May 2011 doc IEEE 15 12 0458 01









- Slides: 30

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward Project: IEEE P 802. 15 Working Group for Wireless Personal Area Networks (WPANs) Submission Title: Moving KMP Forward Date Submitted: September 19, 2012 Source: Robert Moskowitz, Verizon Address 1000 Bent Creek Blvd, Mechanics. Burg, PA, USA Voice: +1 (248) 968 -9809, e-mail: rgm@labs. htt-consult. com Re: Key Managementn over 4 e Multipurpose Frames Abstract: Discussion of KMP transport Purpose: To refine our understanding of the transport mechism Notice: This document has been prepared to assist the IEEE P 802. 15. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) reserve(s) the right to add, amend or withdraw material contained herein. Release: The contributor acknowledges and accepts that this contribution becomes the property of IEEE and may be made publicly available by P 802. 15. Submission 1 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward Moving KMP Forward Robert Moskowitz Palm Springs, CA Sept 19, 2012 Submission 2 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward Abstract Agreements to date Open items Next steps Submission 3 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward Agreements to date KMP encapsulation data format State Machines general content General statements on Security Associations KMP guidelines general format Submission 4 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP Transport Use a COMMAND Frame IE for KMP encapsulation – – 802. 15. 4 IE with max size of 2047 802. 15. 7 IE max size of 255 • • Submission Multiple IEs per frame an option Issue with COMMAND frame, need to file maintenance item 5 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP Transport MAC details – Unauthenticated PDUs always use long addresses • – KMP payload MAY be fragmented over multiple IEs/frames • Submission e. g. KMP rekeying within authenticated PDUs MAY use short addresses Use Forced ACK for fragmentation chaining support 6 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP Information Element Frame format – MAC specific information • ID/Length – – – Content • • Submission 802. 15. 4 = 0 x 0 a/max 2047 802. 15. 7 = 0 x 03/max 255 Control Field – 1 byte KMP fragment 7 Robert Moskowitz,

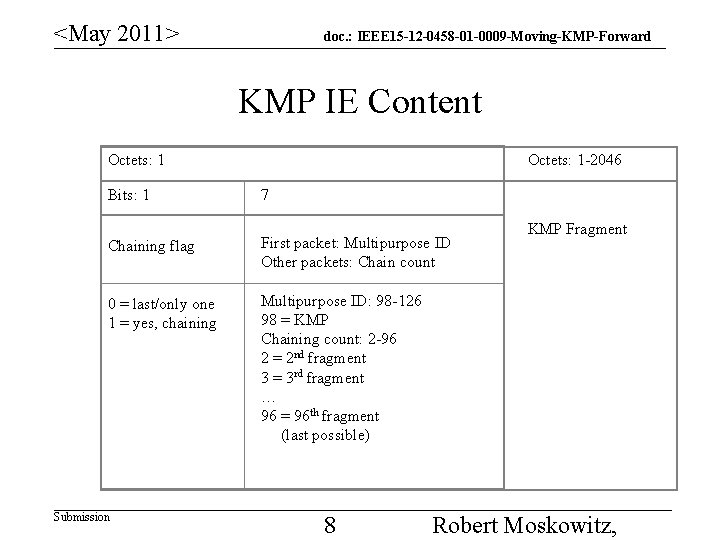
<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP IE Content Octets: 1 Bits: 1 Octets: 1 -2046 7 Chaining flag First packet: Multipurpose ID Other packets: Chain count 0 = last/only one 1 = yes, chaining Multipurpose ID: 98 -126 98 = KMP Chaining count: 2 -96 2 = 2 nd fragment 3 = 3 rd fragment … 96 = 96 th fragment (last possible) Submission 8 KMP Fragment Robert Moskowitz,

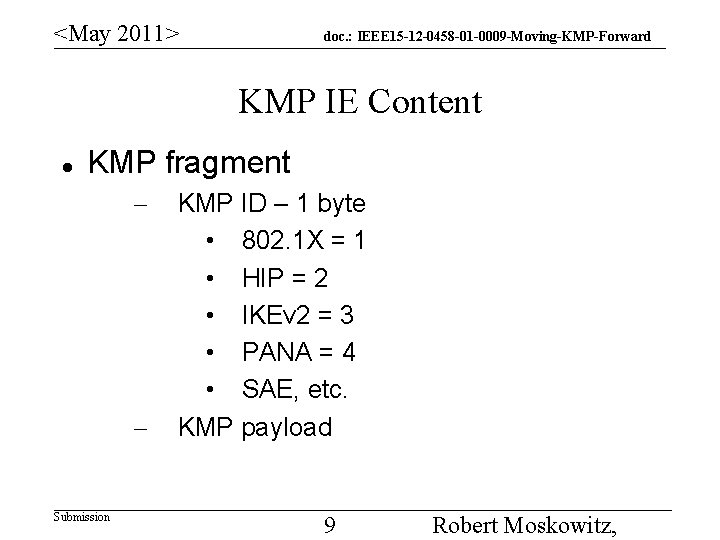
<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP IE Content KMP fragment – – Submission KMP ID – 1 byte • 802. 1 X = 1 • HIP = 2 • IKEv 2 = 3 • PANA = 4 • SAE, etc. KMP payload 9 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP Content Examples go here! Submission 10 Robert Moskowitz,

