Metafuzz 0 9 Deep Fuzzing MS Word Office


















- Slides: 29

Metafuzz 0. 9 Deep Fuzzing MS Word / Office (With Ruby) (rubyrubypythonsucksyayruby!) Private & Confidential Property of COSEINC

Basic Fuzzer Problems for Word • • • Opening Word is SLOW Success detection is harder than crash detection Dr Watson, Dialog Boxes, Hangs, HDD Grind Lots of internal exception handling Hard to parse file formats Massive Attack Surface means millions of tests • My first fuzzer did a blistering 20 -30 tests per minute. Private & Confidential Property of COSEINC

omgwtfdoc? Each FKP can be viewed as a bucket or bin that contains the properties of a certain range of FCs in the Word file. In Word files, a PLC, the plcfbte (PLex of FCs containing Bin Table Entries) is maintained. It records the association between a particular range of FCs and the PN (Page Number) of the FKP that contains the properties for that FC range in the file. In a complex (fast-saved) Word document, FKP pages are intermingled with pages of text in a random pattern which reflects the history of past fast saves. In a complex document, a plcfbte. Chpx which records the location of every CHPX FKP must be stored and a plcfbte. Papx which records the location of every PAPX FKP must be stored. In a non-complex, full-saved document, all of the CHPX FKPS are recorded in consecutive 512 -byte pages with the FKPs recorded in ascending FC order, as are all of the PAPX FKPS. A plcfbte. Lvcx serves the same purpose for LVCX FKPS. In a full save document, the plcfbte‘s may not have been able to expand during the save process due to a lack of RAM. In this situation, the plcfbte‘s are interspersed with the property pages in a linked list of FBD pages. Private & Confidential Property of COSEINC

General Approach • Distributed fuzzing will be essential for speed • Use OLE automation to detect success • Independent process to kill hung applications and deal with dialog boxes • Write a few core parsers that abstract the scut work of the binary format and focus on deep structures • Integrate with CDB to catch first chance exceptions and gather information Private & Confidential Property of COSEINC

Things to know about Word. doc http: //www. microsoft. com/interop/docs/Office. Binary. Formats. mspx • Also, check “Supporting Technologies” link for spec for “Compound Binary File Format Specification” • Basically, . DOC, . PPT and. XLS are OLE Structured Storage files, which means they are more or less a FAT filesystem inside a file. • This means that structures you want to fuzz may well be broken into bits and scattered at random throughout the file. • ruby-ole gem by Charles Lowe helps a LOT here. Install it, then… require ‘ruby-ole’ Ole: : Storage. open('c: tmp. doc', 'rb+') {|ole| ole. file. open("1 Table", "wb+") {|f| f. write( fuzz(f. read) ) } • TSBrowse Demo Private & Confidential Property of COSEINC

Things to know about Word. doc • Your guide to the file – the FIB (File Information Block), a 1472 byte page turner. • Lots of general info, followed by a long list of offset / length pairs describing structures in the Table Stream. • FIBBrowse Demo • Parsing it – Binstruct • It’s little endian. That’s important. Private & Confidential Property of COSEINC

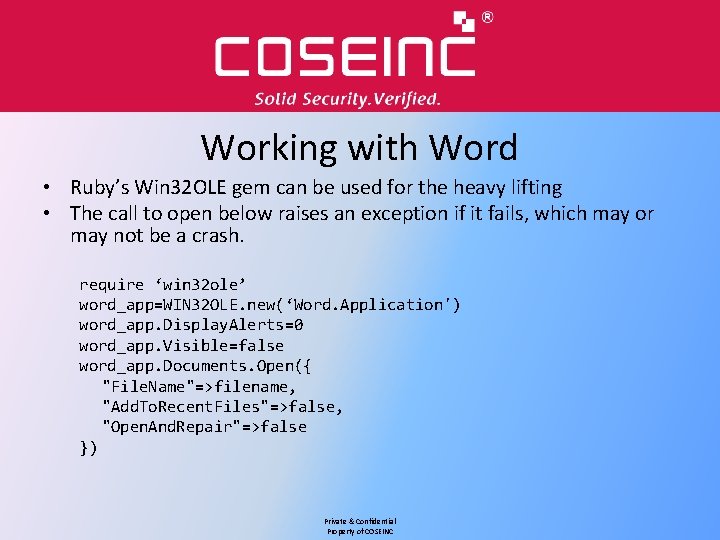
Working with Word • Ruby’s Win 32 OLE gem can be used for the heavy lifting • The call to open below raises an exception if it fails, which may or may not be a crash. require ‘win 32 ole’ word_app=WIN 32 OLE. new(‘Word. Application') word_app. Display. Alerts=0 word_app. Visible=false word_app. Documents. Open({ "File. Name"=>filename, "Add. To. Recent. Files"=>false, "Open. And. Repair"=>false }) Private & Confidential Property of COSEINC

