Methods of Protecting the Stack Overflow Vulnerability Aiman

Methods of Protecting the Stack Overflow Vulnerability Aiman Rasheed Department: ICS KFUPM, Dhahran, KSA May 4, 2004

Agenda n n n n Introduction What are Buffer Overflows? How Severe are Buffer Overflows Recent Buffer Overflow Vulnerabilities Most Severe Buffer Overflow Vulnerabilities Requirements to Launch an Attack Goals Attack Targets Benefits an Attacker may get Protection Mechanism Solutions Based Taxonomy Proposed Strategy Conclusion
Introduction n n Operations happening at Function Call Stack Structure

Introduction Operations happening at Function Call n q q q The function’s parameters are saved onto the stack The caller’s registers are also saved onto the stack The return address is saved onto stack Execution is transferred to the called function. Once the function completes its task, it jumps back to the return address saved on the stack
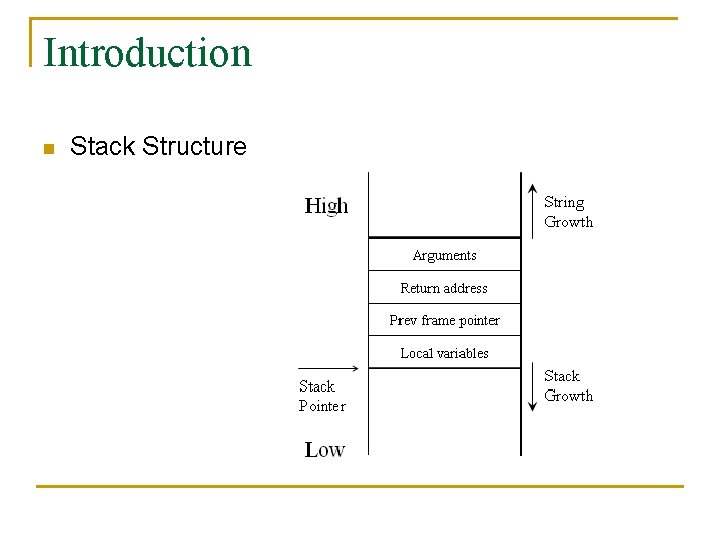
Introduction n Stack Structure
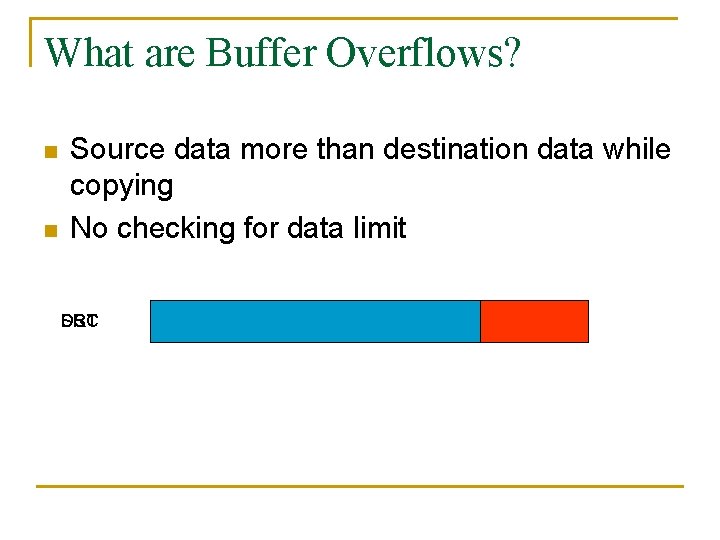
What are Buffer Overflows? n n Source data more than destination data while copying No checking for data limit DST SRC