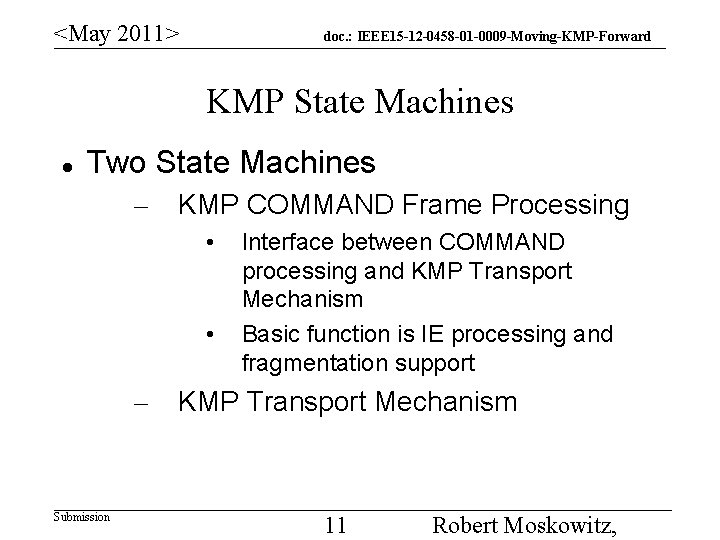
<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP State Machines Two State Machines – KMP COMMAND Frame Processing • • – Submission Interface between COMMAND processing and KMP Transport Mechanism Basic function is IE processing and fragmentation support KMP Transport Mechanism 11 Robert Moskowitz,

