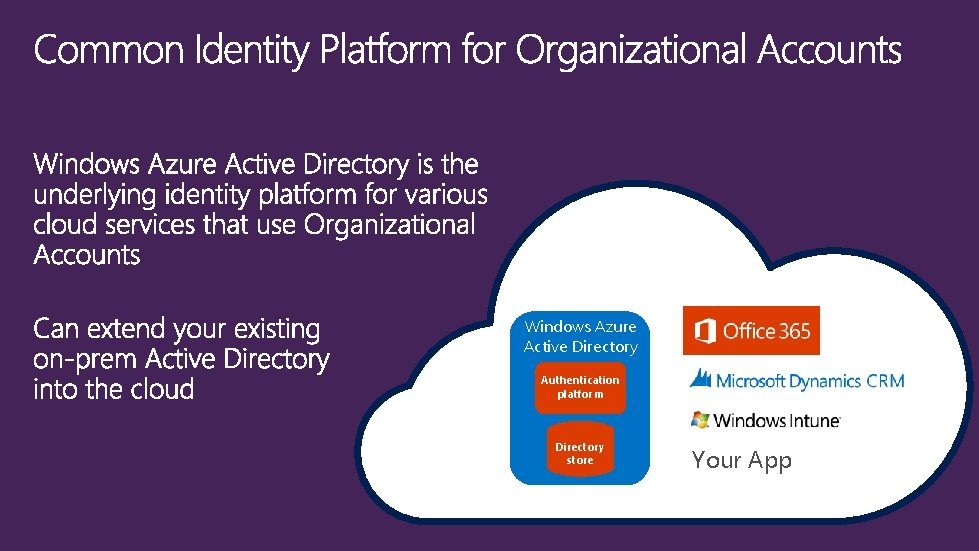
Microsoft Account Ex: alice@outlook. com User Windows Azure Active Directory Organizational Account Ex: alice@contoso. com User

Windows Azure Active Directory Authentication platform Directory store Your App

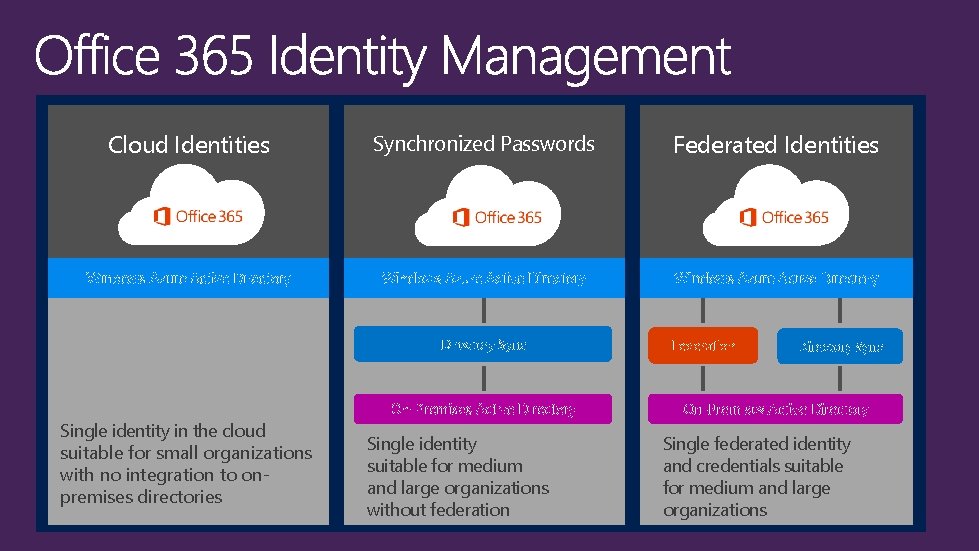
Cloud Identities Synchronized Passwords Federated Identities Windows Azure Active Directory Sync Single identity in the cloud suitable for small organizations with no integration to onpremises directories On-Premises Active Directory Single identity suitable for medium and large organizations without federation Federation Directory Sync On-Premises Active Directory Single federated identity and credentials suitable for medium and large organizations