![What are Buffer Overflows? n A simple example; void main(){ char buffer. A[256]; my. What are Buffer Overflows? n A simple example; void main(){ char buffer. A[256]; my.](http://slidetodoc.com/presentation_image/08324d192a3a54c692c444a3ddc0ee6d/image-7.jpg)
What are Buffer Overflows? n A simple example; void main(){ char buffer. A[256]; my. Function(buffer. A); } void my. Function(char *str) { char buffer. B[16]; strcpy(buffer. B, str); }
![Attack Example char shellcode[] = "xebx 1 fx 5 ex 89x 76x 08x 31xc Attack Example char shellcode[] = "xebx 1 fx 5 ex 89x 76x 08x 31xc](http://slidetodoc.com/presentation_image/08324d192a3a54c692c444a3ddc0ee6d/image-8.jpg)
Attack Example char shellcode[] = "xebx 1 fx 5 ex 89x 76x 08x 31xc 0x 88x 46x 07x 89x 46x 0 cxb 0x 0 b" "x 89xf 3x 8 dx 4 ex 08x 8 dx 56x 0 cxcdx 80x 31xdbx 89xd 8x 40xcd" "x 80xe 8xdcxffxff/bin/sh"; char large_string[128]; void main(){ char buffer[96]; int i; long *long_ptr = (long *) large_string; for (i = 0; i < 32; i++) *(long_ptr + i) = (int) buffer; for (i = 0; i < strlen(shellcode); i++) large_string[i] = shellcode[i]; strcpy(buffer, large_string); }
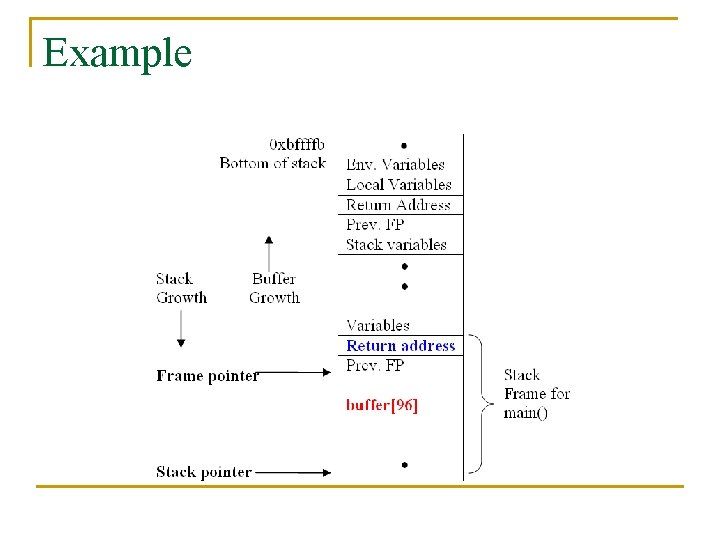
Example
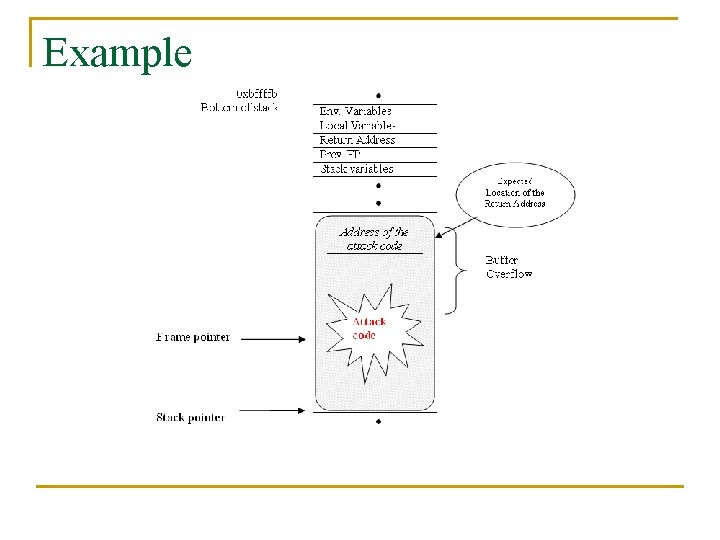
Example
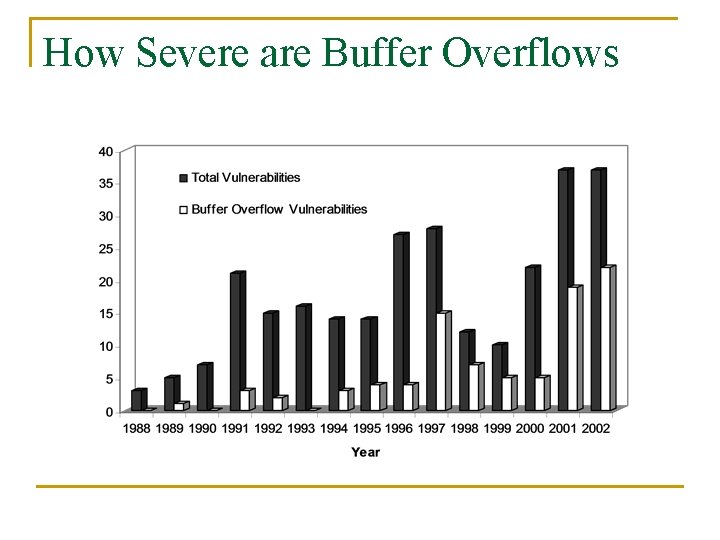
How Severe are Buffer Overflows
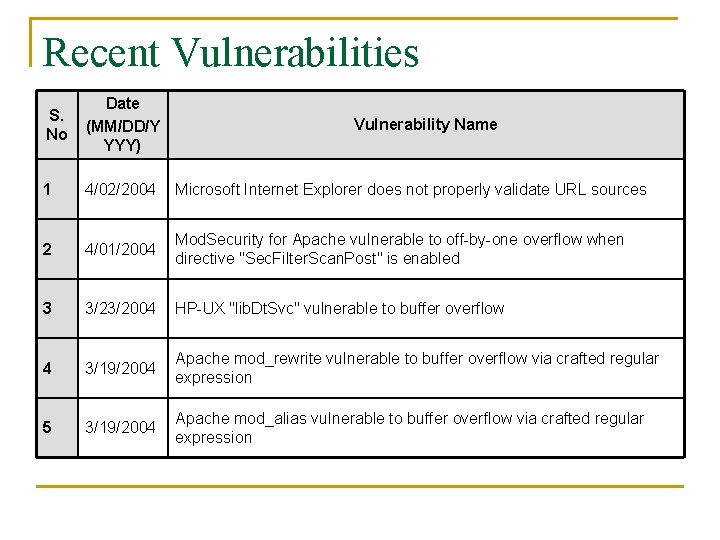