Working with Word 1. Open the Visual Basic Editor from inside Word ALT+F 11 2. Press F 2 for the Object Browser 3. Poke around. Private & Confidential Property of COSEINC

Working with Word require ‘win 32/registry’ Win 32: : Registry: : HKEY_CURRENT_USER. open( 'SOFTWAREMicrosoftOffice12. 0WordResiliency', Win 32: : Registry: : KEY_WRITE) do |reg| reg. delete_key "Startup. Items" rescue nil reg. delete_key "Disabled. Items" rescue nil end Private & Confidential Property of COSEINC

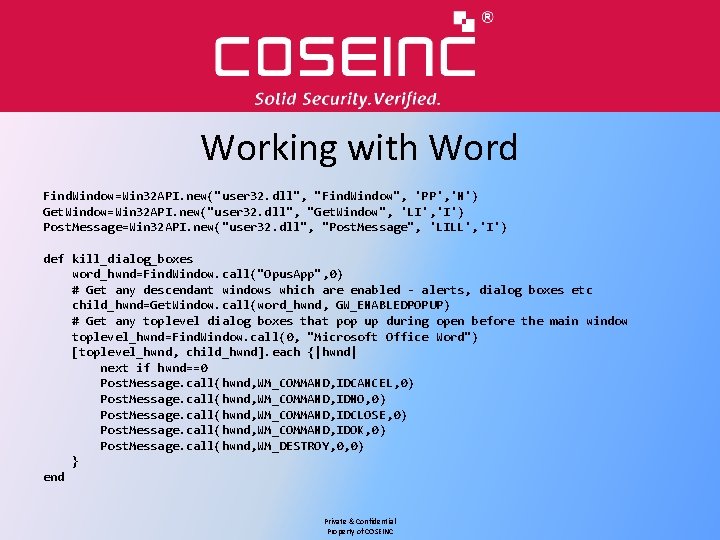
Working with Word • Word has a massive, horrible array of dialog boxes with which to hang your fuzzer. • Do I have dialog boxes to deal with? GW_ENABLEDPOPUP=6 Find. Window=Win 32 API. new("user 32. dll", "Find. Window", 'PP', 'N') Get. Window=Win 32 API. new("user 32. dll", "Get. Window", 'LI', 'I') window_caption=rand(2**32). to_s win 32 ole_app. caption=window_caption window_id=Find. Window. call(0, window_caption) Get. Window. call(window_id, GW_ENABLEDPOPUP)!=0 Private & Confidential Property of COSEINC

Working with Word Find. Window=Win 32 API. new("user 32. dll", "Find. Window", 'PP', 'N') Get. Window=Win 32 API. new("user 32. dll", "Get. Window", 'LI', 'I') Post. Message=Win 32 API. new("user 32. dll", "Post. Message", 'LILL', 'I') def kill_dialog_boxes word_hwnd=Find. Window. call("Opus. App", 0) # Get any descendant windows which are enabled - alerts, dialog boxes etc child_hwnd=Get. Window. call(word_hwnd, GW_ENABLEDPOPUP) # Get any toplevel dialog boxes that pop up during open before the main window toplevel_hwnd=Find. Window. call(0, "Microsoft Office Word") [toplevel_hwnd, child_hwnd]. each {|hwnd| next if hwnd==0 Post. Message. call(hwnd, WM_COMMAND, IDCANCEL, 0) Post. Message. call(hwnd, WM_COMMAND, IDNO, 0) Post. Message. call(hwnd, WM_COMMAND, IDCLOSE, 0) Post. Message. call(hwnd, WM_COMMAND, IDOK, 0) Post. Message. call(hwnd, WM_DESTROY, 0, 0) } end Private & Confidential Property of COSEINC

Working with Word creates temp files all over the place This fills up your client disk and fragments it Best thing to do is create a RAMDisk (later) ~$foo. doc gets created next to foo. doc Other temp files may be created in %TMP% or %TEMP% Still more in. . . Temporary Internet Files/Content. Word and Temporary Internet Files/Content. Office • Those directories may be hidden even when “show hidden files” is turned on, so you may need to type the name into the File Browser. • • • Private & Confidential Property of COSEINC

