Microsoft Challenge Handshake Authentication Protocol CS 265 Spring


- Slides: 14

Microsoft Challenge Handshake Authentication Protocol CS 265 Spring 2005 Chung. Shun Wei

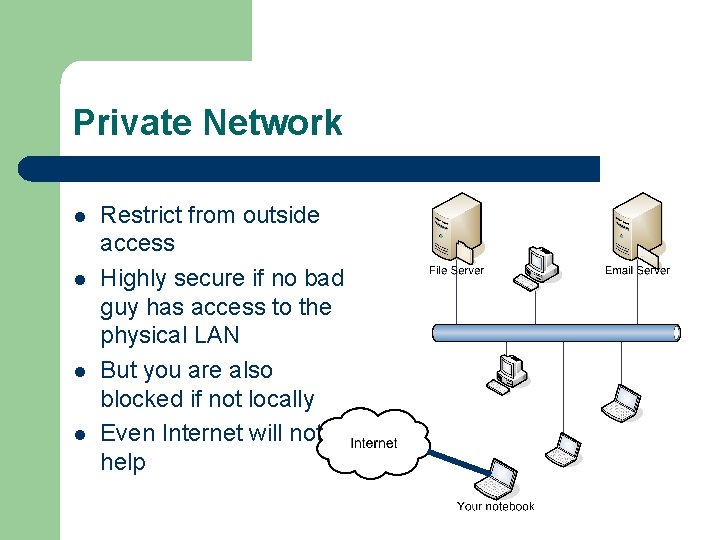
Private Network l l Restrict from outside access Highly secure if no bad guy has access to the physical LAN But you are also blocked if not locally Even Internet will not help

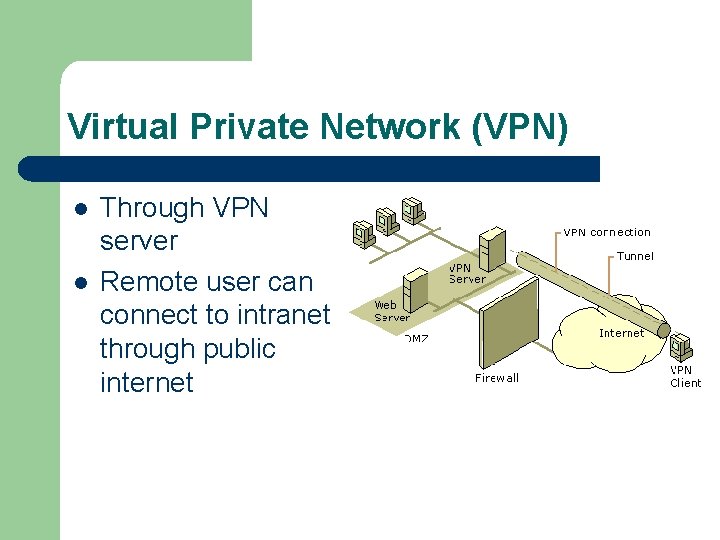
Virtual Private Network (VPN) l l Through VPN server Remote user can connect to intranet through public internet

VPN Authentication l Password Authentication Protocol (PAP) – – l Username & password in clear text Use it only when VPN server only support PAP Challenge Handshake Authentication Protocol (CHAP) – Encrypt password

Microsoft Challenge Handshake Authentication Protocol (MS-CHAP) l l l Base on CHAP MS-CHAP version 1 and version 2 MS-CHAP v 2 is an improvement over MS-CHAP v 1

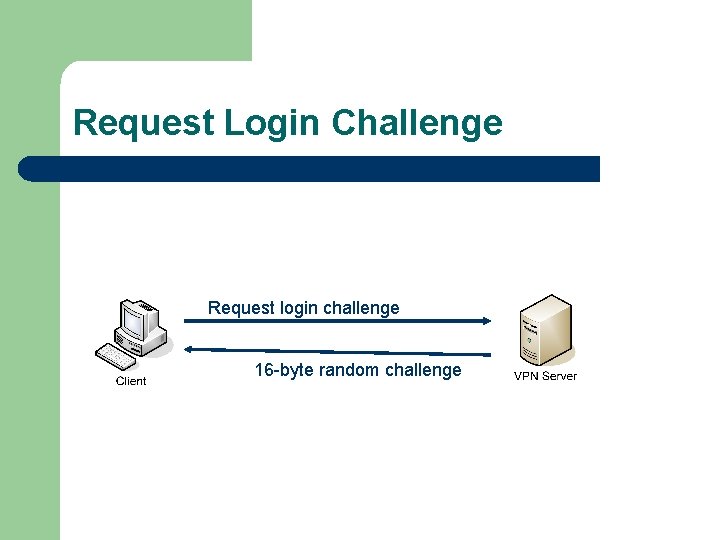
Request Login Challenge Request login challenge 16 -byte random challenge

