MCTS Guide to Microsoft Windows Server 2008 Network




































- Slides: 50

MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration Chapter 10 Securing Windows Server 2008

Objectives • Manage security in Windows Server 2008 with various Windows utilities • Discuss threats to Internet Protocol Security • Create Internet Protocol Security policies • Discuss Network Access Protection • Install Network Access Protection MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 2

Managing Security in Server 2008 • Tools for managing network security – – – Security Configuration Wizard Windows Firewall Encrypting File System Bit. Locker Microsoft Baseline Security Analyzer MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 3

Security Configuration Wizard • Security Configuration Wizard (SCW) – Provides a step-by-step wizard for hardening your network servers • Security policies can be created for: – – Role-based service configuration Network security Registry settings Audit policy MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 4

Security Configuration Wizard (continued) • Activity 10 -1: Creating a Role-Based Security Policy • Time Required: 15 minutes • Objective: Create a security policy using the SCW MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 5

Windows Firewall • Allows users to turn the firewall off or on • By default, Windows Firewall is turned on and allows exceptions for programs and ports • Allows you to create exceptions for inbound traffic • Exception – Instruction to open a port briefly, allow a program or service to pass information, and then close the port MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 6

MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 7

MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 8

Windows Firewall (continued) • Activity 10 -2: Working with Windows Firewall • Time Required: 10 minutes • Objective: Become familiar with the Windows Firewall interface MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 9

Windows Firewall (continued) • Windows Firewall with Advanced Security – Provides a more robust interface for managing the firewall policies in detail – Used to manage Windows Firewall based on port, services, applications, and protocols MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 10

MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 11

Windows Firewall (continued) • Activity 10 -3: Working with WFAS • Time Required: 10 minutes • Objective: Modify an inbound rule MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 12

Windows Firewall (continued) • Windows Firewall with Advanced Security Console – Can be used to manage the following areas • • Inbound rules Outbound rules Connection security rules Monitoring MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 13

Windows Firewall (continued) • Activity 10 -4: Creating a New Firewall Rule • Time Required: 10 minutes • Objective: Create a firewall rule MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 14

Windows Firewall (continued) • Windows Server 2008 uses the following network profiles – Public – Private – Domain • Deploying Windows Firewall Settings via Group Policy – WFAS allows you to import or export firewall policies MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 15

Windows Firewall (continued) • Activity 10 -5: Configuring Firewall Rules with Network Profiles • Time Required: 10 minutes • Objective: Configure firewall rules with network profiles MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 16

Windows Firewall (continued) • Activity 10 -6: Working with Firewall Policies in the Group Policy Management Editor • Time Required: 15 minutes • Objective: Using Group Policy objects and firewall policies to deploy firewall settings MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 17

Encrypting File Services • Symmetric encryption – Uses a single key and is faster and more efficient than public key encryption • Public key (asymmetric) encryption – Each user has a public key available to everyone and a private key known only to the user • EFS in Windows Server 2008 – When a user encrypts a file, a symmetric file encryption key (FEK) is generated that EFS uses to encrypt the file MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 18

Encrypting File Services (continued) • Activity 10 -7: Working with cipher. exe • Time Required: 10 minutes • Objective: Using cipher. exe with EFS MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 19

Encrypting File Services (continued) • Activity 10 -8: Using Windows Explorer to Encrypt Files with EFS • Time Required: 10 minutes • Objective: Configure file and folder encryption through the graphical user interface (GUI) MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 20

Bit. Locker • Provides hard drive–based encryption of servers and Windows Vista computers • Encrypts entire Windows system volume of a computer running Windows Server 2008 • Designed to enhance protection against data theft or exposure on computers that are lost or stolen MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 21

Bit. Locker (continued) • Four authentication modes used by Bit. Locker – Bit. Locker with a TPM – Bit. Locker with Universal Serial Bus (USB) flash drive in place of TPM – Bit. Locker with a TPM and a personal identification number (PIN) – Bit. Locker with a TPM and a USB flash drive MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 22

