Mc Afee Data Protection Total Protection Suite for








- Slides: 28

Mc. Afee Data Protection Total Protection Suite for Data (To. PS Data)

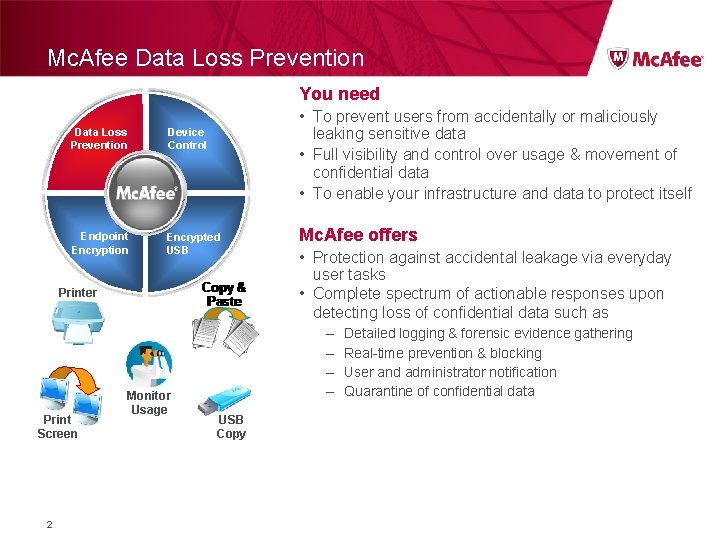
Mc. Afee Data Loss Prevention You need • To prevent users from accidentally or maliciously leaking sensitive data • Full visibility and control over usage & movement of confidential data • To enable your infrastructure and data to protect itself Data Loss Prevention Device Control Endpoint Encryption Encrypted USB Printer Print Screen 2 Monitor Usage Mc. Afee offers • Protection against accidental leakage via everyday user tasks • Complete spectrum of actionable responses upon detecting loss of confidential data such as – – USB Copy Detailed logging & forensic evidence gathering Real-time prevention & blocking User and administrator notification Quarantine of confidential data

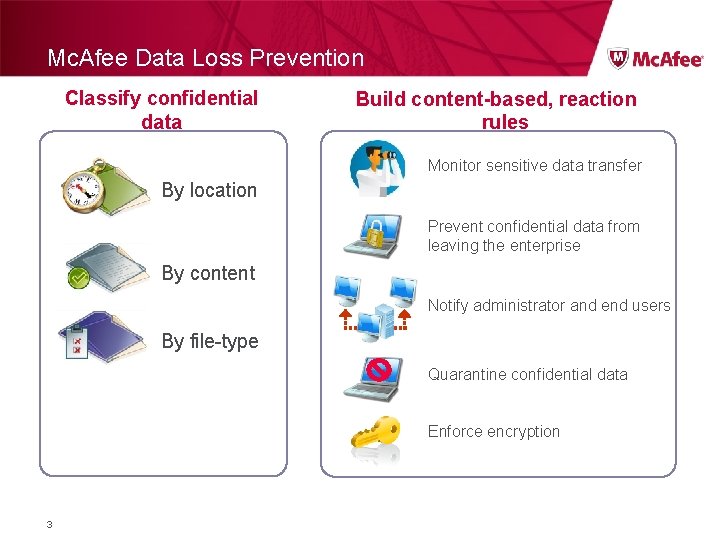
Mc. Afee Data Loss Prevention Classify confidential data Build content-based, reaction rules Monitor sensitive data transfer By location Prevent confidential data from leaving the enterprise By content Notify administrator and end users By file-type Quarantine confidential data Enforce encryption 3