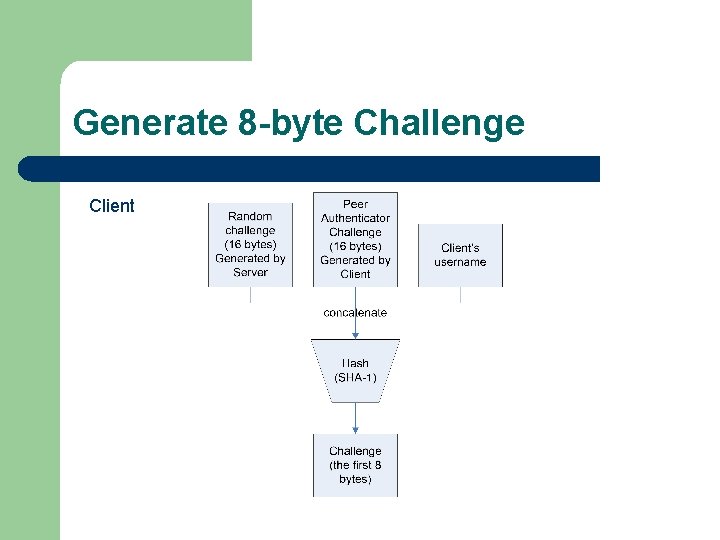
Generate 8 -byte Challenge Client

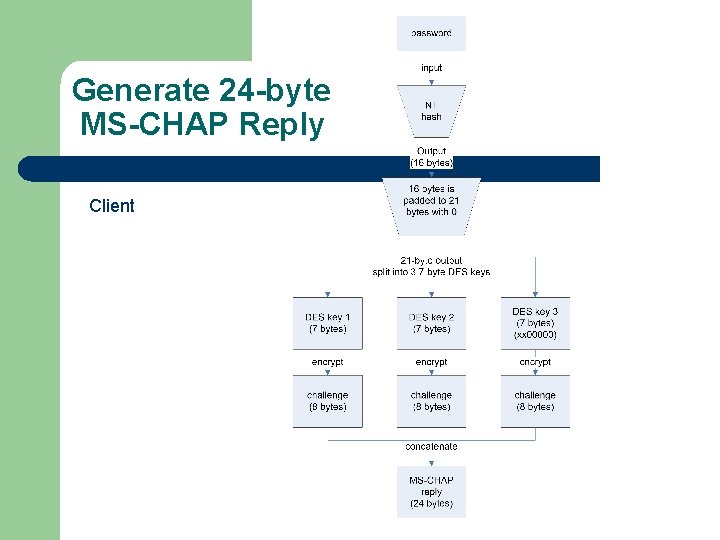
Generate 24 -byte MS-CHAP Reply Client

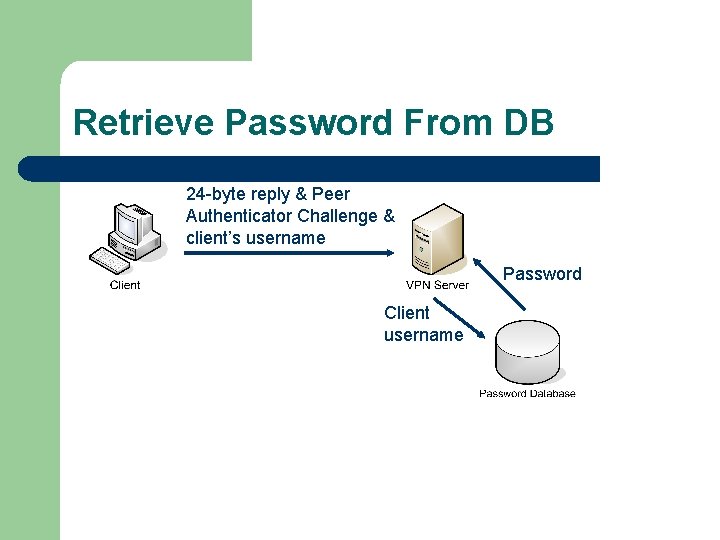
Retrieve Password From DB 24 -byte reply & Peer Authenticator Challenge & client’s username Password Client username

