May 2011 doc IEEE 802 11 110792 r










- Slides: 14

May 2011 doc. : IEEE 802. 11 -11/0792 r 1 IEEE 802. 11 i is Secure Date: 2011 -05 -11 Authors: Submission Slide 1 IEEE 802. 11 WG

May 2011 doc. : IEEE 802. 11 -11/0792 r 1 Synopsis • Unsubstantiated allegations regarding security vulnerabilities in IEEE 802. 11 were made during the WAPI NP process and were used to justify the need for this project. • IEEE 802 attempted, multiple times, to rebut these allegations. • ISO/IEC/SC 6/WG 1 did not properly process IEEE 802’s comments. • Where do we go from here? Submission Slide 2 IEEE 802. 11 WG

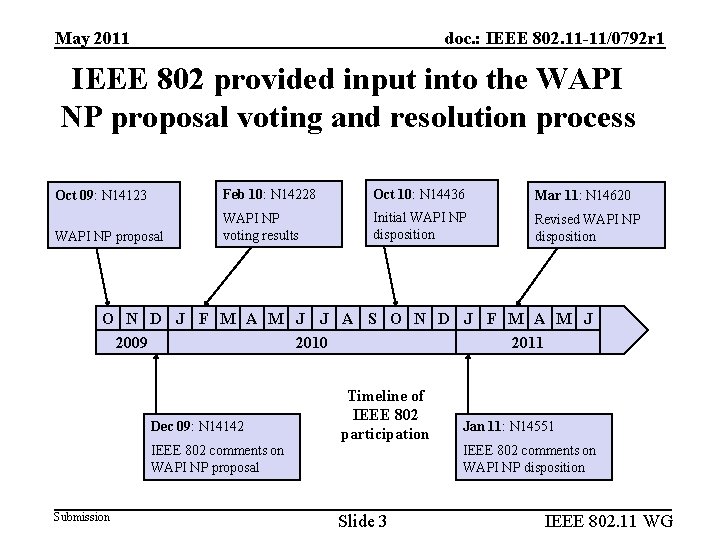
May 2011 doc. : IEEE 802. 11 -11/0792 r 1 IEEE 802 provided input into the WAPI NP proposal voting and resolution process Oct 09: N 14123 Feb 10: N 14228 Oct 10: N 14436 Mar 11: N 14620 WAPI NP proposal WAPI NP voting results Initial WAPI NP disposition Revised WAPI NP disposition O N D J F M A M J J A S O N D J F M A M J 2009 D 2010 J 2011 Dec 09: N 14142 IEEE 802 comments on WAPI NP proposal Submission Timeline of IEEE 802 participation Slide 3 Jan 11: N 14551 IEEE 802 comments on WAPI NP disposition IEEE 802. 11 WG

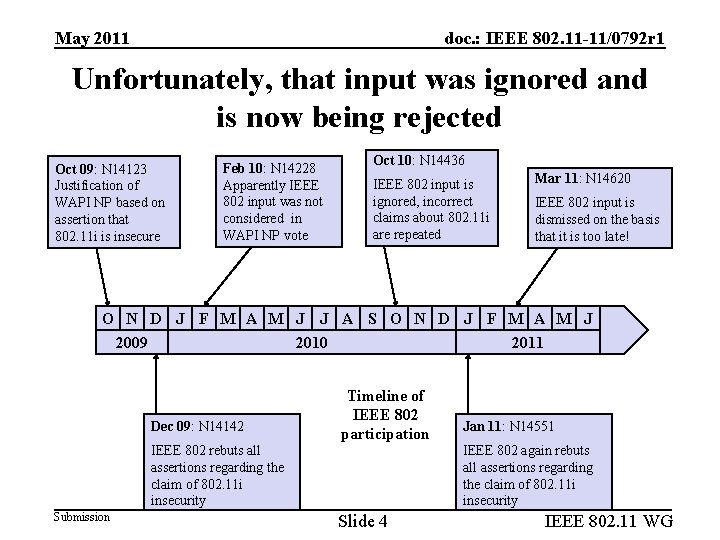
May 2011 doc. : IEEE 802. 11 -11/0792 r 1 Unfortunately, that input was ignored and is now being rejected Oct 09: N 14123 Justification of WAPI NP based on assertion that 802. 11 i is insecure Feb 10: N 14228 Apparently IEEE 802 input was not considered in WAPI NP vote Oct 10: N 14436 IEEE 802 input is ignored, incorrect claims about 802. 11 i are repeated Mar 11: N 14620 IEEE 802 input is dismissed on the basis that it is too late! O N D J F M A M J J A S O N D J F M A M J 2009 D 2010 J 2011 Dec 09: N 14142 IEEE 802 rebuts all assertions regarding the claim of 802. 11 i insecurity Submission Timeline of IEEE 802 participation Slide 4 Jan 11: N 14551 IEEE 802 again rebuts all assertions regarding the claim of 802. 11 i insecurity IEEE 802. 11 WG