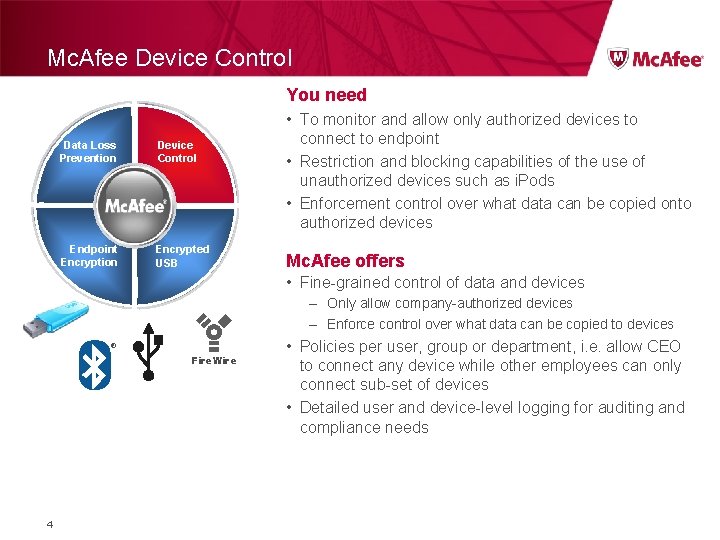
Mc. Afee Device Control You need Data Loss Prevention Device Control Endpoint Encryption Encrypted USB • To monitor and allow only authorized devices to connect to endpoint • Restriction and blocking capabilities of the use of unauthorized devices such as i. Pods • Enforcement control over what data can be copied onto authorized devices Mc. Afee offers • Fine-grained control of data and devices – Only allow company-authorized devices – Enforce control over what data can be copied to devices ® Fire. Wire 4 • Policies per user, group or department, i. e. allow CEO to connect any device while other employees can only connect sub-set of devices • Detailed user and device-level logging for auditing and compliance needs

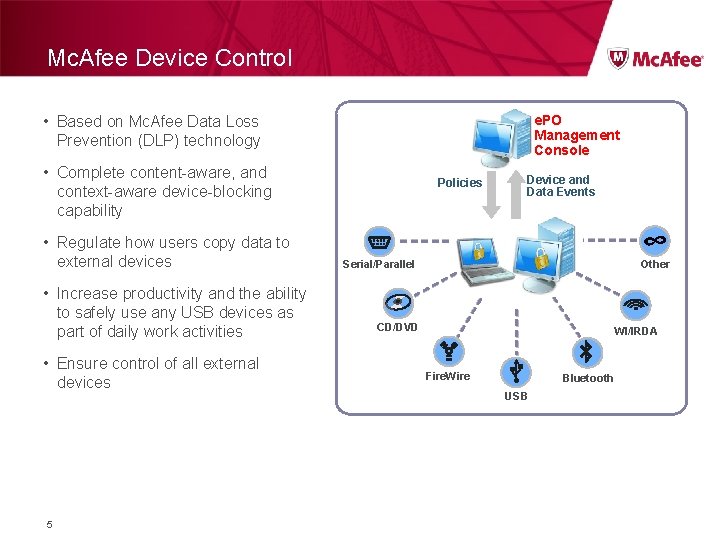
Mc. Afee Device Control e. PO Management Console • Based on Mc. Afee Data Loss Prevention (DLP) technology • Complete content-aware, and context-aware device-blocking capability • Regulate how users copy data to external devices • Increase productivity and the ability to safely use any USB devices as part of daily work activities • Ensure control of all external devices 5 Policies Device and Data Events Serial/Parallel Other CD/DVD WI/IRDA Fire. Wire Bluetooth USB

Mc. Afee Endpoint Encryption EEPCv. 6. X You need Data Loss Prevention Device Control • Encryption for laptops, desktops, and mobile devices with the flexibility to choose full-disk or file/folder encryption • Confidence in integrity of sensitive data when a device is lost or stolen Endpoint Encryption • Safe Harbor protection (i. e. Loss of encrypted data = non-event and does not require public disclosure) Encrypted USB Mc. Afee offers • Broad support for laptops, desktops, and mobile devices • Full audit-trails for compliance & auditing needs • Support for multiple strong authentication methods • Certifications: FIPS 140 -2, Common Criteria Level 4 (highest level for software products), BITS, CSIA, etc. 6