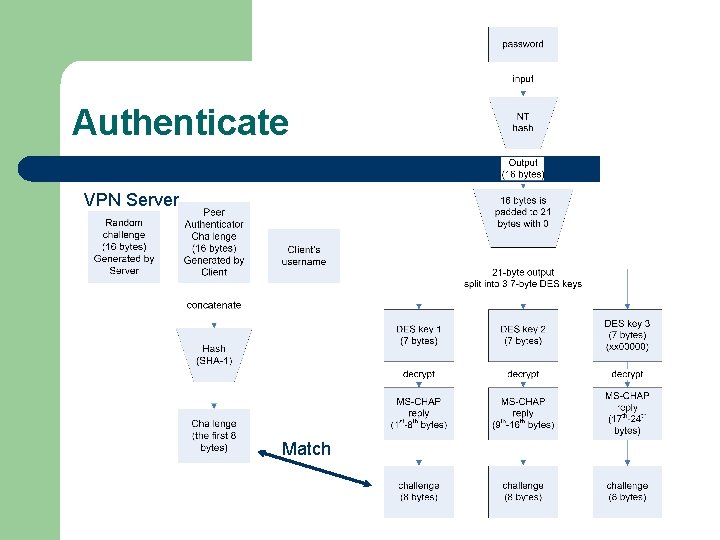
Authenticate VPN Server Match

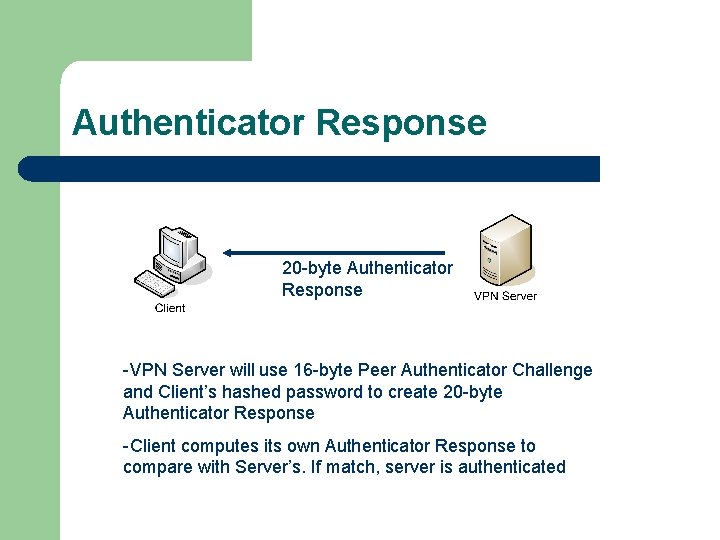
Authenticator Response 20 -byte Authenticator Response -VPN Server will use 16 -byte Peer Authenticator Challenge and Client’s hashed password to create 20 -byte Authenticator Response -Client computes its own Authenticator Response to compare with Server’s. If match, server is authenticated

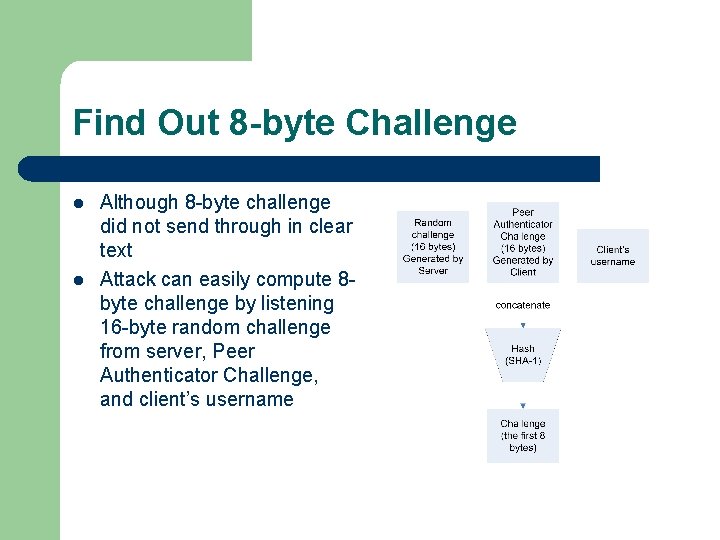
Find Out 8 -byte Challenge l l Although 8 -byte challenge did not send through in clear text Attack can easily compute 8 byte challenge by listening 16 -byte random challenge from server, Peer Authenticator Challenge, and client’s username

