Memory Management for RealTime Java Hierarchical RealTime Java
- Slides: 1

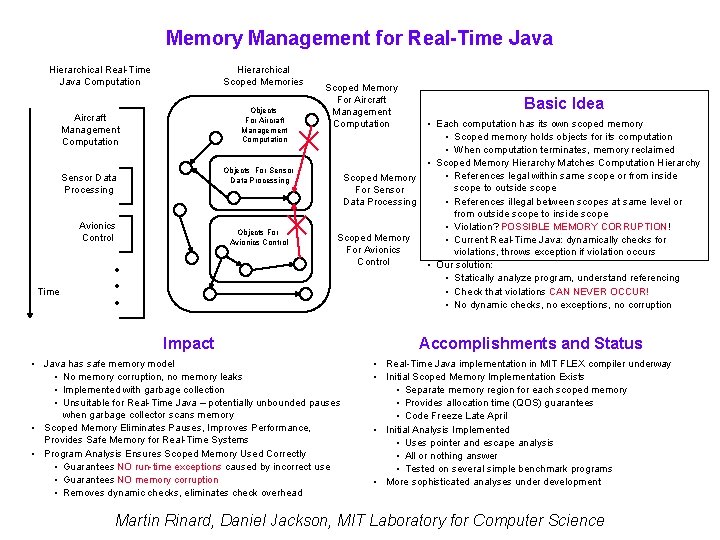
Memory Management for Real-Time Java Hierarchical Real-Time Java Computation Hierarchical Scoped Memories Objects For Aircraft Management Computation Objects For Sensor Data Processing Avionics Control Time Scoped Memory For Aircraft Management Computation Objects For Avionics Control • • • Scoped Memory For Sensor Data Processing Scoped Memory For Avionics Control Impact • Java has safe memory model • No memory corruption, no memory leaks • Implemented with garbage collection • Unsuitable for Real-Time Java – potentially unbounded pauses when garbage collector scans memory • Scoped Memory Eliminates Pauses, Improves Performance, Provides Safe Memory for Real-Time Systems • Program Analysis Ensures Scoped Memory Used Correctly • Guarantees NO run-time exceptions caused by incorrect use • Guarantees NO memory corruption • Removes dynamic checks, eliminates check overhead Basic Idea • Each computation has its own scoped memory • Scoped memory holds objects for its computation • When computation terminates, memory reclaimed • Scoped Memory Hierarchy Matches Computation Hierarchy • References legal within same scope or from inside scope to outside scope • References illegal between scopes at same level or from outside scope to inside scope • Violation? POSSIBLE MEMORY CORRUPTION! • Current Real-Time Java: dynamically checks for violations, throws exception if violation occurs • Our solution: • Statically analyze program, understand referencing • Check that violations CAN NEVER OCCUR! • No dynamic checks, no exceptions, no corruption Accomplishments and Status • Real-Time Java implementation in MIT FLEX compiler underway • Initial Scoped Memory Implementation Exists • Separate memory region for each scoped memory • Provides allocation time (QOS) guarantees • Code Freeze Late April • Initial Analysis Implemented • Uses pointer and escape analysis • All or nothing answer • Tested on several simple benchmark programs • More sophisticated analyses under development Martin Rinard, Daniel Jackson, MIT Laboratory for Computer Science