MEDICAL DEVICE AND HEALTHCARE IT JOINT STRATEGIC PLAN







- Slides: 12

MEDICAL DEVICE AND HEALTHCARE IT JOINT STRATEGIC PLAN Task Group Co-chairs • Kevin Mc. Donald - Mayo Clinic • Rob Suarez – BD • Aftin Ross - FDA

BACKGROUND • Healthcare and Public Health Sector Coordinating Council • 2013 Presidential Policy Directive – 16 critical industry identified and a charge to organize a public / private partnership to protect these essential assets • Designated Sector Coordinator by HHS & DHS • Coordinates collaboration between private and public sector • Health Care Industry Cybersecurity Task Force Report • Published in June 2017 • 6 imperatives that are the focus of the Cybersecurity Working Group • #2 – Increase security and resilience of medical devices and health IT • Healthcare Sector Coordinating Council Joint Cybersecurity Working Group • >300 people involved, 180 private sector organization and 7 government bodies • One of the standing working groups in the HSCC • Health Care Sector Coordinating Council Cybersecurity Task groups • 13 task groups • Range from Medical Technology Cyber Security Risk Management to Future Gazing

MEDICAL TECHNOLOGY & HEALTHCARE IT CYBERSECURITY TASK GROUP Objectives: Establish a voluntary framework and joint strategic plan for medical devices and healthcare information technology cybersecurity which outlines how to achieve the following: • Address risk of end-of-life and legacy products • Promote transparency on security and its relation to patient safety for products • Provide consistent secure product development practices • Clarify vulnerability communication and incident response coordination • Assess maturity and establish milestones for achieving success • Create governance structure for continuous improvement • Participants: Medical Device Manufacturers, Healthcare IT Vendors, Healthcare Providers, Trade Associations, Federal Agencies, Standards Organizations, and Security Technology and Research

MEDICAL TECHNOLOGY & HEALTHCARE IT CYBERSECURITY TASK GROUP • Mission • Establish a plan as a part of a multi-stakeholder collaborative effort that builds upon the recommendations put forward in imperative 2 of the Healthcare and Public Health Sector Cybersecurity Task Force Report • Specifically, a voluntary framework and integrated security plan for medical devices and health IT which seeks to address challenges associated with legacy products, secure development lifecycle practices, security and vulnerability communications to stakeholders, incident response coordination, and cybersecurity maturity assessment for continuous improvement • 60+ members • Mix of medical device vendors, consultants, Healthcare Delivery Organizations, Professional Groups, Industry Groups, GPOs, Government Agencies

“TG 1 B” TASK GROUP • Based on the Health Care Industry Cybersecurity Task Force Report recommendations within Imperative 2 “Increase the security and resilience of medical devices and health IT” • Mapped to National Institute for Standards and Technology Cybersecurity Framework • Developing criteria for assessing maturity towards the framework and plan • Definition of responsibilities for achieving milestones • Consensus-based approach to drafting the framework and plans includes: 1. Draft the JSP with a small group of manufacturers, Adva. Med, and FDA 2. Present and solicit feedback from broader manufacturer group 3. Present and solicit feedback through FDA, Adva. Med, MITA, MDMA, CHIME, Med. ISAO to a small group of healthcare providers for additional feedback 4. Through the Healthcare SCC perform industry review and establish a governance model to ensure baseline strategy is routinely updated

FRAMEWORK FOR INCORPORATING CYBERSECURITY • Voluntary framework for medical devices and health IT to be considered during: • Design • Developmen t • Production • Deployment • Service • Support • End of Life Framework should fit into existing design control and quality systems and can align with multiple development methodologies

Examples

IMPLEMENTATION FRAMEWORK • Framework for implementing includes: • Risk Management • Design Control • Vulnerability and Patch Management • Cybersecurity Management Plan • • Security Testing Security Documentation End of Life Complaint Handling Framework includes responsibilities for all involved with the process

Examples

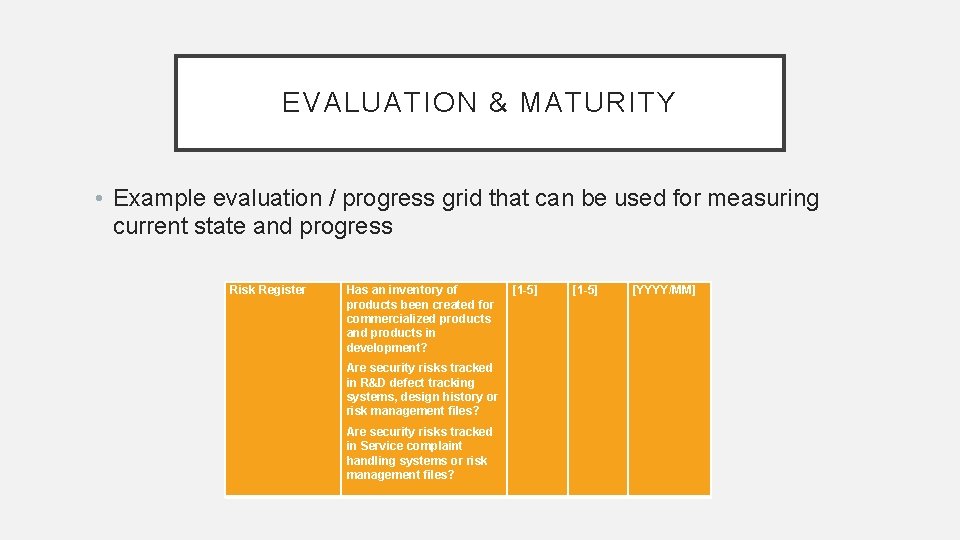
EVALUATION & MATURITY • Example evaluation / progress grid that can be used for measuring current state and progress Risk Register Has an inventory of products been created for commercialized products and products in development? Are security risks tracked in R&D defect tracking systems, design history or risk management files? Are security risks tracked in Service complaint handling systems or risk management files? [1 -5] [YYYY/MM]

REFERENCES INCLUDED • Acronyms • Terminologies • Roles and Responsibilities • Resources • HCIC Task Force Report • Best Practices from other Sectors • Security Design Inputs • Drafting the MDM and HIT CSF • Organizational Structures • Training Organizations for Adoption • Sample Sa. MD Procedure •

QUESTIONS?