Recent Vulnerabilities S. No Date (MM/DD/Y YYY) 1 4/02/2004 Microsoft Internet Explorer does not properly validate URL sources 2 4/01/2004 Mod. Security for Apache vulnerable to off-by-one overflow when directive "Sec. Filter. Scan. Post" is enabled 3 3/23/2004 HP-UX "lib. Dt. Svc" vulnerable to buffer overflow 4 3/19/2004 Apache mod_rewrite vulnerable to buffer overflow via crafted regular expression 5 3/19/2004 Apache mod_alias vulnerable to buffer overflow via crafted regular expression Vulnerability Name
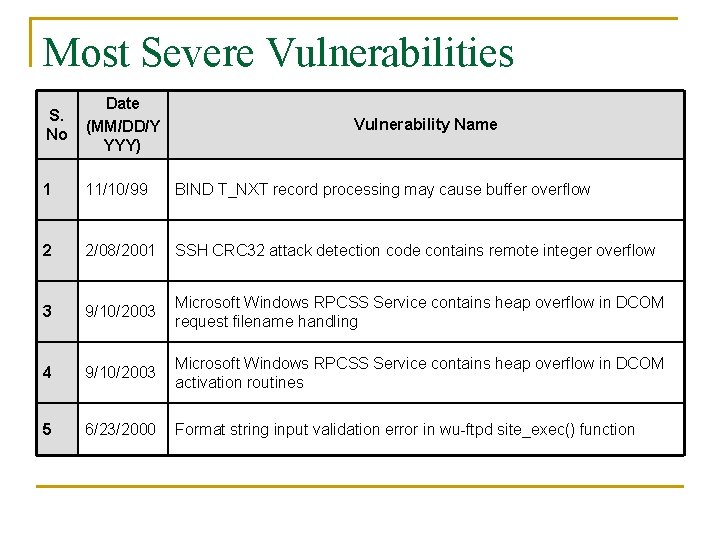
Most Severe Vulnerabilities S. No Date (MM/DD/Y YYY) 1 11/10/99 BIND T_NXT record processing may cause buffer overflow 2 2/08/2001 SSH CRC 32 attack detection code contains remote integer overflow 3 9/10/2003 Microsoft Windows RPCSS Service contains heap overflow in DCOM request filename handling 4 9/10/2003 Microsoft Windows RPCSS Service contains heap overflow in DCOM activation routines 5 6/23/2000 Format string input validation error in wu-ftpd site_exec() function Vulnerability Name
Requirements to Launch an Attack n n n Size of the buffer must be determined Must be able to control the data written into the buffer There must be security sensitive variables or executable program instructions stored below the buffer in stack