Integrating the Debugger I used CDB Command line version of Win. Dbg, just as powerful Instead of painfully wrapping a DLL, I cheated. Take CDB, wrap its STDIN, STDOUT and STDERR Some hoopy code required for Ruby 1. 8 since popen doesn’t work properly and had to be rewritten • Use a Connector class I had already, which manages a read queue from the target and uses blocking writes • • • Private & Confidential Property of COSEINC

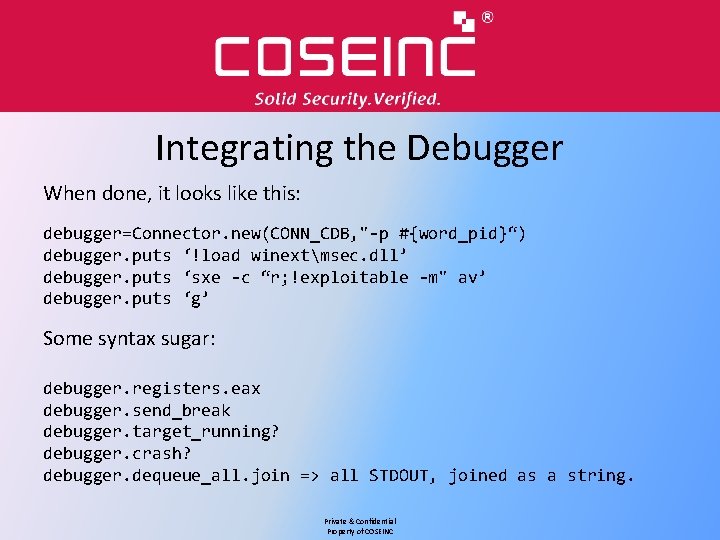
Integrating the Debugger When done, it looks like this: debugger=Connector. new(CONN_CDB, "-p #{word_pid}“) debugger. puts ‘!load winextmsec. dll’ debugger. puts ‘sxe -c “r; !exploitable -m" av’ debugger. puts ‘g’ Some syntax sugar: debugger. registers. eax debugger. send_break debugger. target_running? debugger. crash? debugger. dequeue_all. join => all STDOUT, joined as a string. Private & Confidential Property of COSEINC

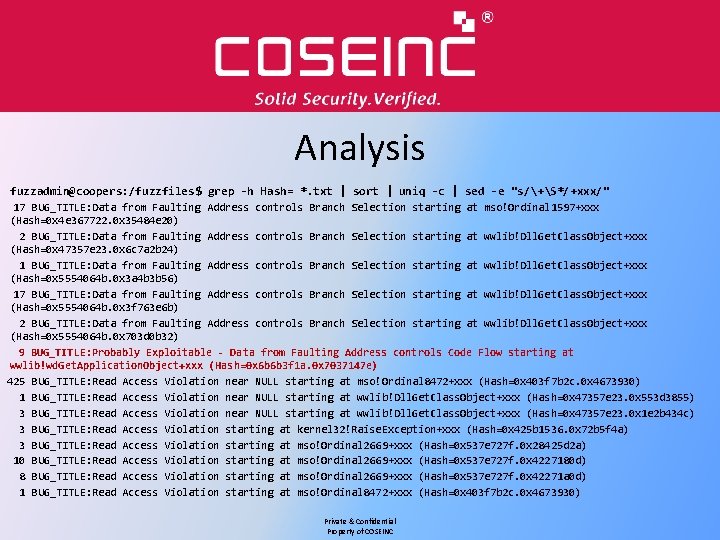
Analysis fuzzadmin@coopers: /fuzzfiles$ grep -h CLASSIFICATION *. txt | sort | uniq -c 9 CLASSIFICATION: PROBABLY_EXPLOITABLE 429 CLASSIFICATION: PROBABLY_NOT_EXPLOITABLE 64 CLASSIFICATION: UNKNOWN fuzzadmin@coopers: /fuzzfiles$ grep -h SHORT *. txt | sort | uniq -c 25 SHORT_DESCRIPTION: Read. AV 429 SHORT_DESCRIPTION: Read. AVNear. Null 39 SHORT_DESCRIPTION: Tainted. Data. Controls. Branch. Selection 9 SHORT_DESCRIPTION: Tainted. Data. Controls. Code. Flow Private & Confidential Property of COSEINC