Bit. Locker (continued) • Installing Bit. Locker – Hard drive that supports Bit. Locker needs to be configured before installing Bit. Locker – Bit. Locker requires at least 1. 5 GB of unallocated or available drive space – System volume is responsible for maintaining the unencrypted boot information – Boot volume will contain the OS files and be encrypted by Bit. Locker MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 23

Bit. Locker (continued) • Activity 10 -9: Installing the Bit. Locker and the Bit. Locker Drive • Preparation Tool in Windows Server 2008 • Time Required: 15 minutes • Objective: Install the Bit. Locker and Bit. Locker Drive Preparation tool MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 24

Bit. Locker (continued) • Activity 10 -10: Configuring Bit. Locker to Use a USB Flash Drive • Time Required: 15 minutes • Objective: Configure Bit. Locker to use a USB flash drive MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 25

Microsoft Baseline Security Analyzer • Excellent tool for performing an initial analysis of your current security setup • When MBSA scans a computer, it creates a report that is organized into the following areas – – – Security Assessment Security Update Scan Results Windows Scan Results Internet Information Services (IIS) Scan Results SQL Server Scan Results Desktop Application Scan Results MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 26

Microsoft Baseline Security Analyzer (continued) • Scanning a computer with MBSA – You can perform MBSA scans using: • The GUI-based tool • The mbsacli. exe command- line tool – One requirement of MBSA is Internet connectivity MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 27

Microsoft Baseline Security Analyzer (continued) • Activity 10 -11: Working with MBSA • Time Required: 15 minutes • Objective: Analyze Windows Server 2008 with MBSA MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 28

Internet Protocol Security • An open-standards framework for securing network communications • IPSec meets three basic goals – Authentication – Integrity – Confidentiality MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 29

IPSec Threats • Depending on the configuration of IPSec, it provides protection from the following threats – – – Data tampering Denial of service Identity spoofing Man-in-the-middle attacks Repudiation Network traffic sniffing MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 30

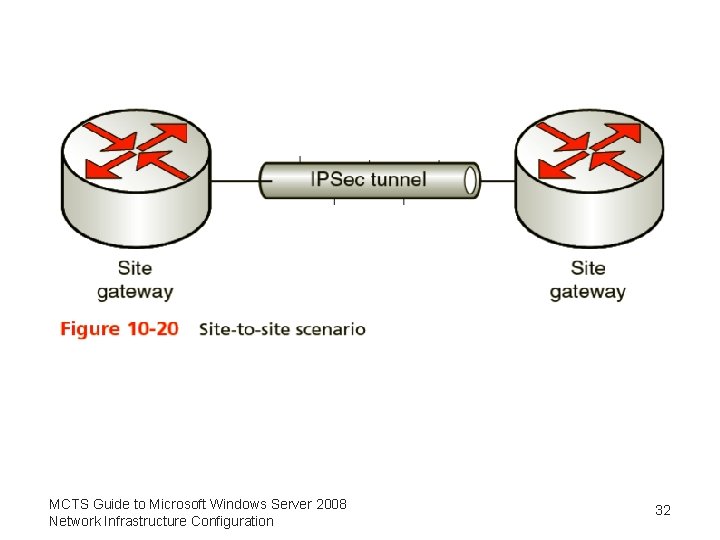
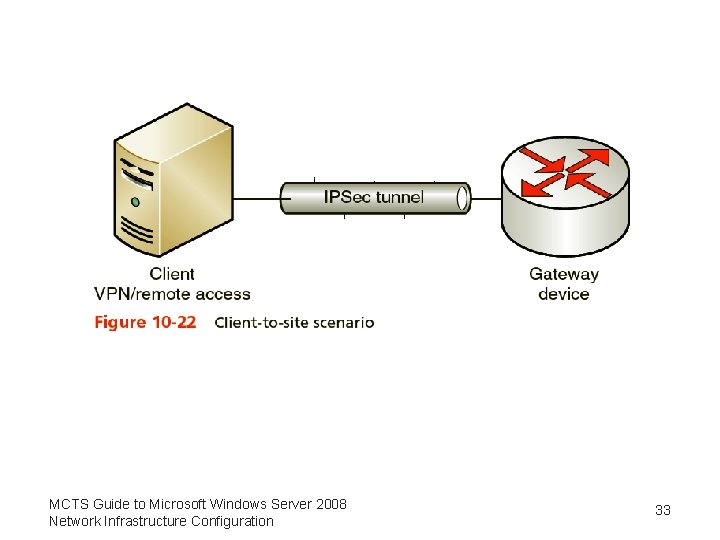
How IPSec Works • IPSec modes of operation – Transport mode – Tunnel mode • Scenarios available when deploying IPSec – Site to site – Client to client – Client to site MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 31

MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 32

MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 33

How IPSec Works (continued) • IPSec security association modes – IPSec uses the Internet Key Exchange (IKE) to negotiate security protocols – IKE generates the encryption and authentication keys used by IPSec for the transaction – IPSec performs transactions in two phases • Main mode/Phase 1 • Quick mode/Phase 2 MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 34

How IPSec Works (continued) • IPSec security methods – IPSec uses two security services • Encapsulating Security Payload • Authentication Header • IPSec policies – Can be managed with the following tools • WFAS, IP Security Policy snap-in • Netsh, GPME MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 35

MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 36

MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 37

How IPSec Works (continued) • Activity 10 -12: Creating an IPSec Policy for Domain Isolation • Time Required: 15 minutes • Objective: Use IPSec to isolate domain computers from nondomain computers MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 38

How IPSec Works (continued) • Activity 10 -13: Creating an IPSec Policy for Serverto-Server Communications • Time Required: 15 minutes • Objective: Use IPSec to secure communication between two hosts MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 39

Network Authentication in Windows Server 2008 • Server 2008 supports the following authentication protocols to some degree – LAN Manager authentication – NTLM version 1 authentication – NTLM version 2 authentication • All forms of NTLM use the challenge-response protocol MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 40

Introduction to Network Access Protection • NAP can be broken into three parts – Health policy validation – Health policy compliance – Access limitation MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 41

NAP Terminology • • Enforcement Client Enforcement Server Host Credential Authorization Protocol Health Registration Authority Network Policy Server Remediation Server System Health Agent System Health Validator MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 42

NAP Enforcement Methods • The five types of NAP enforcement methods used by NAP – 802. 1 x-authenticated connections – Dynamic Host Configuration Protocol (DHCP) address configurations – IPSec communications – Terminal Services Gateway (TS Gateway) connections – Virtual Private Network (VPN) connections MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 43

Implementing NAP • NAP – Designed by Microsoft to allow you to customize it to meet the unique needs of your networks – Implementing and configuring NAP differs from network to network based on requirements and policies MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 44

MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 45

Installing NAP • NAP is part of the NPS role • To install NAP components – Add the NPS role either through the Role Services Wizard or from the command line using servermanagercmd. exe MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 46

Installing NAP (continued) • Activity 10 -14: Installing and Configuring NAP • Time Required: 10 minutes • Objective: Install NAP and configure a NAP policy MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 47

Summary • The SCW – Guides you through the steps of hardening your network servers • Windows Firewall – Provides inbound and outbound traffic enforcement through the Windows Firewall and WFAS consoles • EFS – Microsoft’s built-in service for providing folder- and file-level encryption • Bit. Locker – Provides hard drive–based encryption of servers MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 48

Summary (continued) • At startup – Bit. Locker performs a system integrity authentication prior to booting into the OS • MBSA – Scans single or multiple computers on a network and lets you view existing security scan reports • IPSec – An open-standards framework for securing network communications – Works at the network layer of the OSI model MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 49

Summary (continued) • On Windows networks – Windows Server 2008 uses Kerberos as its default authentication method in Active Directory domains • To use NAP policies – A client must be a part of the NAP infrastructure on a network • The HRA – Distributes health certificates to NAP clients that comply with network health Requirements MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration 50