May 2011 doc. : IEEE 802. 11 -11/0792 r 1 802. 11, 802. 11 i, and 8802 -11 • Initial 802. 11 standard, IEEE 802. 11 -1999 did have a recognized flaw – Security protocol, WEP, was broken soon after publication • IEEE 802. 11 initiated work in 2001 to provide robust security which resulted in the 802. 11 i amendment in 2004 – Provides scalable and flexible authentication using 802. 1 x/EAP – Provides key confirmation and secure derivation of session keys – Provides provably secure authenticated encryption of data • 802. 11 i was reviewed by cryptographers and security professionals • 802. 11 i amended the IEEE 802. 11 standard and is part of 8802 -11 Submission Slide 5 IEEE 802. 11 WG

May 2011 doc. : IEEE 802. 11 -11/0792 r 1 N 14123: WAPI NP justification entirely based on assertion that 802. 11 is insecure • Single assertion to justify WAPI NP: – “It is a well known fact that current WLAN international standards contain serious security loopholes which need to be dealt with by enhanced security mechanisms. ” • Evidence to support this assertion: – “Can your neighbors router make yours sick? ”– Hu, et al, 2008 – “A Wi-Fi virus outbreak? Researchers say it’s possible”– article in Network World, 2008 – “Practical Attacks Against WEP and WPA”– Beck and Tews, 2008 – “A Practical Message Falsification Attack on WPA”– Ohigashi and Morii, 2009 Submission Slide 6 IEEE 802. 11 WG

May 2011 doc. : IEEE 802. 11 -11/0792 r 1 N 14142: IEEE 802 rebuts all claims of 802. 11 i insecurity • “Can your neighbor’s router make yours sick? ” – Assumes either no security, or WEP, on an AP. WEP has been deprecated in favor of 802. 11 i! Says nothing about 802. 11 i. • “A Wi-Fi Virus Outbreak? Researchers say it’s possible” – Refers to paper by Hu et al– i. e. no security or WEP, not 802. 11 i • “Practical Attacks against WEP and WPA” – WPA attack is against TKIP and its MIC, Michael, which is not a one -way function, and whose security is not assumed strong. TKIP was designed in 2003 with a 5 year expectation of validity. Paper says nothing about mandatory aspects of 802. 11 i (i. e. it addresses WPA not WPA 2). • “A Practical Message Falsification Attack Against WPA” – An improvement on paper above-- it’s WPA, no mention of WPA 2 Submission Slide 7 IEEE 802. 11 WG

May 2011 doc. : IEEE 802. 11 -11/0792 r 1 N 14228: Significant Lack of Consideration of IEEE 802 rebuttal during WAPI NP vote • US NB – Two comments made challenging the statement that 802. 11 i is insecure (apparent consideration of IEEE 802 rebuttal). – Seven other substantive comments submitted. • UK NB – Comments alluding to technical concerns. – Mostly focused on “standalone security issue”. • No other NB submitted comments – Silence implies the rebuttal was not considered. Submission Slide 8 IEEE 802. 11 WG