Analysis fuzzadmin@coopers: /fuzzfiles$ grep -h Hash= *. txt | sort | uniq -c | sed -e "s/+S*/+xxx/" 17 BUG_TITLE: Data from Faulting Address controls Branch Selection starting at mso!Ordinal 1597+xxx (Hash=0 x 4 e 367722. 0 x 35484 e 20) 2 BUG_TITLE: Data from Faulting Address controls Branch Selection starting at wwlib!Dll. Get. Class. Object+xxx (Hash=0 x 47357 e 23. 0 x 6 c 7 a 2 b 24) 1 BUG_TITLE: Data from Faulting Address controls Branch Selection starting at wwlib!Dll. Get. Class. Object+xxx (Hash=0 x 5554064 b. 0 x 3 a 4 b 3 b 56) 17 BUG_TITLE: Data from Faulting Address controls Branch Selection starting at wwlib!Dll. Get. Class. Object+xxx (Hash=0 x 5554064 b. 0 x 3 f 763 e 6 b) 2 BUG_TITLE: Data from Faulting Address controls Branch Selection starting at wwlib!Dll. Get. Class. Object+xxx (Hash=0 x 5554064 b. 0 x 703 d 0 b 32) 9 BUG_TITLE: Probably Exploitable - Data from Faulting Address controls Code Flow starting at wwlib!wd. Get. Application. Object+xxx (Hash=0 x 6 b 6 b 3 f 1 a. 0 x 7037147 e) 425 BUG_TITLE: Read Access Violation near NULL starting at mso!Ordinal 8472+xxx (Hash=0 x 403 f 7 b 2 c. 0 x 4673930) 1 BUG_TITLE: Read Access Violation near NULL starting at wwlib!Dll. Get. Class. Object+xxx (Hash=0 x 47357 e 23. 0 x 553 d 3855) 3 BUG_TITLE: Read Access Violation near NULL starting at wwlib!Dll. Get. Class. Object+xxx (Hash=0 x 47357 e 23. 0 x 1 e 2 b 434 c) 3 BUG_TITLE: Read Access Violation starting at kernel 32!Raise. Exception+xxx (Hash=0 x 425 b 1536. 0 x 72 b 5 f 4 a) 3 BUG_TITLE: Read Access Violation starting at mso!Ordinal 2669+xxx (Hash=0 x 537 e 727 f. 0 x 28425 d 2 a) 10 BUG_TITLE: Read Access Violation starting at mso!Ordinal 2669+xxx (Hash=0 x 537 e 727 f. 0 x 4227180 d) 8 BUG_TITLE: Read Access Violation starting at mso!Ordinal 2669+xxx (Hash=0 x 537 e 727 f. 0 x 42271 a 0 d) 1 BUG_TITLE: Read Access Violation starting at mso!Ordinal 8472+xxx (Hash=0 x 403 f 7 b 2 c. 0 x 4673930) Private & Confidential Property of COSEINC

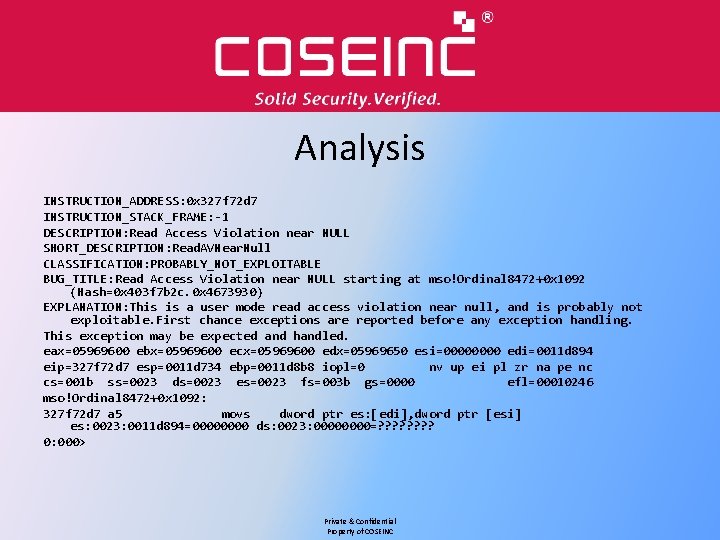
Analysis INSTRUCTION_ADDRESS: 0 x 327 f 72 d 7 INSTRUCTION_STACK_FRAME: -1 DESCRIPTION: Read Access Violation near NULL SHORT_DESCRIPTION: Read. AVNear. Null CLASSIFICATION: PROBABLY_NOT_EXPLOITABLE BUG_TITLE: Read Access Violation near NULL starting at mso!Ordinal 8472+0 x 1092 (Hash=0 x 403 f 7 b 2 c. 0 x 4673930) EXPLANATION: This is a user mode read access violation near null, and is probably not exploitable. First chance exceptions are reported before any exception handling. This exception may be expected and handled. eax=05969600 ebx=05969600 ecx=05969600 edx=05969650 esi=0000 edi=0011 d 894 eip=327 f 72 d 7 esp=0011 d 734 ebp=0011 d 8 b 8 iopl=0 nv up ei pl zr na pe nc cs=001 b ss=0023 ds=0023 es=0023 fs=003 b gs=0000 efl=00010246 mso!Ordinal 8472+0 x 1092: 327 f 72 d 7 a 5 movs dword ptr es: [edi], dword ptr [esi] es: 0023: 0011 d 894=0000 ds: 0023: 0000=? ? ? ? 0: 000> Private & Confidential Property of COSEINC