Attack Goal n n Insert malicious code also known as ‘Code Injections’ Change the execution path of a program

Attack Targets n Return Address q n Overwriting the Return Address of a function with that of an Attack code Function Pointer q Overwriting the Function Pointer with an address of Attack code
Benefits an Attacker may get! n n n Change privilege from normal user to super user Launch DOS ( Denial of Service) Attacks Crash an application, or may cause it to give incorrect results Launch any Malicious Code fruitful for an attacker Get a remote control on the machine Corrupting application in order to disclose confidential information
Protection Mechanism n Static Approaches q n Requires the analysis of source code for detection and removal of vulnerabilities Dynamic Approaches q Run time preventive measurements
Protection Mechanism n Static Approaches q q Need updated database of programming flaws to test for Need source code recompilation for updated applications Existing vulnerable libraries need to be recompiled again as well Useful for applications that are being developed
Protection Mechanism n Dynamic Approaches q q q Need database of known attacks No need of recompilation of source code or libraries It can be applied to legacy systems
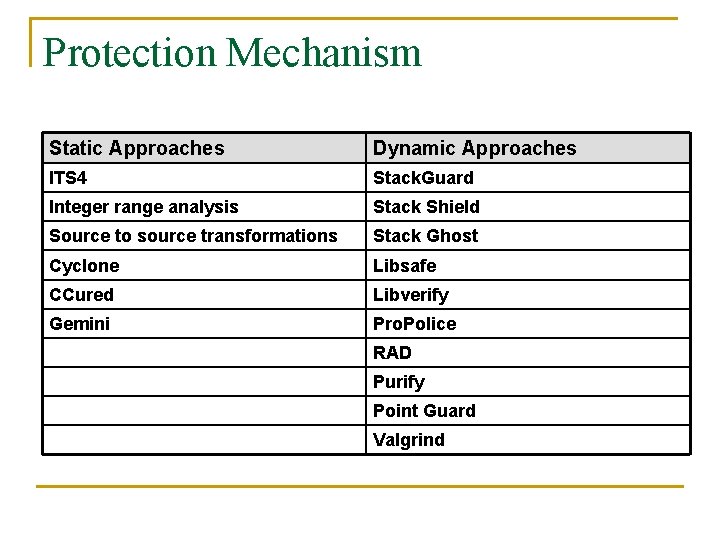
Protection Mechanism Static Approaches Dynamic Approaches ITS 4 Stack. Guard Integer range analysis Stack Shield Source to source transformations Stack Ghost Cyclone Libsafe CCured Libverify Gemini Pro. Police RAD Purify Point Guard Valgrind

Solution Based Taxonomy n Return Address Protection q q q n Access Violation Probing q q n Canary Insertion Guard Value Return Address Repository Code Segment Boundary Checking Run-time Memory Access Checking Bounds Checking q q Array Bounds Checking Source to Source Transformation
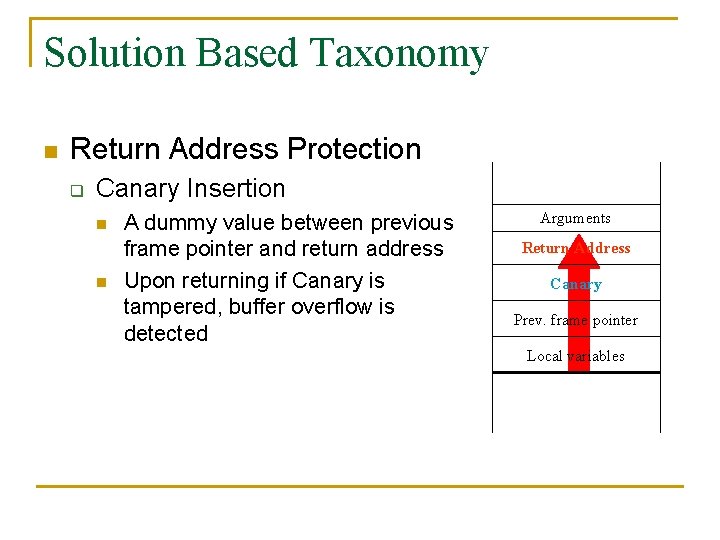
Solution Based Taxonomy n Return Address Protection q Canary Insertion n n A dummy value between previous frame pointer and return address Upon returning if Canary is tampered, buffer overflow is detected Arguments Return Address Canary Prev. frame pointer Local variables
Solution Based Taxonomy n Return Address Protection q Canary Insertion, some ways to circumvent n n q Keep the Canary as intact; overwriting it with the same value Jump over it using an abused pointer Counter solutions n n Random Canary Terminator Canary as NULL character, -1, carriage return and line feed etc
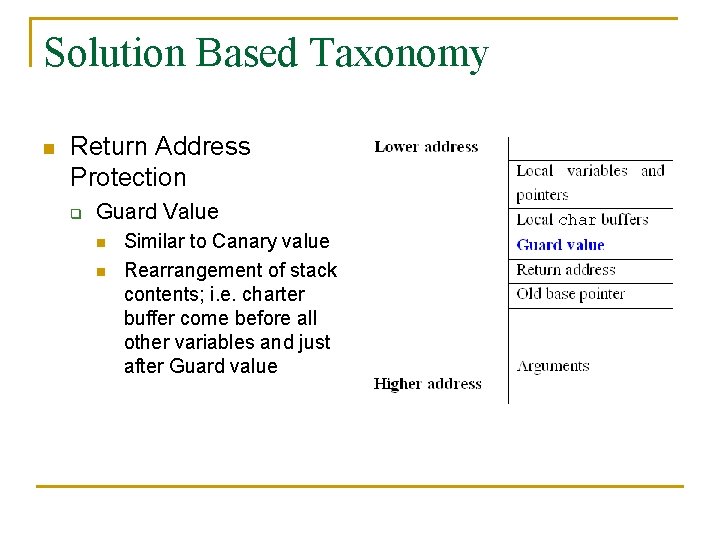
Solution Based Taxonomy n Return Address Protection q Guard Value n n Similar to Canary value Rearrangement of stack contents; i. e. charter buffer come before all other variables and just after Guard value