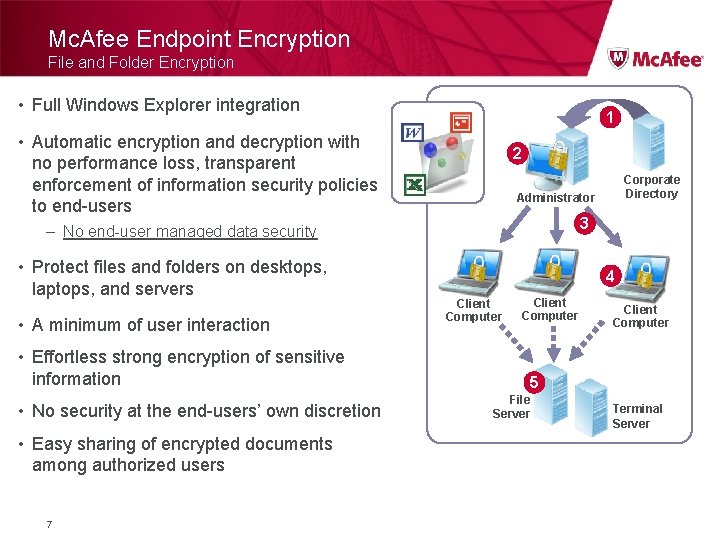
Mc. Afee Endpoint Encryption File and Folder Encryption • Full Windows Explorer integration 1 • Automatic encryption and decryption with no performance loss, transparent enforcement of information security policies to end-users 2 Administrator 3 – No end-user managed data security • Protect files and folders on desktops, laptops, and servers • A minimum of user interaction • Effortless strong encryption of sensitive information • No security at the end-users’ own discretion • Easy sharing of encrypted documents among authorized users 7 Corporate Directory 4 Client Computer 5 File Server Terminal Server

File & Folder Encryption Features • Policy controlled, user transparent encryption of: – – Local documents and folders File server documents and folders Removable media Encrypted e-mail attachments (user initiated) • Internal (Recipients with client) • External (Recipients without client) • True on-the-fly encryption & decryption when accessing and saving protected documents • Flexible policy assignments and management – Encryption keys and encryption settings managed from Mc. Afee Encryption Manager – Amount of end-user options subject to policy control – Policies cannot be circumvented by end-users 8

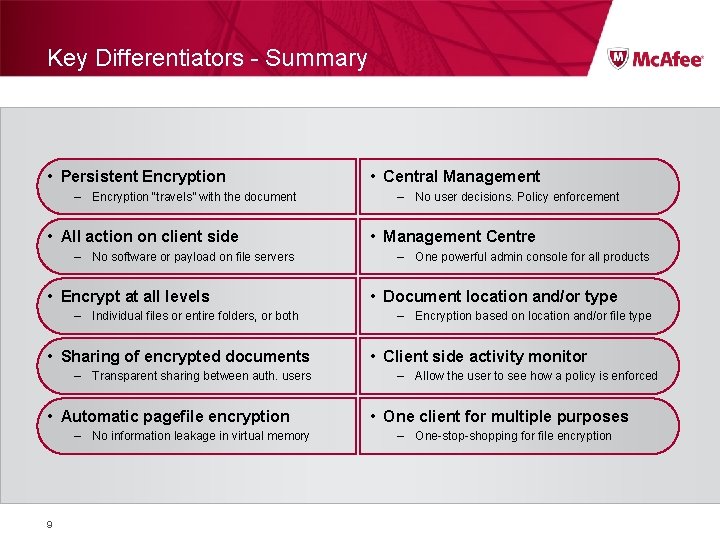
Key Differentiators - Summary • Persistent Encryption – Encryption “travels” with the document • All action on client side – No software or payload on file servers • Encrypt at all levels – Individual files or entire folders, or both • Sharing of encrypted documents – Transparent sharing between auth. users • Automatic pagefile encryption – No information leakage in virtual memory 9 • Central Management – No user decisions. Policy enforcement • Management Centre – One powerful admin console for all products • Document location and/or type – Encryption based on location and/or file type • Client side activity monitor – Allow the user to see how a policy is enforced • One client for multiple purposes – One-stop-shopping for file encryption