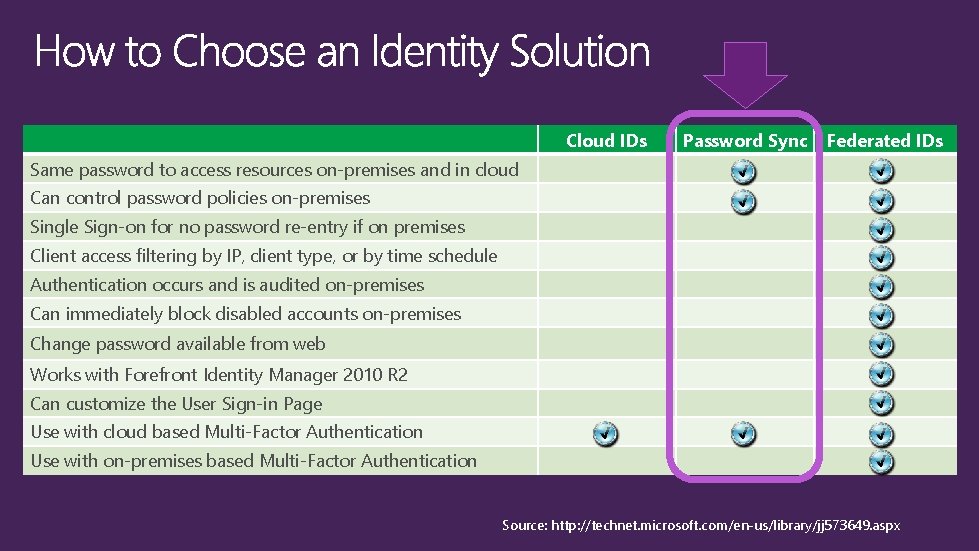
Cloud IDs Password Sync Federated IDs Same password to access resources on-premises and in cloud Can control password policies on-premises Single Sign-on for no password re-entry if on premises Client access filtering by IP, client type, or by time schedule Authentication occurs and is audited on-premises Can immediately block disabled accounts on-premises Change password available from web Works with Forefront Identity Manager 2010 R 2 Can customize the User Sign-in Page Use with cloud based Multi-Factor Authentication Use with on-premises based Multi-Factor Authentication Source: http: //technet. microsoft. com/en-us/library/jj 573649. aspx

Deploying & Configuring ADFS

Deploying AADSync


No Advertising Transparency

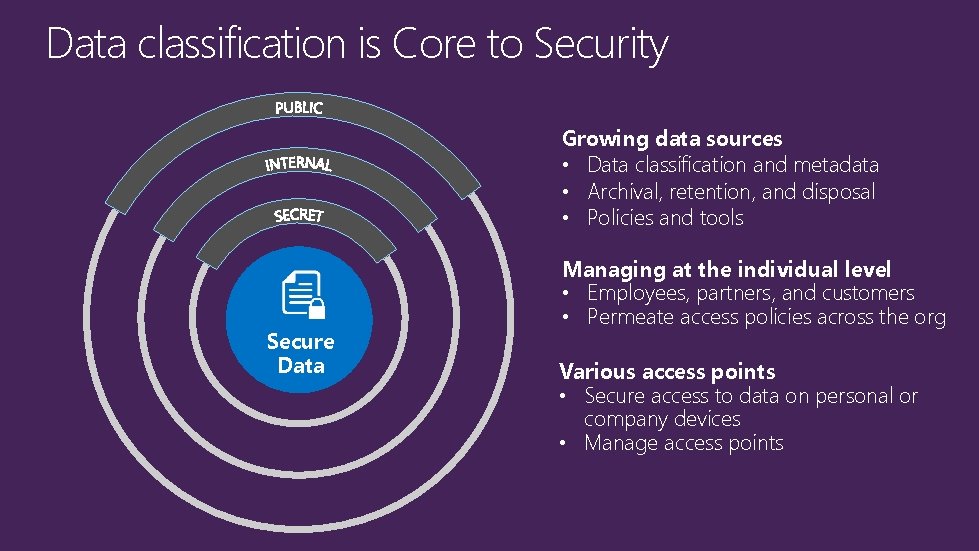
Data classification is Core to Security Growing data sources • Data classification and metadata • Archival, retention, and disposal • Policies and tools Secure Data Managing at the individual level • Employees, partners, and customers • Permeate access policies across the org Various access points • Secure access to data on personal or company devices • Manage access points