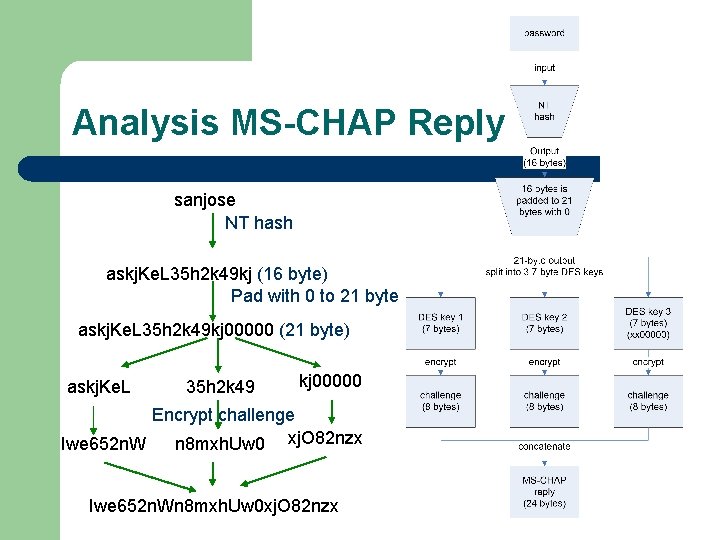
Analysis MS-CHAP Reply sanjose NT hash askj. Ke. L 35 h 2 k 49 kj (16 byte) Pad with 0 to 21 byte askj. Ke. L 35 h 2 k 49 kj 00000 (21 byte) askj. Ke. L 35 h 2 k 49 kj 00000 Encrypt challenge Iwe 652 n. W n 8 mxh. Uw 0 xj. O 82 nzx Iwe 652 n. Wn 8 mxh. Uw 0 xj. O 82 nzx

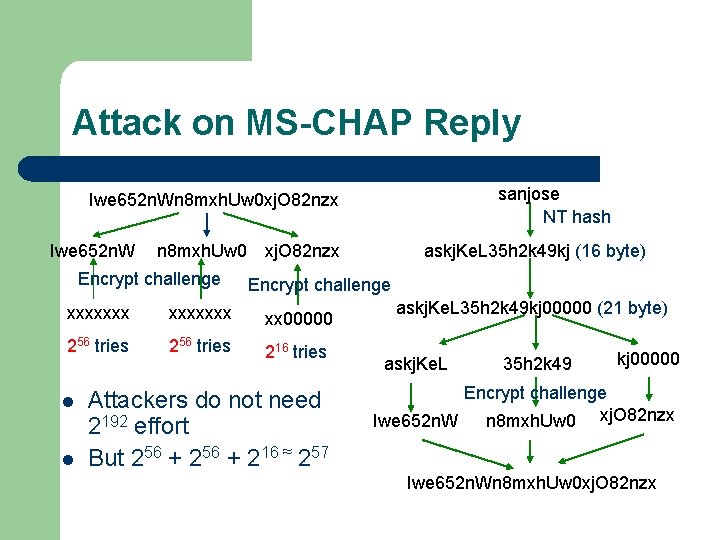
Attack on MS-CHAP Reply sanjose NT hash Iwe 652 n. Wn 8 mxh. Uw 0 xj. O 82 nzx Iwe 652 n. W Encrypt challenge xxxxxxx xx 00000 256 tries 216 tries l l askj. Ke. L 35 h 2 k 49 kj (16 byte) n 8 mxh. Uw 0 xj. O 82 nzx Attackers do not need 2192 effort But 256 + 216 ≈ 257 askj. Ke. L 35 h 2 k 49 kj 00000 (21 byte) askj. Ke. L 35 h 2 k 49 kj 00000 Encrypt challenge Iwe 652 n. W n 8 mxh. Uw 0 xj. O 82 nzx Iwe 652 n. Wn 8 mxh. Uw 0 xj. O 82 nzx