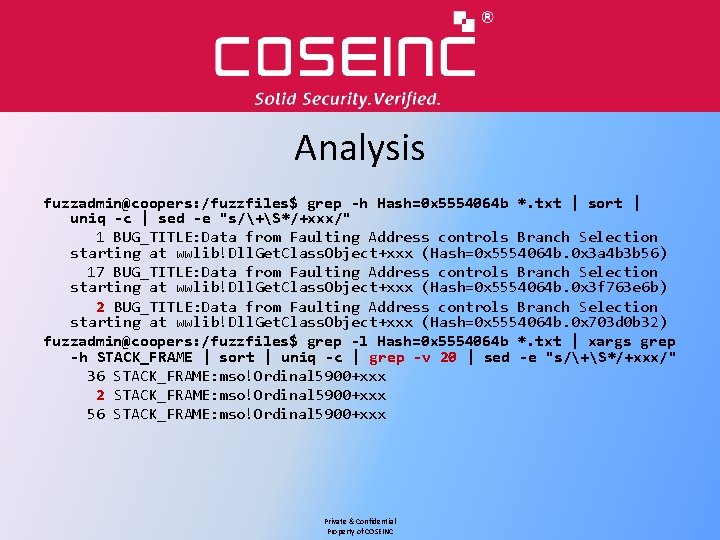
Analysis fuzzadmin@coopers: /fuzzfiles$ grep -h Hash=0 x 5554064 b *. txt | sort | uniq -c | sed -e "s/+S*/+xxx/" 1 BUG_TITLE: Data from Faulting Address controls Branch Selection starting at wwlib!Dll. Get. Class. Object+xxx (Hash=0 x 5554064 b. 0 x 3 a 4 b 3 b 56) 17 BUG_TITLE: Data from Faulting Address controls Branch Selection starting at wwlib!Dll. Get. Class. Object+xxx (Hash=0 x 5554064 b. 0 x 3 f 763 e 6 b) 2 BUG_TITLE: Data from Faulting Address controls Branch Selection starting at wwlib!Dll. Get. Class. Object+xxx (Hash=0 x 5554064 b. 0 x 703 d 0 b 32) fuzzadmin@coopers: /fuzzfiles$ grep -l Hash=0 x 5554064 b *. txt | xargs grep -h STACK_FRAME | sort | uniq -c | grep -v 20 | sed -e "s/+S*/+xxx/" 36 STACK_FRAME: mso!Ordinal 5900+xxx 2 STACK_FRAME: mso!Ordinal 5900+xxx 56 STACK_FRAME: mso!Ordinal 5900+xxx Private & Confidential Property of COSEINC

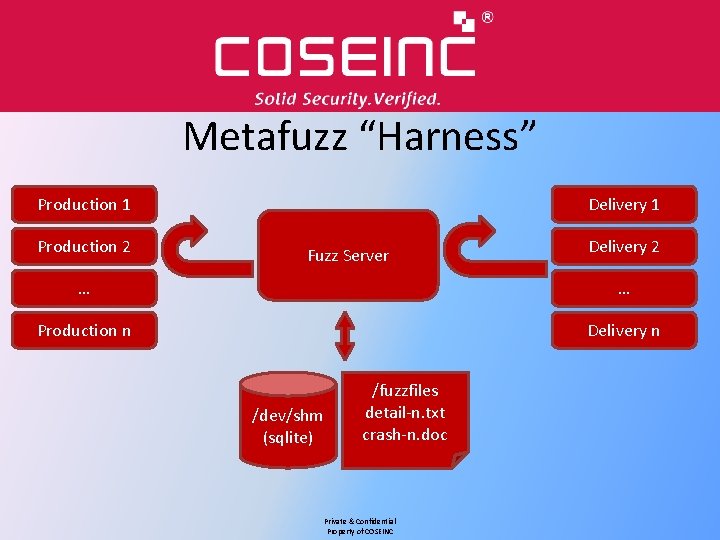
Metafuzz “Harness” Production 1 Production 2 Delivery 1 Fuzz Server Delivery 2 … … Production n Delivery n /dev/shm (sqlite) /fuzzfiles detail-n. txt crash-n. doc Private & Confidential Property of COSEINC