Mc. Afee Endpoint Encryption Mobile Device Encryption Removable Media • External/Removable Media Encryption Ensures that data stored on removable cards can only be accessed from the device from which it came • Removable Media Options – Allow encrypted media only – Allow full access to encrypted media and read-only access to un-encrypted media – Block all access to all media – Deny access to un-encrypted cards 10

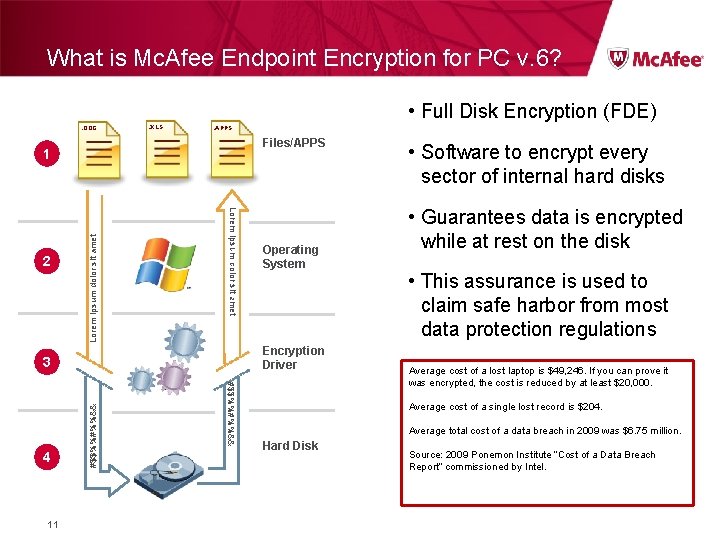
What is Mc. Afee Endpoint Encryption for PC v. 6? • Full Disk Encryption (FDE). DOC . XLS . APPS Files/APPS Lorem ipsum dolor sit amet 2 Lorem ipsum dolor sit amet 1 Encryption Driver #$$%%#%%&& 11 #$$%%#%%&& 3 4 Operating System • Software to encrypt every sector of internal hard disks • Guarantees data is encrypted while at rest on the disk • This assurance is used to claim safe harbor from most data protection regulations Average cost of a lost laptop is $49, 246. If you can prove it was encrypted, the cost is reduced by at least $20, 000. Average cost of a single lost record is $204. Average total cost of a data breach in 2009 was $6. 75 million. Hard Disk Source: 2009 Ponemon Institute “Cost of a Data Breach Report” commissioned by Intel.

Proactive Reporting in e. PO – The Difference Prior to e. PO, Safe. Boot reporting was limited to Safe. Boot installed machines – no information about the machines which are NOT secured – Reactive Reporting: check protection status of a laptop post theft; if machine not listed in the report it means not secured NEW integrated e. PO reporting of Endpoint Encryption reports on the entire e. PO managed machine network – Proactive Reporting: embedded Endpoint Encryption reporting through e. PO presents machines which are not protected with Endpoint Encryption. e. PO can then deploy the client to these machines directly. 12

Proactive Reporting in e. PO – Discovery • Compliance reporting with other vendors is limited to installed machine or an application running on the machine itself • With the proactive e. PO reporting approach Mc. Afee can go one step further and find non-secured machines, although no agent is running on the machine • Use the built-in “e. PO Rogue System detection” option to determine the machines in your organization not running the Mc. Afee Agent (MA) 13