Solution Based Taxonomy n Return Address Protection q Return Address Repository n n At every function call, new stack frame is created and copy of return address is saved When the function returns; q q q Copy of Return Address is retrieved Retrieved copy is compared with Return Address Examples; n Stack. Guard, Propolice, Libverify, etc
Solution Based Taxonomy n Access Violation Probing q Code Segment Boundary Checking n n To make it assured before executing any code that it belongs to the code segment Storing a global variable in data segment and its address is taken as boundary value Any reference outside this boundary value is taken as malicious activity Example; Stack. Shield

Solution Based Taxonomy n Access Violation Probing q Run-time Memory Access Checking n n n Concerns incorrect read and/or write to memory locations Referring to block of memory which is already deallocated Examples; Valgrind, Cyclone, Purify etc

Solution Based Taxonomy n Bounds Checking q Array Bounds Checking n n n Useful technique for code injection attacks protection Needs manual checking to look for illegal buffer assignments Keeping array limits for checking
Solution Based Taxonomy n Bounds Checking q Source to Source Transformation n n n Used to detect unsafe string operations Programs are instrumented with additional variables Instrumented variables describe string attributes Such variables are checked statically Space complexity is increased Good for small scale applications

Proposed Strategy n Memory Mirror q q A bit acting as mirror against every memory locations Set the bit corresponding to memory location containing return address Overwriting of return address will be protected as bit is already set It works as atomic mutex
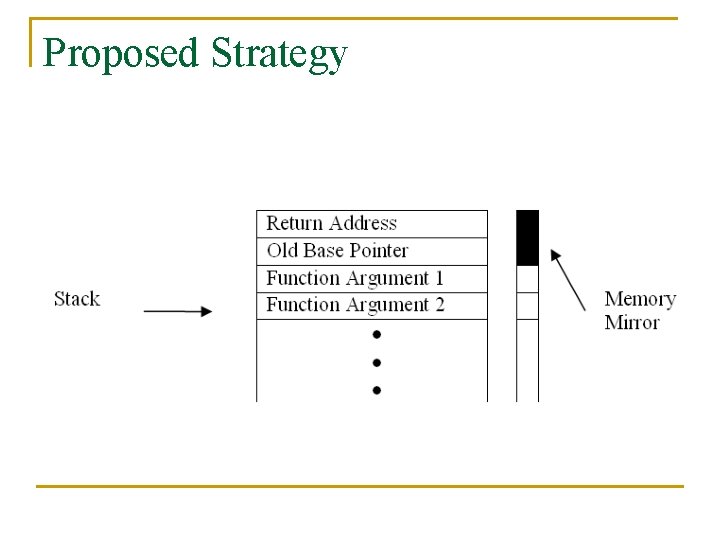
Proposed Strategy

Conclusion n n In today’s computing environment, one of the most common ways of breaching system security is Buffer Overflow Two basic approaches are Static and Dynamic Overlapping solutions can be categorized as; Return Address Protection, Access Violation Probing and Bounds Checking Performance criteria decides whether to use the solution as a debugging tool or as normal application A Memory Mirror approach is presented to enhance security of a system

Special Thanks Dr. Khalid Salah & Syed Zeeshan Muzaffar

Thank You

Q&A
- Slides: 36