Measures to Improve Security in a Microkernel Operating





















- Slides: 32

Measures to Improve Security in a Microkernel Operating System Wasim Al-Hamdani Durga Vemuri Kentucky State University Wasim. al-hamdani@kysu. edu durga. vemuri@kysu. edu Presented by: Fatema Nafa.

WASIM AL-HAMDANI �A Professor of Computer and Technical Sciences at Kentucky State University (KSU). �playing a leading role at KSU in developing the Information Security program. �He has published six textbooks in Arabic dealing with computer science and Cryptography. �His interest is designing cryptographic Operating System Security class

outline § The main goal for this paper. § Introduction. § Achieving security § Kernel’s security. § Kernel security architecture. § Secure microkernel. § The Vfiasco project. § Conclusion. § References. Operating System Security class

What is the main goal? �Explain the concepts and mechanisms used to improve security in Microkernel Operating system. �Describe two real-world microkernel operating systems, that try to achieve security as a goal. Operating System Security class

Introduction. �“Secure Operating System” is a fuzzy term. Secure Operating System �all general purpose computers are controlled by general purpose operating systems like Windows, Mac. OS and Unix variants. Does that mean they are insecure? �If a computer is exposed to an environment that carries risks and the software does not have sufficient countermeasures, then the situation is not secure. Operating System Security class

�We have different kinds of networks so effective steps need to be taken to increase security. �If many systems are running the same operating systems they share the same deficiencies, they are “bug compatible”. �There are more than enough examples of quite primitive pieces of malware causing billions of dollars of damage all over the world in no time. (Firewalls, virus scanners, ) Operating System Security class

What is the problem with software today? �A major limitation of these tools is the signature. It used to recognize viruses and attacks that are already known only. �We May simply be caught by any new attack that enters undetected. �This necessitates costly subscriptions to update the signatures provided by the manufacturers on a regular basis. Operating System Security class

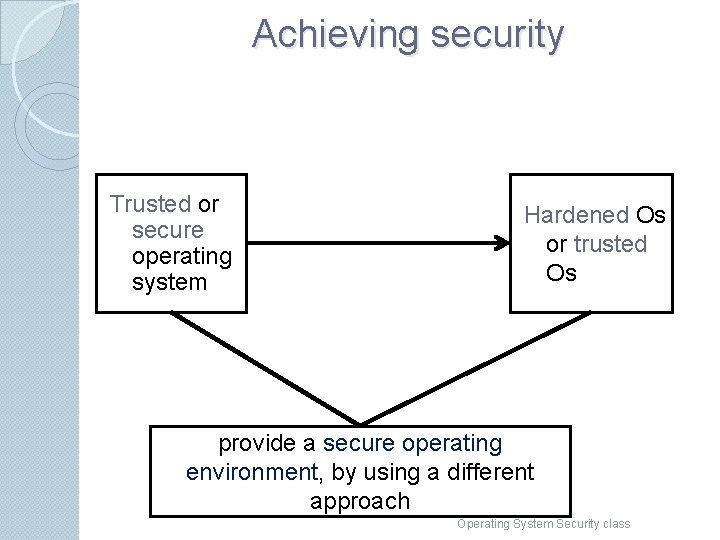
Achieving security Trusted or secure operating system Hardened Os or trusted Os provide a secure operating environment, by using a different approach Operating System Security class

�The security level being implemented is a tradeoff between a number of factors. necessary level of security, regulatory rules, convenience, usability, acceptance, productivity, administrational complexity, scalability. �Security was, and still is a technical problem to be solved. Operating System Security class

Microkernel paradigm. �a microkernel is the near-minimum amount of software that can provide the mechanisms needed to implement an operating system These mechanisms include low-level address space management, thread management, and inter-process communication (IPC). Operating System Security class

� In microkernel designs, most operating system components, such as process management and device management, execute outside the kernel with a lower level of system access. Operating System Security class

How to improve security in kernel‘s operating system. �What is a security kernel? �A Security Kernel is a small module in the Operating System where all security features are located. �works as a part of an operating system to prevent unauthorized access to the system. �contains criteria that must be met before specified programs can be accessed Operating System Security class

Operating System Security class

Improve security by q q Interaction with other objects. Reference Monitors q. Non- Interference. q. Access control. Operating System Security class

Interaction with other objects. �We have some of the questions that motivated the improvement of many software mechanisms to control interaction between users, machines and data. �a lot of measures attempt to map real world security concepts to computer systems, These work well in a structured organization. But the smallest error can open huge security holes. Operating System Security class

Some common mechanisms are: �Multi level security. �Strong authentication. � Restricted views on file systems, databases. �Access control lists (ACL). � Role based access control (RBAC). � Capabilities. � Certificates. Most people in this area concentrate on making applications user friendly but not on making them secure. Operating System Security class

Reference Monitors �modern security experts equate “Reference Monitor” with the core security enforcement mechanisms within the kernel. �Good development practices and security are more synonymous than most people believe. �The role of this fundamental security- enforcement mechanism is : �Validating all access attempts made to resources (data, programs, etc. ) by any Operating System Security class