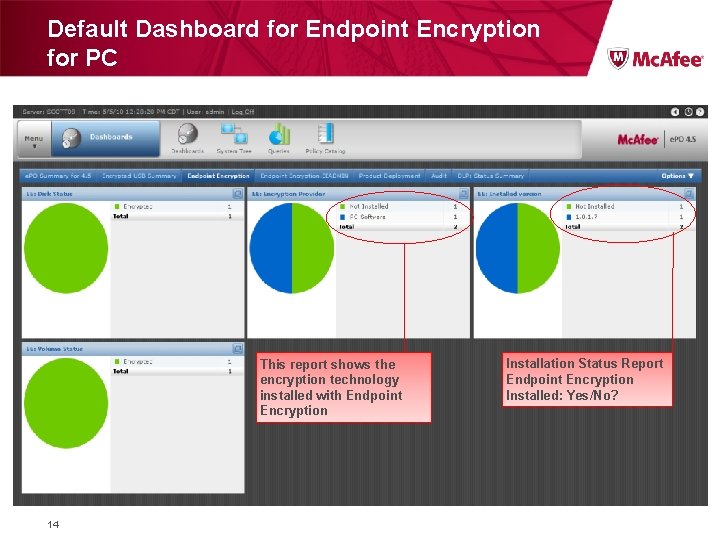
Default Dashboard for Endpoint Encryption for PC This report shows the encryption technology installed with Endpoint Encryption 14 Installation Status Report Endpoint Encryption Installed: Yes/No?

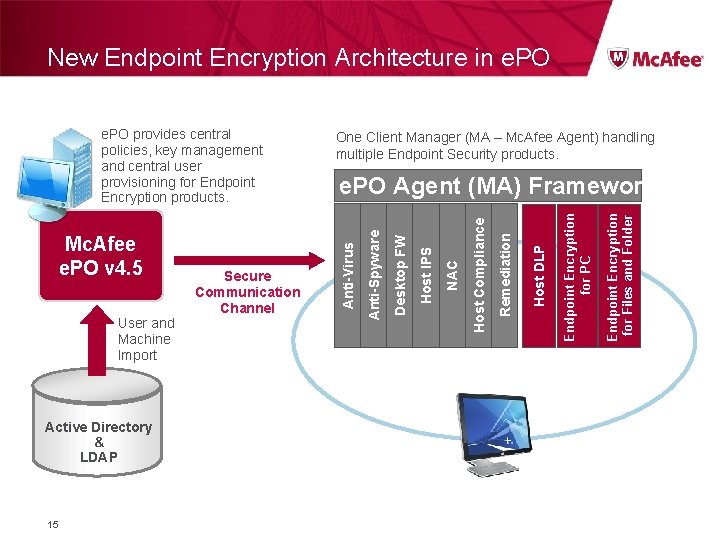
New Endpoint Encryption Architecture in e. PO Active Directory & LDAP 15 Endpoint Encryption for Files and Folder Endpoint Encryption for PC Host DLP Remediation Host Compliance NAC Host IPS Desktop FW User and Machine Import Secure Communication Channel e. PO Agent (MA) Framework Anti-Spyware Mc. Afee e. PO v 4. 5 One Client Manager (MA – Mc. Afee Agent) handling multiple Endpoint Security products. Anti-Virus e. PO provides central policies, key management and central user provisioning for Endpoint Encryption products.

e. PO Integration Goals • Objective reduce overall operational costs associated with an encryption product and to make an Administrator’s life easier – Deployment – Reporting – Same tasks and policies regardless of operating system or software/hardware encryption technology • Improved support for 16 – Clustering – Scalability – Virtualization

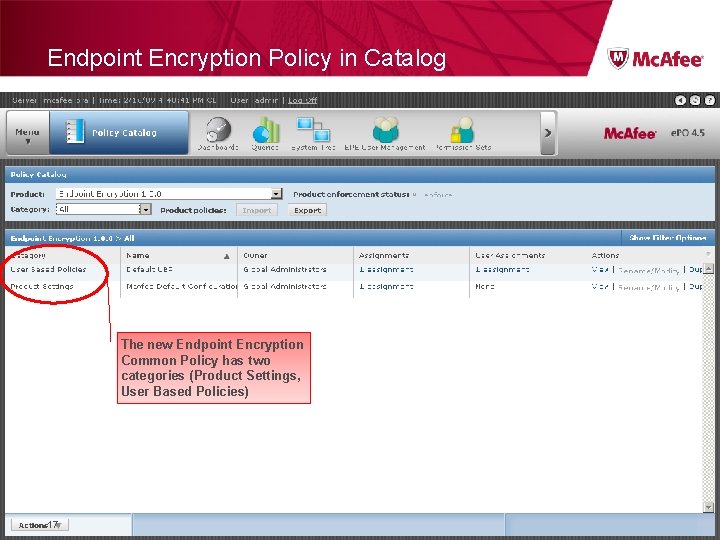
Endpoint Encryption Policy in Catalog The new Endpoint Encryption Common Policy has two categories (Product Settings, User Based Policies) 17