Metafuzz Harness • Almost all the code is generic, and could be used for any file fuzzing work (just need to work out how to test for success etc) • All components auto-resume, so code can be upgraded on the fly without restarting test streams • Very simple, home grown protocol using JSON-serialised hashes over DJBNetstrings • Could write production clients in any language • Network based on Ruby Event. Machine, single threaded, using the Reactor pattern • DB SQLite for now, easy to upgrade • /dev/shm on Ubuntu is your friend for DB Writes • RESTful web interface (beta) to enable production clients to check results and full debugger output for any test (adaptive fuzzing? ) Private & Confidential Property of COSEINC

Optimising Fuzzclients • The ideal client for Office fuzzing is – Stable – no disk bloat, no memory leaks etc – Fast – performs as well as Windows will let us – Managable without a GUI (Thanks to #uncon / Ollie Whitehouse for some great tips here. . . ) Private & Confidential Property of COSEINC

Building an XP Fuzzclient for ESXi • • • (or any VMWare) 1024 MB RAM, or as much as you can spare 8 -10 GB Disk, pre-allocated Enhanced vmxnet NIC (just change the. vmx) No background No screensaver Private & Confidential Property of COSEINC

Building an XP Fuzzclient for ESXi • My Computer->Properties->Advanced – Visual Effects -> Adjust for best performance – Processor Scheduling -> Programs – Memory Usage -> System Cache – Virtual Memory -> Change to 0 MB Private & Confidential Property of COSEINC

Building an XP Fuzzclient for ESXi • Install a RAMDisk. I got a free one at: http: //www. mydigitallife. info/2007/05/27/free-ramdisk-for-windows-vista-xp-2000 -and-2003 -server/ • 64 MB should be enough, as long as you clear it often • Change Temporary Internet Files, and ALL temp files to point to R: Temp • Two User Environment Variables %TMP%, %TEMP% and two System Environment Variables • Write your fuzzer tests to the RAMDisk • Check your work with Process Monitor http: //technet. microsoft. com/en-us/sysinternals/bb 896645. aspx (You’ll still have a little) Private & Confidential Property of COSEINC

Building an XP Fuzzclient for ESXi • • Last but definitely not least. . . gflags /p /enable WINWORD. EXE /full (not sure if that survives a reboot) Full page heap kills performance, but greatly increases the chance of crashing on heap corruption Private & Confidential Property of COSEINC

Building an XP Fuzzclient for ESXi • Office Apps want to be logged on. • We don’t want to type passwords on 72 clients. • Disable user passwords when logging on: http: //support. microsoft. com/kb/315231 • We used an oldskool. bat in the startup folder: – copy /y all code from a share – (re)-enable gflags just in case – re-create required directories in RAMDisk – start the fuzzer Private & Confidential Property of COSEINC

Our Fuzzpark • The Hardware: • 5 Servers, Dual Quad-Core Xeon, 16 GB RAM, 4 x 300 GB SATA disks, one per SATA port • (actually not very high spec, these days) • GB Switch, MTU 9000, all clients with TSO enabled • The Logical Network: • 2 Quad Processor Ubuntu 8. 10 64 -bit servers running a Server and several Production processes each • 72 XP Fuzzclients • Ghetto style shellscripts to restart all clients, power-on, power-off etc from the ESXi command-line Private & Confidential Property of COSEINC

Our Fuzzpark • Peak performance ~50 tests/sec • Peak with Page Heap ~30 tests/sec • Average disk usage per Fuzzclient server ~150 KB/sec (for all 16 clients) • Average CPU usage per Fuzzclient server 99. 99% • Ubuntu Server guests ~30% CPU, could probably handle another 32+ clients Private & Confidential Property of COSEINC

Beer! But questions may be asked first. Private & Confidential Property of COSEINC