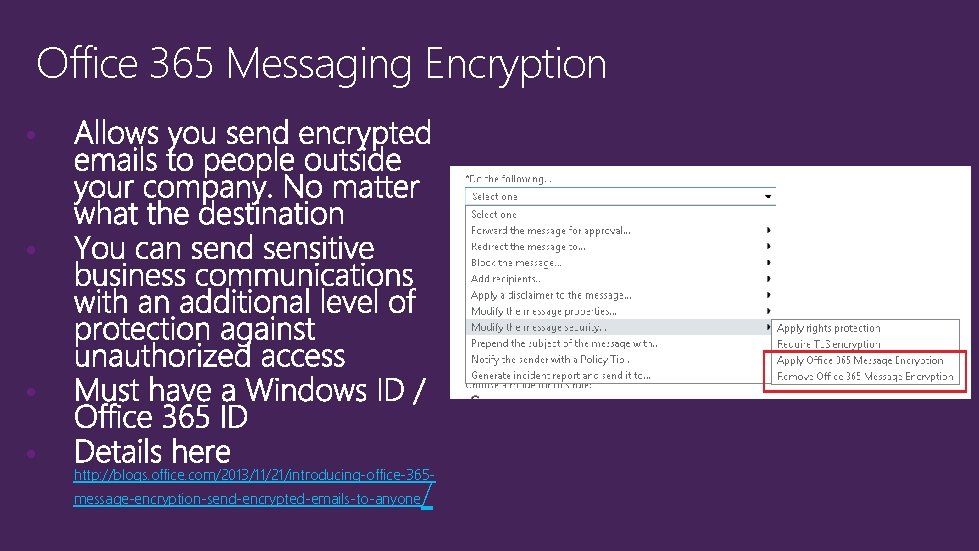
Office 365 Messaging Encryption • • http: //blogs. office. com/2013/11/21/introducing-office-365 message-encryption-send-encrypted-emails-to-anyone /


Exploring Data Leakage

Rights Management deployment options • • •

Office integration w/ Rights Management • For this Office product family… …these restrictions apply for Rights Management use Microsoft Office Professional Plus 2013 Supported for this release. Microsoft Office 2010 Supported for this release. To publish rights-protected content requires Office Professional Plus. To consume rightsprotected content, Office Standard is required. Microsoft Office 2007 Not supported for this release.

Rights Management Services

1 2 3 4 5 6 7 8 Services are highly configurable and scalable without customization. Services are under the Microsoft Security Policy. We provide transparency in data location and transfers. We audit on your behalf and provide certification reports. Microsoft’s liability is capped, consistent with industry standards. Office 365 is an evergreen service. Customers need to stay current. Our solution evolves rapidly with a documented roadmap. We provide services offers to help you migrate to the cloud efficiently.





www. microsoft. com/ trustedcloud www. microsoft. com/sir www. microsoft. com/sdl www. microsoft. com/twc blogs. technet. com/security

http: //technet. microsoft. com/library/dn 765472. aspx http: //technet. microsoft. com/en-us/library/hh 546785. aspx http: //www. microsoft. com/en-us/server-cloud/products/ windows-azure-pack http: //azure. microsoft. com/en-us/

http: //channel 9. msdn. com/Events/Tech. Ed www. microsoft. com/learning http: //microsoft. com/technet http: //developer. microsoft. com