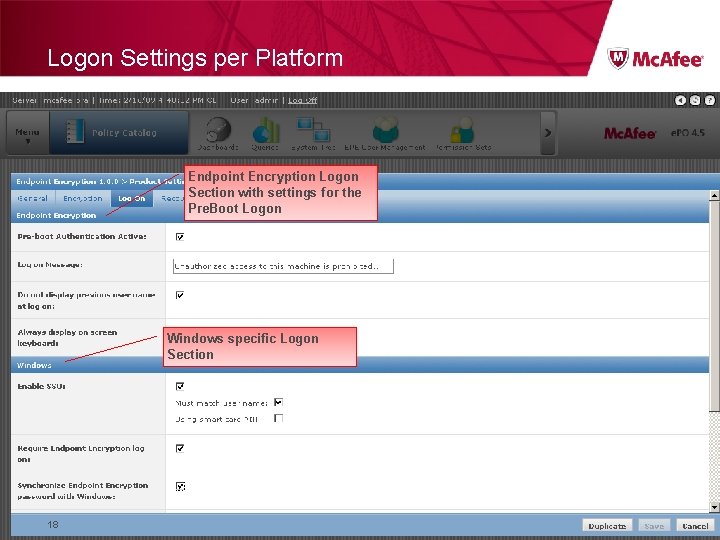
Logon Settings per Platform Endpoint Encryption Logon Section with settings for the Pre. Boot Logon Windows specific Logon Section 18

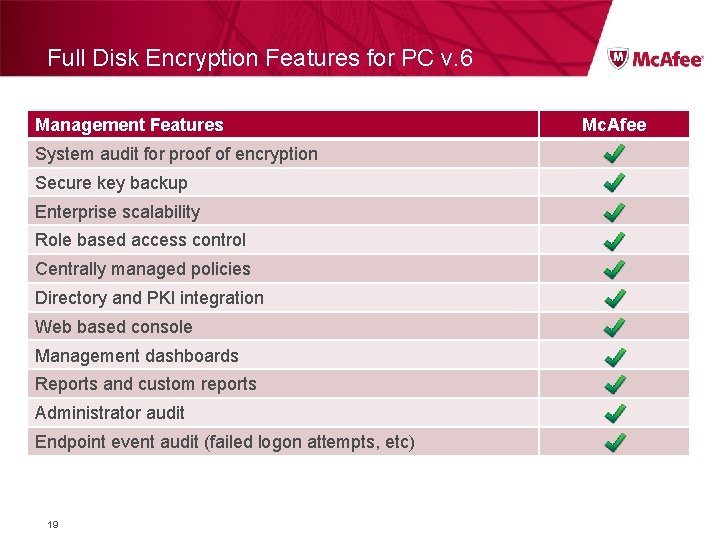
Full Disk Encryption Features for PC v. 6 Management Features System audit for proof of encryption Secure key backup Enterprise scalability Role based access control Centrally managed policies Directory and PKI integration Web based console Management dashboards Reports and custom reports Administrator audit Endpoint event audit (failed logon attempts, etc) 19 Mc. Afee