May 2011 doc. : IEEE 802. 11 -11/0792 r 1 N 14436: Repeats, and extends, invalid claims regarding 802. 11 i security • IEEE 802 rebuttal of previous claims are completely ignored. • Asserts that “Security loopholes in the current IS (ISO/IEC 8802 -11) have been reported in the security literature” but provides no evidence to support that claim. • Additional, new, unsubstantiated claims – WAPI can protect against fake STA/AP attacks and 802. 11 i cannot. – In N 14123, N 14399, N 14402 and N 14410 all “comprehensively address weaknesses in existing network security”. – Specific security problems were asserted during 802. 11 i fast track ballot in 2006. Submission Slide 9 IEEE 802. 11 WG

May 2011 doc. : IEEE 802. 11 -11/0792 r 1 N 14551: IEEE 802 Rebuts New Claims of 802. 11 i insecurity • Repetition of N 14123 – Already addressed by N 14142! Unfortunately N 14142 was ignored. • N 14410 refers to IEEE 802. 16 Security Issues: A Survey – This notes that security was not designed into IEEE 802. 11 -2003, says nothing about IEEE 802. 11 -2004 (or ISO/IEC 8802 -11) • N 14399, N 14402 and N 14410 make claims on lack of mutual authentication between STA, AP and AS – RFC 4017 -compliant EAP methods perform mutual authentication, the AP/AS distinction is logical and in many deployments does not apply, the 4 -way Handshake confirms AS has disclosed PMK to AP and provides implicit authentication. • Claims made during Fast Track Balloting of 802. 11 i – Same sort of non-mutual authentication assertions. Submission Slide 10 IEEE 802. 11 WG

May 2011 doc. : IEEE 802. 11 -11/0792 r 1 N 14620: IEEE 802 Objections and Rebuttal of invalid claims of insecurity dismissed • After failing to address comments per the Directives, they are dismissed on the basis that the comment disposition is no longer concerned with the WAPI NP proposal – “This comment is focusing on the Justification of ISO/IEC 20011, but it should be noted that the NP ballot has passed; the main comment and contribution in this state should be focused and changed to the editing and commenting of WD text. ” • This does not meet our expectations of a mutually beneficial relationship with SC 6 Submission Slide 11 IEEE 802. 11 WG

May 2011 doc. : IEEE 802. 11 -11/0792 r 1 IEEE 802’s Current View of the Process is Best Summarized in Conclusion of N 14551 • IEEE 802 respectfully requests consideration: – … the fundamental justification for a WAPI NP in SC 6 is based on the assertion that there are security loopholes or flaws in mandatory security components included in 802. 11 (and its amendments). However, no valid or credible evidence has been provided to support this assertion. • The reality is that mandatory security components included 802. 11 have no known “security loopholes”. This statement is practically supported by the use of 802. 11 in millions of systems worldwide, in high security applications, by governments, financial institutions, telecommunications providers, enterprises and consumers. • IEEE 802 requests SC 6 do not consider any assertions that mandatory security components included in 802. 11 (and its amendments) are insecure when deciding whether to authorize the WAPI NP proposal. Alternatively, IEEE 802 invites any SC 6 NB to provide valid and credible evidence to the 820. 11 WG of “serious security loopholes”. Submission Slide 12 IEEE 802. 11 WG

May 2011 doc. : IEEE 802. 11 -11/0792 r 1 IEEE 802 Requests SC 6 to Undertake Further Action • Ensure that in all official SC 6 documents there are no unsubstantiated allegations regarding security – For example, the WAPI NP proposal and all associated comment dispositions. – Provide credible evidence of security issues with IEEE 802 technologies • Work with IEEE 802 to improve the security of IEEE 802 technologies – Comments received on IEEE 802. 11 s Draft 10. 0 were very helpful Submission Slide 13 IEEE 802. 11 WG

May 2011 doc. : IEEE 802. 11 -11/0792 r 1 References Submission Slide 14 IEEE 802. 11 WG