Non- Interference. �This problem for files has been enabled by file system permissions, but the operating systems needs to track which programs should adhere to these and more general behaviors. Some advanced mechanisms are: � Separation of kernel and process address spaces, Sandboxes. � Safer kernel extensions like loadable drivers and modules. � Consistency checks, checkpoints/snapshots, persistence Operating System Security class

Access control �One goal of the kernel will be to restrict access to shared resources such as memory, devices and CPUs. �There a lot of different access control models that kernels can be implemented and used as a top-level specification. �access to a resource is an authorized capability to that resource. Operating System Security class

Secure microkernel. �L 4 is a family of second generation microkernel‘s. �Formal Verification of an OS Kernel. �se. L 4 microkernel provides a minimal and efficient lowest software level, and is the only part of the software for this paper that executes in the privileged mode of the hardware. It is a third-generation microkernel Operating System Security class

Operating System Security class

Why Microkernel? �The kernel manages the hardware at the lowest level, and it is not subject to protection or fault isolation mechanisms provided by the hardware. �Small kernel providing core functionality �only code running in privileged mode �Most OS services provided by user-level servers �the kernel is always part of the trusted computing base (TCB). Operating System Security class

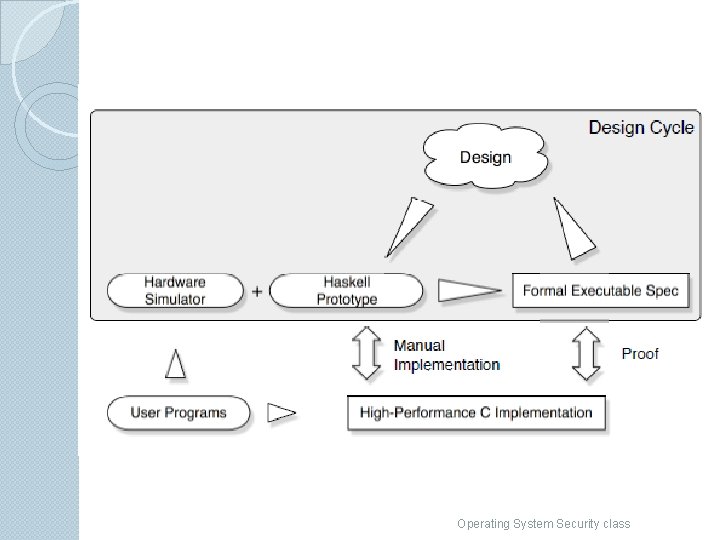
Kernel Design process �designs based on simple models with a high degree of abstraction from hardware. �They use a functional programming language (Haskell) to provide a programming language for the OS. �The next slide shows their approach in more detail Operating System Security class

The Vfiasco project �Fiasco is a real time kernel. �It is written in about 40. 000 lines of C++. �The goal is a bottom-up verification of the kernel. Operating System Security class

Vfiasco case study �The kernel class implemented in about 400 lines of code. �The methods for implementing the insertion and deletion of virtual address space mappings and for making a page directory the CPU's current directory were then selected for proving. �The translation of the code took 4 weeks and resulted in about 400 lines. Operating System Security class

�Several bugs in the Fiasco code were discovered and fixed. �All in all it took 3 months. It was shown that it is possible to prove correctness of regular real life C++ code that was not written with verification in mind. Operating System Security class

Enabling Large Scale Verification in Vfiasco �It is easy to see that verification is possible, but it is still too expensive to do it in the way of the case study. �There is a big number of software characteristics that may be subjected to proofing. Operating System Security class

The Nizaa Architecture �The Nizza security aims at reducing the size of a system's Trusted Computing Base (TCB) by an order of magnitude in comparison to systems �It builds on the Vfiasco microkernel that has been formally verified to a high degree. �It is accompanied by a small set of essential services that are not part of a microkernel. Operating System Security class

Conclusion. �Older microkernel’s did not achieve sufficient flexibility and performance. �a new generation of microkernel architectures shows good results in performance and flexibility. �The microkernel operating systems have strategic advantages like small APIs, small code size. �They are separated into independent units suitable for step by-step verification. Operating System Security class

Conclusion �The chance to become a success in a world with rising security requirements. �The developers need to offer a very comfortable migration path if they want to replace the current operating systems they all are forced to depend on so much Operating System Security class

References P. Derrin, K. Elphinstone, G. Klein, D. Cock, and M. T Chakravarty. Running the manual: An a pproach to high-assurance microkernel development. 2. B. Kauer and M. V¨olp. L 4. sec: Preliminary Microkernel Reference manual Dresden University of Technology http: //os. inf. tu- dresden. de/L 4. Sec/. 3. TCG 2005: TCG: What is the Trusted Computing Group https: //www. trustedcomputinggroup. org/. 4. Wikipedia Various, Security, Wikipedia http: //en. wikipedia. org/wiki/Secure. 5. Anderson: Ross Andersen: Trusted Computing FAQ. University of Cambridge http: //www. cl. cam. ac. uk/users/rja 14/tcpa-faq. html 6. Shapiro: Jonathan Shapiro, Understanding the Windows EAL 4 Evaluation, Johns Hopkins University Information Security Institute , http: //eros. cs. jhu. edu/~shap/NTEAL 4. html 1. Operating System Security class

Operating System Security class