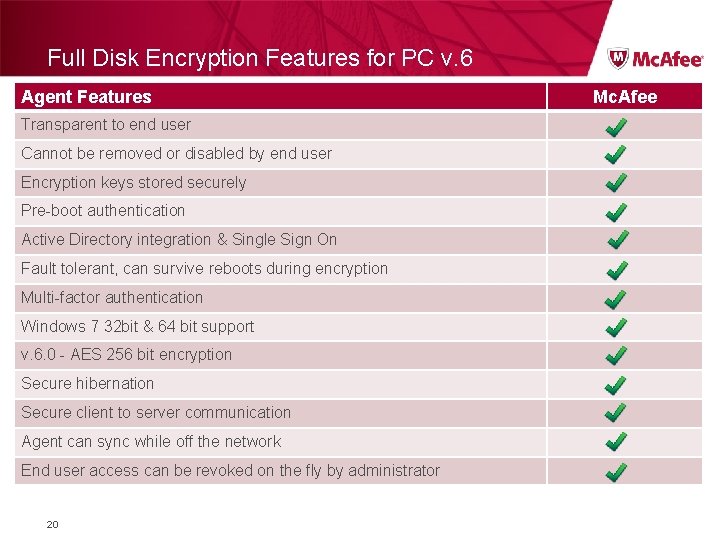
Full Disk Encryption Features for PC v. 6 Agent Features Transparent to end user Cannot be removed or disabled by end user Encryption keys stored securely Pre-boot authentication Active Directory integration & Single Sign On Fault tolerant, can survive reboots during encryption Multi-factor authentication Windows 7 32 bit & 64 bit support v. 6. 0 - AES 256 bit encryption Secure hibernation Secure client to server communication Agent can sync while off the network End user access can be revoked on the fly by administrator 20 Mc. Afee

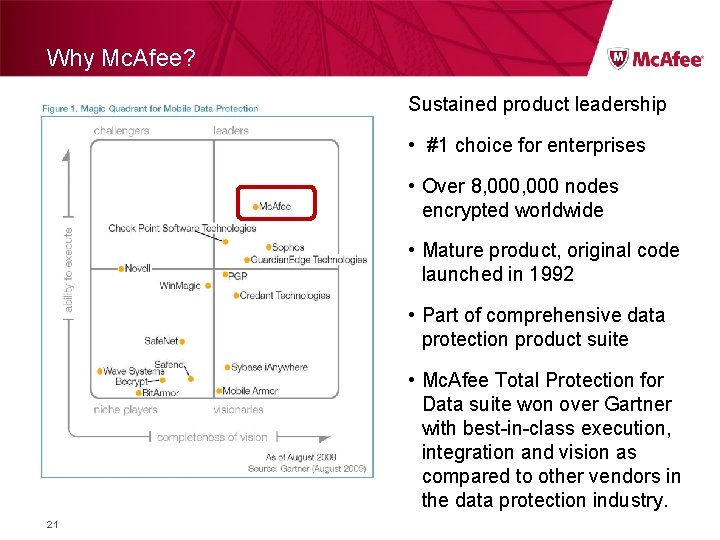
Why Mc. Afee? Sustained product leadership • #1 choice for enterprises • Over 8, 000 nodes encrypted worldwide • Mature product, original code launched in 1992 • Part of comprehensive data protection product suite • Mc. Afee Total Protection for Data suite won over Gartner with best-in-class execution, integration and vision as compared to other vendors in the data protection industry. 21

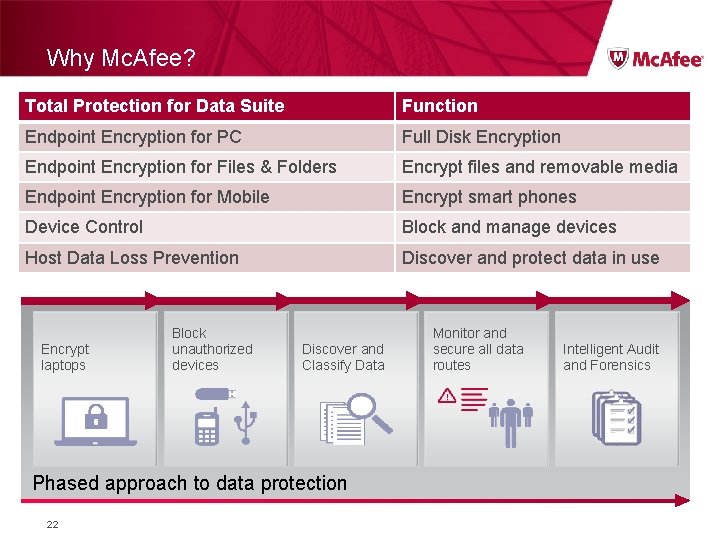
Why Mc. Afee? Total Protection for Data Suite Function Endpoint Encryption for PC Full Disk Encryption Endpoint Encryption for Files & Folders Encrypt files and removable media Endpoint Encryption for Mobile Encrypt smart phones Device Control Block and manage devices Host Data Loss Prevention Discover and protect data in use Encrypt laptops Block unauthorized devices Discover and Classify Data Phased approach to data protection 22 Monitor and secure all data routes Intelligent Audit and Forensics