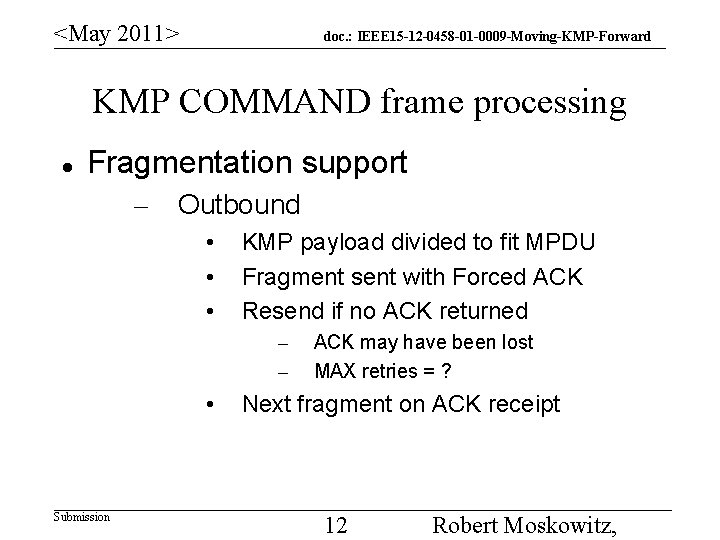
<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP COMMAND frame processing Fragmentation support – Outbound • • • KMP payload divided to fit MPDU Fragment sent with Forced ACK Resend if no ACK returned – – • Submission ACK may have been lost MAX retries = ? Next fragment on ACK receipt 12 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP COMMAND frame processing Fragmentation support – Inbound • Assemble payload from frame received and send ACK – • Submission Could be a duplicate fragment » ACK lost Deliver payload to KMP on completion 13 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP Transport Mechanism State machine to handle triggers to/from KMP higher layer – – Pass through for KMP payloads Triggers from MAC events to KMP • • Submission Security Enabled to start KMP Frame Counter watch to trigger rekey 14 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP Transport Mechanism Security enabled trigger – mac. Security. Enabled = True on device • – Start KMP as first transmission to Coordinator – Before Associate? mac. Security. Enabled = True on coordinator • • Receipt of unsecured frame force start? Receipt of secure frame with unknown keys – Submission Coordinator lost keys (eg reboot) force start? 15 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP Transport Mechanism Frame counter trigger – mac. Frame. Counter = 0 xffff – n • • Submission Where n allows rekeying before key exhaustion Start KMP rekeying With unicast keying either device MAY trigger rekeying? ASSUMPTION: Only coordinators send with group keys and rekey as needed 16 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward Security and PAN architecture Pairwise keying is used for unicast traffic – 2 sets of Security Associations (SAs) Peer-to-Peer communications will only be unicast traffic due to the hidden node challenge Submission 17 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward Security and PAN architecture Two basic SA tables – – Submission Key Table Device Table 18 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP Security Associations Security Association content – – Submission What keys? PTK, GTK, etc. Counters, lifetimes, etc. 19 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP Security Associations Group SAs ASSUMPTIONS – There is no MAC Multicast, only Broadcast • – Submission Question: Did 6 lowpan allocate a Multicast MAC address for ND? Non-coordinator nodes ignore broadcasts 20 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward 15. 4 Specifics Pre 15. 4 e device support – For 6 lowpan PANs • • Submission Develop a submission to the IETF using the Dispatch Type in RFC 4944 PDUs with the KMP Dispatch Type a length field will be equivalent to the 15. 4 e KMP IE A 6 lowpan device that supports 15. 4 e SHOULD also support this pre-15. 4 e mode of operation Who wants to author this? 21 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP Guidelines KMP Sections – General KMP description • – – Use case(s) 802. 15 Profile • • – References to defining documents Parameter specifics, e. g. in HIP, K=0 SA definition • Submission Sub sections as needed, e. g. backend authentication mechanism E. G. Tie into security PID 22 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP Guidelines Initial list of KMPs – 802. 1 X • – – Submission Needs to include an actual key exchange like the 802. 11 i 4 -way handshake HIP – R. Moskowitz/J. Haapola IKEv 2 – T. Kivinen PANA – Yoshihiro Ohba SAE 23 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP Guidelines KMP Profiling for 15. 9 usage – Change in encapsulation • – Additions for SA management • • – Submission e. g. IKEv 2 specified to run over UDP e. g. 802. 1 X does not supply link keys. In 802. 11 usage, this is done via the 4 Way Handshake Special attention to broadcast keying management Others? 24 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward KMP Guidelines KMP use cases – Why this KMP? • • – – Practical examples Deployment advice • • – Submission Code size, CPU/battery demand Multi-layer code reuse Identity installation and registration When performed Life-cycle management • Rekeying 25 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward Open Items Submission 26 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward 15. 4 Security Options Unclear what are the valid constructs – Encrypt controlled by mac. Security. Enabled OR Security. Level • • Submission Thus application can force security when it is not generally selected Likewise an application can set Security. Level to Zero to disable protection for a datagram 27 Robert Moskowitz,

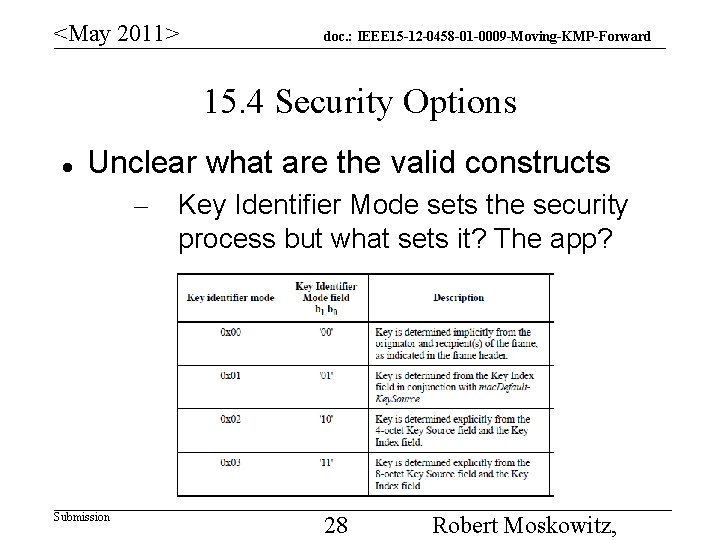
<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward 15. 4 Security Options Unclear what are the valid constructs – Submission Key Identifier Mode sets the security process but what sets it? The app? 28 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward 15. 4 Security Options Unclear what are the valid constructs – Limit to Key Identifier Mode explicit? • • • Submission Key. Id. Mode = 0 x 00 Per device pair keying (unicast) PAN broadcast Coordinator broadcast (for beacons) Device broadcast to coordinator 29 Robert Moskowitz,

<May 2011> doc. : IEEE 15 -12 -0458 -01 -0009 -Moving-KMP-Forward Next Steps Submission 30 Robert Moskowitz,