Users in version 6. 0 • Users are referenced not created – Referenced from Active Directory or LDAP – No local users – Quicker provisioning times possible – Can be used with Auto. Discovery of users functionality • e. PO support – 4. 5: Active Directory only – 4. 5 Patch 2: Will include LDAP support 23

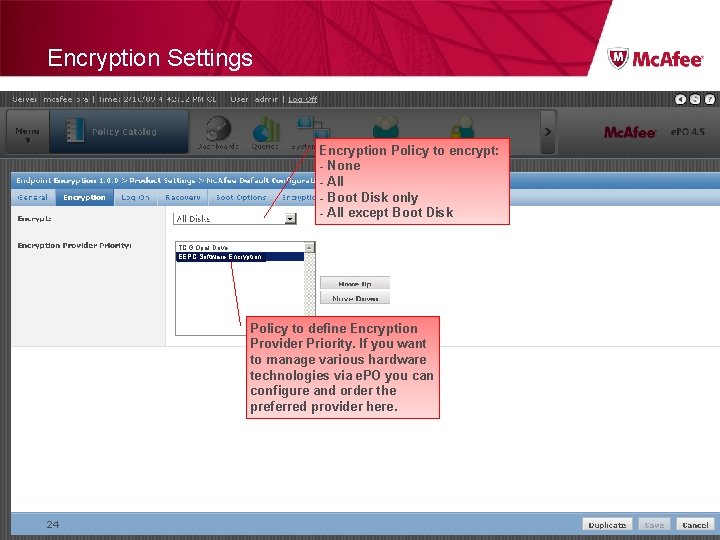
Encryption Settings Encryption Policy to encrypt: - None - All - Boot Disk only - All except Boot Disk TCG Opal Drive EEPC Software Encryption Policy to define Encryption Provider Priority. If you want to manage various hardware technologies via e. PO you can configure and order the preferred provider here. 24

Trusted Computing Group Opal Self Encrypting Drives • Mc. Afee are an active contributor and voting member of the TCG Storage Working Group and provide input to the Opal and Marble specifications • EEPC Version 6. x products will support Self-Encrypting Drives that adhere to the Opal (and Marble) specifications from TCG • Mc. Afee is currently working in conjunction with various manufacturers on incorporating their Opal Drives into EEPC V 6. x 25

Client Supported Platforms and Languages • Management (e. PO) 32 -Bit Only 32 and 64 -Bit – Japanese, French, Spanish, Chinese (Traditional and Simplified), Russian, German, Korean. – Fully localized and supported • Client 32 -Bit Only 32 and 64 -Bit 26 – Same languages and support as Management section – Additional client languages fully localized and available by NOT supported at GA date – Portuguese, Brazilian Portuguese, Italian, Dutch, Greek, Swedish, Norwegian, Danish, Finnish, Polish, Arabic, Estonian and Thai – Supported as of version 6. 0. 1

Mc. Afee Encrypted USB • Deploy easily on an enterprise-wide scale • Easily deploy and track devices through a single console • Streamline workflow to save time and money • Leverage Active Directory to match users and devices • Encrypt data on-the-fly • Enable secure data portability 27

28